Designing a CHAM Block Cipher on Low-End Microcontrollers for Internet of Things
Abstract
:1. Introduction
2. Contribution
- Optimized counter mode of operation for CHAM block cipher: Due to the characteristic of counter mode of operation, the certain amount of input value is constant (i.e., nonce). Through pre-calculation, 5 left rotation by 1-bit, 10 XOR, 3 ADD, and 3 left rotation by word-wise operations are replaced to 5 word-wise look-up table accesses. These techniques optimize whole parameters of CHAM block cipher;
- Variable-key based CHAM-CTR (Counter) implementations: When the key is fixed, there is no update of look-up table and the pre-calculation is performed offline. For practical implementation, variable-key scenarios should be considered. Therefore, we proposed a pre-computation for look-up table in on-the-fly way;
- Parallel implementation of CHAM-64/128: When implementing CHAM-64/128, there are many registers that are not used in an optimal way. By utilizing all of these registers, the parallel encryption is available. It allows multiple plaintexts to be encrypted, simultaneously. We proposed an optimized register allocation. This ensures efficient performance for parallel computation;
- Highly optimized source code and 8-round based implementation: The state-of-art engineering technique is fully utilized with available instruction sets and register files to achieve high performance. The partially unrolled 8-round based implementation is adopted, which optimizes the left rotation by 8-bit wise operations.
Extended Version of WISA’20
3. Backgrounds
3.1. Block Cipher
- Feistel: Feistel structure divides plaintext. One block is used as the round function input. Feistel structure is simple to implement encryption because the structure of decryption and encryption is identical. However it requires a number of move operations;
- Substitution Permutation Network: Substitution Permutation Network (SPN) performs encryption by repeating the process, which substitutes the plaintext through S-BOX and permutates its result. SPN requires the reversed function for decryption. This is practical for hardware implementation.
3.2. Mode of Operation
4. Related Works
4.1. CHAM Block Cipher
4.2. Previous Block Cipher Implementations on 8-bit AVR Microcontrollers
5. Proposed Method
5.1. Optimized CHAM-CTR Mode Encryption
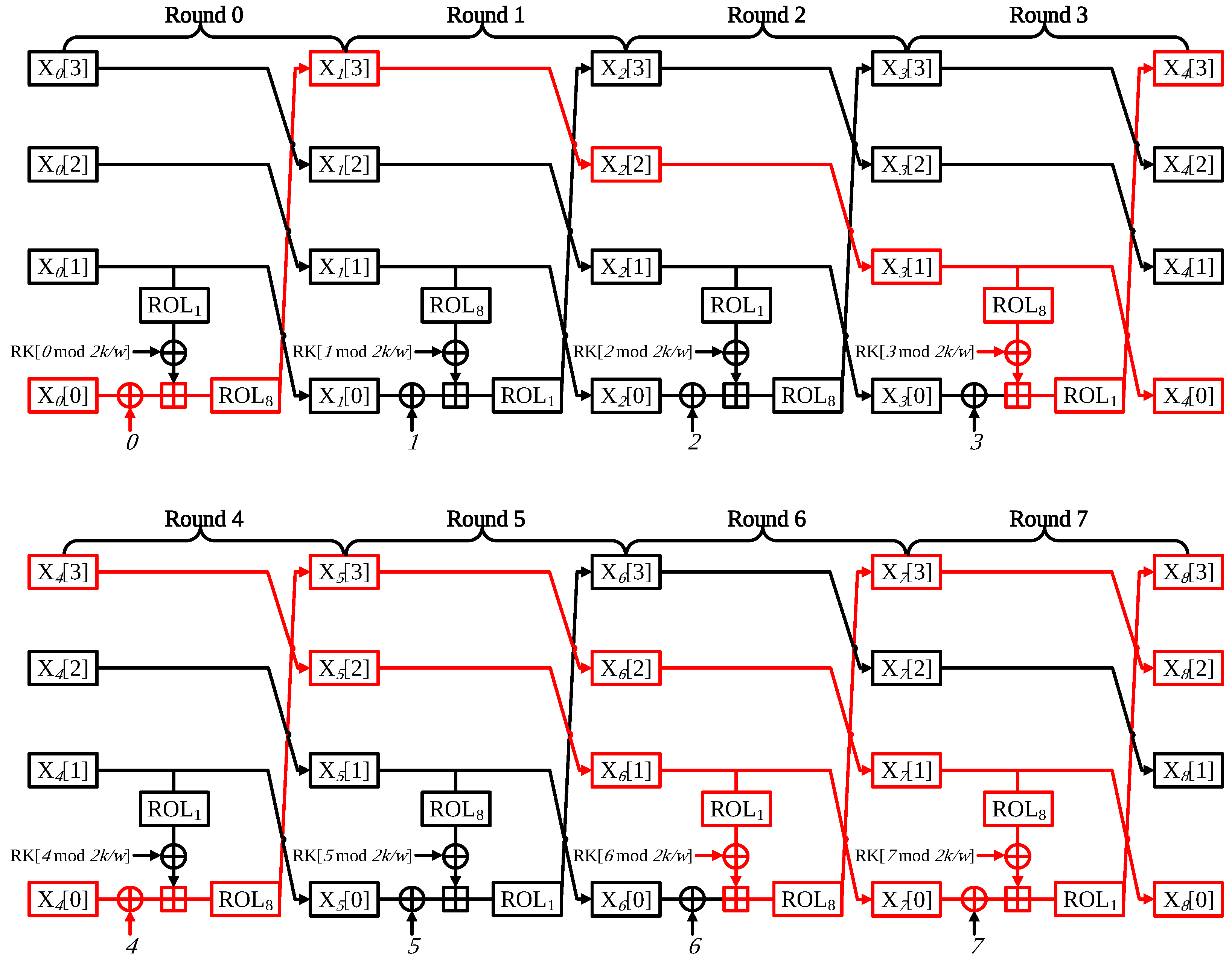
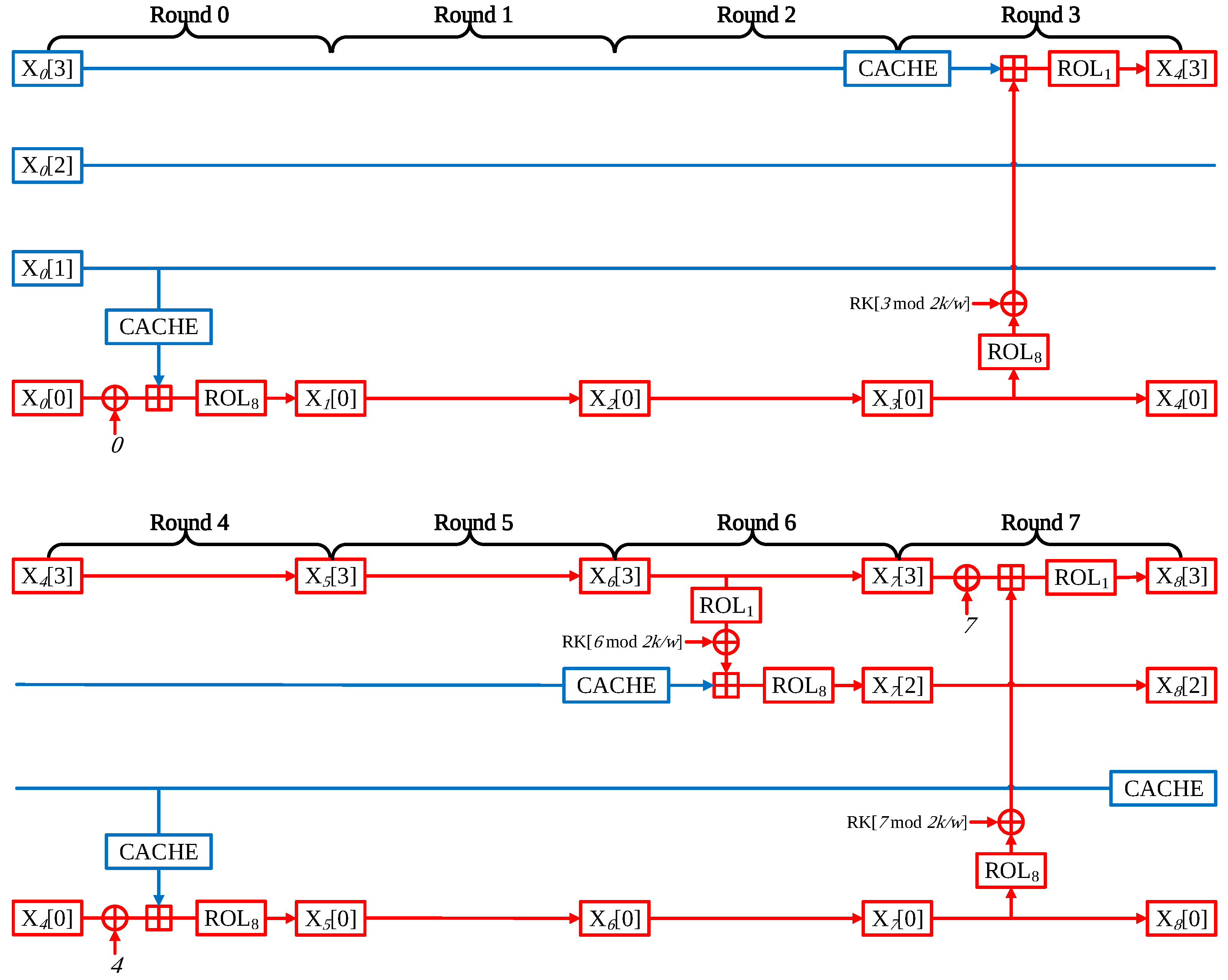
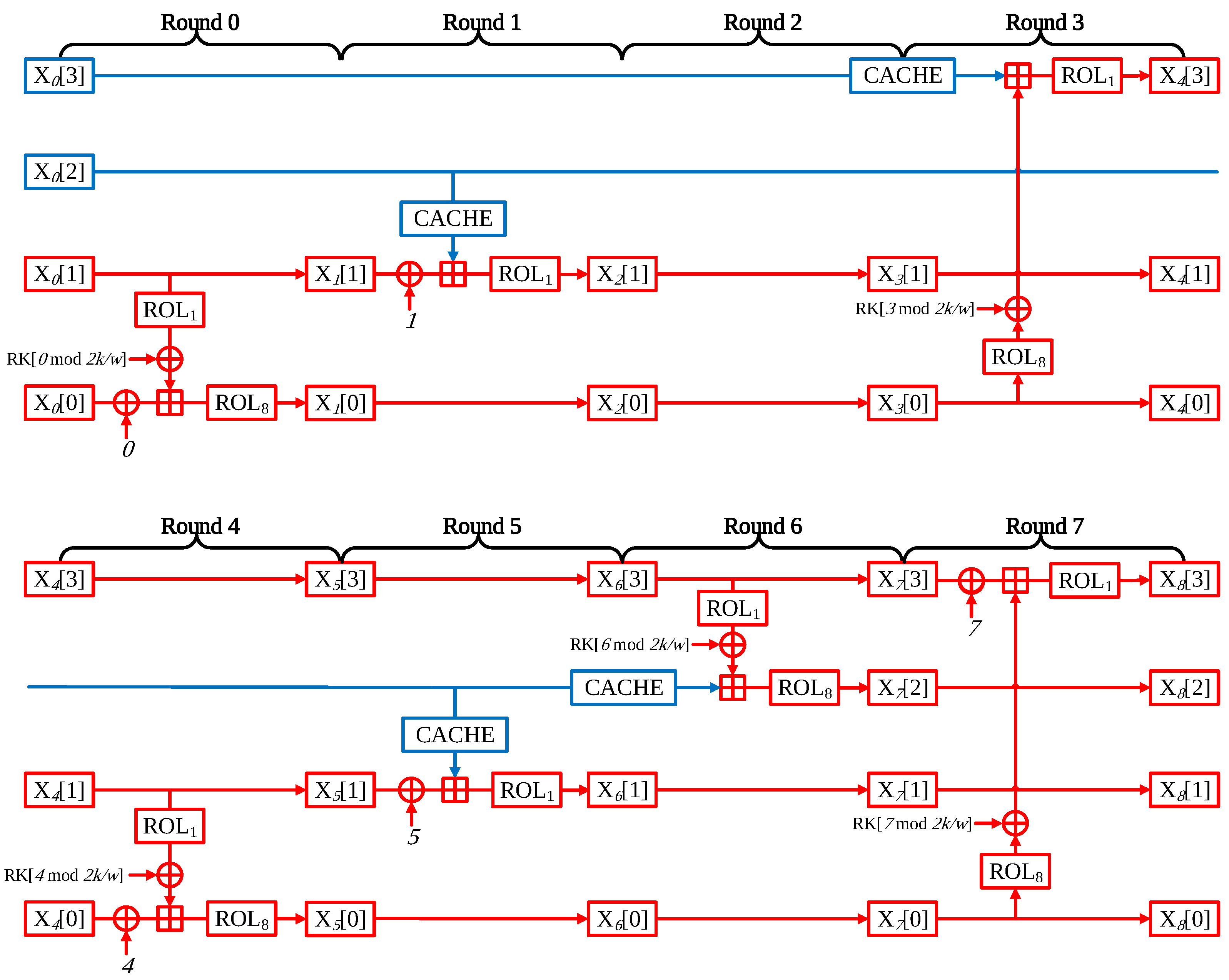
- Round 0: Since X[0] block is counter block, the pre-computation is not feasible as described above. In contrast, X[1] which has the nonce value block, 1-bit left rotation, and XOR with round key operations are performed. At this time, both the nonce and round key are fixed, the result of the operation is always identical. The pre-computation is available at this part. This leads to a simplified round. LDI instruction is used for implementation; LDI instruction can directly assign the 8-bit value in a single clock cycle. This approach reduces 2 clock cycles then memory access in each 8-bit assignment;
- Round 1: Since all of Round 1 inputs are of a fixed value (i.e., nonce, round key, and round counter), whole operations can be skipped. The result of Round 1 is obtained by accessing the look-up table at X[1] block during Round 4.
- Round 2: Similar to Round 1, Round 2 is also skipped. The result value is obtained from the look-up table to X[1] of Round 5.
- Round 3:In Round 3, the (X[0] ⊕ i) part can be pre-computed. In more detail, i stands for the round counter which is a fixed value. In Round 0, X[3] is a fixed nonce value and it is moved to X[0]. Therefore, it can be seen that all values in the (X[0] ⊕ i) part are a fixed value, which can be pre-calculated. It only requires a word assignment. X[1] originated from X[0] (i.e., counter). Thus X[1] cannot be pre-computed;
- Round 4: Each block is word-wise rotate to the left at every end of a round. After Round 3, all blocks return to their own original place. In other words, Round 4 is structurally identical to Round 0. Thus, computations with X[1] (i.e., rotation left by 1-bit and add-round key) can be optimized;
- Round 5: It is able to skip all operations at Round 5, since it has the same structure of Round 1. The X[0] result is brought to the look-up table access after Round 7. This takes 2 clock cycles.
- Round 6:The difference between Round 3 and Round 6 is only the number of rotation. In other words, it has almost the same structure of Round 3. Thus, the optimization is possible at the X[0] operation part like Round 3;
- Round 7: In Figure 1, all values for the operation are affected by the counter value at Round 7. All operations must be implemented;
- Round 8: After Round 7, there is still a remaining part for pre-computation. In Round 8, X[1] has no relation to the counter value. For this reason it can be pre-calculation. However, the performance improvement is 0.6, 0.7, and 0.7 clock cycles per byte for CHAM-64/128, CHAM-128/128, and CHAM-128/256, respectively. This is a very small performance improvement. If the pre-calculation is applied after Round 8, the 8-way based structure will be broken. It makes the code size larger than the proposed implementation. Although there is an optimization room after the Round 7, it is not considered in this paper.
5.1.1. 32-Bit Counter for CHAM-64/128
5.1.2. Countermeasure Against Timing Attack
5.1.3. Optimized Memory Access
5.1.4. Round Counter and Pointer Address Optimization
5.2. Variable-Key Based CHAM-CTR Implementation
| Algorithm 1: Separated version for variable-key implementation. |
| Input: Number of blocks n, Plaintext blocks . |
| Output: Ciphertext blocks . |
|
| Algorithm 2: Integrated version for variable-key implementation. |
| Input: Number of blocks n, Plaintext blocks . |
| Output: Ciphertext blocks . |
|
5.3. Parallel Implementations of CHAM Block Cipher
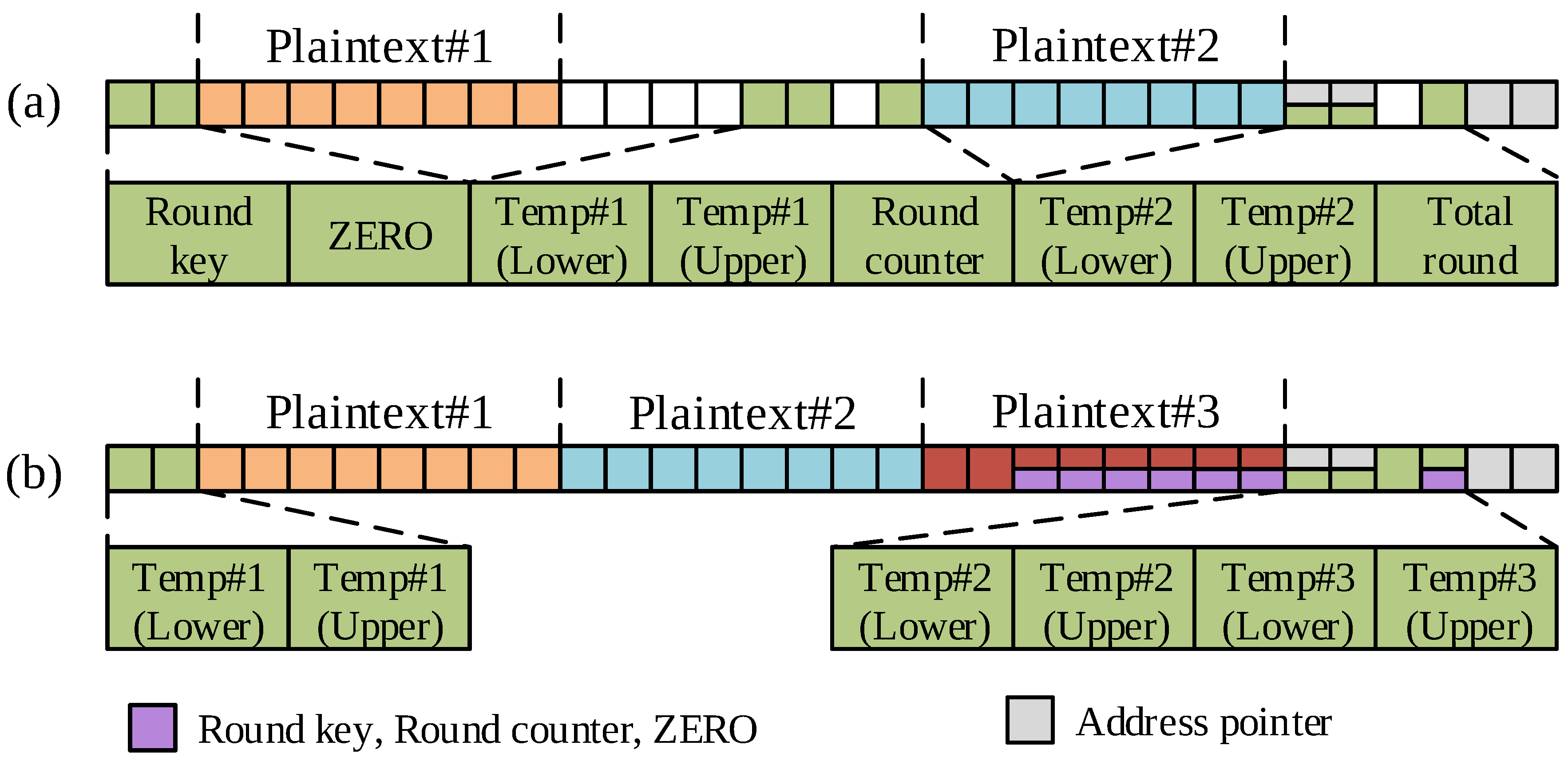
- Total round indicator: Instead of storing the total round indicator in a register, use CPI instruction;
- 3-Plaintext blocks: Every round, the only two blocks (i.e., X[0], and X[1]) are participating encryption. Thus, other plaintext blocks are stored in STACK memory for a short time;
- Address pointer X: Round keys and plaintext can be obtained by accessing them through an address pointer. However, there are only two plaintext blocks participating in the operation in every round. Thus, some plaintext address pointers are stored on STACK;
- Round key: Originally, round key access require word-wise memory access. If accessing byte by byte, instead of word-wise access, only one register requires to load round key;
- Round counter: Round counter is used only when performing XOR operation. After XOR operation, it is stored in STACK;
- ZERO: For 3-parallel implementation, R1 register is used for plaintext, which originally assigned ZERO register. Some registers are used as ZERO register for a while.
| Algorithm 3: Parallel implementation of CHAM-64/128. |
| Input: Plaintext blocks (). |
| Output: Ciphertext blocks (). |
|
5.4. Adaptive Encryption of CHAM Block Cipher
| Algorithm 4: 2-way adaptive encryption for CHAM64/128. |
| Input: Number of blocks N, Plaintext blocks . |
| Output: Ciphertext blocks . |
|
5.5. Optimized Implementations of Primitive Operations
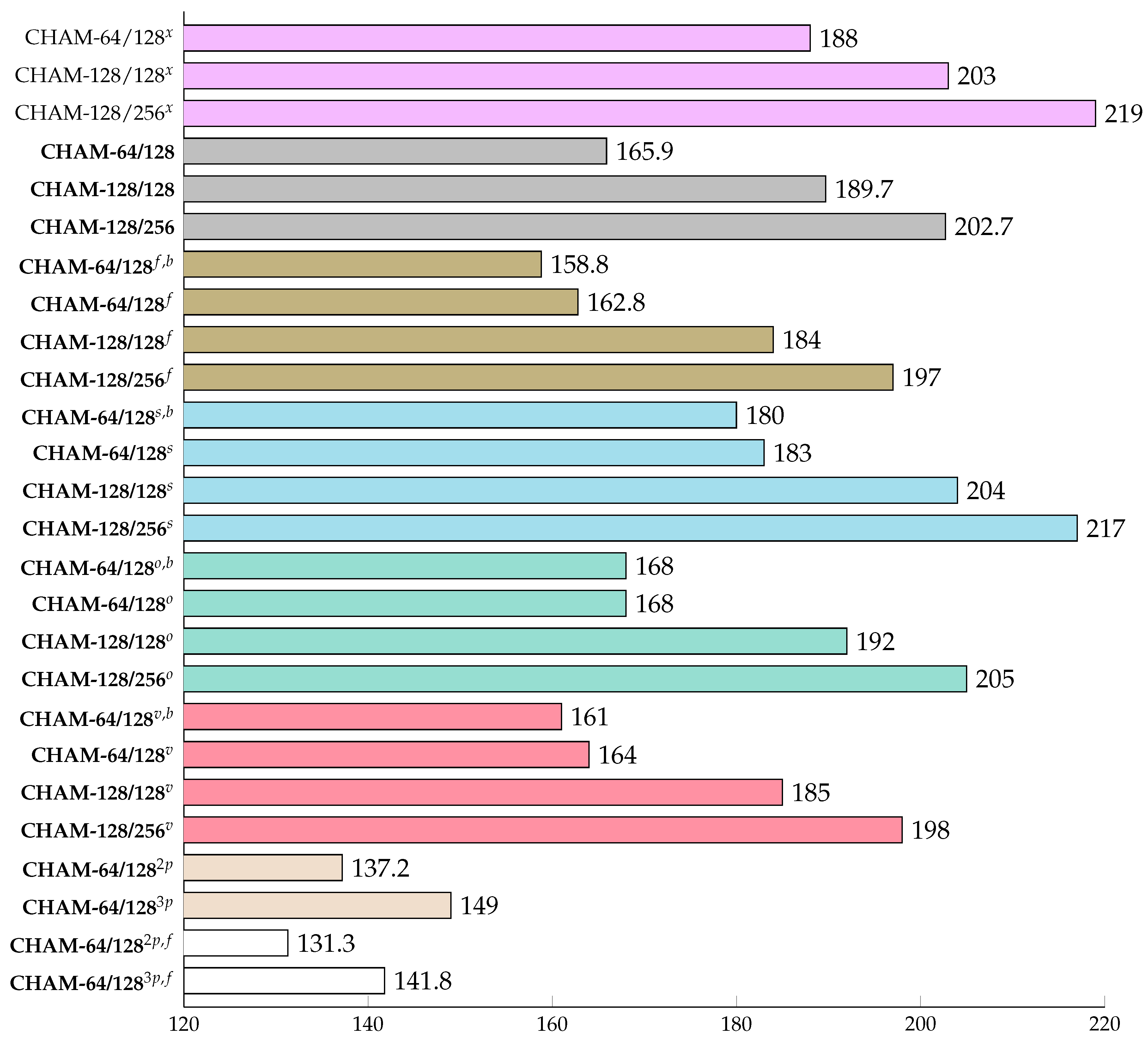
6. Evaluation
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Kwon, H.; Kim, H.; Choi, S.; Jang, K.; Park, J.; Kim, H.; Seo, H. Compact Implementation of CHAM Block Cipher on Low-End Microcontrollers. In International Workshop on Information Security Applications; Springer: Berlin/Heidelberg, Germany, 2020. [Google Scholar]
- Koo, B.; Roh, D.; Kim, H.; Jung, Y.; Lee, D.G.; Kwon, D. CHAM: A Family of Lightweight Block Ciphers for Resource-Constrained Devices. In Proceedings of the International Conference on Information Security and Cryptology (ICISC’17), Seoul, Korea, 29 November–1 December 2017. [Google Scholar]
- Roh, D.; Koo, B.; Jung, Y.; Jeong, I.W.; Lee, D.G.; Kwon, D.; Kim, W.H. Revised Version of Block Cipher CHAM. In Proceedings of the International Conference on Information Security and Cryptology, Nanjing, China, 6–8 December 2019; pp. 1–19. [Google Scholar]
- Seo, H.; Liu, Z.; Choi, J.; Park, T.; Kim, H. Compact implementations of LEA block cipher for low-end microprocessors. In Proceedings of the International Workshop on Information Security Applications, Jeju Island, Korea, 20–22 August 2015; pp. 28–40. [Google Scholar]
- Seo, H.; An, K.; Kwon, H. Compact LEA and HIGHT implementations on 8-bit AVR and 16-bit MSP processors. In Proceedings of the International Workshop on Information Security Applications, Jeju Island, Korea, 23–25 August 2018; pp. 253–265. [Google Scholar]
- Hong, D.; Lee, J.K.; Kim, D.C.; Kwon, D.; Ryu, K.H.; Lee, D.G. LEA: A 128-bit block cipher for fast encryption on common processors. In Proceedings of the International Workshop on Information Security Applications, Jeju Island, Korea, 19–21 August 2013; pp. 3–27. [Google Scholar]
- Seo, H.; Jeong, I.; Lee, J.; Kim, W.H. Compact implementations of ARX-based block ciphers on IoT processors. ACM Trans. Embed. Comput. Syst. (TECS) 2018, 17, 1–16. [Google Scholar] [CrossRef]
- Hong, D.; Sung, J.; Hong, S.; Lim, J.; Lee, S.; Koo, B.S.; Lee, C.; Chang, D.; Lee, J.; Jeong, K.; et al. HIGHT: A new block cipher suitable for low-resource device. In Proceedings of the International Workshop on Cryptographic Hardware and Embedded Systems, Yokohama, Japan, 10–13 October 2006; pp. 46–59. [Google Scholar]
- Eisenbarth, T.; Gong, Z.; Güneysu, T.; Heyse, S.; Indesteege, S.; Kerckhof, S.; Koeune, F.; Nad, T.; Plos, T.; Regazzoni, F.; et al. Compact implementation and performance evaluation of block ciphers in ATtiny devices. In Proceedings of the International Conference on Cryptology in Africa, Ifrane, Morocco, 10–12 July 2012; pp. 172–187. [Google Scholar]
- Kim, B.; Cho, J.; Choi, B.; Park, J.; Seo, H. Compact Implementations of HIGHT Block Cipher on IoT Platforms. Secur. Commun. Netw. 2019, 2019, 5323578. [Google Scholar] [CrossRef]
- Seo, H. Memory-Efficient Implementation of Ultra-Lightweight Block Cipher Algorithm CHAM on Low-End 8-Bit AVR Processors. J. Korea Inst. Inf. Secur. Cryptol. 2018, 28, 545–550. [Google Scholar]
- Osvik, D.A.; Bos, J.W.; Stefan, D.; Canright, D. Fast software AES encryption. In Proceedings of the International Workshop on Fast Software Encryption, Graz, Austria, 15–17 March 2010; pp. 75–93. [Google Scholar]
- Kim, K.; Choi, S.; Kwon, H.; Liu, Z.; Seo, H. FACE–LIGHT: Fast AES–CTR Mode Encryption for Low-End Microcontrollers. In Proceedings of the International Conference on Information Security and Cryptology, Seoul, Korea, 4–6 December 2019; pp. 102–114. [Google Scholar]
- Kim, K.; Choi, S.; Kwon, H.; Kim, H.; Liu, Z.; Seo, H. PAGE-Practical AES-GCM Encryption for Low-End Microcontrollers. Appl. Sci. 2020, 10, 3131. [Google Scholar] [CrossRef]
- Seo, H.; Kwon, H.; Kim, H.; Park, J. ACE: ARIA-CTR Encryption for Low-End Embedded Processors. Sensors 2020, 20, 3788. [Google Scholar] [CrossRef] [PubMed]
- Park, T.; Seo, H.; Lee, S.; Kim, H. Secure data encryption for cloud-based human care services. J. Sens. 2018, 2018, 6492592. [Google Scholar] [CrossRef] [Green Version]
- Beaulieu, R.; Shors, D.; Smith, J.; Treatman-Clark, S.; Weeks, B.; Wingers, L. SIMON and SPECK: Block Ciphers for the Internet of Things. IACR Cryptol. Eprint Arch. 2015, 2015, 585. [Google Scholar]
- Beaulieu, R.; Shors, D.; Smith, J.; Treatman-Clark, S.; Weeks, B.; Wingers, L. The SIMON and SPECK block ciphers on AVR 8-bit microcontrollers. In Proceedings of the International Workshop on Lightweight Cryptography for Security and Privacy, Istanbul, Turkey, 1–2 September 2014; pp. 3–20. [Google Scholar]



| asm | Operands | Description | Operation | #Clock |
|---|---|---|---|---|
| ADD | Rd, Rr | Add without Carry | Rd ← Rd+Rr | 1 |
| ADC | Rd, Rr | Add with Carry | Rd ← Rd+Rr+C | 1 |
| EOR | Rd, Rr | Exclusive OR | Rd ← Rd⊕Rr | 1 |
| LSL | Rd | Logical Shift Left | C∣Rd ← Rd<<1 | 1 |
| ROL | Rd | Rotate Left Through Carry | C∣Rd ← Rd<<1C | 1 |
| MOV | Rd, Rr | Copy Register | Rd ← Rr | 1 |
| MOVW | Rd, Rr | Copy Register Word | Rd+1:Rd ← Rr+1:Rr | 1 |
| LDI | Rd, K | Load Immediate | Rd ← K | 1 |
| LD | Rd, X | Load Indirect | Rd ← (X) | 2 |
| LPM | Rd, Z | Load Program Memory | Rd ← (Z) | 3 |
| ST | Z, Rr | Store Indirect | (Z) ← Rr | 2 |
| PUSH | Rr | Push Register on Stack | STACK ← Rr | 2 |
| POP | Rd | Pop Register from Stack | Rd ← STACK | 2 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kwon, H.; An, S.; Kim, Y.; Kim, H.; Choi, S.J.; Jang, K.; Park, J.; Kim, H.; Seo, S.C.; Seo, H. Designing a CHAM Block Cipher on Low-End Microcontrollers for Internet of Things. Electronics 2020, 9, 1548. https://doi.org/10.3390/electronics9091548
Kwon H, An S, Kim Y, Kim H, Choi SJ, Jang K, Park J, Kim H, Seo SC, Seo H. Designing a CHAM Block Cipher on Low-End Microcontrollers for Internet of Things. Electronics. 2020; 9(9):1548. https://doi.org/10.3390/electronics9091548
Chicago/Turabian StyleKwon, Hyeokdong, SangWoo An, YoungBeom Kim, Hyunji Kim, Seung Ju Choi, Kyoungbae Jang, Jaehoon Park, Hyunjun Kim, Seog Chung Seo, and Hwajeong Seo. 2020. "Designing a CHAM Block Cipher on Low-End Microcontrollers for Internet of Things" Electronics 9, no. 9: 1548. https://doi.org/10.3390/electronics9091548
APA StyleKwon, H., An, S., Kim, Y., Kim, H., Choi, S. J., Jang, K., Park, J., Kim, H., Seo, S. C., & Seo, H. (2020). Designing a CHAM Block Cipher on Low-End Microcontrollers for Internet of Things. Electronics, 9(9), 1548. https://doi.org/10.3390/electronics9091548





