1. Introduction
With the development of wireless sensor networks, the emergent Internet of Things (IoT) uses machines and networks to provide people with convenient services, such as health monitoring, environmental testing, smart appliances and so on. These services have created a new demand for wireless networks, so the improvement of performance of IoT systems has become an interesting topic of research. Long Range (LoRa) is a physical layer technology of Semtech [
1,
2], which has received widespread attention in recent years, mainly because of its long-range communication coverage and low-power requirements as well as the availability of modulation/demodulation hardware [
3].
Similar to the medium access control (MAC) layer protocol of LoRa, Long Range Wide Area Network (LoRaWAN) is an emerging low-complexity protocol for wireless communication in the unlicensed spectrum using LoRa modulation [
4,
5]. It is also considered to be one of the most promising wireless technologies for IoT because of the low complexity, the low power consumption equipment, and its open business model [
6,
7]. LoRaWAN specifications propose interesting solutions regarding MAC layer operations to deliver the best communication performance to connected things despite its crucial impact on the overall performance. Nevertheless, the LoRaWAN MAC layer has not been sufficiently considered by research studies [
8,
9]. Currently, the most widely used protocols in the LoRaWAN MAC layer are ALOHA and carrier sense multiple access (CSMA) [
10]. Compared with traditional ALOHA, a data collision avoidance algorithm (CD-ALOHA) which increases system throughput was proposed in [
11]. However, the CD-ALOHA algorithm cannot adjust the transmission probability of nodes according to different channel states, and will result in weak robustness of the system. Due to its distributed nature and inherent flexibility, the CSMA-type protocol has been the basis of many MAC communication standards that are based on random access. With the help of carrier sensing, they can provide variable packet length and significantly outperform the pioneering ALOHA-type protocols [
12]. In [
13], investigation has been indicated a carrier sense mechanism can be adapted to decrease collisions in LoRa transmissions. Additionally, a CSMA protocol has been proposed, which is capable of handling both short and long messages, as well as being adapted to LoRa networks. Further, by adapting the throughput and power consumption needs of each link, a new CSMA scheme that combines both throughput optimality and energy efficiency has been studied in [
14]. In [
15], the cooperative control feedback scheme has been examined to help senders discern false collision, which is caused by the rendezvous desynchronization problem whilst avoiding back-off misbehavior.
According to the control strategy, the CSMA protocols can be divided into non-persistent CSMA, 1-persistent CSMA, and p-persistent CSMA [
16]. Recently, some studies mainly focused on the evaluation of the p-persistent CSMA to evaluate the scalability of LoRaWAN and improve the packet reception ratio [
17,
18]. In [
17], a novel protocol called p persistent-channel activity recognition multiple access (p-CARMA) was presented to improve the scalability of LoRaWAN by manifolds, which can serve thousands of devices per gateway. In [
18], the persistent-carrier sense multiple access (p-CSMA) MAC protocol was exploited to increase the packet reception rate when sending uplink messages. Nevertheless, it is worth noting that since the value of p is low, there are many terminal devices that delay transmission may result in insufficient channel utilization. The authors investigated the use of adaptive p-persistent CSMA scheme for long term evolution in unlicensed (LTE-U) bands in [
19], however, only specific traffic and load condition was considered, which is unable to provide a flexible trade-off between the system overall throughput performance and the network offered traffic or the channel load when the deployment varies. Although the accessing unlicensed band probability of LTE-U is dynamically changed with the interference measurements, the system’s anti-interference capability still needs to be improved. To begin with, the p-persistent CSMA (from the standpoint of maximum throughput) can be regarded as the boundary closely approximated by the performance of many CSMA-type protocols, if the p-value is selected to guarantee that the same average back-off interval is used. Then, because of its memoryless nature, it is analytically tractable. Furthermore, because the p-persistent CSMA simply allows the user to begin a packet transmission with a common probability p, whenever this user has sensed idle channels, it is well suited for implementation. The stable region of such a system with N users has been investigated in [
20], where it has been shown that the necessary and sufficient condition of the system stability, in terms of the existence of queue stabilizing, is a transmission probability. It is assumed that N users have their own arrival rate and transmission probability, and the system has non-zero sensing times. However, this system uses a fixed probability to transmit data packets, which will make the system channel utilization insufficient with changing load. Another case that has been considered in [
21] is a multiple access system with multiple-packet reception capability that formulates the generalized p-persistent CSMA as a parameterized Markov decision process, in which the characteristics of such CSMA are modeled and transmission probabilities are designed to achieve maximum throughput. However, it has been proved that there are scalability problems in distributed wireless networks. A new collision-free hybrid medium access control protocol is proposed in [
22] for distributed multi-channel networks, which uses time division multiple access (TDMA) technique to avoid the collision at cost of additional delay. Since the LoRaWAN MAC layer does not provide a listen-before-talk (LBT) mechanism, a custom MAC layer was proposed in [
23] with LBT-based CSMA for collision avoidance. Although it has a satisfying performance in small sensor networks, it is not capable of extending to large networks. As explained in [
24], LoRa has unavoidably experienced too many collisions that significantly reduce the average throughput and increase time delay in large-scale IoT environments. The throughput and delay performance determine whether an IoT system can be effectively applied in practice. Therefore, it is necessary to improve the throughput and reduce the delay of conventional LoRa MAC layer.
In this paper, we propose an adaptive p-persistent CD/CSMA MAC layer protocol algorithm for improving the performance of the LoRa protocol. Then, we set different levels of the network offered traffic and divide the channel load into four states in the LoRa module to further maximize the overall throughput and improve the robustness of the system. According to the load size, the value of p will be dynamically adjusted to reduce the load of the network in each condition. Compared with some existing p-persistent CSMA based schemes, the code division multiple access (CDMA) technology is introduced into the adaptive p-persistent scheme. Further, the orthogonal spread spectrum code is embedded to realize CDMA transmission for enhancing the system’s anti-interference capability. Ultimately, we use OPNET to construct LoRa nodes and build a network topology that simulates actual conditions for simulation experiments. The simulation results verify that the proposed adaptive p-persistent CD/CSMA protocol has better performance than the traditional adaptive p-persistent scheme without CDMA protocol under the same conditions and can further reduce channel collision rate.
The rest of the paper is organized as follows.
Section 2 describes the conventional p-persistent CSMA protocol. In
Section 3, we elaborate the proposed adaptive p-persistent CD/CSMA protocol.
Section 4 involves the simulation model design and the results. Finally, the conclusions are presented in
Section 5.
2. Conventional p-Persistent CSMA Protocol
Some of the related terms and the time structure of the p-persistent CSMA are shown in
Figure 1. Time is slotted in the p-persistent CSMA protocol. The size of the slot is
a which is the normalized propagation delay, and all transmissions start at the beginning of each time slot with a packet length equal to
t. It is always assumed that the length of each transmission period (TP) is
T, i.e., if the secondary station (STA) sends packets at time
, all the other STAs should wait until
(where
a is the propagation delay as mentioned previously). When an STA sends a packet, it first senses the channel and then checks it. If the channel is busy, STA insists on sensing the next slot. If the channel is idle, STA sends data with probability
p and is delayed for the next slot with probability
. This process will loop until the data packet is sent out. Since the transmission is deferred with probability
even the channel is detected idle, there exists a silent period between two TPs which is called initial random transmission delay (IRTD) [
25,
26].
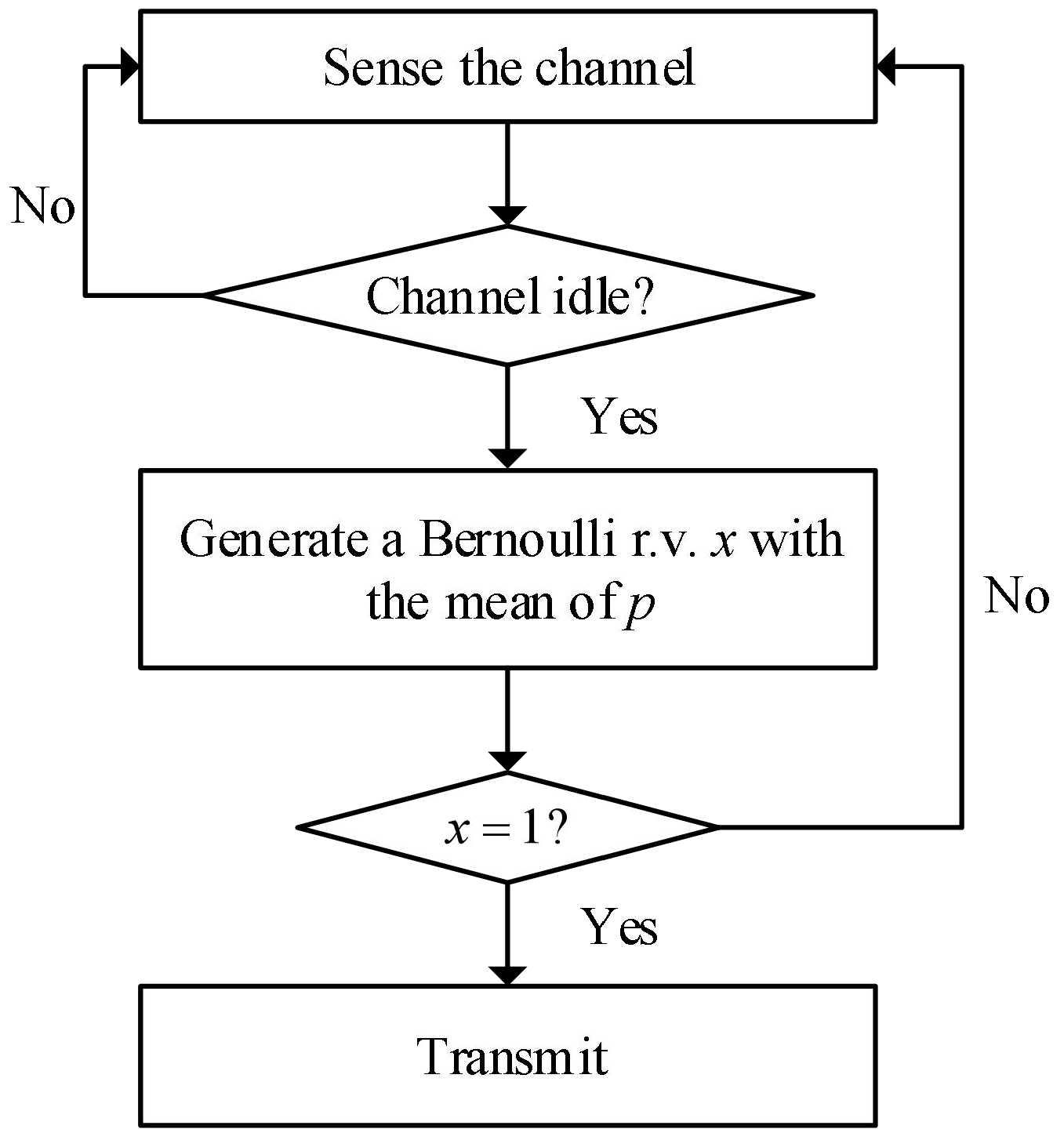
Figure 2 shows the conventional p-persistent CSMA algorithm that uses a time slot media access control method [
19]. When the node detects that the channel is idle, it will generate a Bernoulli random variable
x with the mean of
p. When
, the node will start sending packets.
All packets from all STAs are modelled as a single Poisson process, providing a load
G for mathematical simplicity [
27]. The system throughput is defined as the number of successful transmitted bits per unit time by using probabilistic analysis and renewal theory and is presented by Equation (
1) below:
where
is the duration of the IRTD before the first TP,
is the duration of the IRTD before other TPs and
is the probability that no packet arrives during a TP.
represents the average throughput over the channel fading statistics which is given by the following equation:
where
is the ergodic capacity of a single transmission and
is given by
represents the probability of transmitting a data packet without any collision in the presence of
n STAs successfully. It can be expressed as
The above formulas indicate that the selection of the probability p should be based on the load G so that we can obtain the optimal system throughput. Generally, it is suitable to choose a large p value when the traffic is low; on the contrary, a small p should be selected. However, once p is selected, it is difficult to change, if it does not match the traffic, there will be channel collision, high delay, or low channel utilization.
3. Proposed Adaptive p-Persistent CD/CSMA Protocol
According to the different load status of the channel, the conventional p-persistent CSMA protocols mentioned above are not able to properly select the transmission probability p and are also limited owing to utilizing single channel communication. When the channel load is heavy, a series of challenging problems are encountered in practice, such as channel conflicts problem. Therefore, to solve the heavy load problem, we propose an adaptive p-persistent CD/CSMA protocol, in which the CDMA protocol is introduced to further improve the system throughput.
3.1. CDMA Protocol
The core of the CDMA protocol is spread spectrum, i.e., modulation with a pseudo-random code sequence whose bandwidth is much larger than the signal bandwidth, so that the bandwidth of the original signal is expanded and then modulated by the carrier and transmitted [
28]. The CDMA spread spectrum model is shown in
Figure 3. The signal
is encoded by an encoder to become signal
, and then modulated with a spreading code through spread spectrum modulation. RF modulation is performed with a carrier signal
. The signal received by the receiver is given by the following equation:
where
is the sum of all kinds of noise. The receiver uses the coherent carrier to demodulate the composite signal as given in Equation (
6):
After multiplying by to complete the despreading process, baseband filtering and decoding are performed to obtain the information from the transmitter.
In order to improve performance, the most important problem is how to choose the spread spectrum code. The terminal hardware battery is small and cannot be replaced, which results in the inability to install chips with strong computing power. Hence, if the spread spectrum code order is too large, it may cause terminal overload. By contrast, if the order of spread spectrum code is too small and the total amount of users is larger than the total amount of orthogonal spread code, a large number of users will share a certain spread spectrum code. In this case, the purpose of distinguishing users by the code cannot be achieved. Thus, we will choose the appropriate spread spectrum code order using theoretical analysis.
If a node sends a packet successfully at time
, during the
time from
to
, there is no node that uses the same spread spectrum code to send data. If there are terminals transmitting signals at the same time in
time, the probability that the
i-th terminal and the other
terminals do not use the same spread spectrum code is given by [
11]
where
M is the order of the selected orthogonal spreading code.
During this
time, the probability of
k terminals transmitting simultaneously is
where
G is the channel load. Then, the data frames sent successfully are equal to
The average number of retransmissions for a data frame is given by
Additionally, the normalized average delay is
where
m is the
m-th spreading code.
LoRa is a modulation technology in which the secondary spread spectrum mechanism is formed by embedding CDMA into a LoRa node again. In this paper, the LoRa spread spectrum mechanism is used directly and exploits the six original spread spectrum factors. The optional order of the spreading code M is generally between 1 and 16. With increasing M, the transmission distance will increase, and then the data transmission rate will be decreased. Therefore, in order to balance the system data transmission rate and guarantee enough transmission distance between nodes, the order of the spreading code is set to .
3.2. Adaptive p-Persistent CSMA Protocol
In the theoretical model, we assume that the system contains
n nodes, which continuously send packets and compete for a link at the same time, so the channel will be busy. Besides, the data frames of all end nodes are sent at the same rate. Finally, the link is an ideal channel without other unrelated signals and noise interference. Assuming that a stable network has
n end nodes and the transmission probability of an end node is
, the probability of collision
can be expressed as
Then, the probability of at least one terminal being sent within the observed slot is
Furthermore, the probability that one of the nodes will successfully send is
Equations (10)–(14) show that the number of end nodes n and their transmission probability will affect the collision probability and transmission success probability . The propagation delay can be significantly optimized by reducing the number of channel transmission collisions and collision probability.
The contention window model of different end nodes can be expressed as
The throughput of the
-th end node can be calculated as in Equation (
16),
The normalized throughput of the system is given by
where
represents the average payload successfully received by the receiver in a time slot, and
is the length of the transmission time slot.
P is the payload information sent in a time slot and
is the average value of
P. In addition,
is the average time for data to successfully reach the destination node,
is the time of experiencing a collision in the process of data transmission, and
is the length of the free time slot. Because the effective data frame length is the same, the system throughput is inversely proportional to the length of idle time slot. The total throughput of all stations can be calculated as
The channel load is predicated on the premise of the advantages of CSMA being preserved. When the network is at the light load state, the traditional protocol is used to minimize the delay of media access. When the network is overloaded, the probability of sending data is reduced owing to the increase in the number of conflicts.
Table 1 shows the differences of the proposed p-persistent CD/CSMA protocol and some existing protocols.
Figure 4 shows the flow chart of proposed adaptive p-persistent CD/CSMA protocol that is used to resolve channel conflicts. The system first monitors the channel before sending the data frame because it is necessary to assess the channel state and set the random transmission probability
. The network load is divided into the following four cases based on the collection and analysis of the above network state parameters, i.e., the light load, the moderate load, the heavier load, and the heaviest load. When the current transmission back-off times are
, the system is at the light load and we let
. When
and the number of last transmission back-off is
, the system is at the moderate load and we let
. When
, the system is at the heavier load and
. If the current transmission back-off times are
and
, the current channel state is at the heaviest load and
. According to the different load conditions, we can dynamically adjust the
value. Additionally, with the load of channel increasing, the number of transmission data conflicts
R increases whereas the transmission probability
will decrease. Therefore, the near-optimal
value can be ascertained by simulation. Finally, if the channel data are not transmitted successfully, the system will enter a new waiting state.
4. Simulation Results
In this section, to evaluate the effectiveness and scalability of the proposed p-persistent CD/CSMA protocol, the simulation experiments were conducted by using the OPNET Modeler14.5 and NS-3. When building the network topology structure, it was assumed that all of the nodes were distributed in a square area, and the sink node was located at the center of the area. Then the node layer and MAC layer model were deployed in detail. After a brief description of the deployment scenario, simulation results are presented and discussed in detail.
In the simulations, each channel of the LoRa network had a bandwidth of 125 kHz. We set the packet inter-arrival time (i.e., traffic) parameters for the experiment, which were Poisson (60), Poisson (30), Poisson (10), Poisson (5), and Poisson (3), respectively. The packet sizes were sorted in ascending order by Constant (64), Constant (128) and Constant (256).
4.1. Network Topology
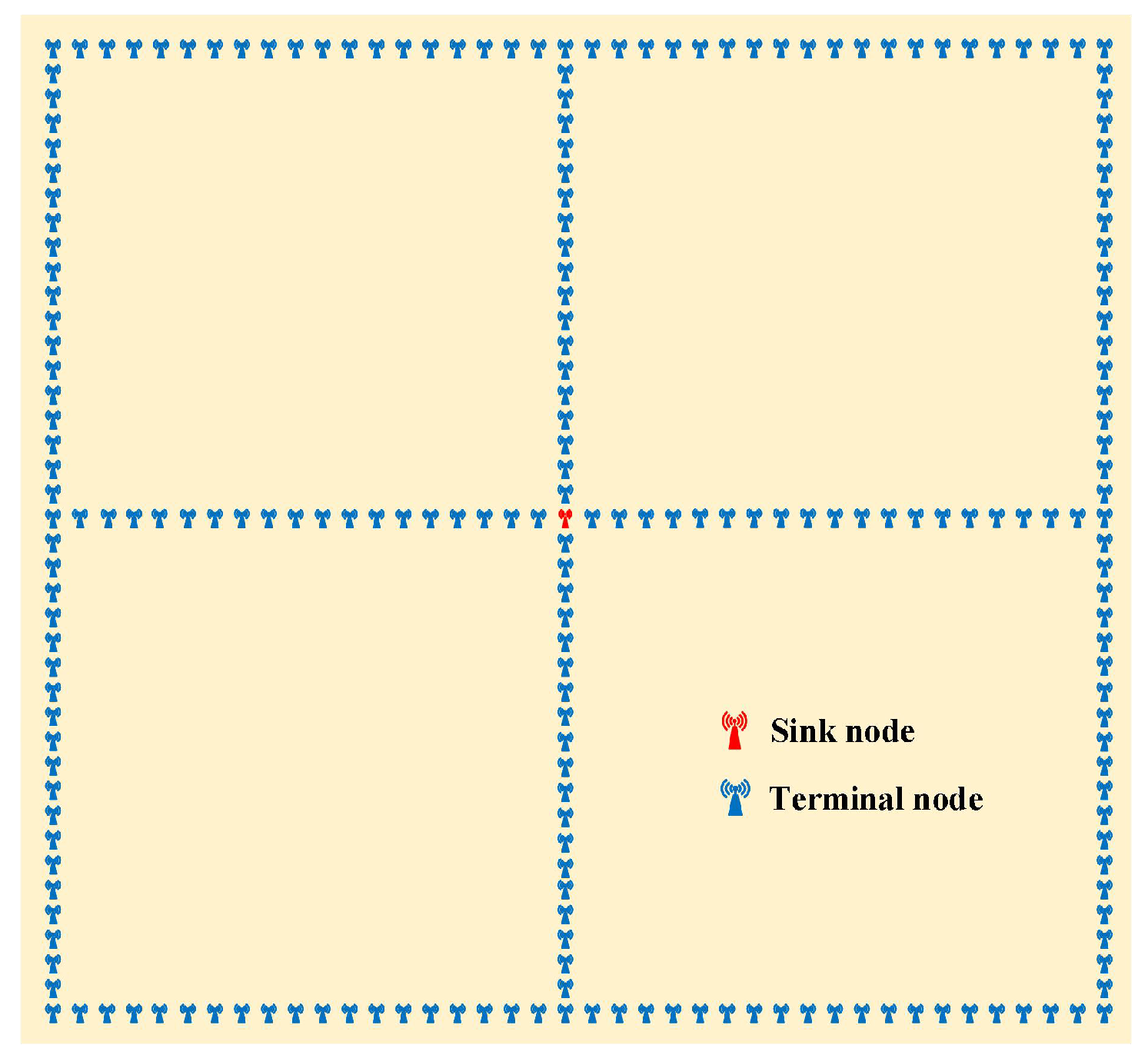
Firstly, the model performed within the range of 6 km × 6 km in the OPNET simulative scene. The scenario involved 230 terminals that communicate with one sink. The centre of the simulation scene is a sink node and the others are terminal nodes. Each edge of the model contained 40 terminals, and each terminal was 100 m apart. The arrangement of nodes is shown in
Figure 5.
4.2. Physical Layer
The physical layer mainly configures the parameters both of the transmitter and receiver. In order to accurately reflect the characteristics of LoRa, the peak data transmission rate, channel bandwidth and the lowest frequency of data transmission were set in the transmitter and receiver. The channel bandwidth of the transmitter and receiver were set to 125 kHz in the simulation, and the maximum channel rate was 5 kbps. Moreover, the range of the LoRa frequency band was 470–518 MHz by default, so the minimum frequency of the transceiver was set to 470 MHz. The channel model mainly adopts the free space propagation model in OPNET.
4.3. Node Layer Model
The object-oriented simulation method is used in OPNET, with all nodes changed on the basis of the same model. In this subsection, we divide the nodes into four layers from bottom to top, as shown in
Figure 6.
The application layer consisted of the Source model and the Sink model. The Source model mainly customized different transmission time slots, produced different size packets, and simulated the Poisson process [
29,
30]. The function of the Sink model was to destroy the packets, which were delivered to the destination node and count the throughput and packet loss rate of the system before their destruction. The network layer controls the routing function of users when sending data. It also drives the MAC model to complete the networking process of the wireless ad hoc network, which initiates the initialization of the network and transmits data packets generated by the application layer. The MAC layer was based on the IEEE802.15.4g communication rules to control how to select wireless communication links when transmitting information [
31,
32]. The MAC layer protocol of LoRa supports CSMA and conflict avoidance technology [
33,
34]. The physical layer was composed of two models; the wireless receiver and the wireless transmitter, as shown in
Figure 6.
4.4. MAC Process Model
The main innovations of our proposed LoRa module are in MAC layer. The proposed adaptive p-persistent CD/CSMA protocol that is used in MAC layer to resolve channel conflicts. The CDMA spread spectrum protocol enables packets to realize wireless channel transmission on multiple channels. The MAC process model is shown in
Figure 7. The Idle state is an interrupt state that detects the channel before sending packet data. When the channel is idle, it is transferred to the Wt_free state machine. Inversely, when the channel is busy, the idle state automatically turns to the Defer_0 state. Irrespective of the state the packet is transferred to, it will be given a random transmission probability
. The random
value was compared with the set
value size, and the back-off algorithm was performed when the random value was less than the set value. Otherwise, the channel will enter the Wt_free state.
4.5. Simulation Results
To evaluate link performance, the system overall throughput and the packet reception rate (PRR) both served as metrics. The system overall throughput
S can be obtained as
[
35], where
L denotes the network offered traffic and
denotes the PRR. In this context, adopting the system overall throughput as a metric not only can evaluate system performance from the ratio between the number of successfully received packets and the total number of sent packets, but also can deploy different levels of the network offered traffic to further maximize the overall throughput of the system and achieve very competitive performance in various system settings. Thus, we consider the scenarios of different traffic and loads and evaluate the performance in terms of system throughput and delay.
To validate the effectiveness of the adaptive p-persistent CSMA protocol, we compare the existing Class A, ALOHA, conventional p-persistent CSMA, and adaptive p-persistent CSMA protocols. The simulation parameters are presented in
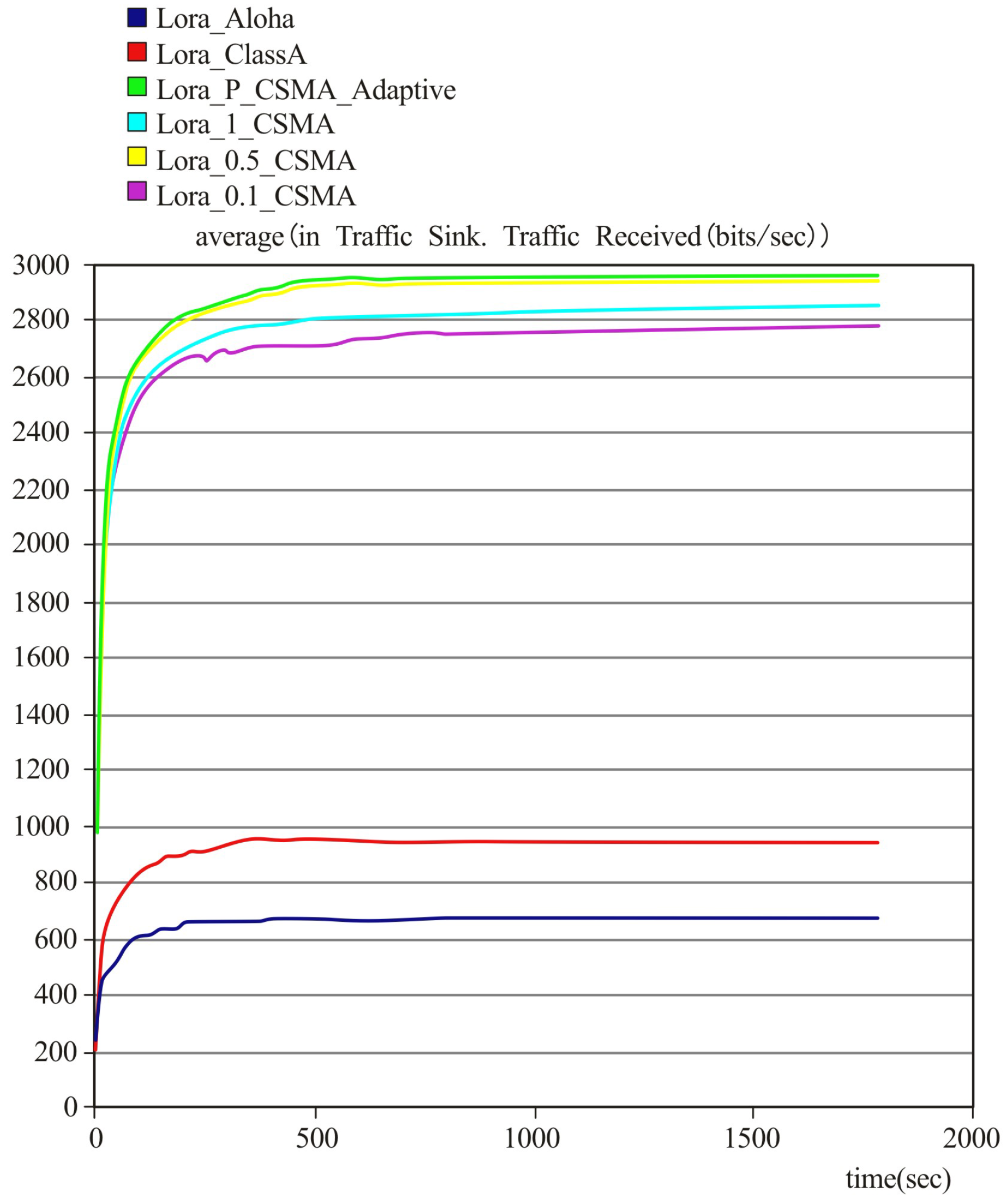
Table 2. It can be seen from
Figure 8 that the throughput of the 0.5-persistent CSMA protocol is higher than that of 1-persistent CSMA and 0.1-persistent CSMA protocols about 100 and 160 bits/s, respectively. This is due to traffic not being spread equally on the channels for high traffic that causes more serious channel collisions. As the limits of the adaptive p-persistent CSMA protocol are much closer to being optimal, the load is spread more uniformly over the channels at high traffic. Thus, we see a drop in collision rate and increased throughput by using the adaptive p. For this reason, the average throughputs of Class A and ALOHA protocols are far much lower than that of the adaptive p-persistent CSMA protocol. In conclusion, the adaptive p-persistent CSMA protocol can achieve a better system performance than other p-persistent CSMA protocols without adaptive p. Moreover, to make the comparison results more intuitive, a summary table has been added at the end of this section. As demonstrated in
Table 3, our protocol can achieve higher throughput, lower latency than the others when the deployments of the network offered traffic or the channel loads varies, which is of great significance for diverse practical applications.
We investigate the impact of duty-cycled transmissions at the end device and the system throughput implemented on NS-3. The NS-3 LoRaWAN module is an extension of the NS-3 module for the low power wide area network. The collision model used in the NS-3 module is based on the capture effect. The LoRaWAN physical layer and MAC layer components are running over each LoRa device and the gateway. The physical layer of each device interacts with that of the respective gateway via the NS-3 spectrum physical module, implementing the devices air interface and channel-specific parameters. More specifically, in the physical layer, which includes the sender and receiver, the bandwidth is 125 kHz, the coding rate is 4/5, the order of spread spectrum code is 6, the peak data transmission rate is 5468 bps/s, and the frequency band is 868 MHz. In this case, a duty cycle of 1% [
35] is beneficial for the system because it limits traffic and hence collisions, thus providing a higher throughput than the system without duty cycle restrictions.
Figure 9 shows a comparison of the system throughput of the proposed protocol for a given value of the network offered traffic and different loads. It can be seen from the simulation results that for a given value of traffic, a higher load can obtain better system overall throughput in the condition of fulfilling the duty cycle requirements.
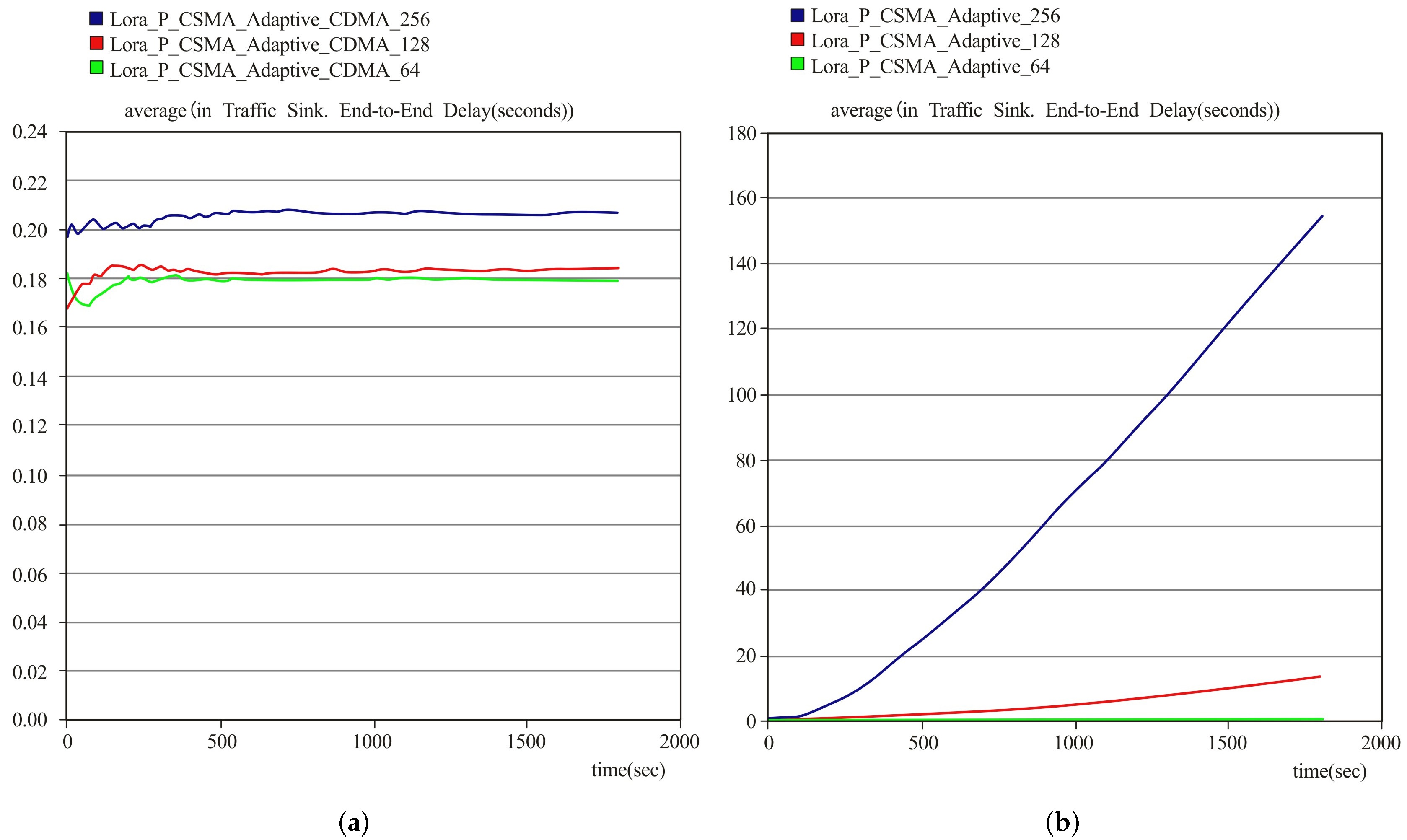
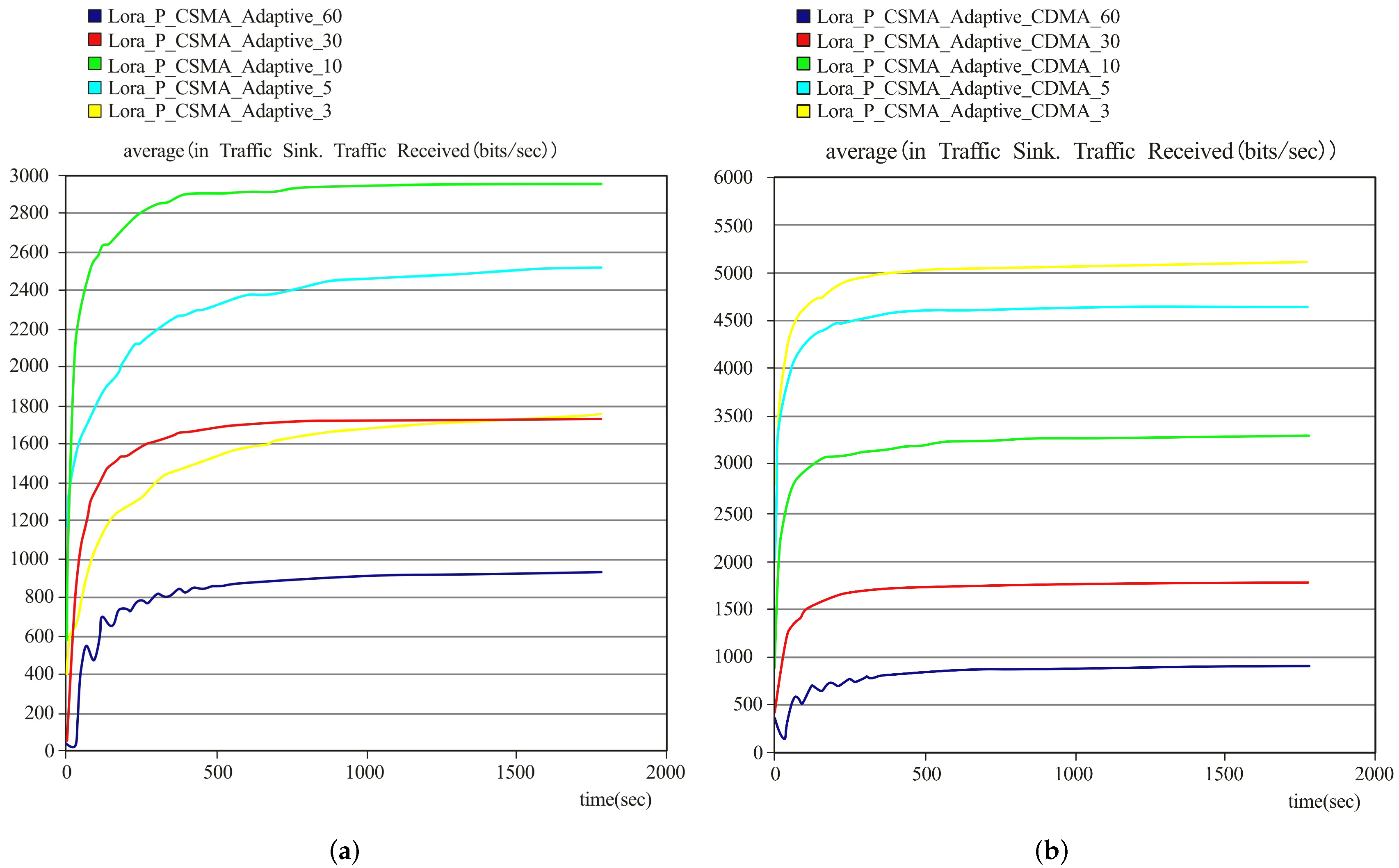
Figure 10 shows the average throughput of the proposed adaptive p-persistent CD/CSMA and the adaptive p-persistent CSMA without CDMA protocols for different traffic and loads. The average throughput of the proposed adaptive p-persistent CD/CSMA protocol is significantly improved by approximately 3000 bits/s compared with the adaptive p-persistent CSMA without the CDMA protocol for the scenario of high traffic and load. In the case of low traffic and load, although the average throughput of the two protocols is close to each other after stabilization, the proposed protocol is also superior to that of the adaptive p-persistent CSMA without CDMA protocol. Therefore, the proposed protocol significantly outperforms the adaptive p-persistent CSMA without CDMA protocol.
Figure 11 shows a comparison of the system delay between the proposed protocol and the adaptive p-persistent CSMA without CDMA protocol for high traffic channel and different loads. The simulation results indicate that the proposed adaptive p-persistent CD/CSMA protocol delivers lower delay even at Poisson (5) of packet inter-arrival time than the adaptive p-persistent CSMA without CDMA protocol. Moreover, when higher load is taken into account, it can be seen that the adaptive p-persistent CSMA protocol has a very high collision rate.
Figure 12 shows the average throughput in terms of the proposed adaptive p-persistent CD/CSMA protocol and adaptive p-persistent CSMA without CDMA protocol for different traffic and high load. The curve of the highest average throughput for the adaptive p-persistent CSMA protocol is Poisson (10), which is superior to the average throughput of Poisson (5) and Poisson (3). Normally, when the system traffic increases for the adaptive p-persistent CSMA protocol, the average throughput should increase as well, but the average throughput of Poisson (5) and Poisson (3) do not increase. This occurs because the channel for this protocol is saturated. On the contrary, the proposed adaptive p-persistent CD/CSMA protocol has the highest average throughput of Poisson (3), which exceeds approximately 3300 bits/s compared with the adaptive p-persistent CSMA protocol. It has been verified that the CDMA protocol is able to decrease collided frames efficiently and reduce the number of retransmission. Therefore, the proposed protocol could be used in cases of high traffic and load to resolve the channel collision problem.