Abstract
In energy detection for cognitive radio spectrum sensing, the noise variance is usually assumed given, by which a threshold is set to guarantee a desired constant false alarm rate (CFAR) or a constant detection rate (CDR). However, in practical situations, the exact information of noise variance is generally unavailable to a certain extent due to the fact that the total noise consists of time-varying thermal noise, receiver noise, and environmental noise, etc. Hence, setting the thresholds by using an estimated noise variance may result in different false alarm probabilities from the desired ones. In this paper, we analyze the basic statistical properties of the false alarm probability by using estimated noise variance, and propose a method to obtain more suitable CFAR thresholds for energy detection. Specifically, we first come up with explicit descriptions on the expectations of the resultant probability, and then analyze the upper bounds of their variance. Based on these theoretical preparations, a new method for precisely obtaining the CFAR thresholds is proposed in order to assure that the expected false alarm probability can be as close to the predetermined as possible. All analytical results derived in this paper are testified by corresponding numerical experiments.
1. Introduction
Cognitive radio [1,2,3,4] is a potential technology to realize flexible and efficient usage of frequency spectrum, and is a promising approach in dealing with the spectrum scarcity in future wireless communication networks. However, a key step to make it a reality is to effectively address some estimation issues, such as transmitter power estimation [5] and monitoring in wireless networks. Spectrum sensing is among the most important ones, which aims to detect whether licensed spectrum is accessible. Some existing spectrum sensing methods in the literature are by way of matched filtering, waveform-based sensing [6], cyclostationary-based sensing [7,8], and energy detection [9,10,11,12], etc. Clearly, energy detection is the most popular way to perform spectrum sensing.
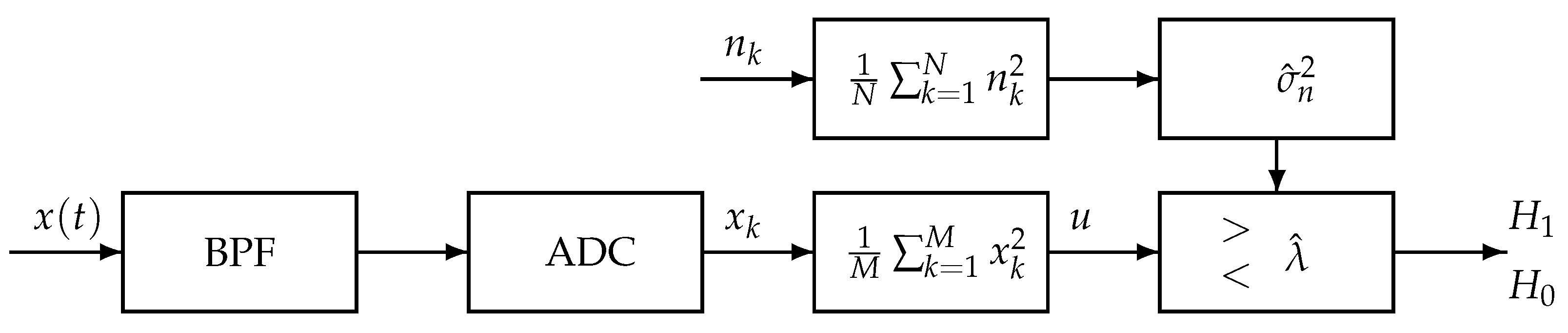
In this paper, the energy detection scheme is carried out under the framework shown in Figure 1, which is a generation of the detection scheme described in [13]. The similar part is that the input signal is first passing a Band-Pass Filter (BPF) and next the signal is digitized by an analog to digital converter (ADC), then, a simple square and average device is used to estimate the received signal energy. For a real input signal, the estimated energy, , is then compared with a threshold, , to decide if a signal is present () or not (). The threshold for energy detection used in [13] is constructed using the information of noise variance and signal-to-noise ratio. In the proposed framework shown by Figure 1, the noise variance is estimated from another available channel, , and then the estimated noise variance is used to construct the detection threshold. This setting of detection is more applicable, since the real complicated noise is derived from various sources and thus its variance may change from time to time. Though the method using estimated noise variance to construct the threshold has been proposed in the literature, e.g., [14,15,16,17], they did not analyze the effect caused by using the estimation variance. An interesting double threshold detection method is presented in [18] using exact noise variance to separate three cases of detection: spectrum free, spectrum occupied and not certain. In this paper, we will calculate the expectation of the detection event by using the estimated variance and thus a much more accurate threshold may be derived for detection.
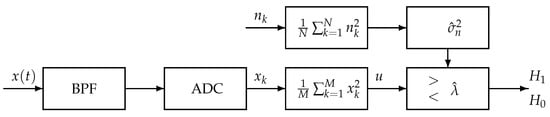
Figure 1.
Energy detector using estimated noise variance by available similar channel. The noise variance is estimated by from the other available similar channel. Then the empirical average energy is detected by principle constant false alarm rate (CFAR) or constant detection rate (CDR) with the threshold using the estimated noise variance .
The threshold is determined typically based on two principles: constant false alarm rate (CFAR) and constant detection rate (CDR), which will be further explained in Section 2. In both cases, the noise variance (power) is generally supposed to be known to determine the threshold, as shown in [19,20]. However, noise variance may vary significantly in both temporal and spatial dimension due to the fact that the total noise is composed of thermal noise, receiver noise, and environmental noise. Generally, one may take the estimated noise variance, to some certain extent, as the noise variance in the calculation of the threshold in energy detection accordingly. The following two examples are given in [13] for practical performance of energy detection. One example is that a certain channel is reserved for special applications by spectrum regulators. The special channel can only be used to estimate noise variance, and can never be used by a secondary user. For instance, channel 37 (from 608 to 614 MHz) in FCC is used in very few occasions but for radioastronomy. Another example is the detection of DTV pilot signals, in which the noise variance can be estimated from some frequency bin not corresponding to the pilot frequency under the low SNR scenario. In both examples, a threshold is computed from the estimated noise variance based on CFAR or CDR principles. Then, the threshold is used in the subsequent detection to determine whether a signal is present or not by comparing with the detected energy from the channel of interest or from the known pilot frequency bin.
What are the encountered problems for detection using estimated noise variance? For CFAR principle, the resultant false alarm rate may not be guaranteed as the preassigned level . Since the resultant rate is actually a random variable. Indeed, the estimated noise variance is a random variable. Thus the CFAR threshold, denoted by , using variance is also a random variable, which implies that the resulted probability of false alarm for energy detection, denoted as , is also a random variable. Obviously, it is generally impossible to expect that equals the preassigned . Let us show a simple example here for demonstration of the theoretical results. Let , , if we want to set a threshold by the standard energy detection method (replacing the noise variance by its estimation) to guarantee , the preassigned false alarm rate to set the threshold should be cautious and it is found by Theorem 1 that it should be approximately , which is much smaller than the desired rate . However, if the sample number N increases to 100, the preassigned false alarm rate could be . As the sample number N increases, the preassigned rate approaches to itself.
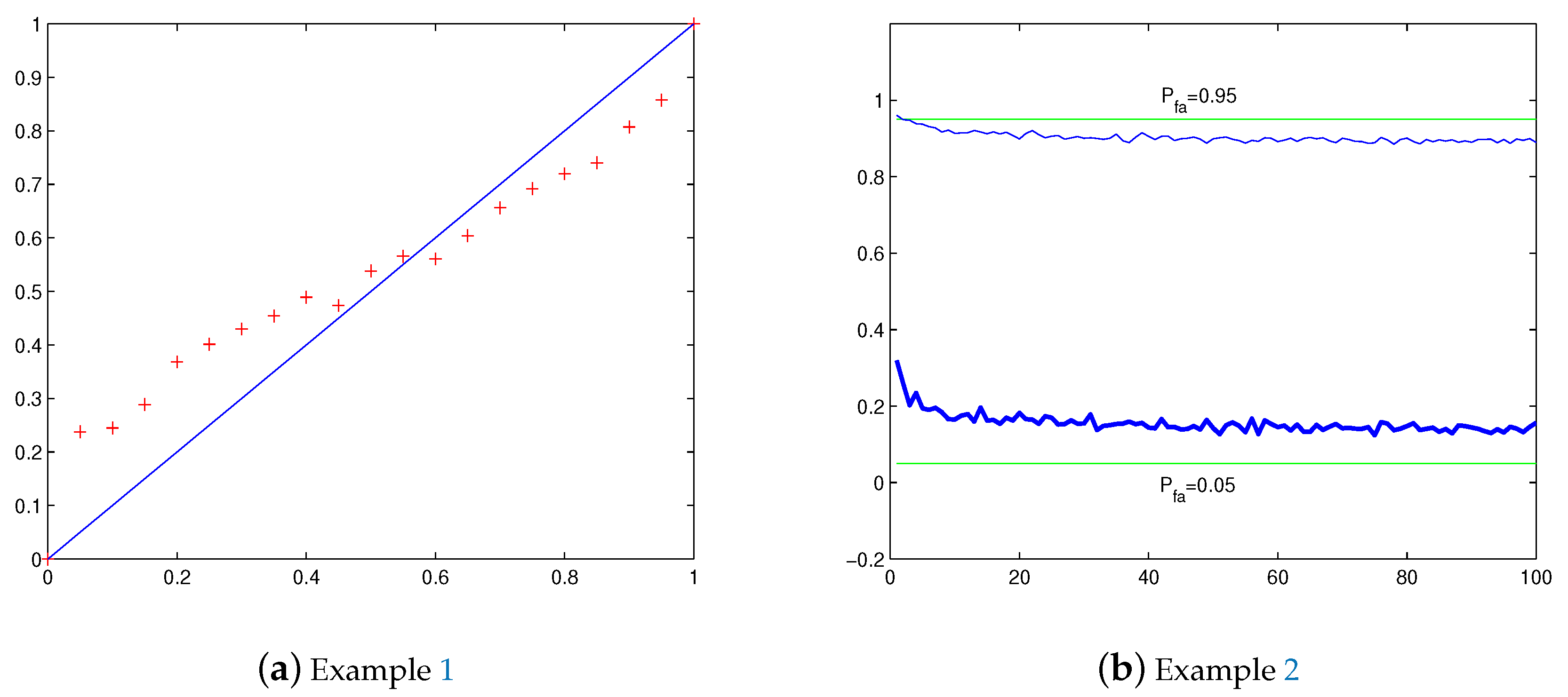
In this paper we analyze the difference between and . It is found in [13] that the expectation of , which is actually calculated using an approximated random variable therein, is greater than for some predesigned , say, , which is shown in Figure 2 therein. Hence, to make a proper choice of the threshold, it is critical to answer the following questions:
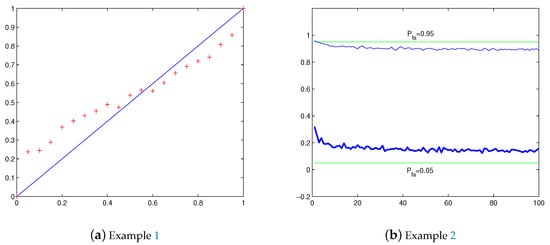
Figure 2.
Plots of Examples 1 and 2. (a) Average false alarm probability vs. Pfa = 0, 0.05, …, 1. (b) vs. M = N = 1, 2, …, 100
- What is the expectation of ?
- What is the variance of ? (equivalently, the second moment of )
- What is the limitation of for a fixed as N, the number of samples used to estimate the noise variance, and M, the number of samples used to perform detection, tend to infinity?
Although a part of these issues, e.g., the first and third for the case of , have been tackled and initially studied in [13]. Yet, the study failed to find an explicit form for , which leaves a large space for further advance. Motivated by this, we investigate the problems by explicitly describing and establishing an upper bound for , which well answers the first issue and the second partly. Moreover, with an approximation of based on an estimated distribution of the resulted threshold , the third question is analyzed for some special cases. Nevertheless, some new CFAR thresholds for energy detection are proposed by confirming that equals to the predesigned false alarm probability .
The rest of this paper is organized as follows. The model setting and hypothesis testing of energy detection by a known noise variance is introduced in Section 2, where the CFAR thresholds are derived in an exact way and an approximating way, respectively, by assuming Gaussian signals. Section 3 numerically investigates the selection of CFAR based on an estimated noise variance to set a CFAR threshold. In Section 4, we analyze some basic statistical properties of the resulted probability of false alarm given by (21) along with , the estimated case given by (24). Specifically, we come up with explicit descriptions for the expectations of and by Theorems 1 and 3, respectively, and some discussions on the corresponding properties. In Section 5, upper bounds on and are derived by Theorems 5 and 6, respectively, due to the difficulty in finding the exact explicit forms by any known special functions. In Section 6, new CFAR thresholds are proposed, aiming to assure that or equals to the predetermined false alarm probability . Concluding remarks and future research are listed in Section 7. All analytical results derived in this paper are regarding CFAR thresholds. However, as a matter of fact, similar results also hold for the CDR case.
2. Model Setting and Hypothesis Testing with Known Noise Variance
Spectrum sensing is an important task for a secondary user in a cognitive radio network in order to determine whether a licensed band is currently occupied by a primary user or not. This is can be formulated into a binary hypothesis testing problem: [13,20]:
where , , and represents the primary user’s signal, the noise, and the received signal, respectively. The noise is assumed to be Gaussian random process of zero mean and variance , whereas the signal is also assumed to be iid Gaussian random process of zero mean and variance of . The signal to noise ratio is defined as the ratio of signal variance to the noise variance
The test statistics generated from the energy detector as shown in Figure 1 are
Under the hypotheses and , the test statistic u is a random variable whose probability density function (PDF) is chi-square distributed. Let us denote a chi-square distributed random variable X with M degrees of freedom as , and recall its PDF as
where denotes Gamma function, given in (15).
Clearly, under hypothesis , ; and under with . Thus, the PDF of test statistics u, given by test, is
When M is sufficiently large, we can approximate the PDF of u using Gaussian distribution:
For a given threshold , the probability of false alarm is given by
where is the upper incomplete gamma function in (16). In addition, its approximating form of corresponding to distribution (6) for large M is
where is defined in (14).
If the required probability of false alarm rate () is predetermined, the threshold () can be set accordingly by
where is the inverse function of . Furthermore, for the approximation case:
where is the inverse function of .
Similarly, under hypothesis , for a given threshold , the probability of detection is given by
where is the upper incomplete gamma function. So, we derive the threshold to achieve a target probability of detection at the required signal level or SNR:
Furthermore, the corresponding approximating case is
The probability of false alarm is fixed to a small value (e.g., 5%) if it is required to guarantee a reuse probability of the unused spectrum, and meanwhile the detection probability should be maximized as much as possible. This is referred to as constant false alarm rate (CFAR) principle [13,19]. On the other hand, if it is required to guarantee a non-interference probability to the primary users, the probability of detection should be set to a high level (e.g., 95%) and the probability of false alarm should be minimized as much as possible. This is called the constant detection rate (CDR) principle [13,19]. By the similarity of (9) and (12), it is clear that the derivation of the threshold values for CFAR and CDR are similar, so the analytic results derived by assuming CFAR based detection can be applied to CDR based detection with minor modifications and vice versa. From now on, we will mainly focus on the discussion of CFAR threshold, since similar conclusions follow directly by minor changes.
Let us introduce some special functions and related notations for ease of reading. The complement of the standard normal distribution function is often denoted as , i.e.,
and is simply referred to as Q-function, in the context of engineering. This represents the tail probability of the standard Gaussian distribution. The Gamma function and regularized upper incomplete Gamma function are defined as
for , respectively. The more complicated Beta function and Beta distribution function are respectively listed below
for , and . A well-known relation between Beta and Gamma function is
We simply use , and to present the inverse functions of , and respectively.
3. Energy Detection Performance Using Estimated Noise Variance
As already mentioned in the introduction, the exact noise variance is generally unavailable; even historic records are sometimes out of use, due to timely changes of thermal conditions and environmental conditions, and so on. So, practically the threshold values in (9) and (12), or the approximating cases (10) and (13), are usually calculated from an estimated noise variance to a certain extent. In this section, we numerically study the performance of energy detection by replacing the noise variance in these formulas by an estimated noise variance . Specifically, we investigate the difference by numerical experiments.
We want to find out the performance of energy detection by simply replacing the exact noise variance in (9) and (12) with the estimated noise variance , i.e., calculate the thresholds as
and then by (7) and (11) respectively the resulted performance probabilities are
Similarly, in the approximating case, the CFAR threshold by replacing with the estimated noise variance is
which is corresponding to (10). Thus the resulted performance probability is
Due to the CFAR and CDR principles having an essentially similar structure, we actually investigate the CFAR case only, i.e., by formulas (19) and (21) to check the evolvement of as the predetermined varying from 0 to 1, or for a fixed as the number of samples tends to infinity. A technical treatment of estimating in the following experiments is replacing it by the corresponding empirical average over a class of sample paths.
Example 1.
We first investigate the difference between and the predesigned as changes along the interval with M and N fixed. In model (1), let and . Consider a given false alarm rate , we use iid Gaussian noises to estimate the variance , and then substitute in (19) to derive the threshold . The energy detection performance by the obtained threshold is evaluated by the corresponding false alarm probability by (21). As aforementioned, it is important to check whether . In order to estimate , repeat independently the aforementioned procedure and calculation for 600 times to calculate the average false alarm probability
to serve as an empirical approximation of , where denotes the calculated probability along the i-th sample path . We let , totally 21 points, to do an experiment. The result is shown in Figure 2a, where is plotted by ’+’. We see that when is close to 0, while when is near 1.
Example 2.
This time we investigate the difference between and the predesigned with a fixed as tends to infinity. Still let in model (1). With the same procedure of Example 1 to calculate by 600 independent sample paths. We let and respectively, and to do an experiment. The result is shown in Figure 2b, where for is plotted by thick line, and by ordinary line. We see that when , and when . Furthermore, it seems that , and thus , for a fixed has a limitation as tends to infinity.
The phenomena discovered by these numerical experiments will be explained in the next two sections by developing an exact formula for and an upper bound for its variance. Nevertheless, the case for approximating CFAR threshold has also been analyzed meanwhile.
4. Calculations of and
In this section, we will derive explicit formulas for the expectation of given by (19) and (21) with respect to predesigned false alarm probability , and the expectation of given by (23) and (24). Moreover, some basic properties are deduced analytically and numerically, which further explains some discoveries in the former section.
Denote as the estimated noise variance from the reference channel (Ch) known to be vacant, where N is the number of samples used to estimate noise variance. Denote u by (3) as the energy detection test statistics from the channel of interest (Ch). Here we assume the number of samples, as aforementioned, used to perform spectrum sensing is M.
Notice that the estimated noise variance, , is a random variable itself, the probability of false alarm or detection is conditioned on one observation of the random variable, e.g., y. Let us consider the case of CFAR. By (7) and (19), the probability of false alarm can be written as
where is the threshold value calculated from (19) by given false alarm probability , and y is a realization of random variable Y.
Since given by (25) is a random variable depending on y, it is natural to consider its expectation with respect to y. Let us summarize a theoretical result regarding as a theorem below.
Theorem 1.
Proof of Theorem 1.
By integrating (25) over the PDF of Y, the expected probability of false alarm can be derived as
where we use the fact in the second step. Letting , we derive
Differentiating by x, we have
Introduce transformation . By the fact that , we proceed as
where is Beta function in (17). Integrating (30) over , by noticing for in (27), we derive
Let . The integral turns to be
where is the Beta distribution function in (18). In the second step, we use the transformation . □
Based on Theorem 1, we conclude a further theoretical discovery as the following theorem, which is actually being pointed out in the numerical experiments of the former section.
Proof.
Let to be brief. Introduce a function . By (26), we have
where . By the fact , i.e., , we have used the following calculation
in the above second step. Note when , so by (34). Note further if , by (34) we have . Together with the fact that , we know that is negative somewhere.
To find more information about the sign of , we recall the famous Stirling’s approximation formula for Gamma function (see page 400 of [21]):
where , and an inequality (see page 88 of [21]):
where and .
By (36),
Together with the facts that and
for , we declare that the derivative of at p, corresponding , i.e., .
On the other hand, by noticing the increase rates of function and in (34), we know that at most has two zeros in . Hence, we conclude that starts as a positive value , then decreases to a negative minimum, and finally increases to a positive value . This means that starts as 0 increases to a positive maximum, and then decreases to negative minimum, finally increases to 0, which is just the assertion desired. □
Now let us consider the counterparts for the approximating threshold of CFAR criterion, i.e., the expectation of given by (23) and (24).
Remark 1.
Based on Theorem 3, we now consider the limitation of as M and N tend to infinity for fixed . By (37), for a fixed , we have
if . Thus, if tends to infinity, we derive the discovery in [13]:
These properties also hold for since the distribution of tends to be the distribution of .
Proof of Theorem 3.
Integrating (24) with respect to y, and noticing that , we have
Letting and . we derive
For simplicity, introduce and . Differentiating over x, we get
where and hereafter denote A sometimes for brief. It follows
In the second step we use the transformation to simplify the expression.
Let us study the function before introducing a transformation. Clearly,
Note and denote , we derive for , and for . Thus, has one unique minimum at . Hence, increases from the minimum to as , and increases from the minimum to as .
Now introduce a transformation for (44) as . Based on the above analysis for function , if the integration region , then the region for w turns to be ; otherwise, the region for v can be divided into two monotonic parts as and , and thus, the regions for w are and . Then, for the case , by the fact that for in (41), we proceed (44) as
For the case , similarly,
These finish the proof. □
Corresponding to Theorem 2, we also have:
Theorem 4.
There exists a such that
where can be calculated by (37). Furthermore, the critical point is close to for large .
Remark 2.
By Theorem 4, we know that at a point close to . This property holds for since the distribution of tends to that of .
Proof.
Let to be brief. Introduce a function
where . So, we have
where , , , and . Clearly, is corresponding to , thus, . Together with the facts that and , we know that there exists a such that . When , corresponding to , clearly,
for , we have , and thus for , which finishes the proof of the first assertion.
By (38), i.e.,
we have
Thus, for large M and N, we know that the zero of , i.e., , is close to , which is corresponding to . This finishes the second assertion. □
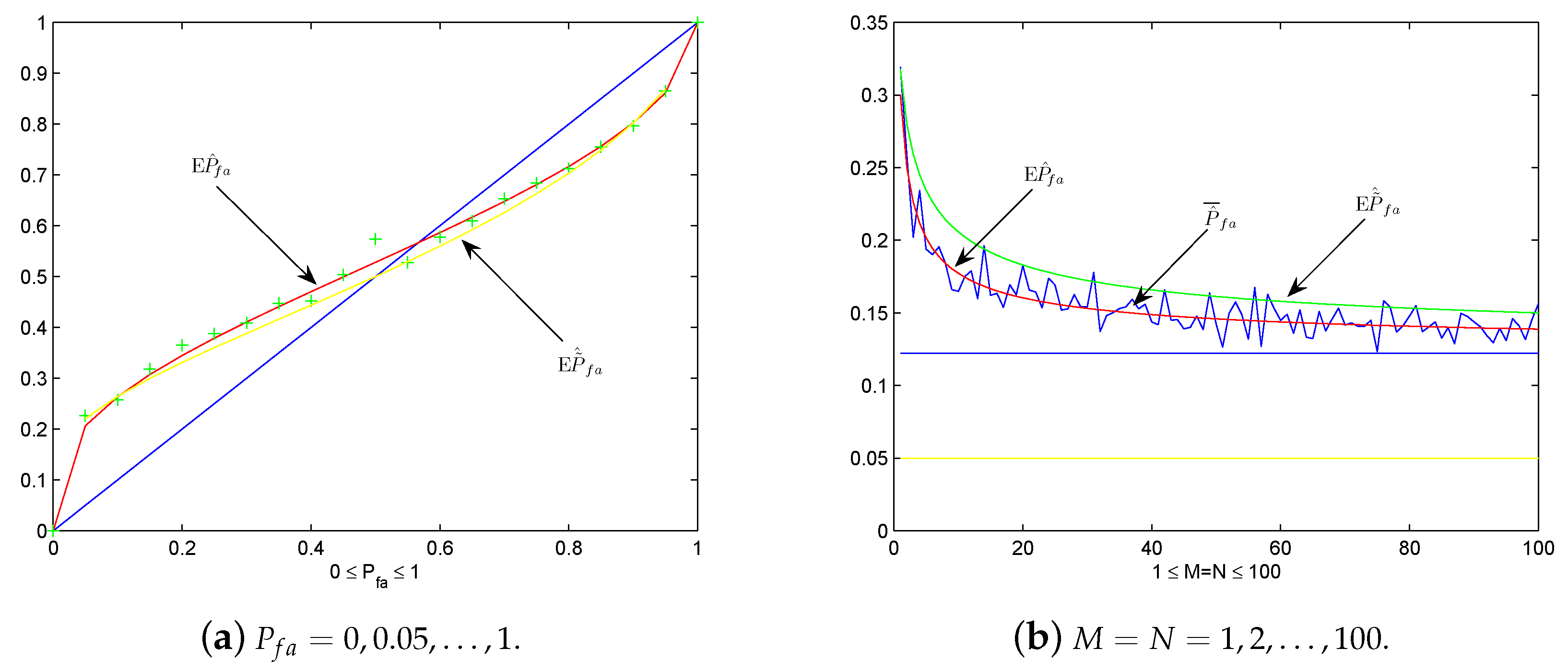
Now let us do some numerical experiments to detect the practicality of these theoretical results. Under the same setting of Example 1, we plot by ’+’, and and as the predesigned in Figure 3a. We see that serves better as the mean value of than , which coincides with the fact that the latter is an approximating case. If is sufficiently large, approximates close as desired. Let us analyze more deeply the graphs in Figure 3a by the discovery in Remark 1. Let , the approximation of and is when is large. Clearly, by noticing . Graphically, this means the curves of and with respect to pass across the diagonal line in Figure 4 around for sufficiently large . If , i.e., close to 0, then . In this case, the graphs of and with respect to is close to the diagonal line.
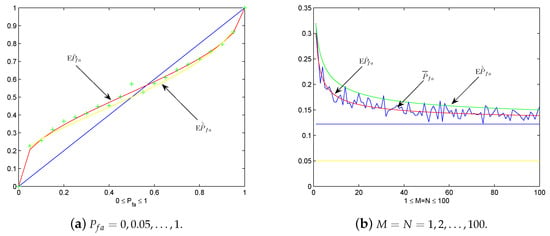
Figure 3.
The plot of by ’+’, and under setting of Pfa = 0, 0.05, …, 1 and M = N = 1, 2, …, 100. (a) The plot of by ’+’, and vs Pfa = 0, 0.05, …, 1. (b) The plot of , and vs. , under Pfa = 0.05.
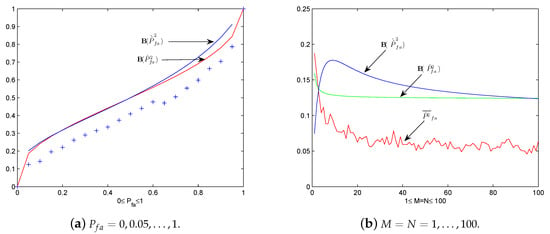
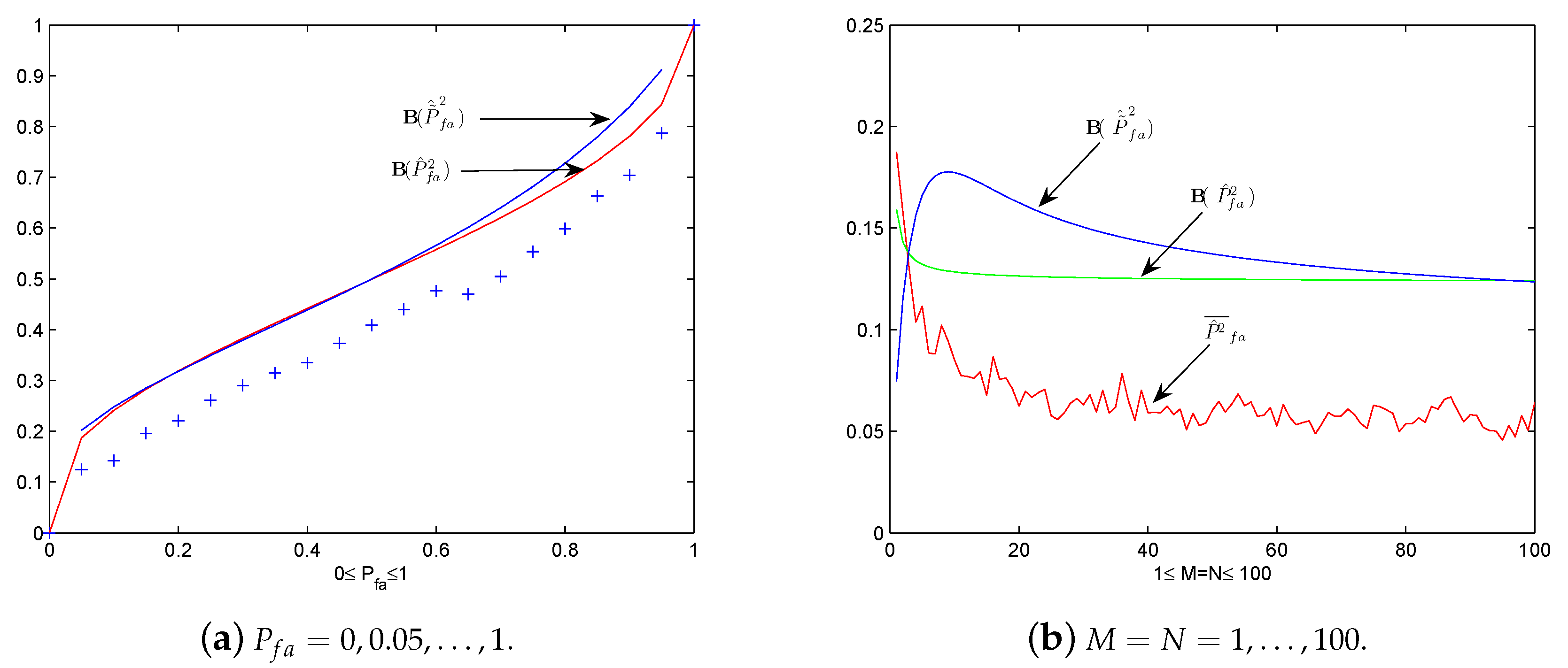
Figure 4.
The plot of approximation of and and their upper bounds. (a) The plot of by ’+’, and vs. = 0, 0.05, …, 1. (b) The plot of by ’+’, and vs. .
On the other hand, in Figure 3b we plot , and under the same setting of Example 2 for . Again, we see that serves better as the mean value of than the approximation . As changes from 1 to 100, and seem tend to the value of the upper straight line in Figure 3b, i.e., , which justifies the observation in Remark 1.
In conclusion, the theoretical discoveries in the above four theorems and two remarks have been verified in these numerical experiments.
5. Upper Bounds of and
After the calculations of and , it is meaningful to have some information about the average deviations of and from their expectations. Technically, it is found very difficult to find explicit forms for and by existing special functions. We have to try to find some upper bounds instead. By the facts that and , we have obvious upper bounds as
Thus, the more sharp upper bounds of and should be less than and respectively. For this target, let us list two propositions and two lemmas for technical preparation.
From the proofs of Theorems 1 and 3, we actually have the following two general results respectively.
Proposition 1.
For a real differentiable function ,
where and , .
Proposition 2.
For two real differentiable functions and ,
We need two more inequalities regarding Gaussian and Gamma distributions respectively as follows. The proofs have been listed in Appendix A.
Lemma 1.
For and ,
Lemma 2.
For ,
By Proposition 1 and Lemma 1, we develop an upper bound for in the following.
Theorem 5.
Let , then an upper bound for is
Remark 3.
Proof of Theorem 5.
By (25), we find an upper bound for the the expectation of squared probability of false alarm as
where we use the notations: and . By Lemma 1, for we derive
In order to use Proposition 1, introduce a transformation . Then, we proceed (53) as
Clearly, corresponding to Proposition 1, in (54). Thus, by Proposition 1, we derive
□
By Proposition 2 and Lemma 2, we develop an upper bound for in the following.
Theorem 6.
Let , then an upper bound for is
where and .
Remark 4.
Proof of Theorem 6.
Now let us do two numerical experiments corresponding to examples in Section 3 to check how the two upper bounds work. The average squared false alarm probability is calculated over 600 sample paths by
to serve as an empirical approximation of , where denotes the calculated probability along the i-th sample path . Under the same setting of Example 1, we plot by ’+’, and as changes from 0 to 1 in Figure 4a. It seems that is the better one, especially in the case . Under the same setting of Example 2, by letting we plot , and for in Figure 4b. The two upper bounds seem not quite satisfied since both of them do not tend to as M (or N) tends to infinity.
6. New Thresholds Based on and
In this section we derive new thresholds to guarantee the expectation or in the approximation formula version, , by the help of Theorems 1 and 3, respectively.
The threshold given by (19) constructed by using estimated noise variance is actually a random variable itself. This leads to the fact that the resulted false alarm probability given by (21) is generally different from the predesigned probability . It is found in Theorem 1 that the expected value of is probably different from the predesigned probability . For instance, let and , as in Example 1, by Theorem 1,
for the threshold given by (19), i.e., where is estimated by independent observations. Obviously, the resulted expectation is much bigger than the predesigned false alarm probability . This means the threshold is selected too low to guarantee the predesigned false probability in an average sense. If we want the expectation , the preassigned probability for energy detection should be suitably smaller. Next we analyze how small the preassigned probability should be and then derive a new threshold to guarantee .
For a given alarm level , say , in order to derive a threshold to guarantee , it is found that the x in (26) should be
by solve the target equation. Then by described in Theorem 1, the preassigned initial threshold for energy detection should be . In other words, due to the fact that the noise variance is estimated by finite samples of noise, if we still want the false alarm rate less than , we may need to be more cautious to select the threshold for energy detection. For the simple example discussed above, i.e., , , if we want , the preassigned false alarm rate should be approximately , which is much smaller than the desired rate . However, if the sample number N increases to 100, the preassigned false alarm rate could be . As the sample number N increases, the preassigned rate approaches to itself.
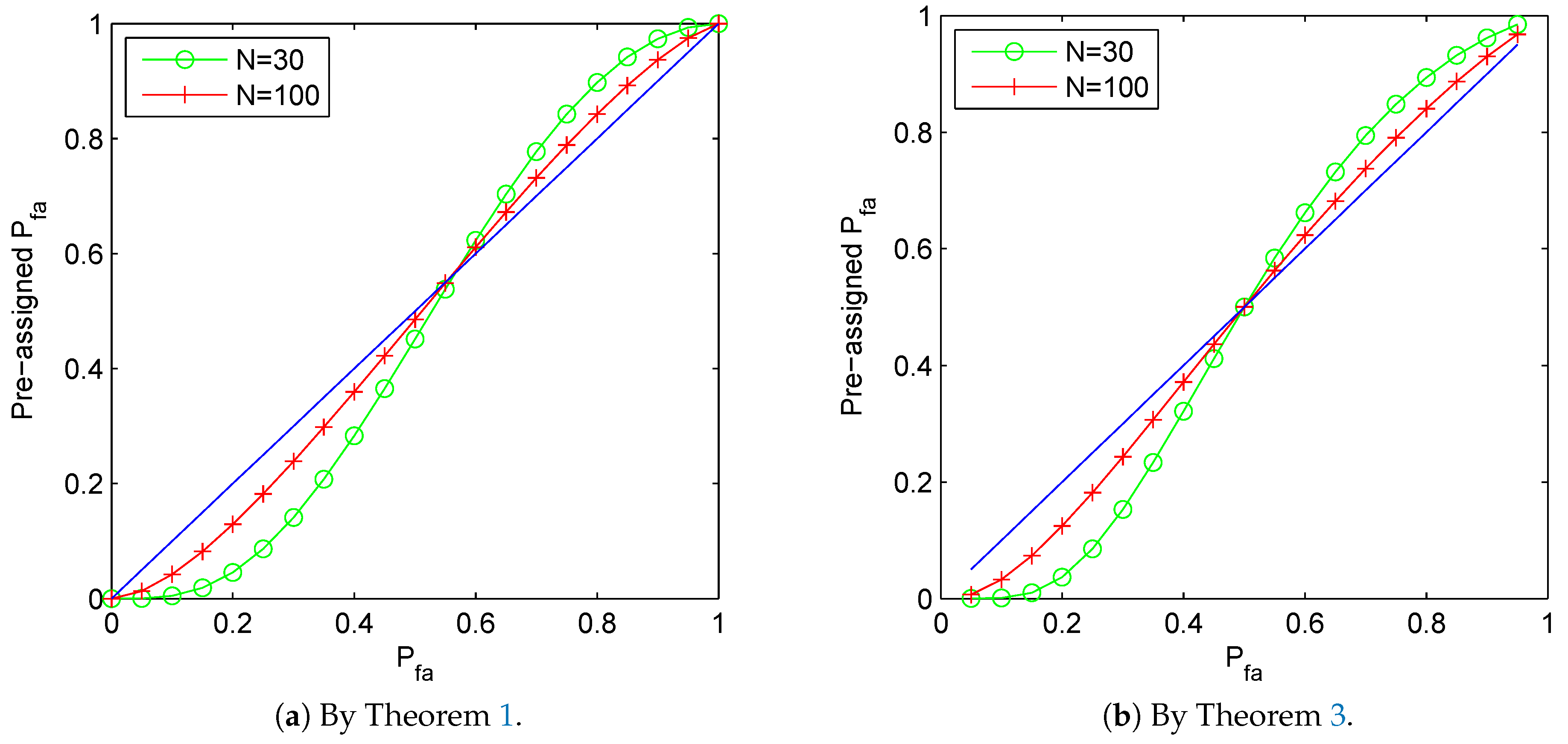
It is plotted in Figure 5a how the cautious preassigned false alarm rate should be under the setting and , for the sequence . It is clearly shown in the figure that the preassigned false alarm rate should be much smaller than the value is designed to be. As the sample number N for estimation increases, the preassigned false alarm rate approaches to the value of .
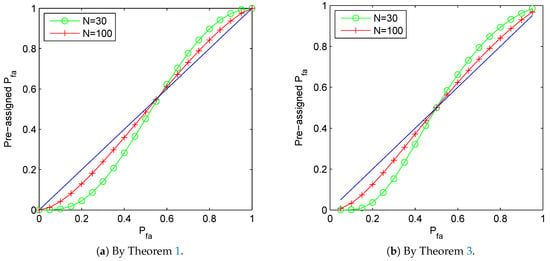
Figure 5.
The plot of preassigned false alarm rate to guarantee and by Theorems 1 and 3 respectively. (a) Preassigned rate derived by Theorem 1 to guarantee . (b) Preassigned rate derived by Theorem 1 to guarantee .
Consequently, by the value of x the derived new threshold is given by
where denotes the inverse function of . By formula (26), we have
This means by this new threshold the expected false alarm probability is just the predesigned false alarm probability . Hence, this new threshold is more accurate to serve as CFAR threshold for energy detection when using estimated noise variance.
Similarly, for a given alarm level , say , we derive a threshold to guarantee . Denote . It can be solved by (26) that
with , , and . Observe that , it follows that . Then by stated in Theorem 3, it is clear that the preassigned false alarm rate should be . It is plotted in Figure 5b how the cautious preassigned false alarm rate should be under the setting and , for the sequence . It is clearly shown in the figure that the preassigned false alarm rate should be much smaller than the value is designed to be. As the sample number N for estimation increases, the preassigned false alarm rate approaches to the value of .
Consequently, by the value of the derived new threshold is given by
Then, by Theorem 3, we have
Hence, this new threshold is much more accurate in an average sense than the empirical threshold simple replacement for energy detection when using estimated noise variance.
7. Conclusions
When using noise variance to set a CFAR threshold of energy detection for spectrum sensing, the derived threshold itself is a random variable. Thus, the resulted probability of false alarm is probably different from the predetermined false alarm probability . In this paper, we analyze some basic statistical properties of the resulted probability of false alarm given by (21) and its approximating case given by (24), and then some more suitable CFAR thresholds of energy detection are proposed. Specifically, we first deduce explicit descriptions for the expectations of and by Theorems 1 and 3 respectively in Section 4, and then some straightforward properties are established. These actually answer the first question we proposed in the introduction. Second, two upper bounds of and are derived by Theorems 5 and 6 respectively in Section 5, due to the difficulty to find exact explicit forms by known special functions. These answer the second question proposed in the introduction partially as well. Third, with the help of Theorem 3, the limitation of or for as M or N tends to infinity is analyzed in Remark 1, which answers partly the third question in the introduction. Finally, new CFAR thresholds are proposed by assuring that or equals the predetermined false alarm probability in Section 6. All analytical results derived in this paper are regarding the CFAR threshold. However, as a matter of fact, similar results hold for the CDR case.
For further consideration, it is of interest to describe explicitly and . This means that a more cautious thresholds setting is possible. Observe that the CFAR and CDR thresholds are considered separately in this paper, it is crucial to consider CFAR and CDR thresholds synchronously in energy detection to achieve low false alarm probability and high detection probability simultaneously.
Author Contributions
X.-L.H. contributed to most of the formulations and simulations, and prepared the original proposed framework under the supervision of P.-H.H. and L.P. gave advices on the overall work of the paper and helped revise the paper.
Funding
This research was supported by Kyungpook National University Research Fund, 2018.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A
Proof of Lemma 1.
Clearly, , and we use a instead of below for brief.
Define . Clearly,
and
We use the fact in the above second step. Clearly, and . Let us point out a basic fact: for and ,
which can be proved by basic calculus. Thus, for , we have
which means when with a sufficiently large point . Now let us consider the derivative of below.
We find that and . Due to the fact that has positive value for , starting at , we know that its derivative must be positive somewhere between 0 and , and thus for . This assertion holds for the i-th derivative of , denoted as , if the order of the first term is positive. This is because the starting points are all .
If k is a positive integer, then the -th and k-th derivatives are
Notice further that and , we know that starts at a positive value and then decreases monotonically to . This further means that starts from 0 to a positive local maximum and then decreases monotonically to , and so on until . Thus, increases piecewise monotonically from to a positive maximum and then decreases to . Then changes its sign twice, i.e., from negative to positive and then negative. Hence, decreases from 0 to a negative minimum and then increases to positive maximum and then decreases to 0. This further holds for , which means the sign of changes from negative to positive once. Finally, we know that decreases from to a negative minimum and then increases to 0. This means as desired.
When k is not an integer, the -th and -th derivatives are
Notice further that and , we know that decreases monotonically from to as x moves from 0 to ∞. The rest of the reasoning is similar to the above case. □
Proof of Lemma 2.
Define . Clearly,
and
Let us study first. Obviously, . By the facts that and , we have . Notice further the monotonicity of and as , the sign of function changes once from negative to positive as x moves from to 0.
It is left to consider the sign of when . By the following inequality
for , we derive
Hence, for , it is sufficient to require
which is equivalent to . This means for . Now only the case for is left. This can be analyzed directly as following: for ,
Here the approximating calculation in the last step is carried out by Matlab.
References
- Xue, D.; Ekici, E.; Vuran, M.C. Cooperative spectrum sensing in cognitive radio networks using multidimensional correlations. IEEE Trans. Wirel. Commun. 2014, 13, 1832–1843. [Google Scholar] [CrossRef]
- Arjoune, Y.; Kaabouch, N. A Comprehensive Survey on Spectrum Sensing in Cognitive Radio Networks: Recent Advances, New Challenges, and Future Research Directions. Sensors 2019, 19, 126. [Google Scholar] [CrossRef] [PubMed]
- Ali, A.; Hamouda, W. Advances on Spectrum Sensing for Cognitive Radio Networks: Theory and Applications. IEEE Commun. Surv. Tutorials 2016, 19, 1277–1304. [Google Scholar] [CrossRef]
- Plata, D.M.M.; Reatiga, A.G.A. Evaluation of energy detection for spectrum sensing based on the dynamic selection of detection-threshold. Procedia Eng. 2012, 35, 135–143. [Google Scholar] [CrossRef]
- Hu, X.-L.; Ho, P.-H. Performance Analysis of Maximum Likelihood Estimation for Transmit Power Based on Signal Strength Model. J. Sens. Actuator Netw. 2018, 7, 38. [Google Scholar] [CrossRef]
- Sahai, A.; Tandra, R.; Mishra, S.M.; Hoven, N. Fundamental design tradeoffs in cognitive radio systems. In Proceedings of the First International Workshop on Technology and Policy for Accessing Spectrum, Boston, MA, USA, 2–5 August 2006. [Google Scholar]
- Oner, M.; Jondral, F. Cyclostationarity based air interface recognition for software radio systems. In Proceedings of the IEEE Radio and Wireless Conference, Atlanta, GA, USA, 22 September 2004; pp. 263–266. [Google Scholar]
- Gardner, W. Exploitation of spectral redundancy in cyclostationary signals. IEEE Signal Process. Mag. 1991, 8, 14–36. [Google Scholar] [CrossRef]
- Urkowitz, H. Energy detection of unknown deterministic signals. Proc. IEEE 1967, 55, 523–531. [Google Scholar] [CrossRef]
- Kostylev, V. Energy detection of a signal with random amplitude. In Proceedings of the 2002 IEEE International Conference on Communications. Conference Proceedings, New York, NY, USA, 28 April–2 May 2002; Volume 3, pp. 1606–1610. [Google Scholar]
- Digham, F.F.; Alouini, M.; Simon, M.K. On the energy detection of unknown signals over fading channels. IEEE Trans. Commun. 2007, 55, 21–24. [Google Scholar] [CrossRef]
- Ghasemi, A.; Sousa, E.S. Collaborative spectrum sensing for opportunistic access in fading environments. In Proceedings of the First IEEE International Symposium on New Frontiers in Dynamic Spectrum Access Networks, MD, USA, USA, 8–11 November 2005; pp. 131–136. [Google Scholar]
- Ye, Z.; Memik, G.; Grosspietsch, J. Energy Detection Using Estimated Noise Variance for Spectrum Sensing in Cognitive Radio Networks. In Proceedings of the Wireless Communications and Networking Conference, Las Vegas, NV, USA, 31 March–3 April 2008; pp. 711–716. [Google Scholar]
- Arjoune, Y.; Mrabet, Z.E.; Ghazi, H.E.; Tamtaoui, A. Spectrum sensing: Enhanced energy detection technique based on noise measurement. In Proceedings of the 2018 IEEE 8th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 8–10 January 2018. [Google Scholar] [CrossRef]
- Kustra, M.; Kosmowski, K.; Suchanski, M. Performance of hybrid sensing method in environment with noise uncertainty. J. Telecommun. Inf. Technol. 2018, 1, 51–57. [Google Scholar] [CrossRef]
- Yusuf, D.P.; Onwuka, E.; Alenoghena, C.; Agajo, J. Discrete wavelet packet based spectrum sensing in cognitive radio using an improved adaptive threshold. In Proceedings of the International Conference on Industrial Engineering and Operations Management, Bandung, Indonesia, 6–8 March 2018. [Google Scholar]
- Joshi, D.R.; Popescu, D.C.; Dobre, O.A. Adaptive spectrum sensing with noise variance estimation for dynamic cognitive radio systems. In Proceedings of the Conference on Information Sciences and Systems (CISS), Princeton, NJ, USA, 17–19 March 2010; pp. 1–5. [Google Scholar]
- Wu, J.; Luo, T.; Yue, G. An Energy Detection Algorithm Based on Double-Threshold in Cognitive Radio Systems. In Proceedings of the International Conference on Information Science and Engineering, Nanjing, China, 26–28 Decemner 2009; pp. 493–496. [Google Scholar]
- Peh, E.; Liang, Y. Optimization of cooperative sensing in cognitive radio networks. In Proceedings of the WCNC 2007, Kowloon, China, 11–15 March 2007; pp. 27–32. [Google Scholar]
- Shellhammer, S.; Shankar, S.; Dandra, R.; Tomcik, J. Performance of power detector sensors of DVT signals in IEEE 802.22 WRANs. In Proceedings of the First International Workshop on Technology and Policy for Accessing Spectrum, Boston, MA, USA, 5 August 2006. [Google Scholar]
- Kuang, J. Applied Inequalities, 3rd ed.; Shandong Science and Technology Press: Jinan, China, 2004. (In Chinese) [Google Scholar]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).