Abstract
Advancements in electronics and sensor technologies are driving the deployment of ubiquitous sensor networks across various applications, including asset monitoring, security, and networking. At the same time, ensuring the integrity and confidentiality of data collected by sensor nodes is crucial to prevent unauthorized access or modification. However, the limited resources f low-power sensor networks present significant challenges for securing innovative Internet-of-Medical Things (IoMT) applications in complex environments. These miniature sensing systems, essential for diverse healthcare applications, grapple with constrained computational power and energy budgets. To address this challenge, this study proposes a dynamic power management strategy within a resource-constrained FPGA-based cryptoprocessor core for secure IoMT networks. The sensor node design comprises two main modules: an 8-bit reduced instruction set computer (RISC) and a cryptographic engine. These modules collaboratively manage their power consumption during the operational stages of data acquisition, encryption, transmission, and sleep mode activation. The cryptographic engine employs a pseudorandom number generator to generate a keystream for data encryption, utilizing direct sequence spread spectrum (DSSS) encoding to ensure secure communication. The experimental results demonstrate the effectiveness of the proposed dynamic power management strategy within the resource-constrained cryptoprocessor core. The sensor node achieves an average power consumption of 0.1 mW while utilizing 2414 logic cells and 5292 registers. A comparative analysis with other state-of-the-art lightweight sensor nodes highlights the advantages of our dynamic power management approach within the cryptoprocessor sensing system.
1. Introduction
The growing interest in Internet-of-Medical Things (IoMT) systems is driving the development of next-generation wireless sensor networks (WSNs) for diverse applications. These applications demand robust security features, along with advancements in electronics, to protect sensitive patient data and ensure the integrity of network operations. Typically, sensor networks consist of low-power, miniature devices used across diverse healthcare domains, including precision medicine [1,2], disease prediction [3], cardiovascular care [4], patient monitoring [5,6], and smart wearable technology [7,8]. However, these sensing systems often face resource and energy constraints, limiting their capabilities for data processing, security, and communication. The necessity of continuous data collection also consumes substantial energy, which significantly restricts the device’s operational time, compromising its effectiveness. These constraints can pose challenges in ensuring the reliability, operability and integrity of the IoMT network.
While some security features, such as data origin authentication and integrity, are included in these networks [9,10,11], many sensing devices remain vulnerable [12] and susceptible to jamming during data transmission [13,14,15]. To address this challenge, recent studies have proposed integrating cryptographic engines as co-processor units [16,17,18,19,20] or lightweight cryptographic systems [21,22]. Cryptographic engines have become essential components in various applications, from secure communication to data protection. As a co-processor unit, they offload cryptographic operations from the main processor, enhancing performance and security. On the other hand, lightweight cryptographic systems are designed to be suitable for resource-constrained devices, such as those found in IoT, embedded systems, and wireless sensor networks. In [9], an ASIC design for an authenticated encryption with associated data (AEAD) cryptosystem was tested against IoT threats. The implementation results were 4744 logic gates and 0.87 mW of average power consumption for a uniform power management strategy. An FPGA-based chaos pseudorandom number generator was integrated into a resource-constrained cryptographic processor in [13]. Despite the lack of a developed power management strategy, an estimated power consumption of 7.8 mW was reported. A reconfigurable elliptic curve cryptographic accelerator on a 65nm CMOS chip, paired with a reduced instruction set computer (RISC)-V processor, was implemented in [16]. The test chip demonstrates hardware-accelerated transmissions while consuming 44.08 J/handshake at 0.8 V. Additionally, a post-quantum cryptoprocessor was designed and integrated into an RISC-V FPGA-based architecture in [17]. Following a uniform power management strategy, the average power consumption was 5.4 mW. An FPGA implementation of a ring oscillator pseudorandom number generator was combined with an SHA-3 cryptographic engine and an IP processor core in [18]. With a uniform sleep rate, the estimated power consumption was 38 mW. The Advanced Encryption Standard (AES) algorithm was also implemented on the physical layer for long-range (LoRa) networks [19]. In [20], a lightweight 32-bit cryptography block cipher was designed for RFID systems. The architecture uses a long key length of 80 bits to avoid exhaustive key searches and four substitution boxes to determine how ciphertext statistics depend on plaintext statistics. The reported power consumption in a healthcare IoT framework was 10.7 mW. Another study in [23] proposes a 64-bit lightweight block cipher named IVLBC, whose key allows for 80 and 128 bits. The components of IVLBC include a Feistel cipher with a tree structure that obtains a compact and involutive S-box. As SLIM and IVLBC have constrained resource areas, a dynamic power management strategy needs to be implemented for their implementation in wireless sensor networks and IoT applications.
Authenticated encryption ciphers and stream ciphers were also studied using the cube attack technique in [24]. A method to identify good cubes was introduced based on the greedy algorithm in combination with a numerical mapping method for estimating the algebraic degree of a cryptosystem. In [25], a complexity-reduced secure and fast encryption routine (SAFER)-based Fermat block encryption method was proposed. This study introduces a diffusion layer that exploits Fermat’s number theory, while the confusion layer remains unchanged. A novel data encryption technique suitable for Internet of Things (IoT) applications is proposed in [26]. The cryptosystem uses a Catalan object as a cryptographic key, providing a combinatorial structure with noncrossing or nonnested matching with the Catalan numbers and data encryption standard (DES) algorithm, which is performed with machine learning-based identification of the encryption method using ciphertext only. Moreover, a key derivation function based on the Chinese Remainder Theorem (CRT) was employed to derive encryption keys from other secure mechanisms.
In [21], a lightweight cryptographic neural network inference system was developed for resource-constrained devices like a Raspberry Pi, with its performance being evaluated using medical datasets. This architecture utilizes a distributed system with two separate edge services that securely perform neural network inference on encoded user data and models, preventing unauthorized access or disclosure. The Paillier cryptosystem, as proposed in [22], presents a promising approach to securing a model-predictive control (MPC) framework, aiming to mitigate risks from cyberattacks that threaten security and information privacy. However, while these studies represent cutting-edge cryptoprocessing systems, they still lack a fully integrated dynamic power management approach within an RISC processor. This is crucial for optimizing power consumption and resource utilization in low-power, resource-constrained IoMT devices.
This work addresses the challenge of implementing a dynamic power management strategy (DPMS) in a low-power, resource-constrained architecture to secure on-device IoMT applications. Specifically, it investigates the performance of a DPMS integrated into a cryptoprocessor in terms of area and power consumption. To achieve this, an 8-bit RISC processor with a direct sequence spread spectrum (DSSS) cryptographic engine was implemented in a Field Programmable Gate Array (FPGA). The DPMS adaptively adjusts the sleep period during data acquisition, encryption, transmission, and sleep modes in the constrained FPGA-based IoMT solution.
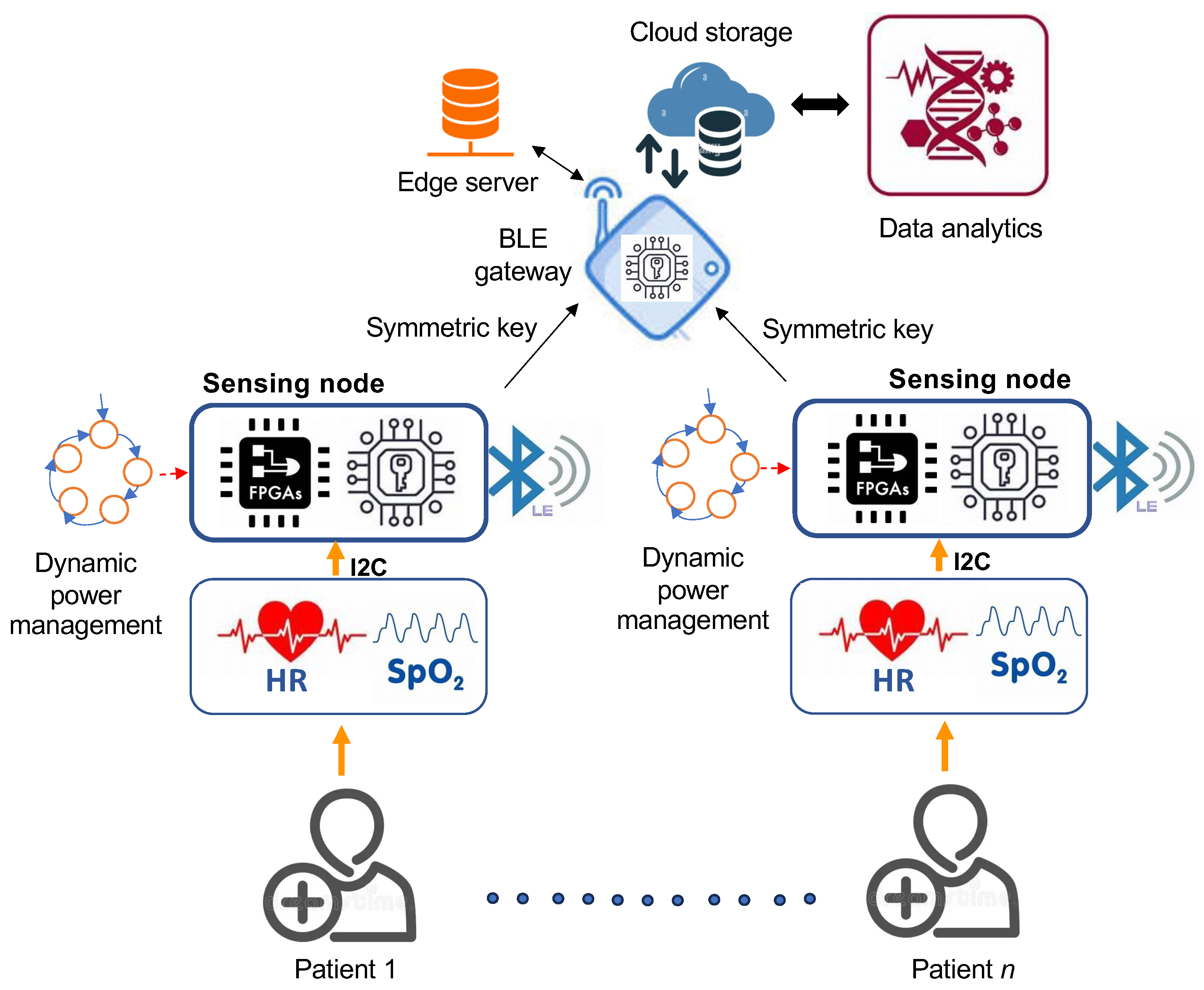
Figure 1 illustrates the conceptual framework of the proposed DPMS, featuring a proof-of-concept cryptoprocessor system for IoMT networks. The system integrates a dynamic power management strategy within an RISC cryptoprocessor built on the same FPGA architecture. This cryptoprocessor conducts data encryption, utilizing direct sequence spread spectrum encoding to ensure secure communication, mitigating typical attacks on WSNs, such as man-in-the-middle (MITM) attacks [27].
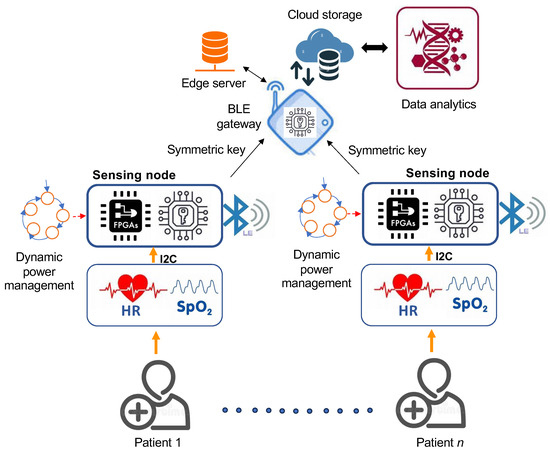
Figure 1.
Conceptual design of the proposed IoMT network for dynamic power management analysis on an FPGA-based cryptoprocessor core.
The main contributions of this paper are as follows:
- A novel dynamic power management strategy implemented in a resource-constrained RISC cryptoprocessor FPGA design for healthcare applications.
- A secure sensing node system utilizing DSSS encoding with an average power consumption of up to 0.1 mW.
- A resource-efficient design employing only 2414 logic cells and 5292 registers, implemented on an Intel 5CSEMA5F31C6N FPGA device.
This paper is structured as follows: Section 2 presents the resource-constrained design of the FPGA-based cryptoprocessor system, with a focus on the DSSS cipher engine. Section 3 details the dynamic power management methodology. Section 4 presents the experimental results for cryptographic performance, power consumption, and area–speed trade-offs. Finally, Section 5 and Section 6 provide the discussion and concluding remarks, respectively.
2. Resource-Constrained RISC Cryptoprocessor Design
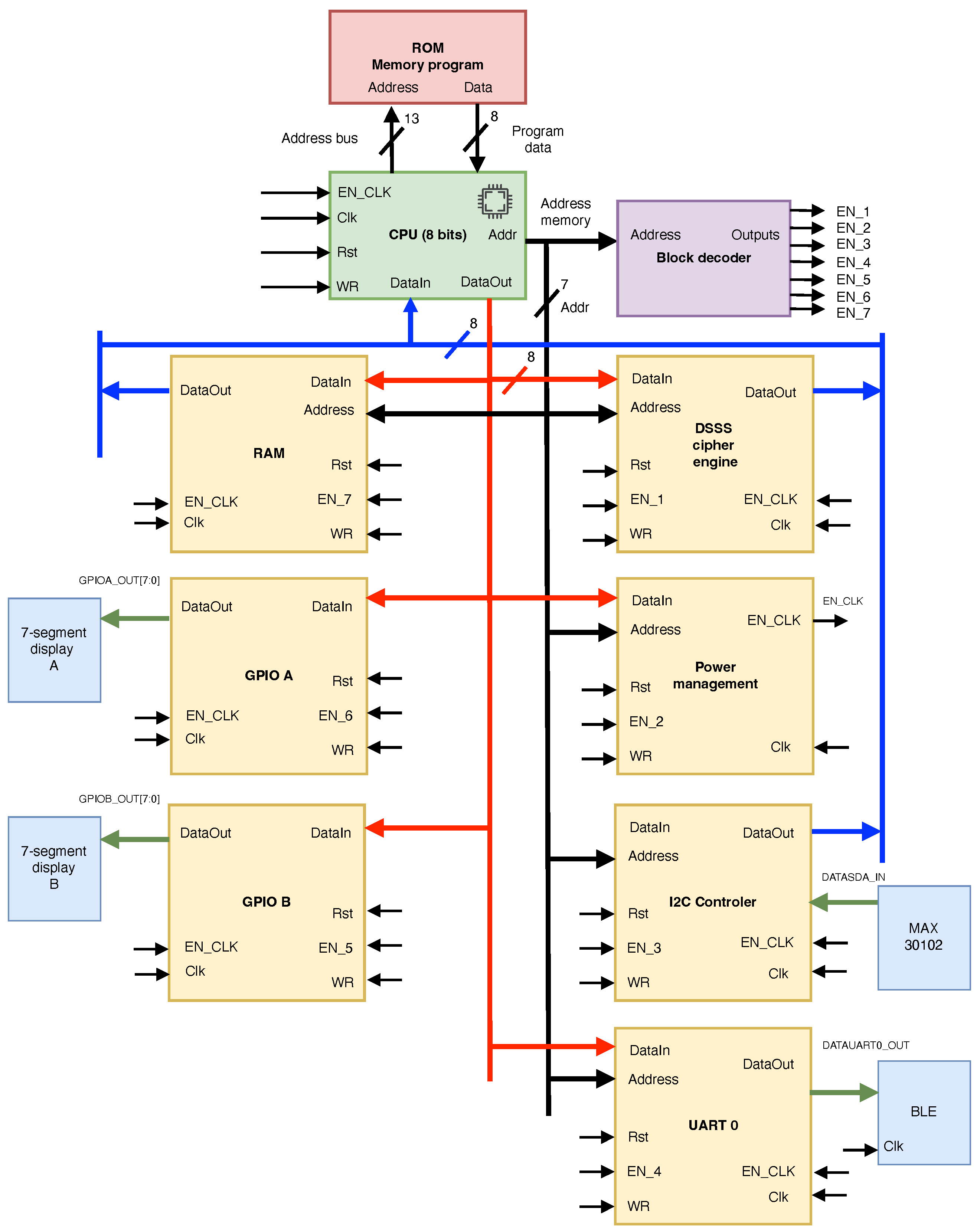
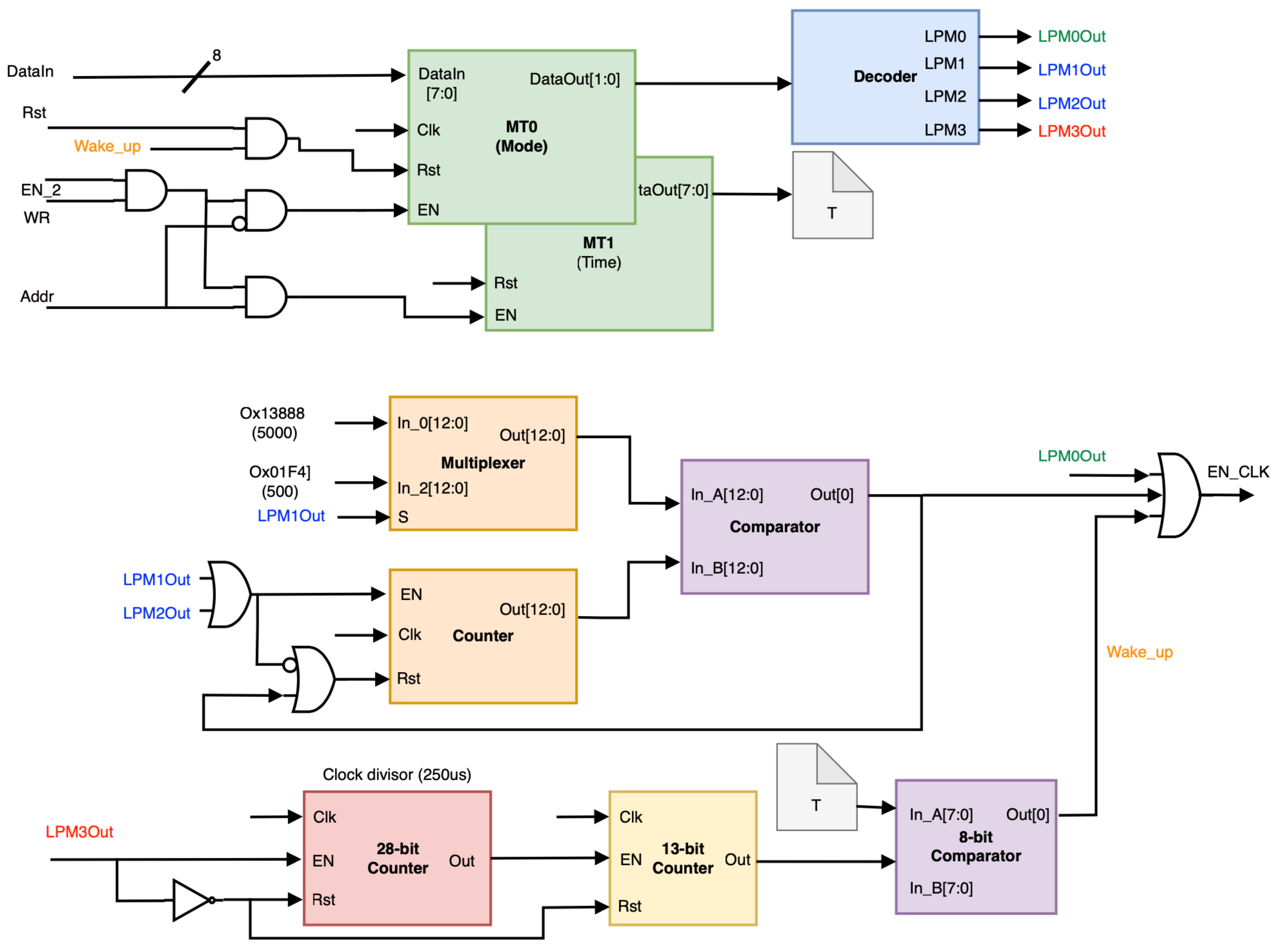
The development of a cryptoprocessor system for IoMT applications was driven by the current need for secure, resource-efficient, and reliable on-device data processing. Such a system must ensure data security, integrity, and timely delivery for accurate health monitoring and prognosis. Figure 2 presents the proposed FPGA-based cryptoprocessor core system block diagram, which includes the RISC processor as peripherals (yellow blocks), a DSSS cipher engine, a power management unit, a block RAM, two global input/output ports, and the communication controllers UART and I2C. A decoder block (in purple) is also used for scheduling and allocation control.
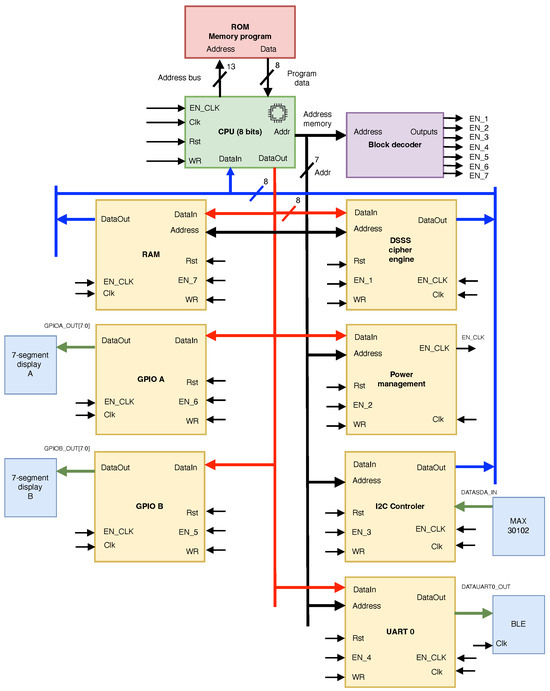
Figure 2.
Block diagram of the FPGA-based cryptoprocessor system.
2.1. FPGA-Based RISC Processor Design
The proposed architecture implements an RISC design that efficiently and securely executes cryptographic algorithms and security protocols. By leveraging the flexibility of FPGAs, the RISC processor can be customized to perform hardware cryptographic operations, enhancing security and performance. The 8-bit RISC processor design executes an instruction within a single clock cycle. It features a dynamic low-power mode, two general-purpose input/output peripherals, a universal asynchronous receiver/transmitter (UART) block, an Inter-Integrated Circuit (I2C) serial communication protocol, and a dedicated DSSS cipher engine. Due to its 128-byte RAM size, the RISC core can only access one 8-bit instruction at a time. Additionally, the processor incorporates an interrupt controller to efficiently handle interrupts from the cipher engine and peripherals. Interrupts can be tailored to specific events by enabling them individually and configuring their triggering mode (edge or level) in software. A custom software library manages the UART peripheral, facilitating data packet transmission to the Bluetooth low-energy (BLE) gateway.
2.2. DSSS Cipher Engine Peripheral Architecture
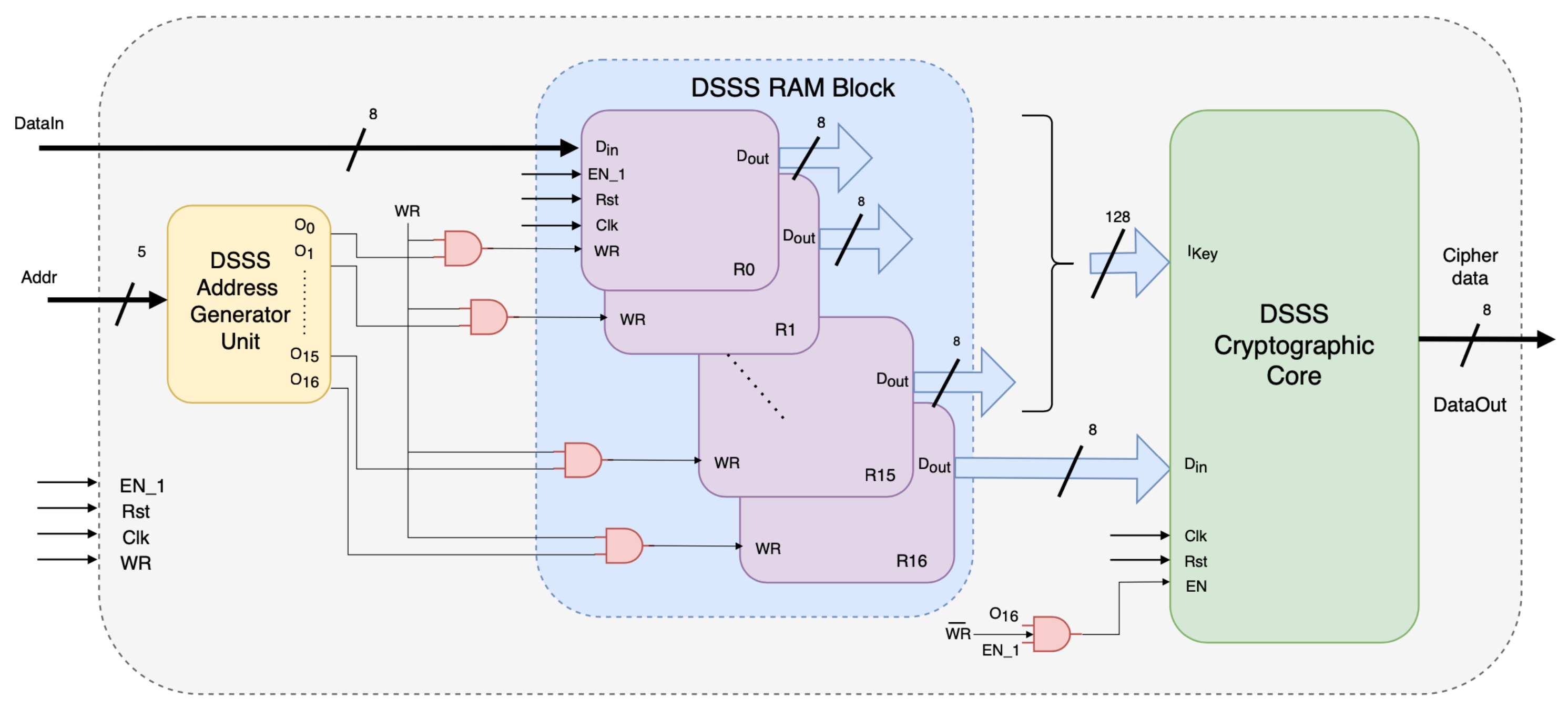
Figure 3 shows the DSSS cipher engine architecture. Three modules are addressed as follows: (a) DSSS address generator unit (DSSS-AGU), (b) DSSS RAM block, and (c) DSSS cryptographic core. The DSSS-AGU module stores the key, which can be programmed through the RISC processor. This module controls the writing operations of the DSSS RAM, ensuring a sequential or specific pattern for loading the key and incoming data.
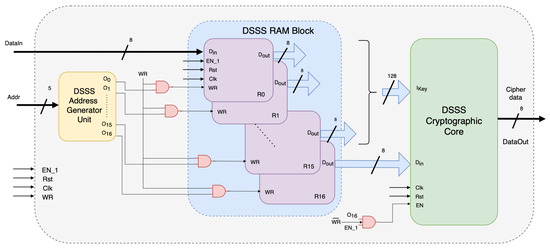
Figure 3.
Design of the DSSS cipher engine.
The DSSS cipher engine uses a spread-spectrum technique, spreading the transmitted data over a wider bandwidth than the original data. The DSSS is highly resistant to interference due to its low signal-to-noise ratio (SNR) and its ability to mitigate multipath fading, which occurs in wireless communication channels. In addition, the spreading factor of a DSSS system can be adjusted to meet different requirements for security, reliability, and bandwidth efficiency. At the receiver, the information bandwidth is restored after despreading, while unintentional interference is eliminated. That is, the message signal is modulated by a pseudorandom number (PN) sequence. Each element of the PN sequence, with a shorter duration than the original message symbols, scrambles and spreads the signal in the spectrum, resulting in a bandwidth determined by the bandwidth of the PN sequence. The smaller the chip duration (the duration of each element of the PN sequence), the larger the bandwidth of the resulting DSSS signal; more bandwidth multiplexed to the message signal results in better resistance against narrowband interference. The DSSS cipher engine employs a PN sequence to spread data bits. This sequence is generated by initializing the 8-bit registers of the DSSS RAM. The baseband operation involves XORing incoming data with the PN, effectively spreading the digital signal for transmission.
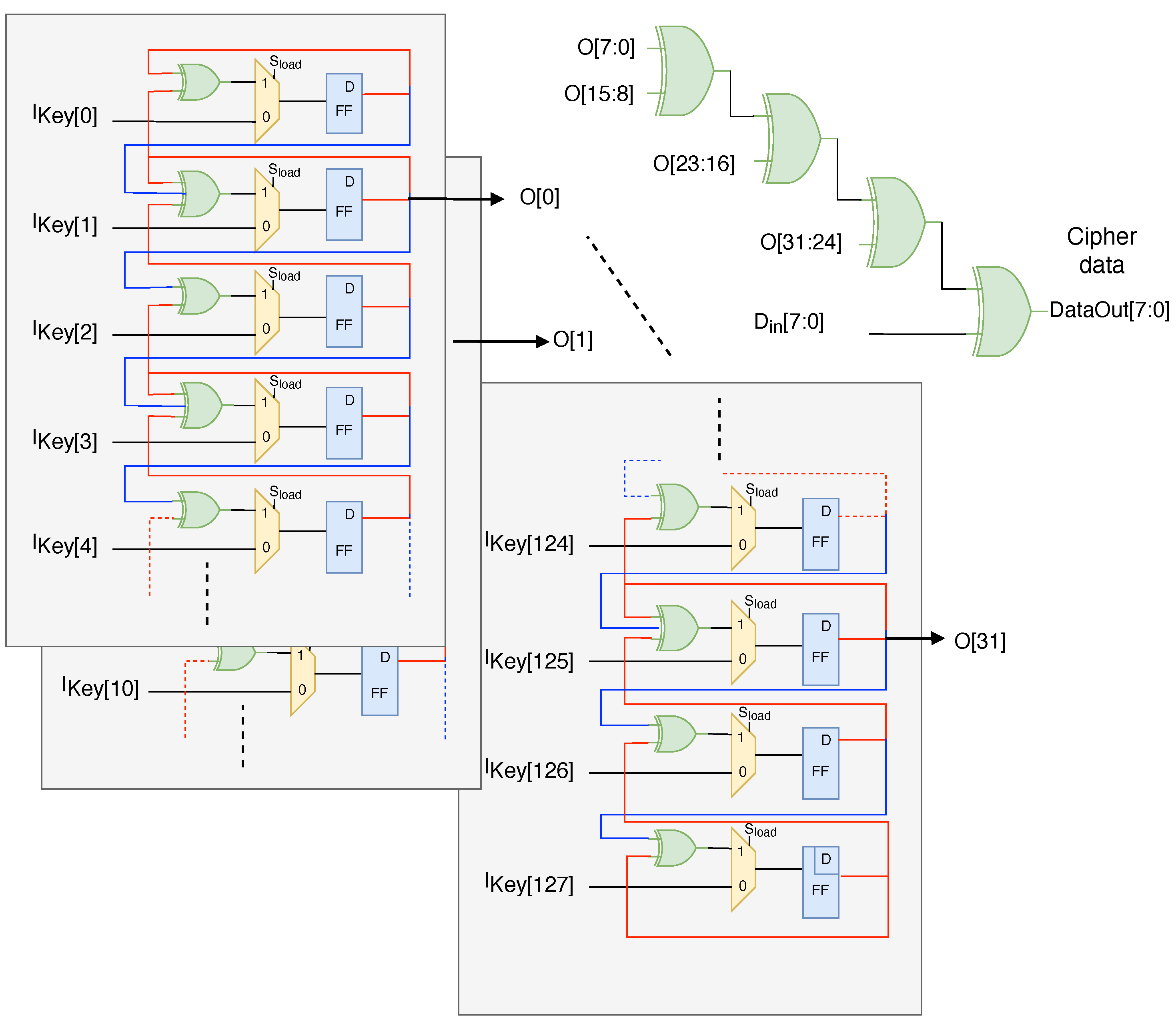
A hybrid cellular automata (HCA) is proposed as a hardware PN generator. Its inherent parallel nature and ability to generate complex patterns from Rules 90 and 150 make it well suited for the DSSS cipher engine. HCAs are grid-like structures of interconnected cells inspired by natural systems. In this implementation, it consist of a two-dimensional array of flip-flops, each storing a current state of 0 or 1. A clock signal synchronizes updates across all cells. In the hybrid structure, Rule 90 determines a cell’s new state from the XOR of its left and right neighbors, and Rule 150 updates a cell’s state based on the majority vote of its neighbors, including itself. These rules can be implemented using XOR gates and majority gates, respectively. Figure 4 illustrates the HCA architecture. This design is capable of generating 32-bit pseudorandom numbers for each clock cycle.
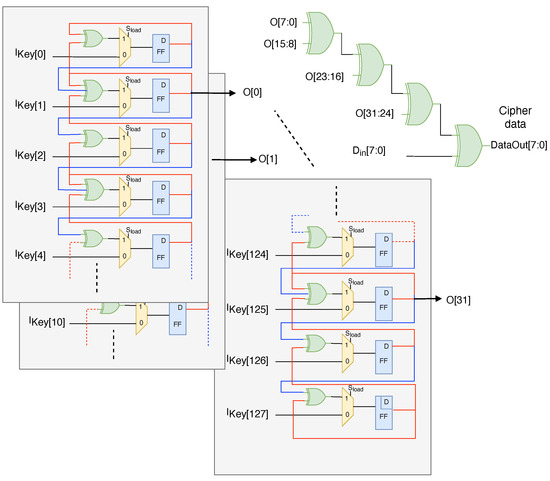
Figure 4.
Hybrid cellular automata architecture based on Rules 90 and 150.
Once the initial 128-bit key is set for the PN generator, a unique 32-bit pseudorandom sequence is generated. To encrypt the data, each bit of the data is XORed with the corresponding bit of the PN sequence, sequentially. This bit-by-bit operation results in encrypted data. The HCA’s design and implementation were evaluated using the NIST (National Institute of Standards and Technology) testing guidelines to assess its security and resilience.
2.3. Power Management Design
This power management architecture optimizes the use of power-saving modes and employs a power-aware dynamic strategy, reducing the frequency of the processor during periods of low activity. The design is attached as a peripheral diagram with two internal registers, MT0 and MT1, configuring the RISC processor in different power modes, as illustrated in Figure 5. That is, one of four low-power modes (LPMs) can be selected, labeled as LPM0 to LPM3. This module generates a signal that is used as a clock enabler for the microprocessor and its peripherals. Considering a main clock frequency of 50 MHz, LPM0 keeps the enable mode switched on, while LPM1 and LPM2 turn the enable mode on for one clock pulse after every 500 or 5000 pulses of the main clock, respectively. LPM3 puts the microprocessor to sleep by removing the clock enable signal for the time programmed in the time register (MT1). Once the programmed time has elapsed, the clock enable mode is turned on, and the mode register is reset to wake up in LPM0.
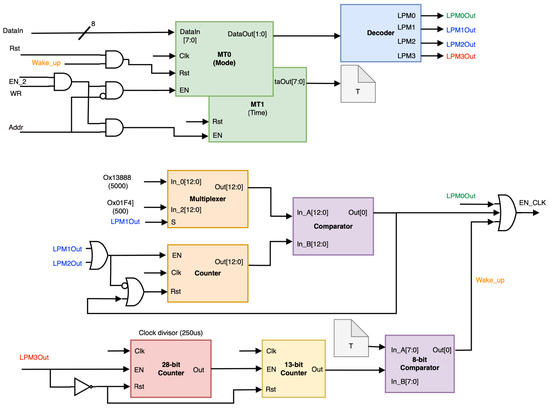
Figure 5.
Low-power mode configuration design.
3. Implementation of the Dynamic Power Strategy
This section describes a dynamic power management strategy (DPMS) to optimize the use of power-saving modes and match performance with power needs. A processing chain for signal encryption is proposed in Figure 6 to efficiently manage the energy of the IoMT sensor node.
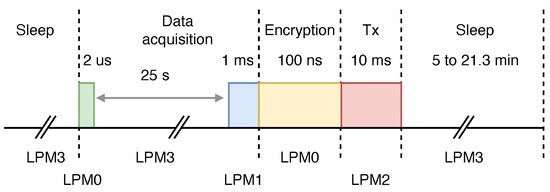
Figure 6.
Flowchart diagram of the proposed DPMS.
3.1. Low-Power Mode Configuration
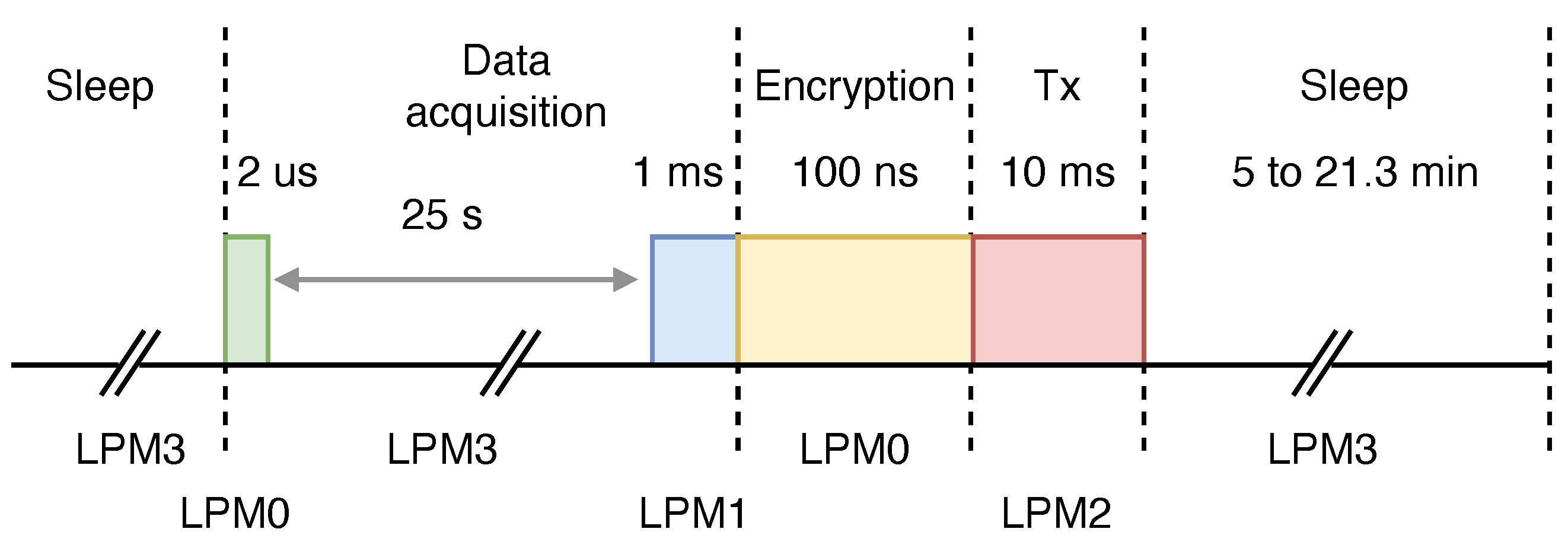
The dynamic data rate capabilities of various low-power modes are crucial for optimizing energy consumption in wireless sensing nodes. By dynamically adjusting the data rate, the power management strategy can trigger sleep-mode transitions more effectively while prioritizing critical information and extending battery life. This technique allows the node to operate at the lowest possible power consumption level while maintaining performance requirements. To achieve this energy optimization, the proposed RISC processor is configured to support different data rates across the low-power modes. Table 1 shows the specifications for configuring register MT0 for different low-power modes.

Table 1.
Specifications for low-power mode configuration of the RISC processor.
To select the sleep period, the MT1 register must be configured. The user defines the exact period based on the DPMS requirements, as shown in Table 2. The sleep period can be dynamically selected for 25 s during data acquisition or from 5 to 21.3 min after data transmission, as illustrated in Figure 6.

Table 2.
Sleep time configuration for LPM3.
3.2. Data Acquisition
The data from the clinical-grade MAX30102 (PPG) sensor (Maxim Integrated, San Jose, CA, USA) were acquired using the I2C peripheral [28]. This sensor contains a pulse oximeter (SpO2) and a heart rate (HR) module with a consumption of 60 A and 0.7 A in sleep mode. Each data acquisition payload of 2 bytes for SpO2 and HR takes 20.48 s at a sampling rate of 25 Hz. According to the DPMS, the RISC processor is first initialized for data acquisition by configuring register MT0 for 2 s in LPM0. Then, the processor waits for 25 s for the sampled data from the PPG sensor in sleep mode (LPM3). Finally, in LPM1, the processor receives the payload from the sensor using the I2C peripheral.
3.3. Data Encryption and Transmission
The DSSS encryption uses the cipher engine as an RISC peripheral. To perform this encryption process, the processor is configured in active mode (LPM0). Using an encryption key of 128 bits, pseudorandom numbers of 32 bits are generated based on the HCA technique every two clock cycles. The signal data from the PPG sensor are encrypted in 100 ns and transmited approximately every 5 min, implying ≈ 288 data transmissions in a day. The cryptoprocessor sends the measured data to the BLE radio through the RISC via the UART. BLE offers low-power communication with a data rate of up to 2 Mbps, making it ideal for applications requiring frequent, short-range data exchanges. BLE employs a packet-based transmission structure. Each packet consists of a 1-byte preamble, 4-byte access address, 2-byte payload, and a 3-byte cyclic redundancy code (CRC) for error detection. The 2-byte payload is used for carrying the actual heart rate and SpO2 data to be transmitted. BLE allows for the transmission of multiple packets in succession, enabling efficient data transfer over short distances. This feature, combined with BLE’s low power consumption, makes it well suited for a wide range of IoT and wearable device applications.
To analyze and optimize low-power modes, a State Transition Table (STT) was employed to characterize the system’s state transitions. As depicted in Table 3, the STT provides a comprehensive overview of power management behavior across different processing states. This STT-driven approach was implemented within the RISC processor to effectively minimize power consumption on the FPGA platform. The final design was synthesized using the Intel Quartus Prime design suite [29].

Table 3.
STT analysis.
Finally, the BLE sensor node transmits ten-byte data packets to a gateway that acts as a bridge between the BLE sensor network and the cloud-based infrastructure. It receives BLE packets from the sensor nodes and processes them using MQTT-SN, a lightweight version of MQTT designed for resource-constrained devices. The gateway then uploads the data to a cloud-based server over Wi-Fi. A UDP socket ensures seamless packet routing between the BLE node and the MQTT-SN gateway. The gateway subscribes to sensor data using a RESTful API built with Node.js. Each sensor node is assigned a unique SensorID, and the gateway programs a NodeID into each node. Upon receiving data, the node transmits a packet to the gateway. The gateway addresses the server using MQTT QoS level 0 over TCP transport to the broker, which then forwards the data to the web application. A cloud-based database stores the sensor data.
4. Implementation Results
The dynamic power management implementation results of the cryptoprocessor system on the FPGA are presented in this section. The secure sensing system for IoMT devices leverages the DSSS architecture to encrypt/decrypt signal measurements from a PPG sensor.
4.1. FPGA-Based Encryption/Decryption Validation Analysis
The integration of the DPMS with the RISC cryptoprocessor design was validated using an Intel 5CSEMA5F31C6N FPGA device. The FPGA contains 31,232 logic elements and includes 384 KB of embedded block RAM (BRAM) and 16 KB of embedded flash memory.
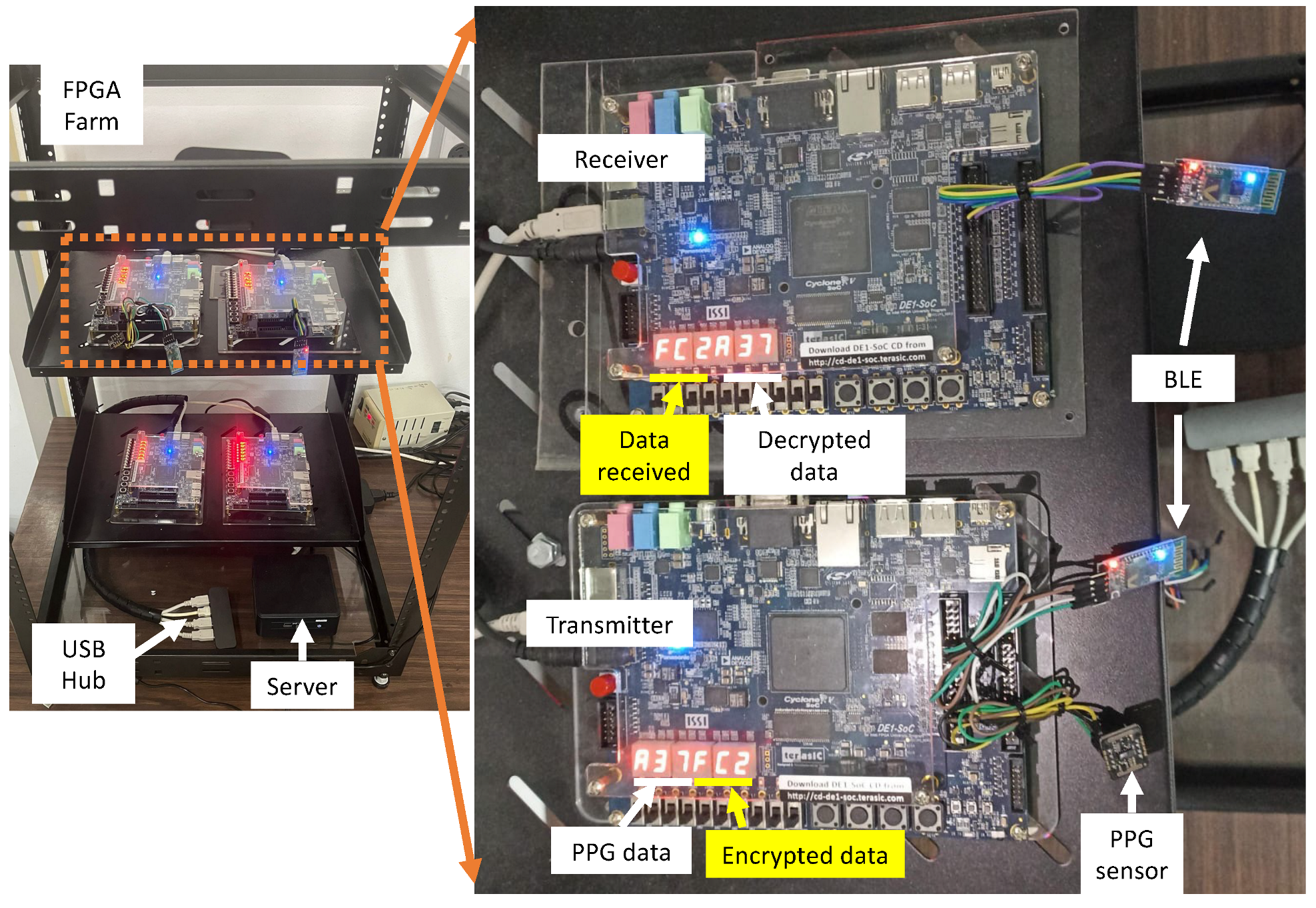
Figure 7 depicts the laboratory setup used for validation testing with one FPGA for data encryptation and transmission and another one for reception and decryption. It can be observed that the PPG sensor is connected to the GPIO peripheral of the RISC processor, while the displays showcase the acquired data and the DSSS-based cipher result. For a functional demonstration, only the least significant 4 bits of each byte within three sequential SpO2 data samples are utilized. These 4-bit values are consecutively displayed on the first three displays of the transmitter. The remaining three displays concurrently showcase the corresponding ciphered versions of these 4-bit data. The receiver scheme implemented in the second FPGA demonstrates the received data and the decrypted data shown on the seven-segment displays.
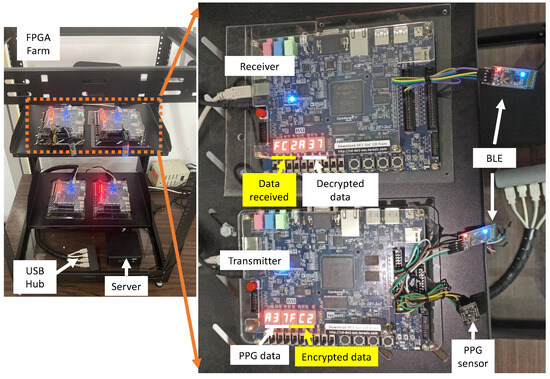
Figure 7.
Validation scheme for the proposed FPGA-based cryptoprocessor system.
In this sense, a test of encryption/decryption was conducted to verify the correct operation of the proposed DSSS-based cryptoprocessor integrated with dynamic power management. The FPGA-based system acquired the PPG sensing measurements to validate the operation of the proposed system.
4.2. FPGA-Based DPMS Performance Analysis
The laboratory tests were conducted as follows: The PPG measurements consisted of 2-byte values for heart rate (HR) and oxygen saturation (SpO2) captured every 25 s. The encryption technique employed was the DSSS, and the BLE transceiver was configured for 0 dB power transmission (range coverage of 10 to 15 m).
4.2.1. Test 1: Hardware Speed Resource Analysis
This experiment analyzes the hardware resource implementation of the DSSS-based cryptoprocessor system. The Intel Quartus Prime design suite software was used for the synthesis. The hardware implementation results on the Intel 5CSEMA5F31C6N FPGA demonstrate the reduced hardware resource utilization of each module within the proposed architecture, as shown in Table 4. The number of logic cells and registers is balanced, ensuring optimal allocation of the designed architecture within the FPGA.

Table 4.
Hardware resource analysis of the proposed cryptoprocessor system.
Additionally, a maximum clock frequency of 100 MHz (a clock period of 10 ns) was achieved when the proposed architecture was synthesized. The total execution time for performing secure packet transmission using the proposed architecture was 25.111 s (25.001 s for data acquisition, 100 ns for encryption, and 10 ms for transmission). The sleep period was dynamically set up for 5 to 21 min.
4.2.2. Test 2: Power Consumption Estimation Analysis
In this test, the experiment involves power consumption analysis for all cryptoprocessor processing states. The power analysis tool used was the Intel Quartus Prime design suite. This software provides reliable power estimates based on pre-built power models for the architecture design in FPGAs, as described in [30,31].
The power consumption of each low-power mode associated with the processing states is the following:
- Data acquisition: Stdby at LPM0 for 2 us (20.01 mW), sleep at LPM3 for 25 s (0.04 mW), and data measurements at LPM1 for 1ms (0.97 mW);
- Data encryption/decryption: LPM0 for 100 ns (20.01 mW);
- Transmission: LPM2 for 10 ms (0.98 mW);
- Sleep mode: LPM3 for 5 min (0.04 mW).
Table 5 illustrates the power consumption analysis of the cryptoprocessor for different operational frequencies. It is important to note the trend of the sleep mode in reducing the system’s average power consumption.

Table 5.
Power consumption analysis of an integrated RISC and DSSS cryptographic engine.
The defined DPMS chooses the sleep duty cycle based on the data variability of the sensors. This means that if the data variability is low, indicating consistent heart rate and SpO2 measurements, there is no need to transmit data. The cryptoprocessor system also demonstrates a good trade-off between energy efficiency and design area. As shown in Table 5, the dynamic power management prevents the system from shutting down by applying sleep periods of up to 21 min.
4.2.3. Test 3: Cryptographic Randomness Performance Analysis
This experiment evaluates a comprehensive suite of statistical tests to assess the randomness of encrypted data. From the NIST test suite, NIST SP 800-22, entitled A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications, consists of 15 individual statistical tests that are considered to analyze the output randomness of the proposed cipher engine block, which is based on the HCA. The NIST SP 800-22 tests are widely used and accepted in the cryptographic community as a reliable means of assessing the randomness of sequences.
Table 6 presents the randomness evaluation of the random number generator for the cryptographic engine of the proposed RISC-based cryptoprocessor system. The p-value results show that all tests were passed successfully, allowing for the conclusion of statistical randomness. Two additional tests from the Diehard test suite, i.e., the Ranks of Matrices and Birthday Spacings tests, were also conducted, with p-values of 0.856 and 0.468, respectively.

Table 6.
NIST test results for randomness evaluation.
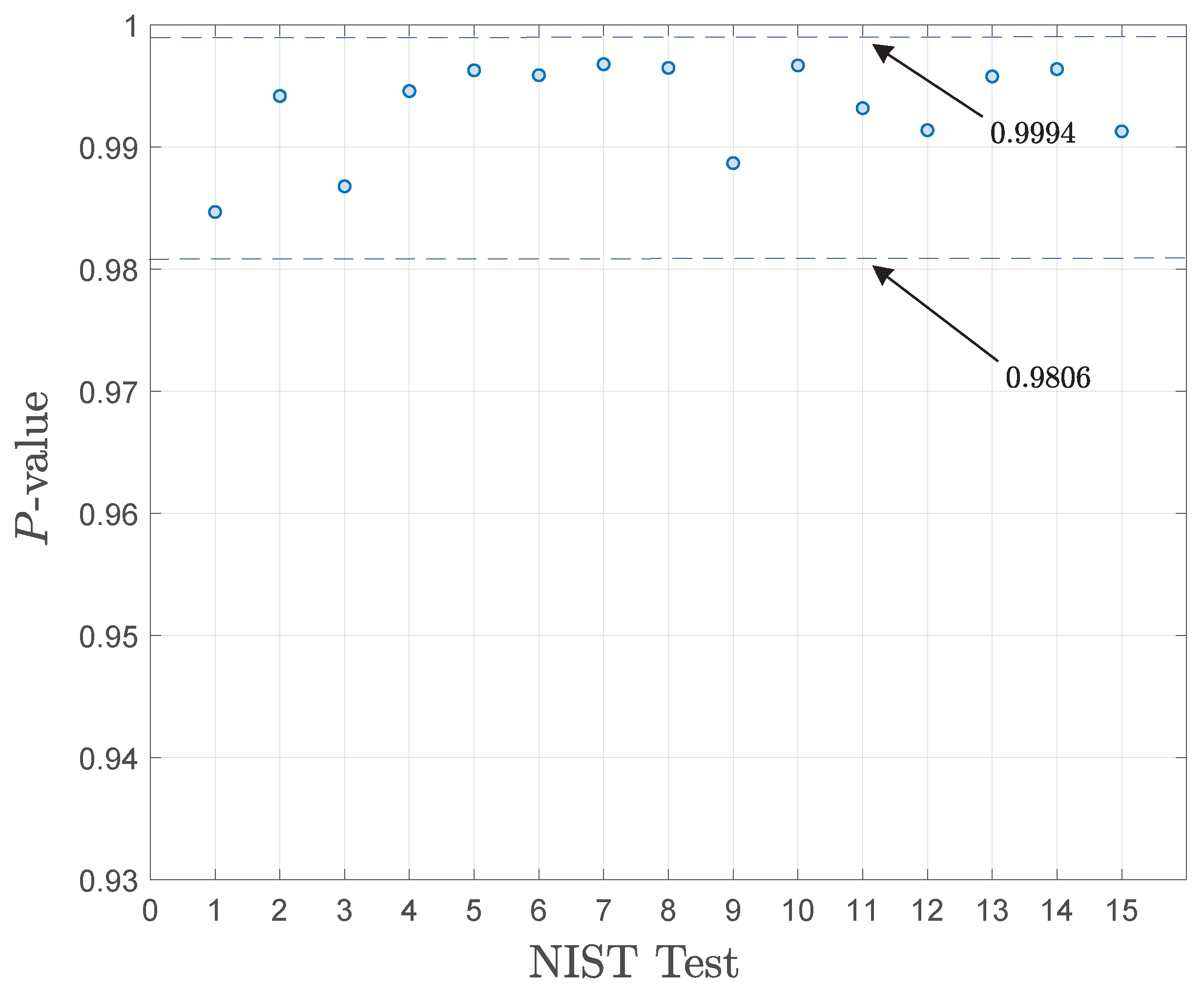
The following parameters were considered: an encryption key of 128 bits and a pseudorandom number generation with a 32-bit dimension. Given the results for the statistical tests, Figure 8 shows the proportion of sequences that pass each test, according to the NIST SP 800-22 suite [32]. Considering 1000 binary uniform random sequences and a significance level of 0.01, if 998 binary sequences achieved p-values ≥ 0.01, then the proportion is . In the context of NIST tests, these results suggest that the generated sequences exhibit statistical randomness. The confidence interval for this proportion is 0.9806 to 0.9994.
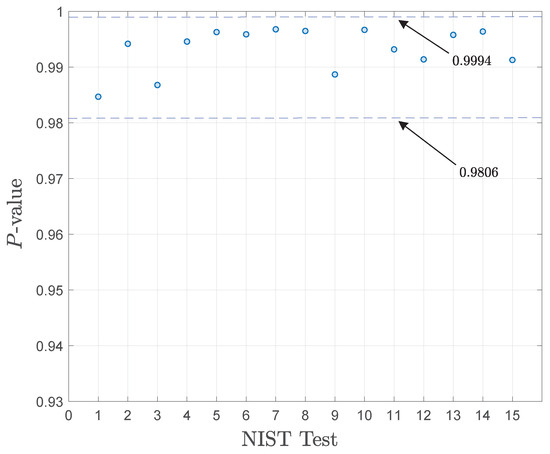
Figure 8.
NIST test results for the proposed FPGA-based cryptoprocessor system.
5. Discussion
Table 7 provides a comparative performance analysis of our approach against other similar systems. In contrast to other FPGA-based power management approaches in cryptoprocessor architectures, such as those presented in [13,17,18], the integration of the DPMS with the DSSS-based cryptoprocessor achieves a power consumption of 0.1 mW. This consumption is 98.1% lower than that of the FPGA-based PQC cryptographic design and significantly lower (88.5%) than that of the AEAD cipher technique on an ASIC. The chaotic-PRNG model discussed in [13] reports a reduced hardware footprint of only 1211 logic cells and 1467 registers. However, although their design is nearly twice as small as the resources employed in our cryptographic system, it does not include dynamic power management in the RISC processor within the FPGA design. A lightweight cryptographic design of an MCU is used to implement the SLIM algorithm following a uniform power management strategy. However, the sequential processing in the MCU leverages a power consumption of 10.7 mW. Additionally, the NIST test results presented in Figure 8 demonstrate a rigorous evaluation of the statistical properties of our sensing nodes, ensuring that they meet the stringent requirements for secure IoMT networks.

Table 7.
Comparative analysis of state-of-the-art encryption engines for IIoT sensing nodes.
6. Conclusions
A dynamic power management strategy integrated within a resource-constrained FPGA-based cryptoprocessor core was proposed for secure IoMT networks. To demonstrate the use of the proposal in a real-time IoMT system, a sensing node was designed that includes PPG measurements consisting of heart rate (HR) and oxygen saturation (SpO2). The designed 8-bit RISC integrates a DSSS engine and a power management module to cooperatively manage the dynamic, energy-aware operation of the wireless sensing node devices. Experimental tests demonstrate the accuracy of the dynamic power management used in the proposed cryptographic system while maintaining an average low power consumption of 0.1 mW. The constrained design, using 2414 logic cells and 5292 registers, further reflects this innovative approach for developing next-generation wireless IoT. Likewise, a comparison with state-of-the-art lightweight sensor nodes was presented, highlighting the advantages of the proposed dynamic power management scheme within the cryptoprocessor core. The design of our resource-constrained FPGA-based cryptoprocessor core can be adapted to improve new IoMT technologies for use in wearable medical applications, such as patient monitoring, disease prediction, and healthcare. The proposed RISC processor code is available in a GitHub repository [33].
Author Contributions
Conceptualization, A.C.-A., J.V.-C. and J.J.E.-L.; formal analysis, A.C.-A., J.V.-C., C.D.-V.-S., R.A.-E. and R.Q.-C.; investigation, A.C.-A., J.V.-C. and D.V.; methodology, A.C.-A., J.V.-C. and J.J.E.-L.; project administration, J.V.-C. and J.J.E.-L.; validation, R.Q.-C., A.C.-A., C.D.-V.-S. and J.V.-C.; writing—original draft, A.C.-A., J.V.-C. and J.J.E.-L.; Writing—review and editing, J.J.E.-L., J.V.-C. and A.C.-A.; funding, J.O.-A. All authors have read and agreed to the published version of the manuscript.
Funding
J. Ortegón-Aguilar, J. Vázquez-Castillo, and A. Castillo-Atoche acknowledge the support of the Consejo Quintanarroense de Humanidades, Ciencias y Tecnologías (COHQCYT).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data are contained within the article.
Acknowledgments
The authors would like to thank the Intel Technology Corporation for their support in donating the FPGA devices.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Babbar, H.; Rani, S.; AlQahtani, S.A. Intelligent Edge Load Migration in SDN-IIoT for Smart Healthcare. IEEE Trans. Ind. Inform. 2022, 18, 8058–8064. [Google Scholar] [CrossRef]
- Raza, A.; Nasar, M.A.; Hanandeh, E.S.; Zitar, R.A.; Nasereddin, A.Y.; Abualigah, L. A Novel Methodology for Human Kinematics Motion Detection Based on Smartphones Sensor Data Using Artificial Intelligence. Technologies 2023, 11, 55. [Google Scholar] [CrossRef]
- Al-Nbhany, W.; Zahary, A.; Al-Shargabi, A.A. Blockchain-IoT Healthcare Applications and Trends: A Review. IEEE Access 2024, 12, 4178–4212. [Google Scholar] [CrossRef]
- Bayoumy, K.; Gaber, M.; Elshafeey, A. Smart wearable devices in cardiovascular care: Where we are and how to move forward. Nat. Rev. Cardiol. 2021, 18, 581–599. [Google Scholar] [CrossRef]
- Zlatintsi, A.; Filntisis, P.P.; Efthymiou, N.; Garoufis, C.; Retsinas, G.; Sounapoglou, T.; Maglogiannis, I.; Tsanakas, P.; Smyrnis, N.; Maragos, P. Person Identification and Relapse Detection from Continuous Recordings of Biosignals Challenge: Overview and Results. IEEE Open J. Signal Process. 2024, 5, 641–651. [Google Scholar] [CrossRef]
- Donati, M.; Panicacci, S.; Ruiu, A.; Dalmiani, S.; Festa, P.; Ait-Ali, L.; Mastorci, F.; Pingitore, A.; Pennè, W.; Fanucci, L.; et al. Exploiting Biomedical Sensors for a Home Monitoring System for Paediatric Patients with Congenital Heart Disease. Technologies 2021, 9, 56. [Google Scholar] [CrossRef]
- Ramasamy, L.K.; Khan, F.; Shah, M.; Prasad, B.V.V.S.; Iwendi, C.; Biamba, C. Secure Smart Wearable Computing through Artificial Intelligence-Enabled Internet of Things and Cyber-Physical Systems for Health Monitoring. Sensors 2022, 22, 1076. [Google Scholar] [CrossRef]
- Woo-García, R.M.; Pérez-Vista, J.M.; Sánchez-Vidal, A.; Herrera-May, A.L.; de-la Rosa, E.O.; Caballero-Briones, F.; López-Huerta, F. Implementation of a Wireless Sensor Network for Environmental Measurements. Technologies 2024, 12, 41. [Google Scholar] [CrossRef]
- Rostampour, S.; Bagheri, N.; Bendavid, Y.; Safkhani, M.; Kumari, S.; Rodrigues, J.J.P.C. An Authentication Protocol for Next Generation of Constrained IoT Systems. IEEE Internet Things J. 2022, 9, 21493–21504. [Google Scholar] [CrossRef]
- Jan, M.A.; Khan, F.; Khan, R.; Mastorakis, S.; Menon, V.G.; Alazab, M.; Watters, P. Lightweight Mutual Authentication and Privacy-Preservation Scheme for Intelligent Wearable Devices in Industrial-CPS. IEEE Trans. Ind. Inform. 2021, 17, 5829–5839. [Google Scholar] [CrossRef] [PubMed]
- Alsarhan, A.; AlJamal, M.; Harfoushi, O.; Aljaidi, M.; Barhoush, M.; Mansour, N.; Okour, S.; Abu, G.; Al-Fraihat, D. Optimizing Cyber Threat Detection in IoT: A Study of Artificial Bee Colony (ABC)-Based Hyperparameter Tuning for Machine Learning. Technologies 2024, 12, 181. [Google Scholar] [CrossRef]
- Paparizos, C.; Tsafas, N.; Birbas, M. A Zynq-Based Robotic System for Treatment of Contagious Diseases in Hospital Isolated Environment. Technologies 2020, 8, 28. [Google Scholar] [CrossRef]
- Bakiri, M.; Guyeux, C.; Couchot, J.F.; Marangio, L.; Galatolo, S. A Hardware and Secure Pseudorandom Generator for Constrained Devices. IEEE Trans. Ind. Inform. 2018, 14, 3754–3765. [Google Scholar] [CrossRef]
- Yang, Y.; He, D.; Kumar, N.; Zeadally, S. Compact Hardware Implementation of a SHA-3 Core for Wireless Body Sensor Networks. IEEE Access 2018, 6, 40128–40136. [Google Scholar] [CrossRef]
- Fotovvat, A.; Rahman, G.M.E.; Vedaei, S.S.; Wahid, K.A. Comparative Performance Analysis of Lightweight Cryptography Algorithms for IoT Sensor Nodes. IEEE Internet Things J. 2021, 8, 8279–8290. [Google Scholar] [CrossRef]
- Banerjee, U.; Wright, A.; Juvekar, C.; Waller, M.; Arvind; Chandrakasan, A.P. An Energy-Efficient Reconfigurable DTLS Cryptographic Engine for Securing Internet-of-Things Applications. IEEE J. Solid-State Circuits 2019, 54, 2339–2352. [Google Scholar] [CrossRef]
- Hadayeghparast, S.; Bayat-Sarmadi, S.; Ebrahimi, S. High-Speed Post-Quantum Cryptoprocessor Based on RISC-V Architecture for IoT. IEEE Internet Things J. 2022, 9, 15839–15846. [Google Scholar] [CrossRef]
- Kamadi, A.; Abbas, Z. Implementation of TRNG with SHA-3 for hardware security. Microelectron. J. 2022, 123, 105410. [Google Scholar] [CrossRef]
- Zhang, C.; Yue, J.; Jiao, L.; Shi, J.; Wang, S. A Novel Physical Layer Encryption Algorithm for LoRa. IEEE Commun. Lett. 2021, 25, 2512–2516. [Google Scholar] [CrossRef]
- Aboushosha, B.; Ramadan, R.A.; Dwivedi, A.D.; El-Sayed, A.; Dessouky, M.M. SLIM: A Lightweight Block Cipher for Internet of Health Things. IEEE Access 2020, 8, 203747–203757. [Google Scholar] [CrossRef]
- Liu, X.; Wu, B.; Yuan, X.; Yi, X. Leia: A Lightweight Cryptographic Neural Network Inference System at the Edge. IEEE Trans. Inf. Forensics Secur. 2022, 17, 237–252. [Google Scholar] [CrossRef]
- Feng, Z.; Cao, G.; Grigoriadis, K.M.; Pan, Q. Secure MPC-Based Path Following for UAS in Adverse Network Environment. IEEE Trans. Ind. Inform. 2023, 19, 11091–11101. [Google Scholar] [CrossRef]
- Huang, X.; Li, L.; Yang, J. IVLBC: An Involutive Lightweight Block Cipher for Internet of Things. IEEE Syst. J. 2023, 17, 3192–3203. [Google Scholar] [CrossRef]
- He, Y.; Wang, G.; Li, W.; Ren, Y. Improved Cube Attacks on Some Authenticated Encryption Ciphers and Stream Ciphers in the Internet of Things. IEEE Access 2020, 8, 20920–20930. [Google Scholar] [CrossRef]
- Guo, X.; Hua, J.; Zhang, Y.; Wang, D. A Complexity-Reduced Block Encryption Algorithm Suitable for Internet of Things. IEEE Access 2019, 7, 54760–54769. [Google Scholar] [CrossRef]
- Saračević, M.H.; Adamović, S.Z.; Miškovic, V.A.; Elhoseny, M.; Maček, N.D.; Selim, M.M.; Shankar, K. Data Encryption for Internet of Things Applications Based on Catalan Objects and Two Combinatorial Structures. IEEE Trans. Reliab. 2021, 70, 819–830. [Google Scholar] [CrossRef]
- Singh, P.; Acharya, B.; Chaurasiya, R.K. Chapter 8—Lightweight cryptographic algorithms for resource-constrained IoT devices and sensor networks. In Security and Privacy Issues in IoT Devices and Sensor Networks; Advances in ubiquitous sensing applications for healthcare; Sharma, S.K., Bhushan, B., Debnath, N.C., Eds.; Academic Press: Cambridge, MA, USA, 2021; pp. 153–185. [Google Scholar] [CrossRef]
- Maxim Integrated MAX30102. Available online: https://www.analog.com/en/products/max30102.html (accessed on 9 October 2024).
- Intel Quartus Prime Design Software. Available online: https://www.intel.la/content/www/xl/es/collections/products/fpga/software/downloads.html (accessed on 9 October 2024).
- Nasser, Y.; Lorandel, J.; Prévotet, J.C.; Hélard, M. RTL to Transistor Level Power Modeling and Estimation Techniques for FPGA and ASIC: A Survey. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2021, 40, 479–493. [Google Scholar] [CrossRef]
- Lin, Z.; Sinha, S.; Zhang, W. An Ensemble Learning Approach for In-Situ Monitoring of FPGA Dynamic Power. IEEE Trans. Comput. Aided Des. Integr. Circuits Syst. 2019, 38, 1661–1674. [Google Scholar] [CrossRef]
- NIST SP 800-22, A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications. Available online: https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-22r1a.pdf (accessed on 15 November 2024).
- GitHub, R. RISC Code FPGA-Based Cryptoprocessor System. Available online: https://github.com/Laboratorio-de-robotica-e-industria-4-0/RISC-Cryptoprocesor (accessed on 23 January 2025).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).