Social Internet of Vehicles for Smart Cities
Abstract
:1. Introduction
2. SIoV Technologies and Components: Next Generation of Vehicles
2.1. Self-Driving
2.2. Safety Driving
2.3. Social Driving
2.4. Electric Vehicles
2.5. Mobile Applications
3. Vehicle Context-Awareness
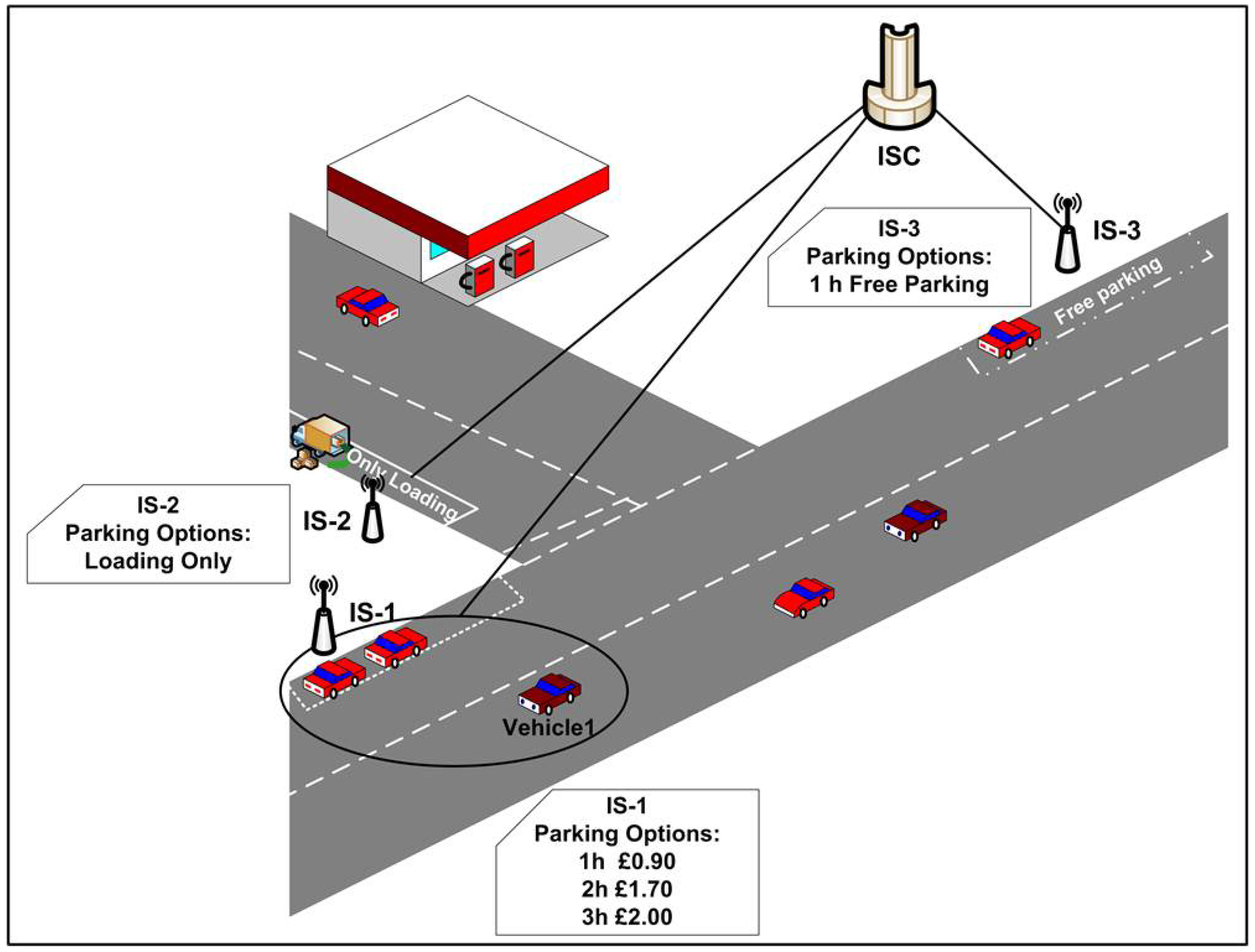
4. Social Network Analysis in SIoVs
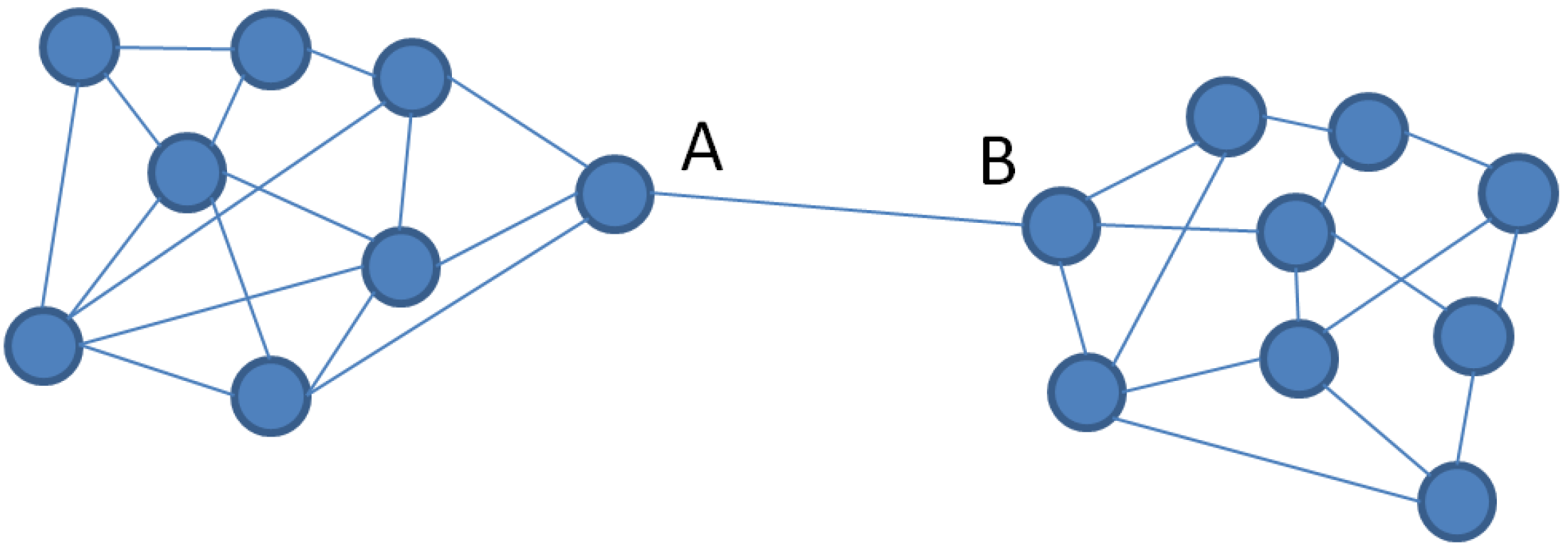
4.1. Centrality of Nodes in an SIoV
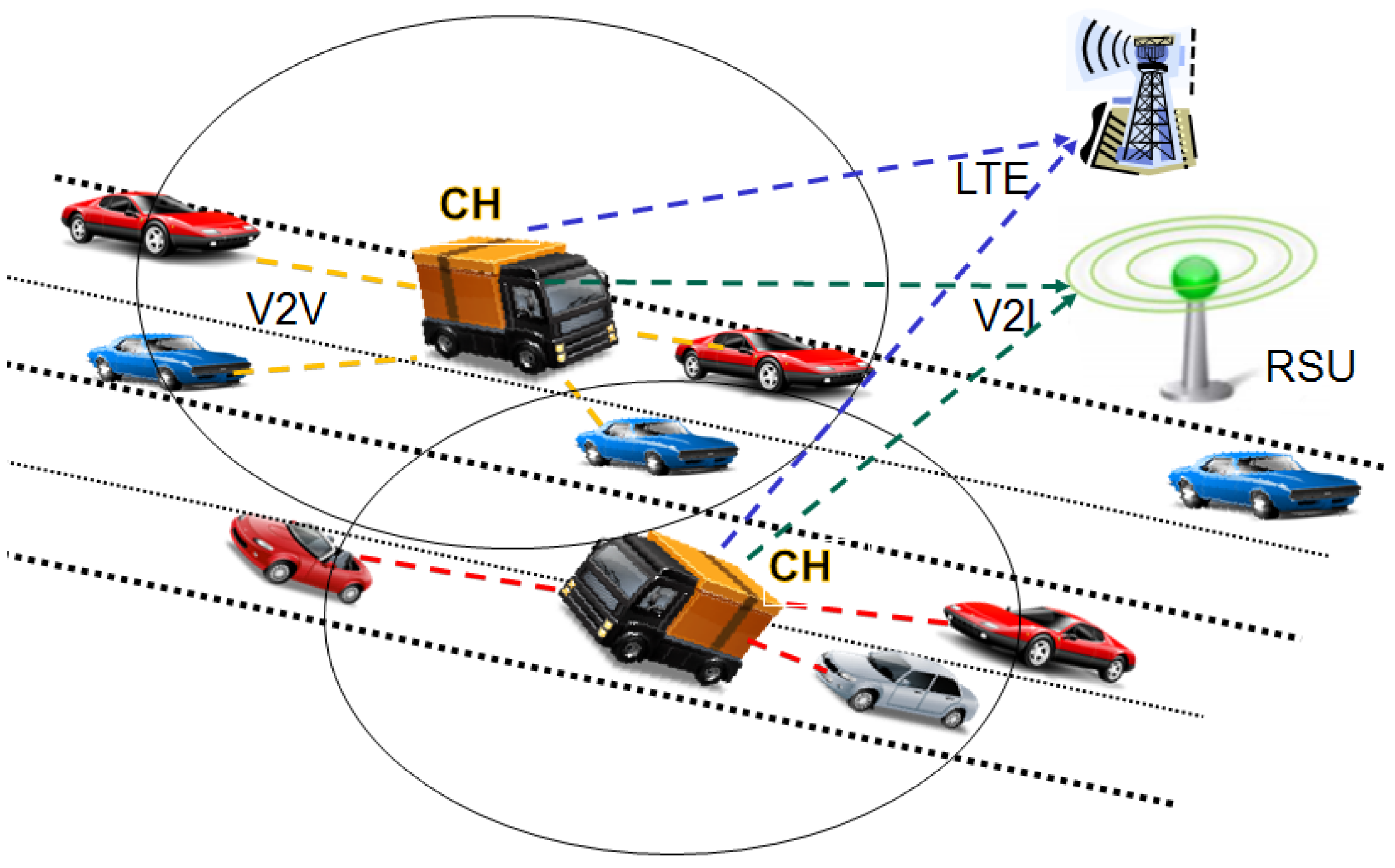
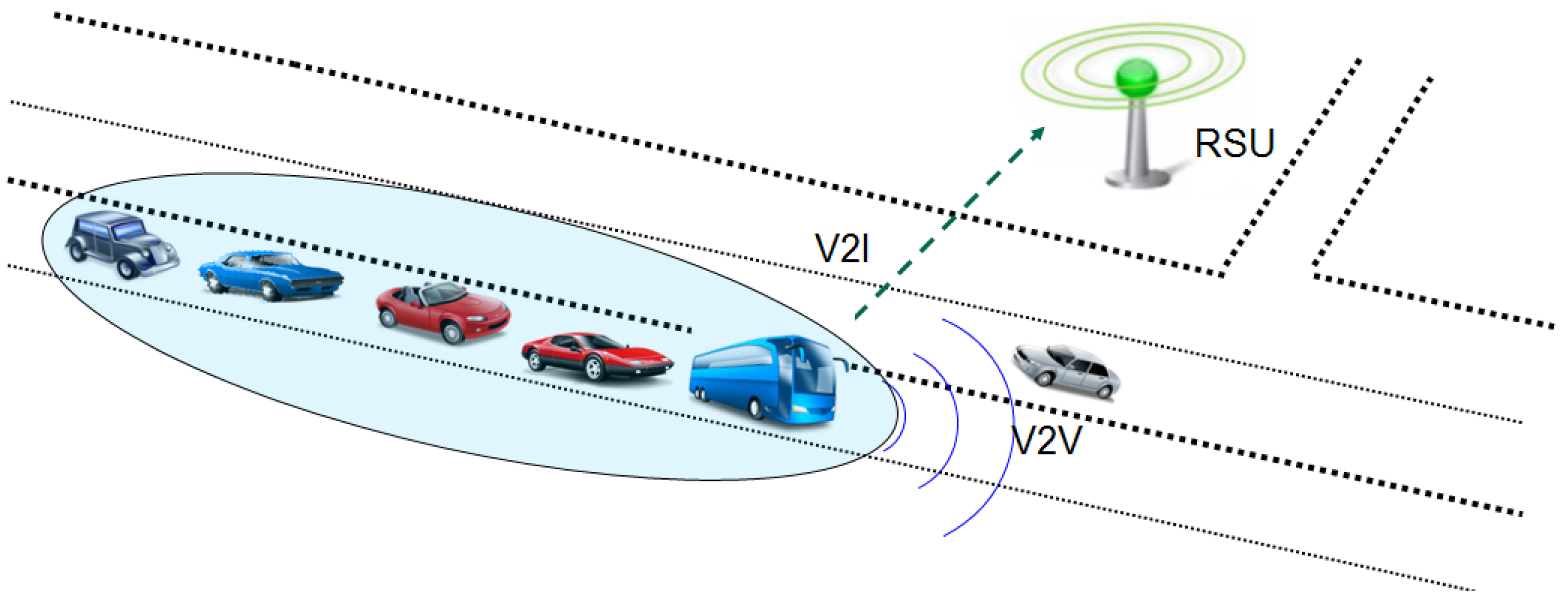
4.2. Social Clustering of Vehicles
5. SIoV Security Issues
5.1. SIoV Threats
5.1.1. Denial of Service Attack
5.1.2. False Message Injection
5.1.3. Malware
5.1.4. Masquerading and Sybil
5.1.5. Impersonation Attack
5.1.6. Solutions and Future Directions
5.2. SIoV Trust Issues
5.2.1. Trust Characteristics of SIoV
Uncertainty
Subjectivity
Intransitivity
Context Dependence
Non-Cooperativeness
5.2.2. Trust and Reputation
6. SIoV Privacy Issues
6.1. Privacy in Vehicular Networks
6.2. Privacy in Social Networks
6.3. Privacy-Enhancing Technologies for the SIoV
7. Conclusions
Conflicts of Interest
References
- Caragliu, A.; Del Bo, C.; Nijkamp, P. Smart cities in Europe. J. Urban Technol. 2011, 18, 65–82. [Google Scholar] [CrossRef]
- Ishida, T.; Isbister, K. Digital Cities: Technologies, Experiences, and Future Perspectives; Number 1765; Springer Science & Business Media: Berlin, Germany, 2000. [Google Scholar]
- Xiong, Z.; Sheng, H.; Rong, W.; Cooper, D.E. Intelligent transportation systems for smart cities: A progress review. Sci. China Inf. Sci. 2012, 55, 2908–2914. [Google Scholar] [CrossRef]
- Bowerman, B.; Braverman, J.; Taylor, J.; Todosow, H.; von Wimmersperg, U. The vision of a smart city. In Proceedings of the 2nd International Life Extension Technology Workshop, Paris, France, 28 September 2000; Volume 28.
- Su, K.; Li, J.; Fu, H. Smart city and the applications. In Proceedings of the 2011 International Conference on Electronics, Communications and Control (ICECC), Zhejiang, China, 9–11 September 2011; pp. 1028–1031.
- Hollands, R.G. Will the real smart city please stand up? Intelligent, progressive or entrepreneurial? City 2008, 12, 303–320. [Google Scholar] [CrossRef]
- El-Hoiydi, A.; Decotignie, J.D. WiseMAC: An ultra low power MAC protocol for the downlink of infrastructure wireless sensor networks. In Proceedings of the Ninth International Symposium on Computers and Communications (ISCC 2004), Alexandria, Egypt, 28 June–1 July 2004; Volume 1, pp. 244–251.
- Perkins, C.E. Ad Hoc Networking; Addison-Wesley Professional; Addison-Wesley: Boston, MA, USA, 2008. [Google Scholar]
- Caballero-Gil, P.; Caballero-Gil, C.; Molina-Gil, J. How to build vehicular ad-hoc networks on smartphones. J. Syst. Architect. 2013, 59, 996–1004. [Google Scholar] [CrossRef]
- Liu, B.; Liu, Z.; Towsley, D. On the capacity of hybrid wireless networks. In Proceedings of the Twenty-Second Annual Joint Conference of the IEEE Computer and Communications on IEEE Societies (INFOCOM 2003), San Francisco, CA, USA, 30 March–3 April 2003; Volume 2, pp. 1543–1552.
- Wang, M.; Shan, H.; Lu, R.; Zhang, R.; Shen, X.; Bai, F. Real-time path planning based on hybrid-VANET-enhanced transportation system. IEEE Trans. Veh. Technol. 2014, 64, 1664–1678. [Google Scholar] [CrossRef]
- Tornell, S.M.; Patra, S.; Calafate, C.T.; Cano, J.C.; Manzoni, P. GRCBox: Extending smartphone connectivity in vehicular networks. Int. J. Distrib. Sens. Netw. 2015, 2015, 478064. [Google Scholar] [CrossRef]
- Marquez-Barja, J.M.; Ahmadi, H.; Tornell, S.M.; Calafate, C.; Cano, J.; Manzoni, P.; Da Silva, L. Breaking the vehicular wireless communications barriers: Vertical handover techniques for heterogeneous networks. IEEE Trans. Veh. Technol. 2014, 64, 5878–5890. [Google Scholar] [CrossRef]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT):Avision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Joerer, S.; Bloessl, B.; Huber, M.; Jamalipour, A.; Dressler, F. Demo: Simulating the impact of communication performance on road traffic safety at intersections. In Proceedings of the 20th Annual International Conference on Mobile Computing and Networking, Maui, HI, USA, 7–11 September 2014; pp. 287–290.
- Maglaras, L.A.; Basaras, P.; Katsaros, D. Exploiting vehicular communications for reducing CO2 emissions in urban environments. In Proceedings of the 2013 International Conference on Connected Vehicles and Expo (ICCVE), Las Vegas, NV, USA, 2–6 December 2013; pp. 32–37.
- Cheng, H.T.; Shan, H.; Zhuang, W. Infotainment and road safety service support in vehicular networking: From a communication perspective. Mech. Syst. Signal Process. 2011, 25, 2020–2038. [Google Scholar] [CrossRef]
- Gruyer, D.; Belaroussi, R.; Revilloud, M. Accurate lateral positioning from map data and road marking detection. Expert Syst. Appl. 2016, 43, 1–8. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G.; Nitti, M. The Social Internet of Things (SIoT)—When social networks meet the internet of things: Concept, architecture and network characterization. Comput. Netw. 2012, 56, 3594–3608. [Google Scholar] [CrossRef]
- Alam, K.; Saini, M.; El Saddik, A. Toward social internet of vehicles: Concept, architecture, and applications. IEEE Access 2015, 3, 343–357. [Google Scholar] [CrossRef]
- Alam, K.M.; Saini, M.; Saddik, A.E. Workload model based dynamic adaptation of social internet of vehicles. Sensors 2015, 15, 23262–23285. [Google Scholar] [CrossRef] [PubMed]
- Nitti, M.; Girau, R.; Floris, A.; Atzori, L. On adding the social dimension to the internet of vehicles: Friendship and middleware. In Proceedings of the 2014 IEEE International Black Sea Conference on Communications and Networking (BlackSeaCom), Odessa, Ukraine, 27–30 May 2014; pp. 134–138.
- Luan, T.; Lu, R.; Shen, X.; Bai, F. Social on the road: Enabling secure and efficient social networking on highways. IEEE Wirel. Commun. 2015, 22, 44–51. [Google Scholar] [CrossRef]
- Schwarz, C.; Thomas, G.; Nelson, K.; McCrary, M.; Sclarmann, N.; Powell, M. Towards Autonomous Vehicles; Technical Report 25-1121-0003-117; Mid-America Transportation Center: Lincoln, NE, USA, 2013. [Google Scholar]
- Squatriglia, C. Ford’s Tweeting Car Embarks on American Journey 2.0. Wired. 2010. Available online: http://www.wired.com/2010/05/ford-american-journey/ (accessed on 15 January 2016).
- Sha, W.; Kwak, D.; Nath, B.; Iftode, L. Social vehicle navigation: Integrating shared driving experience into vehicle navigation. In Proceedings of the 14th Workshop on Mobile Computing Systems and Applications, Jekyll Island, GA, USA, 26–27 February 2013.
- Smaldone, S.; Han, L.; Shankar, P.; Iftode, L. RoadSpeak: Enabling voice chat on roadways using vehicular social networks. In Proceedings of the 1st Workshop on Social Network Systems, Glasgow, UK, 1 April 2008; pp. 43–48.
- Leggett, T. Porsche Concept Challenges Tesla and Posts to Social Media. Available online: http://www. bbc.co.uk/news/technology-34263592 (accessed on 15 January 2016).
- Wan, J.; Zhang, D.; Zhao, S.; Yang, L.; Lloret, J. Context-aware vehicular cyber-physical systems with cloud support: Architecture, challenges, and solutions. IEEE Commun. Mag. 2014, 52, 106–113. [Google Scholar] [CrossRef]
- Vegni, A.; Loscri, V. A Survey on Vehicular Social Networks. IEEE Commun. Surv. Tutor. 2015, 17, 2397–2419. [Google Scholar] [CrossRef]
- Al-Sultan, S.; Al-Doori, M.M.; Al-Bayatti, A.H.; Zedan, H. A comprehensive survey on vehicular ad hoc network. J. Netw. Comput. Appl. 2014, 37, 380–392. [Google Scholar] [CrossRef]
- Vegni, A.M.; Biagi, M.; Cusani, R. Smart Vehicles, Technologies and Main Applications in Vehicular Ad Hoc Networks; INTECH Open Access Publisher: Rijeka, Croatia, 2013. [Google Scholar]
- Silberg, G.; Wallace, R. Self-Driving Cars: The Next Revolution; Technical Report; KPMG: Amstelveen, The Netherlands, 2012. [Google Scholar]
- SAE On-Road Automated Vehicle Standards Committee. Taxonomy and Definitions for Terms Related to On-Road Motor Vehicle Automated Driving Systems; Technical Report J3016_201401; SAE: Hong Kong, China, 2014. [Google Scholar]
- Mercedes-Benz UK Ltd. Saloon—Specs, Prices & Offers. Available online: http://www2.mercedesbenz.co.uk/content/unitedkingdom/mpc/mpc_unitedkingdom_website/en/home _mpc/passengercars/home/new_cars/models/s-class/_w222.flash.html (accessed on 15 January 2016).
- BMW of North America. BMW I Overview—BMW North America. Available online: http://www. bmwusa.com/bmw/BMWi (accessed on 15 January 2016).
- Audi of America. Audi Innovation: Performance for the Driver. Available online: http://www.audiusa. com/technology (accessed on 15 January 2016).
- Ding, Z. The enlightenment of vision zero to China’s road safety management. In Proceedings of the 2010 WASE International Conference on Information Engineering (ICIE), Beidaihe, China, 14–15 August 2010; Volume 3, pp. 352–355.
- Barrachina, J.; Garrido, P.; Fogue, M.; Martinez, F.J.; Cano, J.C.; Calafate, C.T.; Manzoni, P. Reducing emergency services arrival time by using vehicular communications and Evolution Strategies. Expert Syst. Appl. 2014, 41, 1206–1217. [Google Scholar] [CrossRef]
- Waze. Real-time maps and traffic information based on the wisdom of the crowd. Available online: http://solsie.com/2009/09/real-time-maps-and-traffic-information-based-on-the-wisdom-of-the-crowd/ (accessed on 15 January 2016).
- Arrington, M. Google Redefines GPS Navigation Landscape: Google Maps Navigation for Android 2.0; TechCrunch: San Francisco, CA, USA, 2009. [Google Scholar]
- Portland makes Uber and Lyft legal—For now. Available online: http://www.oregonherald.com/oregon/localnews.cfm?id=8910 (accessed on 15 January 2016).
- Machiels, N.; Leemput, N.; Geth, F.; van Roy, J.; Buscher, J.; Driesen, J. Design criteria for electric vehicle fast charge infrastructure based on flemish mobility behaviour. IEEE Trans. Smart Grid 2014, 5, 320–327. [Google Scholar] [CrossRef]
- Putrus, G.; Suwanapingkarl, P.; Johnston, D.; Bentley, E.; Narayana, M. Impact of electric vehicles on power distribution networks. In Proceedings of the IEEE Vehicle Power and Propulsion Conference (VPPC ’09), Dearborn, MI, USA, 7–10 September 2009; pp. 827–831.
- Ruiz, M.A.; Abdallah, F.A.; Gagnaire, M.; Lascaux, Y. Telewatt: An innovative electric vehicle charging infrastructure over public lighting systems. In Proceedings of the 2013 International Conference on Connected Vehicles and Expo (ICCVE), Las Vegas, NV, USA, 2–6 December 2013; pp. 741–746.
- Jung, G.; Song, B.; Shin, S.; Lee, S.; Shin, J.; Kim, Y.; Lee, C.; Jung, S. Wireless charging system for On-Line Electric Bus (OLEB) with series-connected road-embedded segment. In Proceedings of the 2013 12th International Conference on Environment and Electrical Engineering (EEEIC), Wroclaw, Poland, 5–8 May 2013; pp. 485–488.
- Maglaras, L.; Topalis, F.V.; Maglaras, A.L. Cooperative approaches for dymanic wireless charging of Electric Vehicles in a smart city. In Proceedings of the 2014 IEEE International Energy Conference (ENERGYCON), Cavtat, Croatia, 13–16 May 2014; pp. 1365–1369.
- Boriboonsomsin, K.; Barth, M.J.; Zhu, W.; Vu, A. Eco-routing navigation system based on multisource historical and real-time traffic information. IEEE Trans. Intell. Transp. Syst. 2012, 13, 1694–1704. [Google Scholar] [CrossRef]
- Liu, Z.; Zhang, W.; Ji, X.; Li, K. Optimal planning of charging station for electric vehicle based on particle swarm optimization. In Proceedings of the 2012 IEEE Innovative Smart Grid Technologies—Asia (ISGT Asia), Tianjin, China, 21–24 May 2012; pp. 1–5.
- Dutta, P. Coordinating rendezvous points for inductive power transfer between electric vehicles to increase effective driving distance. In Proceedings of the 2013 International Conference on Connected Vehicles and Expo (ICCVE), Las Vegas, NV, USA, 2–6 December 2013; pp. 649–653.
- Jakubiak, J.; Koucheryavy, Y. State of the art and research challenges for VANETs. In Proceedings of the 2008 5th IEEE Consumer Communications and Networking Conference, Las Vegas, NV, USA, 10–12 January 2008.
- Eskandarian, A. Handbook of Intelligent Vehicles; Springer: London, UK, 2012. [Google Scholar]
- Wang, Z.; Lu, J. The design and implementation of client about vehicle context-aware system based on Ubiquitous Network. In Proceedings of the 2013 IEEE 4th International Conference on Electronics Information and Emergency Communication (ICEIEC), Beijing, China, 15–17 November 2013; pp. 325–328.
- Alhammad, A.; Siewe, F.; Al-Bayatti, A. An InfoStation-based context-aware on-street parking system. In Proceedings of the 2012 International Conference on Computer Systems and Industrial Informatics (ICCSII), Sharjah, UAE, 18–20 December 2012; pp. 1–6.
- Hu, X.; Zhao, J.; Seet, B.C.; Leung, V.; Chu, T.; Chan, H. S-Aframe: Agent-Based Multilayer Framework With Context-Aware Semantic Service for Vehicular Social Networks. IEEE Trans. Emerg. Top. Comput. 2015, 3, 44–63. [Google Scholar]
- Shu, W.; Zhang, G.; Wu, M.Y.; Lu, J.L. A social-network-enabled green transportation system. In Proceedings of the 2013 International Conference on Connected Vehicles and Expo (ICCVE), Las Vegas, NV, USA, 2–6 December 2013; pp. 425–430.
- Scott, J. Social Network Analysis; Sage Publications Ltd: Thousand Oaks, CA, USA, 2012. [Google Scholar]
- Cunha, F.; Carneiro Vianna, A.; Mini, R.; Loureiro, A. How effective is to look at a vehicular network under a social perception? In Proceedings of the 2013 IEEE 9th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Lyon, France, 7–9 October 2013; pp. 154–159.
- Basaras, P.; Katsaros, D.; Tassiulas, L. Detecting influential spreaders in complex, dynamic networks. Computer 2013, 46, 24–29. [Google Scholar] [CrossRef]
- Borge-Holthoefer, J.; Rivero, A.; Moreno, Y. Locating privileged spreaders on an online social network. Phys. Rev. E 2011, 85. [Google Scholar] [CrossRef] [PubMed]
- Canright, G.S.; Engø-Monsen, K. Spreading on networks: A topographic view. Complexus 2006, 3, 131–146. [Google Scholar] [CrossRef]
- Noel, S.; Jajodia, S. Optimal IDS sensor placement and alert prioritization using attack graphs. J. Netw. Syst. Manag. 2008, 16, 259–275. [Google Scholar] [CrossRef]
- Souza, E.; Nikolaidis, I.; Gburzynski, P. A new aggregate local mobility (ALM) clustering algorithm for VANETs. In Proceedings of the 2010 IEEE International Conference on Communications (ICC), Cape Town, South Africa, 23–27 May 2010; pp. 1–5.
- Bavelas, A. A mathematical model for group structures. Hum. Organ. 1948, 7, 16–30. [Google Scholar] [CrossRef]
- Cuzzocrea, A.; Papadimitriou, A.; Katsaros, D.; Manolopoulos, Y. Edge betweenness centrality: A novel algorithm for QoS-based topology control over wireless sensor networks. J. Netw. Comput. Appl. 2012, 35, 1210–1217. [Google Scholar] [CrossRef]
- Bali, R.S.; Kumar, N.; Rodrigues, J.J. Clustering in vehicular ad hoc networks: Taxonomy, challenges and solutions. Veh. Commun. 2014, 1, 134–152. [Google Scholar] [CrossRef]
- Daly, E.M.; Haahr, M. Social network analysis for routing in disconnected delay-tolerant manets. In Proceedings of the 8th ACM International Symposium on Mobile ad Hoc Networking and Computing, Montreal, QC, Canada, 9–14 September 2007; pp. 32–40.
- Loulloudes, N.; Pallis, G.; Dikaiakos, M.D. The Dynamics of Vehicular Networks in Urban Environments; arXiv preprint arXiv:1007.4106; Cornell University: Ithaca, NY, USA, 2010. [Google Scholar]
- Maglaras, L.A.; Stathakidis, E.; Jiang, J. Social aspect of vehicular communications. EAI Trans. Cloud Syst. 2015, 1, 1–10. [Google Scholar] [CrossRef]
- Bradai, A.; Ahmed, T. ReViV: Selective rebroadcast mechanism for video streaming over VANET. In Proceedings of the 2014 IEEE 79th Vehicular Technology Conference (VTC Spring), Seoul, Korea, 18–21 May 2014; pp. 1–6.
- Aslam, B.; Amjad, F.; Zou, C.C. Optimal roadside units placement in urban areas for vehicular networks. In Proceedings of the 2012 IEEE Symposium on Computers and Communications (ISCC), Cappadocia, Turkey, 1–4 July 2012; pp. 000423–000429.
- Rashidi, M.; Batros, I.; Madsen, T.K.; Riaz, M.T.; Paulin, T. Placement of Road Side Units for floating car data collection in highway scenario. In Proceedings of the 2012 4th International Congress on Ultra Modern Telecommunications and Control Systems and Workshops (ICUMT), St. Petersburg, Russia, 3–5 October 2012; pp. 114–118.
- Lu, R.; Lin, X.; Shen, X. SPRING: A social-based privacy-preserving packet forwarding protocol for vehicular delay tolerant networks. In Proceedings of the 2010 IEEE INFOCOM, San Diego, CA, USA, 14–19 March 2010; pp. 1–9.
- Huang, X.; Kang, J.; Yu, R. Optimal roadside unit placement with location privacy enhancement in vehicular social network. In Proceedings of the 2015 5th International Conference on Information Science and Technology (ICIST), Changsha, China, 24–26 April 2015; pp. 254–259.
- Barrachina, J.; Garrido, P.; Fogue, M.; Martinez, F.J.; Cano, J.C.; Calafate, C.T.; Manzoni, P. D-RSU: A density-based approach for road side unit deployment in urban scenarios. In Proceedings of the 2012 IEEE Intelligent Vehicles Symposium, Madrid, Spain, 3–7 June 2012; pp. 1–6.
- Yu, J.Y.; Chong, P.H.J. A survey of clustering schemes for mobile ad hoc networks. IEEE Commun. Surv. Tutor. 2005, 7, 32–48. [Google Scholar] [CrossRef]
- Younis, O.; Krunz, M.; Ramasubramanian, S. Node clustering in wireless sensor networks: Recent developments and deployment challenges. IEEE Netw. 2006, 20, 20–25. [Google Scholar] [CrossRef]
- Tseng, Y.C.; Ni, S.Y.; Chen, Y.S.; Sheu, J.P. The broadcast storm problem in a mobile ad hoc network. Wirel. Netw. 2002, 8, 153–167. [Google Scholar] [CrossRef]
- Nyongesa, F.; Djouani, K.; Olwal, T.; Hamam, Y. Doppler Shift Compensation Schemes in VANETs. Mob. Inf. Syst. 2015, 2015, 438159. [Google Scholar] [CrossRef]
- Fogue, M.; Garrido, P.; Martinez, F.J.; Cano, J.C.; Calafate, C.T.; Manzoni, P. Identifying the key factors affecting warning message dissemination in VANET real urban scenarios. Sensors 2013, 13, 5220–5250. [Google Scholar] [CrossRef] [PubMed]
- Maglaras, L.; Katsaros, D. Distributed clustering in vehicular networks. In Proceedings of the 2012 IEEE 8th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Barcelona, Spain, 8–10 October 2012; pp. 593–599.
- Hassanabadi, B.; Shea, C.; Zhang, L.; Valaee, S. Clustering in vehicular ad hoc networks using affinity propagation. Ad Hoc Netw. 2014, 13, 535–548. [Google Scholar] [CrossRef]
- Vegni, A.M.; Stramacci, A.; Natalizio, E. Opportunistic clusters selection in a reliable enhanced broadcast protocol for vehicular ad hoc networks. In Proceedings of the 2013 10th Annual Conference on Wireless On-demand Network Systems and Services (WONS), Banff, AB, Canada, 18–20 March 2013; pp. 95–97.
- Shi, J.; Wang, X.; Huang, M. Social-Based Routing for Vehicular Ad Hoc Networks in Fixed-Route Transportation Scenarios. In Wireless Communications, Networking and Applications; Springer: Berlin, Germany, 2016; pp. 681–691. [Google Scholar]
- Maglaras, L.; Katsaros, D. Social clustering of vehicles based on semi-Markov processes. IEEE Trans. Veh. Technol. 2015, 65, 318–332. [Google Scholar] [CrossRef]
- Jia, D.; Lu, K.; Wang, J.; Zhang, X.; Shen, X. A Survey on platoon-based vehicular cyber-physical systems. IEEE Commun. Surv. Tutor. 2015, 18. [Google Scholar] [CrossRef]
- Van Arem, B.; van Driel, C.J.; Visser, R. The impact of cooperative adaptive cruise control on traffic-flow characteristics. IEEE Trans. Intell. Transp. Syst. 2006, 7, 429–436. [Google Scholar] [CrossRef]
- Mohaien, A.; Kune, D.F.; Vasserman, E.Y.; Kim, M.; Kim, Y. Secure encounter-based mobile social networks: Requirements, designs, and tradeoffs. IEEE Trans. Dependable Secur. Comput. 2013, 10, 380–393. [Google Scholar] [CrossRef]
- Raya, M.; Hubaux, J.P. The security of vehicular ad hoc networks. In Proceedings of the 3rd ACM Workshop on Security of Ad Hoc and Sensor Networks, Alexandria, VA, USA, 7 November 2005; pp. 11–21.
- Zeadally, S.; Hunt, R.; Chen, Y.S.; Irwin, A.; Hassan, A. Vehicular ad hoc networks (VANETS): Status, results, and challenges. Telecommun. Syst. 2012, 50, 217–241. [Google Scholar] [CrossRef]
- Malla, A.M.; Sahu, R.K. Security attacks with an effective solution for DOS attacks in VANET. Int. J. Comput. Appl. 2013, 66, 45–49. [Google Scholar]
- Lesser, V.; Ortiz, C.L., Jr.; Tambe, M. Distributed Sensor Networks: A Multiagent Perspective; Springer Science & Business Media: Berlin, Germany, 2012; Volume 9. [Google Scholar]
- Cao, Z.; Kong, J.; Gerla, M.; Chen, Z.; Hu, J. Filtering false data via authentic consensus in vehicle ad hoc networks. Int. J. Auton. Adapt. Commun. Syst. 2010, 3, 217–235. [Google Scholar] [CrossRef]
- Koscher, K.; Czeskis, A.; Roesner, F.; Patel, S.; Kohno, T.; Checkoway, S.; McCoy, D.; Kantor, B.; Anderson, D.; Shacham, H.; et al. Experimental security analysis of a modern automobile. In Proceedings of the 2010 IEEE Symposium on Security and Privacy (SP), Oakland, CA, USA, 16–19 May 2010; pp. 447–462.
- Krishna, A.S.; Hussain, S.A. Smart vehicle security and defending against collaborative attacks by malware. Int. J. Embed. Softw. Comput. 2015. [Google Scholar] [CrossRef]
- Zhang, T.; Antunes, H.; Aggarwal, S. Defending connected vehicles against malware: Challenges and a solution framework. IEEE Internet Things J. 2014, 1, 10–21. [Google Scholar] [CrossRef]
- Newsome, J.; Shi, E.; Song, D.; Perrig, A. The sybil attack in sensor networks: Analysis & defences. In Proceedings of the 3rd International Symposium on Information Processing in Sensor Networks, Berkeley, CA, USA, 26–27 April 2004; pp. 259–268.
- Raya, M.; Papadimitratos, P.; Hubaux, J.P. Securing vehicular communications. IEEE Wirel. Commun. 2006, 13, 8–15. [Google Scholar] [CrossRef]
- Chhatwal, S.S.; Sharma, M. Detection of impersonation attack in VANETs using BUCK Filter and VANET Content Fragile Watermarking (VCFW). In Proceedings of the 2015 International Conference on Computer Communication and Informatics (ICCCI), Coimbatore, India, 8–10 January 2015; pp. 1–5.
- Kumar, N.; Iqbal, R.; Misra, S.; Rodrigues, J.J. An intelligent approach for building a secure decentralized public key infrastructure in VANET. J. Comput. Syst. Sci. 2015, 81, 1042–1058. [Google Scholar] [CrossRef]
- Schweppe, H.; Weyl, B.; Roudier, Y.; Idrees, M.S.; Gendrullis, T.; Wolf, M.; Serme, G.; de Oliveira, S.A.; Grall, H.; Sudholt, M.; et al. Securing car2X applications with effective hardware software codesign for vehicular on-board networks. In Proceedings of the 27th Joint VDI/VW Automotive Security Conference, Berlin, Germany, 11–12 October 2011.
- Lu, R.; Lin, X.; Liang, X.; Shen, X. A dynamic privacy-preserving key management scheme for location-based services in vanets. IEEE Trans. Intell. Transp. Syst. 2012, 13, 127–139. [Google Scholar] [CrossRef]
- Golbeck, J. Computing with trust: Definition, properties, and algorithms. In Proceedings of the 2006 Securecomm and Workshops, Baltimore, MD, USA, 28 August–1 September 2006; pp. 1–7.
- Golbeck, J. Computing with Social Trust; Springer Science & Business Media: Berlin, Germany, 2008. [Google Scholar]
- Adams, W.J.; Hadjichristofi, G.C.; Davis, N.J., IV. Calculating a node’s reputation in a mobile ad hoc network. In Proceedings of the 24th IEEE International Performance, Computing, and Communications Conference, Phoenix, AZ, USA, 7–9 April 2005; pp. 303–307.
- Gupta, S. A General Context-dependent Trust Model for Controlling Access to Resources. Ph.D. Thesis, Jadavpur University, Kolkata, India, 2012. [Google Scholar]
- Yang, X.; Guo, Y.; Liu, Y. Bayesian-inference-based recommendation in online social networks. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 642–651. [Google Scholar] [CrossRef]
- Sherchan, W.; Nepal, S.; Paris, C. A survey of trust in social networks. ACM Comput. Surv. 2013, 45. [Google Scholar] [CrossRef]
- Jøsang, A.; Hayward, R.; Pope, S. Trust Network Analysis with Subjective Logic. In Proceedings of the 29th Australasian Computer Science Conference, Hobart, Australia, 16–19 January 2006; Volume 48, pp. 85–94.
- Cerutti, F.; Toniolo, A.; Oren, N.; Norman, T.J. Context-Dependent Trust Decisions with Subjective Logic; arXiv preprint arXiv:1309.4994; Cornell University: Ithaca, NY, USA, 2013. [Google Scholar]
- Cho, J.H.; Chen, R. On the tradeoff between altruism and selfishness in MANET trust management. Ad Hoc Netw. 2013, 11, 2217–2234. [Google Scholar] [CrossRef]
- Fogue, M.; Martinez, F.; Garrido, P.; Fiore, M.; Chiasserini, C.F.; Casetti, C.; Cano, J.; Calafate, C.; Manzoni, P. Securing warning message dissemination in vanets using cooperative neighbour position verification. IEEE Trans. Veh. Technol. 2014, 64, 2538–2550. [Google Scholar] [CrossRef]
- Cho, J.H.; Swami, A.; Chen, I.R. A survey on trust management for mobile ad hoc networks. IEEE Commun. Surv. Tutor. 2011, 13, 562–583. [Google Scholar] [CrossRef]
- Eckhoff, D.; Sommer, C. Driving for Big Data? Privacy Concerns in Vehicular Networking. IEEE Secur. Priv. 2014, 12, 77–79. [Google Scholar] [CrossRef]
- Dötzer, F. Privacy Issues in Vehicular Ad Hoc Networks. In Privacy Enhancing Technologies; Danezis, G., Martin, D., Eds.; Number 3856 in Lecture Notes in Computer Science; Springer: Berlin, Heidelberg, Germany, 2006; pp. 197–209. [Google Scholar]
- Wiedersheim, B.; Ma, Z.; Kargl, F.; Papadimitratos, P. Privacy in inter-vehicular networks: Why simple pseudonym change is not enough. In Proceedings of the 7th International Conference on Wireless On-Demand Network Systems and Services, Kranjska Gora, Slovenia, 3–5 February 2010; pp. 176–183.
- Hartenstein, H.; Laberteaux, K.P. A tutorial survey on vehicular ad hoc networks. IEEE Commun. Mag. 2008, 46, 164–171. [Google Scholar] [CrossRef]
- Lin, X.; Sun, X.; Ho, P.H.; Shen, X. GSIS: A Secure and Privacy-Preserving Protocol for Vehicular Communications. IEEE Trans. Veh. Technol. 2007, 56, 3442–3456. [Google Scholar]
- Buttyán, L.; Holczer, T.; Vajda, I. On the effectiveness of changing pseudonyms to provide location privacy in VANETs. In Security and Privacy in Ad-Hoc and Sensor Networks; Stajano, F., Meadows, C., Capkun, S., Moore, T., Eds.; Number 4572 in Lecture Notes in Computer Science; Springer: Berlin, Heidelberg, Germany, 2007; pp. 129–141. [Google Scholar]
- Freudiger, J.; Raya, M.; Félegyházi, M.; Papadimitratos, P. Mix-zones for location privacy in vehicular networks. In Proceedings of the First International Workshop on Wireless Networking for Intelligent Transportation Systems (Win-ITS), Vancouver, BC, Canada, 14–17 August 2007.
- Huang, L.; Matsuura, K.; Yamane, H.; Sezaki, K. Enhancing wireless location privacy using silent period. In Proceedings of the 2005 IEEE Wireless Communications and Networking Conference, New Orleans, LA, USA, 13–17 March 2005; Volume 2, pp. 1187–1192.
- Caballero-Gil, C.; Molina-Gil, J.; Hernández-Serrano, J.; León, O.; Soriano-Ibañez, M. Providing k-anonymity and revocation in ubiquitous VANETs. Ad Hoc Netw. 2016, 36, 482–494. [Google Scholar] [CrossRef]
- Gross, R.; Acquisti, A. Information Revelation and Privacy in Online Social Networks. In Proceedings of the 2005 ACM Workshop on Privacy in the Electronic Society, Alexandria, VA, USA, 7 November 2005; pp. 71–80.
- Bonneau, J.; Preibusch, S. The Privacy Jungle: On the Market for Data Protection in Social Networks. In Economics of Information Security and Privacy; Moore, T., Pym, D., Ioannidis, C., Eds.; Springer: New York, NY, USA, 2010; pp. 121–167. [Google Scholar]
- Zheleva, E.; Getoor, L. To join or not to join: The illusion of privacy in social networks with mixed public and private user profiles. In Proceedings of the 18th International Conference on World Wide Web, Madrid, Spain, 20–24 April 2009; pp. 531–540.
- Mislove, A.; Viswanath, B.; Gummadi, K.P.; Druschel, P. You are who you know: Inferring user profiles in online social networks. In Proceedings of the third ACM International Conference on Web Search and Data Mining, New York, NY, USA, 4–6 February 2010; pp. 251–260.
- Thomas, K.; Grier, C.; Nicol, D.M. unFriendly: Multi-party Privacy Risks in Social Networks. In Privacy Enhancing Technologies; Atallah, M.J., Hopper, N.J., Eds.; Number 6205 in Lecture Notes in Computer Science; Springer: Berlin, Heidelberg, Germany, 2010; pp. 236–252. [Google Scholar]
- Lucas, M.M.; Borisov, N. FlyByNight: Mitigating the Privacy Risks of Social Networking. In Proceedings of the 7th ACM Workshop on Privacy in the Electronic Society, Sydney, Australia, 19–22 May 2008; pp. 1–8.
- Beato, F.; Kohlweiss, M.; Wouters, K. Scramble! Your social network data. In Privacy Enhancing Technologies; Fischer-Hübner, S., Hopper, N., Eds.; Number 6794 in Lecture Notes in Computer Science; Springer: Berlin, Heidelberg, Germany, 2011; pp. 211–225. [Google Scholar]
- Guha, S.; Tang, K.; Francis, P. NOYB: Privacy in online social networks. In Proceedings of the First Workshop on Online Social Networks, Reno, NV, USA, 23–24 February 2008; pp. 49–54.
- Narayanan, A.; Shmatikov, V. De-anonymizing social networks. In Proceedings of the 30th IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 17–20 May 2009; pp. 173–187.
- Korolova, A.; Motwani, R.; Nabar, S.U.; Xu, Y. Link privacy in social networks. In Proceedings of the 17th ACM Conference on Information and Knowledge Management, Napa Valley, CA, USA, 26–30 October 2008; pp. 289–298.
- Effendy, S.; Yap, R.H.; Halim, F. Revisiting link privacy in social networks. In Proceedings of the Second ACM Conference on Data and Application Security and Privacy, San Antonio, TX, USA, 7–9 February 2012; pp. 61–70.
- Takabi, H.; Joshi, J.; Ahn, G.J. Security and privacy challenges in cloud computing environments. IEEE Secur. Priv. 2010, 8, 24–31. [Google Scholar] [CrossRef]
- Wagner, I.; Eckhoff, D. Privacy assessment in vehicular networks using simulation. In Proceedings of the 2014 Winter Simulation Conference (WSC), Savanah, GA, USA, 7–10 December 2014; pp. 3155–3166.
- Wagner, I.; Eckhoff, D. Technical Privacy Metrics: A Systematic Survey. arXiv:1512.00327. 2015. Available online: http://arxiv.org/abs/1512.00327 (accessed on 5 February 2016).
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons by Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Maglaras, L.A.; Al-Bayatti, A.H.; He, Y.; Wagner, I.; Janicke, H. Social Internet of Vehicles for Smart Cities. J. Sens. Actuator Netw. 2016, 5, 3. https://doi.org/10.3390/jsan5010003
Maglaras LA, Al-Bayatti AH, He Y, Wagner I, Janicke H. Social Internet of Vehicles for Smart Cities. Journal of Sensor and Actuator Networks. 2016; 5(1):3. https://doi.org/10.3390/jsan5010003
Chicago/Turabian StyleMaglaras, Leandros A., Ali H. Al-Bayatti, Ying He, Isabel Wagner, and Helge Janicke. 2016. "Social Internet of Vehicles for Smart Cities" Journal of Sensor and Actuator Networks 5, no. 1: 3. https://doi.org/10.3390/jsan5010003
APA StyleMaglaras, L. A., Al-Bayatti, A. H., He, Y., Wagner, I., & Janicke, H. (2016). Social Internet of Vehicles for Smart Cities. Journal of Sensor and Actuator Networks, 5(1), 3. https://doi.org/10.3390/jsan5010003







