Context-Based Support to Enhance Developers’ Learning of Software Security
Abstract
1. Introduction
2. Scientific Background and Related Work
2.1. Convention Software Security Teaching and Learning
2.2. Context-Based Teaching and Learning
2.3. Tool-Based Support for Learning Software Security
- (1)
- The tool is context-based, in which context-based learning is facilitated in the learning process.
- (2)
- The tool is ontology-based, in which the security knowledge is modeled with contextual situations and incorporates theoretical knowledge to complement the concrete description.
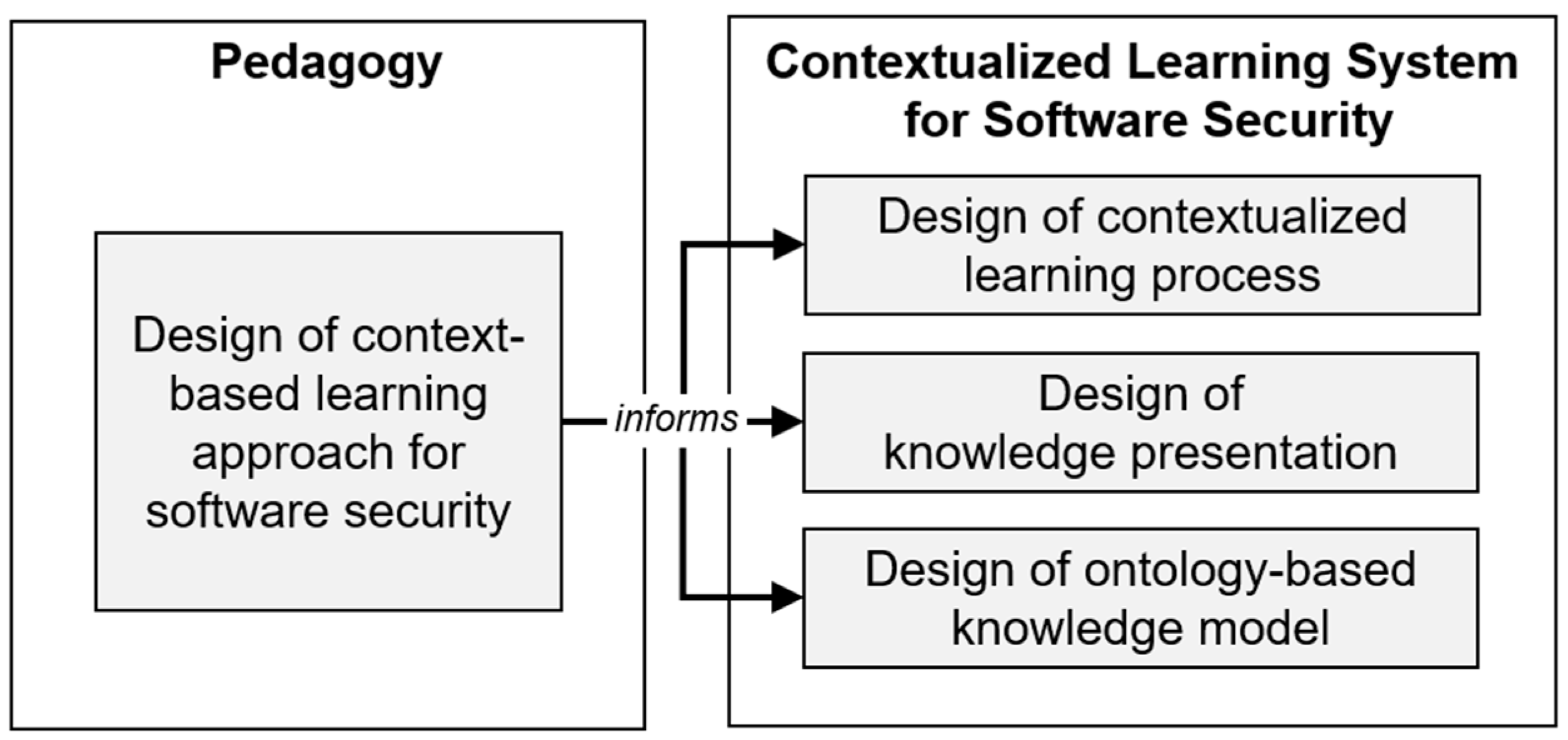
3. Design Consideration
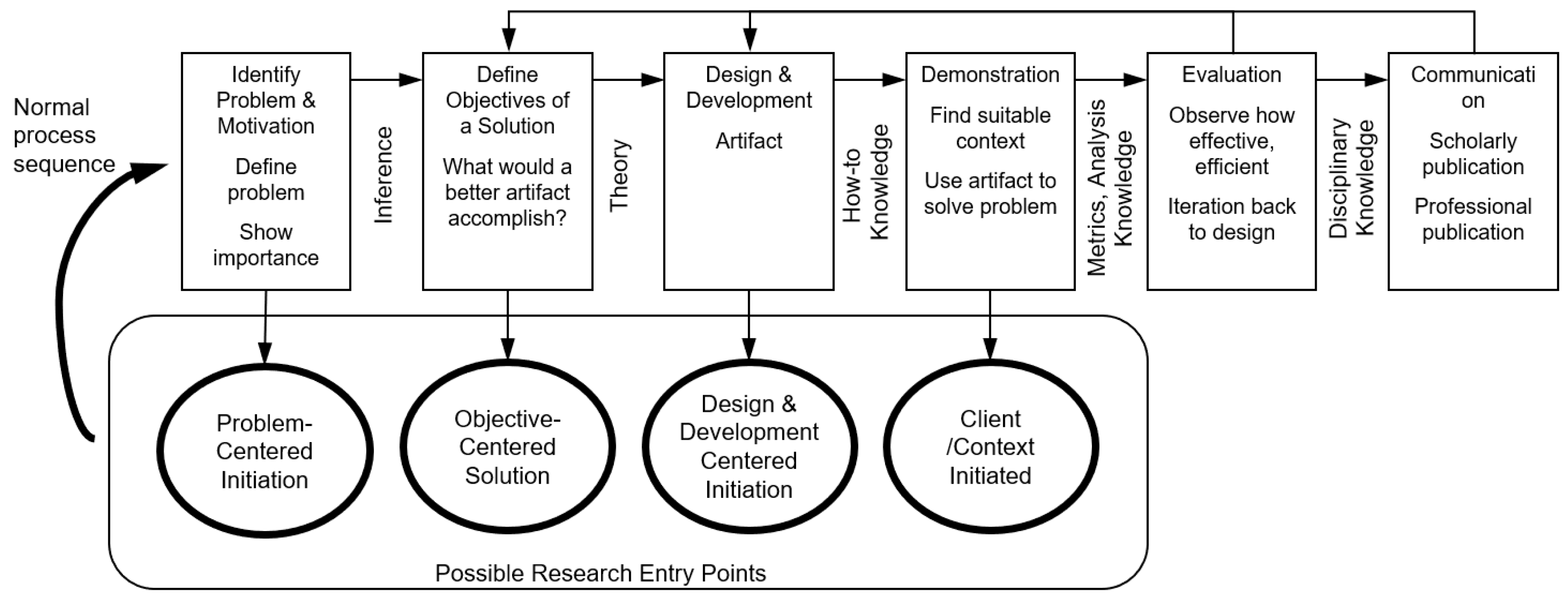
4. Research Methodology
4.1. DC1: A Context-Based Learning Approach for Software Security
4.1.1. Objective and Solution
4.1.2. Design and Development
4.1.3. Demonstration and Evaluation
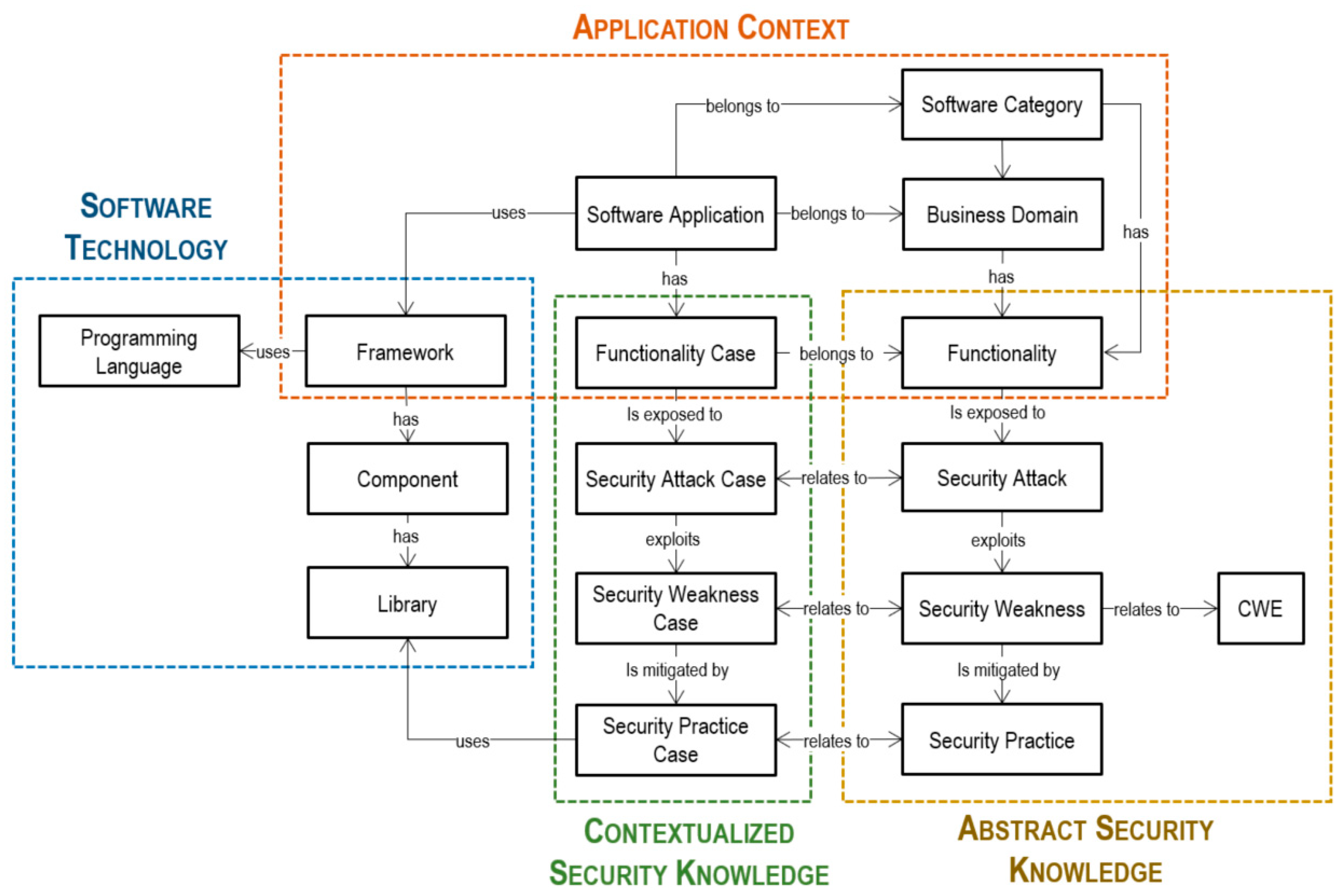
4.2. DC 2: A Context-Based Ontology for Managing Contextualizing Security Knowledge
4.2.1. Objective and Solution
4.2.2. Design and Development
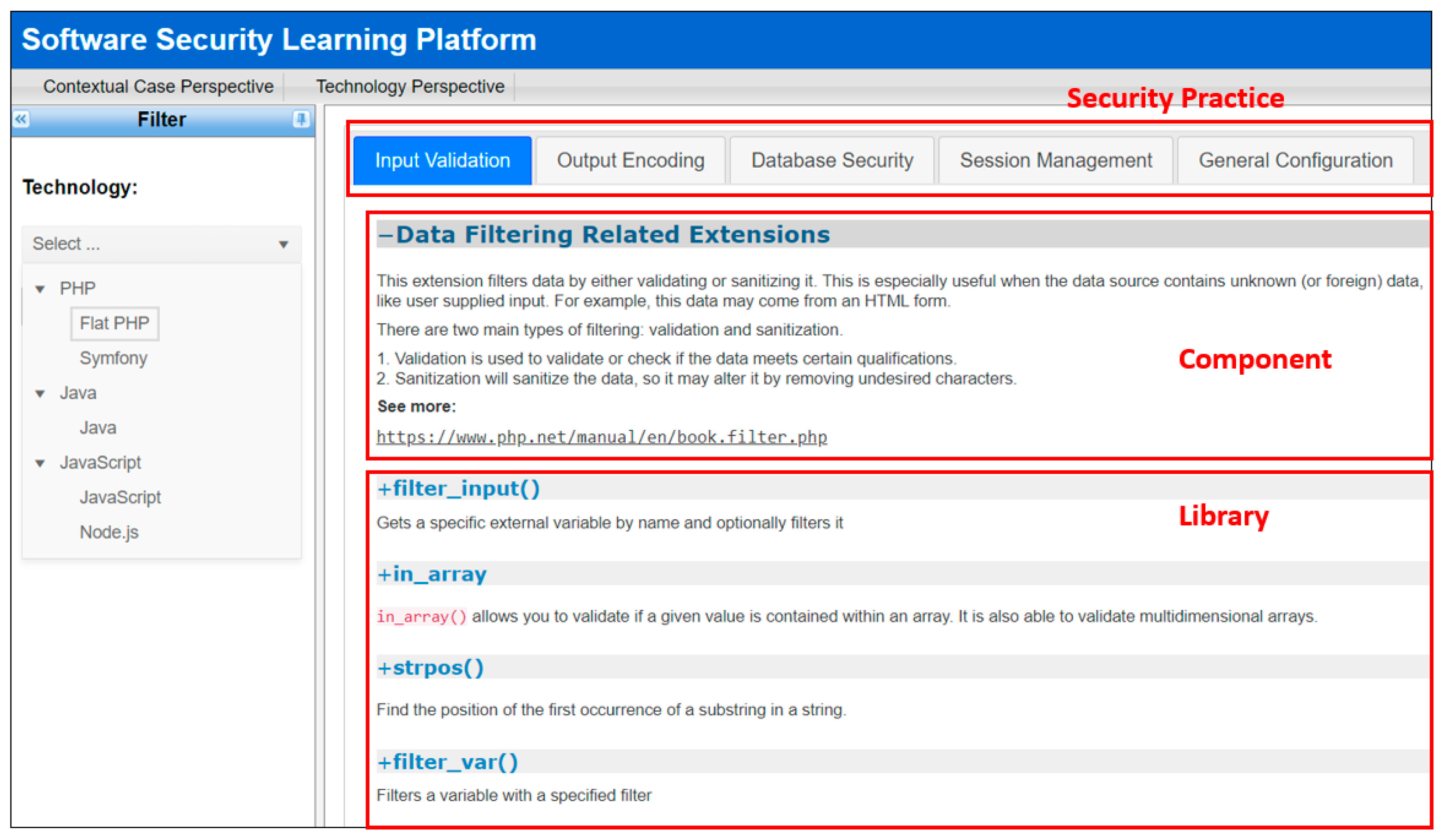
- Application context perspective.
- Software technology perspective.
- Abstract security knowledge perspective.
- Contextualized security knowledge perspective.
4.2.3. Demonstration and Evaluation
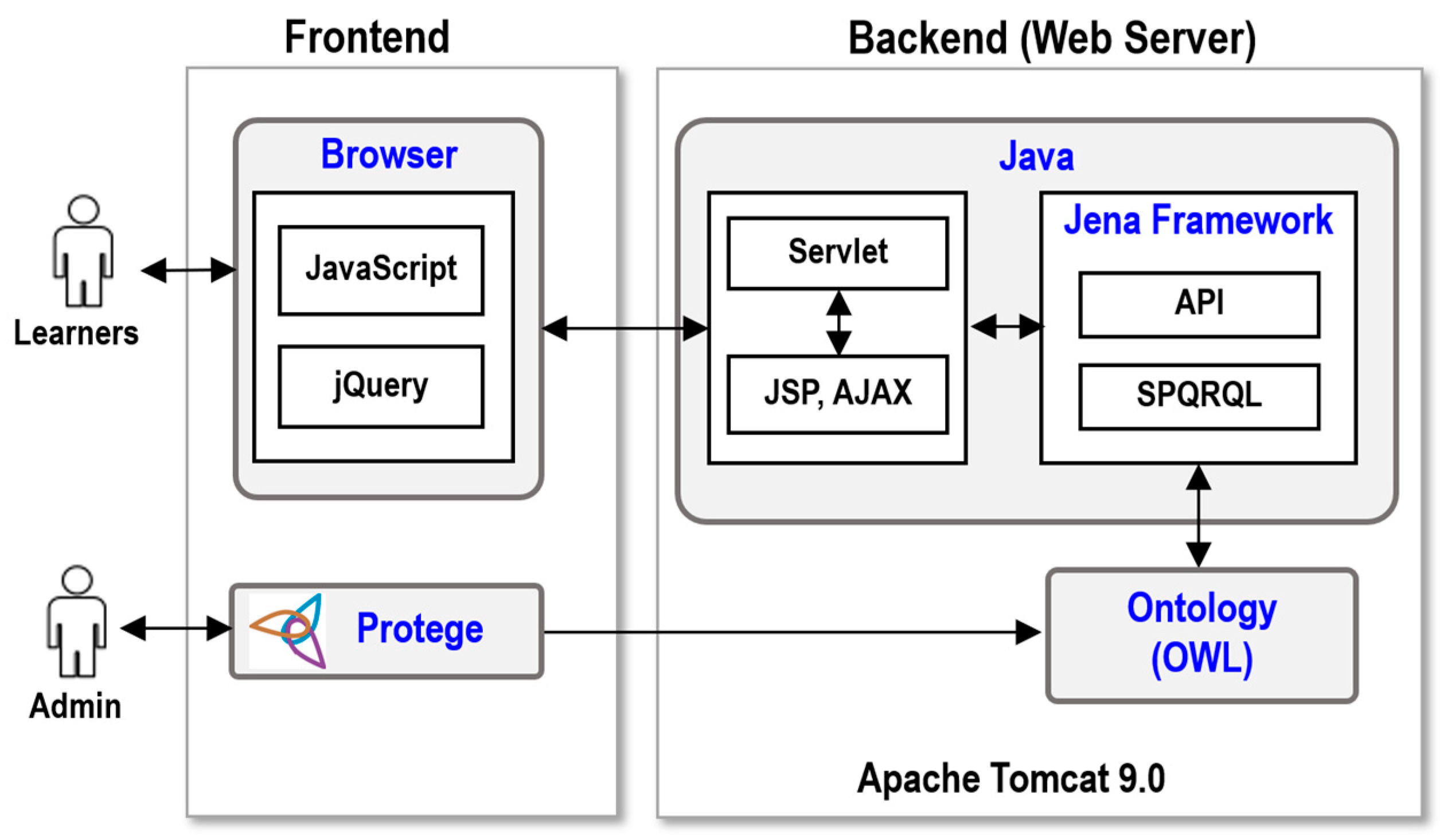
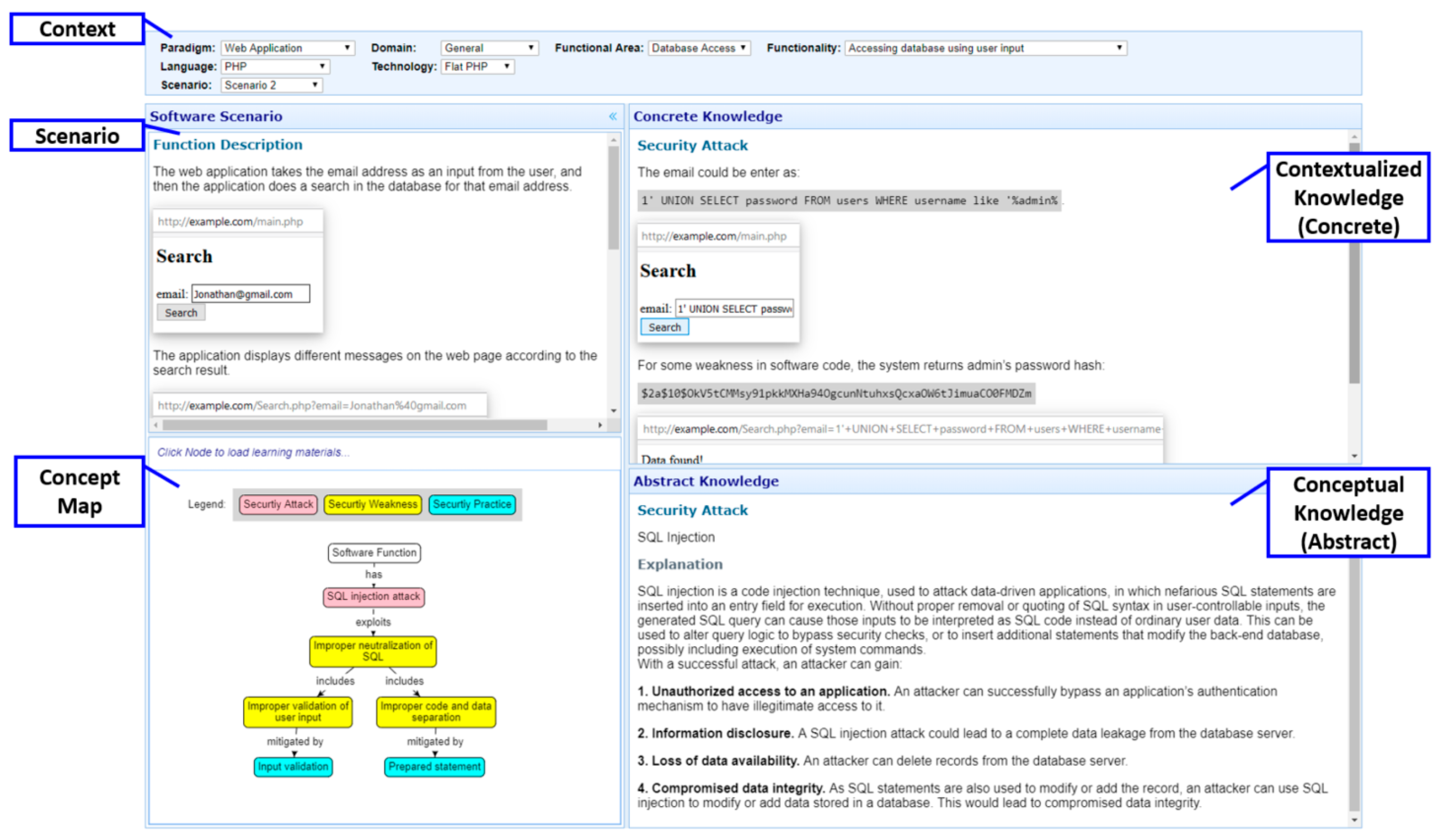
4.3. DC 3: An Ontology-Based Contextualized Learning System for Software Security
4.3.1. Objective and Solution
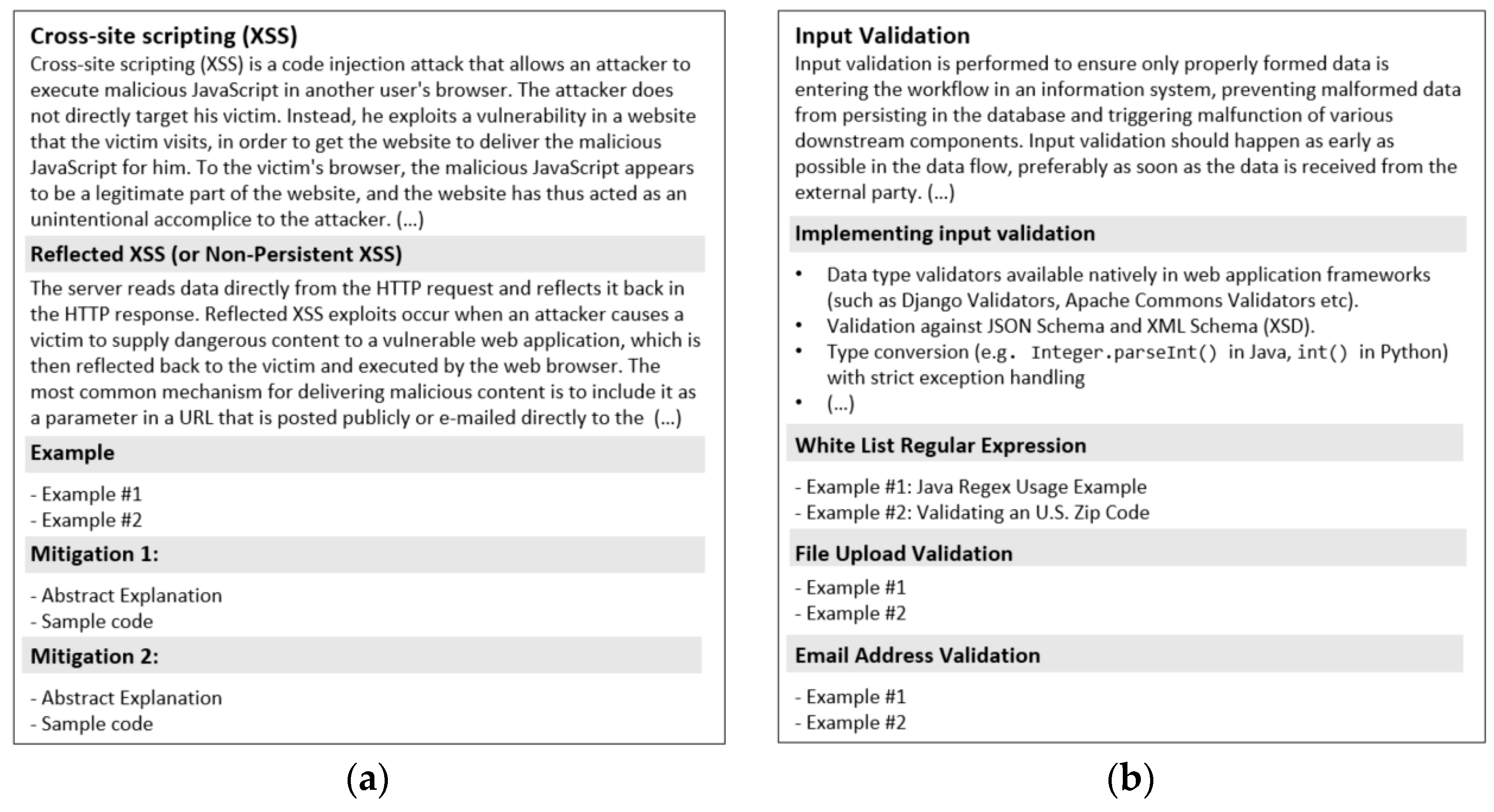
4.3.2. Design and Development
4.3.3. Demonstration and Evaluation
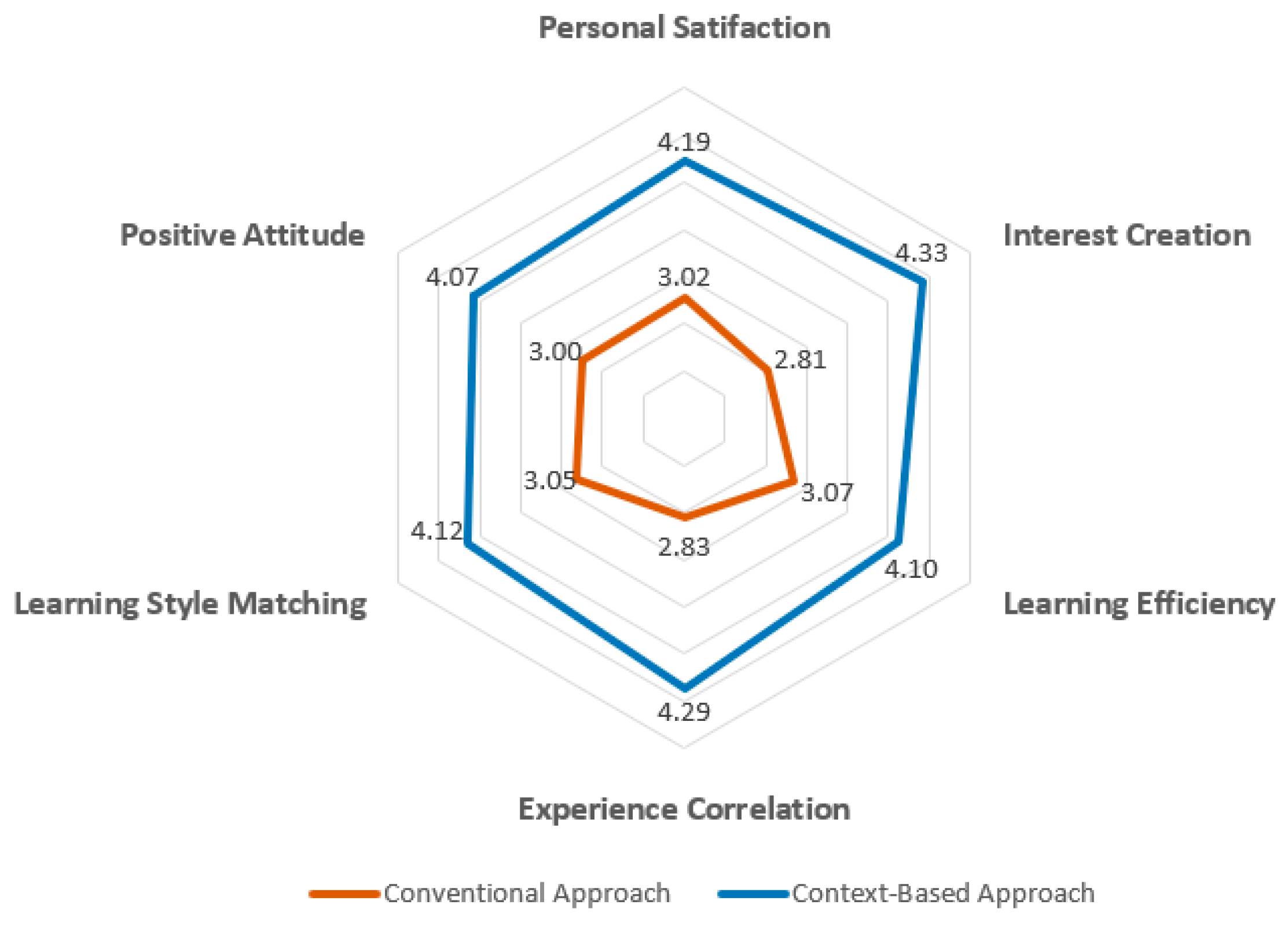
- Preliminary evaluation.
- Evaluation in open-source software development environments.
4.4. DC 4: Revision of the Learning System and an Evaluation in a Software Company
4.4.1. Objective and Solution
4.4.2. Design and Development
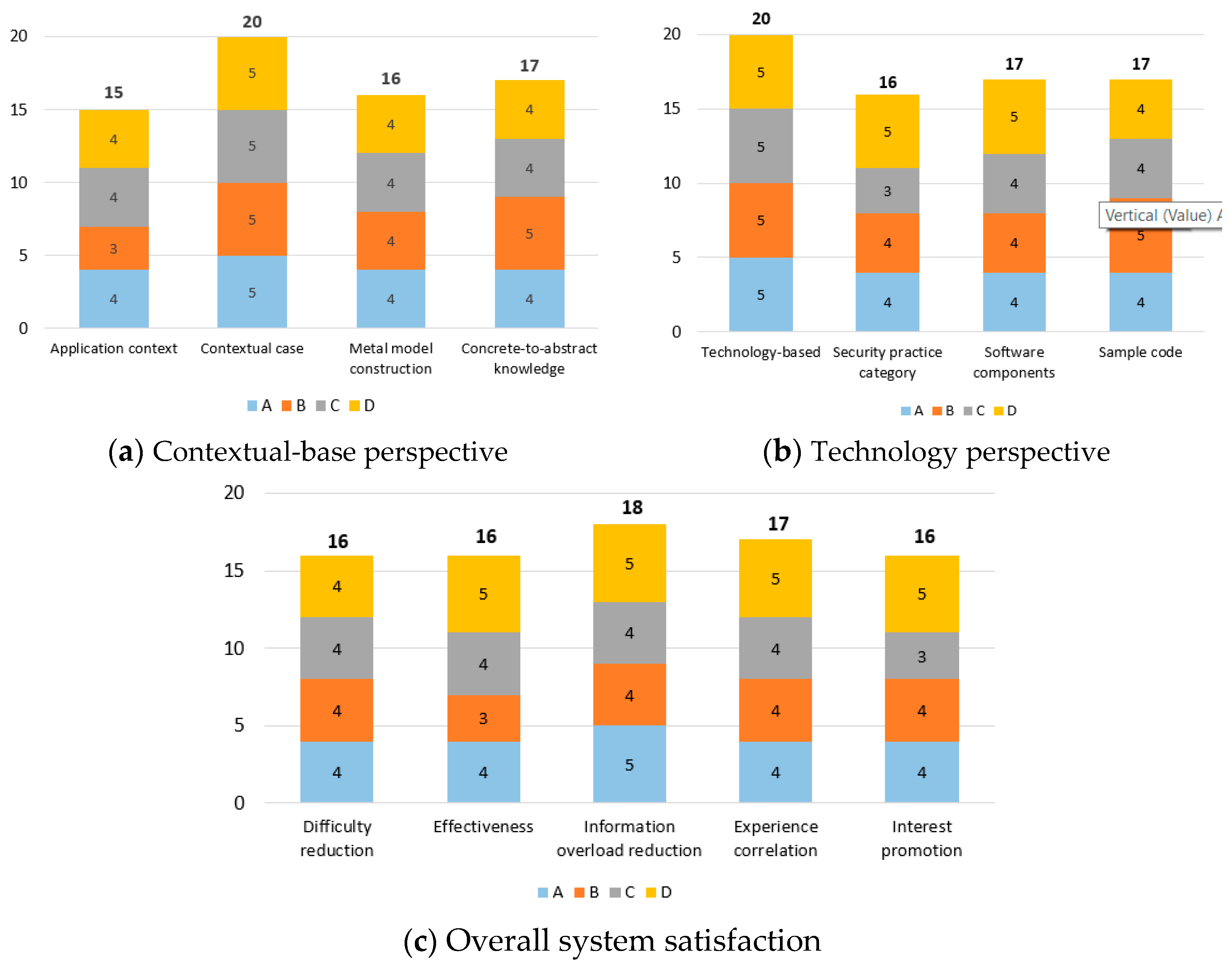
- Contextual case perspective
- B.
- Technology perspective
- C.
- Demonstration and evaluation
“This is a good design where people can learn things from real-world cases. Secure programming is something that you will have to understand and experience a lot. If it comes to learning it from real-time examples, then it’s very easy as you can understand things from your perspective.”
“We [developers] learned some surface features of security principles and concepts of how we were taught in the school. In works, however, we need to have enough experience to understand its application. It is very important to provide such learning experiences that can help us solve security problems in different contexts.”
“I appreciate how it connects software behavior with relevant security information—it’s excellent for learning.”
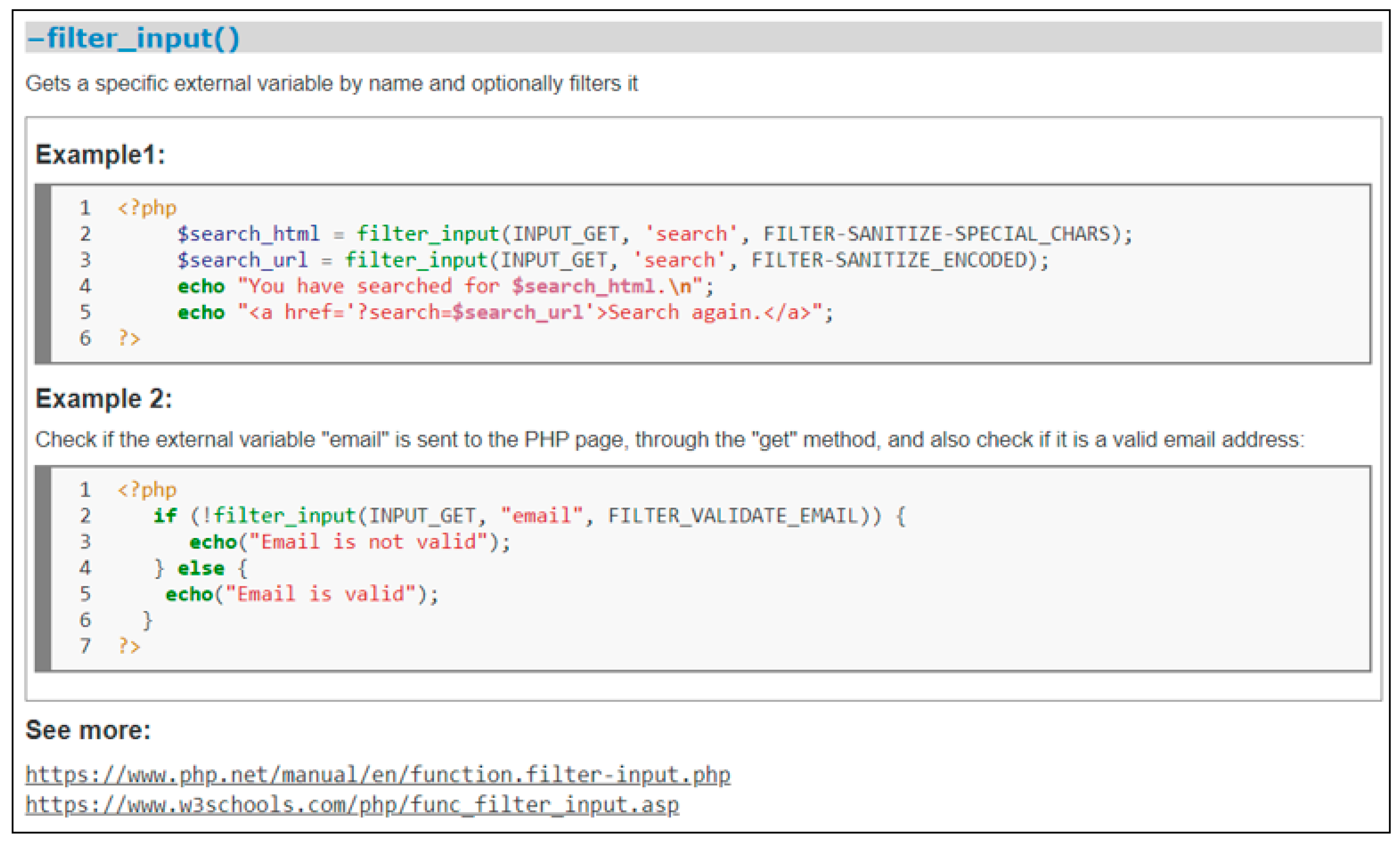
“When it comes to complex coding solutions, they are more easily comprehended when the solution is presented with accompanying example code. It’s an easier way for readers to understand how something works in comparison to reading long paragraphs of explanation.”
“I found it easier to understand the information when it was presented in a step-by-step, concrete manner.”
“I liked how the presenter used analogies and comparisons to help us understand the importance of security measures.”
“The design of putting [programming] language and the [secure] coding practices together servers one-stop learning for me.”
“I prefer to understand [software] security by studying the given practices of the programming language. Especially nowadays, we developers, commonly use libraries or functions for daily tasks. Knowing the security knowledge from the technology side is straightforward and very efficient.”
“The short snippets of source code and organization of the content made it easily digestible.”
“The way of interaction is relatively simple: the designed frames lead to sufficient visual space. Users do not need to swap between different pages.”
“Easy to use. Good information. Good readability and layout.”
5. Discussion
6. Threats to Validity
7. Conclusions
7.1. Future Research Opportunities
7.1.1. The Context-Based Learning Approach
7.1.2. The Contextualized Learning System
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Stack Overflow. Developer Survey. 2021. Available online: https://insights.stackoverflow.com/survey/2021 (accessed on 2 November 2022).
- Veracode; DevOps.com. DevSecOps Global Skills Survey. 2017. Available online: https://info.veracode.com/analyst-report-devsecops-global-skill-survey.html (accessed on 2 November 2012).
- Larabel, M. The Linux Kernel Has Grown by 225k Lines of Code So Far This Year from 3.3k Developers. 2018. Available online: https://www.phoronix.com/scan.php?page=news_item&px=Linux-September-2018-Stats (accessed on 4 November 2020).
- Agrawal, A.; Rahman, A.; Krishna, R.; Sobran, A.; Menzies, T. We Don’t Need Another Hero? The Impact of ”Heroes” on Software Development. arXiv 2017, arXiv:1710.09055. [Google Scholar]
- Young, A. Too Much Information: Ineffective Intelligence Collection. 2013. Available online: https://hir.harvard.edu/too-much-information/ (accessed on 13 October 2012).
- Hoq, K.M.G. Information overload: Causes, consequences and remedies-A study. Philos. Prog. 2014, 55–56, 49–68. [Google Scholar] [CrossRef]
- Murayama, K.; Blake, A.B.; Kerr, T.; Castel, A.D. When enough is not enough: Information overload and metacognitive decisions to stop studying information. J. Exp. Psychol. Learn. Mem. Cogn. 2016, 42, 914. [Google Scholar] [CrossRef]
- Ryoo, J.; Techatassanasoontorn, A.; Lee, D. Security education using second life. IEEE Secur. Priv. 2009, 7, 71–74. [Google Scholar] [CrossRef]
- Apvrille, A.; Pourzandi, M. Secure software development by example. IEEE Secur. Priv. 2005, 3, 10–17. [Google Scholar] [CrossRef]
- Fenstermacher, G.D.; Richardson, V. On making determinations of quality in teaching. Teach. Coll. Rec. 2005, 107, 186–213. [Google Scholar] [CrossRef]
- Land, S.; Jonassen, D. Theoretical Foundations of Learning Environments; Routledge: London, UK, 2012. [Google Scholar]
- Cooper, S.; Cunningham, S. Teaching computer science in context. ACM Inroads 2010, 1, 5–8. [Google Scholar] [CrossRef]
- Ko, A.J.; Myers, B.A. Debugging reinvented: Asking and answering why and why not questions about program behavior. In Proceedings of the 30th International Conference on Software Engineering, Leipzig, Germany, 10–18 May 2008; ACM: New York, NY, USA, 2008; pp. 301–310. [Google Scholar]
- Gruber, T.R. Toward principles for the design of ontologies used for knowledge sharing? Int. J. Hum.-Comput. Stud. 1995, 43, 907–928. [Google Scholar] [CrossRef]
- McGraw, G. Software Security: Building Security In; Addison-Wesley Professional: Boston, MA, USA, 2006. [Google Scholar]
- Dey, A.K. Understanding and using context. Pers. Ubiquitous Comput. 2001, 5, 4–7. [Google Scholar] [CrossRef]
- Brézillon, P. Modeling and using context: Past, present and future. In Rapport de Recherche Interne LIP6; University of Paris: Paris, France, 2002. [Google Scholar]
- Brézillon, P.; Araujo, R. Reinforcing shared context to improve collaboration. Rev. Sci. Technol. Inf.-Série RIA Rev. Intell. Artif. 2005, 19, 537–556. [Google Scholar] [CrossRef]
- Ackerman, M.S. Definitional and contextual issues in organizational and group memories. Inf. Technol. People 1996, 9, 10–24. [Google Scholar] [CrossRef]
- National Research Council. Evaluating and improving undergraduate teaching. In Science, Technology, Engineering, and Mathematics; National Academies Press: Washington, DC, USA, 2003. [Google Scholar]
- Brézillon, P. Making context explicit in communicating objects. In Communicating with Smart Objects: Developing Technology for Usable Pervasive Computing Systems; Kogan Page: London, UK, 2003. [Google Scholar]
- Brézillon, P. Context in problem solving: A survey. Knowl. Eng. Rev. 1999, 14, 47–80. [Google Scholar] [CrossRef]
- Perin, D. Facilitating student learning through contextualization: A review of evidence. Community Coll. Rev. 2011, 39, 268–295. [Google Scholar] [CrossRef]
- Predmore, S.R. Putting it into Context. Tech. Connect. Educ. Careers 2005, 80, 22–25. [Google Scholar]
- National Research Council. How People Learn: Brain, Mind, Experience, and School: Expanded Edition; National Academies Press: Washington, DC, USA, 2000. [Google Scholar]
- Bennett, J.; Lubben, F.; Hogarth, S. Bringing science to life: A synthesis of the research evidence on the effects of context-based and STS approaches to science teaching. Sci. Educ. 2007, 91, 347–370. [Google Scholar] [CrossRef]
- Gilbert, J.K. On the nature of “context” in chemical education. Int. J. Sci. Educ. 2006, 28, 957–976. [Google Scholar] [CrossRef]
- Shrivastav, H.; Hiltz, S.R. Information overload in technology-based education: A meta-analysis. In Proceedings of the Nineteenth Americas Conference on Information Systems, Chicago, IL, USA, 15–17 August 2013. [Google Scholar]
- Millar, R. Beyond 2000: Science Education for the Future; Nuffield Foundation: London, UK, 1998. [Google Scholar]
- Nentwig, P.; Waddington, D. Making It Relevant: Context Based Learning of Science; Waxmann Verlag: Münster, Germany, 2006. [Google Scholar]
- Hazeyama, A.; Shimizu, H. A learning environment for software security education. In Proceedings of the 2011 Fifth International Conference on Secure Software Integration and Reliability Improvement-Companion, Jeju Island, Republic of Korea, 27–29 June; IEEE: Piscataway, NJ, USA, 2011; pp. 7–8. [Google Scholar]
- Hazeyama, A.; Shimizu, H. Development of a Software Security Learning Environment. In Proceedings of the 2012 13th ACIS International Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing, Kyoto, Japan, 8–10 August 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 518–523. [Google Scholar]
- Whitney, M.; Lipford-Richter, H.; Chu, B.; Zhu, J. Embedding secure coding instruction into the IDE: A field study in an advanced CS course. In Proceedings of the 46th ACM Technical Symposium on Computer Science Education, Kansas City, MO, USA, 4–7 March 2015; ACM: New York, NY, USA, 2015; pp. 60–65. [Google Scholar]
- Zhu, J.; Lipford, H.R.; Chu, B. Interactive support for secure programming education. In Proceedings of the 44th ACM Technical Symposium on Computer Science Education, Denver, CO, USA, 6 March 2013; ACM: New York, NY, USA, 2013; pp. 687–692. [Google Scholar]
- Schweitzer, D.; Brown, W. Using visualization to teach security. J. Comput. Sci. Coll. 2009, 24, 143–150. [Google Scholar]
- Yuan, X.; Vega, P.; Qadah, Y.; Archer, R.; Yu, H.; Xu, J. Visualization tools for teaching computer security. ACM Trans. Comput. Educ. TOCE 2010, 9, 20. [Google Scholar] [CrossRef]
- Bishop, M.; Dai, J.; Dark, M.; Ngambeki, I.; Nico, P.; Zhu, M. Evaluating secure programming knowledge. In Proceedings of the IFIP World Conference on Information Security Education, Rome, Italy, 29–31 May 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 51–62. [Google Scholar]
- Irvine, C.E.; Thompson, M.F.; Allen, K. CyberCIEGE: Gaming for information assurance. IEEE Secur. Priv. 2005, 3, 61–64. [Google Scholar] [CrossRef]
- Nerbråten, Ø.; Røstad, L. Hacmegame: A tool for teaching software security. In Proceedings of the 2009 International Conference on Availability, Reliability and Security, Jukuoka, Japan, 16–19 March 2009; IEEE: Piscataway, NJ, USA, 2009; pp. 811–816. [Google Scholar]
- Peffers, K.; Tuunanen, T.; Niehaves, B. Design Science Research Genres: Introduction to the Special Issue on Exemplars and Criteria for Applicable Design Science Research; Taylor & Francis: Abingdon, UK, 2018. [Google Scholar]
- Winter, R. Design science research in Europe. Eur. J. Inf. Syst. 2008, 17, 470–475. [Google Scholar] [CrossRef]
- Peffers, K.; Tuunanen, T.; Rothenberger, M.A.; Chatterjee, S. A design science research methodology for information systems research. J. Manag. Inf. Syst. 2007, 24, 45–77. [Google Scholar] [CrossRef]
- Kuechler, W.; Vaishnavi, V.K.; Petter, S. The aggregate general design cycle as a perspective on the evolution of computing communities of interest. In Design Science Research Methods and Patterns; Auerbach Publications: Boca Raton, FL, USA, 2007. [Google Scholar]
- Hevner, A.R.; March, S.T.; Park, J.; Ram, S. Design science in information systems research. MIS Q. 2004, 28, 75–105. [Google Scholar] [CrossRef]
- Rivet, A.E.; Krajcik, J.S. Contextualizing instruction: Leveraging students’ prior knowledge and experiences to foster understanding of middle school science. J. Res. Sci. Teach. Off. J. Natl. Assoc. Res. Sci. Teach. 2008, 45, 79–100. [Google Scholar] [CrossRef]
- Kamina, P.; Iyer, N.N. From concrete to abstract: Teaching for transfer of learning when using manipulatives. In Proceedings of the Northeastern Educational Research Association (NERA), Rocky Hill, CT, USA, 21–23 October 2009. [Google Scholar]
- Johannesson, P.; Perjons, E. An Introduction to Design Science; Springer: Berlin/Heidelberg, Germany, 2014. [Google Scholar]
- Wand, Y.; Storey, V.C.; Weber, R. An ontological analysis of the relationship construct in conceptual modeling. ACM Trans. Database Syst. TODS 1999, 24, 494–528. [Google Scholar] [CrossRef]
- Tudorache, T.; Nyulas, C.; Noy, N.F.; Musen, M.A. WebProtégé: A collaborative ontology editor and knowledge acquisition tool for the web. Semant. Web 2013, 4, 89–99. [Google Scholar] [CrossRef] [PubMed]
- Wen, S.-F.; Katt, B. Managing Software Security Knowledge in Context: An Ontology Based Approach. Information 2019, 10, 216. [Google Scholar] [CrossRef]
- W3C. SPARQL 1.1 Query Language. 2013. Available online: https://www.w3.org/TR/sparql11-query/ (accessed on 3 June 2022).
- Brank, J.; Grobelnik, M.; Mladenic, D. A survey of ontology evaluation techniques. In Proceedings of the Conference on Data Mining and Data Warehouses (SiKDD 2005), Ljubljana, Slovenia, 17 October 2005; pp. 166–170. [Google Scholar]
- Hlomani, H.; Stacey, D. Approaches, methods, metrics, measures, and subjectivity in ontology evaluation: A survey. Semant. Web J. 2014, 1, 1–11. [Google Scholar]
- NorthBridge, BlackDuck. 2016 Future of Open Source Survey. 2016. Available online: http://www.slideshare.net/blackducksoftware/2016-future-of-open-source-survey-results (accessed on 23 November 2022).
- BlackDuck Software. 2017 Open Source Security and Risk Analysis. 2017. Available online: https://www.gcomtw.com/mailshot/Synopsys/2002BlackDuck/repossra19.pdf (accessed on 13 September 2018).
- Snyk. The State of Open Source Security—2019. 2019. Available online: https://snyk.io/opensourcesecurity-2019/ (accessed on 2 November 2022).
- Numally, J.C. Psychometric Theory; McGraw-Hill: New York, NY, USA, 1978. [Google Scholar]
- Seel, N.M.; Al-Diban, S.; Blumschein, P. Mental Models & Instructional Planning. In Integrated and Holistic Perspectives on Learning, Instruction and Technology; Springer: Berlin/Heidelberg, Germany, 2000. [Google Scholar]
- Turpin, K. OWASP Secure Coding Practices-Quick Reference Guide. 2010. Available online: https://owasp.org/www-project-secure-coding-practices-quick-reference-guide/ (accessed on 3 November 2022).
- Nasehi, S.M.; Sillito, J.; Maurer, F.; Burns, C. What makes a good code example?: A study of programming Q&A in StackOverflow. In Proceedings of the 2012 28th IEEE International Conference on Software Maintenance (ICSM), Trento, Italy, 23–28 September 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 25–34. [Google Scholar]
- Wen, S.-F. Learning secure programming in open source software communities: A socio-technical view. In Proceedings of the 6th International Conference on Information and Education Technology, Osaka, Japan, 6–8 January 2018; ACM: New York, NY, USA, 2018; pp. 25–32. [Google Scholar]
- Nunamaker, J.F., Jr.; Briggs, R.O. Toward a broader vision for information systems. ACM Trans. Manag. Inf. Syst. TMIS 2011, 2, 20. [Google Scholar] [CrossRef]
- Bider, I.; Kowalski, S. A framework for synchronizing human behavior, processes and support systems using a socio-technical approach. In Enterprise, Business-Process and Information Systems Modeling; Springer: Berlin/Heidelberg, Germany, 2014. [Google Scholar]
- Kowalski, S. IT Insecurity: A Multi-Discipline Inquiry; Department of Computer and System Sciences, University of Stockholm and Royal Institute of Technology: Stockholm, Sweden, 1994. [Google Scholar]
- Al Sabbagh, B.; Kowalski, S. A socio-technical framework for threat modeling a software supply chain. In Proceedings of the 2013 Dewald Roode Workshop on Information Systems Security Research, Niagara Falls, NY, USA, 4–5 October 2013; International Federation for Information Processing: Laxenburg, Austria, 2013. [Google Scholar]



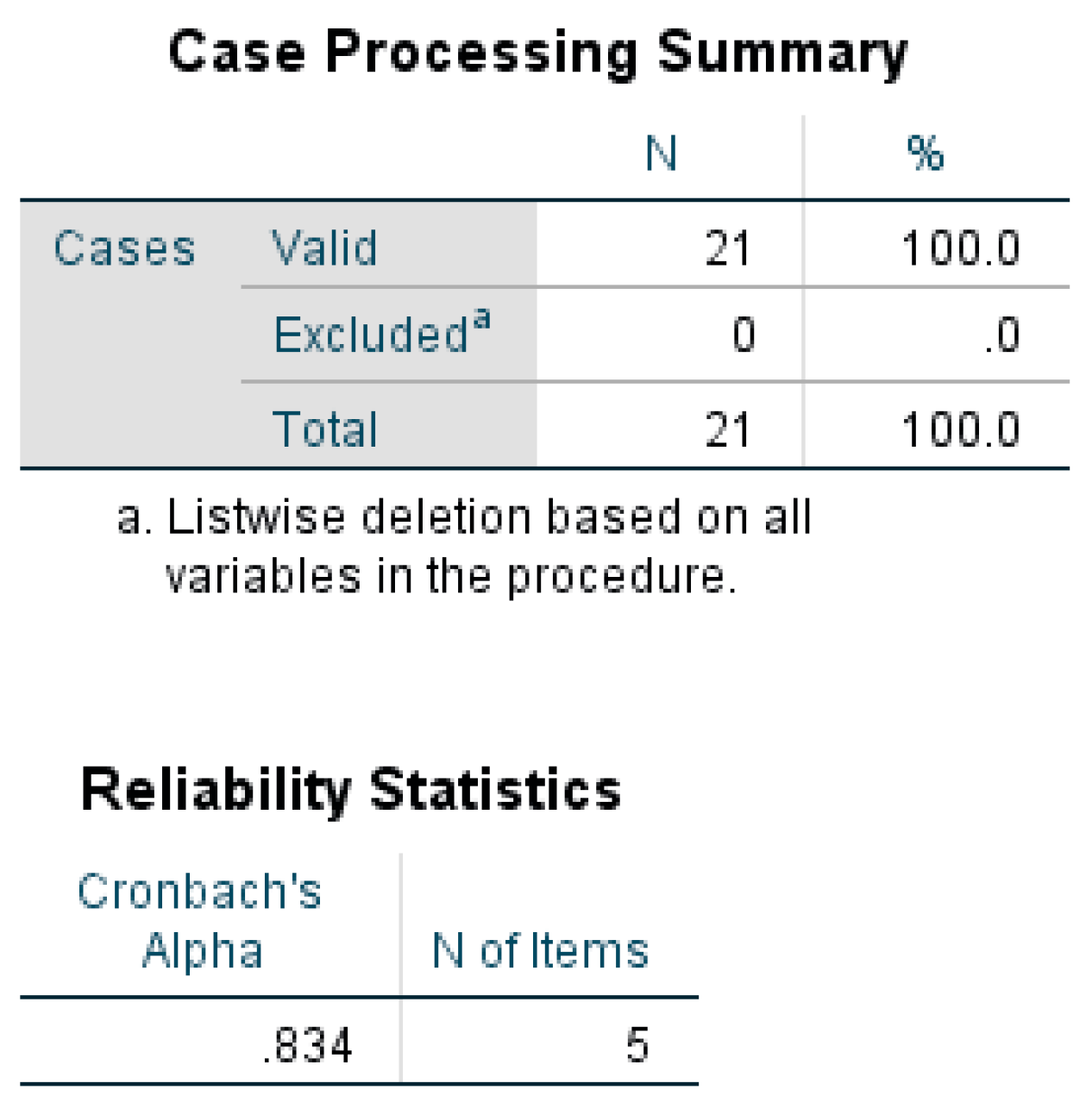



| Round | Group A | Group B | |||||
|---|---|---|---|---|---|---|---|
| N | Mean | SD | N | Mean | SD | ||
| 1 | Pre-test | 20 | 26.75 | 5.20 | 22 | 24.32 | 5.19 |
| Post-test | 20 | 29.50 | 6.90 | 22 | 33.86 | 4.86 | |
| Knowledge gain | 2.75 | 9.54 | |||||
| 2 | Pre-test | 20 | 21.75 | 8.78 | 22 | 20.00 | 9.26 |
| Post-test | 20 | 26.25 | 6.90 | 22 | 30.91 | 8.54 | |
| Knowledge gain | 4.50 | 10.91 | |||||
| Levine’s Test | t-Test | ||||||||
|---|---|---|---|---|---|---|---|---|---|
| F | Sig. | t | df | Sig. (2-Tailed) | Mean Difference | Std. Error Difference | |||
| Pre-Test | 1st round | Equal variances assumed | 0.238 | 0.628 | 1.516 | 40 | 0.137 | 2.432 | 1.604 |
| Equal variances not assumed | 1.516 | 39.601 | 0.138 | 2.432 | 1.605 | ||||
| 2nd round | Equal variances assumed | 0.012 | 0.913 | 0.627 | 40 | 0.534 | 1.750 | 2.791 | |
| Equal variances not assumed | 0.629 | 39.921 | 0.533 | 1.750 | 2.784 | ||||
| Mean | Std. Deviation | ||
|---|---|---|---|
| Control Group | Pre-Test | 30.00 | 11.757 |
| Post-Test | 40.28 | 9.922 | |
| Knowledge Gain | 10.28 | ||
| Experimental Group | Pre-Test | 30.83 | 11.789 |
| Post-Test | 46.94 | 7.503 | |
| Knowledge Gain | 16.11 | ||
| Category | Question | Mean |
|---|---|---|
| System Operation | I agree that the applied learning technique in the system is novel and it can assist my learning. | 4.11 |
| I am very clear about the learning procedure embedded in the system. | 4.00 | |
| The system organizes security knowledge in a structured and collected manner. | 4.21 | |
| The knowledge content provided by the system is easy to understand. | 4.00 | |
| I think that the system is useful for learning security knowledge. | 4.05 | |
| Average | 4.07 | |
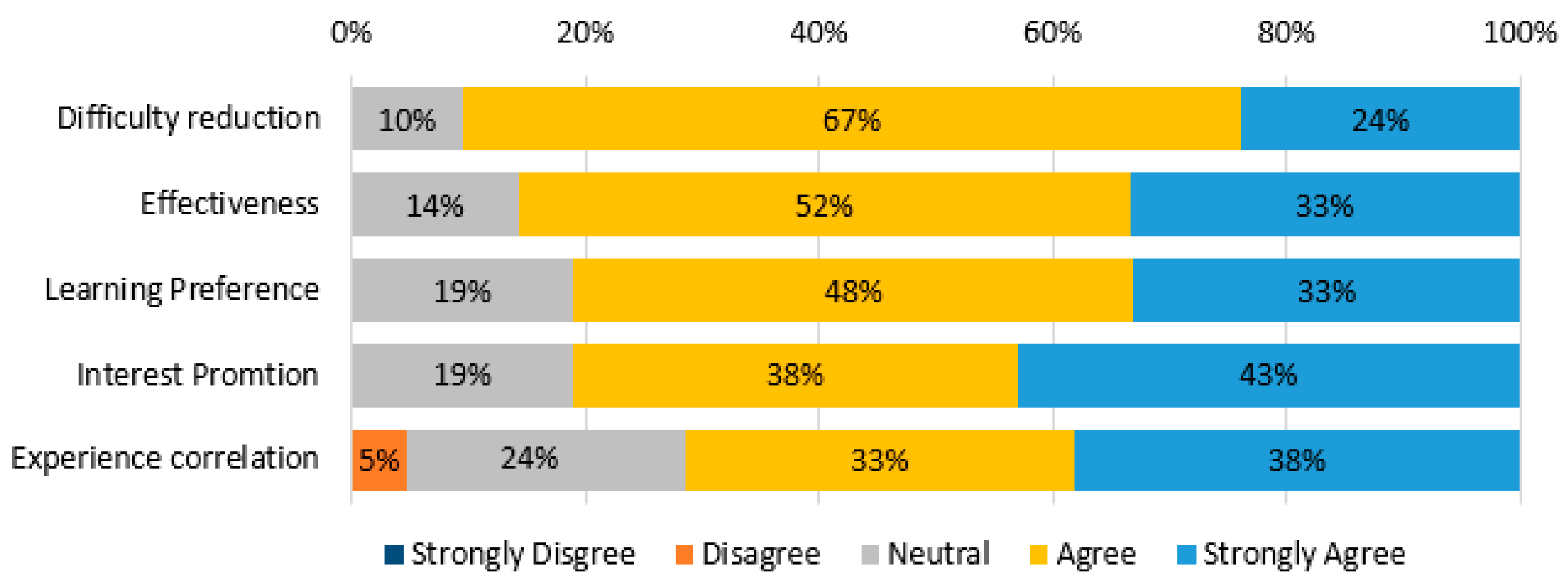
| Learning Attitude | The system helps me deepen the memorized impression of the learning subject. | 4.11 |
| The system helps me relate security knowledge to what I knew or experienced before. | 4.16 | |
| The system reduces the difficulty of learning secure programming. | 4.11 | |
| I find that at times studying the learning materials gives me a feeling of personal satisfaction. | 4.05 | |
| The system helps me foster a positive attitude toward learning security knowledge. | 4.00 | |
| Average | 4.09 |
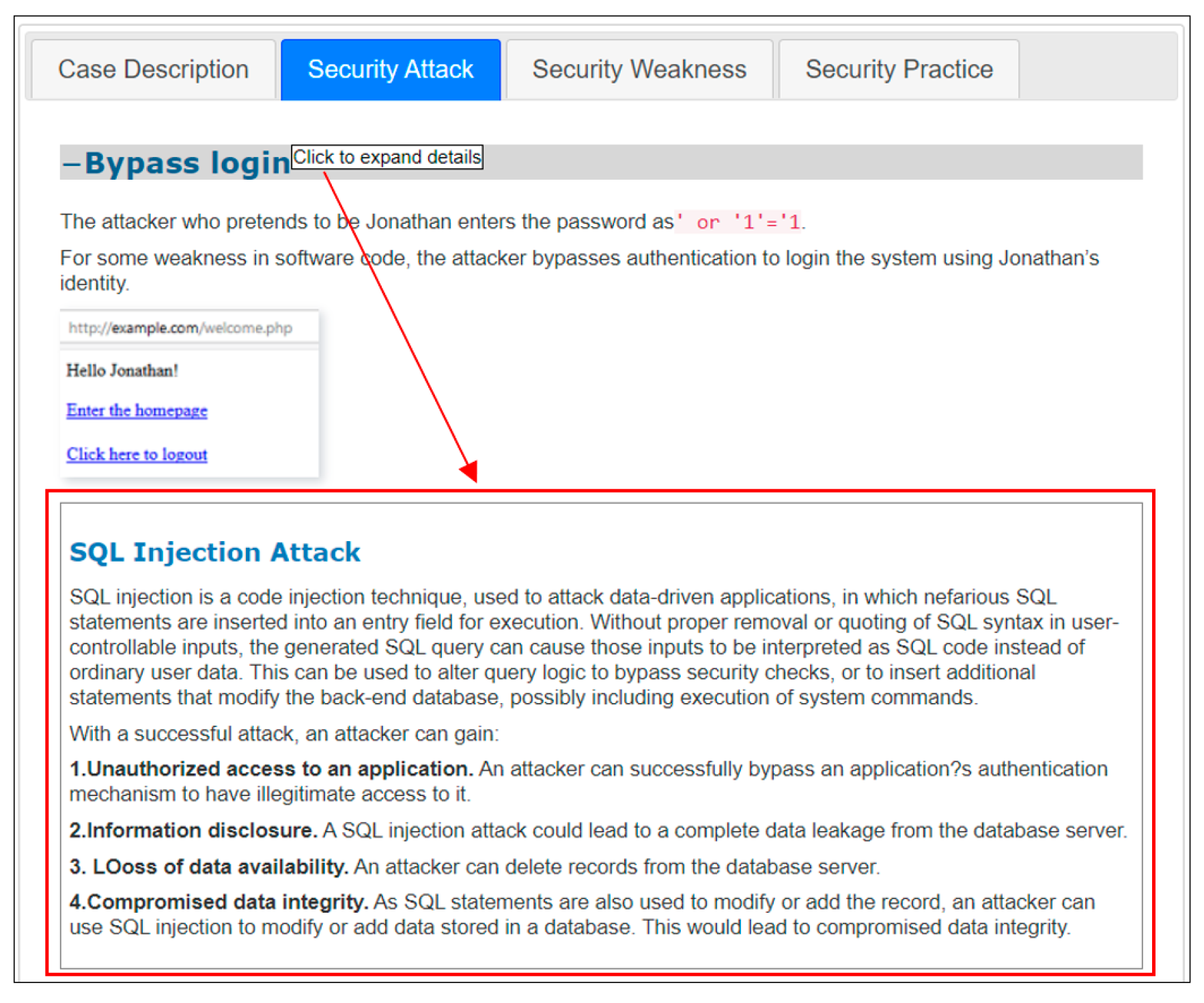
| Functionality | Case | Security Attack |
|---|---|---|
| Generate HTML using users supplied data | User Registration | Cross-site scripting |
| Bulletin board | Cross-site scripting | |
| Functions with users’ credentials | Change password | Cross-site request forgery |
| Update Profile | Cross-site request forgery | |
| Access database using user-supplied data | User login | SQL injection |
| Search email | SQL injection | |
| Include external files in HTML | Switch displayed language | Remote file inclusion |
| File operation | List documents | Directory traversal |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wen, S.-F. Context-Based Support to Enhance Developers’ Learning of Software Security. Educ. Sci. 2023, 13, 631. https://doi.org/10.3390/educsci13070631
Wen S-F. Context-Based Support to Enhance Developers’ Learning of Software Security. Education Sciences. 2023; 13(7):631. https://doi.org/10.3390/educsci13070631
Chicago/Turabian StyleWen, Shao-Fang. 2023. "Context-Based Support to Enhance Developers’ Learning of Software Security" Education Sciences 13, no. 7: 631. https://doi.org/10.3390/educsci13070631
APA StyleWen, S.-F. (2023). Context-Based Support to Enhance Developers’ Learning of Software Security. Education Sciences, 13(7), 631. https://doi.org/10.3390/educsci13070631








