Poliseek: A Fast XACML Policy Evaluation Engine Using Dimensionality Reduction and Characterized Search
Abstract
1. Introduction
2. Related Work
2.1. Rearranging Rules in Reordering and Clustering with Statistical Analysis
2.2. Match Process with Decision Diagram and Finite-State Machine
2.2.1. Decision Diagram
2.2.2. Finite-State Machine
2.3. Normalizing Policy Set with Predicate Logic in Formal Description
3. Preliminary Definitions
3.1. Abbreviations
- R: a complex rule vector in an XACML policy.
- RQ: a user request vector represented by XACML.
- SR: a sub-rule vector with atomic attribute values.
- ISR: a sub-rule vector with atomic attribute intervals.
- CV: a candidate value, a single-point value in projection results obtained by dimensionality reduction.
- ICV: a candidate interval, an interval value in projection results.
3.2. Conventional Notations
- : an integer set.
- W: an identification space, a one-dimensional space of the dimensionality reduction results where CV’s and ICV’s are distributed.
- : denotes the absolute value of the variable x.
- I: a unit matrix.
3.3. Functions
- E(x) calculates the mathematical expectation of a random variable x.
- f(x) refers to the probability density function of an attribute value x in request vectors.
- T(X) returns an m × 1 vector whose elements are m sum values of each row in an m × n matrix X.
3.4. Operators
- represents the union of sets A and B.
- represents the scalar product of two matrices or vectors A and B.
- represents the operation of multiplying each element in an n × k matrix B by each row element on the corresponding position in a 1 × k column vector A; it returns an n × k matrix.
- returns a matrix Cn×k whose element cij is the smaller value between the elements in the same position in n × k matrices A and B.
- returns a matrix Cn×k whose element cij is the larger value between the elements in the same position in n × k matrices A and B.
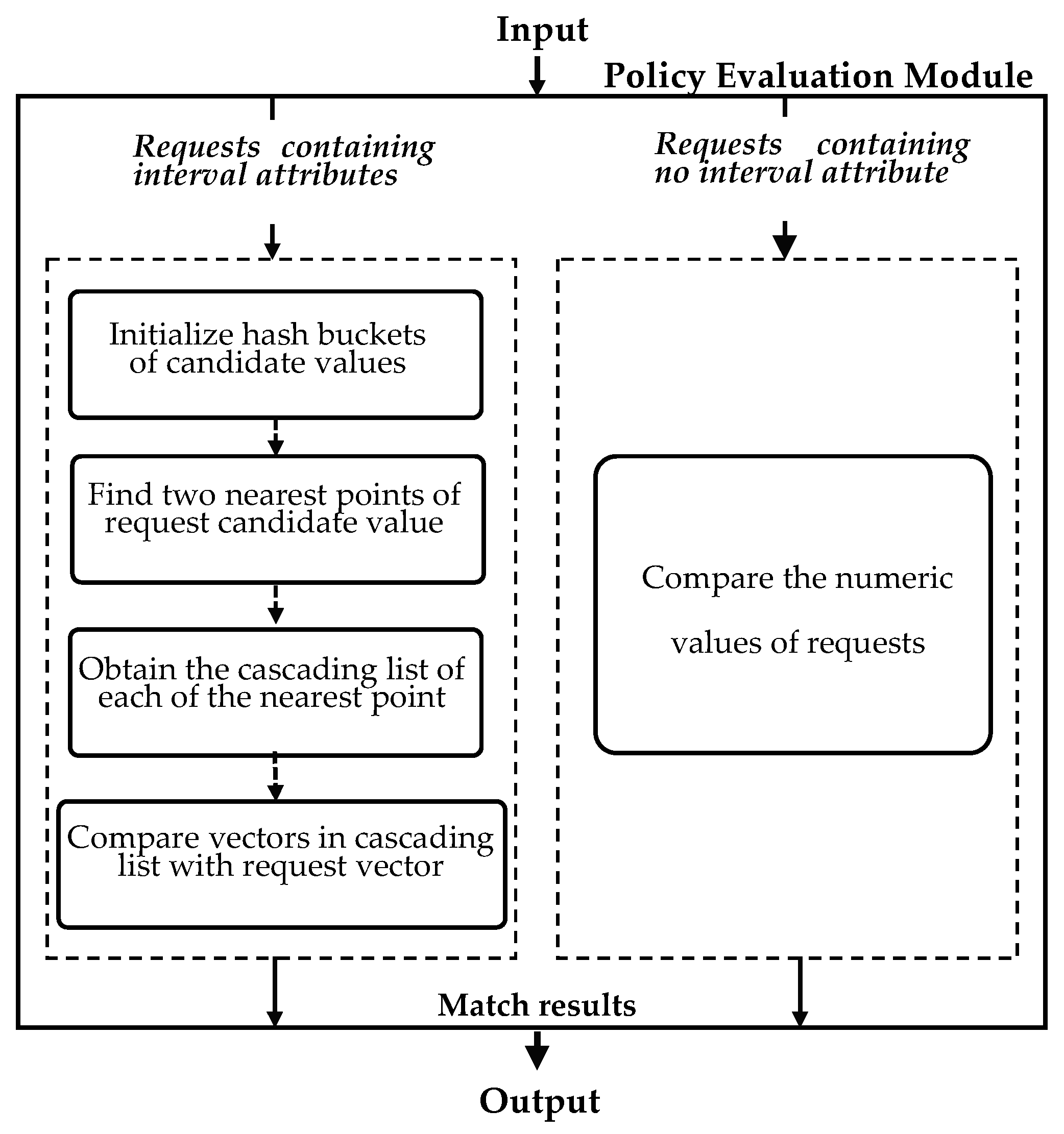
4. Approach Overview
4.1. Policy Preprocessing Module
4.2. Rule Dimensionality Reducer and Rule Diffuser
4.3. Policy Evaluation Module
5. Formalization of Rule Dimensionality Reducer and Diffuser
5.1. Preprocessing Methods for Interval and Default Values
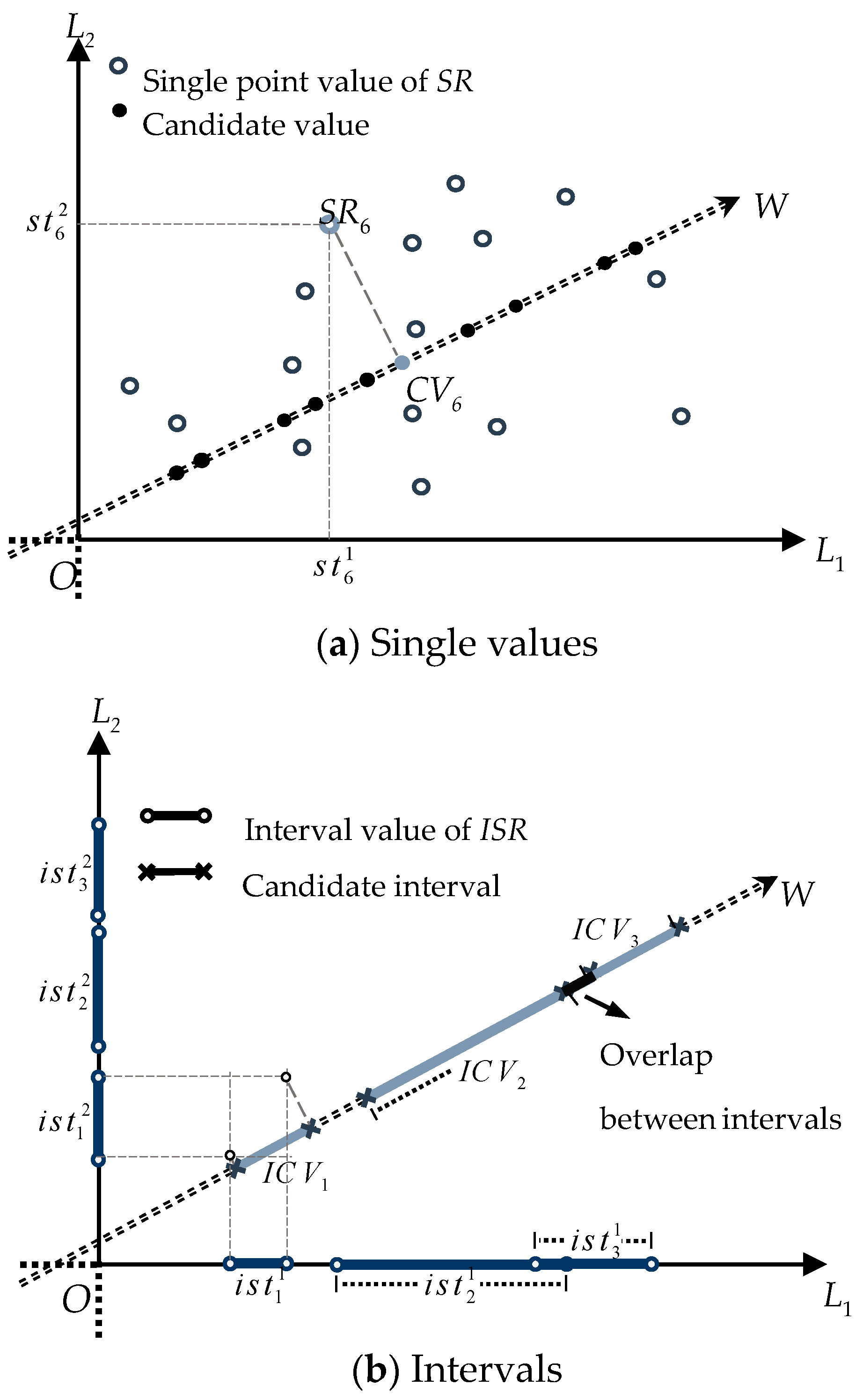
5.2. Construction of Rule Dimensionality Reducer
5.3. Design and Optimization of Rule Diffuser
- (1)
- Preparation
- (2)
- Construction of optimization model for converting vectors in diffuser
| Algorithm 1: Calculating Candidate Results for XACML Rules | |
| Input: NV: numerical vectors of XACML rules (SR’s and ISR’s) | |
| Output: CR: candidate results (CV’s and ICV’s) | |
| 1: | begin: Calculating_Candidate_Values(SR) |
| 2: | for in NV |
| 3: | = extend() |
| 4: | end for |
| 5: | L, R, ω = Initialize(NV) |
| 6: | |
| 7: | |
| 8: | object = Expected_Activated_Value() |
| 9: | constraint: |
| 10: | ω = Differential_Evolution(object, constraints, NV) |
| 11: | for in NV |
| 12: | |
| 13: | CR.join() |
| 15: | end for |
| 16: | for in NV |
| 17: | |
| 18: | CR.join() |
| 19: | end for |
| 20: | return CR |
| 21: | end |
6. Fast Policy Evaluation Module
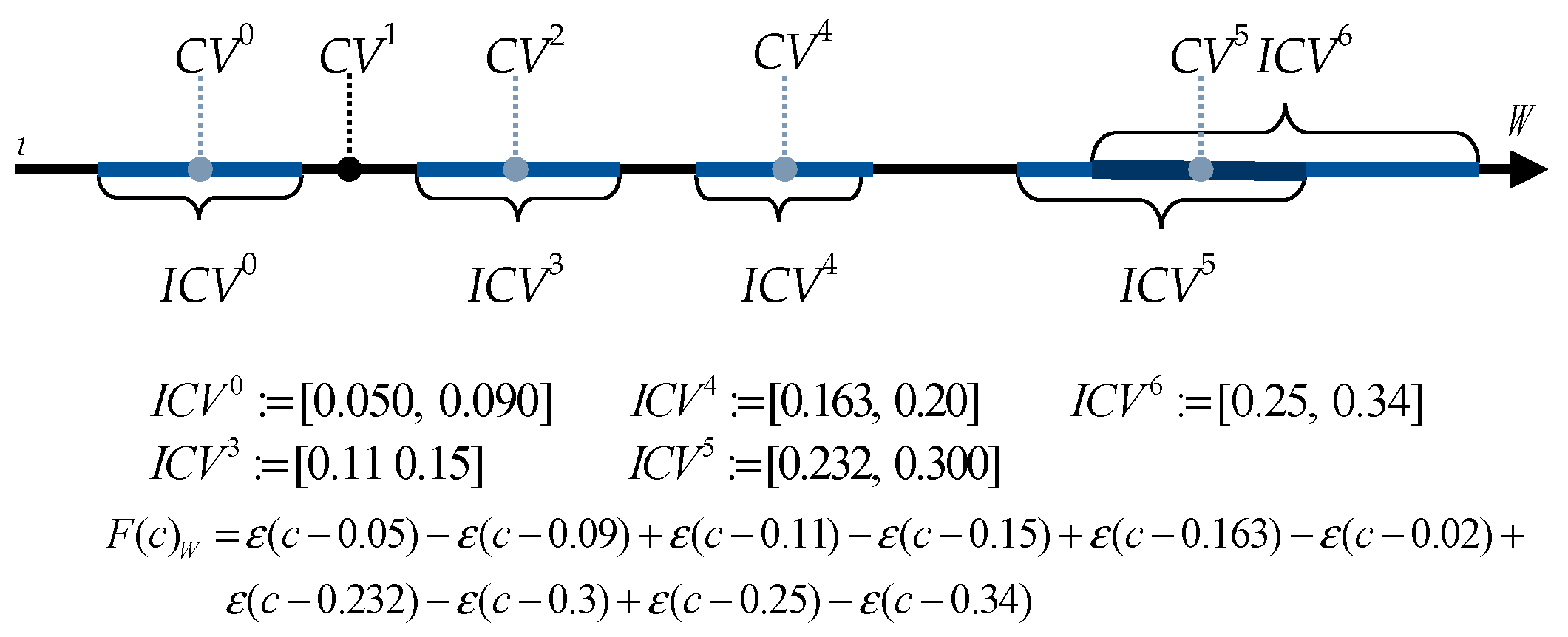
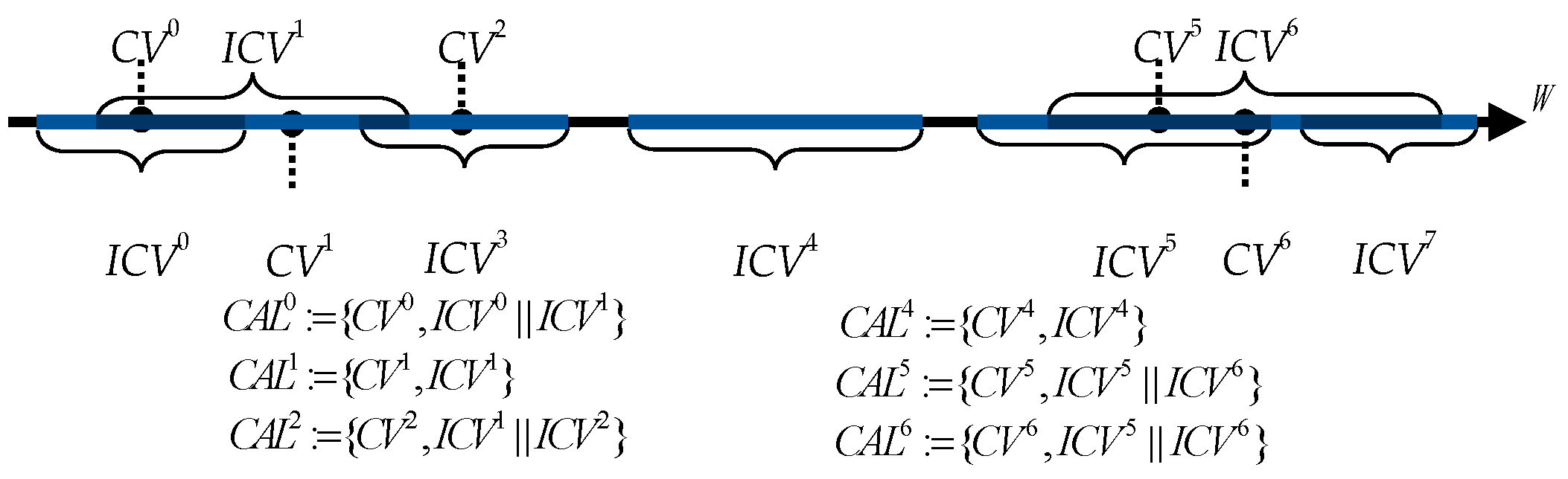
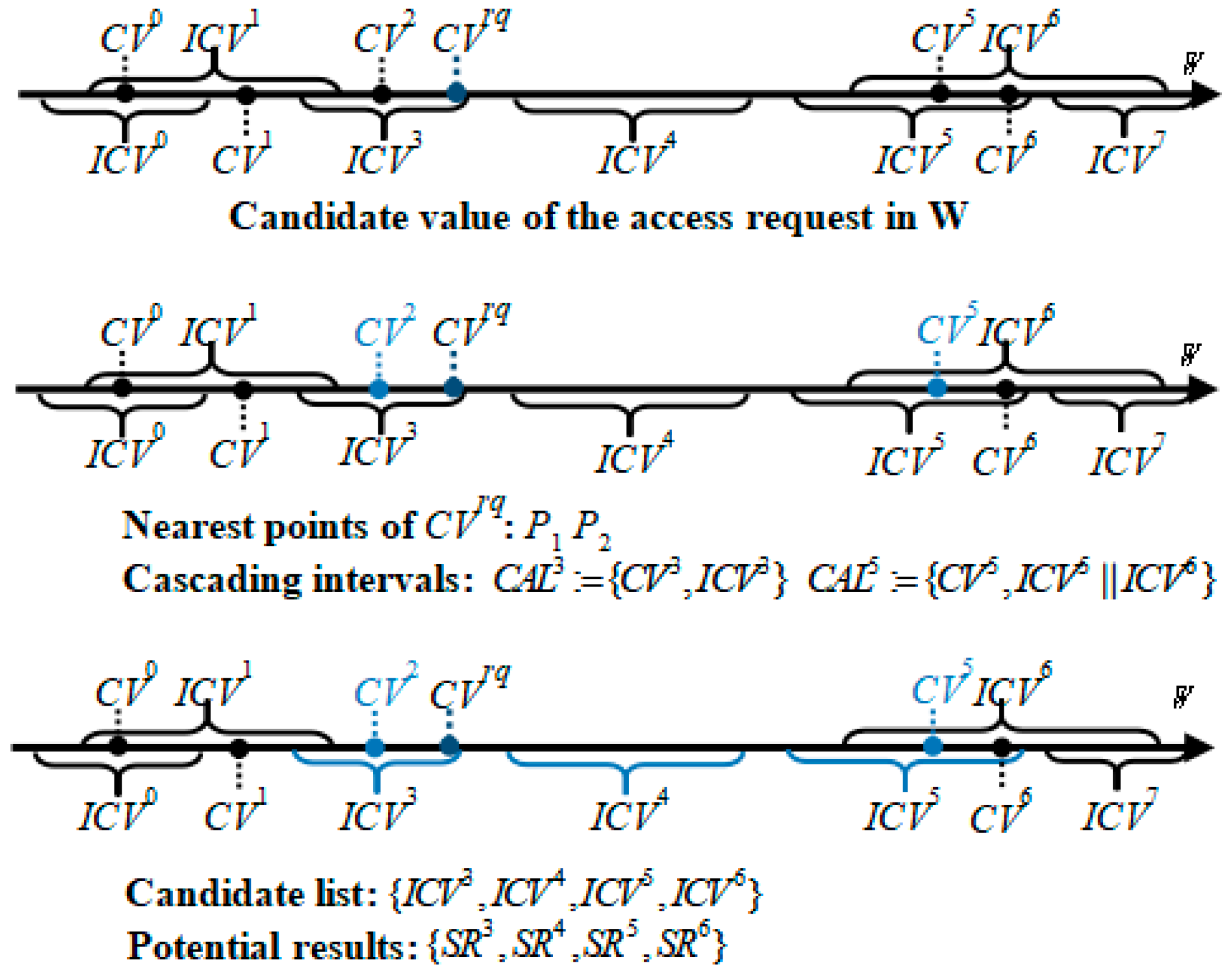
6.1. Cascading Adjacent Candidate Intervals
| Algorithm 2: Cascading Adjacent Intervals | |
| Input: : candidate value of rules | |
| Output: : cascading intervals | |
| 1: | begin: Cascading_Adjacent_Intervals() |
| 2: | forin all candidate intervals |
| 3: | if |
| 4: | .insert() |
| 5: | end if |
| 6: | end for |
| 7: | return |
| 8: | end |
6.2. Policy Evaluation for Access Requests
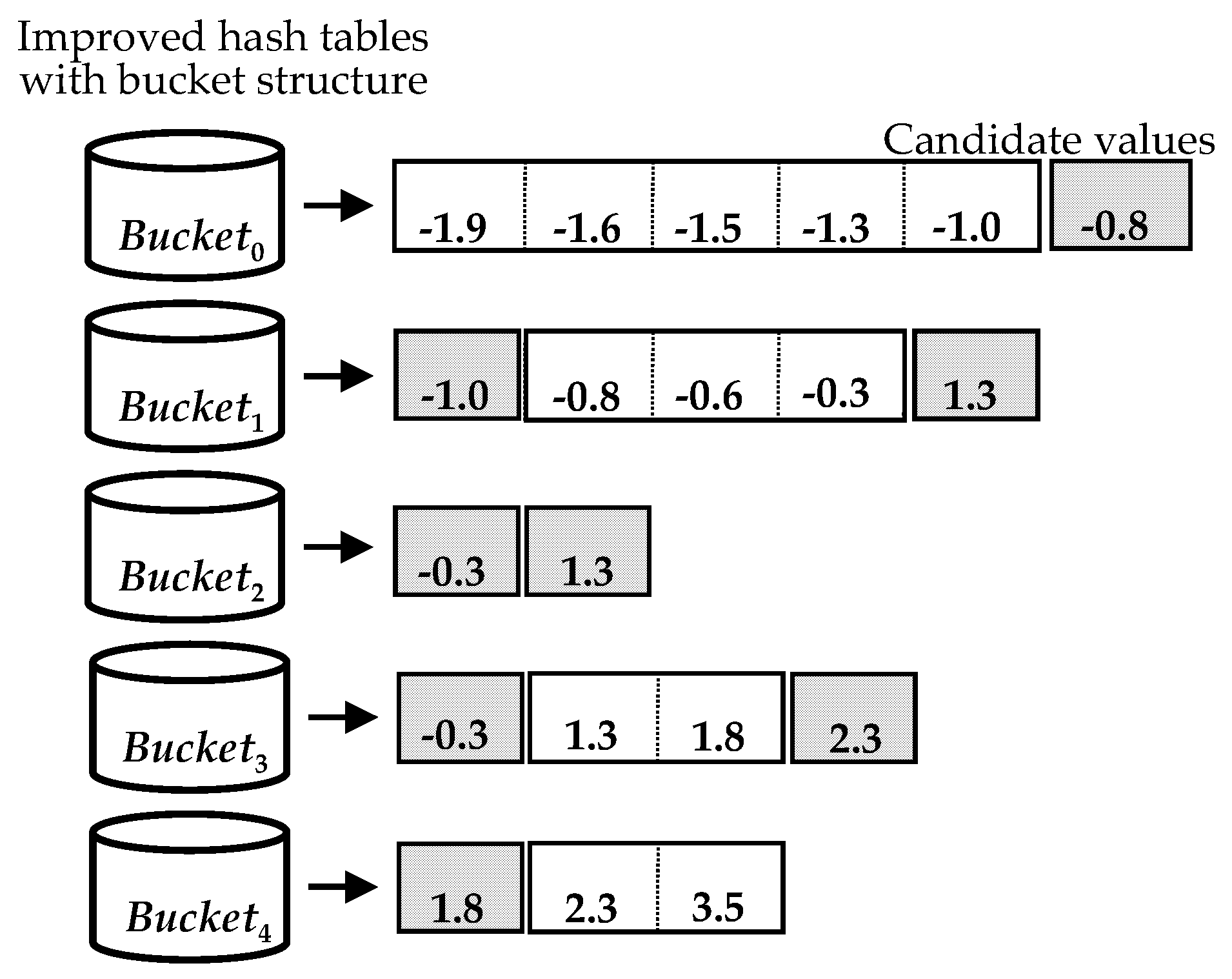
6.2.1. Search Values Using Modified Hash Tables
6.2.2. Candidate List and Interval Match
| Algorithm 3: Interval Policy Match Algorithm | |
| Input: CVRQ: candidate value of requests | |
| Output: MR: match results | |
| 1: | begin: Policy_Evaluation(CVRQ) |
| 2: | hash_tables = Initialize() |
| 3: | potential_bucket = hash_tables[CVRQ] |
| 4: | P1, P2 = Searching_Algorithm(potential_bucket) |
| 5: | CALP1 = Cascading_Adjacent_Intervals(P1) |
| 6: | CALP2 = Cascading_Adjacent_Intervals(P2) |
| 7: | candidate_list= |
| 8: | for interval in [P1, P2] |
| 9: | if intervalcandidate_list |
| 10: | candidate_list.join(interval) |
| 11: | end if |
| 12: | end for |
| 13: | for potential_interval in candidate_list |
| 14: | MR = vector_compare(rq,potential_interval) |
| 15: | end for |
| 16: | return MR |
| 17: | end |
7. Evaluation Experiments and Performance Analysis
7.1. Policy Configuration and Experimental Settings
7.2. Generation of Test Requests
7.3. Design and Constitution of Policy Evaluation Experiments
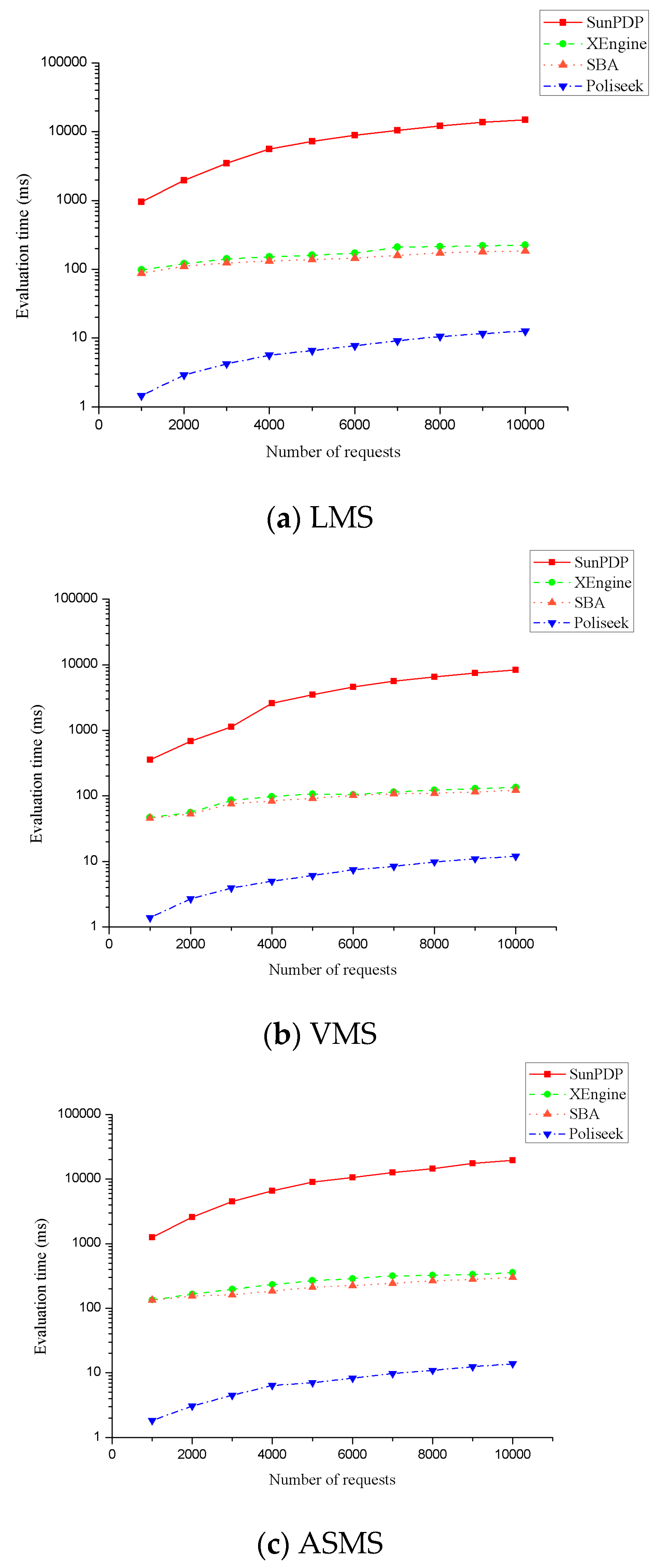
7.4. Comparisons and Analyses of Policy Evaluation Results
- (1)
- Evaluation Performance of Single Values
- (1)
- Poliseek can maintain the shortest evaluation time in all three policy sets, and Sun PDP spends more than ten times the evaluation time of XEngine and SBA-XACML.
- (2)
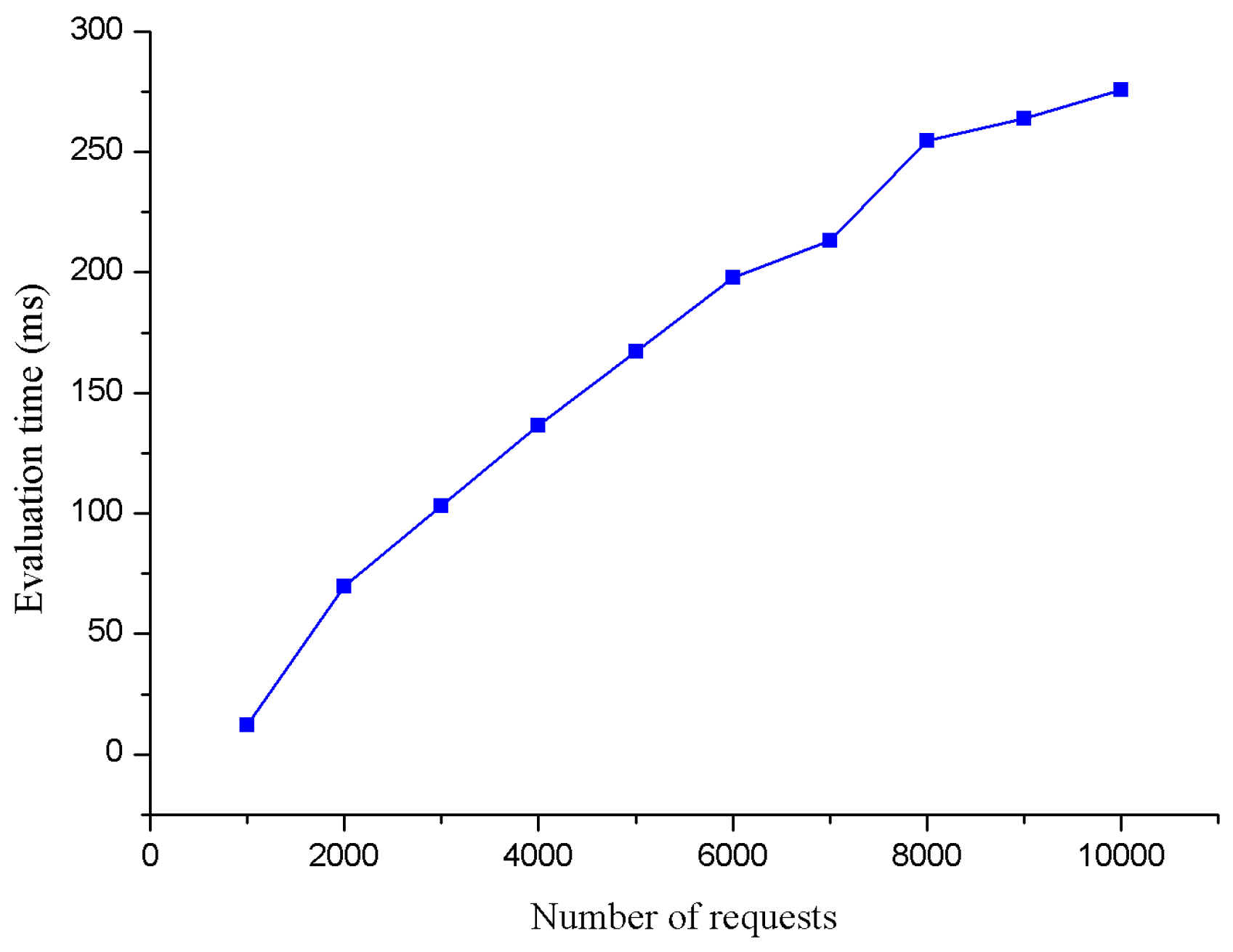
- When the number of test requests increases to 10,000, Poliseek only costs approximately 10 ms, but Sun PDP encounters severe performance loss. XEngine and SBA-XACML have relatively steady performances of approximately 100 ms time cost.
- (3)
- When the number of test requests reaches 10,000, the evaluation time of Sun PDP, XEngine, and SBA-XACML are 691 times, 11 times, and 10 times longer than Poliseek in LMS, 1169 times, 10 times, and 14 times longer in VMS, 1410 times, 25 times, and 21 times longer in ASMS, respectively. Hence, it can be concluded that Poliseek is far superior to other schemes for evaluation performance.
- (4)
- When the number of test requests exceeds 10,000, with the increase in the number of requests, the evaluation time of Poliseek is always controlled within 10 ms, which proves that Poliseek has good stability and can effectively be applied to the request evaluation task of large-scale or even super-large-scale policy sets.
- (2)
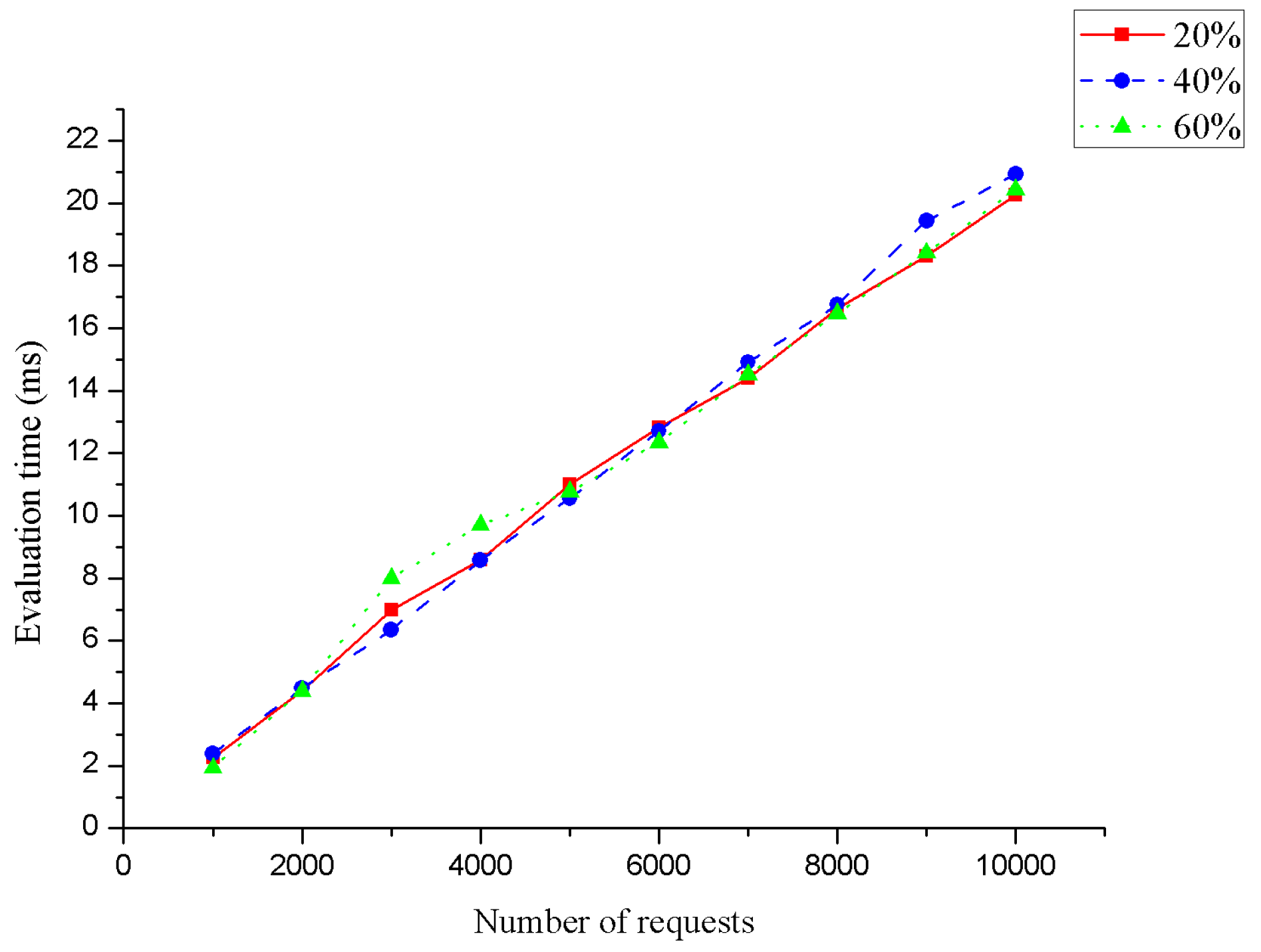
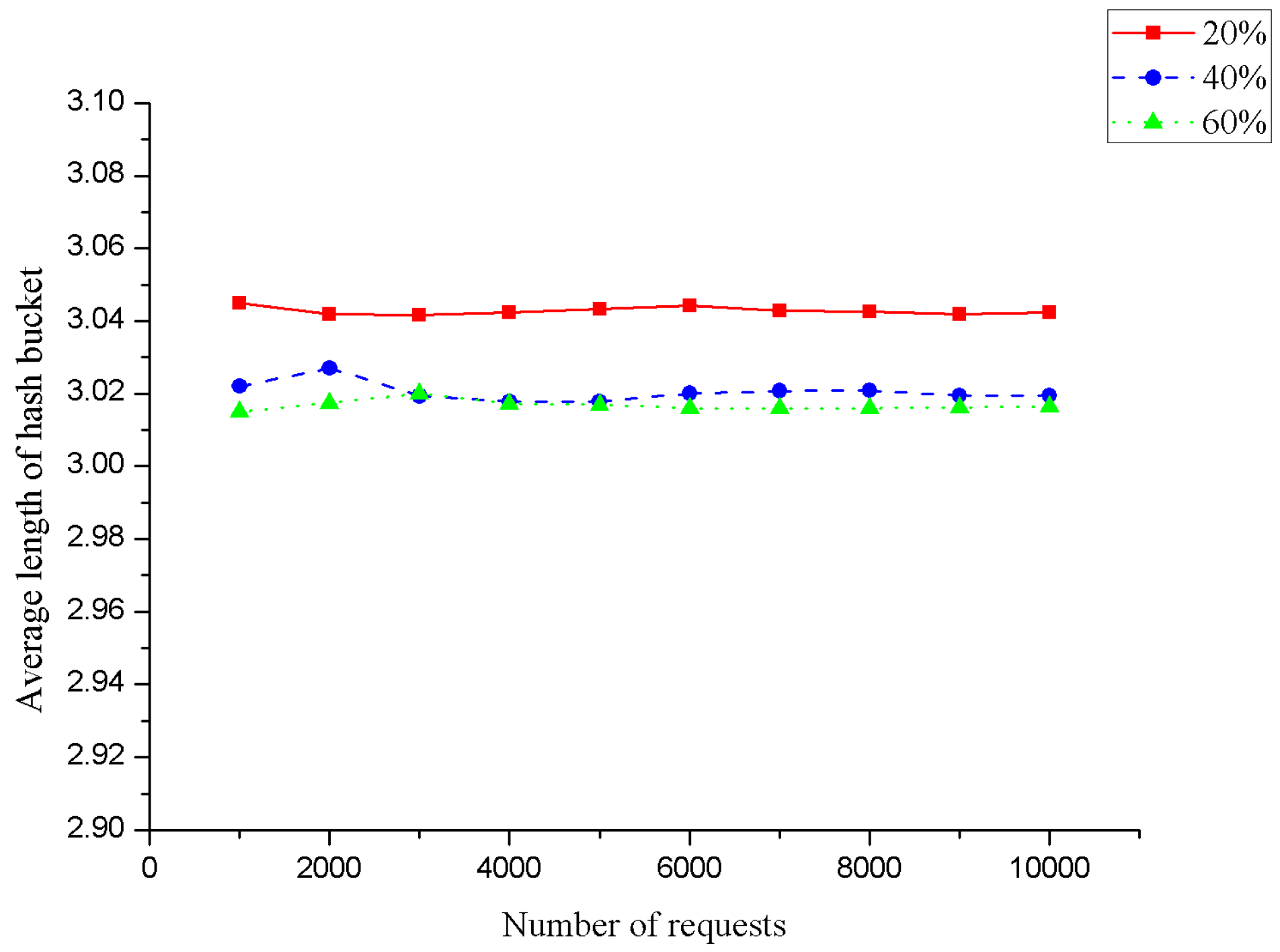
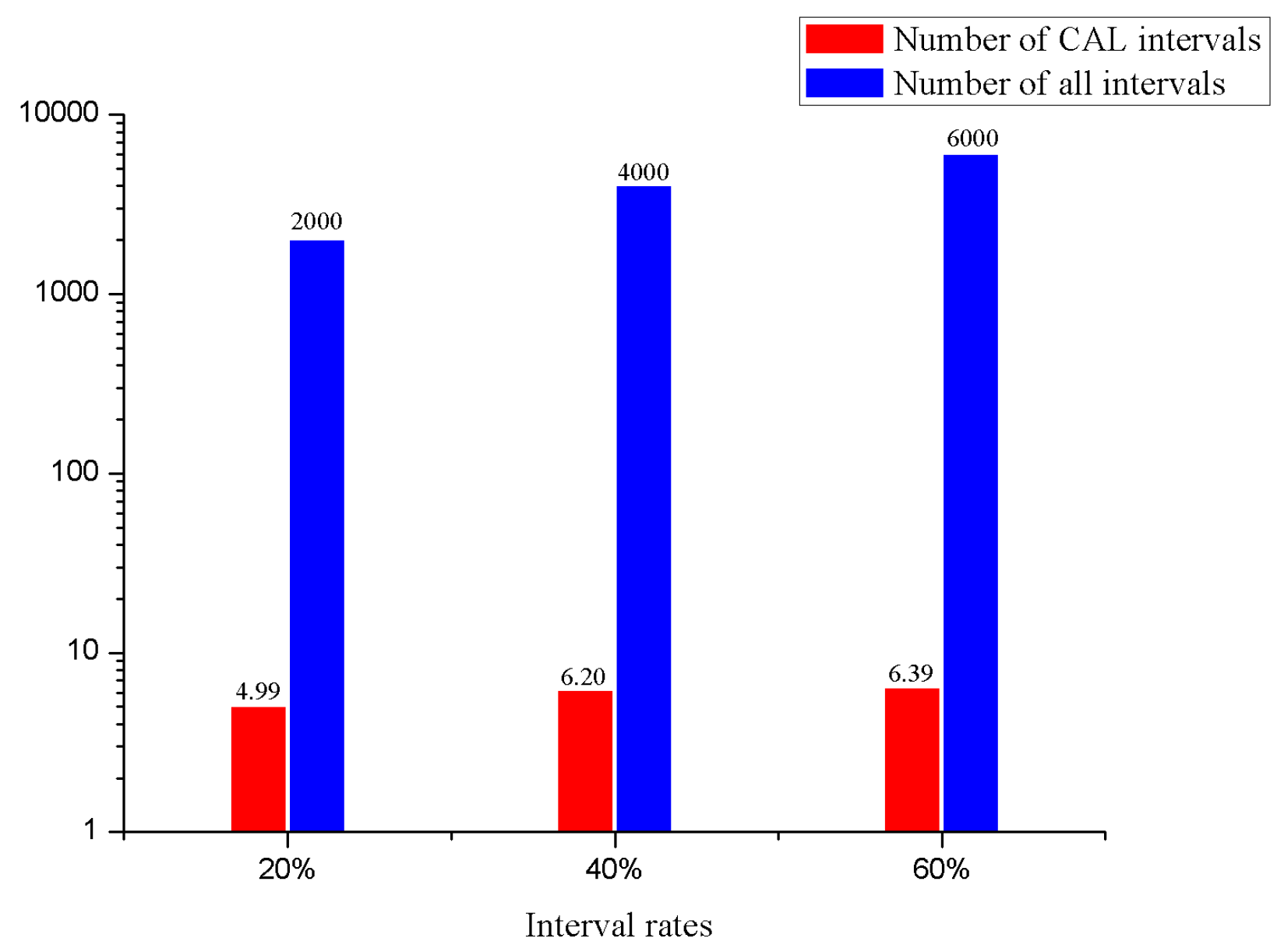
- Effect of Intervals on Evaluation Performance
- (3)
- Effect of Intervals on Other Aspects
8. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Nomenclature
| R | A complex rule vector in an XACML policy |
| RQ | A user request vector represented by XACML |
| SR | A sub-rule vector with atomic attribute values |
| ISR | A sub-rule vector with atomic attribute intervals |
| CV | A candidate value, a single-point value in projection results obtained by dimensionality reduction |
| ICV | A candidate interval, an interval value in projection results |
| An integer set | |
| W | An identification space, a one-dimensional space of the dimensionality reduction results where CV’s and ICV’s are distributed |
| The absolute value of the variable x | |
| I | A unit matrix |
| E(x) | Calculates the mathematical expectation of a random variable x |
| f(x) | Refers to the probability density function of an attribute value x in request vectors |
| T(X) | Returns an m × 1 vector whose elements are m sum values of each row in an m × n matrix X |
| Represents the union of sets A and B | |
| Represents the scalar product of two matrices or vectors A and B | |
| Represents the operation of multiplying each element in an n × k matrix B by each row element on the corresponding position in a 1 × k column vector A; it returns an n × k matrix | |
| Returns a matrix Cn×k whose element cij is the smaller value between the elements in the same position in n × k matrices A and B | |
| Returns a matrix Cn×k whose element cij is the larger value between the elements in the same position in n × k matrices A and B | |
| The jth value in the lth category of the ith attribute | |
| The jth sub-rule derived from | |
| The ith value in the set of Rk | |
| A set of values for each in N sub-rules |
References
- Qin, X.; Huang, Y.; Yang, Z.; Li, X. LBAC: A lightweight blockchain-based access control scheme for the internet of things. Inf. Sci. 2020, 554, 222–235. [Google Scholar] [CrossRef]
- Deng, F.; Yu, Z.; Zhang, L.; Wang, J.; Feng, K.; Kong, W.; Li, L.; Wu, J. ANNPDP: An Efficient and Stable Evaluation Engine for Large-Scale Policy Sets. IEEE Trans. Serv. Comput. 2020, 15, 1926–1939. [Google Scholar] [CrossRef]
- Margheri, A.; Masi, M.; Pugliese, R.; Tiezzi, F. A Rigorous Framework for Specification, Analysis and Enforcement of Access Control Policies. IEEE Trans. Softw. Eng. 2017, 45, 2–33. [Google Scholar] [CrossRef]
- Gao, L.; Yan, Z.; Yang, L.T. Game Theoretical Analysis on Acceptance of a Cloud Data Access Control System Based on Reputation. IEEE Trans. Cloud Comput. 2016, 8, 1003–1017. [Google Scholar] [CrossRef]
- Dammak, M.; Senouci, S.-M.; Messous, M.A.; Elhdhili, M.H.; Gransart, C. Decentralized Lightweight Group Key Management for Dynamic Access Control in IoT Environments. IEEE Trans. Netw. Serv. Manag. 2020, 17, 1742–1757. [Google Scholar] [CrossRef]
- Ning, J.; Cao, Z.; Dong, X.; Liang, K.; Wei, L.; Choo, K.-K.R. CryptCloud+: Secure and Expressive Data Access Control for Cloud Storage. IEEE Trans. Serv. Comput. 2018, 14, 111–124. [Google Scholar] [CrossRef]
- Parducci, B.; Lockhart, H.; Rissanen, E. eXtensible Access Control Markup Language (XACML) Version 3.0, OASIS Standard. 2010. Available online: http://docs.oasis-open.org/xacml/3.0/xacml-3.0-core-spec-os-en.html (accessed on 31 October 2022).
- Althumali, H.; Othman, M.; Noordin, N.K.; Hanapi, Z.M. Priority-based load-adaptive preamble separation random access for QoS-differentiated services in 5G networks. J. Netw. Comput. Appl. 2022, 203, 103396. [Google Scholar] [CrossRef]
- Lee, B.M.; Yang, H. Energy efficient scheduling and power control of massive MIMO in massive IoT networks. Expert Syst. Appl. 2022, 200, 116920. [Google Scholar] [CrossRef]
- Sun, P.J. XACML Policy Evaluation Optimization Research Based on Attribute Weighted Clustering and Statistics Reordering. In Proceedings of the 2017 IEEE International Conference on Information and Automation (ICIA), Macao, China, 18–20 July 2017; pp. 1190–1195. [Google Scholar] [CrossRef]
- Ngo, C.; Makkes, M.X.; Demchenko, Y.; de Laat, C. Multi-data-types interval decision diagrams for XACML evaluation engine. In Proceedings of the 2013 Eleventh Annual Conference on Privacy, Security and Trust, Tarragona, Spain, 10–12 July 2013; pp. 257–266. [Google Scholar] [CrossRef]
- Ngo, C.; Demchenko, Y.; de Laat, C. Decision Diagrams for XACML Policy Evaluation and Management. Comput. Secur. 2015, 49, 1–16. [Google Scholar] [CrossRef]
- Mourad, A.; Tout, H.; Talhi, C.; Otrok, H.; Yahyaoui, H. From model-driven specification to design-level set-based analysis of XACML policies. Comput. Electr. Eng. 2016, 52, 65–79. [Google Scholar] [CrossRef]
- Mourad, A.; Jebbaoui, H. SBA-XACML: Set-based approach providing efficient policy decision process for accessing Web services. Expert Syst. Appl. 2015, 42, 165–178. [Google Scholar] [CrossRef]
- Vasan, K.K.; Surendiran, B. Dimensionality reduction using Principal Component Analysis for network intrusion detection. Perspect. Sci. 2016, 8, 510–512. [Google Scholar] [CrossRef]
- DeCarlo, L.T. Psychol methods: On the meaning and use of kurtosis. Psychol. Methods 1997, 2, 292–307. [Google Scholar] [CrossRef]
- Xia, X. A conflict detection approach for XACML policies on hierarchical resources. In Proceedings of the IEEE International Conference on Green Computing and Communications, Besancon, France, 20 November 2012; pp. 755–760. [Google Scholar]
- Jebbaoui, H.; Mourad, A.; Otrok, H.; Haraty, R. Semantics-based approach for detecting flaws, conflicts and redundancies in XACML policies. Comput. Electr. Eng. 2015, 44, 91–103. [Google Scholar] [CrossRef]
- Deng, F.; Zhang, L.-Y. Elimination of policy conflict to improve the PDP evaluation performance. J. Netw. Comput. Appl. 2017, 80, 45–57. [Google Scholar] [CrossRef]
- Deng, F.; Chen, P.; Zhang, L.-Y.; Wang, X.-Q.; Li, S.-D.; Xu, H. Policy Decomposition for Evaluation Performance Improvement of PDP. Math. Probl. Eng. 2014, 2014, 1–14. [Google Scholar] [CrossRef]
- Marouf, S.; Shehab, M.; Squicciarini, A.; Sundareswaran, S. Adaptive Reordering and Clustering-Based Framework for Efficient XACML Policy Evaluation. IEEE Trans. Serv. Comput. 2010, 4, 300–313. [Google Scholar] [CrossRef]
- Liu, X.; Li, T.; Zhou, Z.; Hu, L. An efficient multi-objective reliability-based design optimization method for structure based on probability and interval hybrid model. Comput. Methods Appl. Mech. Eng. 2022, 392, 114682. [Google Scholar] [CrossRef]
- Yang, C.; Wang, Z.; Oh, S.-K.; Pedrycz, W.; Yang, B. Ensemble fuzzy radial basis function neural networks architecture driven with the aid of multi-optimization through clustering techniques and polynomial-based learning. Fuzzy Sets Syst. 2022, 438, 62–83. [Google Scholar] [CrossRef]
- Liu, A.X.; Chen, F.; Hwang, J.; Xie, T. Designing Fast and Scalable XACML Policy Evaluation Engines. IEEE Trans. Comput. 2010, 60, 1802–1817. [Google Scholar] [CrossRef]
- Liu, T.; Wang, Y. Beyond Scale: An Efficient Framework for Evaluating Web Access Control Policies in the Era of Big Data. In Advances in Information and Computer Security, Proceedings of the 10th International Workshop on Security, IWSEC 2015, Nara, Japan, 26–28 August 2015; Springer: Berlin/Heidelberg, Germany, 2015; pp. 316–334. [Google Scholar] [CrossRef]
- Ros, S.P.; Lischka, M.; Mármol, F.G. Graph-based XACML evaluation. In Proceedings of the ACM Symposium on Access Control Models and Technologies, Newark, NJ, USA, 20 June 2012; pp. 83–92. [Google Scholar]
- Sun’s XACML Implementation. Available online: http://sunxacml.sourceforge.net/ (accessed on 21 November 2022).
- Ayache, M.; Erradi, M.; Freisleben, B.; Khoumsi, A. Towards an Efficient Policy Evaluation Process in Multi-Tenancy Cloud Environments. In Proceedings of the 2016 ACM on Cloud Computing Security Workshop, New York, NY, USA, 28 October 2016; pp. 55–59. [Google Scholar] [CrossRef]
- Deng, F.; Wang, S.-Y.; Zhang, L.-Y.; Wei, X.-Q.; Yu, J.-P. Establishment of attribute bitmaps for efficient XACML policy evaluation. Knowl.-Based Syst. 2018, 143, 93–101. [Google Scholar] [CrossRef]
- Turkmen, F.; Hartog, J.D.; Ranise, S.; Zannone, N. Analysis of XACML policies with SMT. In Proceedings of the International Conference on Principles of Security and Trust, London, UK, 11 April 2015; pp. 115–134. [Google Scholar]
- Turkmen, F.; Demchenko, Y. On the use of SMT solving for XACML policy evaluation. In Proceedings of the International Conference on Cloud Computing Technology and Science, Hong Kong, China, 11 December 2017; pp. 539–544. [Google Scholar]
- Turkmen, F.; Hartog, J.D.; Ranise, S.; Zannone, N. Formal analysis of XACML policies using SMT. Comput. Secur. 2017, 66, 185–203. [Google Scholar] [CrossRef]
- Deng, F.; Yu, Z.; Liu, W.; Luo, X.; Fu, Y.; Qiang, B.; Xu, C.; Li, Z. An efficient policy evaluation engine for XACML policy management. Inf. Sci. 2021, 547, 1105–1121. [Google Scholar] [CrossRef]
- Fang, Z.; Ren, J.; Marshall, S.; Zhao, H.; Wang, S.; Li, X. Topological optimization of the DenseNet with pretrained-weights inheritance and genetic channel selection. Pattern Recognit. 2020, 109, 107608. [Google Scholar] [CrossRef]
- Xie, L.; Yin, M.; Yin, X.; Liu, Y.; Yin, G. Low-Rank Sparse Preserving Projections for Dimensionality Reduction. IEEE Trans. Image Process. 2018, 27, 5261–5274. [Google Scholar] [CrossRef] [PubMed]
- Ouyang, M.; Jeon, T.; Sotiras, A.; Peng, Q.; Mishra, V.; Halovanic, C.; Chen, M.; Chalak, L.; Rollins, N.; Roberts, T.P.L.; et al. Differential cortical microstructural maturation in the preterm human brain with diffusion kurtosis and tensor imaging. Proc. Natl. Acad. Sci. USA 2019, 116, 4681–4688. [Google Scholar] [CrossRef]
- Ximei, L.; Latif, Z.; Changfeng, W.; Latif, S.; Khan, Z.; Wang, X. Mean-variance-kurtosis hybrid multi-objective portfolio optimization model with a defined investment ratio. J. Eng. Technol. 2018, 6, 293–306. [Google Scholar]
- Storn, R.; Price, K. Differential evolution—A simple and efficient heuristic for global optimization over continuous spaces. J. Glob. Optim. 1997, 11, 341–359. [Google Scholar] [CrossRef]
- Yu, Z.; Si, Z.; Li, X.; Wang, D.; Song, H. A novel hybrid particle swarm optimization algorithm for path planning of UAVs. IEEE Internet Things J. 2022, 9, 22547–22558. [Google Scholar] [CrossRef]
- Manaseer, S.; Hwaitat, A.K.A. Measuring parallel performance of sorting algorithms. Mod. Appl. Sci. 2018, 12, 23–31. [Google Scholar] [CrossRef][Green Version]
- Pretschner, A.; Baudry, B. Test-driven assessment of access control in legacy applications. In Proceedings of the International Conference on Software Testing, Verification, and Validation, Lillehammer, Norway, 9 April 2008; pp. 238–247. [Google Scholar]
- Mouelhi, T.; Fleurey, F.; Baudry, B.; Traon, Y.L. A model-based framework for security policy specification, deployment and testing. In Proceedings of the 11th International Conference on Model Driven Engineering Languages and Systems, Toulouse, France, 28 September 2008; pp. 537–552. [Google Scholar]
- Mouelhi, T.; Le Traon, Y.; Baudry, B. Transforming and Selecting Functional Test Cases for Security Policy Testing. In Proceedings of the 2009 International Conference on Software Testing Verification and Validation, Denver, CO, USA, 1–4 April 2009; pp. 171–180. [Google Scholar] [CrossRef]
- Bertolino, A.; Lonetti, F.; Marchetti, E. Systematic XACML request generation for testing purposes. In Proceedings of the 36th EUROMICRO Conference on Software Engineering and Advanced Applications, Washington, DC, USA, 1 September 2010; pp. 3–11. [Google Scholar]
- Bertolino, A.; Daoudagh, S.; Lonetti, F.; Marchetti, E. Automatic XACML requests generation for policy testing. In Proceedings of the IEEE Fifth International Conference on Software Testing, Verification and Validation, Montreal, QC, Canada, 18 April 2012; pp. 842–849. [Google Scholar]
- Martin, E.; Xie, T. A fault model and mutation testing of access control policies. In Proceedings of the 16th International World Wide Web Conference, Banff, AB, Canada, 8 May 2007; pp. 667–676. [Google Scholar]
- Martin, E.; Tao, X. Automated test generation for access control policies via change-impact analysis. In Proceedings of the ICSE 2007 Workshops: Third International Workshop on Software Engineering for Secure Systems, Minneapolis, MN, USA, 20 May 2007; pp. 5–6. [Google Scholar]
- Yu, Z.; Sohail, A.; Jamil, M.; Beg, O.A.; Tavares, J. Hybrid algorithm for the classification of fractal designs and images. Fractals 2022, 30, 1–20. [Google Scholar] [CrossRef]
- Sohail, A.; Yu, Z.; Arif, R.; Nutini, A.; Nofal, T. Piecewise differentiation of the fractional order CAR-T cells-SARS-2 virus model. Results Phys. 2022, 33, 1–7. [Google Scholar] [CrossRef] [PubMed]
- Yu, Z.; Gao, H.; Wang, D.; Alnuaim, A.; Firdausi, M.; Mostafa, A. SEI2RS malware propagation model considering two infection rates in cyber-physical systems. Phys. A Stat. Mech. Its Appl. 2022, 597, 1–12. [Google Scholar] [CrossRef]
- Yu, Z.; Wang, H.; Wang, D.; Li, Z.; Song, H. CGFuzzer: A fuzzing approach based on coverage-guided generative adversarial networks for industrial IoT protocols. IEEE Internet Things J. 2022, 9, 21607–21619. [Google Scholar] [CrossRef]
- Yu, Z.; Sohail, A.; Nofal, T.; Tavares, J. Explainability of neural network clustering in interpreting the COVID-19 emergency data. Fractals 2022, 30, 1–10. [Google Scholar] [CrossRef]
- Li, H.; Zhang, M.; Chen, D.; Zhang, J.; Meng, Y.; Li, Z. Image Color Rendering Based on Hinge-Cross-Entropy GAN in Internet of Medical Things. Comput. Model. Eng. Sci. 2023, 135, 779–794. [Google Scholar] [CrossRef]

| A Typical Example of an XACML Rule | |
|---|---|
| 1: | <Policy> |
| 2: | <Rule Effect = “Permit” RuleId = “R26”> |
| 3: | <Target> |
| 4: | <Subject> |
| 5: | <AttributeValue>Julius Hibbert<AttributeValue> |
| 6: | </Subject> |
| 7: | <Resource> |
| 8: | <AttributeValue>comment</AttributeValue> |
| 9: | </Resource> |
| 10: | <Action> |
| 11: | <AttributeValue>read</AttributeValue> |
| 12: | <AttributeValue>write</AttributeValue> |
| 13: | </Action> |
| 14: | </Target> |
| 15: | <Condition> |
| 16: | <AttributeValue>integer ≤ −1</AttributeValue> |
| 17: | </Condition> |
| 18: | </Rule> |
| 19: | <Rule Effect = “Permit” RuleId = “R27”> |
| 20: | <Target> |
| 21: | <Subject> |
| 22: | <AttributeValue>Jessie<AttributeValue> |
| 23: | </Subject> |
| 24: | <Resource> |
| 25: | <AttributeValue>comment</AttributeValue> |
| 26: | </Resource> |
| 27: | <Action> |
| 28: | <AttributeValue><AnyValue></AttributeValue> |
| 29: | </Action> |
| 30: | </Target> |
| 31: | <Condition> |
| 32: | <AttributeValue>integer≤ 6</AttributeValue> |
| 33: | <AttributeValue>03:23 < time < 04:10</AttributeValue> |
| 34: | </Condition> |
| 35: | </Rule> |
| 36: | </Policy> |
| Subject | Julius Hibbert:1 | Jessie:2 | |
| Resource | comment:1 | ||
| Action | read:1 | write:2 | |
| Requests with Default Value | 1000 | 2000 | 3000 | 4000 | 5000 | 6000 | 7000 | 8000 | 9000 | 10,000 |
|---|---|---|---|---|---|---|---|---|---|---|
| 20% | 2.250 | 4.411 | 6.997 | 8.583 | 11.00 | 12.84 | 14.39 | 16.63 | 18.30 | 20.25 |
| 40% | 2.385 | 4.483 | 6.353 | 8.571 | 10.56 | 12.72 | 14.91 | 16.76 | 19.46 | 20.93 |
| 60% | 1.937 | 4.400 | 8.001 | 9.706 | 10.78 | 12.35 | 14.52 | 16.46 | 18.41 | 20.43 |
| Requests with Default Value | 1000 | 2000 | 3000 | 4000 | 5000 | 6000 | 7000 | 8000 | 9000 | 10,000 |
|---|---|---|---|---|---|---|---|---|---|---|
| Poliseek | 12.04 | 69.91 | 103.2 | 136.4 | 167.1 | 198.0 | 213.2 | 254.7 | 263.9 | 275.9 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Deng, F.; Yu, Z.; Zhan, X.; Wang, C.; Zhang, X.; Zhang, Y.; Qin, Z. Poliseek: A Fast XACML Policy Evaluation Engine Using Dimensionality Reduction and Characterized Search. Mathematics 2022, 10, 4530. https://doi.org/10.3390/math10234530
Deng F, Yu Z, Zhan X, Wang C, Zhang X, Zhang Y, Qin Z. Poliseek: A Fast XACML Policy Evaluation Engine Using Dimensionality Reduction and Characterized Search. Mathematics. 2022; 10(23):4530. https://doi.org/10.3390/math10234530
Chicago/Turabian StyleDeng, Fan, Zhenhua Yu, Xinrui Zhan, Chongyu Wang, Xiaolin Zhang, Yangyang Zhang, and Zilu Qin. 2022. "Poliseek: A Fast XACML Policy Evaluation Engine Using Dimensionality Reduction and Characterized Search" Mathematics 10, no. 23: 4530. https://doi.org/10.3390/math10234530
APA StyleDeng, F., Yu, Z., Zhan, X., Wang, C., Zhang, X., Zhang, Y., & Qin, Z. (2022). Poliseek: A Fast XACML Policy Evaluation Engine Using Dimensionality Reduction and Characterized Search. Mathematics, 10(23), 4530. https://doi.org/10.3390/math10234530







