This lightweight security gateway protocol aims to enhance security operation by ensuring operational latency preferences. In this section, in order to demonstrate the proposed ELSGP protocol, we will explore the challenges of the existing edge server-based edge layer architecture. Subsequently, we will present how the proposed IoT edge layer architectural model mitigates the explored challenges. Finally, following the presentation of the model, the ELSGP protocol will be presented.
3.1. Challenges of the Existing Edge Server-Based System
In many research studies and previous IoT computational models, edge layer servers are proposed to assist constrained IoT devices. However, for this research paper, we investigated edge server operations and discovered several challenges for edge-server based IoT edge layer communication systems. These challenges include the following:
1. Edge server failure and its impact: In a highly populated IIoT system, an edge server computes, stores, and controls data for many edge devices. The impact of the failure of one server may cause a significant outage or it may increase the load on the other servers.
2. Handling diversified devices: In an industrial scenario, many heterogeneous devices are controlled from or through the edge server. Therefore, the servers need to be designed and configured according to the requirements of the system operations, which is challenging if there is a requirement to maintain the diversified compatibilities.
3. Supporting multi-communication technologies: Several communication technologies need to be incorporated into the server system, which makes the server configuration complex. Wi-Fi, Zigbee, Bluetooth, 6LoWPAN, 5G, and so on are the different kinds of communication technologies that interconnect the edge devices to the system. Maintaining the various technologies from the same server is truly complex and challenging.
3.2. The Proposed Model
The proposed model has been developed to make the edge server-based edge layer architecture more distributed in terms of computation, security, and system operational tasks.
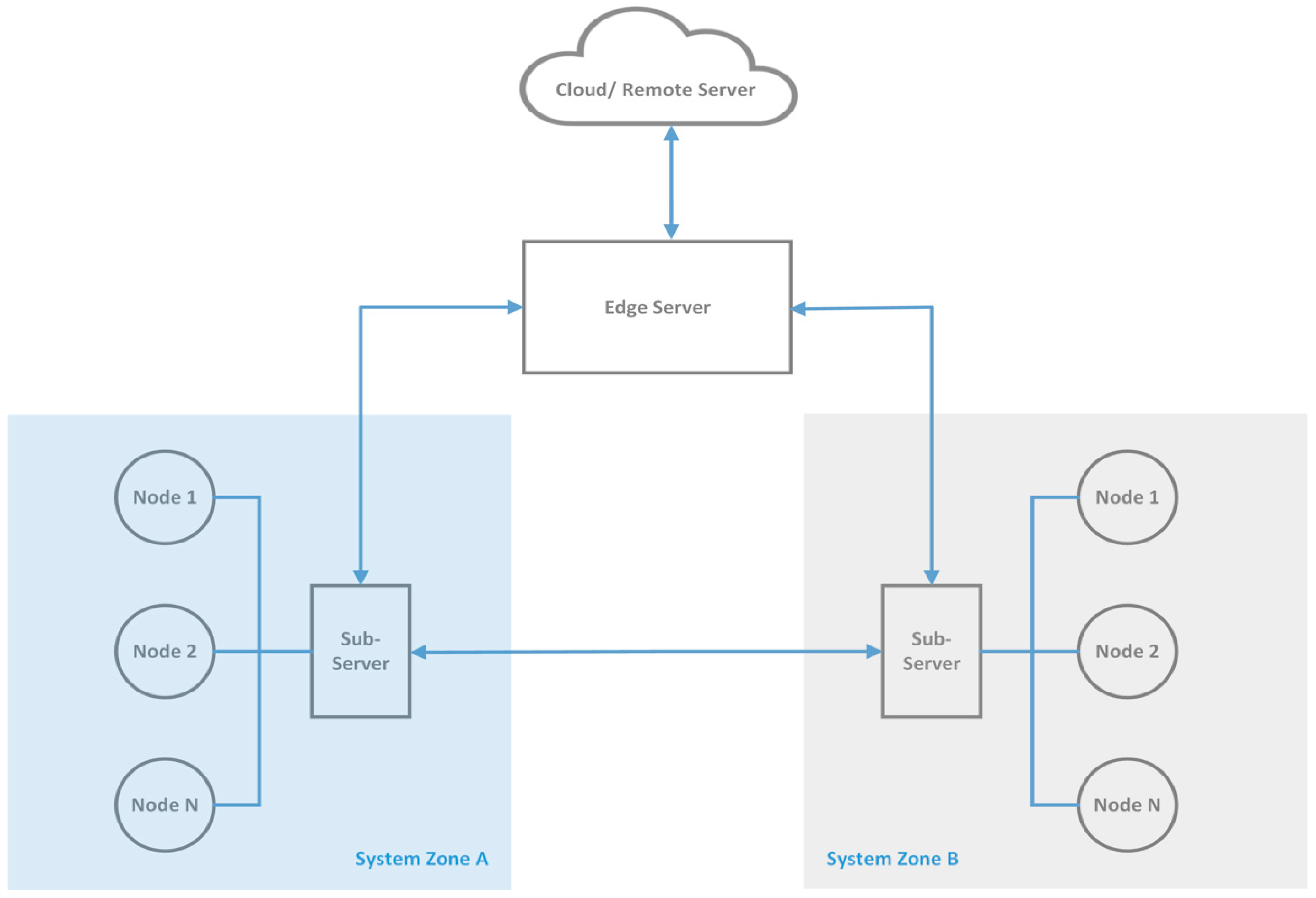
Figure 1 shows the proposed edge layer architecture. The end nodes are considered as the IoT devices, which include edge IoT devices, operational sensors, and actuators.
In this architectural model, we have introduced a new network entity called a sub-server, which is a server-like device that is not meant to replace an edge server but is designed to enhance the capabilities of the constrained IoT devices. Implementing a sub-server can help to achieve the following objectives:
To support lightweight communication and advanced encryption at the same time in the edge layer.
To fulfill the latency requirement of sensitive traffic.
To reduce operational tasks at the edge server.
To achieve logical and physical isolation among the group of IoT devices to reduce attack surfaces.
To enable a more distributed computational system.
To provide two-layer validation, i.e., primary and secondary validation (IoT device to sub-server and sub-server to edge server). When the generated data travel from one logical zone to another zone or (to or from) the edge server, this two-stage validation could help to maintain privacy and isolate the devices of one logical group from other groups of the same system.
The end nodes will have client principles, and the Sub-servers will have both server and client principles. Participating sensors in the network can act like a typical sensor network wherein the communication channels can be established in a wired or wireless medium. However, according to this designed architecture, the formation of a wired/wireless sensor network(s) should follow the developed principles, which are elaborated in
Section 3.2.1.
Based on a system requirement, one or many edge servers can act as the coordinating server(s). Both sub-server and edge servers should have gateway features, and these features are elaborated in
Section 3.2.3 and
Section 3.2.4. As is the case with the typical IoT architecture, the edge servers are connected to a cloud-based server or a remote server.
3.2.1. Concept of Zones and Groups
In the proposed model, every IoT device is directly connected to a sub-server through a wired or wireless medium. A zone is determined as a physical group of IoT devices that are directly connected and administrated through or from a sub-server. Every end device within a zone should contain the same Zonal ID. Here, the zonal ID is denoted as ZID. According to the proposed model, every ZID of a particular network should be configured identically to the others. The ZID can be determined by the system admin or through a predetermined group policy.
The key differences between the zone and group concepts can be summarized as follows: A zone is the physical segmentation of all operational nodes, whereas a group is all about the logical segmentation of the devices. Grouping can be modified by system control commands, whereas a zone is more resistant to change; a zone can only be changed when a device is physically moved to another zone.
In an IoT system, an end device may need to transfer or receive data from other end devices to execute an operation. Virtual grouping between end devices may require fulfilling the security and independent communication requirements of a system. A group of end devices from the same or different zones can exchange data without repeated authentication processes, and it is expected to reduce the data transmission latency and computation resource usage. In an IoT system, numerous heterogeneous devices perform operational tasks together. Depending on the system requirements, these devices have various attributes, which may create a complex operational environment. On the other hand, among these devices, many homogeneities or operational dependencies exist. To synchronize and secure system operations with the designed model, we have introduced the idea of grouping.
According to the proposed protocol, a logical grouping (as shown in
Figure 2) categorizes end devices based on attributes and predesigned group policy to isolate the group devices from other groups and secure intra-group communication. The devices in a local zone can be the members of a group, but the devices of a group may not be members of a local zone. Group members of a particular group are modifiable through the group policy or under the local or remote administration. In contrast, A-Zone members cannot be modified within the policy framework or local/remote administration unless the physical changes happen in the zone. However, The
ZID can be determined via the system admin or through a predetermined group policy.
3.2.2. Implementation of Microservices
In a complex IIoT environment, heterogeneous devices need to be operated and maintaining the quality of service (QoS) of the system is challenging. In various contexts, conventional edge computing cannot fulfill the QoS [
15]. Therefore, researchers are currently focusing on implementing µs in IoT systems due to their multitudinous properties, including scalability, modularity, resiliency, and compatibility in heterogeneous devices [
15].
In the proposed model, multiple operations need to be conducted at different levels of the system, which could make the system more complex. µs can be implemented to resolve this problem and simplify the operational tasks. From protocol translation services to the different kinds of gateway operations in the edge layer, µs can be implemented to make the system more simplistic, resilient, and constrained resource-compatible.
To rescue the operational and computational tasks in a cloud–edge-based hybrid environment, numerous applications need to be processed at the edge to fulfill the latency requirement, and monolithic services can be replaced with µs [
33]. The µs will be deployed in a sub-server and edge server according to the predetermined policy framework.
However, maintaining the dependency relationship within the µs is complex in a large IIoT system, as a large amount of data needs to be transferred among the adjacent µs [
33]. In a µs-based system, every service request and response should have a unique identifier, i.e., a correlation ID [
34]. Managing and coordinating these unique request processing identifiers requires additional computational resources.
In this distributed computation-based architecture, to make the µs more simplistic, the µs-based applications are processed into two phases. In phase 1, only the relational services will be deployed and operated at the sub-server. The relational services may vary from one sub-server to another sub-server. This way, the transition of redundant data and the processing of redundant operations can be stopped. In phase 2, only the adjacent µs need to be deployed. The adjacent µs also may vary from one edge server to another edge server.
3.2.3. Gateway Functions at Sub-Server (Phase 1)
The end devices are constrained in nature. These devices have limited computational power, operate on light-power batteries, and have less memory in use. The main purpose of the sub-server is to assist the end devices with processing, memorizing, and optimizing power consumption. Many lightweight gateway protocols have been designed to establish communication with the other internal or external devices of a system. These protocols have different characteristics and implementation methods to establish communication among the devices. Many access requests come from the external network of the existing system, though this is not applicable to the in-use lightweight protocols. For example, if a web command passes to the IoT system, it usually passes with HTTP/HTTPS protocols. However, the HTTP/HTTPS is not a lightweight protocol; thus, it may need to be converted into a lightweight protocol like COAP or MQTT [
35]. A protocol translation may come into operation to convert the conventional protocols to the lightweight protocols or lightweight protocols to the conventional protocols.
Transmitting external requests: Transmitting, executing, and deploying external requests from a different zone, group, or network requires passing through the various predetermined security points of a particular system to ensure the security requirements. In this circumstance, implementing lightweight compatibility with end devices becomes more challenging. Security operations such as authentication, authorization, data request validation, and encryption require additional computation. Sub-servers control downstream communication (with the end IoT devices), as they can act as a parent device. As a parent device, a sub-server should act like the head-point that responds to the upstream data request, encrypts the transmitted data, encapsulates it, supports the implementation of VPN tunneling, and validates the requests.
Validating requests: In an unprotected environment, IoT devices can become the entry point for an attacker to gain access, which may disrupt the whole system. Therefore, validating the upstream data can be an effective solution to reduce this vulnerability. This type of validation includes analyzing data packet patterns, validating access tokens, handling unknown access and unknown data pattern, and validating unique identifiers like ZID, Dynamic DID, and the correlation ID for µs (if µs have been adopted).
Gateway Load balancing: In
Figure 1, we present our proposed IoT edge layer architecture, in which sub-servers are interconnected as well as connected with the edge server. To deploy load balancing, the execution command operated by the local/remote server or the edge server (depending on the system architecture and deployment policy), the sub-servers will interact with the load balancing control command and share the deployed tasks among them. The sub-servers also exchange their load status with the parent edge server and within the predetermined sub-server group members. This way, the entire system is deployed based on a distributed processing architecture.
Adopting microservices: In heterogeneous IoT systems, researchers have shown more interest in adopting µs instead of a monolithic architecture. However, implementing and managing the µs in a large and complex environment requires some additional processing, which may increase the use of processing resources at a particular stage. To avoid the additional processing requirements from the end devices, we introduced the concept of a sub-server. The sub-server manages every unique µs request and response on behalf of the end devices, exempting the end devices from additional data processing or computational resource usage. Converting the existing system solution to a smart solution is always challenging. The existing independent system solutions or monolithic legacy system solutions can still be transformable with the µs [
36].
Adopting Software-defined gateway functions: A software-defined gateway (SDG) is designed to focus on industrial interconnections to converge with heterogeneous devices [
30]. We adopted the software-defined IoT gateway to automate and dynamically manage the edge network for flexibility and easy programmability [
37].
3.2.4. Gateway Functions at Edge Server (Phase 2)
In this architecture, the gateway has some smart functions, including protocol translation between different used protocols, executing µs, executing policy framework, filtering, and processing generated data at the edge before sending it to the remote server or cloud, executing an external operational command, and managing the logical groups of the internal devices. Regarding our proposed model, the gateway functions at the edge server are presented below.
Transmitting external requests: The proposed model is a gateway-centric local network wherein an edge server is the ultimate edge gateway device for transmitting external requests. In this gateway-centric local network, the dependent devices act as the client. The sub-server itself provides a client-supporting functionality as well as a parenting functionality to the end devices. To execute the gateway functions of an edge gateway to the end devices, the corresponding sub-server passes the gateway functions to the end devices. This property of a sub-server can be denoted as Transparent mode; for the edge gateway, it becomes Server mode, and for the end devices, it is Client mode. In summary, in our proposed protocol, these three tire devices have three different modes: Server, Transparent, and Client. The edge gateway and the end devices operate only on the Server and Client mode, respectively, but the sub-server can perform in two modes: Client or Transparent.
Managing the encryption decision: In an IoT environment, it is very challenging to implement a robust encryption method through all IoT communication channels. To implement strong security, strong encryption needs to be implemented. The implementation of encryption depends on the security requirement. The decision to execute encryption from lightweight to strong [
38] depends on the security requirement of the policy framework.
Protocol translation: In an IoT network, Different protocols are used to manage, control, and execute the command and establish a connection between external and internal networks. In large and complex heterogeneous IIoT networks, various independent protocols are implemented. Achieving synchronization and interoperability within this large variety of protocols are challenging [
39].
Managing logical groups: A logical group enables the devices to logically isolate one group of devices from another. Managing and interconnecting devices within a logical group ensures the implementation of the group policy and other relevant policies. By implementing grouping techniques, devices (including sub-servers) from different zones can be compiled into a group, enhancing security, manageability, and interoperability and enforcing the group policy among the group members. According to our proposed model, an edge server locally assigns coordinates and manages the associated end device groups. An edge server also maintains a correlation with the external devices corresponding to other edge servers to form a group. These external device groups can be called extended groups. The operational and security features of both types of groups (immediate and extended) can be defined through a related group policy in the policy framework.
Dynamic load distribution and balancing: The motivation for introducing the sub-server is to assist the edge server with operational and computational tasks. Dynamic load distribution can be used to reduce the workload from the edge server. As the hub of the local IoT system of the proposed model, an edge server executes commands regarding dynamic load distribution and load balancing depending on the availability of the end nodes, traffic transmission channel preferences, system preferences, and deployment policy.
Filtering the generated data: To avoid overwhelming the whole IoT system, the filtering functions filter the routine or unnecessary data and send the critical and infrequent data away for future analysis and development purposes. Traffic filtering techniques are implemented to optimize the network traffic to comply with the available network bandwidth. The filtering techniques used for the proposed protocol were developed via categorizing, prioritizing, and processing the generated traffic based on traffic attributes and the generating device.
Adopting Microservices: At the edge server, the µs are coordinated and deployed to the associated sub-servers based on the operations that need to be performed. Every microservice deployment and operation can be identified with a unique correlation ID that correlates with a processing request. In this IoT service model, the functions of the µs include (but are not limited to) authentication, protocol translation, managing logical groups, software-defined gateway functions, ABAC operations, deploying filtering decisions, managing, and deploying core policy framework.
Adopting SDN-enabled gateway functions: In the context of evaluating IoT networks and network management features, SDNs have become a promising form of technology for enhancing the programmability, resiliency, and security of an IoT network [
37]. SDN-enabled gateway functions are adopted to execute advanced gateway functions. The control commands of remote or cloud servers are managed at the edge server and sub-server for execution at the edge network. In the proposed model, the developed policy framework defines the SDN-enabled gateway functions.
3.2.5. ELSGP Operational Flow and Policy Framework
Connectivity, privacy, security, adoption with open standards, device and data heterogeneity, and interoperability are the key concerns for the evaluation of IoT domains [
40]. We have developed a prototype of a policy framework based on the above-mentioned key concerns of IoT domains. We focused on the IIoT domain for the development of the policy framework. To demonstrate and execute the policy framework functions in the proposed model, we developed algorithms with the main functions of the designed ELSGP.
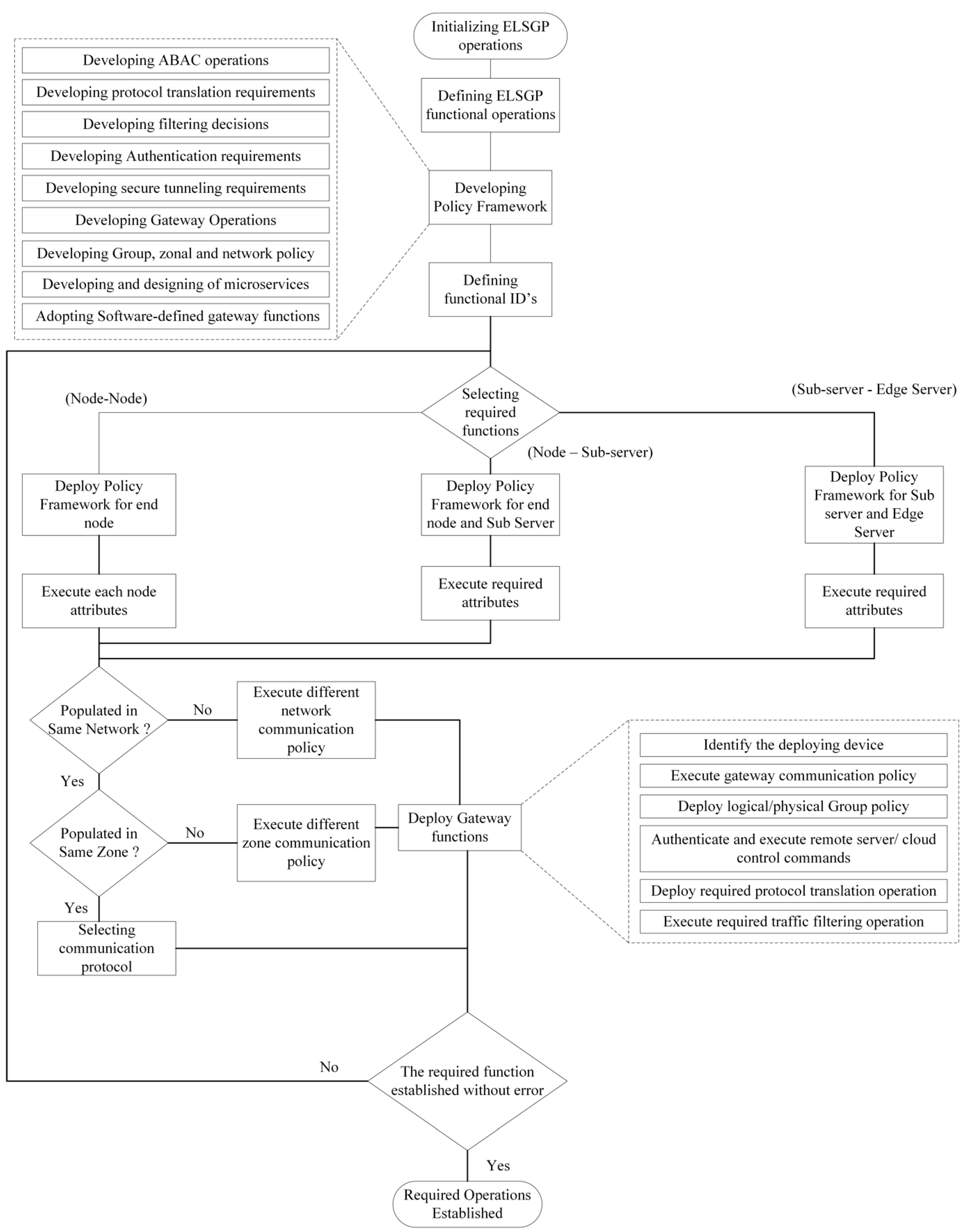
In
Figure 3, we present a flowchart of the used ELSGP operational streams. The ELSGP operations followed the developed policy framework. The flow of the policy framework execution is illustrated, along with several identical operations, which include the following: developing ABAC operations; defining protocol translation requirements and operational flow; transmitting traffic filtering decisions; authentication requirements; secure tunneling requirements; the deployment process of the software-defined gateway functions; defining and developing gateway operations (if software-defined gateway functions are not deployed); developing group, zonal, and network policies (depends on the executing model; here, we have considered our proposed model); and designing and developing µs.
The policy framework deployment depends on the nature of the device. Our developed model contains three types of devices at the edge layer: end devices (end IoT devices like sensors and actuators), a sub-server, and edge servers.
Dynamic policy generation, adjustment, and enforcement are currently being researched for the deployment of various software-defined functionalities [
41]. To alleviate the critical challenges via the use of the designed ELSGP protocol, a policy is dynamically deployed on each node and communication channel based on the predefined modular functions, functional IDs, and device IDs.
3.3. Design of ELSGP
The ELSGP was designed with six basic functions: attribute-based access control, authentication, dynamic load balancing and distribution, dynamic interoperability function, traffic filtering, and secure Tunneling. Algorithms were developed based on the functions of the proposed ELSGP.
3.3.1. Authentication
In the edge server gateway, several security operations need to be processed and validated at the edge layer [
42]. Edge-based authentication will increase data communication security among the nodes [
18]. Untrusted request management is one of the security operations that needs to be conducted before processing the generated data from an end node [
42].
The proposed ELSGP authentication process is designed with three parameters: MAC, DID, and an access token. In this protocol, to enhance security and access control, every operating device in the IoT system network will have multiple DID, which a sub-server will manage. An edge server will manage the access token. The DID will be allocated dynamically depending on the system security requirement. A single DID will expire depending on the defined operating time to authenticate one or more operational request(s). In this scenario, the DID can be allocated dynamically, and the dynamically deployed device ID is denoted as DDID. An AND operation between MAC and DID/DDID will authenticate the node requests and the node-generated data. IoT device communication WITHIN a logical group or a system zone will be validated via MAC, DID/DDID, and the access token (determined depending on system security level and lightweight weight performance requirement).
The authentication process is facilitated via the use of two algorithms. The first algorithm is for access token distribution and validation, and the second algorithm calls the described functions in the access token distribution and validation algorithm to the authentication algorithm. The authentication process cannot be independently conducted, but it depends on the participating protocol(s) to finalize the authentication process (Algorithms 1 and 2).
| Algorithm 1 Access Token Distribution and Validation |
F(ATD)//Defining Access Token Distribution function F(ATV)//Defining Access Token Validation function DID, ZID, NID//Defining Device ID, Zone ID, and Network ID F(DDID)//Defining function for Dynamically defined device ID Get_Source ()//Function for Identifying source operating device Get_Destination ()//Function for Identifying destination operating device Initialize F(DDID)//Operation at Sub-server Step A: Get pattern Define DDID Bitstream format Step B: Set DDID Generate DDID Allocate DDID Step C: Reset DDID Define Reset Period//the reset function triggering interval Repeat {Generate DDID Allocate DDID} Initialize F(ATD)//Operation at edge server Step A: Get_Source () Get DID/F(DDID) Get ZID, NID and MAC Step B: Get_Destination () Get DID/F(DDID) Get ZID, NID and MAC Step C: Generate AT//Access token (AT) generating operation Re-Generate AT Step D: Distribute AT//(AT) distributing operation Sync regenerated AT Initialize F(ATV)//Operation at edge server Step A: Verify AT Timestamp Step B: Verify AT Bitstream Step C: Validate AT If Step A AND Step B = True Else validation unsuccessful
|
It is essential to establish a trust relationship between an end node and a server to validate the generated traffic from a trusted device. Our developed access token validation and distribution technique can be an effective solution to establish a strong trust relationship between the server and the end IoT nodes. The end devices are allocated with the device ID. Depending on the system preference, the allocation can be either statically user-defined or dynamically system-defined. For dynamic device ID allocation, a sub-server operation, the function F(DDID) is used. The second function, F(ATD), is for access token distribution, an edge server operation. The third and the final function of the algorithm is to validate the distributing access token. The two main steps of this function are to verify the timestamp of the received and generated access token and verify the bitstream.
The bitstream of an access token is predefined but should not be identifiable by an end device or an operating sub-server. The access token bitstream can be verifiable at the edge server, which is expected to enhance the trustworthiness between the transmitting devices without additional computing requirements at the end device. In Algorithm 2, function F1_Auth is initialized for establishing the authentication and protocol translation functions. F1_Auth executes the access token distribution, validation, and dynamic device ID allocation functions, as presented in Algorithm 2.
This authentication process is only for authenticating end devices and the generated traffic from the nodes (not the user). User authentication will be performed with the used protocol.
| Algorithm 2 Authentication and Dynamic Interoperability functions |
F1_Auth () // Defining Authentication function F2_IO () // Defining interoperability (IO) function F(P) // Defining protocol translation function deployment_id // unique deployment id as µs identity P// operating protocol Initialize F1_Auth Initialize F(ATD) // For both server and client Initialize F(ATV) Validate DID, ZID, NID // For both server and client Initialize F(DDID) // If the system authentication requirement allowed If Check result is TRUE Authorize device Authorize generated Traffic Check IO requirement If check returns True Initialize F2_IO () Get system configuration information Get deployment_id Request µs // from cloud or remote server Get µS// operation at edge server, getting the requested µs Deploy µS //Deploy µs operation at Sub-server Initialize F(P) If F(P) = Success Get P //The operating communication protocol(s) P Get entities of the operating protocol Authorize protocol translation service Else stop translation function to find protocol entities Else stop IO function Else Reject Authentication request
|
3.3.2. Dynamic Interoperability Function
In a real IIoT environment, many communication protocols and operational standards are outlined, which makes interoperability and scalability more challenging [
43]. Recent research has uncovered several solutions to the interoperability problem, including protocol proxy, protocol translation, and middleware or MiddleBridge [
39,
44,
45].
Example Scenario
An IIoT system can be operated via the use of various protocols, such as CoAP, MQTT, REST, AMQP, HTTP, HTTPS, WebSocket, and so on. In this sample scenario, we assume an IIoT system is operated with A and B protocols. Protocol A complies with advanced encryption, where the computational requirement is much higher than the maximum operational requirement of the end devices. Therefore, a much lighter protocol, protocol B, is used for the end devices. Various portions of the edge layer of the system are operated with some legacy solution. An edge server converts the transmitted traffic between protocols A and B.
The existing problems of the IIoT system include the fact that the edge layer is vulnerable to low-security exposure, requires massive operational tasks for translating the protocol, is hugely complex in terms of system management and maintenance (not dynamic), and makes it very hard to adopt safer and new technology due to the legacy solutions. The system requirement is to mitigate these existing problems.
Existing solutions: Middleware or MiddleBridge is hardware that works as a protocol converter. However, the middleware solution is mainly adaptable with network-layer protocols but not with the application layer protocols, and this is one of the limitations of middleware [
39]. Using a protocol proxy is another solution for the interrogatability problem, but the protocol proxy solution is not efficient enough in an IIoT environment wherein the number of participants is high [
39,
44]. Protocol translation can mitigate the limitations of the middleware and protocol proxy techniques. Protocol translation is required where two or more protocols (from network layer protocol to application layer protocols) are used to establish communication. This translating mechanism bridges two different protocols that can convert the proprietary aspects of the entities or the data standard of a protocol to a different protocol [
45]. Executing a large operation every time at the edge layer and securing seamless interconnection and configuration compatibility for the heterogeneous end devices can be challenging for the protocol translation.
The developed interoperability functions: The interoperability function should be secure, dynamic, and compatible with various end device configurations (including legacy solutions) while using the least amount of operational tasks possible. The interoperability operation can also securely convey remote control commands to the edge layer. The developed interoperability gateway function supports strong encryption up to the edge layer distribution point (sub-server) and complies with the enhanced lightweight security protocols when an end device communicates with a remote/cloud server (or with another end device of a different network). The implementation of these security features also depends on the adopted policy framework or the system security level and the lightweight performance requirements.
A master server (according to the proposed model, the master server is an edge server) will execute the configurations of the interoperability function. Depending on the system configuration information of an IIoT edge layer, the µs deployment will vary. All the interoperability functions will be deployed as one or many µs. Every different µs deployment should have a unique deployment ID. By sharing the system configuration information, the master server will request the deploying file, which should be stored in a remote/cloud server. For example, in the Azure cloud service, the deployment ID is denoted as a parameter named deploymentid, which is needed to execute deploy the JSON file [
46]. Once the system environment is changed, the interoperability function executes different deployment files with the associated µs. The master server deploys the µs to a designated device (according to the proposed model, the designated device is a sub-server), and the designated device executes µs to all the associated end devices.
In Algorithm 2, F2_IO is denoted as the interoperability function. The steps of initializing F2_IO are getting the system configuration information and requesting the deploying µs. If the µs discover the protocol translation requirement, the function F(P) is executed to find the operating protocol. If different protocols participate in completing the communication, then the protocol translation function F(P) requires translating theparticipating protocol entities. For example, two protocols participate to establish communication where one protocol needs to be transformed into another. The protocol translating function translates the entities of one protocol into another protocol’s entities. If one protocol establishes the communication, then the protocol translation function cannot be executed.
Referring to the above sample scenario, for the interoperability between protocols A and B, the F(P) function can be dynamically executed. The associated deployment file can be executed by obtaining the system configuration information, including the legacy solution. The deployment can be recorded with deployment ID for similar use. Repeated system management and maintenance tasks can be performed dynamically.
3.3.3. Attribute-Based Access Control (ABAC)
Every operating device can be identified with its individual identification (ID) depending on the attribute of the device, which is called the attribute tag (ATAG), to control the device’s access to a system network. The ATAG must incur a light overhead to fulfill the network bandwidth requirement(s) and the round-trip delay.
To validate the ABAC operation, an
ATAG along, with an Authentication function (
F1_Auth), will authenticate the device access request to join onto a network as shown in Algorithm 3, communicating with the other network devices, validating the generated or received data, and executing and validating the control command.
| Algorithm 3 Attribute-based access control |
F3_ABAC () // Defining Attribute based access control function ATAG // Defining Attribute TAG from Attribute policy R_F3 () // function for defining the rules from the policy Begin Initialize F3_ABAC () Initialize R_F3 () If R_F3 () = Success Check ATAG If F1_Auth () AND ATAG = True Allow traffic flow Else Reject traffic flow Else Stop F3_ABAC () Acknowledge error initialization end
|
3.3.4. Traffic Filtering
The traffic filtering function of the designed protocol is to optimize the network traffic to comply with the bandwidth requirement. Categorizing, prioritizing, and processing the generated data based on the attributes and filtering the repeated traffic are the key functions of the traffic filtering process shown in Algorithm 4.
| Algorithm 4 Traffic Filtering |
T, PT, FT, UT //regular traffic, priority traffic, flooding traffic, unknown traffic F4_TF ()// Defining the traffic filtering function Traffic_Filtering_Policy // defining traffic filtering policy TC ()// defining Traffic classifier function PF ()// defining priority function SF () // defining summery function TA ()// Traffic analyzer function Begin Initialize F4_TF () Initialize TC () If TC ()→ T = true Deploy Traffic_Filtering_Policy Elseif TC ()→ PT = true Execute PF () AND Deploy Traffic_Filtering_Policy Elseif TC ()→ FT = True Execute SF () AND Deploy Traffic_Filtering_Policy Else TC ()→ UT =True Stop UT // stop unknown traffic flow Execute TA () If TA () =False //Traffic analyzer function return Block UT Update Traffic_Filtering_Policy Else Allow UT End
|
In the traffic filtering function, transmitted traffic is categorized into four types: regular traffic, priority traffic, flooding traffic, and unknown traffic, denoted as T, PT, FT, and UT, respectively. Periodic traffic can be defined as regular traffic. At a certain interval, periodic traffic indicates the status of known events. The traffic filtering function F4_TF () is developed with four subfunctions: a traffic classifier, priority function, summary function, and traffic analyzer function. Traffic filtering policies may vary in different IoT systems. The subfunctions operate according to the rules defined in the traffic filtering policy. The traffic analyzer subfunction categorizes the transmitted traffic as unknown traffic if the nature of the traffic cannot be determined with predefined rules.
3.3.5. Secure Tunneling
The proposed protocol aims to validate internal communication (within a system zone) and external communication (with devices or servers out of a system zone). Device identity parameters, encapsulating function, and secure tunneling policies will be used to establish a secure tunnel between two nodes of different networks or system zones.
In Algorithm 5, the secure tunneling function is denoted as
F5_ST (). The subfunction
P () is initialized to establish a logical path between the source and destination devices, where several identification parameters are used for accomplishing the functional operation. Depending on the level of the secure tunneling preferences, a secure communication tunnel can be formed in three ways: a full strong encrypted state, a lightweight state, and a policy-defined state.
| Algorithm 5 Secure Tunneling |
F5_ST ()// Defining the secure tunneling function O, G, Z, N //Object, Group, Zone, and network Encap_Dcap, Enc_Dec // Encapsulation and encryption requirement value Tunnel_sec // the secure tunneling policy Encap(), Dcap (), Enc_t ()// defining encapsulation, decapsulation, encrypted tunneling functions P() // network path defining function Begin Initialize F5_ST () Get O, G, Z, N // for Source Get O, G, Z, N // for destination Initialize P () Get Logical path // between source and destination If Encap_Dcap= true // at lightweight state Initialize Encap() // For transmitting traffic Get keys// for device itself and next-hop device (from Source) Set XOR // XOR operation between the key and data O → Z → G → N //Defining encapsulation order Initialize Dcap ()// For retrieving traffic O← Z← G ← N // //Defining decapsulation order Get keys // for device itself and next-hop device (from Destination) Set XNOR // XNOR operation between the key and received data, for retrieving transmitted traffic Else Stop Encap() Stop Dcap () If Enc_Dec= true Get protocol Initialize Enc_t () End if If Tunnel_sec =true // at lightweight state Execute Tunnel_sec End if End
|
Full strong encrypted state: A full strong encrypted state is formed when the source and destination devices are connected with a strongly encrypted tunnel.
Enc () is required to outline the steps of forming a secure tunnel where the parameter
Enc_Dec is needed to define which protocol will be used for the strongly encrypted tunneling protocol, such as Secure Shell (SSH) or Secure Socket Tunneling Protocol (SSTP), an internet protocol security (IPsec). However, in an IoT environment, these protocols are not used to establish a secure connection between two devices due to the constrained nature of the IoT devices. These protocols are only used temporarily to connect with devices to execute control commands. For example, Amazon Web Services (AWS) IoT secure tunneling is formed for a short-term to set up a secure connection with a remote IoT device [
47].
Lightweight state: At a very low computing stage in which a full strong encrypted tunnel cannot be created, a secure encapsulation method can be applied to transmit traffic between a source and a destination device. In the above-listed algorithm, we presented a method of secure tunneling wherein the parameter Encap_Dcap is required to identify the lightweight state. If the channel is required to form with a lightweight state, then the parameter Encap_Dcap returns True and the subfunction Encap() is initialized. In the lightweight state, two secret keys are exchanged within the source and destination end. One key is for the source device itself and the other key is for the next-hop device (where the hop count is 1). An XOR operation is set between the exchanged key and the device-generated data frame. This process is repeated at the next-hop device but with different keys. Data encapsulation is formed using this order O → Z → G → N. Data decapsulation is for the destination, which is directed using the reverse order, followed by an XNOR operation to retrieve the received data frame.
Policy-defined state: A policy-defined state is also part of the solution, this arrangement fulfills the requirement of balancing full strong encryption and a lightweight state. Tunnel_sec defines the secure tunneling policy, which includes the participating protocol and policy that applies to the configured network segments. The policy deployment file will be defined with a unique deployment ID for future reuse.
3.3.6. Dynamic Load Distribution and Balancing
The function of dynamic load distribution and balancing depends on several parameters of the edge servers and sub-servers. The parameters are divided into two categories: load information parameters and load status parameters. The load information parameters include the number of operating sub-servers, the load threshold values for each edge server, the load threshold values for each sub-server, the health check threshold values, the task queue threshold values for each edge server, and the task queue threshold values of each participating sub-server. The health check value depends on the CPU capacity, power status, channel status, computing time, and system preference.
The load status parameters include health check current values, current load at the designated sub-server, the current task queue value of the designated edge server, the current task queue value of the designated sub-server, and identifying the sub-server(s) available for load sharing. In Algorithm 6, the dynamic load distribution and balancing function is split into three steps: obtaining the load information parameter, obtaining the load status, and defining the load balancing and distribution function.
| Algorithm 6 Dynamic load distribution and balancing |
F6_dldb ()// Defining the Dynamic load distribution and balancing function Step A Get load information parameters Nss //number of sub-servers L //load threshold value for edge server l //load threshold value for sub-server ht //health check threshold values TQt //Task queue threshold value of an edge server tqt //Task queue threshold value of a sub-server Step B Get load status parameters h //current health check values cl //current load at designated sub-server CL //current load at designated edge server TQ //Current task queue value of the designated edge server tq// Current task queue value of the designated sub-server ls //available sub-server(s) for load sharing Step C Balance load Initialized F6_dldb() if (CL ≥ L or TQ≥ TQt ) Calculate ΔL // ΔL ←(CL-L) Select ls If cl <l AND ht <h AND tq<tqt Endif Distribute ΔL∝ Δl or ΔTQ∝ Δ tq //ΔTQ←(TQ-TQt) and Δtq←(tqt–tq) Update load parameters Update status parameters Else repeat Step c
|
In step C, the load balancing and distribution function is defined. If a server exceeds its load threshold value or task queue threshold value, then F6_dldb () is initialized. A sub-server is selected for load sharing if the current load value is less than the threshold value AND health check values are better than the threshold value AND the current task queue value is less than the threshold value. The exceeded load of an edge server ΔL distribution is proportional to the Δl (difference between the threshold load and the current load of a sub-server), and ΔTQ is distributed with the proportion of Δtq. The load information and status parameters are updated according to the executed modifications.