Abstract
Moth search (MS) is a nature-inspired metaheuristic optimization algorithm based on the most representative characteristics of moths, Lévy flights and phototaxis. Phototaxis signifies a movement which organism towards or away from a source of light, which is the representative features for moths. The best moth individual is seen as the light source in Moth search. The moths that have a smaller distance from the best one will fly around the best individual by Lévy flights. For reasons of phototaxis, the moths, far from the fittest one, will fly towards the best one with a big step. These two features, Lévy flights and phototaxis, correspond to the processes of exploitation and exploration for metaheuristic optimization. The superiority of the moth search has been demonstrated in many benchmark problems and various application areas. A comprehensive survey of the moth search was conducted in this paper, which included the three sections: statistical research studies about moth search, different variants of moth search, and engineering optimization/applications. The future insights and development direction in the area of moth search are also discussed.
MSC:
78M50; 80M50
1. Introduction
Because of the increasing complexity of the optimization problems [1,2], metaheuristic algorithms [3,4,5,6] have become increasingly important for solving these complex optimization problems, such as engineering optimization [7], picture processing [8,9,10,11,12], flow shop scheduling [13,14,15], feature selection [16], path planning [17,18], neural networks [19,20,21,22], multi-objective and many-objective optimization [23,24,25,26,27], shape design [28], object extraction [29], cyber-physical social systems [30], classification [31,32,33,34,35], facial micro-expression recognition [36], big data and large-scale optimization [37,38,39], fuzzy systems [40], and the knapsack problem [41]. These problems have been solved by some well-known methods, such as genetic algorithms (GAs) [42,43], differential evolution (DE) [44,45,46,47,48], particle swarm optimization (PSO) [49,50,51,52,53,54], monarch butterfly optimization (MBO) [55,56,57,58,59], elephant herding optimization (EHO) [60], artificial bee colonies (ABC) [61], polar bear optimization (PBO) [62], ant colony optimization (ACO) [63], harmony search (HS) [64,65,66,67], krill herd (KH) [68,69,70,71,72], cuckoo search (CS) [73,74,75,76,77,78,79], earthworm optimization algorithm (EWA) [80], monkey algorithms (MAs) [81,82], firefly algorithms (FAs) [83,84], moth flame optimization (MFA) [85], grey wolf optimization (GWO) [86], biogeography-based optimization (BBO) [87,88], bat algorithms (BAs) [89], wolf pack algorithm (WPA) [90], and moth search [91].
Inspired by characteristics of moths, Wang [91] proposed a novel swarm intelligence method, namely Moth search (MS) algorithm, in 2018. The MS contains two most representative characteristics of moths, phototaxis and Lévy flights. The moths that have a smaller distance from the best one will fly around the best individual by Lévy flights [92]. The best moth individual is seen as the light source in Moth search, which considered the target for the moths. For reasons of phototaxis, the moths, far from the fittest one, will fly towards the best one with a big step. These two features, Lévy flights and phototaxis, correspond to the processes of exploitation and exploration for metaheuristic optimization. In this paper, a comprehensive review of the MS algorithm, including the walk behavior of the historical development of MS, different variants and applications, are presented.
The remainder of this paper is organized as follows. The walk behavior of the historical development of moth search is detailed in Section 2. Different variants of moth search are presented in Section 3. Engineering optimization/applications are presented in Section 4. A conclusion and suggestions for future work was presented in Section 5.
2. Historical Development of Moth Search
2.1. Moth Search Research Studies
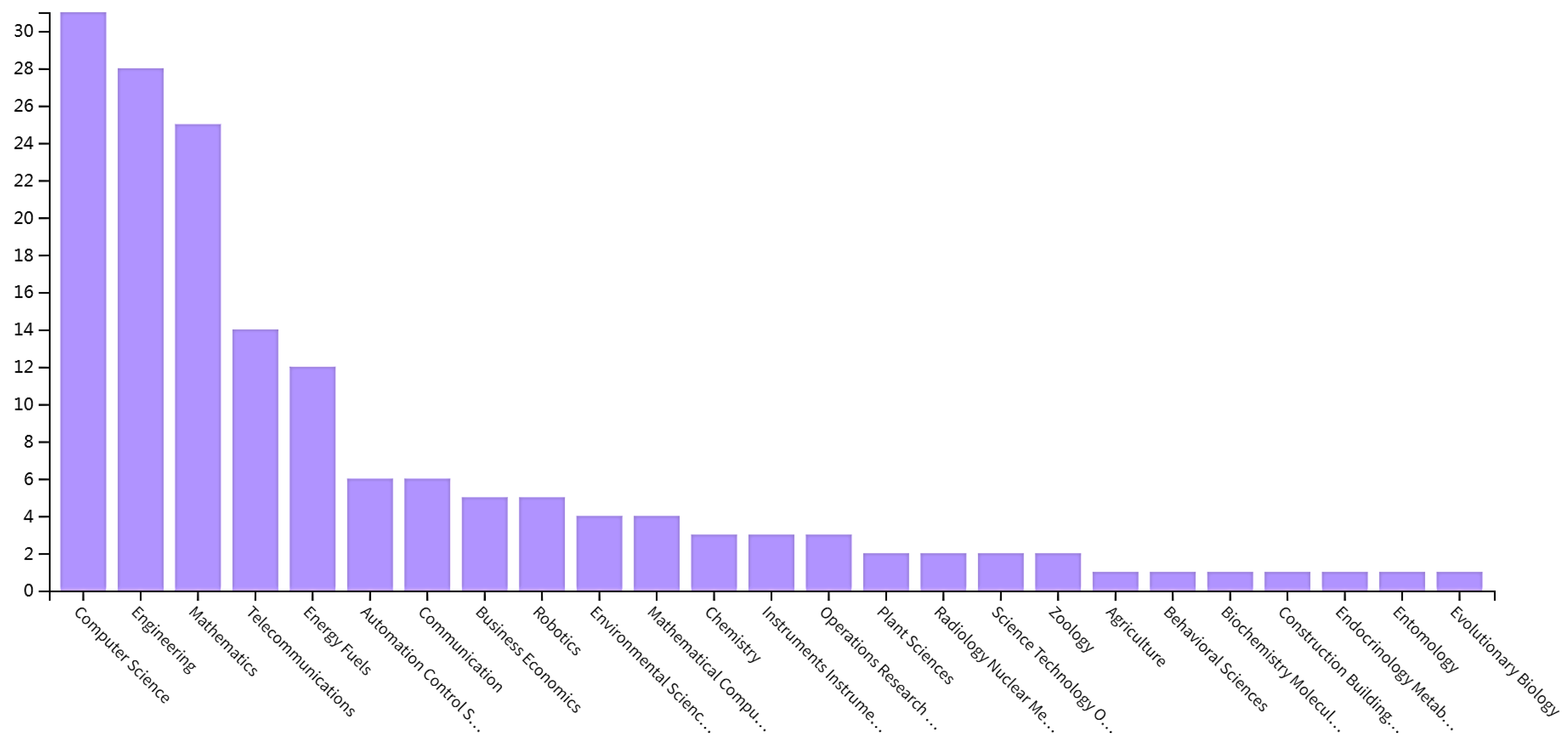
Moth search has been around for a long time. Since moth search was proposed, its related studies have been published up to 23 August 2022. A temporal histogram has been given in Figure 1 and Figure 2 for the collected published articles.
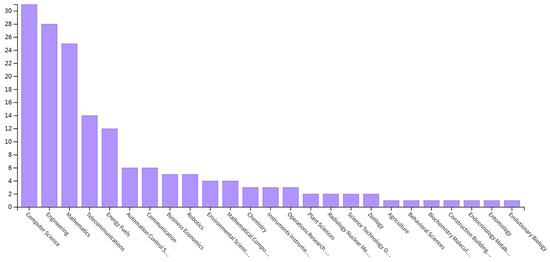
Figure 1.
Related MS publications since 2018.
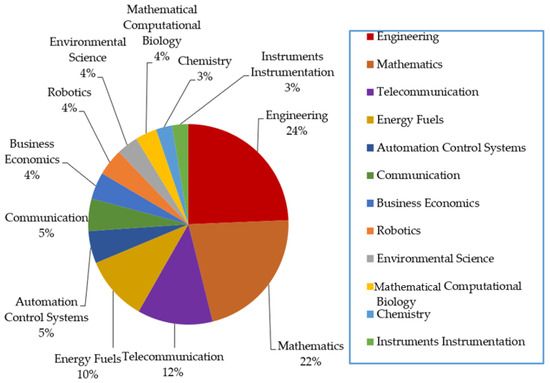
Figure 2.
Related MS publications since 2018.
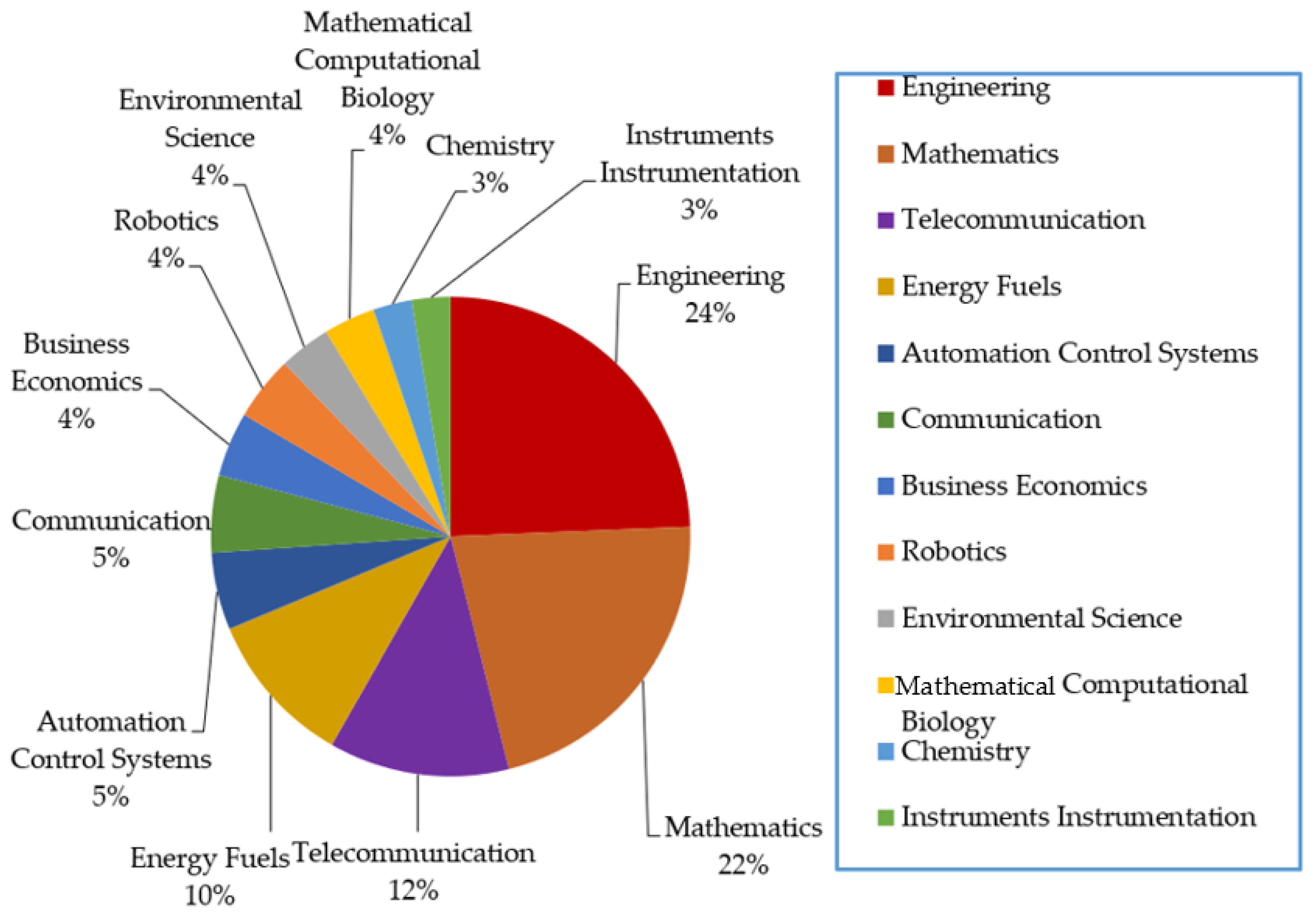
The collected articles are from variety of fields covering mathematics, engineering, telecommunication, energy fuels, automation control systems, communication, business economics, robotics, environmental science, mathematical computational biology, chemistry, instruments instrumentation, operations research management science, plant sciences, radiology nuclear, science technology, zoology, agriculture, behavioral sciences, and biochemistry molecule. Among them, 31 papers were published in computer sciences field, accounting for 59.615%. 28 papers were published in engineering field, accounting for 53.846%. Mathematics field contains 25 papers, accounting for 48.077%. Telecommunication field contains 14 papers, accounting for 26.923%. Energy fuels field contains 12 papers, accounting for 23.077%. Automation control systems field contains 6 papers, accounting for 11.538%. Communication field contains 6 papers, accounting for 11.538%. Business economics field contains 5 papers, accounting for 9.615%. 5 papers were published in robotics field, accounting for 9.615%. Environmental science field contains 4 papers, accounting for 7.692%. Mathematical computational biology field contains 4 papers, accounting for 7.692%. Chemistry field contains 3 papers, accounting for 5.769%. Instruments instrumentation field contains 3 papers, accounting for 5.769%.
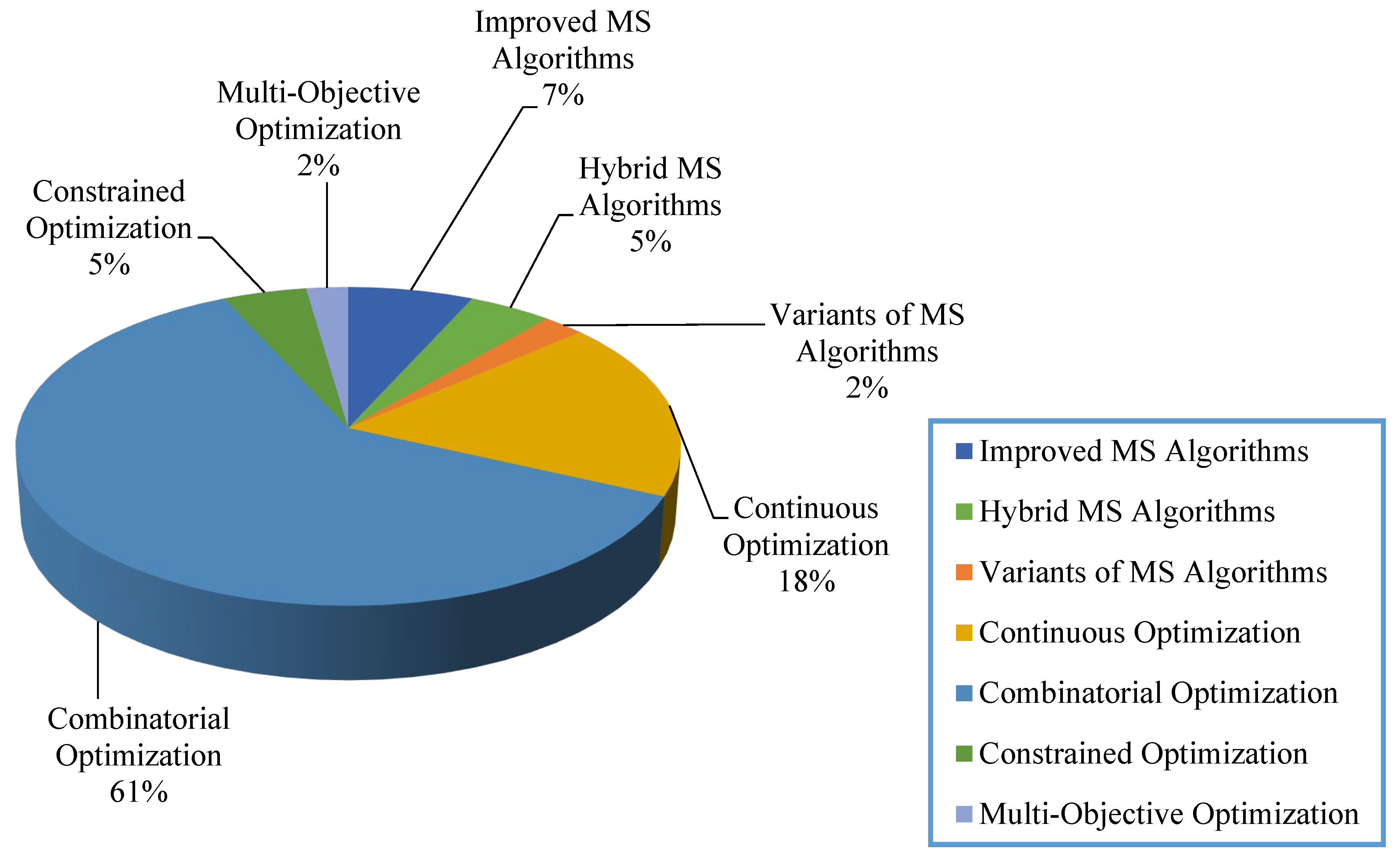
MS optimization was systematically summarized and studied in this paper. From the various papers collected, 56 representative papers from 1 January 2018 to 23 August 2022 were selected and used for our survey. The classification proportions of MS optimization were showed in Figure 3. Table 1 showed that this paper divides the MS optimization into 2 categories: different variants of moth search and engineering optimization/applications. Different variants of moth search are accounting for 14%. Engineering optimization/applications relatively frequently, with its proportion is 86%.
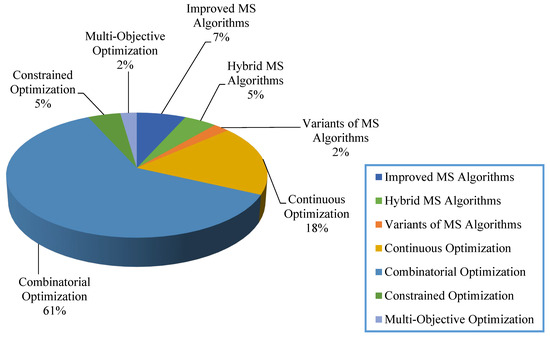
Figure 3.
Classification proportions of MS.

Table 1.
Classification proportions for MS.
2.2. Basics of Moth Search
Moth search (MS) algorithm is a novel swarm intelligence method proposed by Wang in 2018, which inspired by the most representative characteristics of moths [93], Lévy flights and phototaxis. The moths that have a smaller distance from the best one will fly around the best individual by Lévy flights. Others will fly towards the best one in line. According to the fitness, the population was divided into two subgroups in MS algorithm. The moths in subgroup 1 are much closer to the optimal individual than subgroup 2. An offspring of subpopulation 1 and subpopulation 2 is generated by fly straightly and Lévy flights, respectively.
MS is widely used to solve various complex optimization problems in the real world since it was proposed. Despite its searches quickly with high accuracy and wide use, MS suffers from poor balance between exploitation and exploration. Lévy flight with the step size scaling actor is one of the most important parameters for MS algorithm. Lévy flight contains a random walk with continuous heavy tailed distribution. Although Lévy flight can improve performance of the MS algorithm, in the later stage of the algorithm, the MS is easily jumped away from the optimal solution because of the alternate patterns with long and short jumps for the Lévy flight. Therefore, many researchers have proposed some different MS variants of t to improve the global search ability.
2.2.1. Lévy Flights
Lévy flights are a random walk mechanism that satisfies heavy-tailed distribution, which can make large jumps at local locations with a high probability. The probability density distribution of Lévy flight has three characteristics: sharp peaks, asymmetry and trailing. Because of alternated between occasional long-distance jumps and frequent short distance jumps, it can expand the population search area and jump out of local optimal. The moths will fly around the best individual by Lévy flights. For each individual i in subpopulation1, their positions are updated by Lévy flights, as described in Equation (1).
where is the updated position, and is the original position at generation t. L(s) represent the step drawn for Lévy flights. α indicate the scale factor which can be given as:
where indicated as max walk step. The L(s) can be formulated as follows:
where L(s) is the gamma function, and s be regarded as the position of moth individual which is bigger than 0. β = 1.5.
2.2.2. Fly Straightly
It is well-known that phototaxis is moths tend to fly around the light source. The changes in angle will be clearly discernible when a moth that is close to the light source uses it for navigation with a small distance. The moth will instinctively redirect to move towards the light source, which will lead to a path closer to the light source. In this process, the i-th flights can be formulated as:
where indicate an acceleration factor. represent the best moth at the t-th generation. Λ indicate a scale factor which can improve the diversity of the population and control the convergence speed of the algorithm.
On the other hand, when the moth flies beyond the light source, the position for moth i is formulated as:
where and are the best and original position for moth i, respectively. is a scale factor and is acceleration factor.
2.2.3. Schematic Description of MS Algorithm
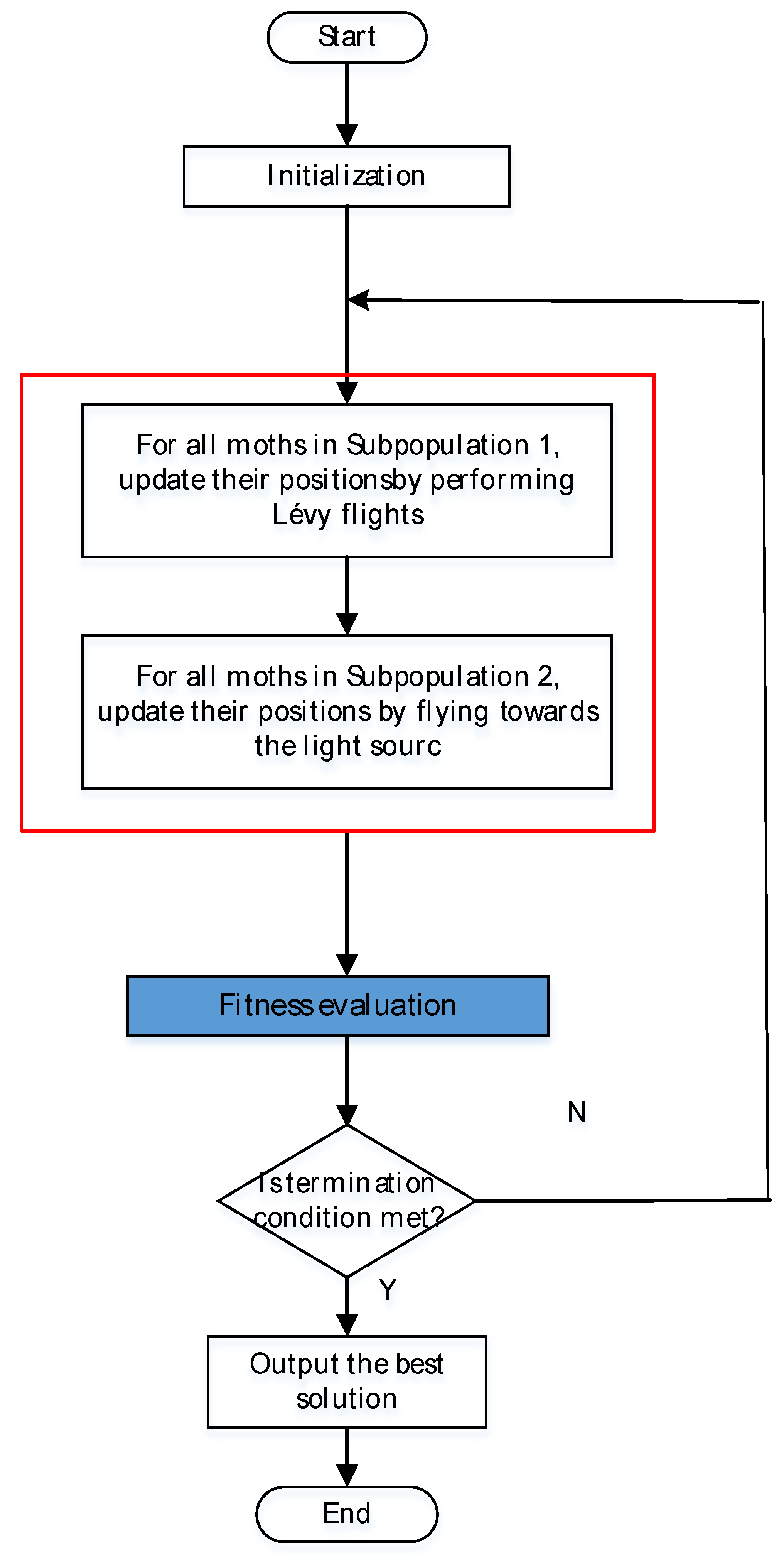
According to the analyses above, the basic steps of the MS are shown as follows Algorithm 1. Figure 4 designed the corresponding flowchart.
| Algorithm 1: Moth search algorithm |
| (1) Begin (2) Initialization. randomly initialize the population P of NP moths randomly, the generation number T = 1, the maximum generation MaxGen; (3) Evaluate each individual as per its position; (4) While T < MaxGen do (5) Sort all the moth individuals according to per their fitness; (6) for i = 1 to NP/2 (subgroup 1) do (7) Evaluate by performing Lévy flights; (8) end for i (9) for i = NP/2 + 1 to NP (subgroup 2) do (10) if rand > 0.5 then (11) Evaluate by Equation (4); (12) else (13) Evaluate by Equation (5); (14) end if (15) end for i (16) Evaluate the population according to the updated positions; (17) T = T + 1; (18) end while (19) Output the best solution. (20) End. |
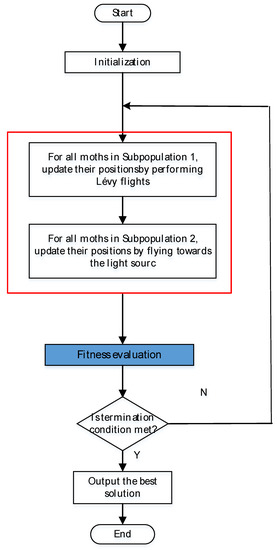
Figure 4.
Flowchart of the MS algorithm.
2.2.4. Analysis of Algorithm Complexity
The computational complexity of the MS algorithm is analyzed according to the steps for MS algorithm. The dimension is D and population size is NP. Sort the population in step (5) with time complexity O(NP). Execute by performing Lévy flights for subgroup 1 in steps (6)–(8)with time complexity O(NP/2 × D). In steps (9)–(15), execute by performing Lévy flights in Subpopulation 2 with time complexity O(NP/2 × D). In step (16), evaluate the population as per the newly updated positions with time complexity O (NP). In summary, the total time complexity of MS algorithm is O(T × NP × D). From the above analysis, the total time complexity of the MS algorithm is O(T × NP × D) after omitting the low-order terms, which are only related to T, NP, and D.
3. Different Variants of Moth Search
Several MS variants have been proposed to solve different optimization problems. The variants of MS are divided into three groups: improved MS, hybrid MS, and variants of MS, as shown in Table 2.

Table 2.
The classification proportions for different variants of MS.
3.1. Improved MS Algorithms
Feng et al. [94] proposed a binary MS algorithm for solving the 0–1 multidimensional knapsack problem (MKP). The self-learning flight straightly was introduced into the enhanced MS, which aims to make each individual learn. Through testing 89 different widely used benchmark instances, the results concluded that the proposed SLMS can enhance global search ability and population diversity for solving the MKP problem.
Feng et al. [95] established nine novel MS-based algorithms for DKP namely de MS1–MS9. In order to verify the influence of fly straightly operator and Lévy flights operator in MS algorithm, Lévy flights operator was replaced with nine types of new mutation operator based on the global harmony search. The experiment results showed that the proposed new MS-based approaches showed better comprehensive performance.
Mariyappan et al. [96] proposed a game model-combined improved MS optimization (GMMSO) to explore the design space and optimize the system space. The GMMSO comprised the game model notion in the input portion, was employed to explore the design space of the system structure effectively for various possible configurations, which ultimately find the best solution in a reasonable time. This experiment is implemented in the field Programma Ble gate array (FPGA) Xilinx Zynq and Virtex platforms, the simulation results revealed that the GMMSO obtained outstanding performance in delay measurement, data rate, and static power consumption compared with the traditional heuristic mixed integer linear programming methods.
3.2. Hybrid MS Algorithms
Any algorithm has its limitations. Although the moth search algorithm is a new optimization method, which can solve many problems in different fields, we noticed that MS is easy to fall into local optimization for solving complex optimization problems by analyzing basic moth search. The hybrid of MS algorithm and other metaheuristicsm algorithms, such as the mutation and explosion operators, are introduced into the MS. This approach can not only strong exploitation capability and preserve the advantages of fast convergence but also significantly enhance the exploration capability.
Starnberger et al. [97] presented a hybridized moth search algorithm with an artificial bee colony to tackle constrained optimization problems. According to the results obtained during experiments on a set of 13 classic constrained benchmarks, the hybridized MS algorithm has potential in dealing with constrained functions optimization.
Han et al. [98] designed a new hybrid moth search-fireworks algorithm (MSFWA) which introduced the explosion and mutation operators from the fireworks algorithm to solve constrained engineering optimization problems. The simulation results using 23 benchmark functions showed that the MSFWA not only preserved the strong exploitation capability but also enhanced the exploration capability.
Chaudhary et al. [99] studied an improved search technique to reduce the range of uniform random movement for MS algorithm, which enhanced overall efficiency and convergence capabilities. In the improved method, uniform and Lévy distributions, as well as Cauchy distribution, have been employed to apply different swarm algorithms, including MS algorithm. The experimental results indicated that improved method has a positive influence by employing different random distributions.
3.3. Variants of MS Algorithms
Srivani et al. [100] studied a dragonfly moth search (DMS) optimization to reveal the efficiency of the classification model using spark architecture. Features selection is accomplished by employing the DMS algorithm. The performance of the classification method is carried out in two different phases, offline and online. The parameters, such as sensitivity, accuracy and specificity metrics, are evaluated on the DMS method.
4. Engineering Optimization/Applications
MS optimization is a search optimization method inspired by things in nature. It has two properties, Lévy flight and phototaxis. The moths that have a smaller distance from the best one will fly around the best individual by Levy flights. Compared with traditional optimization methods, MS optimization has significant advantages in solving speed and accuracy, which can obtain the solution closest to the optimal solution in the shortest time. Therefore, it has been widely used in many engineering fields, as shown in Table 3.

Table 3.
The classification of engineering optimization/applications.
4.1. Continuous Optimization
4.1.1. Neural Networks
Fri et al. [101] integrated data envelopment analysis (DEA) and artificial neural network (ANN) in a single framework to evaluate the performance of operations for the container terminal. In the proposed framework, MS is employed to train the feed forward neural network (FNN) for determining the efficiency scores. The efficacy of the proposed framework was demonstrated on two container terminals of tangier and casablanca.
Reshma et al. [102] integrated chicken swarm optimization (CSO) and moth search algorithm to train optimally deep convolutional neural network (DCNN) classifier for pixel identification in image steganography. The inverse Tetrolet transform is applied to extract the secret message from an embedded image. The performance of image steganography is established based on the dataset. The results showed that the proposed method achieved excellent results for three correlation parameters, such as correlation coefficient, structural similarity index, and peak signal-to-noise ratio.
Shankar et al. [103] developed a new MS algorithm based on classification and detection model for diabetic retinopathy images (DNN-MSO). Different processes, such as preprocessing, segmentation, feature extraction, and classification, are involved with DNN-MSO. The analysis of the computational validated on diabetic retinopathy dataset indicated that the DNN-MSO has superior characteristics for curacy, sensitivity and specificity.
Srivastava et al. [104] developed a novel method, namely moth monarch optimization-based deep belief neural network (MMO-DBN) for deception detector. Two phases of feature extraction and classification were undergone in MMO-DBN classifier. Deep belief neural network (DBN) was used to subject these extracted features for classification. Monarch butterfly optimization (MBO) and MS algorithm were integrated to train. The MMO-DBN obtained the higher accuracy, which showed the superiority of the proposed MMO-DBN in deception detection.
Xu et al. [105] considered a novel optimized method containing five main types of noise reduction, tumor segmentation, morphology, feature extraction and gray-level co-occurrence matrix, and classification for early diagnosis of the brain tumor, in which an enhanced MS algorithm is utilized to optimize the classifier network. The simulation results are applied to three different datasets, revealed that the reposted method has good achievements toward the other methods.
Rekha et al. [106] considered novel method combining water wave optimization (WWO) and the MS, namely the water moth search algorithm (WMSA) for the detection of intrusion and malicious activities. The deep recurrent neural network (RNN) classifier effectively was detected by using the selected features. The research results showed that the proposed WMSA showed improved results with maximal specificity, accuracy, and sensitivity.
Sophia et al. [107] demonstrated an advanced multi-resolution algorithm (MRA) for optimally identifying and classifying pathologies, in which the vocal regions are acquired by using the genetic k-means algorithm. In addition, moth search-rider optimization-based deep convolutional neural networks (MRA-based DCNN) are used for pathology classification, and the local directional pattern (LDP) fed is used to generate pathology features. The hybrid optimization (MRA) is integrated by adopting the rider optimization algorithm (ROA) and moth search algorithm (MS). The experimentation is conducted by using the real databases regarding the performance metrics divulge, and the results indicated that the proposed module obtained the accuracy, specificity, and sensitivity.
4.1.2. Big Data Processing
Srivani et al. [108] illustrated a technique based on the integration of dragonfly algorithm (DA) and MS, namely DMS algorithm, which handled the concept drift effectively for the big data stream classification without any concept drift. The DMS algorithm aimed at feature selection and optimal tuning of the stacked auto-encoder (SAE). The effective feature selection-based SAE ensured the classification of the data and enhanced the classification accuracy.
4.2. Combinatorial Optimization
4.2.1. Knapsack
Feng et al. [109] combined twelve transfer functions divided three families (S-shape, V-shaped, and other shape) with MS to solve set-union knapsack problem (SUKP). Through the evaluation for three groups of fifteen SUKP instances, the simulation results showed that the transfer function demonstrated excellent performance and convergence rate.
Feng et al. [110] investigated an improved MS for solving SUKP, in which Lévy flight is replaced by enhancing the interaction operator (EIO). The mutation operator (MO) of differential evolution (DE) is employed into EIO to enhance the ability of information interaction among individuals. The analysis of the computational results indicated that the improved MS is superior to the other metaheuristic algorithm.
4.2.2. Power Systems
Singh et al. [111] designed MS for solving optimal distributed energy resources (DERs) integration problems of distribution systems. An optimal DERs integration problem with MS is formulated at annual energy loss minimization considering multiple distributed generations. The optimal DERs allocation is determined for minimization of annual energy loss at three different load levels. The simulation experimental results demonstrated that MSO has a better searching ability to determine optimal solutions for optimal DERs allocation problems.
Dhillon et al. [112] considered MS to address frequency control problem, which was caused by sudden source and load fluctuation in a three-area test power system. The experiments were simulated on MATLAB (R) and Simulink (R) platform. The effectiveness and accuracy of the proposed method were demonstrated in load frequency control problem.
Singh et al. [113] introduced MS for solving the distributed energy resources integration problems (DER). In order to verify the performance of the proposed method, two benchmark test distribution networks of 33 and 118 buses are implemented; the experimental results indicated that the proposed method optimally utilized the distribution system resources and generated higher deployment benefits at lesser DER penetration.
Srivastava et al. [114] introduced a new hybrid algorithm which termed lion algorithm with moth-based mutation (LA-MM) hybridized both lion algorithm and moth search. LA-MM is used to optimize the generating power of added generators with the bus system, which managed the congestion with minimized rescheduling cost. Experimentally, it has been proved that the LA-MM took the benefits of different optimization algorithms for fast convergence, which reduced grave damage caused by the congestion causes.
4.2.3. Static Drone Localization
Strumberger et al. [115] devised the MS algorithm to adjust static drone location problem. The MS algorithm is applied to establish monitoring all targets with the least possible number of drones. Instances with 30 uniformly distributed targets were tested, and the results indicated that MS algorithm full coverage of targets, which showed potential in dealing with this kind of problem.
4.2.4. Wireless Sensor Network
Strumberger et al. [116] developed hybridized moth search algorithm adapted to solve localization problem for wireless sensor networks. According to test on the same problem instances of node localization problem, the research results showed that hybridized MS algorithms are promising to deal with wireless sensor network localization.
Tandon et al. [117] modified bio-inspired cross-layer routing protocol (BiHCLR) combining MS and slap swarm optimization, to achieve effective and energy preserving routing in wireless sensor networks (WSN) for the Internet of Things (IoT). In BiHCLR, in order to enable energy preservation, the fuzzy logic approach was executed to select the cluster head for every grid. The experimentation was conducted in six indicators. The experimental results showed that the performance of the BiHCLR outperformed all other conventional techniques.
Boursianis et al. [118] applied MS to derive the final geometry of the proposed antenna for triple-band single-layer Rectenna for radio frequency (RF) energy harvesting (EH). The proposed rectifier is designed based on the Greinacher topology. The experiments showed that the proposed Rectenna can efficiency harvest RF energy from outdoor sources.
4.2.5. Scheduling
Elaziz et al. [119] devised an improved MS algorithm to minimize the makespan that required to schedule a number of tasks on different virtual machines for cloud task scheduling problem. In the proposed method, the DE is introduced into MS for improving the exploitation ability. The experiment was compared with other metaheuristic algorithms for synthetical and real trace data, respectively. It was concluded that the proposed algorithm outperformed other algorithms for cloud task scheduling problems.
Zade et al. [120] proposed a hybrid algorithm, namely hybrid multi-objective fuzzy hitchcock bird (MOHFHB) with moth search algorithm to solve multi-objective scheduling problems. Two concepts, crowding distance and ranking non-dominated solution, are added to determine the optimal Pareto front in MOHFHB. The experiments showed that the makespan and resource utilization have been improved.
Gokuldhev et al. [121] developed a hybridization of moth search algorithm (MSA) and flower pollination algorithm (FPA), namely local pollination moth search algorithm (LPMSA) for proper task scheduling in the cloud. FPA algorithm is used to improve the exploitation capacity of MSA. The experimentation is simulated under the platform of JAVA, and the results indicated that the LPMSA reduced the makespan and energy consumption during proper task scheduling.
4.2.6. Energy
Fathy et al. [122] developed an enhanced moth search algorithm (EMSA) to identify the optimal parameters of triple-junction (TJS) photovoltaic panel under different operating conditions. In order to avoid MS from being stuck in the local point, the disruptor operator is introduced into MS, which improved the diversity of the algorithm. The panel is tested under different solar radiation conditions. The results compared with other metaheuristic optimization showed that the EMSA extracted the optimal parameters of TJS based module operated at different operating conditions.
Boursianis et al. [123] introduced moth search algorithm to design a modified micros trip patch antenna of three varying slots. The proposed antenna with MS exhibited tuning operation in the long range and the cellular communications frequency. The experimental results indicated excellent performance for RF energy harvesting applications.
Huang et al. [124] devised the hybrid system based moth search algorithm, to analyze regarding the smoothness of the energy generation trend. In order to reduce the variance of electricity generation annually, MS is used for calculating the output of the PV voltage. The hybrid system is evaluated via three different hydrological periods, such as wet, drought, and normal. The research results showed that hydropower and PV are complementary, which can compensate for shortcomings and reduce energy in different conditions.
Sun et al. [125] presented a novel modified moth search algorithm namely converged moth search algorithm (CMSA) for minimizing the total of the squared deviations (TSD) between the experimental data and the output voltage in proton exchange membrane Fuel cells (PEMFCs). The CMSA method is applied to two different test cases, NedStack PS6 and BCS 500-WPS6. The simulation results revealed that the CMSA has the minimum values for both case studies toward the other compared algorithms, which showed that the CMSA has a good data agreement with the experimental data.
Shobana et al. [126] studied a dispatch strategy with fitness sorted moth search algorithm (FS-MSA) to enhance the economy of the micro grid system, which minimized the cost of system operation and environmental control for meeting system load requirements. The experimental results indicated that the FS-MSA model obtained excellent performance.
4.2.7. Water Quality Monitoring
Hussein et al. [127] proposed a new alternative machine learning method, namely MSA-RVFL, to predict the missing values of total algal count. The method combined the advantage of the random vector functional link network (RVFL). The performance results showed that the MSA-RVFL reduced the processing time and minimized the input variables, compared with GA-RVFL and PSO-RVFL methods whenever the number of inputs is large or small during water quality monitoring programs.
4.2.8. Computer Vision
Wagdarikar et al. [128] presented an improved chronological-moth search (Chronological-MS) for video watermarking based on interesting regions. Chronological concept is used in chronological-MS to select the optimal regions for the video watermarking. The chronological-MS is used to carry out for interesting regions identified. The simulation results showed that chronological-MS showed superior performance with correlation coefficient.
4.2.9. Information Security
Kumar et al. [129] proposed more secure data encryption combined moth search algorithm (MSA) with elliptic curve cryptography (ECC), in which optimal value of the elliptic curve was selected. Multi-level security with less computational power was provided by combining DNA encoding with the ECC encryption algorithm. The experimental is conducted based on safety, decryption time, and encryption time. The results indicated that the proposed two-layer security with minimum key size and less storage space, which protected different attacks effectively.
Alotaibi et al. [130] designed an effective attack detection method based on moth elephant herding optimization (MEHO), which is developed by integrating the MS algorithm and the elephant herding optimization (EHO), to resolve the vulnerabilities in the computing devices. The data is cleaned via removing the noise and artifacts at the stage of the pre-processing. Then, the auto encoder classifier was used to perform the attack detection. In order to verify the performance of the method, the metrics, like accuracy, false acceptance rate (FAR) and detection rate is evaluated. The results indicated that the MEHO showed excellent performance.
Varghese et al. [131] deployed the hybridized concepts combining monarch butterfly optimization with moth search algorithm to optimally tune the weight of deep convolutional neural network (DCNN). A new intrusion detection system (IDS) model based on machine learning (ML) technology in cloud networks is established. The results showed that the method provided better outcomes compared to exciting methods.
4.2.10. Text Mining
Venkata Sailaja et al. [132] used MS algorithm to select optimal weights in support vector neural network (SVNN). The proposed classifier, namely MS-SVNN, performed incremental learning using SVNN, and the weights were bounded in a limit using rough set theory. 20 News group dataset and the Reuters dataset are used for simulation experimentation. Moreover, the text categorization is done by using the rough set MS-SVNN classifier and the optimal weights based on the MS. The analysis of the computational results indicated that the online text categorization scheme-based MS-SVNN can identify the unique words from the dataset and obtain the features like semantic word-based features from the keyword set.
Yarlagadda et al. [133] demonstrated Modsup-based frequent item set and rider optimization-based MS (Rn-MSA) for clustering the documents. The Rn-MSA is designed for document clustering by combining the MS and rider optimization algorithm. The performance of the proposed Rn-MSA is evaluated in precision, recall, F-Measure, and accuracy. The study results showed that the developed document clustering method indicated its superiority.
4.2.11. Information Metasearch
Kaur et al. [134] considered MS approach along with two distance measure methods for the rank aggregation (RA) module, which merged the output derived from distinct search engines. In order to select the best optimized document, the novel method assigns a relevance rank to similar documents from different search engines. The experimental results indicated that the approach outperformed than another conventional algorithm.
4.2.12. Path Optimization
More et al. [135] investigated a novel algorithm, namely moth whale optimization algorithm (MWOA), to determine the optimal multipath for the transmission of the videos from one vehicle to other in the vehicular ad hoc network (VANET). The MWOA is designed for the integration of whale optimization algorithm (WOA) and MS algorithm. The VANET is simulated based optimal selection of the multipath under geographic routing scheme. The simulation results revealed that MWOA showed the superiority-based packet delivery ratio (PDR), throughput, and packet end-to-end delay for effective video transmission.
4.3. Constrained Optimization
4.3.1. Linear and Nonlinear Constrained Optimization
Razmjooy et al. [136] proposed an optimal design for control of the synchronous machine, which is a 4th order linear Philips-Heffron synchronous machine. A controller is utilized for stability by minimizing a fitness function, which removed the unstable Eigen-values to the left-hand side of the imaginary axis. The considered parameters of the controller are optimized by moth search algorithm. The simulation experimental results demonstrated that the proposed method gave better efficiency for comparing particle swarm optimization.
4.3.2. Bridges Design
Carrasco et al. [137] applied moth search algorithm to optimize the process of calculating the hanger magnitudes and the order for obtaining one or several satisfactory solutions. The experimental results are obtained for an arch bridge and three hangers. The efficiency and effectiveness are compared with the black hole algorithm.
4.3.3. Industry Design
Ong et al. [138] utilized a soft computing technique for optimizing the performance of the electrical discharge machining (EDM). The MS was introduced to determine the optimal machining parameters which maximized the MRR and minimized the EWR. The EDM experiment was conducted, and the effectiveness was evaluated in material removal rate (MRR) and electrode wear rate (EWR). The experimental results indicated that the optimization capability of MS was validated based on the obtained optimal parameters.
4.4. Multi-Objective Optimization
Thokar et al. [139] proposed multi-objective nested optimization framework based involved two-layered structure for the simultaneous optimal allocation of multiple solar photovoltaics (SPVs) and battery energy storage system (BESS) in the distribution networks. Moth search is combined with a new weighted sum approach in the proposed method. The experimental results indicated that the proposed model ensured the high penetration of SPVs and the optimal utilization of BESSs, which enhanced energy efficiency and absorbed the excess renewable power generation during light load hours.
5. Conclusions and Future Directions
This paper systematically summarized moth search. We searched through Google scholar with the keyword “moth search”. We selected 56 representative papers from 1 January 2018 to 23 August 2022 from the various papers. We found that the development trend and space of MS is promising from the summary analysis of these papers. A large number of researchers improved the MS algorithm and successfully applied them to various optimization fields. However, some problems still are worth study.
- (1)
- Up to now, there is still not sufficient explanation for theoretical analysis about MS. Therefore, strengthening the theoretical analysis study of MS will be an important research direction in the future.
- (2)
- Constrained optimization and multi-objective optimization have always been important research problems. Therefore, MS is worth further study to solve the problems in these fields.
- (3)
- Lowing proportion of engineering applications is undoubtedly a shortcoming of MS, which will be an important challenge.
- (4)
- MS is used to solve continuous and discrete optimization problems should be considered in future research [140,141].
- (5)
- MS has a lower proportion combining with machine learning methods than the others [142,143].
Author Contributions
Conceptualization, J.L.; research literature, H.L.; literature search, G.-G.W. and Q.A.; writing—original draft preparation, J.L.; writing—review and editing, H.L., Y.-H.Y. and Q.D.; funding acquisition, G.-G.W. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Project of Wenzhou Key Laboratory Foundation under Grant 2021HZSY0071.
Acknowledgments
The authors would like to thank the anonymous reviewers and the editor for their careful reviews and constructive suggestions to help us improve the quality of this paper.
Conflicts of Interest
The authors declare that they have no conflict of interest.
References
- Cui, Z.; Xue, F.; Cai, X.; Cao, Y.; Wang, G.-G.; Chen, J. Detection of malicious code variants based on deep learning. IEEE Trans. Ind. Inform. 2018, 14, 3187–3196. [Google Scholar] [CrossRef]
- Li, X.; Cao, S.; Gao, L.; Wen, L. A threshold-control generative adversarial network method for intelligent fault diagnosis. Complex Syst. Model. Simul. 2021, 1, 55–64. [Google Scholar] [CrossRef]
- Wang, G.-G.; Tan, Y. Improving metaheuristic algorithms with information feedback models. IEEE Trans. Cybern. 2019, 49, 542–555. [Google Scholar] [CrossRef]
- Zhao, F.; Di, S.; Cao, J.; Tang, J.; Jonrinaldi. A novel cooperative multi-stage hyper-heuristic for combination optimization problems. Complex Syst. Model. Simul. 2021, 1, 91–108. [Google Scholar] [CrossRef]
- Li, J.; Lei, H.; Alavi, A.H.; Wang, G.-G. Elephant herding optimization: Variants, hybrids, and applications. Mathematics 2020, 8, 1415. [Google Scholar] [CrossRef]
- Wang, Y.; Cai, S.; Chen, J.; Yin, M. Sccwalk: An efficient local search algorithm and its improvements for maximum weight clique problem. Artif. Intell. 2020, 280, 103230. [Google Scholar] [CrossRef]
- Minocha, S.; Singh, B. A novel equilibrium optimizer based on levy flight and iterative cosine operator for engineering optimization problems. Expert Syst. 2022, 39, e12843. [Google Scholar] [CrossRef]
- Huang, Z.; Huang, L.; Li, Q.; Zhang, T.; Sang, N. Framelet regularization for uneven intensity correction of color images with illumination and reflectance estimation. Neurocomputing 2018, 314, 154–168. [Google Scholar] [CrossRef]
- Huang, Z.; Zhang, Y.; Li, Q.; Zhang, T.; Sang, N. Spatially adaptive denoising for X-ray cardiovascular angiogram images. Biomed. Signal Process. Control 2018, 40, 131–139. [Google Scholar] [CrossRef]
- Huang, Z.; Chen, L.; Zhang, Y.; Yu, Z.; Fang, H.; Zhang, T. Robust contact-point detection from pantograph-catenary infrared images by employing horizontal-vertical enhancement operator. Infrared Phys. Technol. 2019, 101, 146–155. [Google Scholar] [CrossRef]
- Huang, Z.; Zhang, Y.; Li, Q.; Li, Z.; Zhang, T.; Sang, N.; Xiong, S. Unidirectional variation and deep cnn denoiser priors for simultaneously destriping and denoising optical remote sensing images. Int. J. Remote Sens. 2019, 40, 5737–5748. [Google Scholar] [CrossRef]
- Huang, Z.; Zhang, Y.; Li, Q.; Li, X.; Zhang, T.; Sang, N.; Hong, H. Joint analysis and weighted synthesis sparsity priors for simultaneous denoising and destriping optical remote sensing images. IEEE Trans. Geosci. Remote Sens. 2020, 58, 6958–6982. [Google Scholar] [CrossRef]
- Gao, D.; Wang, G.-G.; Pedrycz, W. Solving fuzzy job-shop scheduling problem using de algorithm improved by a selection mechanism. IEEE Trans. Fuzzy Syst. 2020, 28, 3265–3275. [Google Scholar] [CrossRef]
- Wang, G.-G.; Gao, D.; Pedrycz, W. Solving multi-objective fuzzy job-shop scheduling problem by a hybrid adaptive differential evolution algorithm. IEEE Trans. Ind. Inform. 2022, 18, 8519–8528. [Google Scholar] [CrossRef]
- Zhang, W.; Hou, W.; Li, C.; Yang, W.; Gen, M. Multidirection update-based multiobjective particle swarm optimization for mixed no-idle flow-shop scheduling problem. Complex Syst. Model. Simul. 2021, 1, 176–197. [Google Scholar] [CrossRef]
- Zhang, Y.; Song, X.; Gong, D. A return-cost-based binary firefly algorithm for feature selection. Inf. Sci. 2017, 418, 561–574. [Google Scholar] [CrossRef]
- Jiang, L.; Huang, H.; Ding, Z. Path planning for intelligent robots based on deep q-learning with experience replay and heuristic knowledge. IEEE/CAA J. Autom. Sin. 2020, 7, 1179–1189. [Google Scholar] [CrossRef]
- Juan, L.; Yuan-Hua, Y.; Hong, L.; Gai-Ge, W. Solving logistics distribution center location with improved cuckoo search algorithm. Int. J. Comput. Intell. Syst. 2020, 14, 676–692. [Google Scholar]
- An, Q.; Chen, X.; Zhang, J.; Shi, R.; Yang, Y.; Huang, W. A robust fire detection model via convolution neural networks for intelligent robot vision sensing. Sensors 2022, 22, 2929. [Google Scholar] [CrossRef]
- Bhandari, D.; Paul, S.; Narayan, A. Deep neural networks for multimodal data fusion and affect recognition. Int. J. Artif. Intell. Soft Comput. 2020, 7, 130–145. [Google Scholar] [CrossRef]
- Lin, H.; Zhao, B.; Liu, D.; Alippi, C. Data-based fault tolerant control for affine nonlinear systems through particle swarm optimized neural networks. IEEE/CAA J. Autom. Sin. 2020, 7, 954–964. [Google Scholar] [CrossRef]
- Yu, Y.; Lei, Z.; Wang, Y.; Zhang, T.; Peng, C.; Gao, S. Improving dendritic neuron model with dynamic scale-free network-based differential evolution. IEEE/CAA J. Autom. Sin. 2022, 9, 99–110. [Google Scholar] [CrossRef]
- Wang, G.-G.; Cai, X.; Cui, Z.; Min, G.; Chen, J. High performance computing for cyber physical social systems by using evolutionary multi-objective optimization algorithm. IEEE Trans. Emerg. Top. Comput. 2020, 8, 20–30. [Google Scholar] [CrossRef]
- Cai, X.; Geng, S.; Zhang, J.; Wu, D.; Cui, Z.; Zhang, W.; Chen, J. A sharding scheme-based many-objective optimization algorithm for enhancing security in blockchain-enabled industrial internet of things. IEEE Trans. Ind. Inform. 2021, 17, 7650–7658. [Google Scholar] [CrossRef]
- Li, G.; Wang,, G.-G. A novel adaptive weight algorithm based on decomposition and two-part update strategy for many-objective optimization. Inf. Sci. 2022, 615, 323–347. [Google Scholar] [CrossRef]
- Cui, Z.; Zhang, Z.; Hu, Z.; Geng, S.; Chen, J. A many-objective optimization based intelligent high performance data processing model for cyber-physical-social systems. IEEE Trans. Netw. Sci. Eng. 2021, 9, 3825–3834. [Google Scholar] [CrossRef]
- Cui, Z.; Zhao, P.; Hu, Z.; Cai, X.; Zhang, W.; Chen, J. An improved matrix factorization based model for many-objective optimization recommendation. Inf. Sci. 2021, 579, 1–14. [Google Scholar] [CrossRef]
- Rizk-Allah, R.M.; El-Sehiemy, R.A.; Deb, S.; Wang, G.-G. A novel fruit fly framework for multi-objective shape design of tubular linear synchronous motor. J. Supercomput. 2017, 73, 1235–1256. [Google Scholar] [CrossRef]
- Liu, G.; Zou, J. Level set evolution with sparsity constraint for object extraction. IET Image Process. 2018, 12, 1413–1422. [Google Scholar] [CrossRef]
- Cui, Z.; Sun, B.; Wang, G.-G.; Xue, Y.; Chen, J. A novel oriented cuckoo search algorithm to improve dv-hop performance for cyber-physical systems. J. Parallel Distrib. Comput. 2017, 103, 42–52. [Google Scholar] [CrossRef]
- Alweshah, M.; Abdullah, S. Hybridizing firefly algorithms with a probabilistic neural network for solving classification problems. Appl. Soft Comput. 2015, 35, 513–524. [Google Scholar] [CrossRef]
- Bousmaha, R.; Hamou, R.M.; Amine, A. Automatic selection of hidden neurons and weights in neural networks for data classification using hybrid particle swarm optimization, multi-verse optimization based on Lévy flight. Evol. Intell. 2021, 15, 1695–1714. [Google Scholar] [CrossRef]
- Prabu, M.; Chelliah, B.J. Mango leaf disease identification and classification using a cnn architecture optimized by crossover-based levy flight distribution algorithm. Neural Comput. Appl. 2022, 34, 7311–7324. [Google Scholar] [CrossRef]
- Parashar, S.; Senthilnath, J.; Yang, X.-S. A novel bat algorithm fuzzy classifier approach for classification problems. Int. J. Artif. Intell. Soft Comput. 2017, 6, 108–128. [Google Scholar] [CrossRef]
- Arora, J.; Tushir, M. A new kernel-based possibilistic intuitionistic fuzzy c-means clustering. Int. J. Artif. Intell. Soft Comput. 2018, 6, 306–325. [Google Scholar] [CrossRef]
- Banerjee, R.; De, S.; Dey, S. Wtaof-ilpb based feature learning and lfssoa-rbfnn based classification for facial micro-expression recognition. Wirel. Pers. Commun. 2021. Available online: https://link.springer.com/article/10.1007/s11277-021-08794-5 (accessed on 24 September 2022). [CrossRef]
- Tsipianitis, A.; Tsompanakis, Y. Improved cuckoo search algorithmic variants for constrained nonlinear optimization. Adv. Eng. Softw. 2020, 149, 102865. [Google Scholar] [CrossRef]
- Hu, L.; Yang, S.; Luo, X.; Yuan, H.; Zhou, M. A distributed framework for large-scale protein-protein interaction data analysis and prediction using mapreduce. IEEE/CAA J. Autom. Sin. 2021, 9, 160–172. [Google Scholar] [CrossRef]
- Wang, Y.; Gao, S.; Zhou, M.; Yu, Y. A multi-layered gravitational search algorithm for function optimization and real-world problems. IEEE/CAA J. Autom. Sin. 2021, 8, 94–109. [Google Scholar] [CrossRef]
- Hu, Z.; Wang, J.; Zhang, C.; Luo, Z.; Luo, X.; Xiao, L.; Shi, J. Uncertainty modeling for multicenter autism spectrum disorder classification using takagi–sugeno–kang fuzzy systems. IEEE Trans. Cogn. Dev. Syst. 2022, 14, 730–739. [Google Scholar] [CrossRef]
- Liu, X.-J.; He, Y.-C. Estimation of distribution algorithm based on lévy flight for solving the set-union knapsack problem. IEEE Access 2019, 7, 132217–132227. [Google Scholar] [CrossRef]
- Goldberg, D.E. Genetic Algorithms in Search, Optimization and Machine Learning; Addison-Wesley: New York, NY, USA, 1998. [Google Scholar]
- Aghaee, R.; Momeni, M.; Moallem, P. Semisupervised band selection from hyperspectral images using levy flight-based genetic algorithm. IEEE Geosci. Remote Sens. Lett. 2022, 19, 6006805. [Google Scholar] [CrossRef]
- Storn, R.; Price, K. Differential evolution-a simple and efficient heuristic for global optimization over continuous spaces. J. Glob. Optim. 1997, 11, 341–359. [Google Scholar] [CrossRef]
- Xu, Z.; Unveren, A.; Acan, A. Probability collectives hybridised with differential evolution for global optimisation. Int. J. Bio-Inspired Comput. 2016, 8, 133–153. [Google Scholar] [CrossRef]
- Wang, G.; Guo, L.; Duan, H.; Liu, L.; Wang, H.; Shao, M. Path planning for uninhabited combat aerial vehicle using hybrid meta-heuristic de/bbo algorithm. Adv. Sci. Eng. Med. 2012, 4, 550–564. [Google Scholar] [CrossRef]
- Feng, X.; Muramatsu, H.; Katsura, S. Differential evolutionary algorithm with local search for the adaptive periodic-disturbance observer adjustment. IEEE Trans. Ind. Electron. 2021, 68, 12504–12512. [Google Scholar] [CrossRef]
- Zhong, X.; Cheng, P. An elite-guided hierarchical differential evolution algorithm. Appl. Intell. 2021, 51, 4962–4983. [Google Scholar] [CrossRef]
- Kennedy, J.; Eberhart, R. Particle swarm optimization. In Proceedings of the IEEE International Conference on Neural Networks, Perth, Australia, 27 November–1 December 1995; IEEE: Perth, Australia; pp. 1942–1948. [Google Scholar]
- Wang, G.-G.; Gandomi, A.H.; Yang, X.-S.; Alavi, A.H. A novel improved accelerated particle swarm optimization algorithm for global numerical optimization. Eng. Comput. 2014, 31, 1198–1220. [Google Scholar] [CrossRef]
- Sun, J.; Feng, B.; Xu, W. Particle swarm optimization with particles having quantum behavior. In Proceedings of the Congress on Evolutionary Computation (CEC 2004), Portland, OR, USA, 19–23 June 2004; IEEE: Portland, OR, USA; pp. 325–331. [Google Scholar]
- Adewumi, A.O.; Arasomwan, M.A. On the performance of particle swarm optimisation with(out) some control parameters for global optimisation. Int. J. Bio-Inspired Comput. 2016, 8, 14–32. [Google Scholar] [CrossRef]
- Lu, X.-L.; He, G. Qpso algorithm based on Lévy flight and its application in fuzzy portfolio. Appl. Soft Comput. 2021, 99, 106894. [Google Scholar] [CrossRef]
- Bejarbaneh, E.Y.; Masoumnezhad, M.; Armaghani, D.J.; Binh Thai, P. Design of robust control based on linear matrix inequality and a novel hybrid pso search technique for autonomous underwater vehicle. Appl. Ocean. Res. 2020, 101, 102231. [Google Scholar] [CrossRef]
- Wang, G.-G.; Zhao, X.; Deb, S. A novel monarch butterfly optimization with greedy strategy and self-adaptive crossover operator. In Proceedings of the 2015 Second International Conference on Soft Computing & Machine Intelligence (ISCMI 2015), Hong Kong, China, 23–24 November 2015; IEEE: Hong Kong, China; pp. 45–50. [Google Scholar]
- Ates, A.; Akpamukcu, M. Modified monarch butterfly optimization with distribution functions and its application for 3 dof hover flight system. Neural Comput. Appl. 2021, 34, 3697–3722. [Google Scholar] [CrossRef]
- Kim, M.; Chae, J. Monarch butterfly optimization for facility layout design based on a single loop material handling path. Mathematics 2019, 7, 154. [Google Scholar] [CrossRef]
- Wang, G.-G.; Deb, S.; Cui, Z. Monarch butterfly optimization. Neural Comput. Appl. 2019, 31, 1995–2014. [Google Scholar] [CrossRef]
- Yi, J.-H.; Lu, M.; Zhao, X.-J. Quantum inspired monarch butterfly optimization for ucav path planning navigation problem. Int. J. Bio-Inspired Comput. 2020, 15, 75–89. [Google Scholar] [CrossRef]
- Wang, G.-G.; Deb, S.; Coelho, L.d.S. Elephant herding optimization. In Proceedings of the 2015 3rd International Symposium on Computational and Business Intelligence (ISCBI 2015), Bali, Indonesia, 7–9 December 2015; IEEE: Bali, Indonesia; pp. 1–5. [Google Scholar]
- Yonar, A.; Yapici Pehlivan, N. Artificial bee colony with levy flights for parameter estimation of 3-p weibull distribution. Iran. J. Sci. Technol. Trans. A Sci. 2020, 44, 851–864. [Google Scholar] [CrossRef]
- Yang, T.; Liu, X. Prediction of thermophysical properties of chlorine eutectic salts via artificial neural network combined with polar bear optimization. J. Energy Storage 2022, 55, 105658. [Google Scholar]
- Dorigo, M.; Stutzle, T. Ant Colony Optimization; MIT Press: Cambridge, UK, 2004. [Google Scholar]
- Geem, Z.W.; Kim, J.H.; Loganathan, G.V. A new heuristic optimization algorithm: Harmony search. Simulation 2001, 76, 60–68. [Google Scholar] [CrossRef]
- Wang, G.; Guo, L.; Duan, H.; Wang, H.; Liu, L.; Shao, M. Hybridizing harmony search with biogeography based optimization for global numerical optimization. J. Comput. Theor. Nanosci. 2013, 10, 2318–2328. [Google Scholar] [CrossRef]
- Niknam, T.; Fard, A.K. Optimal energy management of smart renewable micro-grids in the reconfigurable systems using adaptive harmony search algorithm. Int. J. Bio-Inspired Comput. 2016, 8, 184–194. [Google Scholar] [CrossRef]
- Rezoug, A.; Boughaci, D. A self-adaptive harmony search combined with a stochastic local search for the 0–1 multidimensional knapsack problem. Int. J. Bio-Inspired Comput. 2016, 8, 234–239. [Google Scholar] [CrossRef]
- Gandomi, A.H.; Alavi, A.H. Krill herd: A new bio-inspired optimization algorithm. Commun. Nonlinear Sci. Numer. Simul. 2012, 17, 4831–4845. [Google Scholar] [CrossRef]
- Li, Z.-Y.; Yi, J.-H.; Wang, G.-G. A new swarm intelligence approach for clustering based on krill herd with elitism strategy. Algorithms 2015, 8, 951–964. [Google Scholar] [CrossRef]
- Wang, G.-G.; Gandomi, A.H.; Alavi, A.H.; Deb, S. A multi-stage krill herd algorithm for global numerical optimization. Int. J. Artif. Intell. Tools 2016, 25, 1550030. [Google Scholar] [CrossRef]
- Wang, G.-G.; Gandomi, A.H.; Alavi, A.H.; Gong, D. A comprehensive review of krill herd algorithm: Variants, hybrids and applications. Artif. Intell. Rev. 2019, 51, 119–148. [Google Scholar] [CrossRef]
- Wang, G.-G.; Guo, L.; Gandomi, A.H.; Hao, G.-S.; Wang, H. Chaotic krill herd algorithm. Inf. Sci. 2014, 274, 17–34. [Google Scholar] [CrossRef]
- Li, J.; Li, Y.; Tian, S.; Zou, J. Dynamic cuckoo search algorithm based on taguchi opposition-based search. Int. J. Bio-Inspired Comput. 2019, 13, 59–69. [Google Scholar] [CrossRef]
- Li, J.; Xiao, D.; Lei, H.; Zhang, T.; Tian, T. Using cuckoo search algorithm with q-learning and genetic operation to solve the problem of logistics distribution center location. Mathematics 2020, 8, 149. [Google Scholar] [CrossRef]
- Li, J.; Xiao, D.; Zhang, T.; Liu, C.; Li, Y.; Wang, G. Multi-swarm cuckoo search algorithm with Q-learning model. Comput. J. 2021, 64, 108–131. [Google Scholar] [CrossRef]
- Wang, G.-G.; Gandomi, A.H.; Yang, X.-S.; Alavi, A.H. A new hybrid method based on krill herd and cuckoo search for global optimization tasks. Int. J. Bio-Inspired Comput. 2016, 8, 286–299. [Google Scholar] [CrossRef]
- Wang, G.-G.; Deb, S.; Gandomi, A.H.; Zhang, Z.; Alavi, A.H. Chaotic cuckoo search. Soft Comput. 2016, 20, 3349–3362. [Google Scholar] [CrossRef]
- Wang, G.-G.; Gandomi, A.H.; Zhao, X.; Chu, H.E. Hybridizing harmony search algorithm with cuckoo search for global numerical optimization. Soft Comput. 2016, 20, 273–285. [Google Scholar] [CrossRef]
- Li, J.; Li, Y.; Tian, S.; Xia, J. An improved cuckoo search algorithm with self-adaptive knowledge learning. Neural Comput. Appl. 2019, 32, 11967–11997. [Google Scholar] [CrossRef]
- Wang, G.-G.; Deb, S.; Coelho, L.D.S. Earthworm optimization algorithm: A bio-inspired metaheuristic algorithm for global optimization problems. Int. J. Bio-Inspired Comput. 2018, 12, 1–22. [Google Scholar] [CrossRef]
- Santucci, V.; Baioletti, M.; Di Bari, G. An improved memetic algebraic differential evolution for solving the multidimensional two-way number partitioning problem. Expert Syst. Appl. 2021, 178, 114938. [Google Scholar] [CrossRef]
- Tang, D.; Liu, Z.; Yang, J.; Zhao, J. Memetic frog leaping algorithm for global optimization. Soft Comput. 2018, 23, 11077–11105. [Google Scholar] [CrossRef]
- Peng, L.; Zhang, D. An adaptive levy flight firefly algorithm for multilevel image thresholding based on renyi entropy. J. Supercomput. 2022, 78, 6875–6896. [Google Scholar] [CrossRef]
- Wu, J.; Wang, Y.-G.; Burrage, K.; Tian, Y.-C.; Lawson, B.; Ding, Z. An improved firefly algorithm for global continuous optimization problems. Expert Syst. Appl. 2020, 149, 113340. [Google Scholar] [CrossRef]
- Abu Khurmaa, R.; Aljarah, I.; Sharieh, A. An intelligent feature selection approach based on moth flame optimization for medical diagnosis. Neural Comput. Appl. 2021, 33, 7165–7204. [Google Scholar] [CrossRef]
- Heidari, A.A.; Pahlavani, P. An efficient modified grey wolf optimizer with lévy flight for optimization tasks. Appl. Soft Comput. 2017, 60, 115–134. [Google Scholar] [CrossRef]
- Liu, L.; Wang, A.; Sun, G.; Zheng, T.; Yu, C. An improved biogeography-based optimization approach for beam pattern optimizations of linear and circular antenna arrays. Int. J. Numer. Model. Electron. Netw. Devices Fields 2021, 34, e2910. [Google Scholar] [CrossRef]
- Shirani, M.R.; Safi-Esfahani, F. Bmda: Applying biogeography-based optimization algorithm and mexican hat wavelet to improve dragonfly algorithm. Soft Comput. 2020, 24, 15979–16004. [Google Scholar] [CrossRef]
- Chen, Y.; Zhang, X.; Karimian, H.; Xiao, G.; Huang, J. A novel framework for prediction of dam deformation based on extreme learning machine and levy flight bat algorithm. J. Hydroinform. 2021, 23, 935–949. [Google Scholar] [CrossRef]
- Chen, X.; Cheng, F.; Liu, C.; Cheng, L.; Mao, Y. An improved wolf pack algorithm for optimization problems: Design and evaluation. PLoS ONE 2021, 16, e0254239. [Google Scholar] [CrossRef] [PubMed]
- Wang, G.-G. Moth search algorithm: A bio-inspired metaheuristic algorithm for global optimization problems. Memetic Comput. 2018, 10, 151–164. [Google Scholar] [CrossRef]
- Li, J.; An, Q.; Lei, H.; Deng, Q.; Wang, G.-G. Survey of lévy flight-based metaheuristics for optimization. Mathematics 2022, 10, 2785. [Google Scholar] [CrossRef]
- Zvereva, E.L.; Kozlov, M.V. Variations in search behavior of codling moth, Cydia pomonella (Tortricidae, Papilionida), males observed in the field. Zool. Zhurnal 1992, 71, 15–23. [Google Scholar]
- Feng, Y.; Wang, G.-G. Binary moth search algorithm for discounted {0–1} knapsack problem. IEEE Access 2018, 6, 10708–10719. [Google Scholar] [CrossRef]
- Feng, Y.; Wang, G.-G. A binary moth search algorithm based on self-learning for the multidimensional knapsack problems. Future Gener. Comput. Syst. 2022, 126, 48–64. [Google Scholar] [CrossRef]
- Mariyappan, I.; Veluchamy, M. Gmmso: Game model-combined improved moth search approach for reconfigurable asymmetric multi-processor system-on-chip architecture. Eng. Optim. 2022. [Google Scholar] [CrossRef]
- Starnberger, I.; Tuba, E.; Bacanin, N.; Beko, M.; Tuba, M. Hybridized moth search algorithm for constrained optimization problems. In Proceedings of the 2018 International Young Engineers Forum (YEF-ECE), Costa da Caparica, Portugal, 4 May 2018; IEEE: Costa da Caparica, Portugal; pp. 1–5. [Google Scholar]
- Han, X.; Yue, L.; Dong, Y.; Xu, Q.; Xie, G.; Xu, X. Efficient hybrid algorithm based on moth search and fireworks algorithm for solving numerical and constrained engineering optimization problems. J. Supercomput. 2020, 76, 9404–9429. [Google Scholar] [CrossRef]
- Chaudhary, R.; Banati, H. Improving convergence in swarm algorithms by controlling range of random movement. Nat. Comput. 2021, 20, 513–560. [Google Scholar] [CrossRef]
- Srivani, B.; Sandhya, N.; Rani, B.P. A case study for performance analysis of big data stream classification using spark architecture. Int. J. Syst. Assur. Eng. Manag. 2022. [Google Scholar] [CrossRef]
- Fri, M.; Douaioui, K.; Lamii, N.; Mabrouki, C.; Semma, E.A. A hybrid framework for evaluating the performance of port container terminal operations: Moroccan case study. Pomor. Sci. J. Marit. Res. 2020, 34, 261–269. [Google Scholar] [CrossRef]
- Reshma, V.K.; Kumar, V.R.S.; Shahi, D.; Shyjith, M.B. Chicken-moth search-based deep convolutional neural network for image steganography. Scalable Comput. Pract. Exp. 2020, 21, 217–232. [Google Scholar]
- Shankar, K.; Perumal, E.; Vidhyavathi, R.M. Deep neural network with moth search algorithm based detection and classification of diabetic retinopathy images. SN Appl. Sci. 2020, 2, 748. [Google Scholar] [CrossRef]
- Srivastava, N.; Dubey, S. Moth monarch optimization-based deep belief network in deception detection system. Sadhana-Acad. Proc. Eng. Sci. 2020, 45, 166. [Google Scholar] [CrossRef]
- Xu, L.; Gao, Q.; Yousefi, N. Brain tumor diagnosis based on discrete wavelet transform, gray-level co-occurrence matrix, and optimal deep belief network. Simul. Trans. Soc. Model. Simul. Int. 2020, 96, 867–879. [Google Scholar] [CrossRef]
- Rekha, P.M.; Shahapure, N.H.; Punitha, M.; Sudha, P.R. Water moth search algorithm-based deep training for intrusion detection in iot. J. Web Eng. 2021, 20, 1781–1812. [Google Scholar]
- Sophia, N.A.; Jiji, G.W. Classification of acute pathology for vocal cord using advanced multi-resolution algorithm. Int. J. Pattern Recognit. Artif. Intell. 2022, 36, 2292002. [Google Scholar] [CrossRef]
- Srivani, B.; Sandhya, N.; Padmaja Rani, B. An effective model for handling the big data streams based on the optimization-enabled spark framework. In Intelligent System Design; Springer: Singapore, 2021; pp. 673–696. [Google Scholar]
- Feng, Y.; An, H.; Gao, X. The importance of transfer function in solving set-union knapsack problem based on discrete moth search algorithm. Mathematics 2019, 7, 17. [Google Scholar] [CrossRef]
- Feng, Y.; Yi, J.-H.; Wang, G.-G. Enhanced moth search algorithm for the set-union knapsack problems. IEEE Access 2019, 7, 173774–173785. [Google Scholar] [CrossRef]
- Singh, P.; Bishnoi, S.K.; Meena, N.K. Moth search for optimal integration of ders for annual energy loss minimization in distribution systems. In Proceedings of the 8th IEEE India International Conference on Power Electronics (IICPE), Jaipur, India, 13–15 December 2018. [Google Scholar]
- Dhillon, S.S.; Lather, J.S.; Wang, G.-G.; Kaur, P.; Kumar, L. Monarch butterfly optimized control with robustness analysis for grid tied centralized and distributed power generations. J. Ambient. Intell. Humaniz. Comput. 2020, 13, 3595–3608. [Google Scholar] [CrossRef]
- Singh, P.; Bishnoi, S.K.; Meena, N.K. Moth search for optimal ders integration in conjunction to oltc tap operations in distribution systems. IEEE Syst. J. 2020, 14, 880–888. [Google Scholar] [CrossRef]
- Srivastava, J.; Yadav, N.K. Rescheduling-based congestion management by metaheuristic algorithm: Hybridizing lion and moth search models. Int. J. Numer. Model. Electron. Netw. Devices Fields 2021, 35, e2952. [Google Scholar] [CrossRef]
- Strumberger, I.; Sarac, M.; Markovic, D.; Bacanin, N. Moth search algorithm for drone placement problem. Int. J. Comput. 2018, 3, 75–80. [Google Scholar]
- Strumberger, I.; Tuba, E.; Bacanin, N.; Beko, M.; Tuba, M. Wireless sensor network localization problem by hybridized moth search algorithm. In Proceedings of the 2018 14th International Wireless Communications & Mobile Computing Conference (IWCMC), Limassol, Cyprus, 25–29 June 2018; IEEE: Limassol, Cyprus; pp. 316–321. [Google Scholar]
- Tandon, A.; Kumar, P.; Rishiwal, V.; Yadav, M.; Yadav, P. A bio-inspired hybrid cross-layer routing protocol for energy preservation in wsn- assisted iot. KSII Trans. Internet Inf. Syst. 2021, 15, 1317–1341. [Google Scholar]
- Boursianis, A.D.; Papadopoulou, M.S.; Koulouridis, S.; Rocca, P.; Georgiadis, A.; Tentzeris, M.M.; Goudos, S.K. Triple-band single-layer rectenna for outdoor rf energy harvesting applications. Sensors 2021, 21, 3460. [Google Scholar] [CrossRef]
- Elaziz, M.A.; Xiong, S.; Jayasena, K.P.N.; Li, L. Task scheduling in cloud computing based on hybrid moth search algorithm and differential evolution. Knowl. Based Syst. 2019, 169, 39–52. [Google Scholar] [CrossRef]
- Zade, B.M.H.; Mansouri, N.; Javidi, M.M. Multi-objective scheduling technique based on hybrid hitchcock bird algorithm and fuzzy signature in cloud computing. Eng. Appl. Artif. Intell. 2021, 104, 104372. [Google Scholar] [CrossRef]
- Gokuldhev, M.; Singaravel, G. Local pollination-based moth search algorithm for task-scheduling heterogeneous cloud environment. Comput. J. 2022, 65, 382–395. [Google Scholar] [CrossRef]
- Fathy, A.; Elaziz, M.A.; Sayed, E.T.; Olabi, A.G.; Rezk, H. Optimal parameter identification of triple-junction photovoltaic panel based on enhanced moth search algorithm. Energy 2019, 188, 116025. [Google Scholar] [CrossRef]
- Boursianis, A.D.; Koulouridis, S.; Rocca, P.; Goudos, S.K. Modified patch antenna design using moth search algorithm for rf energy harvesting applications. In Proceedings of the International Workshop on Antenna Technology (iWAT), Bucharest, Romania, 25–28 February 2020. [Google Scholar]
- Huang, G.; He, B.; Meng, F.; Rodriguez, D. Evaluation of a multi-objective model in energy generation under the influence of different hydrological conditions based on moth search algorithm. Int. J. Ambient. Energy 2020, 20, 3888–3899. [Google Scholar] [CrossRef]
- Sun, S.; Su, Y.; Yin, C.; Jermsittiparsert, K. Optimal parameters estimation of pemfcs model using converged moth search algorithm. Energy Rep. 2020, 6, 1501–1509. [Google Scholar] [CrossRef]
- Shobana, S.; Praghash, K.; Ramya, G.; Rajakumar, B.R.; Binu, D. Integrating renewable energy in electric v2g: Improved optimization assisting dispatch model. Int. J. Energy Res. 2022, 46, 7917–7934. [Google Scholar] [CrossRef]
- Hussein, A.M.; Abd Elaziz, M.; Abdel Wahed, M.S.M.; Sillanpää, M. A new approach to predict the missing values of algae during water quality monitoring programs based on a hybrid moth search algorithm and the random vector functional link network. J. Hydrol. 2019, 575, 852–863. [Google Scholar] [CrossRef]
- Wagdarikar, A.M.U.; Senapati, R.K. Optimization based interesting region identification for video watermarking. J. Inf. Secur. Appl. 2019, 49, 102393. [Google Scholar] [CrossRef]
- Kumar, P.; Kumar Bhatt, A. Enhancing multi-tenancy security in the cloud computing using hybrid ecc-based data encryption approach. IET Commun. 2020, 14, 3212–3222. [Google Scholar] [CrossRef]
- Alotaibi, A.S. A hybrid attack detection strategy for cybersecurity using moth elephant herding optimisation-based stacked autoencoder. IET Circuits Devices Syst. 2021, 15, 224–236. [Google Scholar] [CrossRef]
- Varghese, M.; Jose, M.V. Securing cloud from attacks: Machine learning based intrusion detection in cloud sensor networks. Adhoc Sens. Wirel. Netw. 2021, 50, 143–171. [Google Scholar]
- Venkata Sailaja, N.; Padmasree, L.; Mangathayaru, N. Incremental learning for text categorization using rough set boundary based optimized support vector neural network. Data Technol. Appl. 2020, 54, 585–601. [Google Scholar] [CrossRef]
- Yarlagadda, M.; Gangadhara Rao, K.; Srikrishna, A. Frequent itemset-based feature selection and rider moth search algorithm for document clustering. J. King Saud Univ. Comput. Inf. Sci. 2022, 34, 1098–1109. [Google Scholar] [CrossRef]
- Kaur, P.; Wang, G.-G.; Singh, M.; Singh, S. Rank aggregation using moth search for web. In International Conference on Innovative Computing and Communications; Springer: Singapore, 2021; pp. 63–74. [Google Scholar]
- More, S.; Naik, U. Optimal multipath routing for video transmission in vanets. Wirel. Pers. Commun. 2021, 116, 805–827. [Google Scholar] [CrossRef]
- Razmjooy, N.; Razmjooy, S.; Vahedi, Z.; Estrela, V.V.; de Oliveira, G.G. A new design for robust control of power system stabilizer based on moth search algorithm. In Metaheuristics and Optimization in Computer and Electrical Engineering; Springer: Cham, Switzerland, 2021; pp. 187–202. [Google Scholar]
- Carrasco, O.; Crawford, B.; Soto, R.; Lemus-Romani, J.; Astorga, G.; Salas-Fernandez, A. Optimization of bridges reinforcements with tied-arch using moth search algorithm. In Proceedings of the 8th International Work-Conference on the Interplay Between Natural and Artificial Computation (IWINAC), Almeria, Spain, 3–7 June 2019; pp. 244–253. [Google Scholar]
- Ong, P.; Chong, C.H.; bin Rahim, M.Z.; Lee, W.K.; Sia, C.K.; bin Ahmad, M.A.H. Intelligent approach for process modelling and optimization on electrical discharge machining of polycrystalline diamond. J. Intell. Manuf. 2020, 31, 227–247. [Google Scholar] [CrossRef]
- Thokar, R.A.; Gupta, N.; Niazi, K.R.; Swarnkar, A.; Meena, N.K. Multiobjective nested optimization framework for simultaneous integration of multiple photovoltaic and battery energy storage systems in distribution networks. J. Energy Storage 2021, 35, 102263. [Google Scholar] [CrossRef]
- Fu, Y.P.; Hou, Y.S.; Wang, Z.F.; Wu, X.W.; Gao, K.Z.; Wang, L. Distributed scheduling problems in intelligent manufacturing systems. Tsinghua Sci. Technol. 2021, 26, 625–645. [Google Scholar] [CrossRef]
- Fu, Y.P.; Tian, G.D.; Fathollahi-Fard, A.M.; Ahmadi, A.; Zhang, C.Y. Stochastic multi-objective modelling and optimization of an energy-conscious distributed permutation flow shop scheduling problem with the total tardiness constraint. J. Clean. Prod. 2019, 226, 515–525. [Google Scholar] [CrossRef]
- Ghosh, P.; Mandal, S.N. PigB: Intelligent pig breeds classification using supervised machine learning algorithms. Int. J. Artif. Intell. Soft Comput. 2022, 7, 242–266. [Google Scholar] [CrossRef]
- Singh, S.; Maurya, L.S.; Hussain, M.S. Machine learning classification models for student placement prediction based on skills. Int. J. Artif. Intell. Soft Comput. 2022, 7, 194–207. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).