5G Cellular Networks: Coverage Analysis in the Presence of Inter-Cell Interference and Intentional Jammers
Abstract
1. Introduction
1.1. Motivation
1.1.1. Increased Reliance on Wireless Communication
1.1.2. Using HetNets
1.1.3. Distributed Denial-of-Service Attacks
1.1.4. Intentional Jammers and Inter-Cell Interference
1.1.5. Interference Reduction Schemes
1.1.6. Proposed Work
1.2. Related Work
1.3. Contributions and Objectives
- Investigation of the disruption caused by IJs’ attacks to the legitimate UL communication in HetNets.
- The mitigation of both ICI and IJs-I for the improvement of network performance gain. For this, among the best available techniques such as RFA is employed.
- This work focuses on increasing capacity and coverage of the network and, thus, renders HetNets as a key enabler for future 5G.
- To make the network more resilient to both ICI and IJs-I. This can be achieved by efficient resource use via RFA.
- To investigate UL coverage for the proposed setup against different network parameters, such as SBS density, IJs’ density, and SIR threshold.
2. System Model
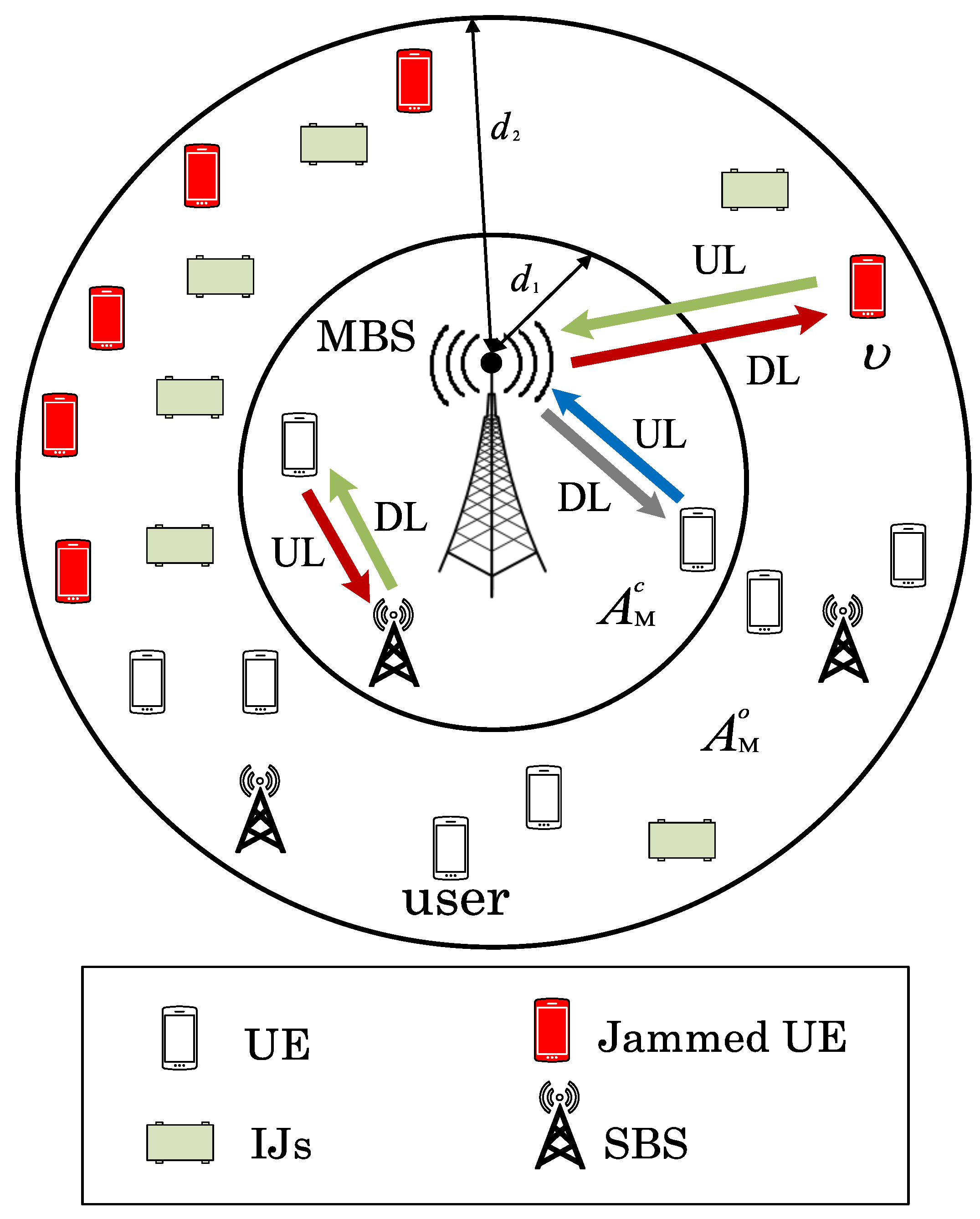
2.1. Network Layout and Assumptions
2.2. IJs Mechanism
2.3. Reverse Frequency Allocation
3. Coverage Probability Analysis
3.1. Coverage Probability for UL in the Presence of IJs without RFA
3.2. Coverage Probability for UL in the Presence of IJs with RFA
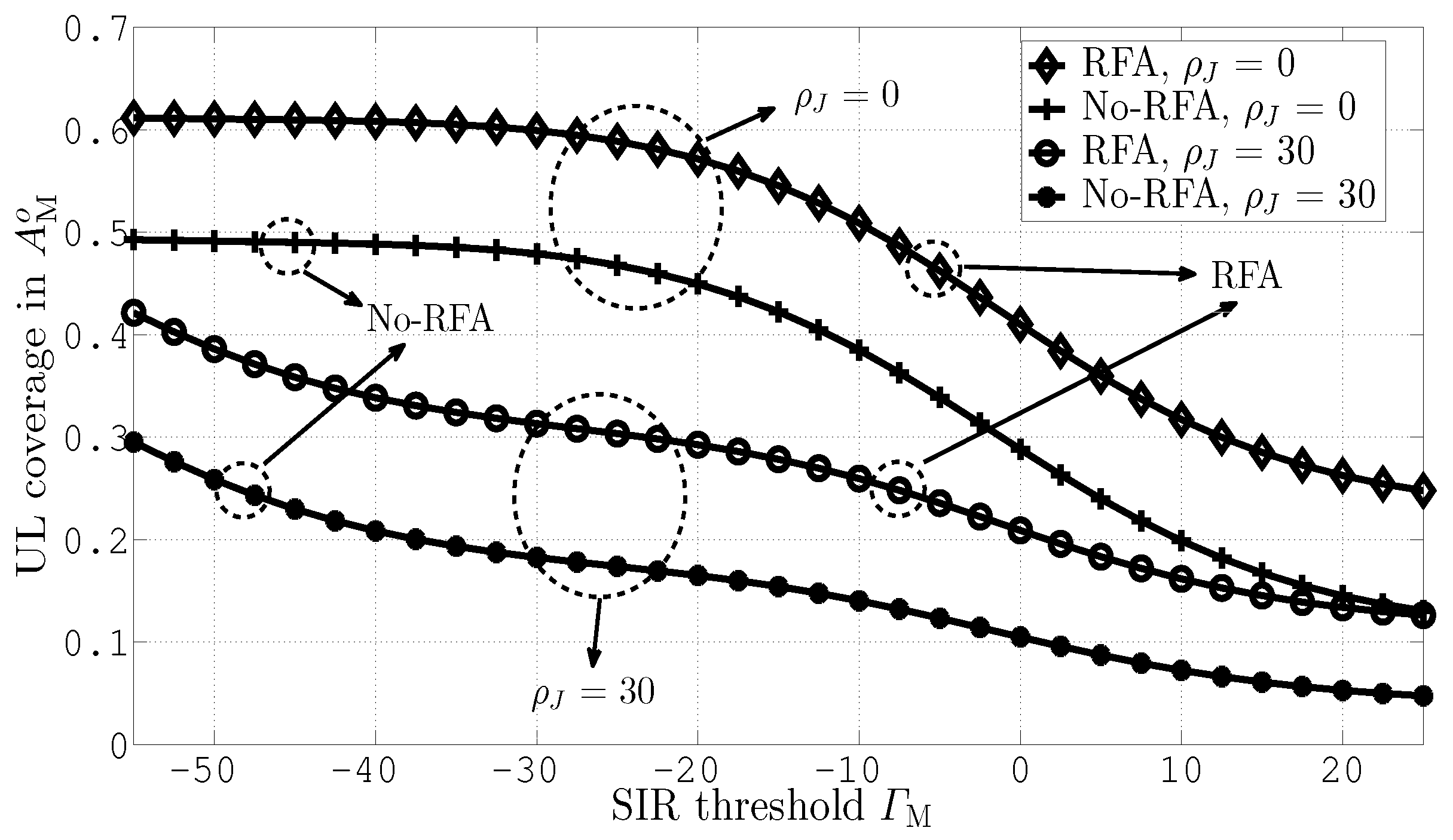
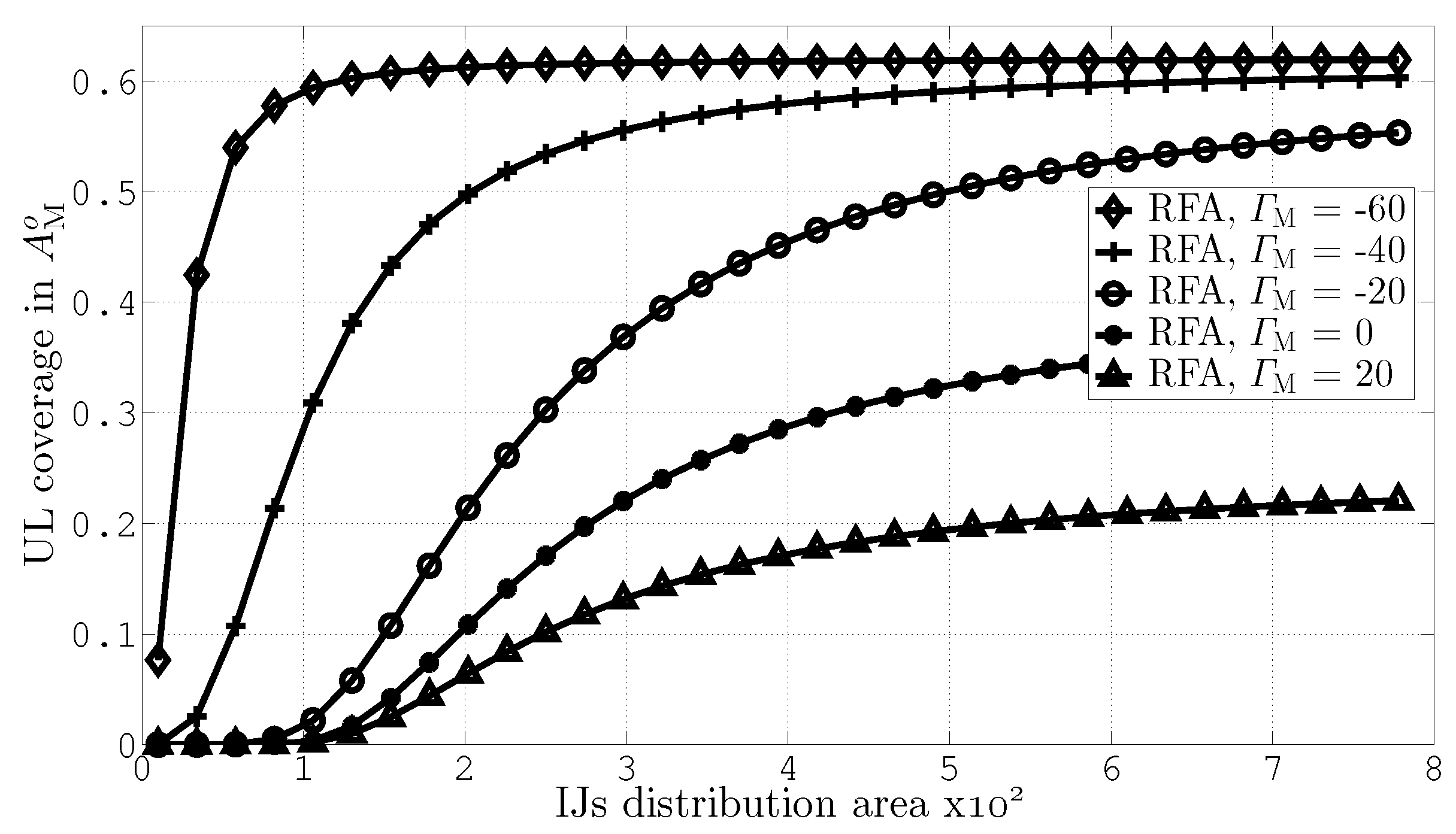
4. Results and Discussion
5. Conclusions
- UL coverage can be further improved with inclusion of decoupled user associations. It can be used in conjunction with RFA to help in reduction of ICI and IJs-I.
- In this paper, we have considered jamming to affect the wide band. However, jamming of only certain portion of the band may be investigated as a future work.
Author Contributions
Funding
Conflicts of Interest
Appendix A. Proof of the LT of (4)
Appendix B. Proof of the LT of (17)
References
- Da Costa, D.B.; Duong, T.Q.; Imran, M.A.; Ngo, H.Q.; Yang, N.; Dobre, O.A. Modeling, analysis, and design of 5G ultra-dense networks. IEEE Access 2019, 7, 18894–18898. [Google Scholar] [CrossRef]
- Andrews, J.G.; Buzzi, S.; Choi, W.; Hanly, S.V.; Lozano, A.; Soong, A.C.; Zhang, J.C. What will 5G be? IEEE J. Sel. Areas Commun. 2014, 32, 1065–1082. [Google Scholar] [CrossRef]
- Błaszczyszyn, B.; Haenggi, M.; Keeler, P.; Mukherjee, S. Stochastic Geometry Analysis of Cellular Networks; Cambridge University Press: Cambridge, UK, 2018. [Google Scholar]
- Abbas, Z.H.; Abbas, G.; Haroon, M.S.; Muhammad, F.; Kim, S. Proactive uplink interference mitigation in HetNets stressed by uniformly distributed wideband jammers. Electronics 2019, 8, 1496. [Google Scholar] [CrossRef]
- Mirkovic, J.; Reiher, P. A taxonomy of DDoS attack and DDoS defense mechanisms. ACM SIGCOMM Comput. Commun. Rev. 2004, 34, 39–53. [Google Scholar] [CrossRef]
- Jover, R.P. Security attacks against the availability of LTE mobility networks: Overview and research directions. In Proceedings of the International Symposium on Wireless Personal Multimedia Communication (WPMC), Atlantic City, NJ, USA, 24–27 June 2013; pp. 1–9. [Google Scholar]
- Huo, Y.; Fan, X.; Ma, L.; Cheng, X.; Tian, Z.; Chen, D. Secure communications in tiered 5G wireless networks with cooperative jamming. IEEE Trans. Wirel. Commun. 2019, 18. [Google Scholar] [CrossRef]
- Jundong, W. Complex environment noise barrage jamming effects on airborne warning radar. Am. J. Remote Sens. 2018, 6, 59–63. [Google Scholar] [CrossRef]
- Viterbi, A. A robust ratio-threshold technique to mitigate tone and partial band jamming in coded MFSK systems. In Proceedings of the MILCOM 1982-IEEE Military Communications Conference-Progress in Spread Spectrum Communications, Boston, MA, USA, 17–20 October 1982; Volume 1, pp. 22–24. [Google Scholar]
- Haroon, M.S.; Ahmad, S.; Khan, J.A. LLR-based erasure decoding of SFH-MFSK in the presence of tone jamming. In Proceedings of the 11th International Bhurban Conference on Applied Sciences & Technology (IBCAST), Islamabad, Pakistan, 14–18 January 2014; pp. 453–457. [Google Scholar]
- Girke, F.; Kurtz, F.; Dorsch, N.; Wietfeld, C. Towards resilient 5G: Lessons learned from experimental evaluations of LTE uplink jamming. In Proceedings of the 2019 IEEE International Conference on Communications Workshops (ICC Workshops), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar]
- Ham, C.V.; Scoughton, T.E. Radio Frequency Jammer. U.S. Patent 7,318,368, 15 January 2008. [Google Scholar]
- Wang, S.; Gao, Y.; Sha, N.; Zhang, G.; Zang, G. Physical layer security in K-tier heterogeneous cellular networks over nakagami-m channel during uplink and downlink phases. IEEE Access 2019, 7, 14581–14592. [Google Scholar] [CrossRef]
- Muhammad, F.; Haroon, M.S.; Abbas, Z.H.; Abbas, G.; Kim, S. Uplink interference management for HetNets stressed by clustered wide-band jammers. IEEE Access 2019, 7, 182679–182690. [Google Scholar] [CrossRef]
- Soret, B.; De Domenico, A.; Bazzi, S.; Mahmood, N.H.; Pedersen, K.I. Interference coordination for 5G new radio. IEEE Wirel. Commun. 2017, 25, 131–137. [Google Scholar] [CrossRef]
- Zou, S.; Liu, N.; Pan, Z.; You, X. Joint power and resource allocation for non-uniform topologies in heterogeneous networks. In Proceedings of the 83rd Vehicular Technology Conference (VTC Spring), Nanjing, China, 15–18 May 2016; pp. 1–5. [Google Scholar]
- Han, T.; Gong, J.; Liu, X.; Islam, S.R.; Li, Q.; Bai, Z.; Kwak, K.S. On downlink NOMA in heterogeneous networks with non-uniform small cell deployment. IEEE Access 2018, 6, 31099–31109. [Google Scholar] [CrossRef]
- Haroon, M.S.; Abbas, Z.H.; Abbas, G.; Muhammad, F. Analysis of interference mitigation in heterogeneous cellular networks using soft frequency reuse and load balancing. In Proceedings of the 28th International Telecommunication Networks and Applications Conference (ITNAC), Sydney, NSW, Australia, 21–23 November 2018; pp. 1–6. [Google Scholar]
- Haroon, M.S.; Abbas, Z.H.; Abbas, G.; Muhammad, F. Coverage analysis of ultra-dense heterogeneous cellular networks with interference management. Wirel. Netw. 2019, 26, 2013–2025. [Google Scholar] [CrossRef]
- Hashima, S.; Muta, O.; Alghonimey, M.; Shalaby, H.; Frukawa, H.; Elnoubi, S.; Mahmoud, I. Area spectral efficiency performance comparison of downlink fractional frequency reuse schemes for MIMO heterogeneous networks. In Proceedings of the International Conference on Information Science, Electronics and Electrical Engineering, Hokkaido, Japan, 26–28 April 2014; Volume 2, pp. 1005–1010. [Google Scholar]
- Lichtman, M.; Poston, J.D.; Amuru, S.; Shahriar, C.; Clancy, T.C.; Buehrer, R.M.; Reed, J.H. A communications jamming taxonomy. IEEE Secur. Privacy 2016, 14, 47–54. [Google Scholar] [CrossRef]
- Gecgel, S.; Goztepe, C.; Kurt, G.K. Jammer detection based on artificial neural networks: A measurement study. In Proceedings of the ACM Workshop on Wireless Security and Machine Learning, Miami, FL, USA, 15–17 May 2019; pp. 43–48. [Google Scholar]
- Zhang, L.; Restuccia, F.; Melodia, T.; Pudlewski, S.M. Jam sessions: Analysis and experimental evaluation of advanced jamming attacks in MIMO networks. In Proceedings of the Twentieth ACM International Symposium on Mobile Ad Hoc Networking and Computing, Catania, Italy, 2–5 July 2019; pp. 61–70. [Google Scholar]
- Ciuonzo, D.; Aubry, A.; Carotenuto, V. Rician MIMO channel-and jamming-aware decision fusion. IEEE Trans. Signal Process. 2017, 65, 3866–3880. [Google Scholar] [CrossRef]
- Haroon, M.S.; Muhammad, F.; Abbas, G.; Abbas, Z.H.; Hassan, A.K.; Waqas, M.; Kim, S. Interference management in ultra-dense 5G networks with excessive drone usage. IEEE Access 2020, 8, 102155–102164. [Google Scholar] [CrossRef]
- Liu, K.H.; Yu, T.Y. Performance of off-grid small cells with non-uniform deployment in two-tier HetNet. IEEE Trans. Wirel. Commun. 2018, 17, 6135–6148. [Google Scholar] [CrossRef]
- Muhammad, F.; Abbas, Z.H.; Li, F.Y. Cell association with load balancing in nonuniform heterogeneous cellular networks: Coverage probability and rate analysis. IEEE Trans. Veh. Technol. 2016, 66, 5241–5255. [Google Scholar] [CrossRef]
- Ijaz, A.; Hassan, S.A.; Zaidi, S.A.R.; Jayakody, D.N.K.; Zaidi, S.M.H. Coverage and rate analysis for downlink HetNets using modified reverse frequency allocation scheme. IEEE Access 2017, 5, 2489–2502. [Google Scholar] [CrossRef]
- Ejaz, W.; Anpalagan, A.; Imran, M.A.; Jo, M.; Naeem, M.; Qaisar, S.B.; Wang, W. Internet of Things (IoT) in 5G wireless communications. IEEE Access 2016, 4, 10310–10314. [Google Scholar] [CrossRef]
- Li, S.; Da Xu, L.; Zhao, S. 5G Internet of Things: A survey. J. Ind. Inf. Integr. 2018, 10, 1–9. [Google Scholar] [CrossRef]
- Farahani, B.; Firouzi, F.; Chang, V.; Badaroglu, M.; Constant, N.; Mankodiya, K. Towards fog-driven IoT eHealth: Promises and challenges of IoT in medicine and healthcare. Future Gen. Comput. Syst. 2018, 78, 659–676. [Google Scholar] [CrossRef]
- Bovenzi, G.; Ciuonzo, D.; Persico, V.; Pescapè, A.; Rossi, P.S. IoT-enabled distributed detection of a nuclear radioactive source via generalized score tests. In International Symposium on Signal Processing and Intelligent Recognition Systems; Springer: Berlin, Germany, 2018; pp. 77–91. [Google Scholar]
- Jiang, X.; Zheng, B.; Zhu, W.P.; Wang, L.; Zou, Y. Large system analysis of heterogeneous cellular networks with interference alignment. IEEE Access 2018, 6, 8148–8160. [Google Scholar] [CrossRef]
- Haroon, M.S.; Abbas, Z.H.; Muhammad, F.; Abbas, G. Analysis of coverage-oriented small base station deployment in heterogeneous cellular networks. Phys. Commun. 2020, 38, 100908. [Google Scholar] [CrossRef]
- Haroon, M.S.; Abbas, Z.H.; Muhammad, F.; Abbas, G. Coverage analysis of cell-edge users in heterogeneous wireless networks using Stienen’s model and RFA scheme. Int. J. Commun. Syst. 2020, 33, e4147. [Google Scholar] [CrossRef]
- Jacob, P.; James, A.; Madhukumar, A.S. Downlink capacity improvement and interference reduction through reverse frequency allocation. In Proceedings of the 2012 IEEE International Conference on Communication Systems (ICCS), Singapore, 21–23 November 2012; pp. 329–333. [Google Scholar]
- Arif, M.; Wyne, S.; Navaie, K.; Haroon, M.S.; Qureshi, S. Clustered jamming in aerial HetNets with decoupled access. IEEE Access 2020, 8, 142218–142228. [Google Scholar] [CrossRef]
- Haenggi, M. Stochastic Geometry for Wireless Networks; Cambridge University Press: Cambridge, UK, 2012. [Google Scholar]





| Acronym | Description |
|---|---|
| IJs | Intentional jammers |
| HetNets | Heterogeneous cellular networks |
| SBSs | Small base stations |
| MBS | Macro base station |
| IJs-I | IJs-interference |
| UL | Uplink |
| RFA | Reverse frequency allocation |
| IoT | Internet of things |
| ICI | Inter-cell interference |
| NU-HetNets | Non-uniform HetNets |
| FFR | Fractional frequency reuse |
| SFR | Soft frequency reuse |
| DL | Downlink |
| NOMA | Non-orthogonal multiple access |
| 5G | Fifth-generation |
| M-EUs | MBS edge-users |
| LT | Laplace transform |
| DDoS | Distributed denial-of-service |
| SIR | Signal-to-interference ratio |
| Notation | Description |
|---|---|
| , , , | IHPPPs of MBSs, SBSs, users, |
| and IJs, respectively | |
| SIR threshold | |
| Radius of and , | |
| respectively | |
| , and | Densities of MBSs, SBSs, and |
| IJs, respectively | |
| Path loss exponent, | |
| , and | |
| Typical user | |
| Denotes RFA employment | |
| Ratio of | |
| Ratio of | |
| Ratio of | |
| Ratio of |
| Parameter | Configuration |
|---|---|
| Channel bandwidth | 10 MHz |
| MBS, SBSs, IJs | IHPPPs |
| Code iterations | 1000 |
| A | |
| 20/ | |
| 4/ | |
| 20/ | |
| Transmit powers of MBS, SBS, , and IJs | 45 dBm, 33 dBm, 20 dBm, and 20 dBm, respectively |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Qasim, M.; Haroon, M.S.; Imran, M.; Muhammad, F.; Kim, S. 5G Cellular Networks: Coverage Analysis in the Presence of Inter-Cell Interference and Intentional Jammers. Electronics 2020, 9, 1538. https://doi.org/10.3390/electronics9091538
Qasim M, Haroon MS, Imran M, Muhammad F, Kim S. 5G Cellular Networks: Coverage Analysis in the Presence of Inter-Cell Interference and Intentional Jammers. Electronics. 2020; 9(9):1538. https://doi.org/10.3390/electronics9091538
Chicago/Turabian StyleQasim, Muhammad, Muhammad Sajid Haroon, Muhammad Imran, Fazal Muhammad, and Sunghwan Kim. 2020. "5G Cellular Networks: Coverage Analysis in the Presence of Inter-Cell Interference and Intentional Jammers" Electronics 9, no. 9: 1538. https://doi.org/10.3390/electronics9091538
APA StyleQasim, M., Haroon, M. S., Imran, M., Muhammad, F., & Kim, S. (2020). 5G Cellular Networks: Coverage Analysis in the Presence of Inter-Cell Interference and Intentional Jammers. Electronics, 9(9), 1538. https://doi.org/10.3390/electronics9091538






