1. Introduction
The amount of technical systems operating autonomously and without human interference is continuously growing. It is of utmost importance to demonstrate that such autonomous systems cannot harm people, cause damage, or breach any other important specification. Autonomous vehicles and moving robots are examples of such safety-critical applications, where the discrete and continuous aspects are tightly intertwined—these systems are often referred to as hybrid systems.
Model-based formal verification is an important approach toward safer systems. In particular, reachability analysis computes the set of reachable states of a model and can be used to check whether unsafe states are possible [
1,
2]. To include different possible behaviors of the real system, verification models for reachability analysis are non-deterministic. This means that at each point in time, there might be multiple evolutions of the model, and one has to reason about all of them. The basic assumption of model-based verification is that the model is related to the system in a way that the safety of the system can be implied if the safety of the model has been shown. We call a relation between a system and a model
conformance relation and argue that it should also be defined formally. Otherwise, one cannot be sure that the used conformance relation allows to transfer safety properties from the model to the real system, which would make the formal verification effort useless. Hence, the conformance relation connects the formal world of reasoning with the real world.
A major challenge of a verification model is that it simultaneously has to be amenable to verification and conformance. This is challenging because (i) a model with significant non-determinism is conformant, but it might have too many reachable states to verify properties (model 1 in
Figure 1) and (ii) a model with insignificant non-determinism is amenable for verification, but it might not be conformant to the real system because some states cannot be produced by the model (model 4 in
Figure 1). Between these two extremes are the most useful models, amenable for both verification and conformance (model 2 and model 3 in
Figure 1). We argue that an optimal model has just enough non-determinism such that reachset conformance holds to sustain the most freedom possible for verification. A method is needed to build verification models maximizing verification capabilities while ensuring conformance.
In a previous paper [
3], we introduced
reachset conformance and showed how to test it for a given (hybrid-system) model
M and measurements of a (real) system
S. Here, we extend these results in several aspects:
Natural choice: We show that safety properties can be transfered from M to S exactly in the case when reachset conformance between M and S holds. Therefore, reachset conformance is the natural choice to transfer safety properties.
Quantified reachset conformance check: A robustness measure is introduced, which is based on the distance of a point to the boundary of a reachable set. In our setting, reachable sets are represented as zonotopes, and as a result, exclusion can be checked using linear programming techniques. This is computed for the measured data of the real system of some input and the output of the verification model for the same input, cf.
Figure 2.
Model adaptation: We show how to automatically adapt the non-determinism of a model
M, such that
M becomes reachset-conformant to
S. This is computed by identifying bounds on non-deterministic parameters. The bounds are optimized using Bayesian optimization to minimize the non-determinism while being conformant,
Figure 1. In addition to building a reachset-conformant model, the method maximizes the verification capabilities of the model, cf. model 3 in
Figure 2. Thus, our method helps to overcome the burden of building a formal verification model.
Autonomous vehicle application: We apply our methods to a real automated vehicle and construct a verification model of the vehicle. Measured driving data of the automated vehicle were recorded, and our model adaptation was applied to identify the non-determinism of the verification model such that the model is reachset-conformant to the automated vehicle. Our verification model is amenable to verification, showing that our approach is applicable to the highly relevant use case of autonomous vehicles. This is the first work showing reachset conformance for a real (autonomous) vehicle.
The paper is structured as follows: First, we discuss related work on conformance and verification in
Section 2. In
Section 3, we present the underlying formalism of hybrid automata and other preliminaries. In
Section 4, we present reachset conformance, prove that it is necessary and sufficient to transfer safety properties, and compare it to trace conformance, which is discussed in [
4]. In
Section 5, we present a testing method for reachset conformance. In
Section 6, we introduce our model adaptation algorithm. In
Section 7, we apply the presented techniques to a real vehicle and build a reachset-conformant vehicle model. Finally, we give some conclusions and future directions.
3. Preliminaries
In this paper, we use
hybrid automata as a modeling formalism. A hybrid automaton can be seen as a finite automaton whose discrete states are annotated with differential inclusions that define the non-deterministic evolution of the continuous states [
31]. An overview of definitions of hybrid automata and their differences has been presented by Frehse [
17]. In our work, a (non-deterministic) hybrid automaton
H consists of
A finite set of locations ;
A continuous state space ;
An initial set ;
A continuous input space ;
A flow function , where is the power set of X;
An invariant set for each location q;
A set of discrete transitions ;
A guard set for each transition ;
A jump function for each transition ;
An output space ;
An output map .
For a given input function
, which maps each point in time to an input value, a
state trace x of
H is
with discrete states
, continuous state functions
, and with the initial state
. The transitions from
to a new state
have to satisfy
. The continuous state function
has to satisfy the invariant set
and the differential inclusion
. Upon a discrete transition
, the continuous state satisfies
as well as
. Note that we have a non-deterministic initial state, non-deterministic flow and jump functions, so there are multiple state traces possible for a given input trajectory
. The set of state traces for a given hybrid automaton
H with initial set
under input
is denoted by
.
While state traces represent the internal states of the system, they are not observable. Instead, we are able to observe the output trace
which is the mapping of the state trace
x onto the observable output space via the map
:
The set of all output traces under an input trajectory and the initial set is denoted by . Therefore, the set represents all possible observable behaviors over time for the given and . If has one element only for every and a single initial state, the hybrid automaton H is called deterministic and non-deterministic otherwise.
The already existing trace conformance, which we talked about in the overview section, can now be defined formally:
Definition 1 (trace conformance [
4]).
Let S and M be two systems with the same input set and output space, and with the initial sets and , then S is trace conformant to M, which is denoted by , ifholds for all . This means when trace conformance holds, all observable behavior over time of
S is also observable of
M. A safety property consists of a set of unsafe output states
for every time
t. If this set is never reachable, i.e.,
then
H is considered safe.
Given such a safety property with
and a model
M, verification deals with algorithmically checking that (
4) holds. When reasoning about the future evolution of a system
H, one has to consider all—potentially infinitely many—output traces. With infinitely many traces, dealing with the output traces directly is intractable. One important approach to solve this problem is to use reachability analysis. For one point in time
t, the
reachable set (or shorter: reachset) of outputs of the hybrid automaton
H at time
t contains all output states which are possible at time
t for a given input trajectory
:
We call the sequence of these reachable sets
over time
t as the
reach sequence of
H. Note that the elements of
are functions over time, whereas the set
consists of output states for one point in time
t only. Reachable sets can be used to reason about properties of
H by verifying that no unsafe set
of a safety property is reachable:
Since the reach sequence is an abstraction of the output traces
, trace conformance is not the best relation for transference between reach sequences, as described in
Section 4. Therefore, we present reachset conformance in the following section.
Let us now more formally and generally specify the problems addressed in this paper. Given a non-deterministic model
M of a hybrid system
S, the type of relation
between
S and
M needed to transfer any safety property
from
M to
S is:
where
means system
S has the property
.
Let us also introduce a Gaussian process (Section 6.4, [
32]) with parameter vectors
and
as a function
mapping the input
p to a Gaussian distribution with mean
and variance
. The
are the samples, and the Gaussian process generalizes the mapping by estimating the similarity between different values for
p. The functions
and
are defined as [
32]:
where
is the matrix transposition, and
is a kernel function defined (in our case) as
,
, and the matrix
K contains the entries
in the
row and
column. The parameters
can be computed using hyperparameter optimization with
P and
V (Section 6.4.2, [
32]).
4. Reachset Conformance
With the preliminaries from
Section 3, we are now able to formally define the notion of reachset conformance.
Definition 2 (reachset conformance [
3]).
Let S and M be two systems with the same input space and output space. Let and be the initial sets of S and M, respectively; then, S is reachset-conformant to M, denoted by , if for all possible inputs and : Reachset conformance directly considers the non-determinism of models while still being able to transfer safety properties.
Proposition 1. Let two systems S and M be given with and initial sets and , respectively. Let a safety property with forbidden state sets be given for all t. For any input trajectory , the following transference holds for every t: Proof. Since S is reachset conformant to M and thus is a subset of for all t, the proposition follows immediately. □
The following theorem shows that reachset conformance is the natural choice for the transference of safety properties.
Theorem 1. Let two systems S and M be given. The transference of safety properties is equivalent to reachset conformance:
Proof. One direction follows from Proposition 1. Let us assume that (10) holds for all
t and all possible
. Choosing
, which is the complement of the reachable set of
M at time
t, the intersection of
and
is obviously empty. Since this property is transferable from
M to
S, the equation
holds, and thus,
. This works for every
t, and thus,
S is reachset conformant to
M. □
Although we are mainly interested in the transference of safety properties, there are temporal fragments which transfer with reachset conformance. For instance, temporal properties formalizable in reachset temporal logic, which were introduced by Roehm et al. [
33]. However, temporal properties cannot be transfered in general, as the reach sequence is an abstraction of the output traces. Reachset conformance is a weaker conformance notion than trace conformance:
Theorem 2. Let S and M be two systems with the same input set and output space; then,holds. The converse holds if the system M (and thus S) is deterministic. Proof. Let be an input trajectory, t be a point in time, and . Then, there is a with . From , it follows that is also a trace of M and . The proposition follows, because the aforementioned implication holds for all y, t, and . When the system M is deterministic, there is only one trace in , and the reachable set for any time consists of only one state. Hence, S has the same trace and is also deterministic. □
This shows that reachset conformance is weaker compared to trace conformance and that we can transfer properties between reachsets in cases where trace conformance does not hold.
5. Reachset Conformance Testing
In this section, we show how to check the reachset conformance of a real system
S against a model
M. Additionally, we introduce a robustness measure which quantifies conformance. Since proving a physical model against the real world is not possible, the goal is to check if the non-conformance S
![Mathematics 10 03567 i001 Mathematics 10 03567 i001]()
M can be shown by a counter-example for a given input
. Hence, we have to prove that the negation of (
9) holds, which is
Our test to check reachset conformance consists of three steps:
- 1.
Obtain measurements of the system S as an underapproximation of the reachable states of for a finite set T of points in time .
- 2.
Compute an overapproximation of the reachable set of for all .
- 3.
Check if holds for any .
If for any t a non-inclusion is found, a counter-example is found, and non-conformance is proven. In the following, we discuss the steps in detail.
5.1. Obtain Measurements of S
Real measurements are subject to noise, and we assume there exists an error
, which bounds the deviation of all measurements
to the true trace
:
In our case, we consider to be the Euclidean 2-norm. Taking all runs of S for the same input , this approach builds up reachable sets underapproximations.
5.2. Overapproximation of the Reachable Sets of M
An overapproximation of
M can be efficiently computed using reachability analysis. Our work builds on the tool CORA [
6] to compute reachable set overapproximations for hybrid automata with nonlinear continuous dynamics. CORA uses zonotopes to represent reachable sets due to their efficiency in linear transformations and Minkowski additions [
34].
Definition 3 (Zonotope).
An n-dimensional zonotope Z in generator representation (G-representation) is the setwhere is called the center and are called the generators of Z. 5.3. Exclusion Check
For a given , we have to check if a given measurement with is excluded from . Since we consider the measurement error, we have to check that all possible candidates for the real value are not contained to prove exclusion. Hence, the ball around has to be completely outside the reachable set to prove that a counter-example exists.
The distance is important information, which we will use for the model adaptation. Therefore, we are using support functions to define a distance metric (note that the approach using support functions can be applied to other convex (reach-)sets representations as well) [
35].
Definition 4 (robustness).
Let a vector , a point , and a zonotope Z with center c and m generators be given. Thenis the directed robustness of Z and x in direction d. The robustness of x and Z is defined as . If the robustness metric is negative, x lies outside of Z and the robustness gives the negative of the minimal distance between Z and x in the Euclidean norm. If x is contained in Z, the robustness is the distance of x to the surface of Z. Hence, the robustness metric enables us to check exclusion.
Theorem 3. A point is not contained in a zonotope Z if and only if the robustness is negative: Proof. Let us assume that
and
Z has the generators
. Then, there exists
with
and
. For any
d holds
The other direction follows analogously. □
For a given point
with error
, we are able to show exclusion of the real measurement by checking
(see Proposition 5, [
3]). Hence,
has to be computed. This can be achieved by sampling directions
d and approximating the robustness, as shown in [
3]. Another approach is to use linear programming to find the direction
d which minimizes
.
6. Model Adaptation
As the verification capabilities of a model are highly dependent on the sizes of the reachsets, the measure
on the reachsets is used to determine the verification capabilities:
where the volume function Vol is a metric on the reachable sets. Here, we are using the volume of the reachsets
but the P-radius [
36] and F-radius [
37] can be used as well in case of computational limitations. Similarly, the conformance measure
is defined as
to show how robust the model is conformant for given measurements
of the real system
S under input
and initial condition
. Hence, an optimal model
(with respect to
Figure 1) can be defined as
where
is the set of all possible models. For computational feasibility, we assume that
can be represented by a parametrization that is a surjective projection
. The idea is to represent possible amounts of non-determinism by parameters as shown in the following example.
Example 1. Let us consider the toy example of a bouncing ball. At one point in time, it has a certain height h over the ground and a velocity v. Over time, it is accelerated by the gravity and bounces off when reaching the ground. As non-determinism can be involved in the acceleration (continuous part) and the bouncing off (discrete part), the possible choices of the non-determinism can be modeled with parameters resulting in the differential inclusions , and jump function with guard . Using measurements of a real bouncing ball, and can be obtained by solving (19). In this paper, Equation (
19) is solved using Gaussian processes (see
Section 3) and Bayesian optimization with inequality constraints [
38]. The central idea of Bayesian optimization is to use existing function evaluations to build probabilistic regression models. These models are Gaussian processes and are used to select the next parameter to test. In our setting, the Gaussian processes
and
are built to approximate the conformance measure and the verification measure:
As the most interesting region for
is near zero, approximating the cube root instead of
has been shown beneficial in our application in
Section 7 for the learning process.
The model adaptation works by executing the following steps:
- 1.
Initialize vectors with random values and calculate the vectors via .
- 2.
Generate and using and C.
- 3.
Find
minimizing
with
using Bayesian optimization [
38], add
to
P, and add
to
V and
C, respectively.
This iteration is completed iteratively until the probability is high that
with
is the solution of (
19). Using
and
, this is measured using
as an end criterion.
7. Application of Reachset Conformance to an Autonomous Vehicle
Automated vehicles are an important application of hybrid systems. One main verification task for automated vehicles is to ensure safe operation without collisions with other traffic participants. Since there are too many real-world situations to verify all of them beforehand, methods have been created to verify the automated vehicle online [
39,
40]. The verification approach is model-based, which creates the necessity to check that the model and the real vehicle are conformant such that verification results can be transfered.
The following demonstrates when to apply reachset conformance by measuring data of a real automated vehicle and building a reachset conformant model for it with the model adaptation method. As we have a limited amount of experimental data, one should increase the amount of measurements for real-world verification applications.
7.1. Experimental Setup
Four different types of maneuvers with a velocity of
= 10
and a maximum lateral acceleration
= 2
have been considered. As visualized in
Figure 3, the four maneuvers are
- 1.
Single lane-change maneuver: One single lane-change from a right lane to the left lane, which is a typical maneuver for automated vehicles.
- 2.
Double lane-change maneuver: After a single lane-change, the vehicle stays on the left lane for 4 s and switches back to the initial lane. This is a standard overtaking maneuver.
- 3.
Fast double lane-change maneuver: This maneuver is similar to the double-lane change maneuver, but it immediately switches back to the right lane when on the left lane. Such a maneuver occurs when avoiding obstacles on the road and is more dynamic than the double-lane change.
- 4.
Slalom maneuver: To challenge the model with measurements of a more dynamic maneuver, a slalom maneuver was additionally included.
These maneuvers were selected based on the experimental capabilities of the driving location and can be seen as basic maneuvers in an urban multilane setting. Each maneuver was repeated five times with the average duration of a maneuver being 14.16 at a rate of 100 . Overall, the total driven distance of the dynamic maneuvers within the measurement data was around 3 . The data were collected by Deutsches Zentrum für Luft- und Raumfahrt (DLR) with their test vehicle (FASCar II, a Volkswagen Passat TDI), which is equipped with a combined differential GPS receiver (DGPS) and inertial navigation system (INS). All maneuvers used for conformance testing have been executed in automated driving mode, i.e., closed-loop tracking of a predefined reference trajectory, which is sent from a PC to a closed-loop tracking controller on a dSPACE Autobox. We estimate the sensor error for the position of the vehicle by 5 cm and for the orientation of the vehicle by an angle of 0.5.
7.2. Verification Model
The verification model contains of a steered vehicle model, which is combined with a tracking controller providing the steering inputs based on the ideal maneuver trajectory. Our vehicle model is based on the bicycle model [
7,
39]. The state space of the vehicle model is 6-dimensional and has the states
, where
is the position of the vehicle’s rear axle center in an earth-fixed coordinate system, and
is the orientation of the vehicle. The speed of the vehicle’s rear axle center is given as
in the vehicle coordinate system. The velocity components are the respective projections to the vehicle’s longitudinal and lateral axis. The vehicle’s yaw rate is given as
. The vehicle model’s input vector
contains the longitudinal acceleration and the steering angle. The differential equations of the vehicle model are
with constants
,
,
,
,
,
, and
.
The tracking controller by Hess et al. [
41] was used consisting of a feed-forward controller and a PD feedback term for the deviation from the reference trajectory.
The state space of the combined model was divided into eight regions which represent the discrete states of the verification model. In each part, a Taylor expansion of the differential equations of the combined model is used as the differential equations of the verification model. Since the main dimensions of interest are the position and orientation of the vehicle, e.g., to detect possible collisions, these dimensions are used as the outputs and mapped onto this subspace with the output map . The parameters , , and are injected as additive non-determinism , and into the differential equations for x, y, and , respectively.
7.3. Reachset Conformance Testing
The initial points of all runs of a maneuver are used to build the initial set for the model for that maneuver. Since the measurements contain some sensor error, the bounding box of the initial points enlarged by the sensor errors is used as initial set
of the model. The pairwise direction check as described by Roehm et al. [
3] is used to check for the exclusion of measured data from the reachable sets of the three-dimensional output space, considering the sensor error.
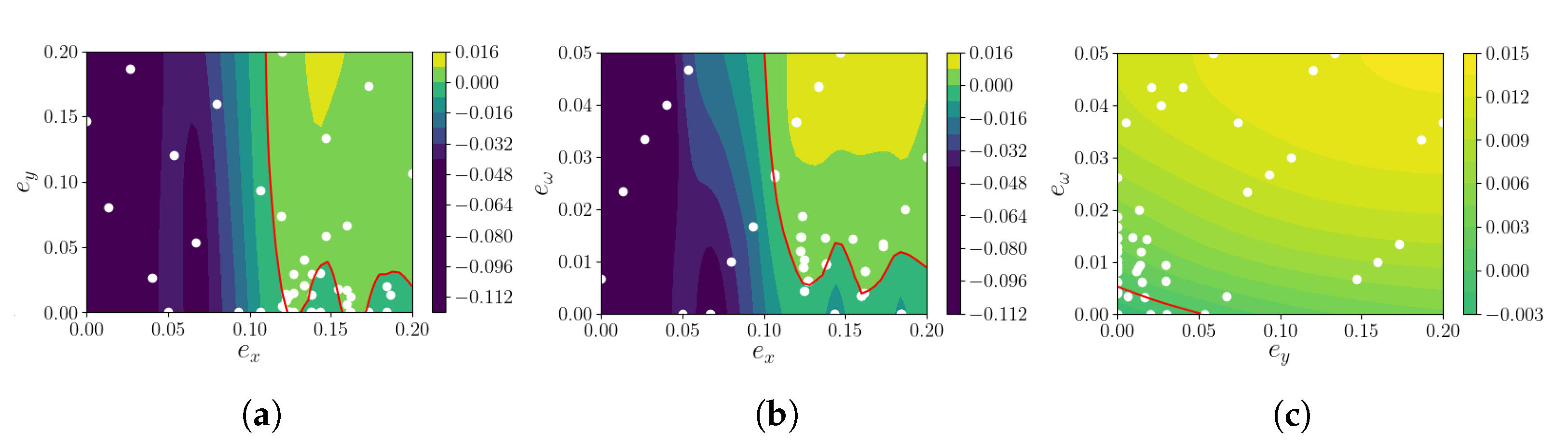
The model adaptation method from
Section 6 has been applied to the model and the measurements of the automated vehicle. The measure
for the mapping from the parameters to the conformance measure after 30 iterations is visualized in
Figure 4. In the figure, one can see the estimated robustness of each combination of non-deterministic bound parameters
. The red line consists of all parameters with
, which are the boundary between the conformant and non-conformanct parameter areas. All parameter combinations on the upper right side of the red line can be considered as conformant.
The white points represent the parameter combinations with which the exclusion check has been executed to compute the robustness for the conformance measure. These combinations were iteratively selected by
and used to update
. As one can see in the figure, the white points are not uniformly distributed, but the density of points is much higher near certain areas of the red line. This is a direct outcome of the model adaptation algorithm. First, parameter combinations in the whole space of parameter combinations are selected to obtain an initial understanding of the regions of interest. After some iterations, the confidence of
increases, and more points near the expected parameter combinations of the optimal model
are selected. Please note that the white points in all subfigures are only projections of the three parameters to two parameters. Even when the white points are sitting on the non-conformant side of the red line in the subfigure, the non-projected parameters may not. In (a) and (b) in
Figure 4, the red line is winding in the lower part. This is due to approximation errors in
. However, this is not a problem for the method, as these areas do not contain the optimal parameter combinations and thus are not explored further.
From
Figure 4, the relation between the different parameters can be seen. The red line in the subfigures with
are mainly horizontal and vertical. This shows that the non-determinism on
x is independed to the non-determinism on
y and
. Contrary,
vs.
shows that when the lateral nondeterminism is increased, the nondeterminism of the yaw rate can be reduced and vice versa. This shows that both have a similar impact on the lateral movement of the vehicle in our maneuvers and is likely a result of the main direction of travel in the
x direction.
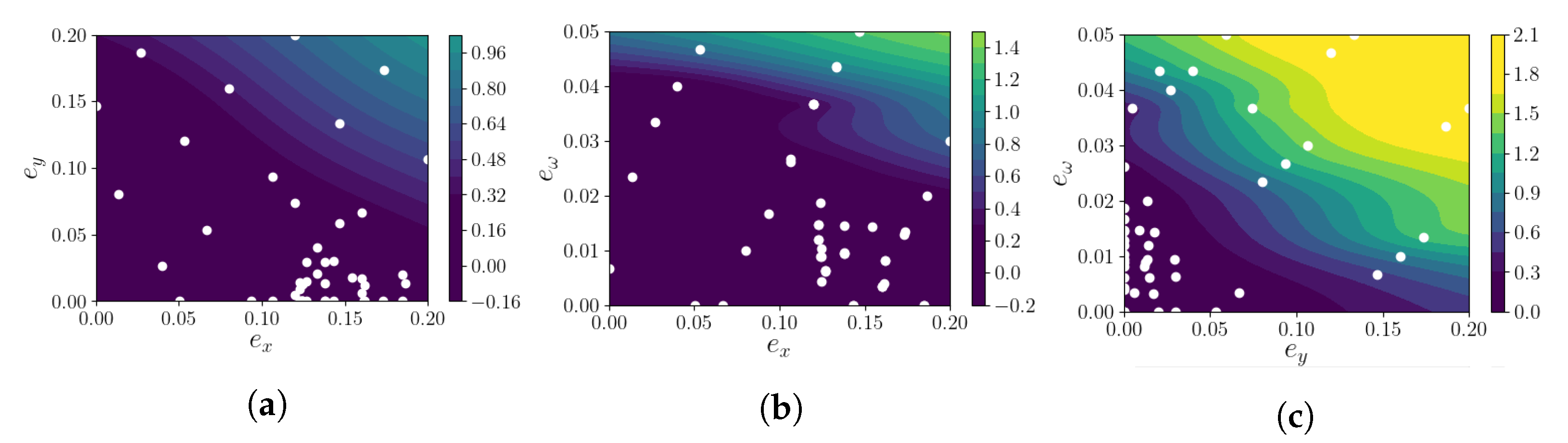
The verification measure with respect to the parameters is visualized in
Figure 5. As in
Figure 4, the verification measure is shown with the white points representing the parameter combinations used. The shape of all projections is looking quite similar. This is due to the monotonicity of the reachset sizes with respect to the non-determinism. When one parameter is increased, the overall non-determinism increases, and thus, so does the reachset size. In the origin, all parameters are zero, the model is deterministic, and the reach sequence reduces to a trace, cf. Theorem 2.
The reachsets of the optimal model are visualized together with the measurement data in
Figure 6. The optimal model has an interval width in the lateral position of 0.22 m and in the longitudinal position of 0.47 m, which can be considered as good enough for all considered driving tasks. Big uncertainty, such as over 0.5 m in the lateral position
, may lead to situations where the vehicle could potentially be already on an adjacent lane and a collision may be possible. Hence, we have built a reachset-conformant model which is amenable for verification purposes.
8. Conclusions
In this paper, reachset conformance was presented that is able to relate a model to the system it models (and to other models as well). It was shown that reachset conformance is the natural conformance relation for safety properties, because safety properties transfer exactly in the case when reachset conformance does hold. Trace conformance implies reachset conformance and is the same in the case of deterministic systems.
Reachset conformance testing of a verification model is completed by searching for counter-examples with measurements of the real system. A robustness measure is introduced to estimate the distance of the model to be conformant or non-conformant based on the distance of a measurement to the reachable set of the verification model. Zonotopes are used as the representation of reachable sets which makes the computation of the robustness feasable.
A conformance measure is defined based on the robustness, and a verification measure is defined based on the size of the reachable sets and used to estimate the applicability of models for verification. The non-determinism of the model is considered as parametric, and a model adaptation algorithm is introduced to search for an optimal model, which minimizes the verification measure and has a positive value of the conformance measure. The algorithm uses Bayesian optimization to approximate the conformance measure and the verification measure and guides the search for the optimal parameters.
Finally, the presented methods are applied to an autonomous vehicle, for which data measurements of real driving maneuvers have been recorded. A parametric verification model is presented, and the methods of the paper are applied to find optimal parameters for that model to maximize the verification capabilities while ensuring conformance. Since the resulting reachable sets of the non-deterministic verification model have a size of at most 0.22 m in the lateral direction and 0.47 m in the longitudinal direction, the model produces small enough reachsets and can be used for verification purposes.
In future work, we want to collect extended amounts of driving data with a wider range of maneuvers and build a verified model that can be run online. This will combine multiple existing research directions and show how complicated it is to run the full pipeline for the verification of autonomous vehicles.
 M can be shown by a counter-example for a given input . Hence, we have to prove that the negation of (9) holds, which is
M can be shown by a counter-example for a given input . Hence, we have to prove that the negation of (9) holds, which is