Attack Analysis Framework for Cyber-Attack and Defense Test Platform
Abstract
:1. Introduction
2. Related Work
3. Attack Analysis Framework
3.1. Cyber Security Knowledge Graph Construction
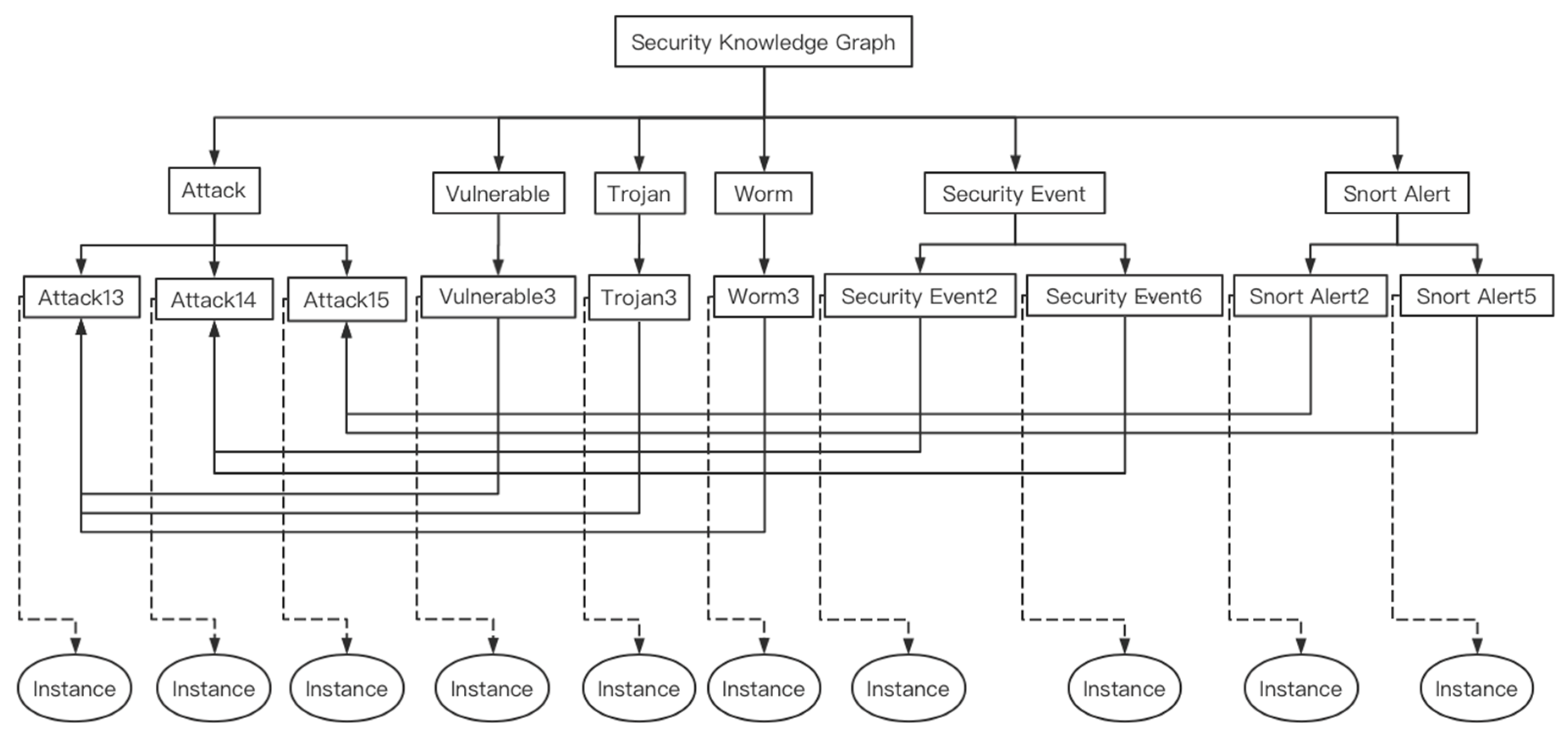
3.1.1. Security Knowledge Graph
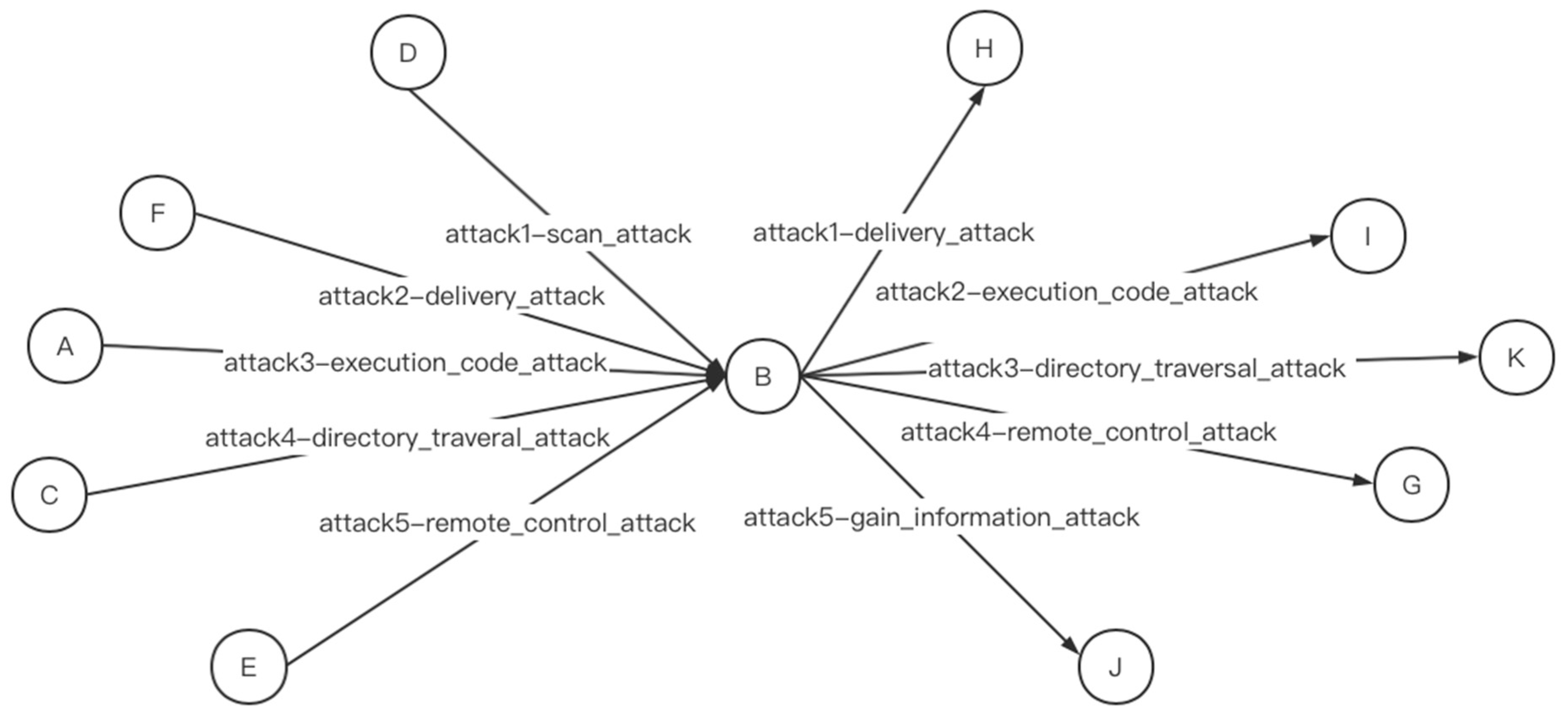
Security Knowledge Ontology Model
Ontology-Instance Data Model
- ①
- 1:1 data model
- ②
- n:1 data model
- ③
- 1:n data model
Self-Defined Reasoning Rules
- (1)
- Fixed reasoning rules
- (2)
- Specific reasoning rules
Named Entity Recognition Based on CRF
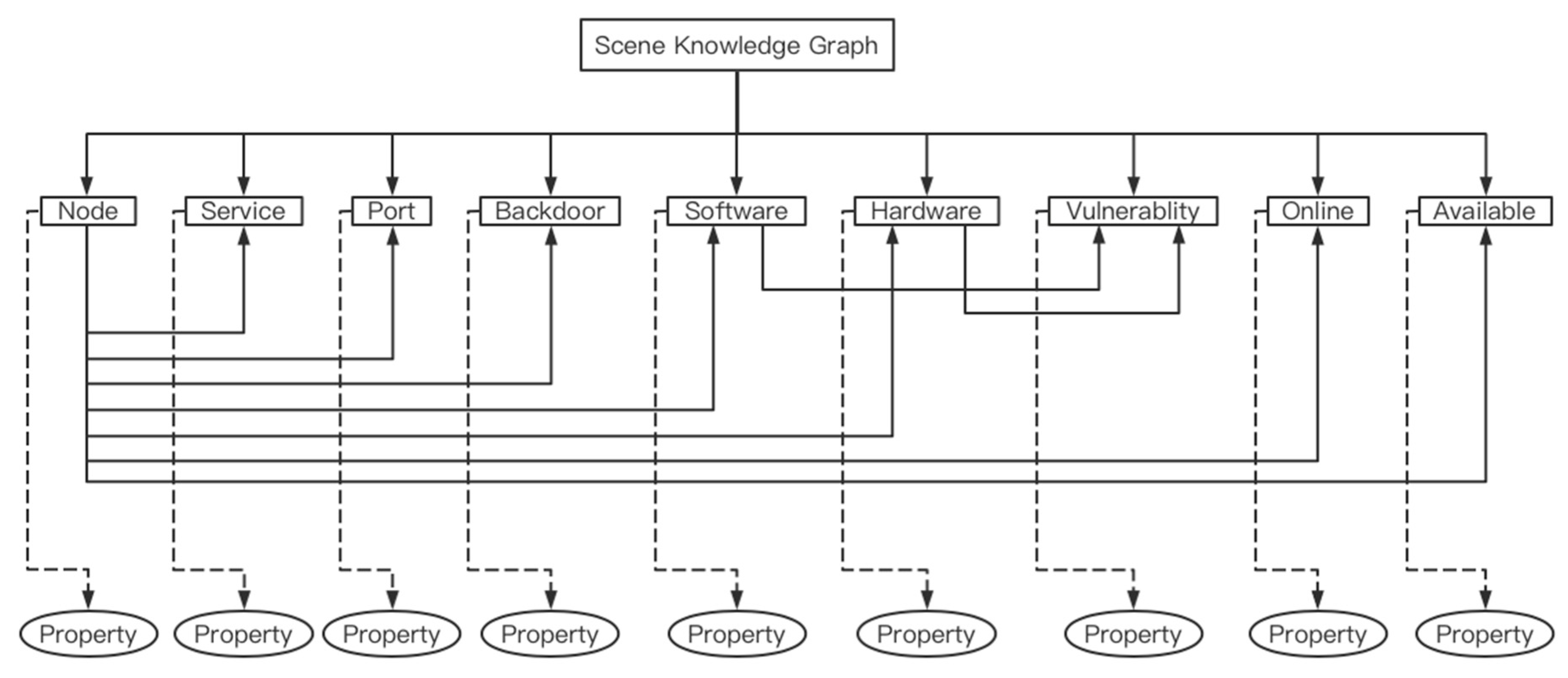
3.1.2. Scene Knowledge Graph
3.2. Threat Element Association Statistics
3.2.1. Set Frequency Threshold
3.2.2. Set Number Threshold
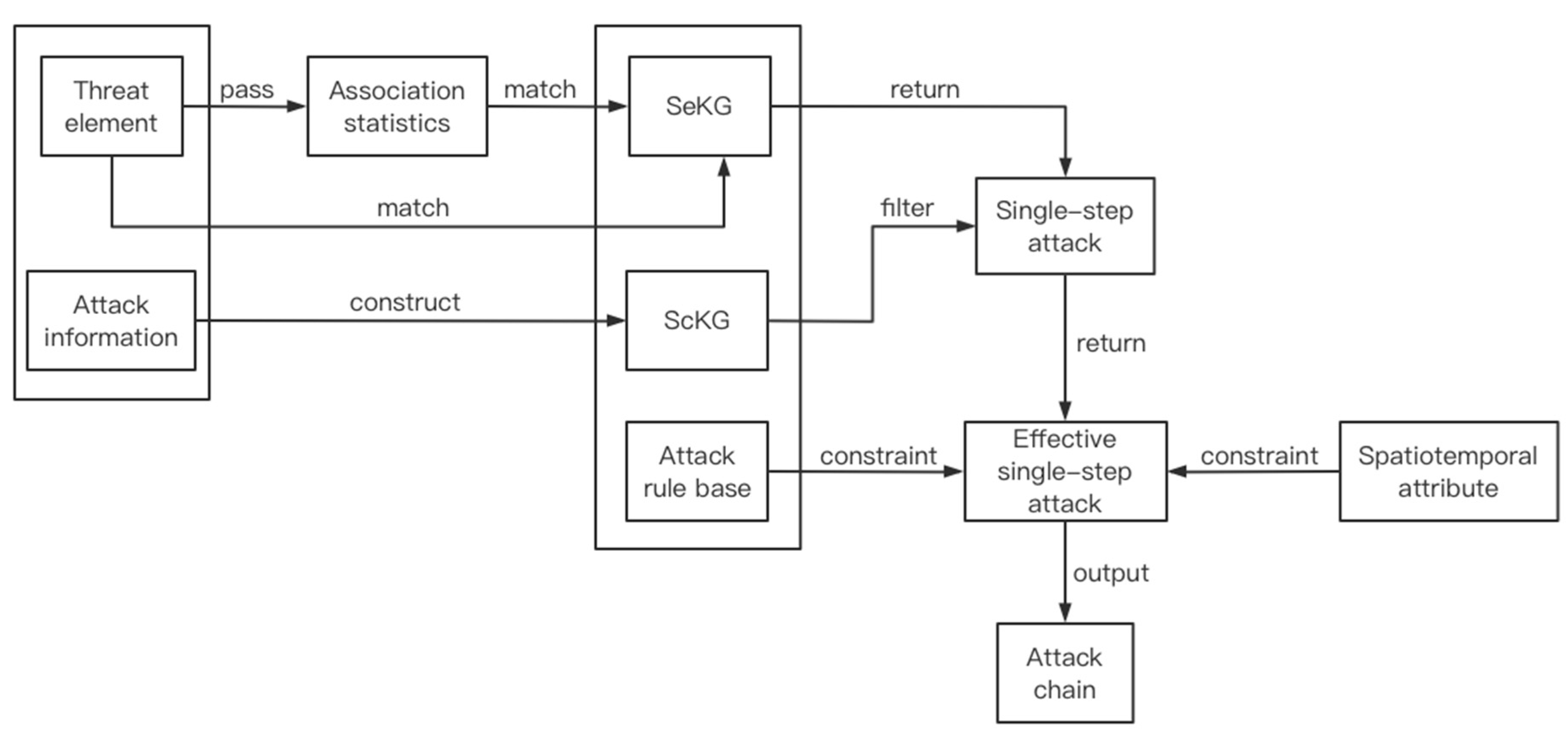
3.3. Attack Analysis and Judgment Based on Association Analysis
3.3.1. Attack Rule Base
3.3.2. Spatiotemporal Constraints
- ①
- set the analysis time window and offset on the Spark framework, and respectively set the alert base and security event base that need to be associated statistically;
- ②
- in a time window, after data fusion and threat element extraction, the input data is first matched with the alert base and security event base set in the first step. If the matching fails, it can be directly matched with the security knowledge graph. If the match is successful, then it is matched with the security knowledge graph after statistical association;
- ③
- the result returned in the previous step is for single-step attacks after using the scene knowledge graph to filter out invalid attacks;
- ④
- match effective single-step attacks with attack rule bases, while constraining time and IP propagation;
- ⑤
- after the analysis of the input data within a time window is completed, the analysis results are cached and output as intermediate results. With the offset of the time window, the results of each analysis are iteratively output. When the attack ends, the complete attack chain will be output. Intermediate results and final results are output in the form of an attack chain. A schematic of the attack chain generation is shown in Figure 16.
3.3.3. Evaluation Mechanism
4. Test and Result Analysis
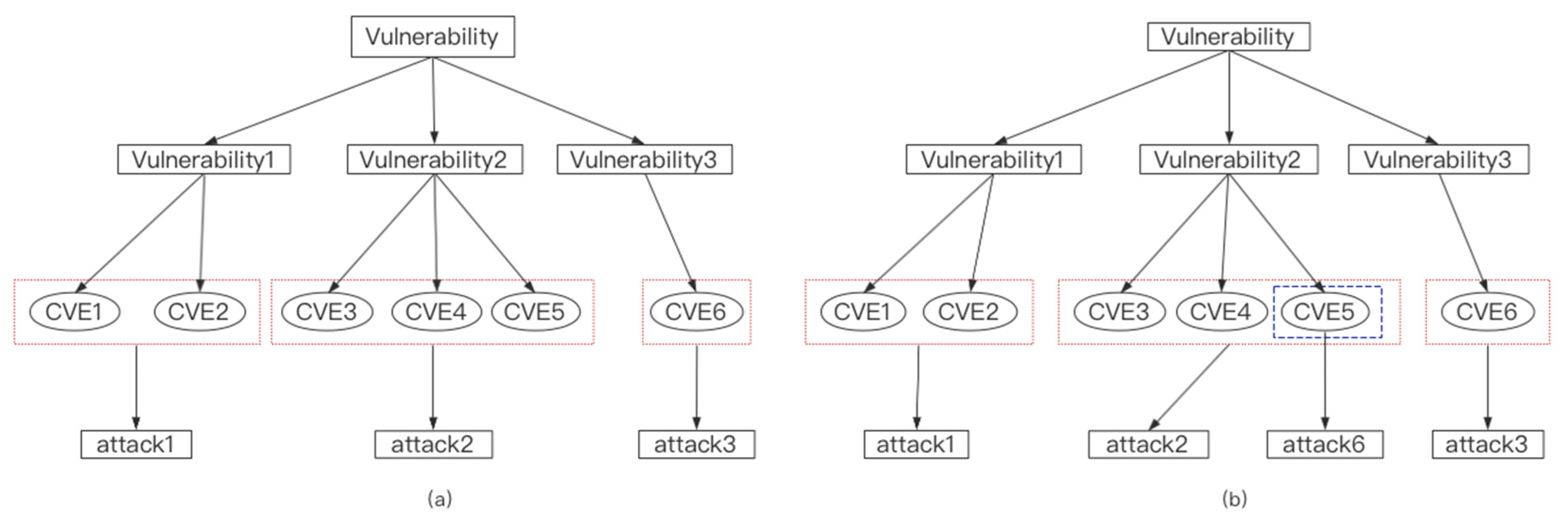
4.1. Verify the Validity of Self-Defined Reasoning Rules
4.2. Verify the Feasibility of the Analysis Framework
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Liu, Q.; LI, Y.; Duan, H. Overview of Knowledge Mapping Technology. J. Comp. Res. Dev. 2016, 3, 582–600. [Google Scholar]
- Zhang, X.; Jiang, L. Overview of Ontology concept Research. Chin. J. Inf. Technol. 2002, 26, 527–531. [Google Scholar]
- Qiu, B. Research on Knowledge Modeling for Domain Ontology; Shandong Normal University: Jinan, China, 2009. [Google Scholar]
- Gómez-Pérez, A.; Benjamins, R. Overview of knowledge sharing and reuse components: Ontologies and problem-solving methods. IJCAI and the Scandinavian AI Societies. In Proceedings of the CEUR Workshop Proceedings, Stockholm, Sweden, 31 July 1999. [Google Scholar]
- Guarino, N. Semantic matching: Formal ontological distinctions for information organization, extraction, and integration. In International Summer School on Information Extraction; Springer: Berlin/Heidelberg, Germany, 1997. [Google Scholar]
- Wang, T.; Ai, Z.; Zhang, X. Knowledge Graph Construction of Threat Intelligence Based on Deep Learning. Comput. Mod. 2018, 280, 25–30. [Google Scholar]
- Tao, Y.; Huang, T.; Li, M. Research on Network Security Level Protection Log Audit Analysis Model Driven by Knowledge Graph. Net. Secur. 2020, 20, 46–51. [Google Scholar]
- Wang, W.; Jiang, R.; Jia, Y. KGBIAC: Knowledge Graph Based Intelligent Alert Correlation Framework. In International Symposium on Cyberspace Safety and Security; Springer: Cham, Switzerland, 2017; pp. 523–530. [Google Scholar]
- Yan, A.K.; Guo, Y.B.; Zhu, T.M. Research on Network Security Incident Correlation Analysis Technology and Tools. Comput. Sci. 2017, 2, 38–45. [Google Scholar]
- Mastani, S.A. Reduced Merge_FSM Pattern Matching Algorithm for Network Intrusion Detection. Int. J. Recent Trends Eng. Technol. 2014, 10, 117. [Google Scholar]
- Forgy, C.L. Rete: A fast algorithm for the many pattern/many object pattern match problem. In Readings in Artificial Intelligence and Databases; Morgan Kaufmann: Burlington, MA, USA, 1989; pp. 547–559. [Google Scholar]
- Gu, X.D.; Gao, Y. Rete algorithm: Current issues and future Challenge. Comput. Sci. 2012, 39, 8–12. [Google Scholar]
- Esmaili, M.; Balachandran, B.; Safavi-Naini, R. Case-based reasoning for intrusion detection. In Proceedings of the 12th Annual Computer Security Applications Conference, San Diego, CA, USA, 9–13 December 1996; IEEE: Piscataway, NJ, USA, 1996; pp. 214–223. [Google Scholar]
- Bo, C.; Ling, Y.U.; Jun-Mo, X. An Application of Simulated Annealing Algorithm in Model-Based Reasoning Intrusion Detection. J. Univ. Electron. Sci. Technol. China 2005, 34, 36–39. [Google Scholar]
- Rubin, D.E.; Mital, V.; Beckman, B.C. Dependency Graph in Data-Driven Model. U.S. Patent 8,352,397, 8 January 2013. [Google Scholar]
- Hansen, S.E.; Atkins, E.T. Automated System Monitoring and Notification with Swatch. In Proceedings of the LISA 93, Monterey, CA, USA, 1–5 November 1993; pp. 145–152. [Google Scholar]
- Rouillard, J.P. Real-time Log File Analysis Using the Simple Event Correlator (SEC). In Proceedings of the LISA, Atlanta, GA, USA, 14–19 November 2004; pp. 133–150. [Google Scholar]
- Cid, D.B. Log Analysis Using OSSEC. 2007. Available online: http://www.academia.edu/8343225/Log_Analysis_using_OSSEC (accessed on 15 August 2020).
- Nguyen, G.; Fischer, M.; Strufe, T. Ossim: A generic simulation framework for overlay streaming. In Proceedings of the 2013 Summer Computer Simulation Conference, Toronto, ON, Canada, 7–10 July 2013; Society for Modeling & Simulation International: Vista, CA, USA, 2013; p. 30. [Google Scholar]
- Proctor, M. Drools: A rule engine for complex event processing. In Proceedings of the 4th International Conference on Applications of Graph Transformations with Industrial Relevance, Budapest, Hungary, 4–7 October 2011; Springer: Berlin/Heidelberg, Germany, 2011; p. 2. [Google Scholar]
- EsperTech. Esper Website. Available online: http://www.espertech.com (accessed on 15 August 2020).
- Ning, P.; Cui, Y.; Reeves, D. Constructing Attack Scenarios through Correlation of Intrusion Alert; North Carolina State University at Raleigh: Raleigh, NC, USA, 2002. [Google Scholar]
- Zhang, J.; Li, X.; Wang, H. Real-time alert correlation approach based on attack planning graph. J. Comput. Appl. 2016, 6, 1538–1543. [Google Scholar]
- Jia, Y.; Qi, Y.; Shang, H.; Jiang, R.; Li, A. A Practical Approach to Constructing a Knowledge Graph for Cybersecurity. Engineering 2018, 4, 53–60. [Google Scholar] [CrossRef]
- Qi, L.I.; Xin, Z.; Pingkang, Z. Improved CFSFDP Algorithm Based on Spark Framework. Electron. Sci. Technol. 2019. [Google Scholar]












| rule: (?m NamedIndividualof ?n), (?p NamedIndividualof ?q), (?n r1 ?q) -> (?m r1?p) |
| rule: (?m NamedIndividualof ?n), (?p NamedIndividualof ?q), (?n r2 ?q) -> (?m r2?p) |
| [rule1: (?m NamedIndividualof ?n), (?p NamedIndividualof ?q), (?n r2 ?q) -> (?m r2?p)] [rule2: (?l equal ?m), (?m r2 ?p) -> (?l r2 ?p)] |
| [rule1: (?m NamedIndividualof ?n), (?p NamedIndividualof ?q), (?n r2 ?q) -> (?m r2?p)] [rule2: (?l SameCategory ?m),(?m r2 ?p) -> (?l r2 ?p)] |
| Simulated Attacks Are All Successful | Simulated Attacks Are Partially Successful | |
|---|---|---|
| Detection Results are All Correct | 100% | 100% |
| Detection Results are Partially Correct | <100% | <100% |
| F1 | F2 | F3 | F4 | F5 | F6 | R | |
|---|---|---|---|---|---|---|---|
| Original SKG | 3 | 24 | 24 | 0 | 3 | 2 | 66.7% |
| Expanded SKG | 3 | 26 | 26 | 0 | 3 | 3 | 100% |
| Simulated Attacks Are All Successful | Simulated Attacks Are Partially Successful | |
|---|---|---|
| Detection Results are All Correct | 100% | 100% |
| Detection Results are Partially Correct | 66.7% | 33.4% |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Qi, Y.; Jiang, R.; Jia, Y.; Li, A. Attack Analysis Framework for Cyber-Attack and Defense Test Platform. Electronics 2020, 9, 1413. https://doi.org/10.3390/electronics9091413
Qi Y, Jiang R, Jia Y, Li A. Attack Analysis Framework for Cyber-Attack and Defense Test Platform. Electronics. 2020; 9(9):1413. https://doi.org/10.3390/electronics9091413
Chicago/Turabian StyleQi, Yulu, Rong Jiang, Yan Jia, and Aiping Li. 2020. "Attack Analysis Framework for Cyber-Attack and Defense Test Platform" Electronics 9, no. 9: 1413. https://doi.org/10.3390/electronics9091413
APA StyleQi, Y., Jiang, R., Jia, Y., & Li, A. (2020). Attack Analysis Framework for Cyber-Attack and Defense Test Platform. Electronics, 9(9), 1413. https://doi.org/10.3390/electronics9091413





