Opportunistic Interference Alignment in Cognitive Radio Networks with Space–Time Coding
Abstract
1. Introduction
- Firstly, the PU’s PA technique is based on an SVD scheme that employs the ST-WF algorithm for the PU link to free up some unused eigenmodes and achieve better channel capacity and;
- Finally, to optimize the transmission rates of SUs; this work proposes an IA technique that combines the merits of DSTBC and linear precoding, yielding a two-dimensional (2-D) beamforming solution that shows better performance in terms of the SUs’ transmission rates.
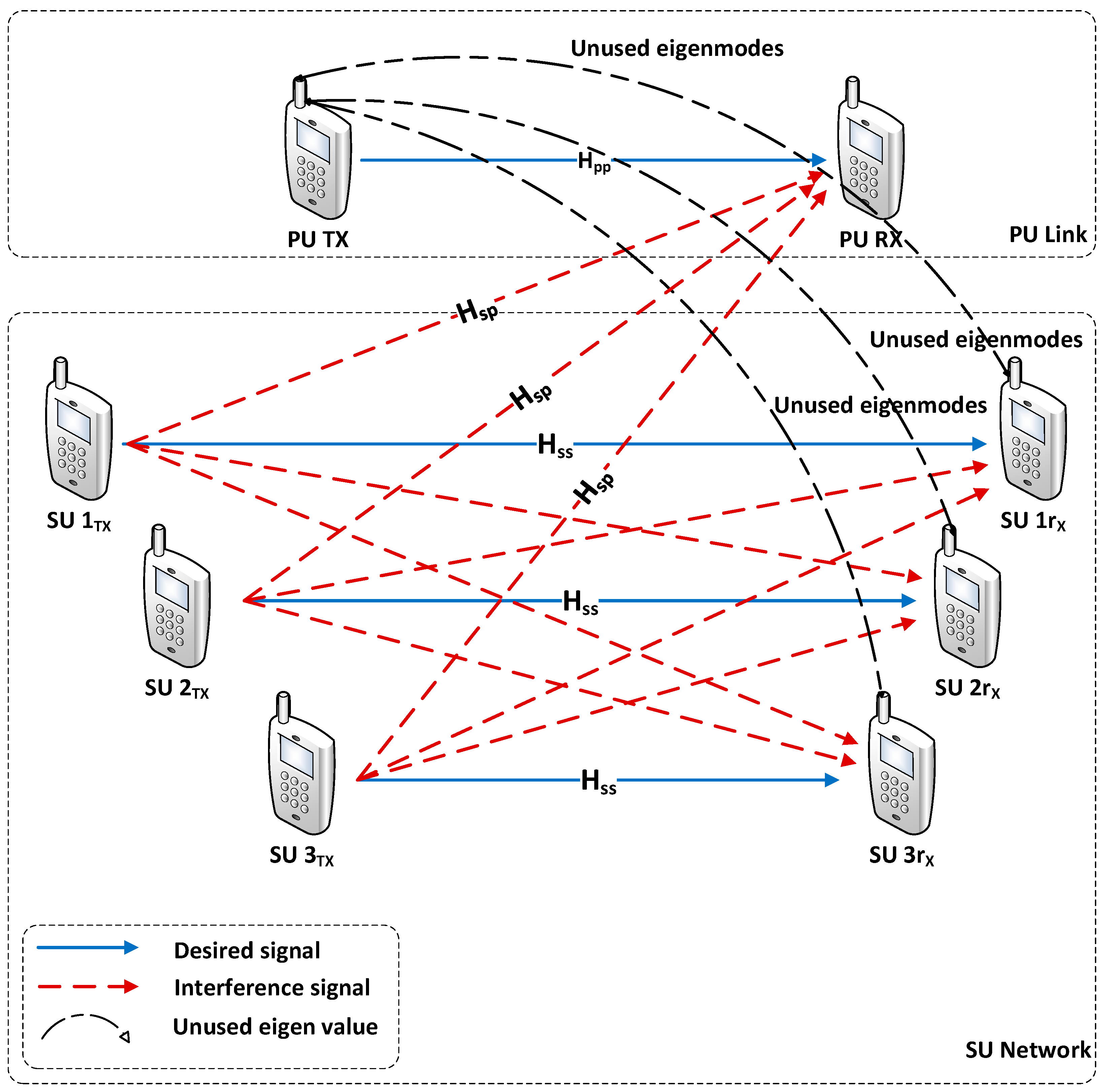
2. System Model and Assumptions
3. PU Link Optimization
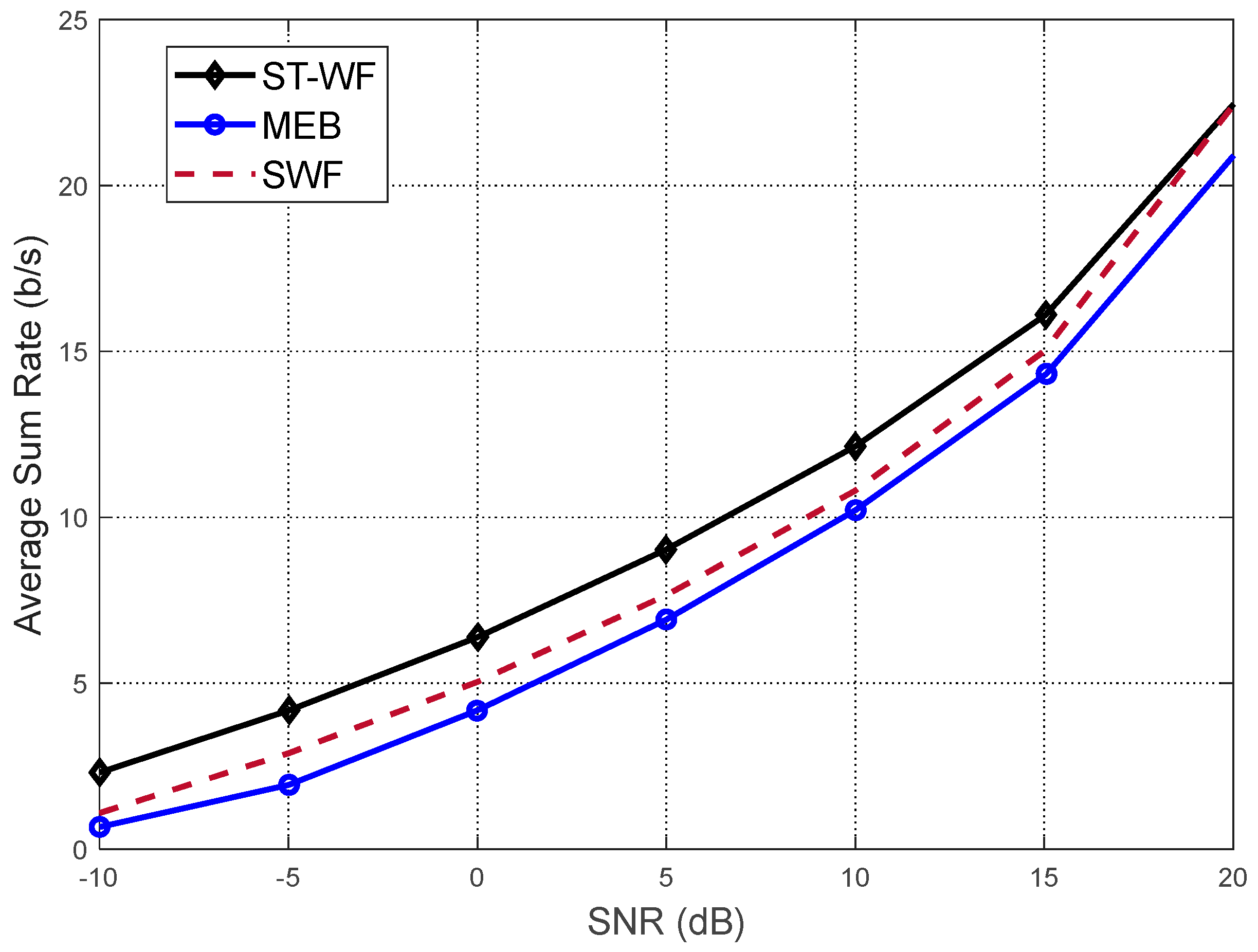
3.1. The Numerical Comparison
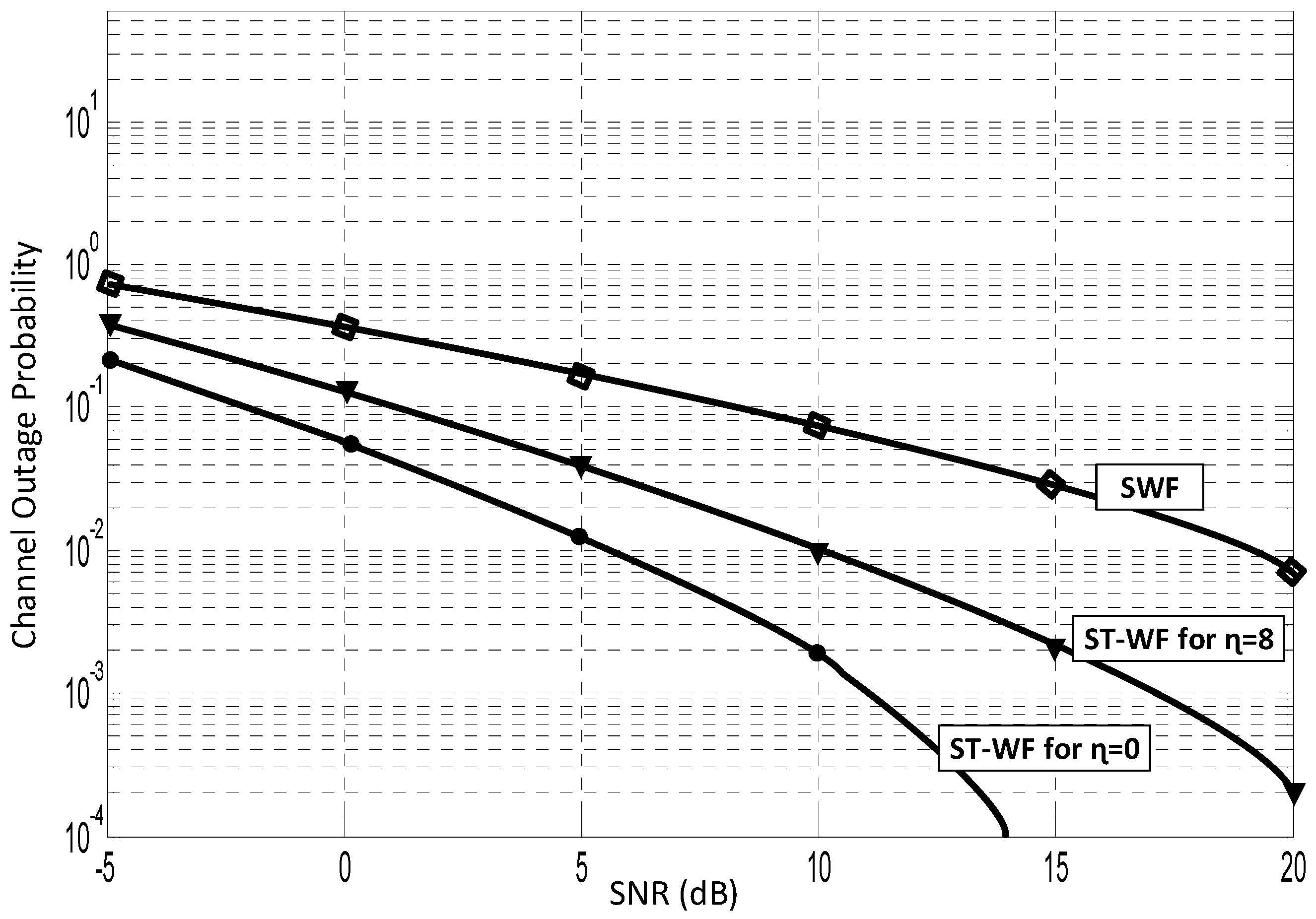
3.2. Outage Probability of ST-WF
4. Opportunistic Interference Alignment
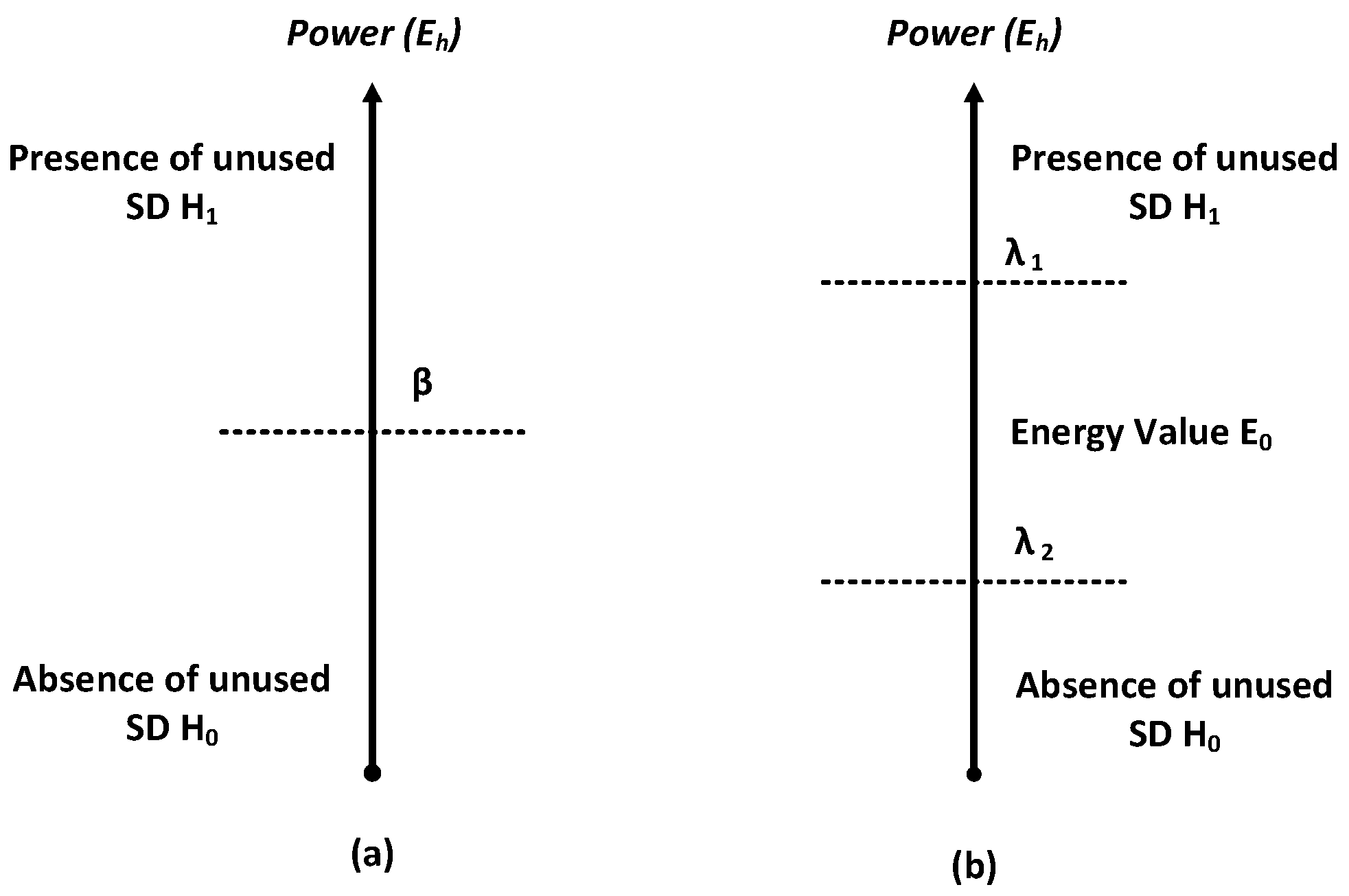
4.1. The Sensing Phase
4.2. The Interference Alignment Phase
4.3. Feasibility Conditions of IA
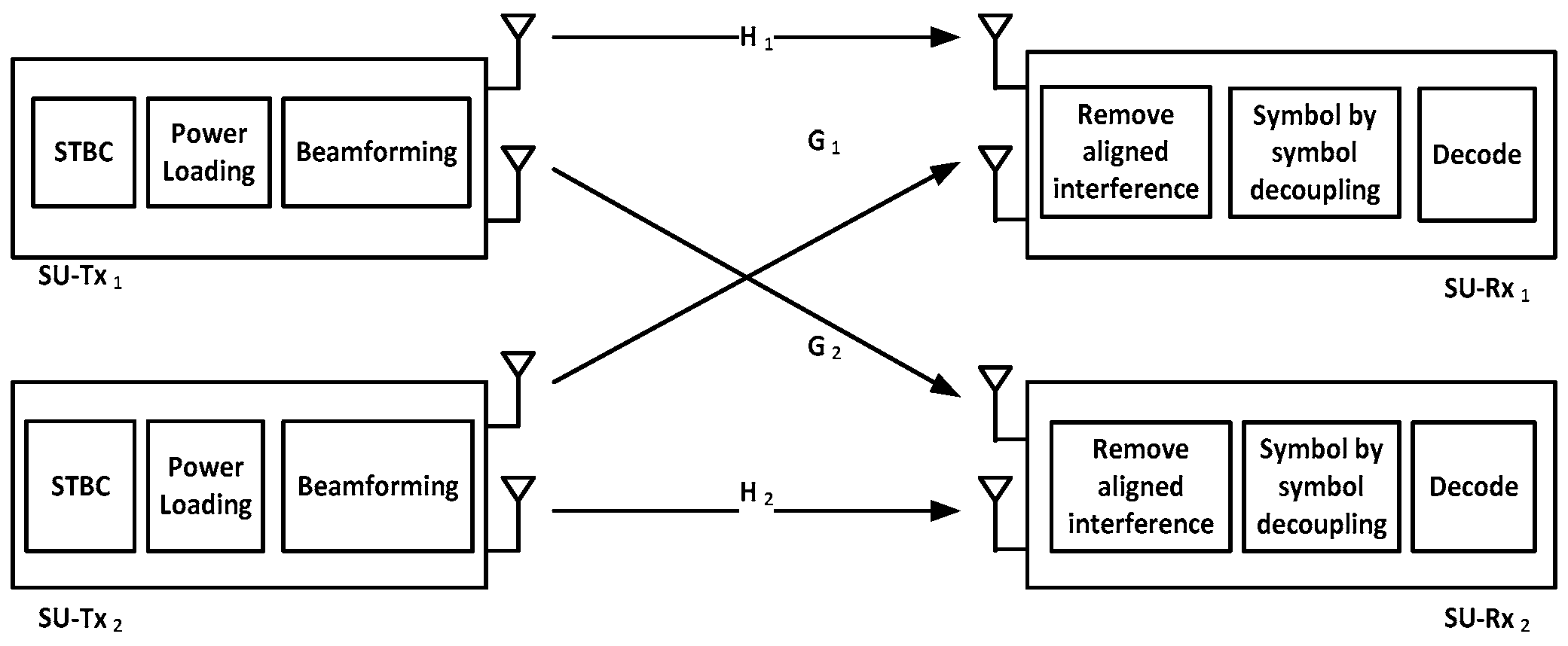
5. Opportunistic Interference Alignment with Space–Time Coding
5.1. Background
5.2. STBC Beamforming IA Process
6. Opportunistic Interference Alignment with Differential-STBC
6.1. Differential Encoding
6.2. Differential Decoding
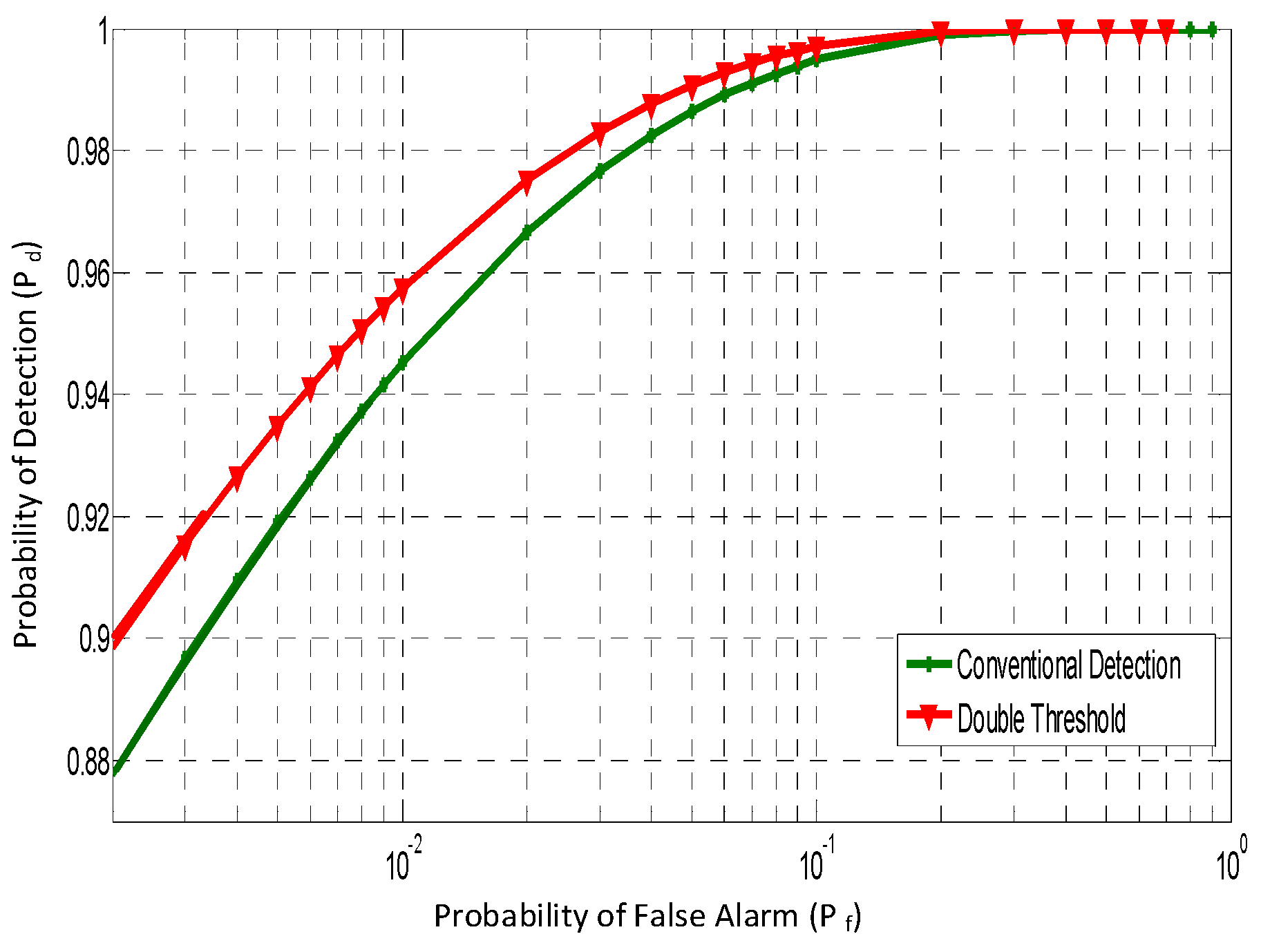
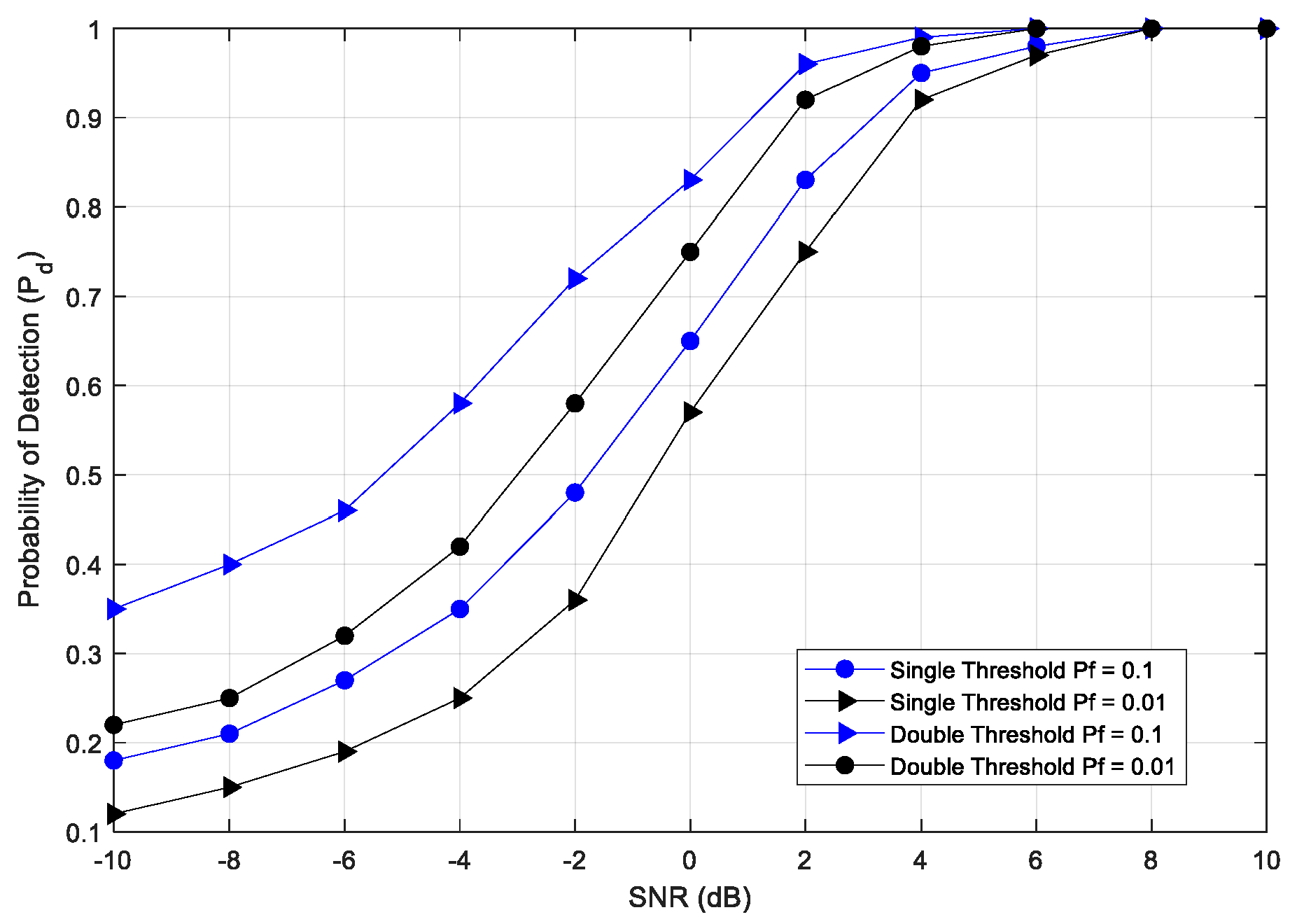
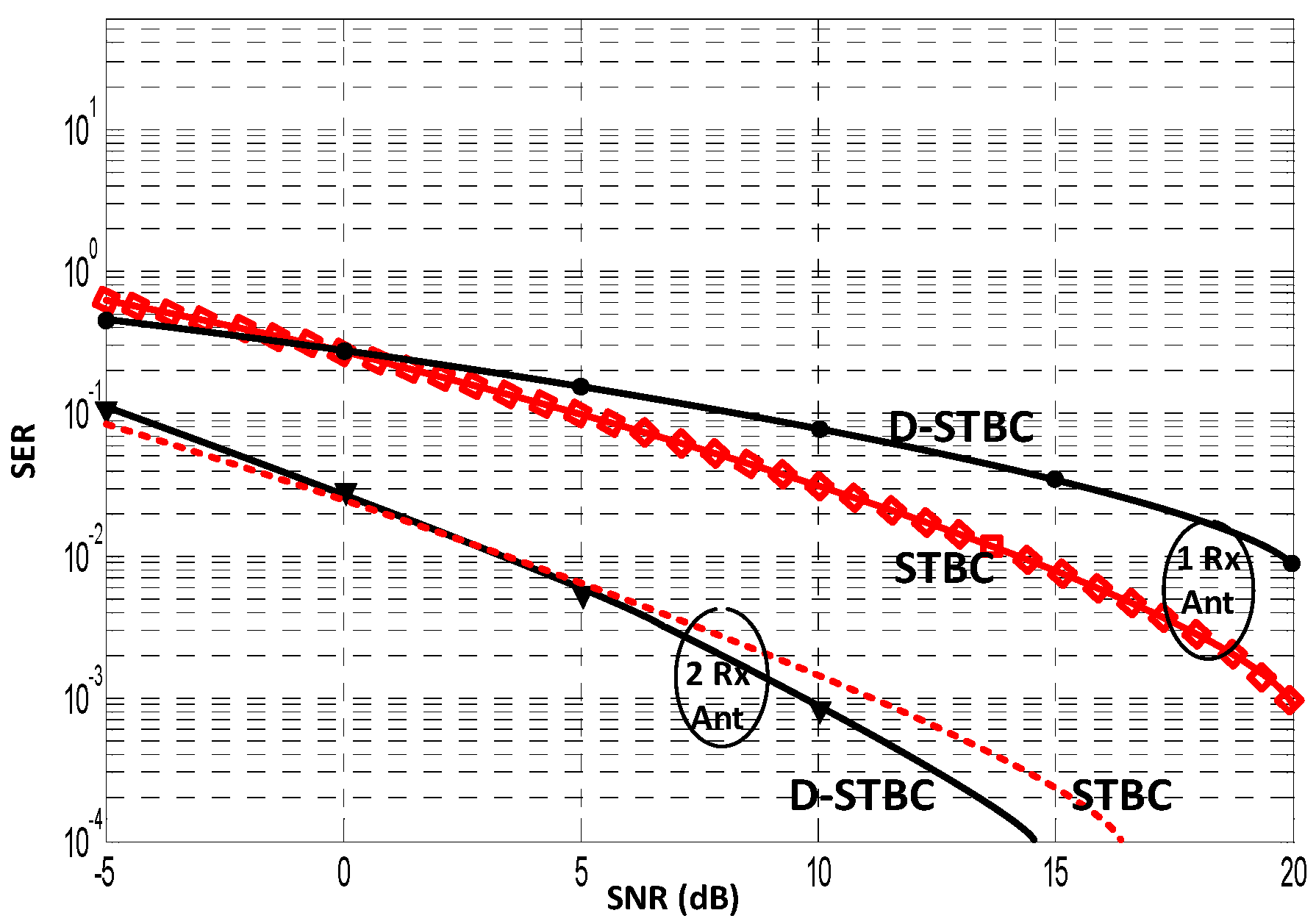
7. Simulation Results and Analysis
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Huang, X.L.; Li, Y.X.; Gao, Y.; Tang, X.W. Q-Learning-Based Spectrum Access for Multimedia Transmission Over Cognitive Radio Networks. IEEE Trans. Cogn. Commun. Netw. 2021, 7, 110–119. [Google Scholar] [CrossRef]
- Dong, L.; Wang, H.M.; Xiao, H. Secure Cognitive Radio Communication via Intelligent Reflecting Surface. IEEE Trans. Commun. 2021, 69, 4678–4690. [Google Scholar] [CrossRef]
- Mitola, J.; Maguire, G.Q. Cognitive radio: Making software radios more personal. IEEE Pers. Commun. 1999, 6, 13–18. [Google Scholar] [CrossRef]
- Nobar, S.K.; Ahmed, M.H.; Morgan, Y.; Mahmoud, S.A. Resource Allocation in Cognitive Radio-Enabled UAV Communication. IEEE Trans. Cogn. Commun. Netw. 2022, 8, 296–310. [Google Scholar] [CrossRef]
- Guo, S.; Zhao, X. Deep Reinforcement Learning Optimal Transmission Algorithm for Cognitive Internet of Things With RF Energy Harvesting. IEEE Trans. Cogn. Commun. Netw. 2022, 8, 1216–1227. [Google Scholar] [CrossRef]
- Haykin, S. Cognitive radio: Brain-empowered Wireless Communications. IEEE J. Sel. Areas Commun. 2005, 23, 201–220. [Google Scholar] [CrossRef]
- Ghosh, S.; Acharya, T.; Maity, S.P. Outage Analysis in SWIPT Enabled Cooperative AF/DF Relay Assisted Two-Way Spectrum Sharing Communication. IEEE Trans. Cogn. Commun. Netw. 2022, 8, 1434–1443. [Google Scholar] [CrossRef]
- Jafar, S.A. Interference Alignment—A New Look at Signal Dimensions in a Communication Network; Now Publishers: Norwell, MA, USA, 2011. [Google Scholar]
- El-Ayach, O.; Peters, S.W.; Heath, R.W. The Practical Challenges of Interference Alignment. IEEE Wirel. Commun. 2013, 20, 35–42. [Google Scholar] [CrossRef]
- Jafar, S.A.; Shamai, S. Degrees of Freedom Region of the MIMO X Channel. IEEE Trans. Inf. Theory 2008, 54, 151–170. [Google Scholar] [CrossRef]
- Perlaza, S.M.; Debbah, M.; Lasaulce, S.; Chaufray, J.M. Opportunistic Interference Alignment in MIMO Interference Channels. In Proceedings of the IEEE 19th International Symposium on Personal, Indoor and Mobile Radio Communications, Cannes, France, 15–18 September 2008; pp. 1–5. [Google Scholar]
- Perlaza, S.M.; Fawaz, N.; Lasaulce, S.; Debbah, M. From Spectrum Pooling to Space Pooling: Opportunistic Interference Alignment in MIMO Cognitive Networks. IEEE Trans. Signal Process. 2010, 58, 3728–3741. [Google Scholar] [CrossRef]
- Krikidis, I. A SVD-Based Location Coding for Cognitive Radio in MIMO Uplink Channels. IEEE Commun. Lett. 2010, 14, 912–914. [Google Scholar] [CrossRef]
- Tang, J.; Lambotharan, S.; Pomeroy, S. Interference Cancellation and Alignment Techniques for multiple-input and multiple-output Cognitive Relay Networks. IET Signal Process. 2013, 7, 188–200. [Google Scholar] [CrossRef]
- Alizadeh, A.; Bahrami, H.R.; Maleki, M.; Sastry, S. Spatial Sensing and Cognitive Radio Communication in the Presence of a K-User Interference Primary Network. IEEE J. Sel. Areas Commun. 2015, 33, 741–754. [Google Scholar] [CrossRef]
- Sboui, L.; Ghazzai, H.; Rezki, Z.; Alouini, M.S. Achievable Rate of a Cognitive MIMO Multiple Access Channel With Multi-Secondary Users. IEEE Commun. Lett. 2015, 19, 403–406. [Google Scholar] [CrossRef]
- Shen, C.; Fitz, M.P. Opportunistic Spatial Orthogonalization and Its Application in Fading Cognitive Radio Networks. IEEE J. Sel. Top. Signal Process. 2011, 5, 182–189. [Google Scholar] [CrossRef]
- Amir, M.; El-Keyi, A.; Nafie, M. Constrained Interference Alignment and the Spatial Degrees of Freedom of MIMO Cognitive Networks. IEEE Trans. Inf. Theory 2011, 57, 2994–3004. [Google Scholar] [CrossRef]
- Yang, H.J.; Shin, W.Y.; Jung, B.C.; Paulraj, A. Opportunistic Interference Alignment for MIMO Interfering Multiple-Access Channels. IEEE Trans. Wirel. Commun. 2013, 12, 2180–2192. [Google Scholar] [CrossRef]
- Baferani, M.H.; Abouei, J.; Yazdi, Z.Z. Interference Alignment in Overlay Cognitive Radio Femtocell Networks. IET Commun. 2016, 10, 1401–1410. [Google Scholar] [CrossRef]
- Tsinos, C.G.; Berberidis, K. Blind Opportunistic Interference Alignment in MIMO Cognitive Radio Systems. IEEE J. Emerg. Sel. Top. Circuits Syst. 2013, 3, 626–639. [Google Scholar] [CrossRef]
- Mosleh, S.; Abouei, J.; Aghabozorgi, M.S. Distributed Opportunistic Interference Alignment Using Threshold-Based Beamforming in MIMO Overlay Cognitive Radio. IEEE Trans. Veh. Technol. 2014, 63, 3783–3793. [Google Scholar] [CrossRef]
- Abdulkadir, Y.; Simpson, O.; Nwanekezie, N.; Sun, Y. Space-Time Opportunistic Interference Alignment in Cognitive Radio Networks. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), Doha, Qatar, 3–6 April 2016. [Google Scholar]
- Shen, Z.; Heath, J.; Andrews, J.; Evans, B.L. Comparison of Space-time Water-filling and Spatial Water-filling for MIMO Fading Channels. In Proceedings of the IEEE Global Telecommunications Conference (GLOBECOM), Dallas, TX, USA, 29 November–3 December 2004. [Google Scholar]
- Shen, Z.; Heath, J.; Andrews, J.; Evans, B.L. Space-Time Water-Filling for Composite MIMO Fading Channels. EURASIP J. Wirel. Commun. Netw. 2006, 2006, 016281. [Google Scholar] [CrossRef][Green Version]
- Goldsmith, A.; Jafar, S.A.; Jindal, N.; Vishwanath, S. Capacity limits of MIMO channels. IEEE J. Sel. Areas Commun. 2003, 21, 684–702. [Google Scholar] [CrossRef]
- Guler, B.; Yener, A. Selective Interference Alignment for MIMO Cognitive Femtocell Networks. IEEE J. Sel. Areas Commun. 2015, 32, 439–450. [Google Scholar] [CrossRef]
- Simpson, O.; Abdulkadir, Y.; Sun, Y.; Chi, B. Relay-Based Cooperative Spectrum Sensing with Improved Energy Detection in Cognitive Radio. In Proceedings of the International Conference on Broadband and Wireless Computing, Communications and Applications, Krakow, Poland, 4–6 November 2015. [Google Scholar]
- Kalamkar, S.S.; Banerjee, A. Improved Double Threshold Energy Detection for Cooperative Spectrum Sensing in Cognitive Radio. Def. Sci. J. 2013, 63, 34–40. [Google Scholar] [CrossRef]
- Jöngren, G.; Skoglund, M.; Ottersten, B. Combining Beamforming and Orthogonal Space–Time Block Coding. IEEE Trans. Inf. Theory 2003, 48, 611–627. [Google Scholar] [CrossRef]
- Zhou, S.; Giannakis, G.B. Optimal Transmitter Eigen-Beamforming and Space—Time Block Coding Based on Channel Correlations. IEEE Trans. Inf. Theory 2003, 49, 1673–1689. [Google Scholar] [CrossRef]
- Bhatnagar, M.R.; Hjørungnes, A. Linear Precoding of STBC over Correlated Ricean MIMO Channels. IEEE Trans. Wirel. Commun. 2010, 9, 1832–1836. [Google Scholar] [CrossRef]
- Abdel-Samad, A.; Davidson, T.N.; Gershman, A.B. Robust Transmit Eigen Beamforming Based on Imperfect Channel State Information. IEEE Trans. Signal Process. 2010, 54, 1596–1608. [Google Scholar] [CrossRef]
- Shi, L.; Zhang, W.; Xia, X.G. On Designs of Full Diversity Space-Time Block Codes for Two-User MIMO Interference Channels. IEEE Trans. Wirel. Commun. 2012, 11, 4184–4191. [Google Scholar]
- Li, L.; Jafarkhani, H. Maximum-Rate Transmission With Improved Diversity Gain for Interference Networks. IEEE Trans. Inf. Theory 2013, 59, 5313–5330. [Google Scholar]
- Naguib, A.; Seshadri, N.; Calderbank, A. Applications of Space-time Block Codes and Interference Suppression for High Capacity and High Data Rate Wireless Systems. In Proceedings of the Asilomar Conference, Pacific Grove, CA, USA, 1–4 November 1998. [Google Scholar]
- Alamouti, A. Simple Transmitter Diversity scheme for Wireless Communications. IEEE J. Sel. Areas Commun. 1998, 16, 1451–1458. [Google Scholar] [CrossRef]
- Cai, X.; Giannakis, G.B. Differential Space—Time Modulation With Eigen-Beamforming for Correlated MIMO Fading Channels. IEEE Trans. Signal Process. 2006, 54, 1279–1288. [Google Scholar]
- Bhatnagar, M.R.; Hjørungnes, A.; Song, L. Precoded Differential Orthogonal Space-Time Modulation Over Correlated Ricean MIMO Channels. IEEE J. Sel. Top. Signal Process. 2011, 2, 124–134. [Google Scholar] [CrossRef]
- Li, F.; Jafarkhani, H. Space-time Processing for X Channel using Precoders. IEEE Trans. Signal Process. 2011, 60, 1849–1861. [Google Scholar] [CrossRef]
- Alotaibi, F.T.; Chambers, J.A. Outage Probability of Cooperative Cognitive Networks Based on Distributed Orthogonal Space–Time Block Codes. IEEE Trans. Veh. Technol. 2011, 61, 3759–3765. [Google Scholar] [CrossRef]
- Telatar, I.E. Capacity of Multi-antenna Gaussian Channels. Eur. Trans. Telecommun. 1999, 10, 585–595. [Google Scholar] [CrossRef]
- Tse, D.; Viswanath, P. Fundamentals of Wireless Communication; Cambridge University Press: Cambridge, UK, 2005. [Google Scholar]
- Guo, X.; Xia, X.G. On Full Diversity Space—Time Block Codes With Partial Interference Cancellation Group Decoding. IEEE Trans. Inf. Theory 2009, 55, 4366–4385. [Google Scholar] [CrossRef]
- StÄuber, G.L. Principles of Mobile Communication, 2nd ed.; Kluwer Academic Publisher: Dordrecht, The Netherlands, 2001. [Google Scholar]
- Simpson, O. Optimal Cooperative Spectrum Sensing for Cognitive Radio. Ph.D. Thesis, University of Hertfordshire, Hatfield, UK, 2016. [Google Scholar]
- Atapattu, S.; Tellambura, C.; Jiang, H. Energy Detection Based Cooperative Spectrum Sensing in Cognitive Radio Networks. IEEE Trans. Wirel. Commun. 2011, 10, 1232–1241. [Google Scholar] [CrossRef]
- Palomar, D.P.; Fonollosa, J.R. Practical Algorithms for a Family of Water-filling Solutions. IEEE Trans. Signal Process. 2005, 53, 686–695. [Google Scholar] [CrossRef]
- Abdulkadir, Y.; Simpson, O.; Nwanekezie, N.; Sun, Y. A Differential Space-Time Coding Scheme for Cooperative Spectrum Sensing in Cognitive Radio Networks. In Proceedings of the IEEE 26th International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Hong Kong, China, 30 August–2 September 2015; pp. 1386–1391. [Google Scholar]
- Yetis, C.M.; Gou, T.; Jafar, S.A.; Kayran, A.H. On Feasibility of Interference Alignment in MIMO Interference Networks. IEEE Trans. Signal Process. 2010, 58, 4771–4782. [Google Scholar] [CrossRef]
- Gomadan, K.; Cadambe, V.R.; Jafar, S.A. A Distributed Numerical Approach to Interference Alignment and Applications to Wireless Interference Networks. IEEE Trans. Inf. Theory 2011, 57, 3309–3322. [Google Scholar] [CrossRef]
- Guo, C.; Peng, T.; Xu, S.; Wang, H.; Wang, W. Cooperative Spectrum Sensing with Cluster-Based Architecture in Cognitive Radio Networks. In Proceedings of the IEEE 69th Vehicular Technology Conference (VTC), Barcelona, Spain, 26–29 April 2009; pp. 1–5. [Google Scholar]
- Gomadam, K.S.; Cadambe, V.R.; Jafar, S.A. Approaching the Capacity of Wireless Networks through Distributed Interference Alignment. In Proceedings of the IEEE Global Telecommunications Conference, New Orleans, LA, USA, 30 November–4 December 2008; pp. 1–6. [Google Scholar]
- Tarokh, V.; Jafarkhani, H. A Differential Detection Scheme for Transmit Diversity. IEEE J. Sel. Areas Commun. 2000, 18, 1161–1174. [Google Scholar] [CrossRef]
- Ganesan, A.; Rajan, B.S. Interference Alignment With Diversity for the 2 × 2 X-Network With Four Antennas. IEEE Trans. Inf. Theory 2014, 60, 3576–3592. [Google Scholar] [CrossRef]
- Jafarkhani, H.; Tarokh, V. Multiple Transmit Antenna Differential detection from Generalized Orthogonal Designs. IEEE Trans. Inf. Theory 2001, 47, 2626–2631. [Google Scholar] [CrossRef]
- Ganesan, G.; Stoica, P. Differential Modulation using Space–time Block Codes. IEEE Signal Process. Lett. 2002, 9, 57–60. [Google Scholar] [CrossRef]
- Abdulkadir, Y.; Simpson, O.; Sun, Y. Interference Alignment for Cognitive Radio Communications and Networks: A Survey. J. Sens. Actuator Netw. 2019, 8, 50. [Google Scholar] [CrossRef]
- Slaney, A.; Sun, Y. Space-time coding for wireless communications. IEE Proc. Commun. 2006, 153, 509–518. [Google Scholar] [CrossRef][Green Version]
- Yang, J.; Sun, Y.; Senior, J.M.; Pem, N. Channel estimation for wireless communications using space-time block coding techniques. In Proceedings of the IEEE International Symposium on Circuits and Systems, Bangkok, Thailand, 25–28 May 2003. [Google Scholar]
- Delestre, F.; Masoud, E.; Sun, Y.; Slaney, A. Detection scheme for space-time block coded wireless communications without channel state information. In Proceedings of the IEEE International Conference on Communication Systems, Guangzhou, China, 19–21 November 2008. [Google Scholar]
- Bani, K.; Kulkarni, V. Hybrid Spectrum Sensing Using MD and ED for Cognitive Radio Networks. J. Sens. Actuator Netw. 2022, 11, 36. [Google Scholar] [CrossRef]
- Abdulkadir, Y. Optimizing Cooperative Spectrum Sensing in Cognitive Radio Networks Using Interference Alignment and Space-Time Coding. Ph.D. Thesis, University of Hertfordshire, Hatfield, UK, 2017. [Google Scholar]
- Nnamdi, N.; Simpson, O.; Wojaiye, G.O.; Sun, Y. Co-Efficient Vector Based Differential Distributed Quasi-Orthogonal Space Time Frequency Coding. Sensors 2023, 23, 7540. [Google Scholar]
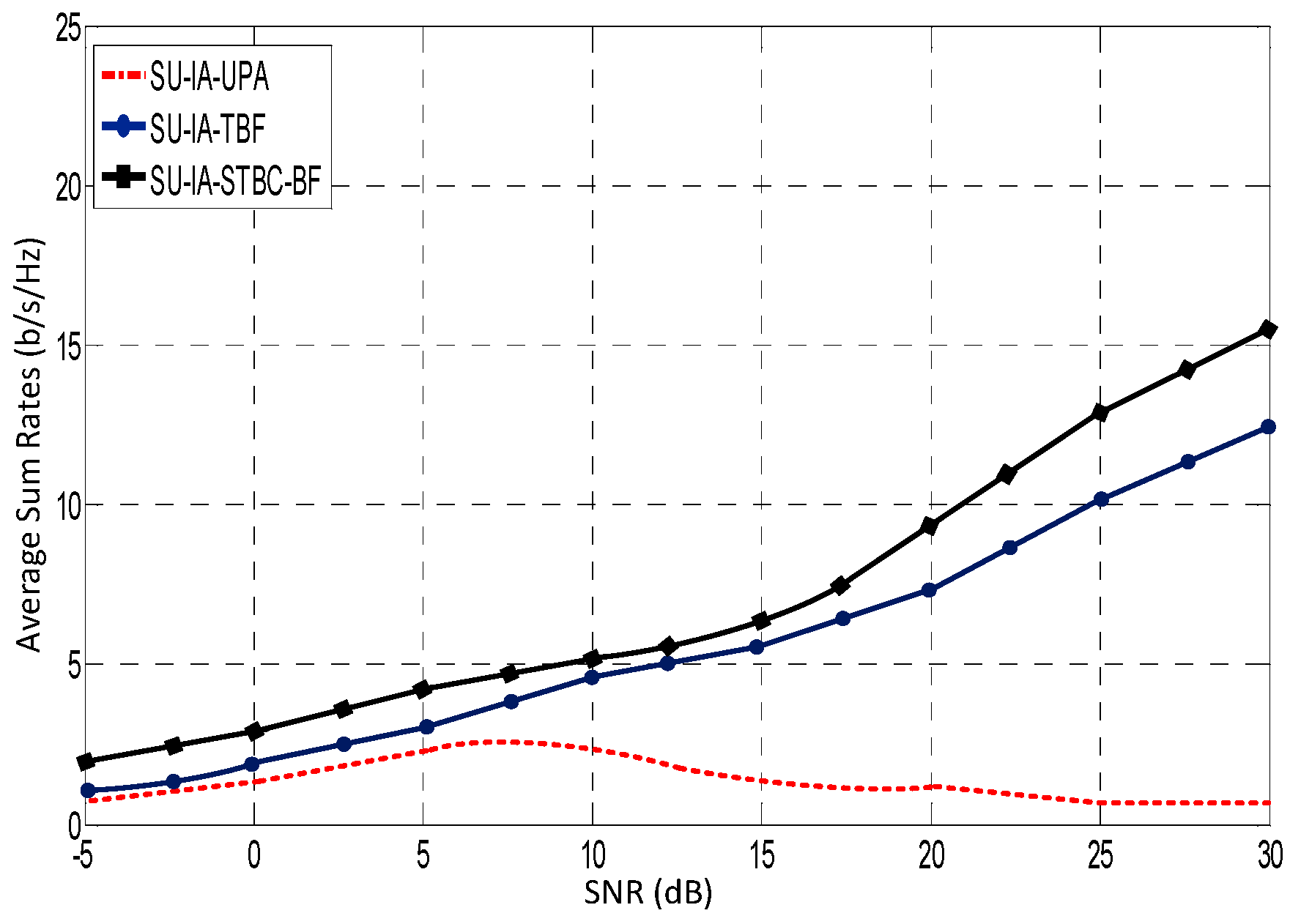
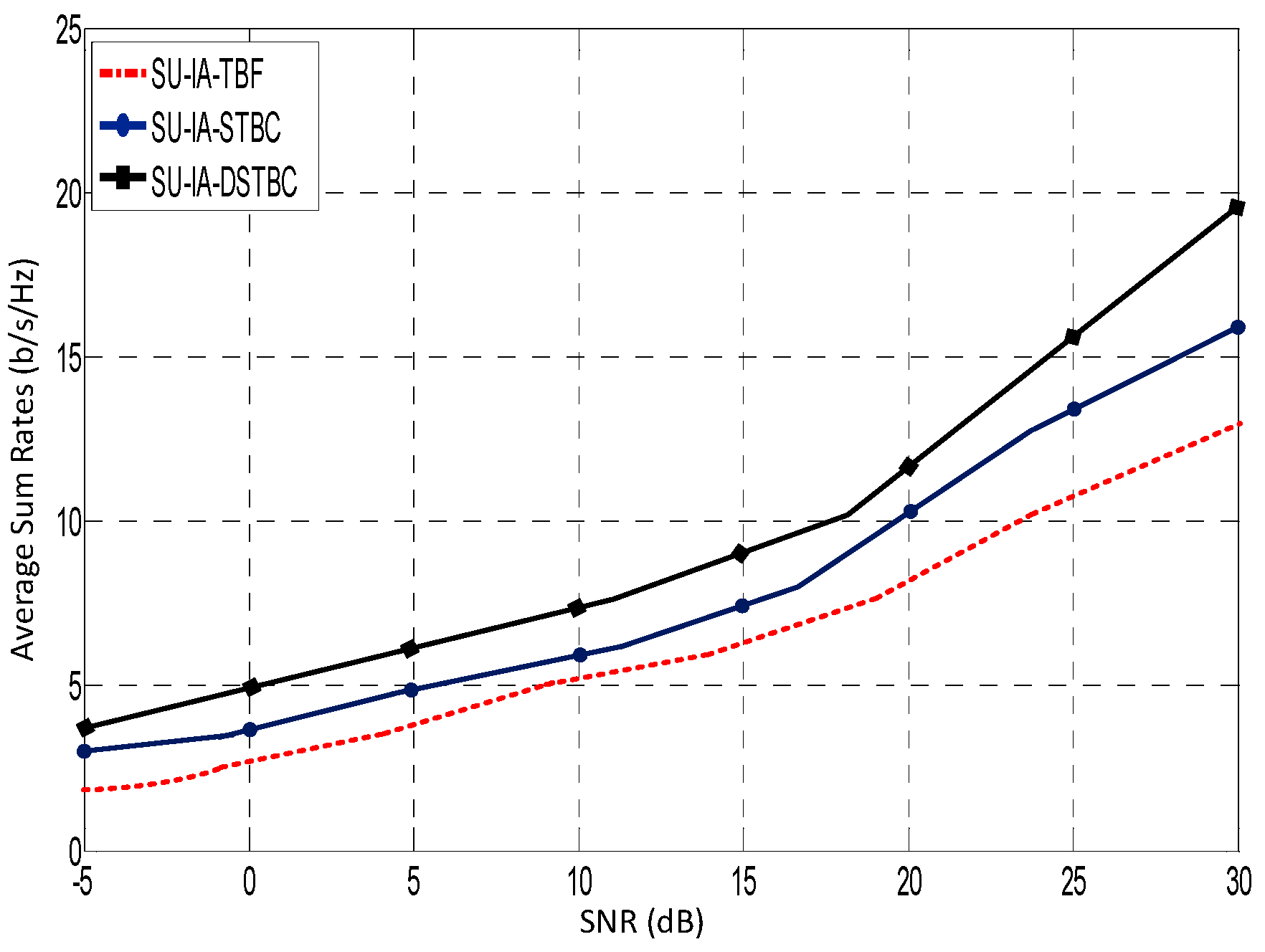
| Aspect | Energy Detection | Matched Filtering | Cyclostationary Feature Detection | Eigenvalue-Based Detection |
|---|---|---|---|---|
| Implementation Complexity | Simple and low complexity | High complexity; requires matched filter design | Moderate to high complexity; requires spectral correlation | Moderate to high complexity; requires covariance matrix computation |
| Prior Knowledge Required | None; signal-agnostic | Requires knowledge of signal’s waveform or pattern | Requires knowledge of signal’s cyclic features | No prior knowledge of signal waveform required |
| Sensitivity to Noise | High; sensitive to noise power variations | Moderate; performance depends on filter design and noise | High; sensitive to noise but can be robust with correct features | Moderate to high; performance affected by noise and interference |
| Application Suitability | Suitable for environments where simplicity and low cost are key | Suitable when exact signal waveform is known and precise synchronization is possible | Suitable for signals with known cyclic features and in moderate-to-high SNR environments | Suitable for detecting signals in noisy environments and when precise signal structure is unknown |
| Steps | Algorithm 1 SU Election Algorithm |
|---|---|
| I | Calculate of all SUs from the FC, and place nodes in ascending order of in a queue. Choose nodes with the shortest in the queue as a set of candidate SUs to form clusters denoted as ; |
| II | Randomly assign nodes as the SU set from where and initialize where ; |
| III | Allocate each node into the cluster, where and denotes the observation vector for each given SU node . For each cluster, update by averaging of all nodes in cluster k. Similarly, update the node ID of each selected SU as . |
| Parameters | Specification |
|---|---|
| Simulation platform | Monte-Carlo simulations using MATLAB |
| Modulation type | BPSK |
| Number of bits per symbol | 1 b/s |
| Diversity technique | STBC, DSTBC |
| Antenna configuration (Number of transmitting antennas and receiving antennas) | 2 × 2, 2 × 1 2 Tx SUs 2 Rx SUs 2 Tx SUs 1 Tx SU |
| Channel | Rayleigh (fixed and independent) |
| Signal-to-noise ratio (SNR) | −5 to 30 dB |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abdulkadir, Y.; Simpson, O.; Sun, Y. Opportunistic Interference Alignment in Cognitive Radio Networks with Space–Time Coding. J. Sens. Actuator Netw. 2024, 13, 46. https://doi.org/10.3390/jsan13050046
Abdulkadir Y, Simpson O, Sun Y. Opportunistic Interference Alignment in Cognitive Radio Networks with Space–Time Coding. Journal of Sensor and Actuator Networks. 2024; 13(5):46. https://doi.org/10.3390/jsan13050046
Chicago/Turabian StyleAbdulkadir, Yusuf, Oluyomi Simpson, and Yichuang Sun. 2024. "Opportunistic Interference Alignment in Cognitive Radio Networks with Space–Time Coding" Journal of Sensor and Actuator Networks 13, no. 5: 46. https://doi.org/10.3390/jsan13050046
APA StyleAbdulkadir, Y., Simpson, O., & Sun, Y. (2024). Opportunistic Interference Alignment in Cognitive Radio Networks with Space–Time Coding. Journal of Sensor and Actuator Networks, 13(5), 46. https://doi.org/10.3390/jsan13050046








