Design and Implementation of an Anonymous and Secure Online Evaluation Protocol
Abstract
:1. Introduction
2. Related Work on Anonymous Evaluation Systems
3. Protocol Description
3.1. Desired Security Properties
- Eligibility: A student should be able to evaluate a university course if and only if: (a) The student belongs to the university, and (b) the student is enrolled in the specific course.
- Fairness: An evaluation is considered fair if and only if: only a student that has attended a minimum number of lectures for the specific course is able to evaluate the course.
- Privacy: An evaluation is considered private if and only if it provides the following properties: (a) Untraceability—A student’s evaluation of a specific course should not be traceable to the student’s identity. (b) Unlinkability—Evaluations of different courses should not be linkable.
- Unforgeability: An evaluation is considered unforgeable if and only if: (a) A student should not be able to use a credential issued for course i to evaluate course j, where or to participate more than once in a course evaluation. (b) A student should not be able to use one or more credentials issued for another honest student. (c) It should not be able for any system entity (students and/or system authorities) to modify an evaluation submitted by a student user. (d) It should not be able for a system authority to submit a fake evaluation on a specific course.
3.2. Phase A: Issuing Phase-Eligible Acceptance Ticket (EAT)
3.3. Phase B: Eligible Evaluation Ticket (EET)
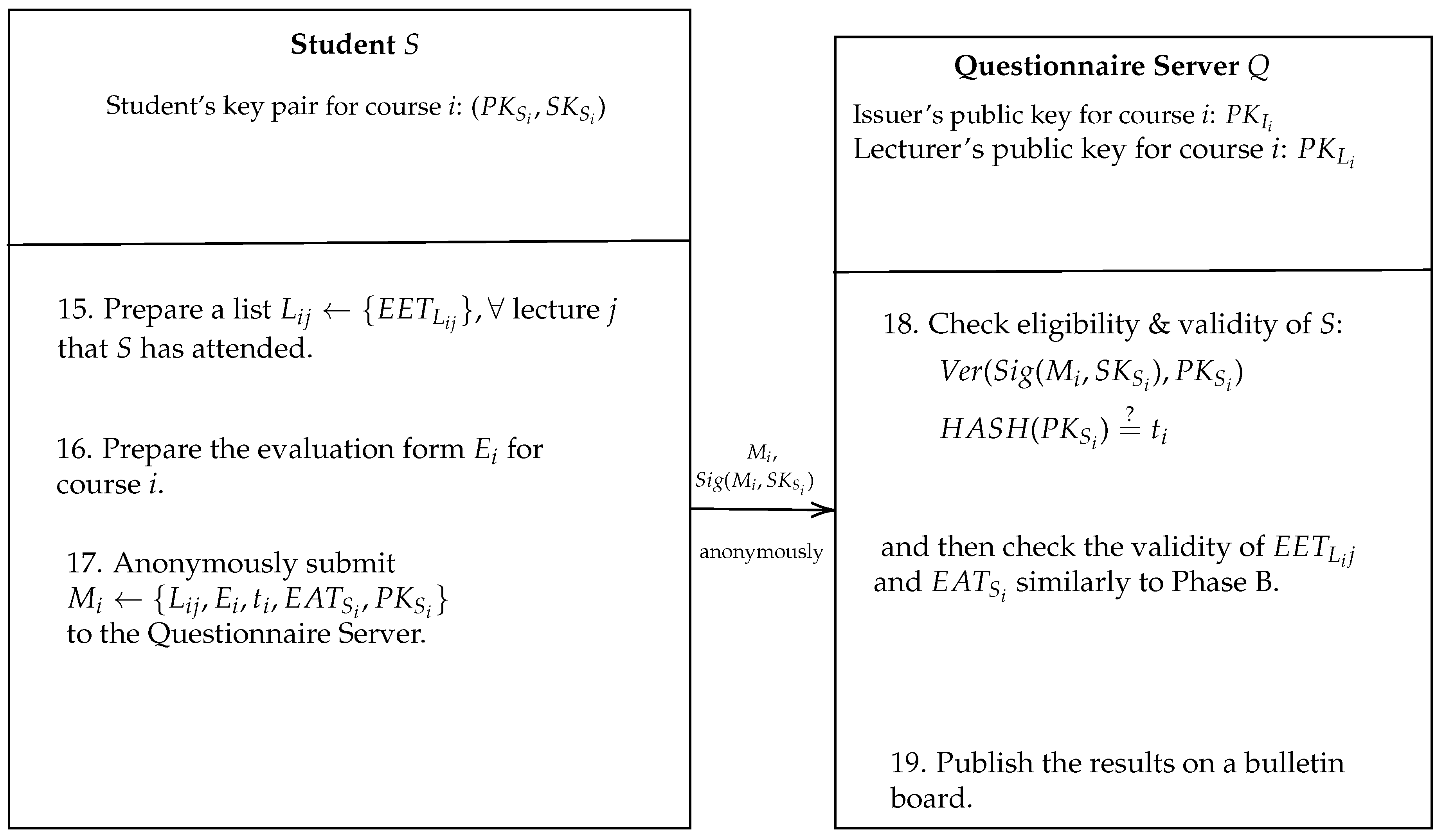
3.4. Phase C: Anonymous Evaluation
4. Security Analysis
4.1. Assumptions
4.2. Adversaries
4.3. Evaluator Eligibility
- Note 1:A collusion attack against the evaluation protocol. Recall that in our threat model (see Section 4.1) the evaluators (Students) are assumed to be colliding malicious entities. Therefore, Students are allowed to collide with other Students and/or external entities, to break the unforgeability property defined in Section 3.1 as follows: Imagine a malicious eligible Student A who hands over its evaluation credentials, i.e., the EAT ticket and key pairs for a given course i, to another malicious user B (a different Student or an external entity). Then B would be able to attend a specific course and/or submit a evaluation on behalf of A. In fact, this attack could scale, i.e., A could gather evaluation credentials for any number of Bs in order to attack the evaluation system.
4.4. Evaluator Privacy
4.5. Analysis with Proverif
4.5.1. Formal Modelling of the Protocol
4.5.2. Student Process
4.5.3. Issuer Process
4.5.4. Main Process
4.5.5. Results Analysis
- (* Injective Correspondance*)
- query x:bitstring, y:pkey; event(termStudent(x,y))==>event(acceptsIssuer(x,y)).
- query x:bitstring; inj-event(termIssuer(x))==>inj-event(acceptsStudent(x)).
- Process 0 (that is, the initial process):
5. System Evaluation
5.1. Implementation
5.2. System Evaluation Scenario
5.3. Performance
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Appendix A. Proverif Architecture

Appendix B. Basic Grammar of Proverif
| Term and Process Grammar | |
|---|---|
| M, N ::= | terms |
| a, b, c, k, m, n, … | names |
| x, y, z | variables |
| (M1, …, Mk) | tuple |
| h(M1, …, Mk) | constructor/destructor application |
| M = N | term equality |
| M <> N | term inequality |
| M && M | conjunction |
| M || M | disjunction |
| not(M) | negation |
| P, Q ::= | processes |
| 0 | null process |
| P | Q | parallel composition |
| !P | replication |
| new n : t; P | name restriction |
| in(M, x : t); P | message input |
| out(M, N); P | message output |
| if M then P else Q | conditional |
| let x = M in P else Q | term evaluation |
| R(M1, …, Mk) | macro usage |
References
- Li, C.; Lalani, F. The COVID-19 Pandemic Has Changed Education Forever. Available online: https://www.weforum.org/agenda/2020/04/coronavirus-education-global-covid19-online-digital-learning/ (accessed on 16 June 2020).
- Kluczniak, K.; Hanzlik, L.; Kubiak, P.; Kutyłowski, M. Anonymous evaluation system. In International Conference on Network and System Security; Springer: Berlin/Heidelberg, Germany, 2015; pp. 283–299. [Google Scholar]
- Baldimtsi, F.; Lysyanskaya, A. Anonymous credentials light. In Proceedings of the 2013 ACM SIGSAC conference on Computer & Communications Security, Berlin, Germany, 4–8 November 2013; pp. 1087–1098. [Google Scholar]
- Camenisch, J.; Lysyanskaya, A. A signature scheme with efficient protocols. In International Conference on Security in Communication Networks; Springer: Berlin/Heidelberg, Germany, 2002; pp. 268–289. [Google Scholar]
- Camenisch, J.; Lysyanskaya, A.; Meyerovich, M. Endorsed e-cash. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP’07), Berkeley, CA, USA, 20–23 May 2007. [Google Scholar]
- Camenisch, J.; Dubovitskaya, M.; Lehmann, A.; Neven, G.; Paquin, C.; Preiss, F.S. Concepts and languages for privacy-preserving attribute-based authentication. In IFIP Working Conference on Policies and Research in Identity Management; Springer: Berlin/Heidelberg, Germany, 2013; pp. 34–52. [Google Scholar]
- Bender, J.; Dagdelen, Ö.; Fischlin, M.; Kügler, D. Domain-specific pseudonymous signatures for the german identity card. In International Conference on Information Security; Springer: Berlin/Heidelberg, Germany, 2012; pp. 104–119. [Google Scholar]
- Cranor, L.F.; Cytron, R.K. Sensus: A security-conscious electronic polling system for the internet. In Proceedings of the Thirtieth Hawaii International Conference on System Sciences, Wailea, HI, USA, 7–10 January 1997. [Google Scholar]
- Fujioka, A.; Okamoto, T.; Ohta, K. A practical secret voting scheme for large scale elections. In International Workshop on the Theory and Application of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1992; pp. 244–251. [Google Scholar]
- Camenisch, J.; Van Herreweghen, E. Design and implementation of the idemix anonymous credential system. In Proceedings of the 9th ACM Conference on Computer and Communications Security; ACM: New York, NY, USA, 2002; pp. 21–30. [Google Scholar]
- Camenisch, J. Specification of the identity mixer cryptographic library. Tech. Rep. 2010, 76, 5–6. [Google Scholar]
- Paquin, C.; Zaverucha, G. U-prove Cryptographic Specification v1.1; Technical Report; Microsoft Corporation: Redmond, WA, USA, 2011. [Google Scholar]
- Benenson, Z.; Girard, A.; Krontiris, I.; Liagkou, V.; Rannenberg, K.; Stamatiou, Y. User acceptance of privacy-abcs: An exploratory study. In International Conference on Human Aspects of Information Security, Privacy, and Trust; Springer: Berlin/Heidelberg, Germany, 2014; pp. 375–386. [Google Scholar]
- Sabouri, A.; Rannenberg, K. Abc4trust: Protecting privacy in identity management by bringing privacy-abcs into real-life. In IFIP International Summer School on Privacy and Identity Management; Springer: Berlin/Heidelberg, Germany, 2014; pp. 3–16. [Google Scholar]
- Rannenberg, K.; Camenisch, J.; Sabouri, A. Attribute-based credentials for trust. In Identity in the Information Society; Springer: Berlin/Heidelberg, Germany, 2015. [Google Scholar]
- Krontiris, I.; Benenson, Z.; Girard, A.; Sabouri, A.; Rannenberg, K.; Schoo, P. Privacy-ABCs as a Case for Studying the Adoption of PETs by Users and Service Providers. In Annual Privacy Forum; Springer: Berlin/Heidelberg, Germany, 2015; pp. 104–123. [Google Scholar]
- Liagkou, V.; Stylios, C.; Petunin, A. Handling Privacy and Concurrency in an Online Educational Evaluation System. Balt. J. Mod. Comput. 2019, 7, 86–98. [Google Scholar] [CrossRef]
- Stamatiou, Y.; Benenson, Z.; Girard, A.; Krontiris, I.; Liagkou, V.; Pyrgelis, A.; Tesfay, W. Course evaluation in higher education: The patras pilot of ABC4Trust. In Attribute-Based Credentials for Trust; Springer: Cham, Swizerland, 2015; pp. 197–239. [Google Scholar]
- Schanzenbach, M.; Kilian, T.; Schütte, J.; Banse, C. Zklaims: Privacy-preserving attribute-based credentials using non-interactive zero-knowledge techniques. arXiv 2019, arXiv:1907.09579. [Google Scholar]
- Mostowski, W.; Vullers, P. Efficient u-prove implementation for anonymous credentials on smart cards. In International Conference on Security and Privacy in Communication Systems; Springer: Berlin/Heidelberg, Germany, 2011; pp. 243–260. [Google Scholar]
- Sene, I.; Ciss, A.A.; Niang, O. I2pa: An efficient abc for iot. Cryptography 2019, 3, 16. [Google Scholar] [CrossRef] [Green Version]
- Chaum, D.; Fiat, A.; Naor, M. Untraceable electronic cash. In Conference on the Theory and Application of Cryptography; Springer: Berlin/Heidelberg, Germany, 1988; pp. 319–327. [Google Scholar]
- Lamport, L. Password authentication with insecure communication. Commun. ACM 1981, 24, 770–772. [Google Scholar] [CrossRef]
- Kotzanikolaou, P.; Chatzisofroniou, G.; Burmester, M. Broadcast anonymous routing (BAR): Scalable real-time anonymous communication. Int. J. Inf. Secur. 2017, 16, 313–326. [Google Scholar] [CrossRef]
- Dierks, T.; Rescorla, E. The Transport Layer Security (TLS) Protocol Version 1.2. 2008. Available online: www.hjp.at/doc/rfc/rfc5246.html (accessed on 20 July 2020).
- Blanchet, B. Modeling and Verifying Security Protocols with the Applied pi Calculus and Proverif. 2016. Available online: https://hal.inria.fr/hal-01423760/ (accessed on 22 April 2020).
- Das, P.; Faust, S.; Loss, J. A formal treatment of deterministic wallets. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security; ACM: New York, NY, USA, 2019; pp. 651–668. [Google Scholar]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- GitHub Development Platform. Available online: https://github.com/sophron/BAR (accessed on 27 February 2020).
- Cremers, C.J. The Scyther Tool: Verification, falsification, and analysis of security protocols. In International Conference on Computer Aided Verification; Springer: Berlin/Heidelberg, Germany, 2008; pp. 414–418. [Google Scholar]
- Doghmi, S.F.; Guttman, J.D.; Thayer, F.J. Searching for shapes in cryptographic protocols. In International Conference on Tools and Algorithms for the Construction and Analysis of Systems; Springer: Berlin/Heidelberg, Germany, 2007; pp. 523–537. [Google Scholar]
- Comon-Lundh, H.; Delaune, S. The finite variant property: How to get rid of some algebraic properties. In International Conference on Rewriting Techniques and Applications; Springer: Berlin/Heidelberg, Germany, 2005; pp. 294–307. [Google Scholar]









| No. of Students | Phase A | Phase B | Phase C | Total Exec. Time |
|---|---|---|---|---|
| 100 | 365 | 737 | 1174 | 2276 |
| 200 | 401 | 810 | 1521 | 2732 |
| 300 | 693 | 1401 | 2741 | 4835 |
| 400 | 800 | 1881 | 2926 | 5607 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Petrakos, N.; Monachos, S.; Magkos, E.; Kotzanikolaou, P. Design and Implementation of an Anonymous and Secure Online Evaluation Protocol. Electronics 2020, 9, 1415. https://doi.org/10.3390/electronics9091415
Petrakos N, Monachos S, Magkos E, Kotzanikolaou P. Design and Implementation of an Anonymous and Secure Online Evaluation Protocol. Electronics. 2020; 9(9):1415. https://doi.org/10.3390/electronics9091415
Chicago/Turabian StylePetrakos, Nikolaos, Stefanos Monachos, Emmanouil Magkos, and Panayiotis Kotzanikolaou. 2020. "Design and Implementation of an Anonymous and Secure Online Evaluation Protocol" Electronics 9, no. 9: 1415. https://doi.org/10.3390/electronics9091415
APA StylePetrakos, N., Monachos, S., Magkos, E., & Kotzanikolaou, P. (2020). Design and Implementation of an Anonymous and Secure Online Evaluation Protocol. Electronics, 9(9), 1415. https://doi.org/10.3390/electronics9091415







