Refined LSTM Based Intrusion Detection for Denial-of-Service Attack in Internet of Things
Abstract
:1. Introduction
- We present an effective model based on an improved deep learning algorithm for detecting and classifying intrusions in IoT.
- We proposed a refined long short-term memory (RLSTM) model which can detect denial-of-service (DoS) intrusions with a high level of accuracy using two voluminous traffic datasets, namely, NSL-KDD and CICIDS-2017 datasets to test the performance of the proposed model.
- To boost the classification performance of the developed model, we performed encoding, dimensionality reduction, and normalization preprocessing procedures on the two datasets.
- We deployed the following performance evaluation metrics: precision, recall, F1-score, and classification accuracy to assess the effectiveness of the proposed models.
- For evaluation, we compared the performance of the modeled RLSTM model with other machine learning methods using both NSL-KDD and CICIDS-2017 datasets. The experimental results illustrate that the modeled RLSTM model is very suitable for IoT intrusion detection. The performance of the RLSTM model is superior to the other considered classification methods on the two datasets.
Overview of Denial-of-Service (DoS) Attack
2. Related Works
3. Proposed IDS Model
3.1. Refined Long Short-Term Memory (RLSTM)
3.2. RLSTM Experimental Setup
| Algorithm 1: RLSTM Model | ||
| 1 | Load Datasets | Datasets: NSL-KDD; CICIDS-2017 (training sets and testing sets); |
| 2 | for | Data in Training and Test datasets do |
| 3 | Extract Features (x) | |
| 4 | Extract Labels (y) | |
| Input: | Features Extracted from Datasets | |
| Output: | Classification results | |
| 5 | for | Features in x do |
| if datasets feature = non-numerical then | ||
| Encode using 1-to-N encoding | ||
| 6 | Normalize features | Using Min-max normalization |
| 7 | Training | Train RLSTM model using the NSL-KDD and CICIDS-2017 training set; |
| Add activation function = Softmax; Then classify; | ||
| 8 | Testing | RLSTM model testing |
| Testing sets are fed into the RLSTM to detect attacks; | ||
| 9 | Evaluation: | |
| Compute (loss = ‘cross entropy’, optimizer = ‘adam’) | ||
| Compute classification results using {accuracy, precision, recall and f1-score} | ||
| 10 | Output: | Classification results |
4. Experimental Evaluation
4.1. Used Datasets
4.2. Data Pre-Processing Steps
4.3. Performance Metrics
5. Results and Discussion
5.1. Evaluation Results of the Two Datasets
5.2. Comparison with Machine Learning Algorithms
5.3. Performance Comparison with Previous Studies
6. Threat to Validity
- Construct validity: refers to the relationship between the experiment carried out and the results obtained. This threat is mostly related to the algorithms employed in the experiment. As a result, we were certain that the algorithm’s descriptions and pseudocodes employed in this study were correct. The results obtained from the performance metrics in terms of accuracy and other metrics were satisfactory, showing that the proposed model is consistent.
- Internal validity: Internal threats are relatively linked to the experimental setup. Because different parameters must be defined and selected for the algorithm, we employed a grid-search approach to mitigate this threat. The performance metrics employed, and the used dataset are all well-known. As a result, there have been no changes that could have resulted in inaccurate evaluation results.
- External validity: external threats refer to the ability to apply our findings and conclusions to different situations. In this study, the experiments were carried out with two voluminous and popular IDS datasets; NSL-KDD and CICIDS-2017 datasets. Due to the limited availability of real-time IoT network traffic datasets, it should be noted that the two datasets deployed are not generated from typical IoT devices. However, the deployed datasets show similar traits, attributes, and trends of IoT network traffic and recent attack scenarios. In addition, the findings from the work were consistent with what has been found in the literature irrespective of the datasets. In the future, when we model another intrusion detection system, we plan to validate the model using the Bot-IoT dataset which is an IDS dataset designed specifically for IoT.
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| ANN | Artificial Neural Network |
| CART | Classification and Regression Tree |
| CNN | Convolutional Neural Network |
| DL | Deep Learning |
| DT | Decision Tree |
| DoS | Denial of Service |
| DDoS | Distributed Denial of Service |
| ERT | Extremely Randomized Trees |
| FN | False Negative |
| FP | False Positive |
| GBM | Gradient Boosted Machine |
| IDS | Intrusion Detection System |
| IoT | Internet of Things |
| k-NN | k-Nearest Neighbor |
| RLSTM | Refined Long Short-Term Memory |
| ML | Machine Learning |
| MLPNN | Multilayer perceptron Neural Network |
| NB | Naïve Bayes |
| NSL-KDD | Network Security Laboratory-Knowledge Discovery in Databases |
| RNN | Recurrent Neural Network |
| TN | True Negative |
| TP | True Positive |
References
- Thamilarasu, G.; Chawla, S. Towards deep-learning-driven intrusion detection for the Internet of Things. Sensors 2019, 19, 1977. [Google Scholar] [CrossRef] [Green Version]
- Evans, D. The Internet of Things: How the next evolution of the Internet is changing everything. CISCO White Pap. 2011, 1, 1–11. [Google Scholar]
- Ray, S.; Jin, Y.; Raychowdhury, A. The changing computing paradigm with Internet of Things: A tutorial introduction. IEEE Des. Test 2016, 33, 76–96. [Google Scholar] [CrossRef]
- Palattella, M.R.; Dohler, M.; Grieco, A.; Rizzo, G.; Torsner, J.; Engel, T.; Ladid, L. Internet of things in the 5G era: Enablers, architecture, and business models. IEEE J. Sel. Areas Commun. 2016, 34, 510–527. [Google Scholar] [CrossRef] [Green Version]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of things: A survey on enabling technologies, protocols, and applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Cvitić, I.; Peraković, D.; Periša, M.; Stojanović, M.D. Novel classification of IoT devices based on traffic flow features. J. Organ. End User Comput. (JOEUC) 2021, 33, 1–20. [Google Scholar] [CrossRef]
- Akpakwu, G.A.; Silva, B.J.; Hancke, G.P.; Abu-Mahfouz, A.M. A survey on 5G networks for the Internet of Things: Communication technologies and challenges. IEEE Access 2017, 6, 3619–3647. [Google Scholar] [CrossRef]
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A survey on IoT security: Application areas, security threats, and solution architectures. IEEE Access 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Cvitić, I.; Peraković, D.; Periša, M.; Gupta, B. Ensemble machine learning approach for classification of IoT devices in smart home. Int. J. Mach. Learn. Cybern. 2021, 12, 3179–3202. [Google Scholar] [CrossRef]
- Al-Garadi, M.A.; Mohamed, A.; Al-Ali, A.; Du, X.; Guizani, M. A survey of machine and deep learning methods for Internet of Things (IoT) security. IEEE Commun. Surv. Tutor. 2020, 22, 1646–1685. [Google Scholar] [CrossRef] [Green Version]
- Yaqoob, I.; Hashem, I.A.T.; Ahmed, A.; Kazmi, S.A.; Hong, C.S. Internet of things forensics: Recent advances, taxonomy, requirements, and open challenges. Future Gener. Comput. Syst. 2019, 92, 265–275. [Google Scholar] [CrossRef]
- Adefemi Alimi, K.O.; Ouahada, K.; Abu-Mahfouz, A.M.; Rimer, S. A survey on the security of low power wide area networks: Threats, challenges, and potential solutions. Sensors 2020, 20, 5800. [Google Scholar] [CrossRef] [PubMed]
- Sambangi, S.; Gondi, L. A Machine Learning Approach for DDoS (Distributed Denial of Service) Attack Detection Using Multiple Linear Regression. In Proceedings of the 14th International Conference on Interdisciplinarity in Engineering, Târgu Mureș, Romania, 8–9 October 2020; Volume 63, p. 51. [Google Scholar]
- Liu, Z.; Thapa, N.; Shaver, A.; Roy, K.; Yuan, X.; Khorsandroo, S. Anomaly detection on iot network intrusion using machine learning. In Proceedings of the 2020 International Conference on Artificial Intelligence, Big Data, Computing and Data Communication Systems (icABCD), Durban, South Africa, 6–7 August 2020; pp. 1–5. [Google Scholar]
- Verma, A.; Ranga, V. ELNIDS: Ensemble learning based network intrusion detection system for RPL based Internet of Things. In Proceedings of the 4th International conference on Internet of Things: Smart innovation and usages (IoT-SIU), Ghaziabad, India, 18 April 2019; pp. 1–6. [Google Scholar]
- Khraisat, A.; Gondal, I.; Vamplew, P.; Kamruzzaman, J.; Alazab, A. A novel ensemble of hybrid intrusion detection system for detecting internet of things attacks. Electronics 2019, 8, 1210. [Google Scholar] [CrossRef] [Green Version]
- Tang, C.; Luktarhan, N.; Zhao, Y. SAAE-DNN: Deep Learning Method on Intrusion Detection. Symmetry 2020, 12, 1695. [Google Scholar] [CrossRef]
- Thapa, N.; Liu, Z.; Kc, D.B.; Gokaraju, B.; Roy, K. Comparison of Machine Learning and Deep Learning Models for Network Intrusion Detection Systems. Future Internet 2020, 12, 167. [Google Scholar] [CrossRef]
- Jazzar, M.; Hamad, M. An Analysis Study of IoT and DoS Attack Perspective. In Proceedings of International Conference on Intelligent Cyber-Physical Systems; Springer: Singapore, 2022; pp. 127–142. [Google Scholar]
- Hussain, F.; Abbas, S.G.; Husnain, M.; Fayyaz, U.U.; Shahzad, F.; Shah, G.A. IoT DoS and DDoS attack detection using ResNet. In Proceedings of the 2020 IEEE 23rd International Multitopic Conference (INMIC), Bahawalpur, Pakistan, 5–7 November 2020; pp. 1–6. [Google Scholar]
- Arnaboldi, L.; Morisset, C. Generating synthetic data for real world detection of DoS attacks in the IoT. In Federation of International Conferences on Software Technologies: Applications and Foundations; Springer: Cham, Switzerland, 2018; pp. 130–145. [Google Scholar]
- Mahmoud, R.; Yousuf, T.; Aloul, F.; Zualkernan, I. Internet of things (IoT) security: Current status, challenges and prospective measures. In Proceedings of the 2015 10th International Conference for Internet Technology and Secured Transactions (ICITST), London, UK, 14–16 December 2015; pp. 336–341. [Google Scholar]
- Leyden, J. Biggest DDoS Attack in History Hammers Spamhaus. The Register, 27 March 2013. Available online: https://www.theregister.co.uk/2013/03/27/spamhaus_ddos_megaflood/ (accessed on 11 September 2021).
- Zargar, S.T.; Joshi, J.; Tipper, D. A survey of defense mechanisms against distributed denial of service (DDoS) flooding attacks. IEEE Commun. Surv. Tutor. 2013, 15, 2046–2069. [Google Scholar] [CrossRef] [Green Version]
- Aminu Ghali, A.; Ahmad, R.; Alhussian, H.S.A. Comparative analysis of DoS and DDoS attacks in Internet of Things environment. In Computer Science On-Line Conference; Springer: Cham, Switzerland, 2020; pp. 183–194. [Google Scholar]
- Kumar, P.; Bagga, H.; Netam, B.S.; Uduthalapally, V. SAD-IoT: Security Analysis of DDoS Attacks in IoT Networks. Wirel. Pers. Commun. 2022, 122, 87–108. [Google Scholar] [CrossRef]
- Almaraz-Rivera, J.G.; Perez-Diaz, J.A.; Cantoral-Ceballos, J.A. Transport and Application Layer DDoS Attacks Detection to IoT Devices by Using Machine Learning and Deep Learning Models. Sensors 2022, 22, 3367. [Google Scholar] [CrossRef]
- Bures, M.; Klima, M.; Rechtberger, V.; Ahmed, B.S.; Hindy, H.; Bellekens, X. Review of Specific Features and Challenges in the Current Internet of Things Systems Impacting Their Security and Reliability. In World Conference on Information Systems and Technologies; Springer: Cham, Switzerland, 2021; pp. 546–556. [Google Scholar]
- Shah, Z.; Ullah, I.; Li, H.; Levula, A.; Khurshid, K. Blockchain Based Solutions to Mitigate Distributed Denial of Service (DDoS) Attacks in the Internet of Things (IoT): A Survey. Sensors 2022, 22, 1094. [Google Scholar] [CrossRef]
- McMillen, D. Internet of Threats: IoT Botnets Drive Surge in Network Attacks. 2021. Available online: https://securityintelligence.com/posts/internet-of-threats-iot-botnets-network-attacks/ (accessed on 17 December 2021).
- Balaban, I. Denial-of-Service Attack. Int. J. Inf. Secur. Cybercrime (IJISC) 2021, 10, 59–64. [Google Scholar] [CrossRef]
- Verma, A.; Ranga, V. Machine learning based intrusion detection systems for IoT applications. Wirel. Pers. Commun. 2020, 111, 2287–2310. [Google Scholar] [CrossRef]
- Mohammed, M.M.; Alheeti, K.M. Evaluating Machine Learning Algorithms to Detect and Classify Attacks in IoT. In Proceedings of the International Conference on Communication & Information Technology (ICICT), Basrah, Iraq, 5–6 June 2021; pp. 180–184. [Google Scholar]
- Chopra, A.; Behal, S.; Sharma, V. Evaluating machine learning algorithms to detect and classify DDoS attacks in IoT. In Proceedings of the 2021 8th International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 17–19 March 2021; pp. 517–521. [Google Scholar]
- Hodo, E.; Bellekens, X.; Hamilton, A.; Dubouilh, P.L.; Iorkyase, E.; Tachtatzis, C.; Atkinson, R. Threat analysis of IoT networks using artificial neural network intrusion detection system. In Proceedings of the International Symposium on Networks, Computers and Communications (ISNCC), Hammamet, Tunisia, 11 May 2016; pp. 1–6. [Google Scholar]
- Mohammed, S. A Machine Learning-Based Intrusion Detection of DDoS Attack on IoT Devices. Int. J. 2021, 10, 2278–3091. [Google Scholar]
- Cvitić, I.; Peraković, D.; Gupta, B.; Choo, K.K.R. Boosting-based DDoS detection in internet of things systems. IEEE Internet Things J. 2021, 9, 2109–2123. [Google Scholar] [CrossRef]
- Roopak, M.; Tian, G.Y.; Chambers, J. An intrusion detection system against ddos attacks in iot networks. In Proceedings of the 2020 10th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 6–8 January 2020; pp. 562–567. [Google Scholar]
- Susilo, B.; Sari, R.F. Intrusion detection in IoT networks using deep learning algorithm. Information 2020, 11, 279. [Google Scholar] [CrossRef]
- Ma, L.; Chai, Y.; Cui, L.; Ma, D.; Fu, Y.; Xiao, A. A deep learning-based DDoS detection framework for Internet of Things. In Proceedings of the ICC 2020-2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar]
- Sahu, A.K.; Sharma, S.; Tanveer, M.; Raja, R. Internet of Things attack detection using hybrid Deep Learning Model. Comput. Commun. 2021, 176, 146–154. [Google Scholar] [CrossRef]
- Roy, B.; Cheung, H. A deep learning approach for intrusion detection in internet of things using bi-directional long short-term memory recurrent neural network. In Proceedings of the 2018 28th International Telecommunication Networks and Applications Conference (ITNAC), Sydney, NSW, Australia, 21–23 November 2018; pp. 1–6. [Google Scholar]
- Hochreiter, S.; Schmidhuber, J. Long short-term memory. Neural Comput. 1997, 9, 1735–1780. [Google Scholar] [CrossRef]
- FatimaEzzahra, L.; Samira, D.; Khadija, D.; Badr, H. Intrusion detection systems using long short-term memory (LSTM). J. Big Data 2021, 8, 65. [Google Scholar]
- Qaddoura, R.; Al-Zoubi, M.; Faris, H.; Almomani, I. A Multi-Layer Classification Approach for Intrusion Detection in IoT Networks Based on Deep Learning. Sensors 2021, 21, 2987. [Google Scholar] [CrossRef]
- Ramotsoela, T.D.; Hancke, G.P.; Abu-Mahfouz, A.M. Behavioural intrusion detection in water distribution systems using neural networks. IEEE Access 2020, 8, 190403–190416. [Google Scholar] [CrossRef]
- Sun, P.; Liu, P.; Li, Q.; Liu, C.; Lu, X.; Hao, R.; Chen, J. DL-IDS: Extracting features using CNN-LSTM hybrid network for intrusion detection system. Secur. Commun. Netw. 2020, 2020, 8890306. [Google Scholar] [CrossRef]
- Yao, R.; Wang, N.; Liu, Z.; Chen, P.; Sheng, X. Intrusion Detection System in the Advanced Metering Infrastructure: A Cross-Layer Feature-Fusion CNN-LSTM-Based Approach. Sensors 2021, 21, 626. [Google Scholar] [CrossRef] [PubMed]
- Tavallaee, M.; Bagheri, E.; Lu, W.; Ghorbani, A.A. A detailed analysis of the KDD CUP 99 data set. In Proceedings of the 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications, Ottawa, ON, Canada, 8–10 July 2009; pp. 1–6. [Google Scholar]
- Alimi, O.A.; Ouahada, K.; Abu-Mahfouz, A.M.; Rimer, S.; Alimi, K.O.A. A review of research works on supervised learning algorithms for SCADA intrusion detection and classification. Sustainability 2021, 13, 9597. [Google Scholar] [CrossRef]
- Imrana, Y.; Xiang, Y.; Ali, L.; Abdul-Rauf, Z. A bidirectional LSTM deep learning approach for intrusion detection. Expert Syst. Appl. 2021, 185, 115524. [Google Scholar] [CrossRef]
- Alimi, O.A.; Ouahada, K.; Abu-Mahfouz, A.M.; Rimer, S. Power system events classification using genetic algorithm-based feature weighting technique for support vector machine. Heliyon 2021, 7, e05936. [Google Scholar] [CrossRef] [PubMed]
- Alimi, O.A.; Ouahada, K.; Abu-Mahfouz, A.M.; Alimi, K.O.A. Empirical Comparison of Machine Learning Algorithms for Mitigating Power Systems Intrusion Attacks. In Proceedings of the 2020 International Symposium on Networks, Computers and Communications (ISNCC), Montreal, QC, Canada, 20–22 October 2020; pp. 1–5. [Google Scholar]

| Parameter | NSL-KDD Specification | CICIDS-2017 Specification |
|---|---|---|
| Sequence input layer | 1 | 1 |
| Sequence input length | 25 features | 65 features |
| Number of hidden layers neurons | 100 | 120 |
| Number of fully connected layers | 2 | 2 |
| Activation function | Softmax | Softmax |
| Optimizer | Adam | Adam |
| Batch size | 150 | 100 |
| Epochs | 50 | 13 |
| Learning rate | 0.01 | 0.001 |
| Traffic | Normal | U2R Attack | DoS Attack | R2L Attack | Probing Attack |
|---|---|---|---|---|---|
| Training | 67,343 | 52 | 45,927 | 995 | 11,656 |
| Testing | 9711 | 200 | 7458 | 2887 | 2421 |
| Filename | Attacks | Number of Samples |
|---|---|---|
| Wednesday working hours. pcap | Benign, | 440,031 |
| DoS Hulk | 231,073 | |
| DoS GoldenEye | 10,293 | |
| DoS Slowloris | 5796 | |
| DoS Slowhttptest | 5499 | |
| Heartbleed | 11 |
| Classifier | Class | Accuracy (%) | Precision (%) | Recall (%) | F-Score (%) |
|---|---|---|---|---|---|
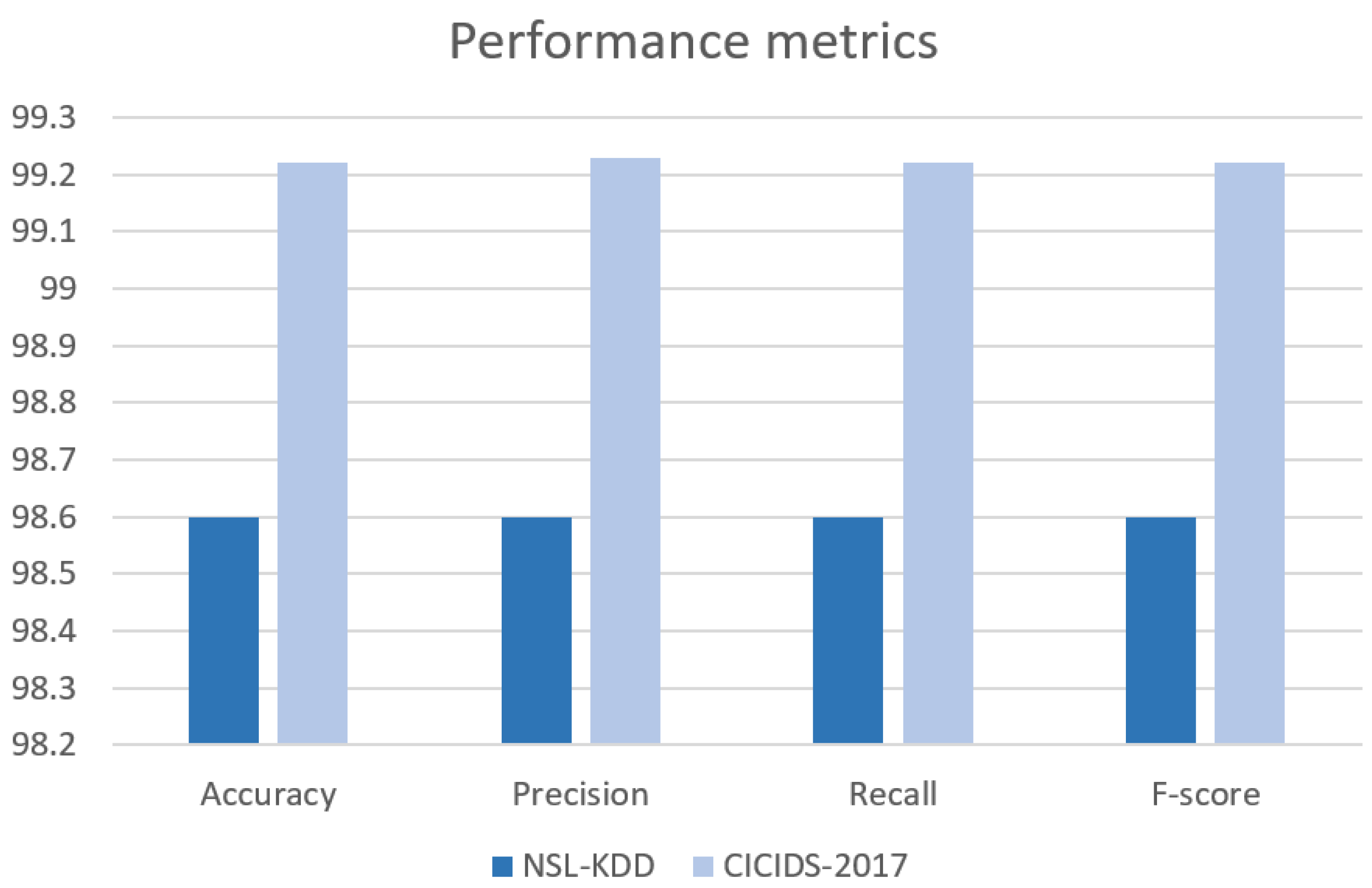
| Proposed RLSTM model | DoS Attack | 98.60 | 99.03 | 98.15 | 98.59 |
| Normal | 98.60 | 98.17 | 99.04 | 98.60 | |
| Average | 98.60 | 98.60 | 98.60 | 98.60 |
| Classifier | Class | Accuracy (%) | Precision (%) | Recall (%) | F-Score (%) |
|---|---|---|---|---|---|
| Proposed RLSTM model | Dos Attack | 99.2 | 98.83 | 99.62 | 99.22 |
| Benign | 99.2 | 99.62 | 98.82 | 99.22 | |
| Average | 99.2 | 99.23 | 99.22 | 99.22 |
| Classifier | Class | Accuracy (%) | Precision (%) | Recall (%) | F-Score (%) |
|---|---|---|---|---|---|
| Proposed MLP model | DoS Attack | 98.39 | 98.51 | 98.27 | 98.39 |
| Normal | 99.39 | 99.27 | 99.51 | 99.89 | |
| Average | 98.89 | 98.89 | 98.89 | 99.14 |
| Classifier | Class | Accuracy (%) | Precision (%) | Recall (%) | F-Score (%) |
|---|---|---|---|---|---|
| Proposed MLP model | Dos Attack | 98.22 | 99.87 | 96.57 | 98.19 |
| Benign | 98.22 | 96.68 | 99.87 | 98.25 | |
| Average | 98.22 | 98.28 | 98.22 | 98.22 |
| Classifier | Accuracy (%) | Precision (%) | Recall (%) | F-Score (%) |
|---|---|---|---|---|
| RF [32] | 94 | / | / | / |
| MLP [35] | 92.84 | / | / | / |
| DT, k-NN, NB [36] | 100, 98, 29 | 100, 96, 27 | 100, 97, 100 | 100, 97, 42 |
| RF, MLP, CNN [39] | 91.27 and 79.01 | / | / | / |
| CNN [40] | 92.99 | / | / | / |
| CNN and LSTM [41] | 91.20 | 90.81 | 92.70 | 91.75 |
| Proposed model | 99.22 | 99.23 | 99.22 | 99.22 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Adefemi Alimi, K.O.; Ouahada, K.; Abu-Mahfouz, A.M.; Rimer, S.; Alimi, O.A. Refined LSTM Based Intrusion Detection for Denial-of-Service Attack in Internet of Things. J. Sens. Actuator Netw. 2022, 11, 32. https://doi.org/10.3390/jsan11030032
Adefemi Alimi KO, Ouahada K, Abu-Mahfouz AM, Rimer S, Alimi OA. Refined LSTM Based Intrusion Detection for Denial-of-Service Attack in Internet of Things. Journal of Sensor and Actuator Networks. 2022; 11(3):32. https://doi.org/10.3390/jsan11030032
Chicago/Turabian StyleAdefemi Alimi, Kuburat Oyeranti, Khmaies Ouahada, Adnan M. Abu-Mahfouz, Suvendi Rimer, and Oyeniyi Akeem Alimi. 2022. "Refined LSTM Based Intrusion Detection for Denial-of-Service Attack in Internet of Things" Journal of Sensor and Actuator Networks 11, no. 3: 32. https://doi.org/10.3390/jsan11030032
APA StyleAdefemi Alimi, K. O., Ouahada, K., Abu-Mahfouz, A. M., Rimer, S., & Alimi, O. A. (2022). Refined LSTM Based Intrusion Detection for Denial-of-Service Attack in Internet of Things. Journal of Sensor and Actuator Networks, 11(3), 32. https://doi.org/10.3390/jsan11030032








