Blockchain-Based Continued Integrity Service for IoT Big Data Management: A Comprehensive Design
Abstract
:1. Introduction
- We propose blockchain-based integrity services for data in transit by proposing decentralized identity management and secure channel establishment. Our designs comprise registration, update, and revocation of the public key and the associated domain names. We also present a secure and reliable Transport Layer Security (TLS) or Datagram Transport Layer Security (DTLS) secure channel using our identity management as its foundation.
- We investigate using the chain of signatures and blockchain receipts to provide data integrity during data at rest for IoT databases. Using both combinations, we can preserve the forensically sound guarantee of the stored raw IoT data and commands.
- We leverage the blockchain to empower the decentralized marketplace and federated learning to encourage IoT entities’ collaborations. This proposal augments the overall data’s robustness because blockchain logs every action in IoT processes. As a result, entities can offer IoT data training services or participate in federated learning processes in a fair, transparent, secure, and verifiable manner.
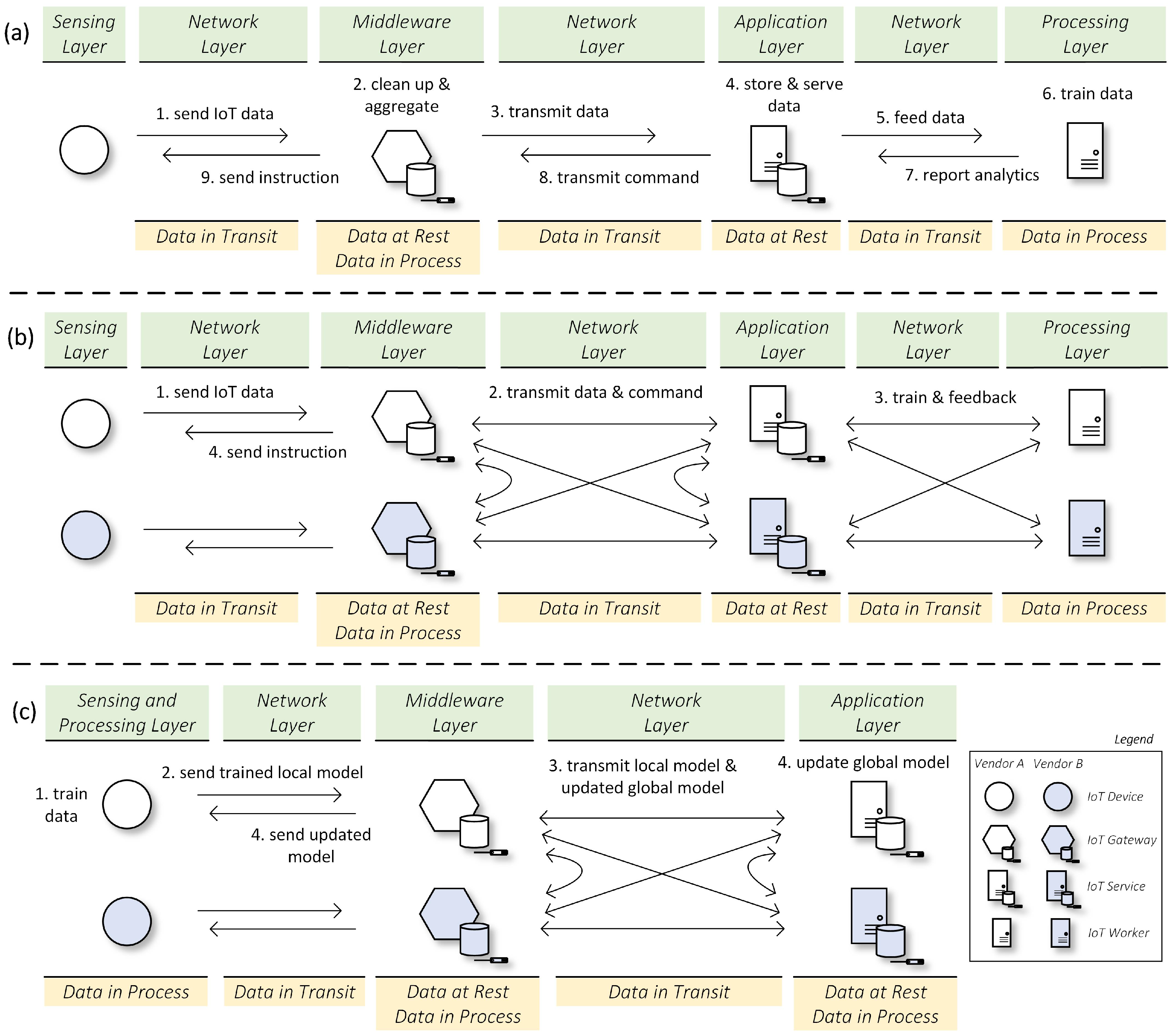
2. IoT Big Data Management
2.1. Characteristics of IoT Data Flow Pipeline
2.2. Types of IoT Data Flow Pipeline
2.3. Basic Challenges and Requirements for IoT Data Flow Pipeline
3. Blockchain Solutions for Data in Transit
3.1. Motivations
3.2. Our Proposed Solutions
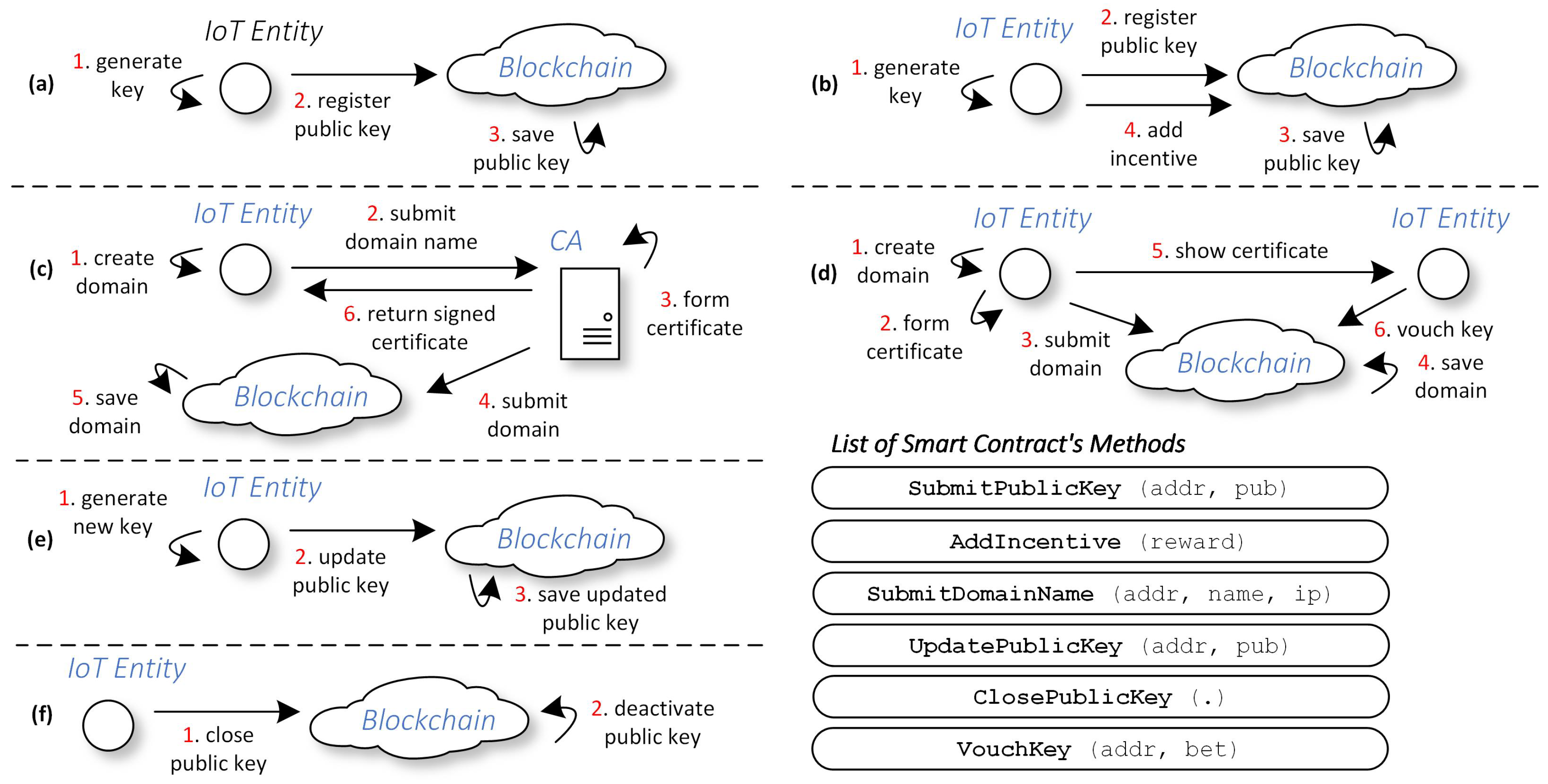
3.2.1. Decentralized Identity Management
- Quasi-centralized approach reduces CA and the DNS server’s centralization impact by implementing a kind of certificate transparency [27] in the blockchain. When we store a list of identities in the blockchain, the list becomes open to all nodes. Thus, they can verify an IoT entity’s trustworthiness and can expose the possibility to detect malicious identity or misbehaving CA and DNS servers quickly.
- The fully decentralized method removes the role of the CA or DNS server altogether, and all participants collectively manage the identity management. Specifically, we employ the Pretty Good Privacy (PGP) technique [28], where we manage identity distributedly in the form of Web of Trust (WoT) [29]. In this second option, we leverage blockchain as a platform to perform WoT.
- The entity generates two pairs of keys—the online and offline key—using ECDSA key-generation procedure similar to the one used to generate the Ethereum address [30]. , , , and are the online public key, online secret key, offline public key, and offline secret key, respectively. From these keys, the entity also generates the corresponding online and offline addresses and . X refers to the entity’s role in the IoT system, whether it is an IoT device, gateway, service, or worker. Thus, .
- The entity submits and to the smart contract by calling the SubmitPublicKey(addr, pub) method. The addr and pub are the entity’s online address and online public key to be submitted. The entity must use its offline address, , as the sender when forming the transaction for this method.
- The smart contract maintains the mapping between offline and online keys in key-value storage. Upon receving the transaction from the previous step, the smart contract retrieves and . It also queries from the sender parameter. The smart contract then saves a new entry in the list using as keys and as its values.
- In the fully decentralized approach, the entity calls the AddIncentive (reward) method to add a prize to encourage other entities to vouch for this key. The reward is the award that endorsers of this public key can claim later. The entity also must use their offline address, , as the sender when creating the transaction for this method. We take this idea from Wilson and Ateniese [22], which discuss the endorsement issues of PGP and WoT for a newly registered key.
- The entity creates an arbitrary domain name, . It also retrieves the public IP, , from the Internet Service Provider (ISP).
- The entity submits and along with , , and to the CA off-chain. It also needs to provide detailed information regarding proof of domain name and public IP address possession for legal purposes. The CA verifies the proof and makes sure that the submitted domain name is unique.
- The CA then forms a certificate that testifies the entity’s possession of the domain name. In particular, the CA creates X.509 certificates for TLS or DTLS scenarios. We borrow the X.509 extensions from [21]. The authors suggest to include blockchain information such as the address of the smart contract, the CA’s blockchain address, and the hashing algorithm as additional info in X.509 fields. Therefore, when another party receives this signature, that party can pinpoint the issuers’ details and determine which smart contract they contact to verify the signature.
- 4.
- The CA submits the , , and to the smart contract by calling the SubmitDomainName(addr, name, ip) method. addr, name, and ip are the offline address, domain, and the public IP address name to be submitted, respectively.
- 5.
- The smart contract maintains a list of registered domain names in a key-value store. Upon receiving the transaction in the previous step, the smart contract puts as the key and as the value in the store. We apply domain names as keys to ensure the uniqueness of the stored namespaces. We save to map the domain name with its IP address. The role of as a value is to bridge this domain name list and the mapping of offline and online keys storage. Therefore, from this link, the smart contract can find a relationship between and its associated online identities, , and .
- 6.
- The CA returns to the entity. The entity can then present this certificate during the handshake of the secure channel establishment that we explain in the next section. By default, other users will trust this certificate because the CA signed it.
- The entity creates an arbitrary domain name, . They also receive the public IP, , from the ISP.
- Because there is no CA in this approach, the entity forms a certificate by itself, which produces proof regarding possession of the domain. We borrow the certificate format proposed in SCPKI [19]. Some mandatory information includes the smart contract address, the entity’s online public key, and its online address. These parameters are essential to guide other users in the verification of the certificate.After that, the entitiy signs the certificate with its online secret key, . refers to X’s certificate. The entity then includes its signature in the certificate, .
- The entity submits , , and to the smart contract by calling the SubmitDomainName(addr, name, ip) method.
- Similar to the quasi-centralized approach, the smart contract then puts as the key and as the value in the storage.
- Once it is stored, the entity can present during the handshake of secure channel establishment.
- 6.
- To endorse a particular certificate, IoT entities can vouch for the certificate’s corresponding online address. The IoT entity calls the VouchKey(addr, bet) method. addr and bet are the online address and the stake to endorse the given address.
- The entity generates a new pair of online key and its address, , , and .
- The entity then uploads both the key and address to the smart contract by creating a transaction that calls the UpdatePublicKey(addr, pub) method. addr and pub are the new online blockchain address and public key. Note that they need to use the old offline address, , as the sender of the transaction when calling this method.
- Upon receiving this transaction, the smart contract checks the sender and ensures that it equals the previously stored address during identity registration. This check is to guarantee that only the original submitter can update the online keys. If everything is valid, the smart contract stores the new online keys in the database.
- The entity creates a transaction that calls the ClosePublicKey(.) method. They need to use the previously registered offline address, , as the sender when forming the transaction.
- Upon receiving this transaction, the smart contract checks its sender and makes sure it exists in storage. This check is to guarantee that only the original submitter can close online keys. If everything is verified, the smart contract marks the online keys as closed.
3.2.2. Secure Channel Establishment
- A trusted party deploys the smart contract in the blockchain network. For example, the CA is responsible for this role in the quasi-centralized approach. For the fully decentralized method, the government can serve this role.
- We employ IoT services and gateways in this scenario merely as an example. One can reuse the protocol to build a secure channel between any IoT entities.
- The gateway already registered its public key, address, namespace, and IP address in the blockchain, specifically , , , and . Moreover, the gateway’s certificate, , is also ready to use.
- The gateway provides IoT data and service by allowing IoT services to access the IoT domain through a URL (e.g., https://gateway.bit) tied to . Thus, is gateway.bit.
- The IoT gateway already built some positive reputation scores in the system.
- The IoT service is trying to access IoT contents from the URL (e.g., https://gateway.bit). Optionally, before the service accesses the URL, it invokes the GetReputation(name) method in the smart contract by including the gateway.bit (i.e., ) as the name argument. The smart contract then returns the reputation score for the gateway.bit domain.
- Assuming that the IoT service is satisfied with the reputation score, it begins to access the URL. We assume that this is the first time the IoT service accesses this URL. Therefore, the service conducts DNS operations to resolve the IP address for the given domain. It calls the ResolveAddress(name) method and puts gateway.bit as the name argument. The smart contract returns the domain’s IP address, .
- The IoT service begins the initial TLS handshake. During this exchange, the service must gather proof that it participates in the handshake to later vote for the gateway’s certificate. For this purpose, we borrow the concept of TLS notary in PADVA [26].
- 4.
- The gateway replies with ServerHello, ServerKeyExchange, and ServerHelloDone messages.ServerKeyExchange includes the server-random property as the server part of the exchange to build the final ephemeral secret key. The gateway puts a UNIX timestamp in this random, which can serve as our proof. Moreover, the gateway also signs the server-random, defined as , and generates the signature, .
- 5.
- Upon receiving the , the IoT service retrieves the gateway’s public key, , from the certificate and verifies that returns True. After that, the service validates the rest of the certificate.
- 6.
- The service compares the required fields in the certificate with the ones stored in the smart contract. It invokes the VerifyCertificate(name) method with gateway.bit as an argument. First, the smart contract makes sure that the certificate (i.e., identifiable by ) exists in the blockchain. Second, it validates that the certificate is still active and not expired. Finally, the smart contract verifies that the certificate is associated with the given domain. The smart contract will return a True value when everything checks out. Otherwise, it returns False.
- 7.
- The service then sends ClientKeyExchange and ChangeCipherSpec messages to negotiate the encryption algorithms and specifications that both parties will use after they established the secure channel. It then closes the handshake by transmitting a Finished message.
- 8.
- Finally, the gateway replies with a ChangeCipherSpec message to confirm the selection of encryption algorithms and specifications. It then ends the handshake by sending a Finished message.
- 9.
- Once the secure channel session expires, the service votes on the gateway by executing the VoteDomain(name, score, proof) method by submitting gateway.bit as the name argument.
3.3. Quick Analysis
4. Blockchain Solutions for Data at Rest
4.1. Motivations
4.2. Our Proposed Solutions
4.2.1. IoT Data Gathering
- In the first image (a), an IoT sensor device, D, transmits its IoT data readings to the nearby IoT gateway, . D also provides its signature to the generated data, , which it signs using its private key, . is an IoT data reading. then relays the message to the IoT service, S. Therefore, also appends its signature to the received data, . When the data arrives at the Cloud, S stores signed data in its database, as shown in the image (e) with .
- The second image (b) depicts a similar scenario like the one in (a). However, we have two gateways now, and . Therefore, the chains are longer compared to the previous example. When the data arrives in S, the service stores the received data depicted in the image (e) with . It contains three signatures: , , and , which were derived from , , and .
- In the third scenario (c), receives two readings from two devices: and . Like the two previous scenarios, device signatures and accompany those readings. The signatures are obtained from and . However, different from previous scenarios, now has a local database. stores and in its local database as shown in image (f) with and . Furthermore, also generates a reference pointer for those two data, . This pointer links contents in its local database with the one stored in S later.
4.2.2. IoT Data Storing
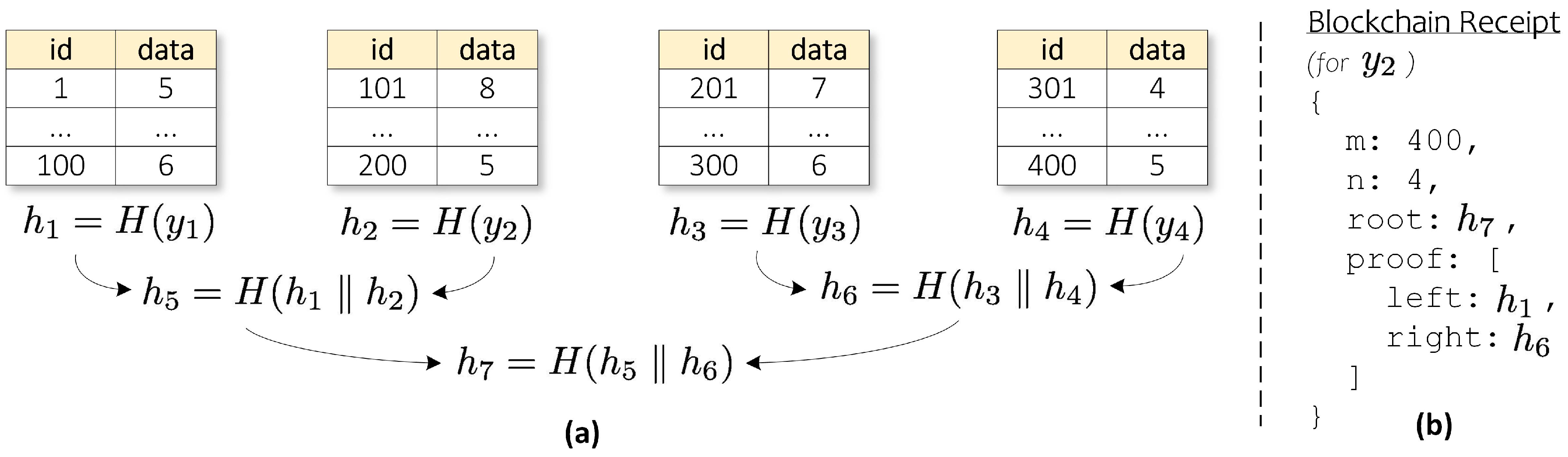
- First of all, we have two essential parameters for blockchain receipts: m and n. m is a threshold defining the number of newly inserted rows in a table to trigger the blockchain receipt generation process. Meanwhile, n is the number of leaves to construct the Merkle Root [44]. These two parameters are configurable by the administrations. For simplicity, let us assume that we set m equal to 400 and n to the value of 4.
- During IoT operations, the IoT service receives and saves IoT data in its database. Suppose that we have a daemon in our system that detects our storage state, similar to the idea proposed in [41]. Once the service has more than 400 newly inserted data, it triggers the m parameter and starts building blockchain receipts.
- Following the m parameter, the service queries 400 rows of tables from the database. We separate these data into a new table, Y. Then, we divide this table into 4 sub-tables, , matching the n parameter. is a concatenation of the first 100 rows in the table, which is . Meanwhile, , , and are for the second, the third, and the fourth 100 rows. They are , , and , respectively.
- 4.
- The service calculates the Merkle Root hash, which is again illustrated in Figure 6a. From each of the sub-tables, the service generates the hash: , , , and . refers to any hash function. After that, the service hashes and to generates . Then, it hashes and to produces , specifically and . Following a pyramid scheme, the service then forms the summit by hashing and together: . This is the Merkle Root hash.
- 5.
- The service then stores in the blockchain by forming a transaction to call the StoreRootHash (hash) method in the smart contract. The hash is the Merkle Root hash to be stored, which is .
- 6.
- Once the service saves the root hash in the blockchain, it generates blockchain receipts for each of the sub-tables. An example of such a receipt is shown in Figure 6b. That receipt is for , which contains data from row 101 to 200. In the receipt, we can find the m, n, , and information. The indicates the Merkle Root hash, while the is the trace of the ’s opposite hash in the pyramid scheme to reach the root hash. Then, the service keeps these blockchain receipts in a secure place separated from IoT raw data storage.
4.2.3. IoT Data Sharing
- The IoT service delivers the IoT data, Y, and its corresponding blockchain receipts to the auditor. In this example, we assume that the service shares the data in plaintext form and without any authentication.
- 2.
- After receiving all of the data and associated receipts, the auditor queries the m and n parameters from the receipt. First, it takes 400 records of data following the m parameter. Then, because n is equal to 4, the auditor splits the data into 4 sub-tables and forms , , , and . For simplicity, we only show the verification of in this section. The corresponding blockchain receipt is depicted in Figure 6b.
- 3.
- contains the second 100 rows of the table: . The auditor hashes to generate , .
- 4.
- Afterward, the auditor queries the information from the receipt. The contains instructions on aligning the provided corresponding hashes ( and ) with to form the Merkle Root hash. The auditor must follow the directions in order. The first line of the gives two parameters: the hash and the hash’s alignment . Therefore, the auditor puts on the of and hashes it to generate , . After that, following the second line guidance, the auditor puts on the of to generate : . When we find no other advice, it means that we reached the Merkle Root hash already. In this case, will be the auditor’s generated root hash.
- 5.
- The auditor then queries the information from the receipt and obtains , the Merkle Root generated by the IoT service.
- 6.
- The auditor then conducts two verifications. First, it needs to ensure that is equal to . Afterward, it needs to check if this is recorded in the blockchain. The auditor forms a transaction that calls the VerifyRootHash(hash) method in the smart contract. The hash is the Merkle Root hash to be verified, which is . The method will return True if they find in the smart contract’s storage.
- 7.
- If all of the above validations do not result in an error (or return False), then the auditor can assure that no one tampered with the sub-table data’s content. The auditor can then continue the same process to verify the rest of the sub-tables, mainly , , and .
4.3. Quick Analysis
5. Blockchain Solutions for Data in Process
5.1. Motivations
5.2. Our Proposed Solutions
5.2.1. Blockchain-Based Decentralized Marketplace
- IoT services act as buyers in our e-marketplace. We assume that they have many raw IoT data from their IoT operations, but they cannot train them on their own.
- IoT workers exist as sellers in the market, which provides training services for IoT services.
- A notary (e.g., the government as a trusted third-party) initially governs the market. This entity develops the market rule by also counting feedback from IoT services and workers as the market players. The market can be run automatically in a decentralized manner without any further intervention once the notary deploys the smart contract.
- The smart contract has a reputation system, and the IoT services and workers already built some positive scores in the system.In general, we can integrate our market with any available reputation system. However, we are interested in using the proposal from [55]. The authors present a reputation procedure with the anonymity feature, which can protect users’ privacy. Therefore, users are most likely to give honest reviews without being worried about being tracked or discriminated against if they give poor score reviews.
- In this scenario, we use deep neural networks [57] as an example of IoT data training. However, this market can be redefined customarily to match any machine learning algorithm. Thus, it is algorithm-agnostic.
- For simplicity, we only show a one-to-one mapping scenario between IoT services and workers. In real cases, race conditions may exist. IoT services can contact many IoT workers, and IoT workers may process multiple jobs from several IoT services.
- The IoT service conducts preparation for IoT data processing. It transforms its whole IoT raw data into a training dataset and splits them into several data chunks (or batches). During this separation, the IoT service applies our data at rest strategy in Section 4 to generate Merkle Root hash and the blockchain receipts. More specifically, Y becomes the whole training dataset, and y is the training batch. Let us also say that is the root hash of the training dataset.
- The IoT service then creates a job request in the smart contract by calling the CreateJobRequest(root, reward, param, deadline) method. root is the Merkle Root hash of the training dataset, . reward is the payment for IoT workers after completing the task, e.g., 100 coins. param is the training parameter and requirements. They can be the type of training (e.g., classification, prediction, or generation) and the desired training result (e.g., having at least 90% accuracy). Finally, deadline is the time limit for the workers to return the training result to the service, e.g., a UNIX timestamp.
- 3.
- The smart contract maintains lists of job requests in local storage. At any given time, they can only have one of the following states in the smart contract.
- Unprocessed is when the IoT service just offered the job request, and no IoT worker processes it.
- InProgress tells us that the IoT service has assigned the job to one of the IoT workers.
- Success indicates that the job request is completed and that both the IoT service and worker are satisfied with the result.
- Failed implies that the job’s processing is unsuccessful due to one of the party cheats or timeout.
- 4.
- IoT worker queries for available job lists in the smart contract by invoking the GetAvailableJobList(.) method. The smart contract returns a list of all jobs that currently have the status of Unprocessed. Each of the available jobs is distinguishable by root or as the job identifier.
- 5.
- Optionally, the worker can check the IoT service reputation by calling the GetReputation(addr) method in the smart contract. addr is the address of the IoT service, , which the worker obtains when querying for the available job list in the previous step. Based on this reputation, the worker can decide whether to trust the job offer.
- 6.
- The worker picks one of the jobs that it is willing to train. In general, it can pick any job with the highest reward to maximize profit. However, the worker should choose wisely with consideration of its processing ability. If the worker fails to report the desired output to the service before the deadline, the worker will not be able to claim the reward, and this event can diminish its reputation.
- 7.
- Upon receving the proposal, the IoT service validates the worker’s signature, and must return True. After that, the IoT service can check the worker’s reputation by calling the GetReputation(addr) method. addr is the worker’s address, . The acceptance of a job request is then subject to the service’s judgments over the worker.
- 8.
- Assuming that the service is satisfied with the worker’s reputation, the service accepts the training offer by calling the AcceptTrainingOffer(root, addr) method. root and addr are the job id, , and the worker’s address, , respectively.
- 9.
- The smart contract sets the job request to InProgress. While in this state, no other workers except the one that the IoT service previously approved can handle this job. This lock-in mechanism ensures that no race conditions happen to boost the fairness of the market.
- 10.
- The service sends batches of raw IoT data to the worker off-chain. On each batch, the service also includes the associated blockchain receipt. With this receipt, the worker can verify that the incoming batches are part of , as described in Section 4. In other words, the service cannot cheat the worker by training more data than they previously registered in step 2.
- 11.
- The worker begins training the received data.
- 12.
- After it is complete, the worker hashes the training result (e.g., the checkpoint data if we are using TensorFlow [58]) and stores it in the smart contract. We denote as the training results from the IoT worker and as its hash, . The worker then calls the ReportTrainingResult(root, trainedHash) method, with root and trainedHash as the job identifier, , and the hash of training result, .
- 13.
- The worker delivers the training result to the service off-chain. Before transmission, the worker must include the job identifier, , and its signature, to the training result. The final training result will be .
- 14.
- The service verifies the signature and checks if the hash of the received training result matches the one in the smart contract. Specifically, must return True and the service can find , calculated from in the smart contract. Furthermore, it makes sure that the result fulfills the desired training output agreed during the job request submission in step 2. Note that the service can replicate (without retraining) the training process easily with the given checkpoint to determine whether the training indeed has the desired output.
- 15.
- Assuming that the service is satisfied with the result, it ends this job request by calling the EndJob(root, status) method. The status is either Success or Failed. If the result fulfills the training objectives, then the service sends Success state. Otherwise, they set the status to Failed. As a fail-safe mechanism, the service can only call this method after the worker submits the training result. Therefore, the service cannot cancel InProgress jobs arbitrarily and damage the worker’s training efforts.
- 16.
- Upon receiving the previous transaction, the smart contract sets the job request to either Success or Failed.
- 17.
- When a job request is successful, the worker withdraws the reward from the smart contract using the ClaimReward(root) method. However, if the job fails, the service takes its previous deposit back from the smart contract using the same method. Moreover, the service can also retrieve their deposit back if the worker cannot complete the training within the given deadline. The smart contract will automatically set the job status to a Failed state.
- 18.
- Once the job session ends, whether it is successful or failed, the service and worker vote for each other’s reputation by invoking the VoteReputation(addr, score) method. addr is the address of the service or worker, or . Meanwhile, the score is the reputation value to give.
5.2.2. Blockchain-Based Federated Learning
- IoT devices generate IoT raw data and train them in their local machine. Instead of allocating their private IoT data, IoT devices share their training results with IoT services.
- Mobile Edge Computing (MEC) servers are edge servers available near IoT devices. They help to alleviate parts of the training from the IoT devices by splitting the training model.
- IoT services take the trained model from IoT devices and provide analytics to IoT users. They also create the training rule and apply it to the smart contract. If IoT devices agree with the regulation, they can join the training.
- The smart contract has a reputation system, and IoT devices and the service have positive scores. We use the same reputation procedure [55] as in our decentralized marketplace.
- In this example, we apply the federated learning that McMahan et al. [50] proposed. However, our design can be reconstructed to match any federated learning algorithm. Thus, it is algorithm-agnostic.
- We only show a one-to-many mapping scenario between the IoT service and their manufactured devices. In real cases, several IoT services can use the platform simultaneously.
- The IoT service prepares the model and its parameters (e.g., the number of nodes and layers, the structure of the model, the value of learning rate, weight, bias, and the activation function to use).
- 2.
- The IoT service signs the model and obtains the signature, , derived from . The denotes the initiated global model. The IoT service then stores this signature and the global model in the InterPlanetary File System (IPFS) [59]. From this action, the service retrieves the IPFS hash, , indicating that the IPFS network has saved its model.
- 3.
- The IoT service then creates a new federated learning process in the blockchain by calling the CreateTrainingRequest(hash, reward, targetRound, deadline) method. hash is the IPFS hash of the model, , which also acts as a training process identifier to distinguish one training from another. reward informs the number of payments for all voluntary training participants (e.g., 10 coins). targetRound denotes the final global epoch required to end this federated learning process (e.g., 3 epochs). Finally, deadline is the time limit range (e.g., in UNIX timestamp) for IoT devices to submit their local model at each epoch.
- 4.
- The smart contract maintains lists of training requests in local storage. At any given time, they can only have one of the following states in the smart contract.
- Unprocessed tells us that the training request is open for anyone to join.
- InProgress informs us that the training registration has finished and that all participants are currently performing training.
- Finished indicates that the IoT service has ended this request.
- 5.
- Interested IoT devices can begin querying for available federated learning processes using the GetAvailableTraining(.) method. The smart contract returns a list of all Unprocessed training requests, which includes the owner address, and the corresponding training identifier, .
- 6.
- Optionally, IoT devices can check for the training request owner’s reputation by calling the GetReputation(addr) method. addr is the address of the IoT service, . If IoT devices satisfy the service’s reputation, they can continue the process. Otherwise, they can stop and look for other training requests.
- 7.
- After choosing one training request to perform, IoT devices register to participate in the training by invoking the RegisterTraining(.) method. The smart contract will take the sender of this transaction, , and will save it to the list of participants in its local storage.
- 8.
- The deadline for the current epoch expires. The smart contract then sets the status of the training request to InProgress and the round parameter to 1. With this change, registration is now closed. The devices can now begin performing training.
- 9.
- IoT devices download the initial global model from the IPFS network using . They also need to verify the authenticity of the model, and must return True.
- 10.
- They then perform the local training using their own machines and private data. Once the training is complete, they update their local model parameters.
- 11.
- IoT devices sign their updated local model and generate the signature, . denotes the updated local model. They then upload the model and its signature in the IPFS network. We denote as the IPFS hash containing the local model update from device a for epoch b. Thus, and represent the first and second IoT devices’ hash for the first epoch.
- 12.
- IoT devices then store the local update metadata to the blockchain by calling the StoreLocalModel(hash, localHash) method. hash is the training identifier, . localHash is the IPFS hash pointer for others to download the updated local model (e.g., ).
- 13.
- When receiving the transaction for this method, the smart contract put the hash and sender of this transaction (i.e., ) into storage. The smart contract maintains a list of the updated local model per epoch.
- 14.
- The deadline for the current epoch expires. The smart contract sets the round parameter to 2.
- 15.
- IoT devices are aware of the round change and begin downloading all updated local models from other devices. They query for all models from to , where n denotes the index of the last IoT device.
- 16.
- Each of them validates the downloaded model and votes for the quality of the model. They make sure that returns True. After that, they call VoteReputation(addr, score) with addr and score as the device’s address and the reputation score to give.
- 17.
- IoT devices simultaneously aggregate all local model parameters from all devices and update the global model.
- 18.
- IoT devices then perform training for the next epoch (repeating step 10 to 17) until round matches the targetRound that the IoT service specified previously in step 3.
- 19.
- Once the final epoch is complete, the IoT service gathers all of the local model parameters from devices.
- 20.
- After that, it updates the global model.
- 21.
- The IoT service starts to distribute the reward to all IoT participants by invoking the CloseTraining(hash, rewardParam) method. hash is the training identifier, . rewardParam is a softmax array multiplier that will be applied to split compensation to all training participants.
- 22.
- The smart contract then changes the training status to Finished.
- 23.
- IoT devices can begin claiming their reward using the ClaimReward(hash) method with the hash sets to .
- 24.
- Last but not least, the IoT device can vote for the IoT service using the VoteReputation(addr, score) method. addr and score are the IoT service address, , and the reputation score to give.
5.3. Quick Analysis
6. Discussion
6.1. Solutions to IoT Big Data Open Problems
6.2. Future Considerations and Challenges
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| IoT | Internet of Things |
| TLS | Transport Layer Security |
| DTLS | Datagram Transport Layer Security |
| CoAP | Constrained Application Protocol |
| MQTT | Message Queuing Telemetry Transport |
| SLA | Service Level Agreement |
| API | Application Programming Interface |
| UUID | Universal Unique Identifier |
| PKI | Public Key Infrastructure |
| DNS | Domain Name Service |
| CA | Certificate Authority |
| PGP | Pretty Good Privacy |
| WoT | Web of Trust |
| ISP | Internet Service Provider |
| ECDSA | Elliptic Curve Digital Signature Algorithm |
| FL | Federated Learning |
| MEC | Mobile Edge Computing |
| IPFS | InterPlanetary File System |
| PoW | Proof-of-Work |
| BFT | Byzantine Fault Tolerance |
| DApp | Distributed Application |
References
- Rayome, A.D. How the Term ’Internet of Things’ Was Invented. Available online: https://tek.io/2E2BBaF (accessed on 22 July 2020).
- Bashmakov, P. 3 Types of Software Architecture for Connected Devices. A Smart Light Bulb Case. Available online: https://bit.ly/2OJHv2u (accessed on 22 July 2020).
- Roman, R.; Zhou, J.; Lopez, J. On the features and challenges of security and privacy in distributed internet of things. Comput. Netw. 2013, 57, 2266–2279. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bit.ly/32Gtgnn (accessed on 22 July 2020).
- Christidis, K.; Devetsikiotis, M. Blockchains and smart contracts for the internet of things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog computing and its role in the internet of things. In Proceedings of the First Edition of the MCC Workshop on Mobile Cloud Computing, Helsinki, Finland, 17 August 2012; pp. 13–16. [Google Scholar]
- Aftab, H.; Gilani, K.; Lee, J.; Nkenyereye, L.; Jeong, S.; Song, J. Analysis of identifiers on IoT platforms. Digit. Commun. Netw. 2019. [Google Scholar] [CrossRef]
- Sharma, A.; Kalbarczyk, Z.; Iyer, R.; Barlow, J. Analysis of credential stealing attacks in an open networked environment. In Proceedings of the 2010 Fourth International Conference on Network and System Security, Melbourne, Australia, 1–3 September 2010; IEEE: Piscataway, NJ, USA, 2010; pp. 144–151. [Google Scholar]
- Rumbold, J.M.; Pierscionek, B.K. What are data? A categorization of the data sensitivity spectrum. Big Data Res. 2018, 12, 49–59. [Google Scholar] [CrossRef] [Green Version]
- Wood, G. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32. [Google Scholar]
- Quorum. Quorum Whitepaper. Available online: https://bit.ly/3hotYKj (accessed on 21 July 2020).
- Pubkey. Eth-Crypto. Available online: https://bit.ly/2OOFWjO (accessed on 22 July 2020).
- Chen, D.; Bovornkeeratiroj, P.; Irwin, D.; Shenoy, P. Private memoirs of iot devices: Safeguarding user privacy in the iot era. In Proceedings of the Systems (ICDCS), Vienna, Austria, 2–6 July 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1327–1336. [Google Scholar]
- Myers, M.; Ankney, R.; Malpani, A.; Galperin, S.; Adams, C.X. 509 Internet Public Key Infrastructure Online Certificate Status Protocol-OCSP. Available online: https://bit.ly/2ZOCSJO (accessed on 10 July 2020).
- Mockapetris, P. Domain nAmes-Concepts and Facilities. Available online: https://bit.ly/321Au4Z (accessed on 10 July 2020).
- Arghire, I. Sectigo Revokes Certificates Used to Sign Malware Following Recent Report. Available online: https://bit.ly/2ZTaPJk (accessed on 10 July 2020).
- Bormann, C.; Castellani, A.P.; Shelby, Z. Coap: An application protocol for billions of tiny internet nodes. IEEE Internet Comput. 2012, 16, 62–67. [Google Scholar] [CrossRef]
- Hunkeler, U.; Truong, H.L.; Stanford-Clark, A. MQTT-S—A publish/subscribe protocol for Wireless Sensor Networks. In Proceedings of the 2008 3rd International Conference on Communication Systems Software and Middleware and Workshops (COMSWARE’08), Bangalore, India, 5–10 January 2008; IEEE: Piscataway, NJ, USA, 2008; pp. 791–798. [Google Scholar]
- Al-Bassam, M. SCPKI: A smart contract-based PKI and identity system. In Proceedings of the ACM Workshop on Blockchain, Cryptocurrencies and Contracts, Abu Dhabi, UAE, 2 April 2017; pp. 35–40. [Google Scholar]
- Namecoin. Dot-Bit. Available online: https://bit.ly/322Abab (accessed on 9 July 2020).
- Yakubov, A.; Shbair, W.; Wallbom, A.; Sanda, D. A blockchain-based pki management framework. In Proceedings of the First IEEE/IFIP International Workshop on Managing and Managed by Blockchain (Man2Block) Colocated with IEEE/IFIP NOMS 2018, Tapei, Tawain, 23–27 April 2018. [Google Scholar]
- Wilson, D.; Ateniese, G. From pretty good to great: Enhancing PGP using bitcoin and the blockchain. In Proceedings of the International Conference on Network and System Security, New York, NY, USA, 3–5 November 2015; Springer: Berlin/Heidelberg, Germany, 2015; pp. 368–375. [Google Scholar]
- Fromknecht, C.; Velicanu, D.; Yakoubov, S. CertCoin: A NameCoin Based Decentralized Authentication System 6.857 Class Project. Available online: https://bit.ly/2Z9FbrW (accessed on 8 July 2020).
- Kalodner, H.A.; Carlsten, M.; Ellenbogen, P.; Bonneau, J.; Narayanan, A. An Empirical Study of Namecoin and Lessons for Decentralized Namespace Design; WEIS Citeseer: Sunbury, PA, USA, 2015. [Google Scholar]
- Moinet, A.; Darties, B.; Baril, J.L. Blockchain based trust & authentication for decentralized sensor networks. arXiv 2017, arXiv:1706.01730. [Google Scholar]
- Szalachowski, P. PADVA: A blockchain-based TLS notary service. In Proceedings of the 2019 IEEE 25th International Conference on Parallel and Distributed Systems (ICPADS), Tianjin, China, 4–6 December 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 836–843. [Google Scholar]
- Laurie, B. Certificate transparency. Commun. ACM 2014, 57, 40–46. [Google Scholar] [CrossRef]
- Zimmermann, P.R.; Zimmermann, P.R. The official PGP User’s Guide; MIT Press Cambridge: Cambridge, MA, USA, 1995; Volume 5. [Google Scholar]
- Golbeck, J.; Parsia, B.; Hendler, J. Trust networks on the semantic web. In International Workshop on Cooperative Information Agents; Springer: Berlin/Heidelberg, Germany, 2003; pp. 238–249. [Google Scholar]
- Tore, T. Technical Guide to Generating an Ethereum Addresses. Available online: https://bit.ly/2O51HvA (accessed on 8 July 2020).
- Greenberg, A. A ’Blockchain Bandit’ Is Guessing Private Keys and Scoring Millions. Available online: https://bit.ly/2WdKrZJ (accessed on 8 July 2020).
- Dierks, T. The Transport Layer Security (TLS) Protocol Version 1.2. Available online: https://bit.ly/2O8Azfc (accessed on 9 July 2020).
- Rescorla, E.; Modadugu, N. Datagram Transport Layer Security Version 1.2. Available online: https://bit.ly/3228mie (accessed on 9 July 2020).
- Helme, S. Revocation Is Broken. Available online: https://bit.ly/2ZhgUQK (accessed on 10 July 2020).
- Leonhard, W. Another Privacy Threat: DNS Logging and How to Avoid It. Available online: https://bit.ly/3iPdcWf (accessed on 10 July 2020).
- MacAskill, E.; Josh, H. WikiLeaks Shutdown Calls Spark Censorship Row. Available online: https://bit.ly/3ea9ClS (accessed on 10 July 2020).
- Boneh, D.; Gentry, C.; Lynn, B.; Shacham, H.I. A Survey of Two Signature Aggregation Techniques. CryptoBytes 2003, 6, 1–10. [Google Scholar]
- Hossain, M.; Karim, Y.; Hasan, R. FIF-IoT: A Forensic Investigation Framework for IoT Using a Public Digital Ledger. In Proceedings of the 2018 IEEE International Congress on Internet of Things (ICIOT), San Francisco, CA, USA, 2–7 July 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 33–40. [Google Scholar]
- Proof of Existence. Select a Document and Have It Certified in the Bitcoin Blockchain. Available online: https://bit.ly/3gXYUko (accessed on 14 July 2020).
- Vaughan, W.; Bukowski, J.; Wilkinson, S. ChainPoint—A Scalable Protocol for Anchoring Data in the Blockchain and Generating Blockchain Receipts. Available online: https://bit.ly/3iYmOOh (accessed on 14 July 2020).
- Liang, X.; Zhao, J.; Shetty, S.; Li, D. Towards data assurance and resilience in iot using blockchain. In Proceedings of the MILCOM 2017–2017 IEEE Military Communications Conference (MILCOM), Baltimore, MD, USA, 23–25 October 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 261–266. [Google Scholar]
- Kishigami, J.; Fujimura, S.; Watanabe, H.; Nakadaira, A.; Akutsu, A. The blockchain-based digital content distribution system. In Proceedings of the 2015 IEEE Fifth International Conference on Big Data and Cloud Computing, Dalian, China, 26–28 August 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 187–190. [Google Scholar]
- Egorov, M.; Wilkison, M.; Nuñez, D. NuCypher KMS: Decentralized key management system. arXiv 2017, arXiv:1707.06140. [Google Scholar]
- Merkle, R.C. Protocols for public key cryptosystems. In Proceedings of the 1980 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 14–16 April 1980; IEEE: Piscataway, NJ, USA, 1980; p. 122. [Google Scholar]
- Luo, Z.; Zhao, S.; Lu, Z.; Sagduyu, Y.E.; Xu, J. Adversarial Machine Learning based Partial-model Attack in IoT. arXiv 2020, arXiv:2006.14146. [Google Scholar]
- McKemmish, R. When is digital evidence forensically sound? In Proceedings of the IFIP International Conference on Digital Forensics, Kyoto, Japan, 28–30 January 2008; Springer: Berlin/Heidelberg, Germany, 2008; pp. 3–15. [Google Scholar]
- Amazon Web Services, Inc. AWS IoT Analytics—Analytics for IoT Devices. Available online: https://amzn.to/2ZrKzXg (accessed on 15 July 2020).
- Microsoft Azure. Ingestion and Processing of Real-Time Automotive IoT Data. Available online: https://bit.ly/32nUwa7 (accessed on 15 July 2020).
- Hynes, N.; Dao, D.; Yan, D.; Cheng, R.; Song, D. A demonstration of sterling: A privacy-preserving data marketplace. Proc. Vldb Endow. 2018, 11, 2086–2089. [Google Scholar] [CrossRef] [Green Version]
- McMahan, B.; Moore, E.; Ramage, D.; Hampson, S.; y Arcas, B.A. Communication-efficient learning of deep networks from decentralized data. In Proceedings of the 20th International Conference on Artificial Intelligence and Statistics, Fort Lauderdale, FL, USA, 20–22 April 2017; pp. 1273–1282. [Google Scholar]
- Li, Z.; Liu, J.; Hao, J.; Wang, H.; Xian, M. CrowdSFL: A Secure Crowd Computing Framework Based on Blockchain and Federated Learning. Electronics 2020, 9, 773. [Google Scholar] [CrossRef]
- Zhao, Y.; Zhao, J.; Jiang, L.; Tan, R.; Niyato, D. Mobile edge computing, blockchain and reputation-based crowdsourcing iot federated learning: A secure, decentralized and privacy-preserving system. arXiv 2019, arXiv:1906.10893. [Google Scholar]
- Gilad, Y.; Hemo, R.; Micali, S.; Vlachos, G.; Zeldovich, N. Algorand: Scaling byzantine agreements for cryptocurrencies. In Proceedings of the 26th Symposium on Operating Systems Principles, Shanghai, China, 28–31 October 2017; pp. 51–68. [Google Scholar]
- Travizano, M.; Sarraute, C.; Ajzenman, G.; Minnoni, M. Wibson: A decentralized data marketplace. arXiv 2018, arXiv:1812.09966. [Google Scholar]
- Liu, D.; Alahmadi, A.; Ni, J.; Lin, X.; Shen, X. Anonymous reputation system for IIoT-enabled retail marketing atop PoS blockchain. IEEE Trans. Ind. Inform. 2019, 15, 3527–3537. [Google Scholar] [CrossRef]
- Kang, J.; Xiong, Z.; Niyato, D.; Yu, H.; Liang, Y.C.; Kim, D.I. Incentive design for efficient federated learning in mobile networks: A contract theory approach. In Proceedings of the 2019 IEEE VTS Asia Pacific Wireless Communications Symposium (APWCS), Singapore, 28–30 August 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–5. [Google Scholar]
- Li, P.; Chen, Z.; Yang, L.T.; Zhang, Q.; Deen, M.J. Deep convolutional computation model for feature learning on big data in internet of things. IEEE Trans. Ind. Inform. 2017, 14, 790–798. [Google Scholar] [CrossRef]
- Abadi, M.; Barham, P.; Chen, J.; Chen, Z.; Davis, A.; Dean, J.; Devin, M.; Ghemawat, S.; Irving, G.; Isard, M. Tensorflow: A system for large-scale machine learning. In Proceedings of the 12th {USENIX} Symposium on Operating Systems Design and Implementation ({OSDI} 16), Savannah, GA, USA, 2–4 November 2016; pp. 265–283. [Google Scholar]
- Benet, J. Ipfs-content addressed, versioned, p2p file system. arXiv 2014, arXiv:1407.3561. [Google Scholar]
- Taylor, K. Stores like Walmart, Lowe’s, and J.Crew Have a New Nightmare for Black Friday—And It Signals a Fundamental Shift in How We Shop. Available online: https://bit.ly/3j2CiRr (accessed on 15 July 2020).
- Gordon, A.; Mehrotra, D. We Think Uber and Lyft’s New Surge Fares Screw Drivers and Riders. Help Us Prove It. Available online: https://bit.ly/32glAIt (accessed on 15 July 2020).
- Mohri, M.; Sivek, G.; Suresh, A.T. Agnostic federated learning. arXiv 2019, arXiv:1902.00146. [Google Scholar]
- Marjani, M.; Nasaruddin, F.; Gani, A.; Karim, A.; Hashem, I.A.T.; Siddiqa, A.; Yaqoob, I. Big IoT data analytics: Architecture, opportunities, and open research challenges. IEEE Access 2017, 5, 5247–5261. [Google Scholar]
- Cachin, C. Architecture of the hyperledger blockchain fabric. In Proceedings of the Workshop on Distributed Cryptocurrencies and Consensus Ledgers, Chicago, IL, USA, 25–29 July 2016; Volume 310, p. 4. [Google Scholar]
- Vukolić, M. The quest for scalable blockchain fabric: Proof-of-work vs. BFT replication. In International Workshop on Open Problems in Network Security; Springer: Berlin/Heidelberg, Germany, 2015; pp. 112–125. [Google Scholar]
- Dinh, T.T.A.; Wang, J.; Chen, G.; Liu, R.; Ooi, B.C.; Tan, K.L. Blockbench: A framework for analyzing private blockchains. In Proceedings of the 2017 ACM International Conference on Management of Data, Chicago, IL, USA, 14–19 May 2017; ACM: New York, NY, USA, 2017; pp. 1085–1100. [Google Scholar]
- Gambetta, D. Can We Trust Trust? In Trust: Making and Breaking Cooperative Relations, Electronic Edition; Department of Sociology, University of Oxford: Oxford, UK, 2000; pp. 213–237. [Google Scholar]
- Eyal, I.; Sirer, E.G. Majority is not enough: Bitcoin mining is vulnerable. Commun. ACM 2018, 61, 95–102. [Google Scholar] [CrossRef]
- Lamport, L.; Shostak, R.; Pease, M. The Byzantine generals problem. ACM Trans. Program. Lang. Syst. TOPLAS 1982, 4, 382–401. [Google Scholar] [CrossRef] [Green Version]
- Ng, F.K. Database Backup Method. U.S. Patent 4,686,620. Available online: https://bit.ly/2ZJQpU5 (accessed on 21 July 2020).
- Katwala, A. We’re Calling It: PGP Is Dead. Available online: https://bit.ly/3fPtMmN (accessed on 21 July 2020).
- Laura, M. Exodus Wallet Review: All You Need to Know. Available online: https://bit.ly/32EiMFh (accessed on 21 July 2020).
- State of the DApps. A List of 3118 Blockchain Apps for Ethereum, Steem, EOS, and More. Available online: https://bit.ly/2WFl178 (accessed on 21 July 2020).
- Deloitte. Deloitte’s 2020 Global Blockchain Survey. Available online: https://bit.ly/2ZLuMmd (accessed on 21 July 2020).
- Rodenburg, B.; Pappas, S.P. Blockchain and Quantum Computing. Project No.: 25SPI050-12. Available online: https://bit.ly/30AfrEB (accessed on 21 July 2020).
- Kiktenko, E.O.; Pozhar, N.O.; Anufriev, M.N.; Trushechkin, A.S.; Yunusov, R.R.; Kurochkin, Y.V.; Lvovsky, A.; Fedorov, A. Quantum-secured blockchain. Quantum Sci. Technol. 2018, 3, 035004. [Google Scholar] [CrossRef] [Green Version]





| Properties | Challenges | Blockchain Solutions |
|---|---|---|
| Identity | Given an IoT data or process, we need to determine who the source of that data or process is. | Blockchain provides public keys that we can use as verifiable identities. |
| Non-repudiation | The origin of IoT data or processes should not deny that they generate such data or processes. | For the sender to store information in the blockchain, they must sign the data as transactions. |
| Tamper-proof | Attackers should not be able to modify the contents of IoT data or process logs maliciously. | Blockchain stages the data into a block data structure with the hash of the block chained to the previous block to produce a hard-to-tamper reference. |
| Fault-tolerant | The data management should be functional despite failures that may happen during its lifetime. | Blockchain network is fully distributed; therefore, it eliminates the single point of failure and increases the system’s robustness. |
| Confidentiality | The system requires having the capability to encrypt sensitive information from being leaked to the public. | Blockchain does not provide this ability. However, we can use the public keys that the blockchain has to provide secure encryption. |
| Privacy | We need to protect users’ privacy by protecting their private data when conducting massive data collections and processings. | The use of public keys in the blockchain renders pseudonymity and strengthens users’ privacy. |
| Trusted SLA | Trust issues hinder collaboration, and producing SLAs is lengthy and tedious task. | Using smart contracts, we can automate the trusted SLA generation process. |
| Project | Related to | Contributions to Our Design |
|---|---|---|
| Yakubov et al. [21] | Identity Management | We apply the proposed idea to extend X.509 certificate fields for our blockchain integration in a quasi-centralized approach. |
| SCPKI [19] | Identity Management | We use the presented WoT scheme to produce a certificate in our fully decentralized method. |
| Wilson and Ateniese [22] | Identity Management | We take the authors’ suggestions regarding the incentive mechanism for public key endorsements in our design. |
| CertCoin [23] | Domain Names, Identity Management | The authors introduce two-key management: online and offline key, which we tweak it to work with our smart contract. |
| Kalodner et al. [24] | Domain Names | We acknowledge the authors’ namespace business model recommendations for our future design. |
| BATM [25] | Reputation | We assume using the proposed reputation system in our design, which considers positive or negative reviews and their timestamp. |
| PADVA [26] | Secure Channel, Reputation | We apply the proposed TLS timestamping in our design, which makes use of client-random and server-random to prove that TLS handshakes are performed. |
| Notation | Description |
|---|---|
| X | The IoT entity, which can be an IoT device, gateway, service, or worker. They are defined as D, , S, and W, respectively. |
| The online public key of X entity. | |
| The online secret key of X entity. | |
| The online blockchain address of X entity. | |
| The offline public key of X entity. | |
| The offline secret key of X entity. | |
| The offline blockcahin address of X entity. | |
| The arbitrary domain name of X entity. | |
| The public IP address of X entity. | |
| A function to generate a signature using any asymmetric digital signature algorithm (e.g., ECDSA) from payload J using the secret key of X entity, . | |
| The generated signature output of the function. | |
| The certificate as proof of identity (e.g., X.509 certificate). | |
| The client-random or server-random parameter from TLS handshake. | |
| A function to verify whether the signature of J payload, , is produced using a secret key corresponding to public key. This function returns True or False. | |
| A concatenation between A data and B data. |
| Project | Related to | Contributions to Our Design |
|---|---|---|
| FIF-IoT [38] | Chain of signatures | The author provides a role model of a chain of signatures based on blockchain. |
| Proof of Existence [39] | Blockchain Receipt | A legacy blockchain receipt proposal acts as our inspiration. |
| ChainPoint [40] | Blockchain Receipt | It provides an example of a working blockchain anchoring technique using Merkle Root hash. |
| Xueping Liang et al. [41] | Blockchain Receipt | We apply the authors’ idea of using daemon to generate blockchain receipts. |
| Jay Kishigami et al. [42] | Data Sharing | The authors propose a licensing mechanism based on the blockchain that we can employ in our design to control IoT data distributions. |
| NuCypher KMS [43] | Data Sharing | We can use the proxy re-encryption technique that the authors propose to make our shared IoT data confidential. |
| Notation | Description |
|---|---|
| The IoT raw data from IoT devices. | |
| The aggregated IoT data after micro-processing in the IoT gateway. | |
| The IoT commands for IoT devices from the IoT service. | |
| The feedback from IoT devices in response to IoT commands. | |
| An identifier used to link the contents of a table in IoT gateways to the one in the IoT service. | |
| A hashing operation of p payload using any hash function (e.g., SHA-256 algorithm). | |
| h | The hash of a payload, the output of . |
| Y | A table in a database. |
| y | A sub-table, which is a segment of a table. |
| A particular row in a table. | |
| m | The threshold of the maximum number of new rows inserted in the table to trigger blockchain receipt generation. |
| n | The number of leaves as a parameter to construct the Merkle Root in the blockchain receipt. |
| Project | Related to | Contributions to Our Design |
|---|---|---|
| Sterling [49] | E-marketplace | This project shows us an example of a privacy-preserving blockchain-based marketplace for private data and machine learning model trading. |
| Wibson [54] | E-marketplace | We can use the notary system that the authors propose to be auditors and mediators between data sellers and data buyers in our marketplace. |
| CrowdSFL [51] | Federated Learning | We can employ the reward distribution mechanism and the El-Gamal re-encryption scheme in this proposal to our design. |
| Yang Zhao et al. [52] | Federated Learning | We borrow the idea of using MEC servers to alleviate some training burdens from IoT devices. |
| Dongxiao Liu et al. [55] | Reputation System | We endorse the use of the proposed reputation system, which provides an anonymous reputation system that is hard to trace to protect the reviewers’ privacy. |
| Jiawen Kang et al. [56] | Incentive Mechanism | We use the proposed incentive mechanism, which presents an incentive mechanism for mobile devices to encourage active participation in the federated learning process. |
| Notation | Description |
|---|---|
| The Mobile Edge Computing (MEC) servers. | |
| The Merkle Root hash of the IoT service dataset, which also acts as job identifier in our marketplace. | |
| A training proposal from IoT worker to IoT service. | |
| The training result from an IoT worker. | |
| The global model from an IoT service for federated learning. | |
| The IPFS hash of our global model, which serves as training process identifier in our federated learning. | |
| The updated local model from an IoT device. | |
| The IPFS hash of a local model from device a for epoch b. |
| No | Open Problems | Related to | Our Solutions |
|---|---|---|---|
| 1 | Users are reluctant to rely on conventional IoT big data systems because they do not provide reliable SLA. | Data in Process | We transform SLAs into smart contracts, and all users can safely assume that the execution of a smart contract is always deterministic; thus, it is trustable. |
| 2 | Users’ sensitive information needs to be secured and protected from external interferences. | Data in Transit Data at Rest Data in Process | Using a combination of a chain of signatures and blockchain receipt, we can easily detect if anyone has tampered with our database. Meanwhile, our blockchain-based secure channel can be used to provide secrecy during data transmissions. |
| 3 | The IoT system should assign a non-repudiable identification system to each of the IoT devices. | Data in Transit Data at Rest Data in Process | We design our identity system based on the public key mechanism, which provides a reliable non-repudiation guarantee. |
| 4 | Enterprises should maintain a metadata repository of the IoT devices for auditing purposes. | Data at Rest | The blockchain receipt can ensure the integrity of the metadata repository such that, when that metadata is shared with auditors, it still preserves the forensically sound guarantee. |
| 5 | The system may face difficulty in keeping IoT devices up to date. | Data in Process | The reputation system can force device owners to update their devices. For instance, we give weak ratings to outdated devices or have a policy that bans obsolete devices. |
| 6 | Administrators also need to identify suspicious traffic patterns for incident management. | Data in Transit | While malicious traffic detections require other technologies (e.g., machine learning algorithm), we can assist this process by ensuring TLS communication integrity. For example, we can prove that a particular TLS handshake indeed happened. |
| 7 | The system also needs to have interoperability and protocol convergence to achieve efficient collaboration. | Data in Transit Data at Rest Data in Process | In our design, the blockchain serves as a standardized integrity platform for participants to collaborate in a secure and trustable manner. |
| 8 | The IoT data training generates low accuracy during the training of the analytic model. | Data in Process | While the actual training accuracy depends on the dataset, the model, and the algorithm, our platform forces participants to train honestly to achieve the best accuracy. |
| 9 | We need to have a parallel computation of the IoT data to support a multi-source platform. | Data in Process | The distributed training through split learning and federated learning come to the rescue. Our platform provides a complementary procedure to protect the integrity of those learnings. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Oktian, Y.E.; Lee, S.-G.; Lee, B.-G. Blockchain-Based Continued Integrity Service for IoT Big Data Management: A Comprehensive Design. Electronics 2020, 9, 1434. https://doi.org/10.3390/electronics9091434
Oktian YE, Lee S-G, Lee B-G. Blockchain-Based Continued Integrity Service for IoT Big Data Management: A Comprehensive Design. Electronics. 2020; 9(9):1434. https://doi.org/10.3390/electronics9091434
Chicago/Turabian StyleOktian, Yustus Eko, Sang-Gon Lee, and Byung-Gook Lee. 2020. "Blockchain-Based Continued Integrity Service for IoT Big Data Management: A Comprehensive Design" Electronics 9, no. 9: 1434. https://doi.org/10.3390/electronics9091434
APA StyleOktian, Y. E., Lee, S.-G., & Lee, B.-G. (2020). Blockchain-Based Continued Integrity Service for IoT Big Data Management: A Comprehensive Design. Electronics, 9(9), 1434. https://doi.org/10.3390/electronics9091434





