A Review on Evaluation and Configuration of Fault Injection Attack Instruments to Design Attack Resistant MCU-Based IoT Applications
Abstract
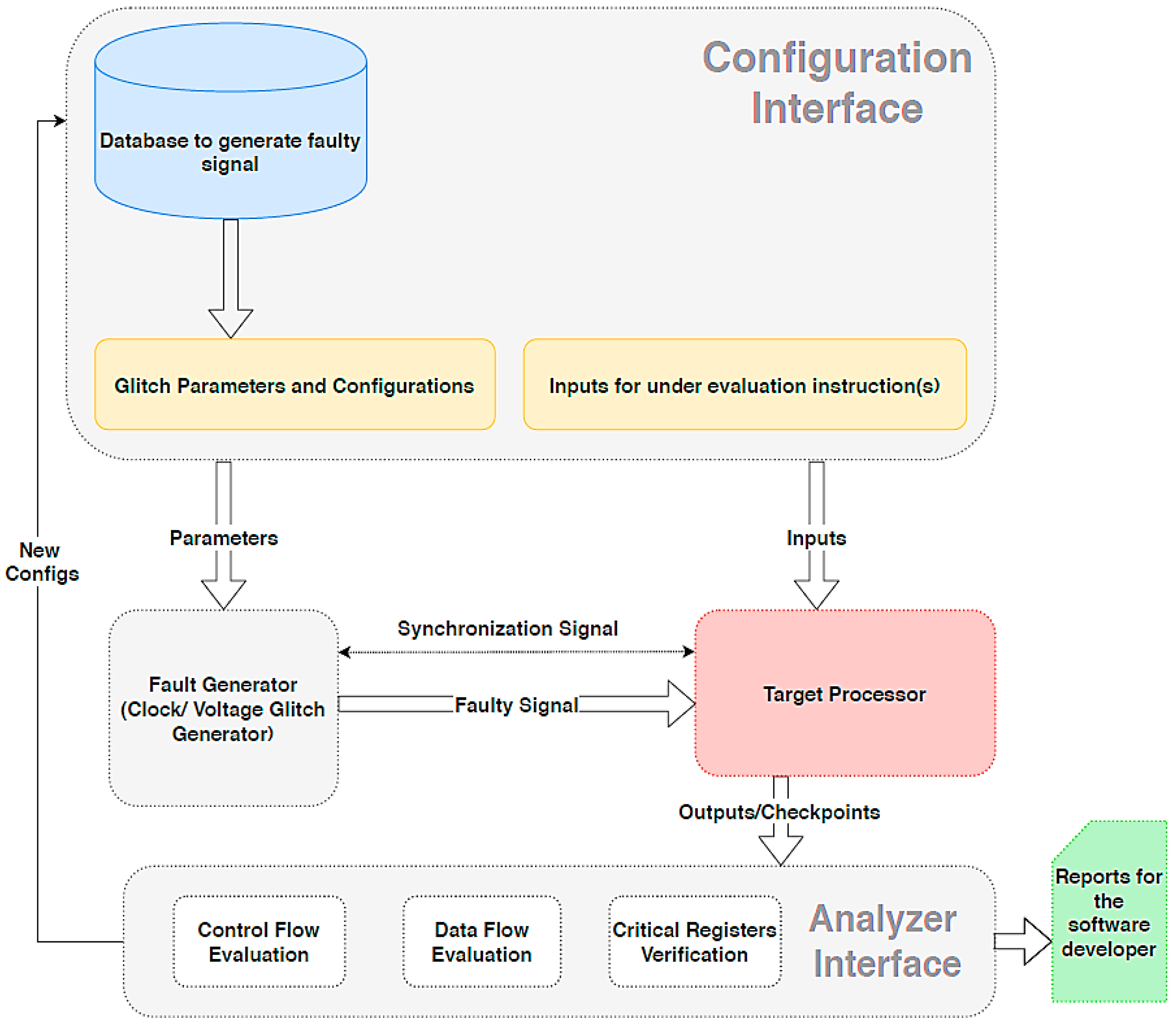
1. Introduction
2. Preliminaries and Basic Concepts
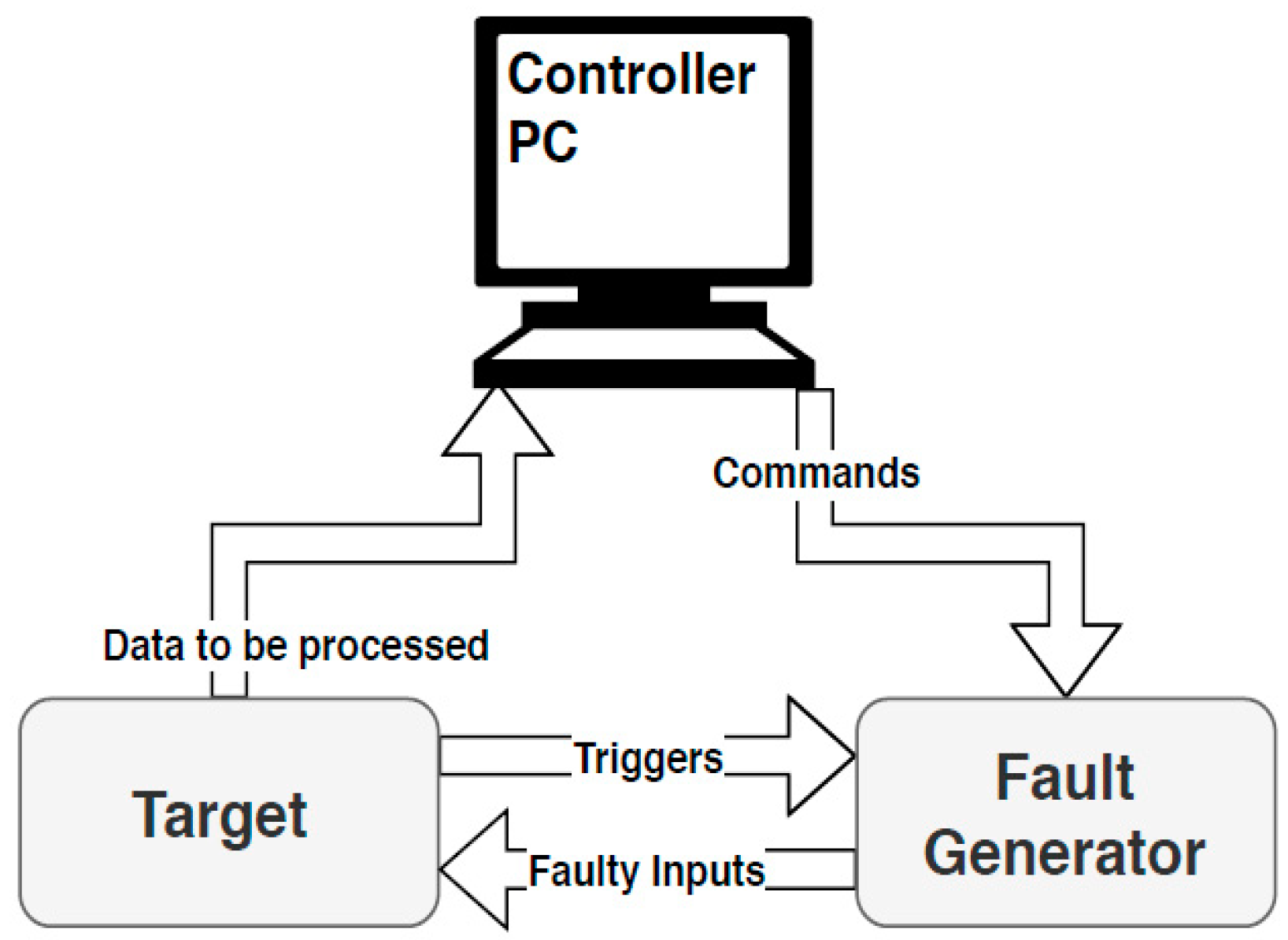
- Accuracy in the generated faulty signal: This parameter is described according to the type of the signal produced. In fact, the more control we have over the generated faulty signals, the more we achieve successful attacks in terms of generating and exploiting the desired faults. Control over the time and location of injected faults can be achieved using the communication lines between the controller PC and the fault generator.
- Run-time fault configuration: In some evaluation platforms, the parameters of a faulty signal produced by the generator can be reconfigured during run-time. They are not limited to the design time and can be used to test a target system during the attack phase. This feature is available in some generators and is based on some kinds of FPGAs, allowing modification of some parameters during the run time [19].
- Reproducibility of the faulty signal: Reproducibility is the ability to obtain the same results in multiple repeats of the same test. Regarding this feature, the faulty signal should be reproducible and validated by a third party if the same hardware is used (for example, the same FPGA). This parameter becomes more important when a unique evaluation platform is designed and used for faulty signal generation [11,19,27,29,37,40,41].
- Randomness in faulty signal: Many of the faulty signal-generating methods presented, such as [7,9,10,18,19,27,28,37], are deterministic methods. To set up a fault generator and to apply an attack with high accuracy, all the output parameters must be prepared and calculated. However, as this requires complete and adequate information about the target, it is not applicable in all real-world attack scenarios. In addition, in order to achieve an efficient attack, a large number of possible combinations of the fault injection parameters need to be covered. This makes deterministic methods intractable within a limited time. To address this issue, a fuzzy-based fault generator has been proposed. It has been reported that this method has a high attack success rate [38]. In Section 3, we elaborate further on the related works.
2.1. Clock-Based Fault Attacks
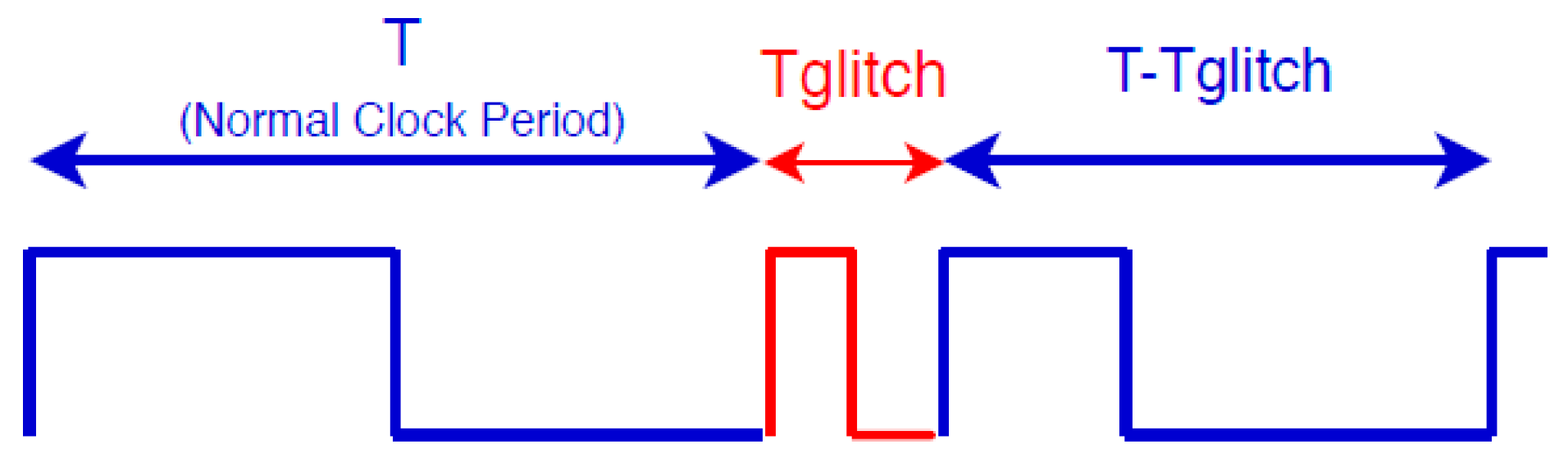
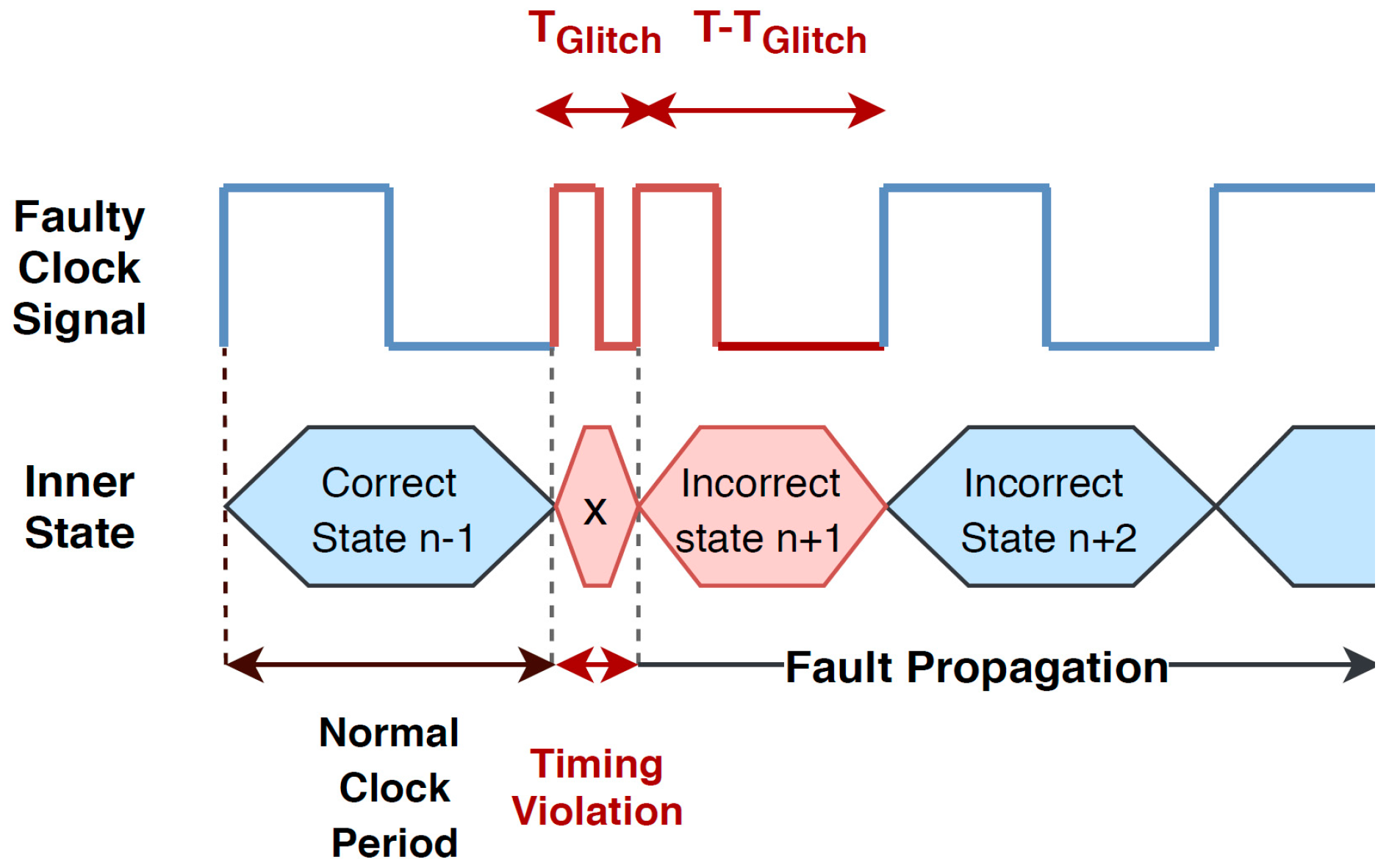
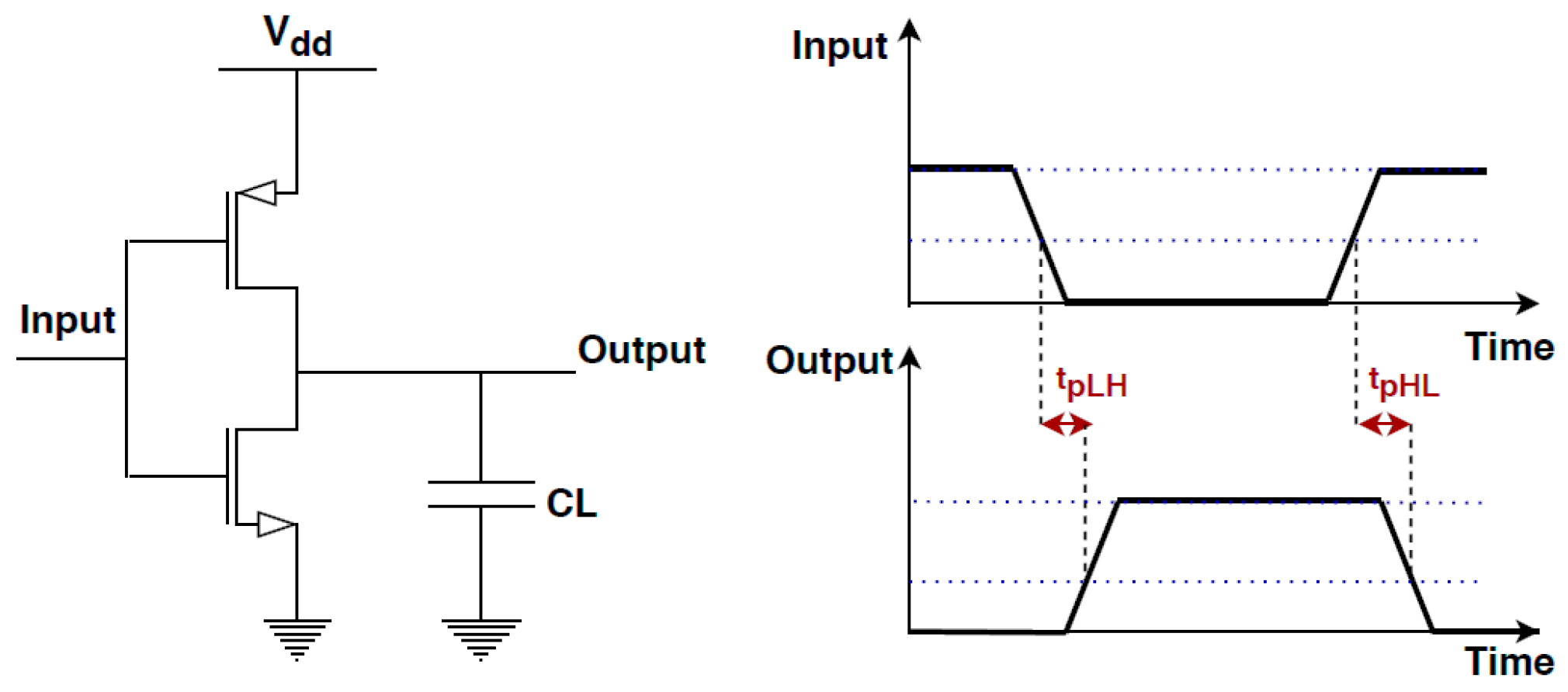
2.1.1. Clock Fault Injection Concept
2.1.2. Clock Glitch Generator Characteristics
- Clock glitch accuracy: This feature includes parameters such as minimum glitch width, gliding shift steps, standard deviation, clock glitching placement, and clock glitch frequency control. These features are dependent on the characteristics of the clock generator and the method used to induce the glitches.
- Minimum glitch width: Most target systems contain protocols to protect their external clock input so that when an abnormal clock is observed and detected, it resets the system or produces an alert. Therefore, less glitch width results in a lower chance of detection. In addition, in many cases, a precise and short glitch is needed to target a specific instruction running on the processor or specific data being fetched. This makes it important to control the glitch width. The precision of the clock glitch width is on the time scale of picoseconds or a few nanoseconds. For example, in Reference [41], a two-channel pulse generator has been used to design an accurate 35 ps glitch. Reference [11,40] and [42] include glitches on the nanosecond scale.
- Standard deviation: The standard deviation of the reported glitch width depends on the glitch generation algorithm and the limitations of the hardware used (e.g., FPGA).
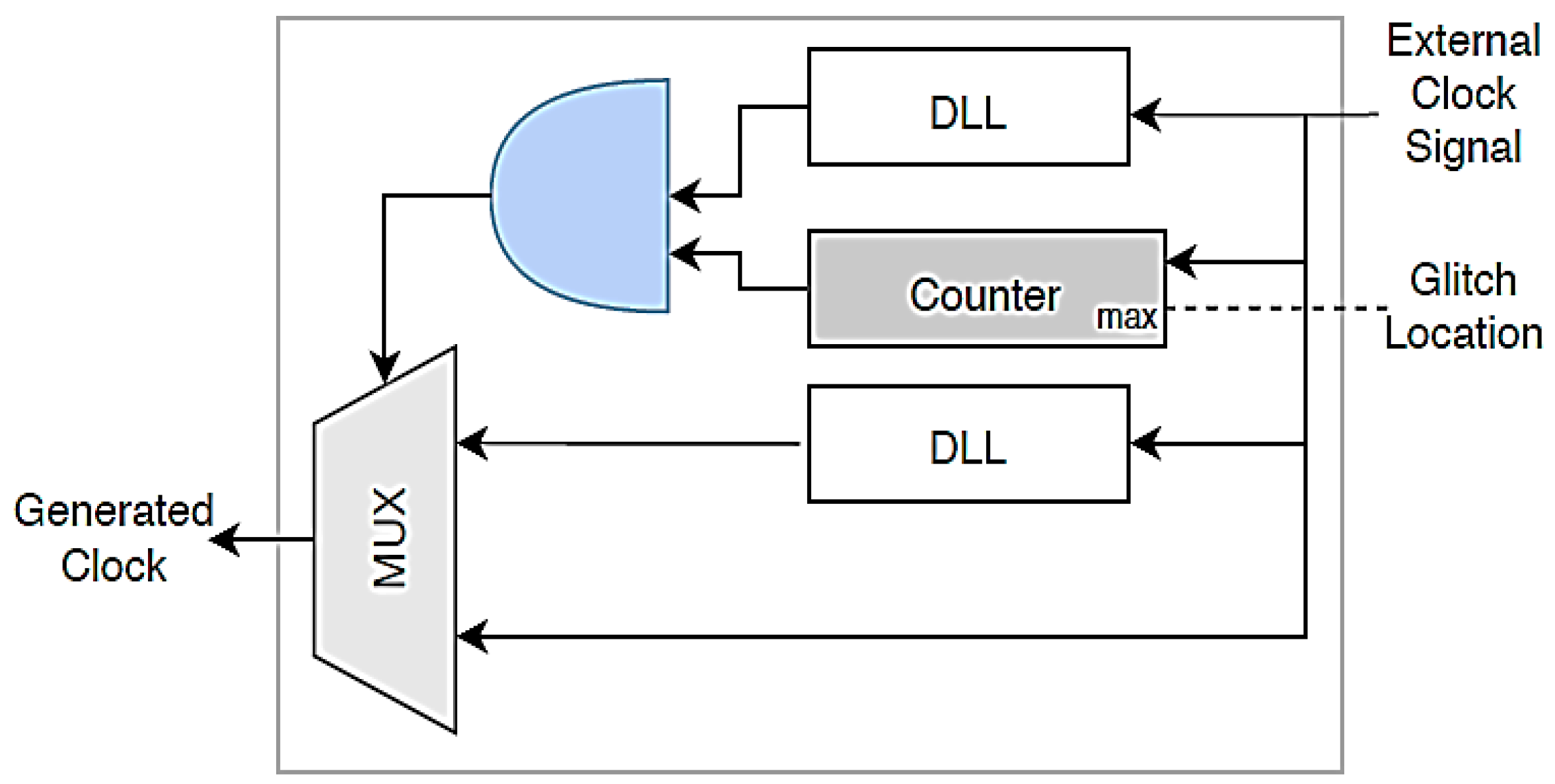
- Clock glitching placement: It is important to induce a glitch into a specific position of the clock signal. For example, it is important to inject a glitch into a system at a certain round of encryption. Reference [40] uses a counter to determine the location of the glitch injection.
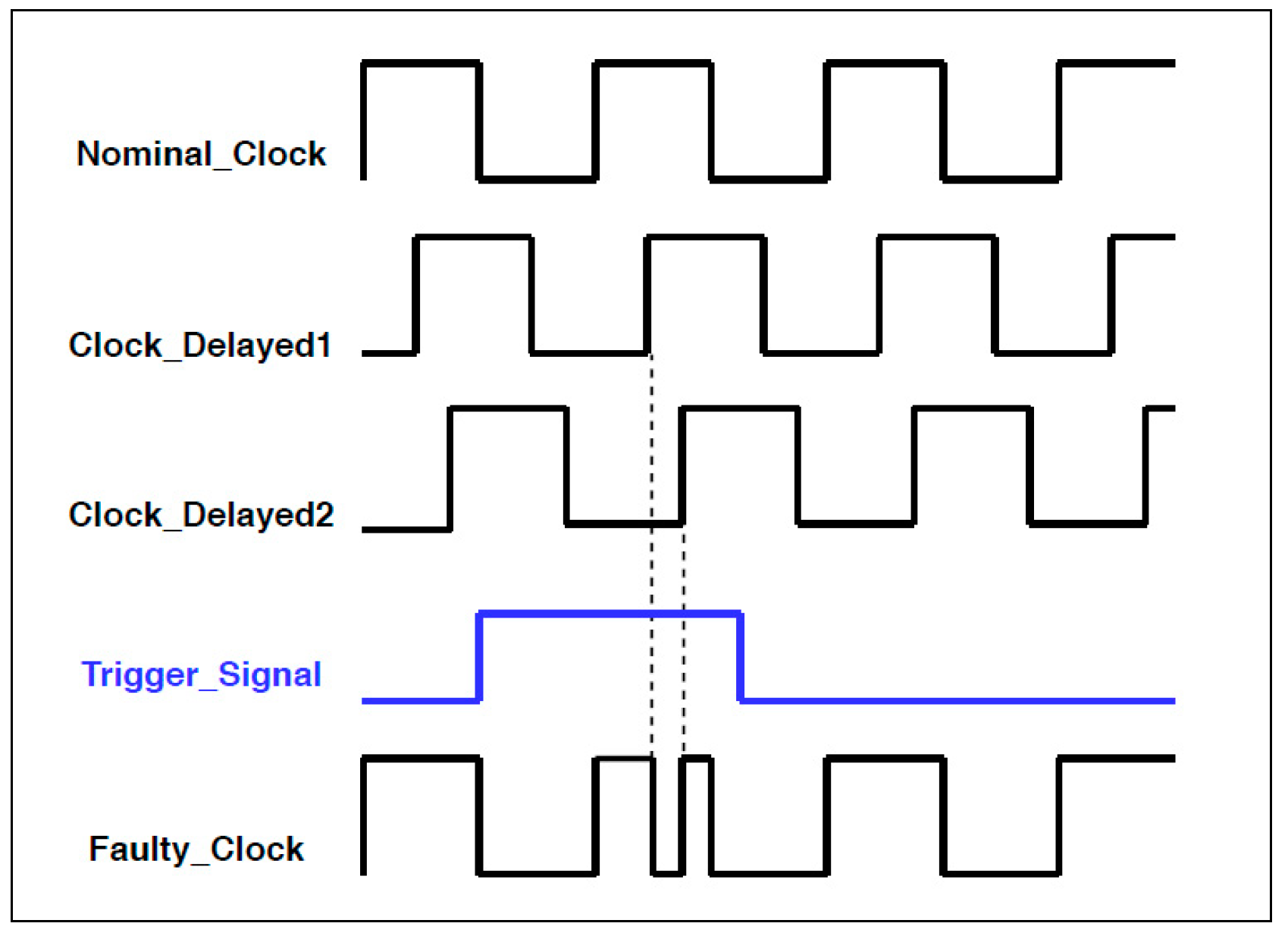
- Clock glitch run-time configuration: Glitchy-clock parameters, such as phase delay and frequency, can be reconfigured at the run-time to help the attacker. For example, in [40], a digital clock manager (DCM) of an FPGA is used to configure the glitch. FPGA run-time adjustment can be used to change the phase-shifted values, but this method is limited to a certain range of values. Reference [19] presents an approach for partial configuration using the FPGA configuration capabilities, including reconfiguring the DCM blocks at the run-time. The ‘bit-stream differential files’ generated by FPGA tools are applied to substantiate the run-time configuration.
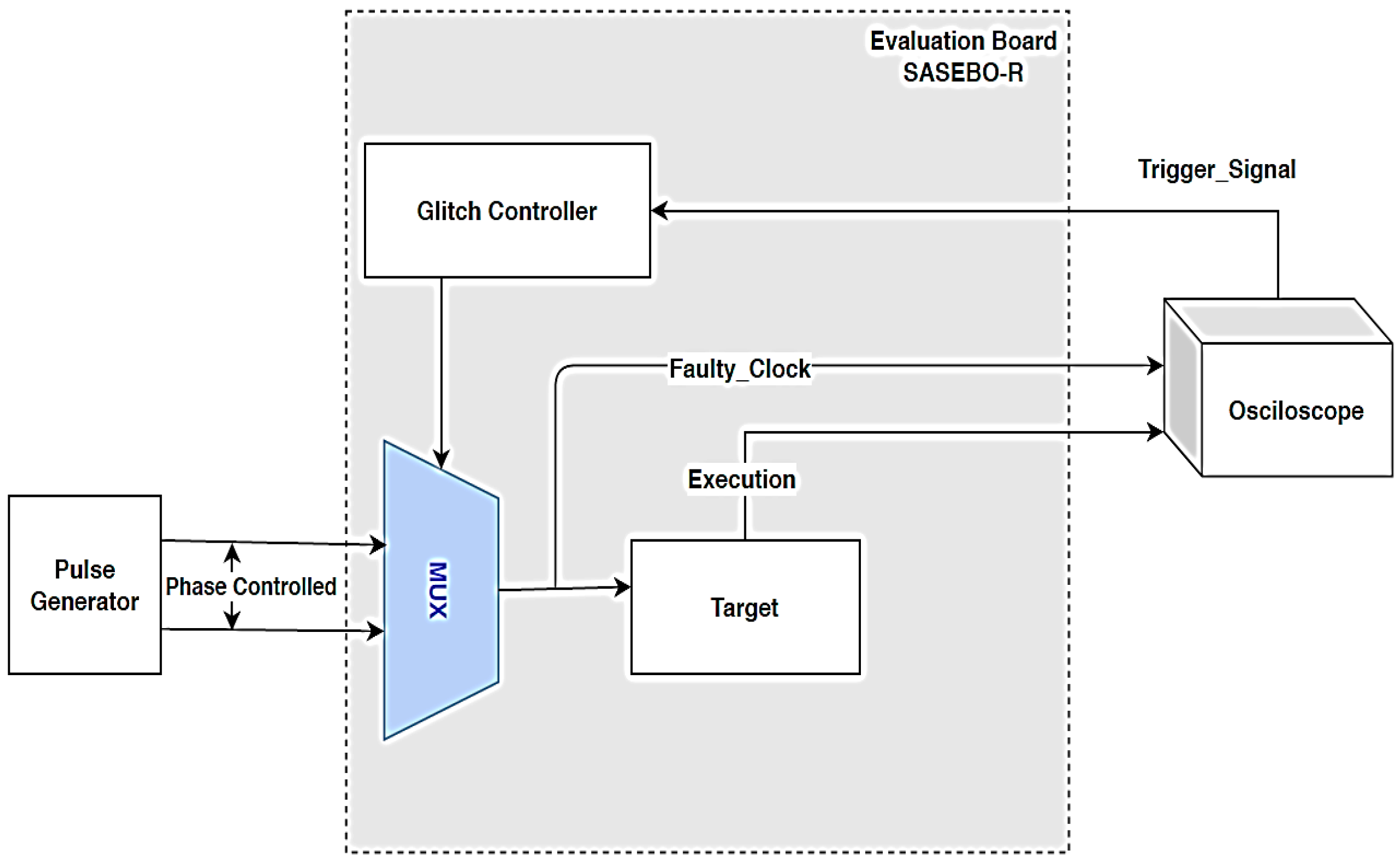
- Clock glitch reproducibility: this helps attackers to reproduce the faulty clock signal with the same characteristics as many times as they wish. It is important in some applications, which require the assessment of vulnerabilities and tracking of the clock glitch attack procedure. Reference [41] includes a unique evaluation platform (SASEBO) for reproducible clock glitch generation.
- Clock glitch randomness: In most clock glitch generators, the glitch parameters—such as frequency, width, precision, etc.—are pre-determined, i.e., they are determined before run-time. This requires complete and adequate information about the target system, which would not be possible in all real-world attack scenarios. Furthermore, in order to have a highly efficient attack, one needs to cover a large number of possible combinations of the parameters mentioned, which would not be practical in a limited time. For this reason, in recent years, new techniques such as the fuzzy glitch generator have been proposed for the generation of clock glitches [38]. All of these techniques use ring oscillators instead of FPGA blocks and demonstrate the ability to achieve a highly successful attack rate. Details of the related works will be provided in the following section. In the next sub-section (Section 2.2.), we will discuss the basic set-ups and main characteristics of voltage glitch generators.
2.1.3. Clock Glitch Attack Examples
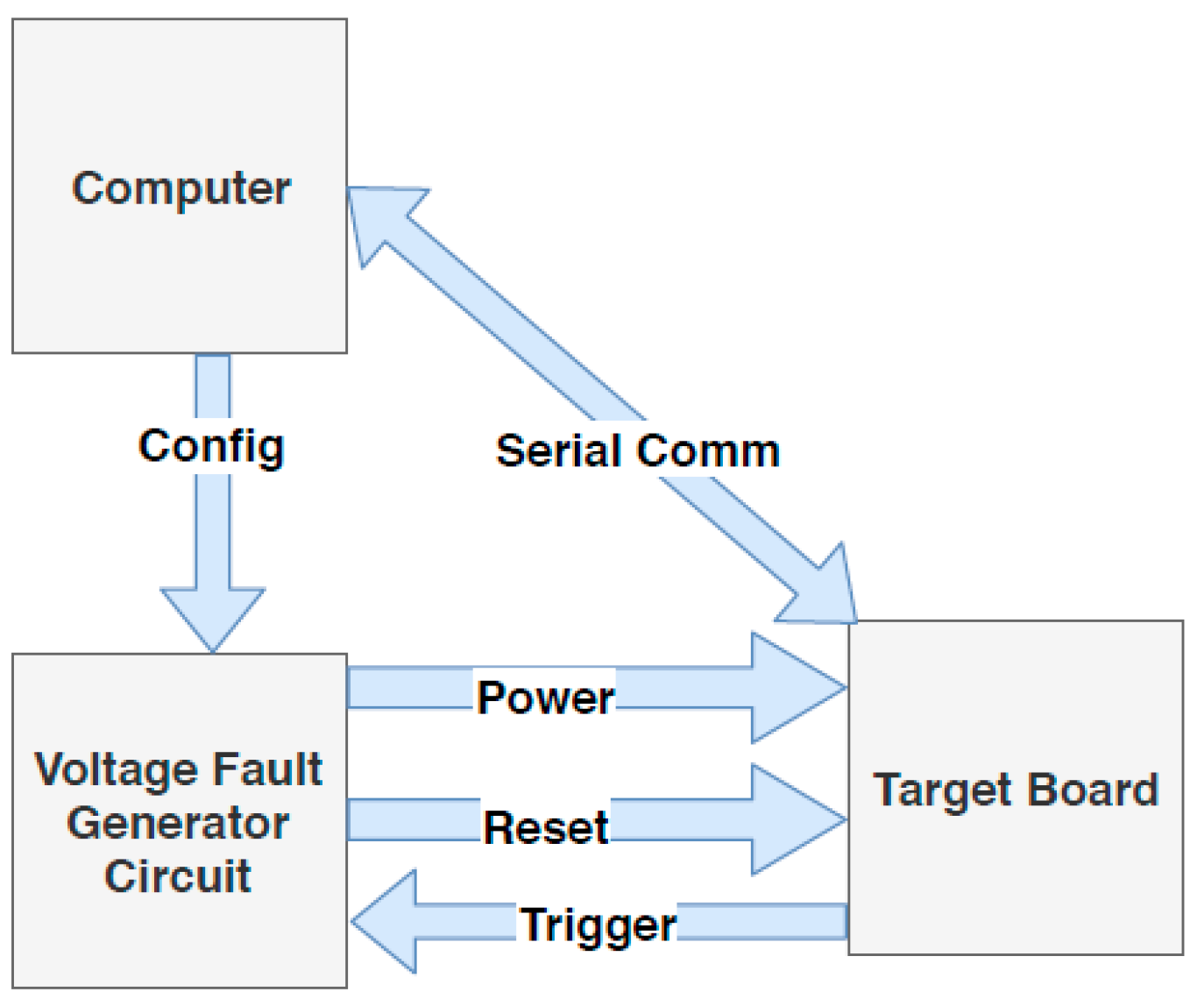
2.2. Voltage-Based Fault Attacks
2.2.1. Voltage Fault Injection Concept
2.2.2. Voltage Glitch Generator Characteristics
- Voltage glitch accuracy: Various parameters can affect the accuracy of the generated voltage glitch, such as minimum glitch width, glitch delay, and glitch placement. These features are dependent on the characteristics of the voltage generator and the method used to induce the glitches.
- Minimum glitch width: Generally, a precise and short voltage glitch is needed to bypass the existing glitch detectors on the external voltage inputs of the targeted systems. These protection modules observe the external voltage inputs and can reset the target system or create an alert to avoid any malfunction. Furthermore, a short voltage glitch is needed to target a specific instruction of the running code on the processor. Therefore, the more accurate and tenuous the voltage glitch is, the more chances an attacker has to accomplish the desired fault attacks. Depending on the equipment employed to generate the faulty signal, the minimum value of the glitch width can be changed. For instance, in the generator presented in [45], a pulse generator is used to generate the optimized voltage glitch, and the minimum pulse width is reported as 10 ns.
- Glitch delay: This parameter shows the amount of time a voltage glitch takes to be injected after the setting up of the trigger signal [7]. To take advantage of the existing vulnerabilities in the running application, the glitch must be induced simultaneously with specific instruction(s) execution. According to the selected glitch width, the glitch delay should be considered to guarantee that the injected glitch hits the targeted instruction. For instance, to generate faulty ciphertexts, it is important to inject a glitch into the target at a certain round of encryption [47]. Other situations in which the glitch injection time is a crucial concern are escalating privileges [7], skipping authentications, and misinterpreting an instruction [8].
- Voltage glitch placement: this parameter is related to the spatial position of the glitch. Spatial precision specifies the exact locations of the targeted circuit affected by the faulty voltage signal. In advanced systems such as modern SoCs, there are different power domains or power islands. A power domain is a group of gates powered by the same supplier. Depending on operational conditions, different voltage suppliers are connected to these domains. This parameter can help the attacker to provoke an erroneous behavior in a specific part. For example, by targeting an area in the chip like register banks and inducing memory faults, the wrong values may be gathered from the memory bus [21].
- Voltage glitch run-time configuration: this parameter is defined as the possibility of reconfiguring the voltage glitch during the run-time. The parameters of generated glitchy voltage signals such as glitch width, delay, and amplitude can be reconfigured at the run-time to help the attacker to examine different attack scenarios. Run-time configurability depends on the specifications of the generator circuit. Reconfigurability can be applied through hardware inputs (e.g., by using sliding switches to adjust glitch width) or by communicating (e.g., UART) with the controller PC [19].
- Voltage glitch reproducibility: This feature helps the attacker to obtain the same voltage glitching attack results when the same glitch is injected into multiple runs. Typically, voltage glitch generations are reproducible when fixed values are identified for the glitch parameters.
- Voltage glitch randomness: Instead of pre-defining and pre-calculating all voltage glitch parameters in every attack scenario, an attacker can select them randomly from an interval of possible values. Using this approach, more combinations of the parameters mentioned can be covered within a short time, which leads to the conducting of more successful attacks. With some of the previously proposed approaches, such as [7], parameters such as glitch width and glitch delay are defined using a divide and conquer method with a randomized parameter approach. Now that we have categorized the important parameters of glitchers, in the next section, we will review some of the main works in the field.
2.2.3. Voltage Glitch Attack Examples
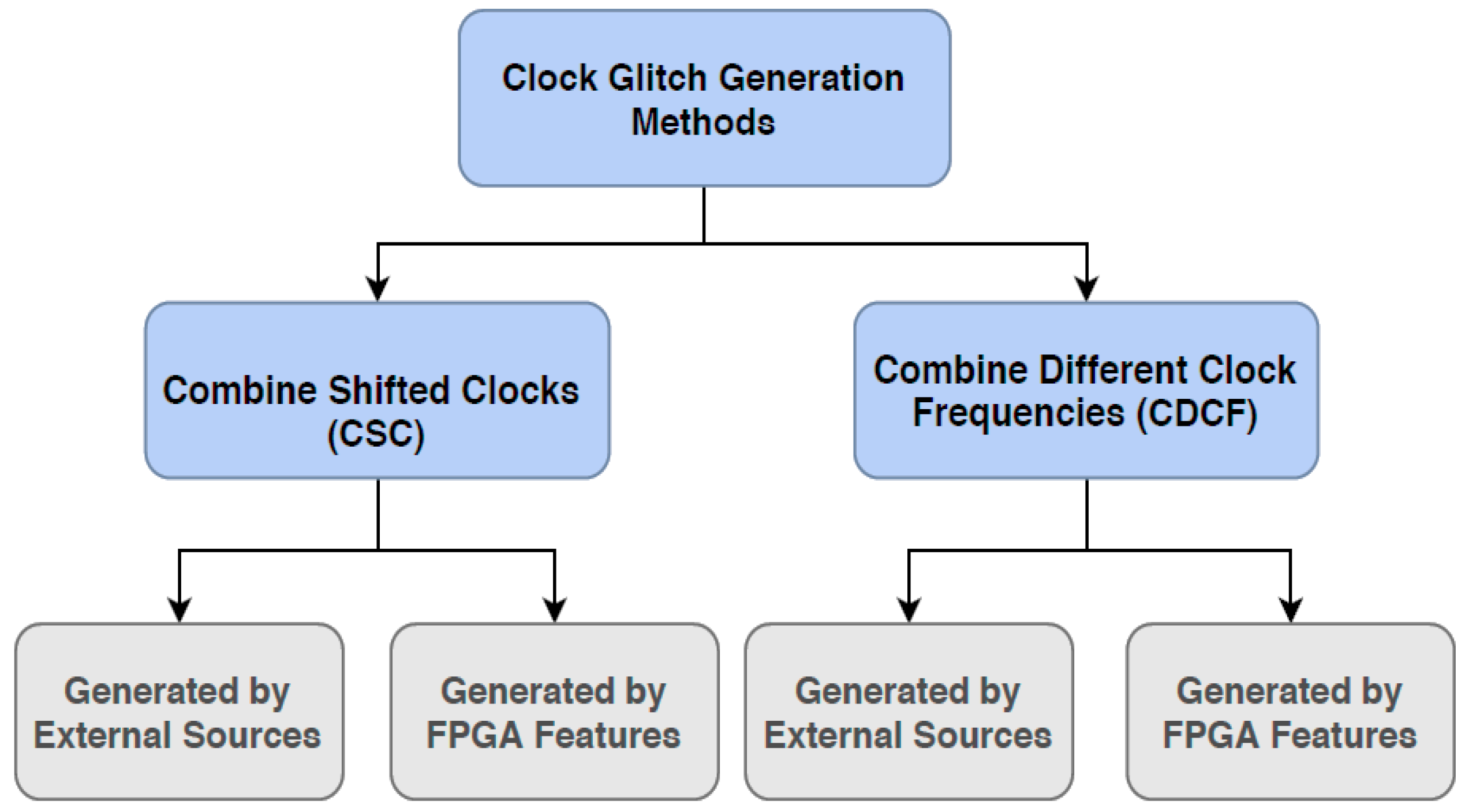
3. A Review of Previously Proposed Clock Glitch Generators
3.1. Combine Shifted Clocks (CSC)
3.2. Combine Different Clock Frequencies (CDCF)
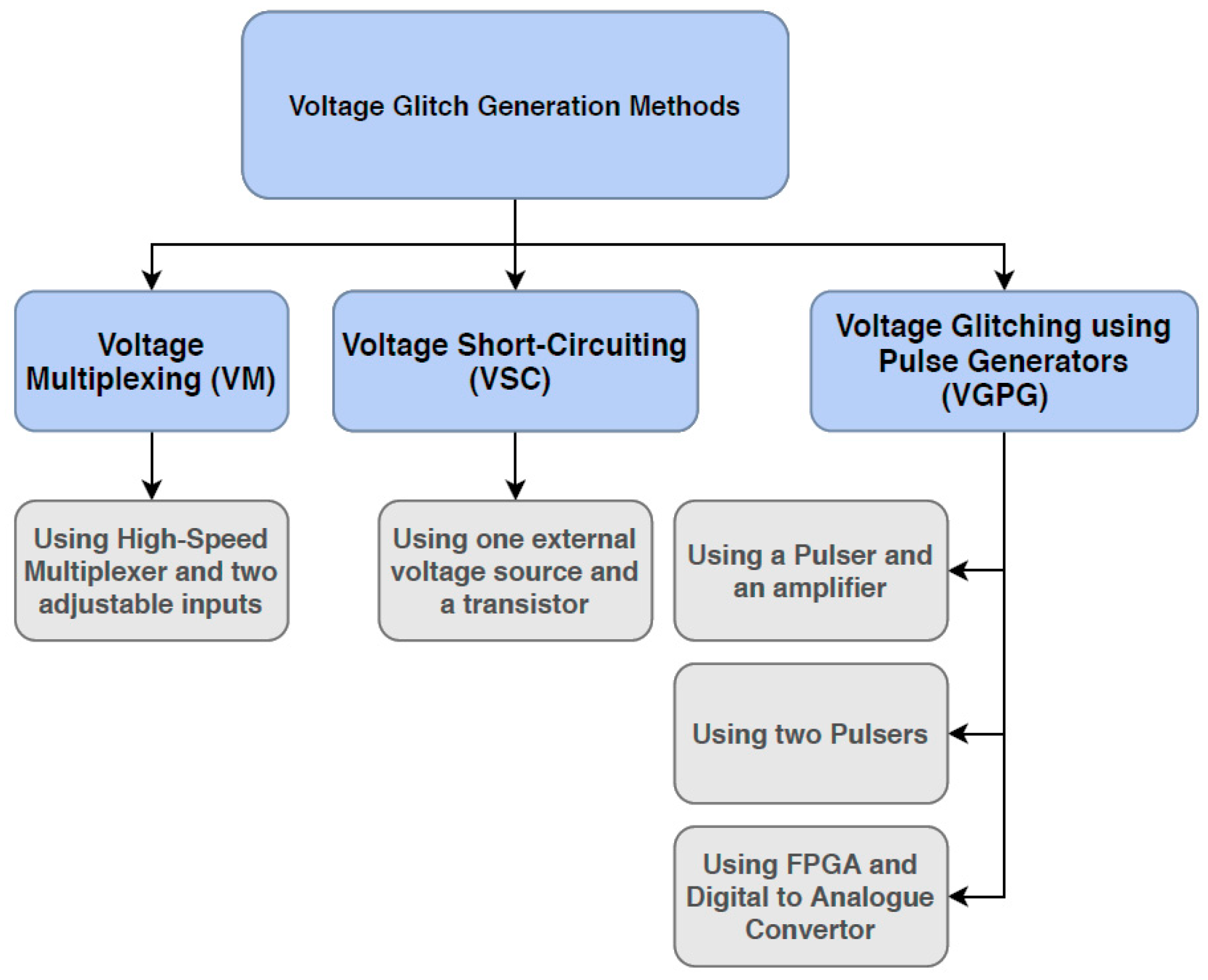
4. A Review of Previously Proposed Voltage Glitch Generators
4.1. Voltage Multiplexing (VM)
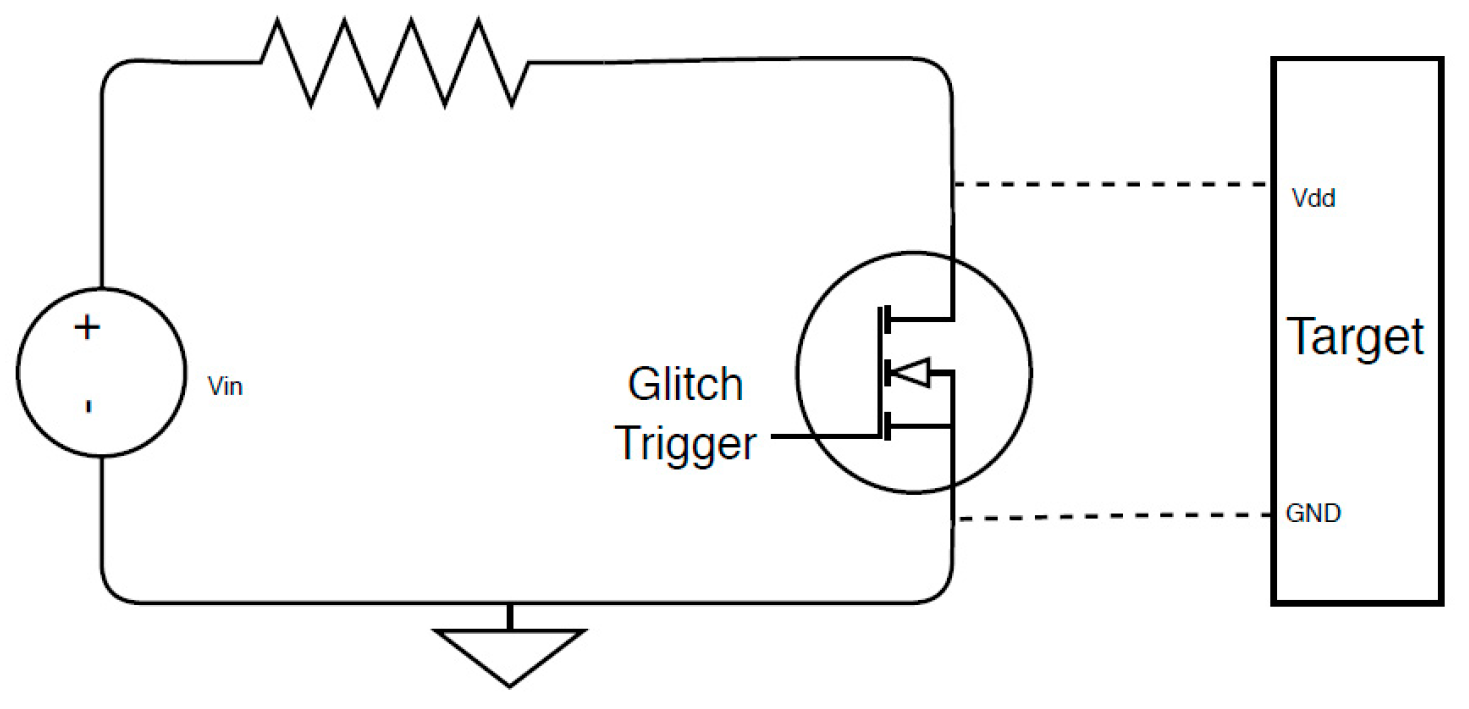
4.2. Voltage Short-Circuiting (VSC)
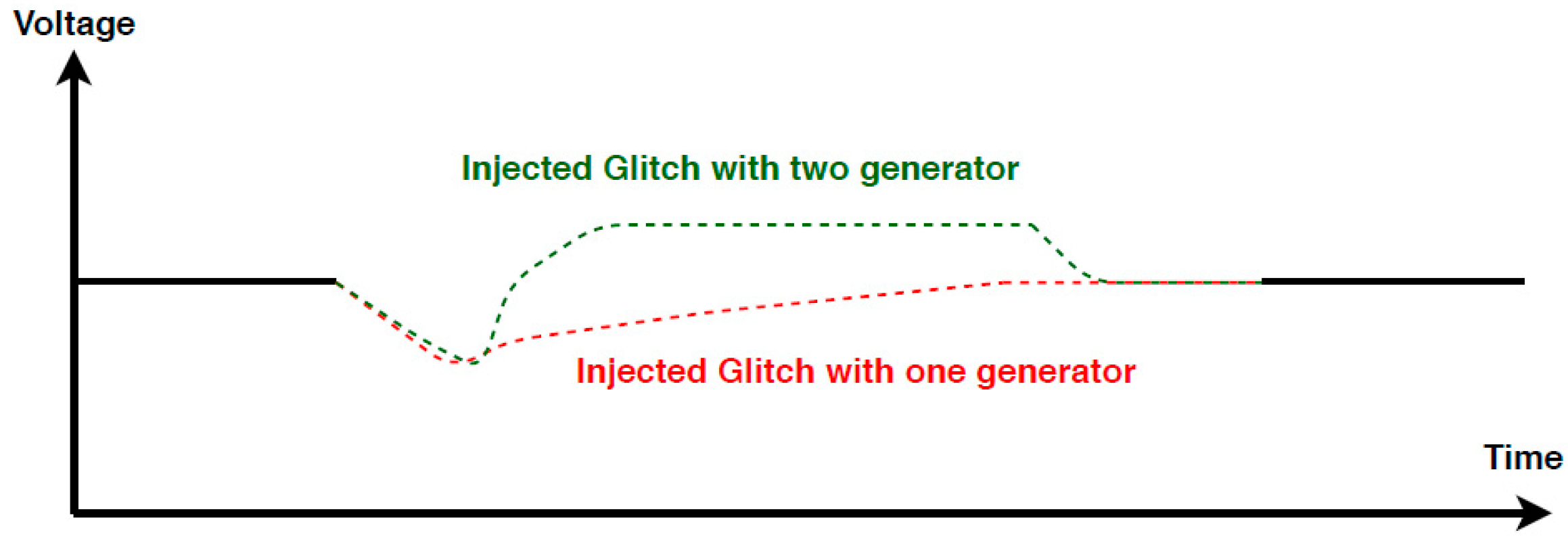
4.3. Voltage Glitching using Pulse Generators (VGPG)
5. Characteristics of an Efficient Evaluation Platform for IoT Software Developers
5.1. Clock Glitch Generator
5.2. Voltage Glitch Generator
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Thakar, A.T.; Pandya, S. Survey of iot enables healthcare devices. In Proceedings of the International Conference on Computing Methodologies and Communication, ICCMC 2017, Erode, India, 18–19 July 2017; pp. 1087–1090. [Google Scholar] [CrossRef]
- Xu, T.; Wendt, J.B.; Potkonjak, M. Security of IoT Systems: Design Challenges and Opportunities. In Proceedings of the 2014 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), San Jose, CA, USA, 2–6 November 2014; pp. 417–423. [Google Scholar] [CrossRef]
- Yang, Y.; Wu, L.; Yin, G.; Li, L.; Zhao, H. A Survey on Security and Privacy Issues in Internet-of-Things. IEEE Internet Things J. 2017, 4, 1250–1258. [Google Scholar] [CrossRef]
- Deogirikar, J. Security Attacks inIoT: A Survey. In Proceedings of the 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Palladam, India, 10–11 February 2017; pp. 32–37. [Google Scholar] [CrossRef]
- Borgohain, T. Survey of Security and Privacy Issues of Internet of Things. arXiv 2015, arXiv:1501.02211. [Google Scholar]
- Lu, Y.; Xu, L. Da Internet of Things (IoT) Cybersecurity Research: A Review of Current Research Topics. IEEE Internet Things J. 2018, 4662. [Google Scholar] [CrossRef]
- Timmers, N. Escalating Privileges in Linux using Voltage Fault Injection. In Proceedings of the 2017 Workshop on Fault Diagnosis and Tolerance in Cryptography (FDTC), Taipei, Taiwan, 25 September 2017. [Google Scholar] [CrossRef]
- Timmers, N.; Spruyt, A.; Witteman, M. Controlling PC on ARM Using Fault Injection. In Proceedings of the 2016 Workshop on Fault Diagnosis and Tolerance in Cryptography (FDTC), Santa Barbara, CA, USA, 16 August 2016; pp. 25–35. [Google Scholar] [CrossRef]
- Barenghi, A.; Bertoni, G.; Parrinello, E.; Pelosi, G. Low voltage fault attacks on the RSA cryptosystem. In Proceedings of the 2009 Workshop on Fault Diagnosis and Tolerance in Cryptography (FDTC), Lausanne, Switzerland, 6 September 2009; pp. 23–31. [Google Scholar] [CrossRef]
- Martín, H.; Korak, T.; Millán, E.S.; Hutter, M. Fault Attacks on STRNGs: Impact of Glitches, Temperature, and Underpowering on Randomness. IEEE Trans. Inf. Forensics Secur. 2015, 10, 266–277. [Google Scholar] [CrossRef]
- Qiao, Y.; Lu, Z.; Liu, H.; Liu, Z. Clock Glitch Fault Injection Attacks on an FPGA AES Implementation. J. Electrotechnol. Electr. Eng. Manag. 2017, 1, 23–27. [Google Scholar]
- Piscitelli, R.; Regazzoni, F. Fault attacks, injection techniques and tools for simulation. In Hardware Security and Trust; Springer: Cham, Switzerland, 2015; pp. 15–20. [Google Scholar] [CrossRef]
- Kazemi, Z.; Papadimitriou, A.; Hely, D.; Fazeli, M.; Beroulle, V. Hardware Security Evaluation Platform for MCU-based Connected Devices: Application to healthcare IoT. In Proceedings of the 3nd International Verification and Security Workshop (IVSW), Costa Brava, Spain, 2–4 July 2018. [Google Scholar]
- Le Bouder, H.; Thomas, G.; Lashermes, R.; Linge, Y.; Robisson, B.; Tria, A. An Evaluation Tool for Physical Attacks. In Ad-hoc, Mobile, and Wireless Networks; Lecture Notes in Computer Science; Springer International Publishing: Cham, Switzerland, 2018. [Google Scholar]
- Thillard, A.; Prouff, E.; Roche, T. Success through confidence: Evaluating the effectiveness of a side-channel attack. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer Science+Business Media: Berlin, Germany, 2013; Volume 8086 LNCS, pp. 21–36. [Google Scholar] [CrossRef]
- Eslami, M.; Ghavami, B.; Raji, M.; Mahani, A. A survey on fault injection methods of digital integrated circuits. Integration 2020, 71, 154–163. [Google Scholar] [CrossRef]
- Potestad-Ordonez, F.E.; Jimenez-Fernandez, C.J.; Valencia-Barrero, M. Vulnerability Analysis of Trivium FPGA Implementations. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2017, 25, 3380–3389. [Google Scholar] [CrossRef]
- Matsubayashi, M.; Satoh, A.; Ishii, J. Clock glitch generator on SAKURA-G for fault injection attack against a cryptographic circuit. In Proceedings of the 2016 IEEE 5th Global Conference on Consumer Electronics (GCCE 2016), Kyoto, Japan, 11–14 October 2016; pp. 5–8. [Google Scholar] [CrossRef]
- Chipwhisperer Side Channel and Fault Injection Attacks Tool Chain. Available online: https://chipwhisperer.readthedocs.io/en/latest/tutorials.html (accessed on 14 July 2020).
- Katashita, T.; Hori, Y.; Sakane, H.; Satoh, A. Side-Channel Attack Standard Evaluation Board SASEBO-W Specification Niat 2012. Available online: https://csrc.nist.gov/csrc/media/events/non-invasive-attack-testing-workshop/documents/10_katashita.pdf (accessed on 14 July 2020).
- Karaklaji, D. Hardware Designer’s Guide to Fault Attacks. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2013, 21, 2295–2306. [Google Scholar] [CrossRef]
- Yuce, B.; Schaumont, P.; Witteman, M. Fault Attacks on Secure Embedded Software: Threats, Design, and Evaluation. J. Hardw. Syst. Secur. 2018, 111–130. [Google Scholar] [CrossRef]
- Selmane, N.; Guilley, S.; Institut, T. Practical Setup Time Violation Attacks on AES Jean-Luc DANGER. In Proceedings of the 2008 Seventh European Dependable Computing Conference, Kaunas, Lithuania, 7–9 May 2008; pp. 91–96. [Google Scholar] [CrossRef]
- Barenghi, B.A.; Breveglieri, L.; Koren, I.; Ieee, F.; Naccache, D. Fault Injection Attacks on Cryptographic Devices: Theory, practice, and countermeasures. Proc. IEEE 2012, 100, 3056–3076. [Google Scholar] [CrossRef]
- Li, Y.; Chen, M.; Wang, J. Introduction to Side-Channel Attacks and Fault Attacks. In Proceedings of the 2016 Asia-Pacific International Symposium on Electromagnetic Compatibility (APEMC), Shenzhen, China, 17–21 May 2016; pp. 573–575. [Google Scholar] [CrossRef]
- Moukarzel, M.; Eisenbarth, T.; Sunar, B. μleech: A side-channel evaluation platform for IoT. In Proceedings of the 2017 IEEE 60th International Midwest Symposium on Circuits and Systems (MWSCAS), Boston, MA, USA, 6–9 August 2017; pp. 25–28. [Google Scholar] [CrossRef]
- Balasch, J.; Gierlichs, B.; Verbauwhede, I. An in-depth and black-box characterization of the effects of clock glitches on 8-bit MCUs. In Proceedings of the 2011 Workshop on Fault Diagnosis and Tolerance in Cryptography (FDTC 2011), Nara, Japan, 28 September 2011; pp. 105–114. [Google Scholar] [CrossRef]
- Beringuier-boher, N.; Hely, D. Voltage Glitch Attacks on Mixed-Signal Systems. In Proceedings of the 2014 17th Euromicro Conference on Digital System Design, Verona, Italy, 27–29 August 2014; pp. 379–386. [Google Scholar] [CrossRef]
- Korak, T.; Hoefler, M. On the effects of clock and power supply tampering on two microcontroller platforms. In Proceedings of the 2014 Workshop on Fault Diagnosis and Tolerance in Cryptography (FDTC 2014), Busan, Korea, 23 September 2014; pp. 8–17. [Google Scholar] [CrossRef]
- Liao, N.; Cui, X.; Liao, K.; Wang, T.; Yu, D.; Cui, X. Improving DFA attacks on AES with unknown and random faults. Sci. China Inf. Sci. 2017, 60, 1–14. [Google Scholar] [CrossRef]
- Dusart, P.; Letourneux, G.; Vivolo, O. Differential Fault Analysis on A.E.S. In International Conference on Applied Cryptography and Network Security; Zhou, J., Yung, M., Han, Y., Eds.; Springer: Berlin/Heidelberg, Germany, 2003; pp. 293–306. [Google Scholar]
- Bozzato, C.; Focardi, R.; Palmarini, F. Shaping the Glitch: Optimizing Voltage Fault Injection Attacks. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2019, 2019, 199–224. [Google Scholar] [CrossRef]
- Kazemi, Z.; Papadimitriou, A.; Souvatzoglou, I.; Aerabi, E.; Ahmed, M.M.; Hely, D.; Beroulle, V. On a Low Cost Fault Injection Framework for Security Assessment of Cyber-Physical Systems: Clock Glitch Attacks. In Proceedings of the 2019 IEEE 4th International Verification and Security Workshop (IVSW), Rhodes Island, Greece, 1–3 July 2019; pp. 7–12. [Google Scholar] [CrossRef]
- Guillen, O.M.; Gruber, M.; De Santis, F. Low-Cost Setup for Localized Semi-invasive Optical Fault Injection Attacks. In International Workshop on Constructive Side-Channel Analysis and Secure Design; Guilley, S., Ed.; Springer International Publishing: Cham, Switzerland, 2017; pp. 207–222. [Google Scholar]
- Sanlyde, D.; Skorobogatov, S.; Anderson, R.; Quisquater, J.-J. On a new way to read data from memory. In Proceedings of the First International IEEE Security in Storage Workshop, Greenbelt, MD, USA, 11 December 2002; pp. 65–69. [Google Scholar]
- Breier, J.; Jap, D. A survey of the state-of-the-art fault attacks. In Proceedings of the 2014 International Symposium on Integrated Circuits (ISIC), Singapore, 10–12 December 2014; pp. 152–155. [Google Scholar]
- Korak, T.; Hutter, M.; Ege, B.; Batina, L. Clock glitch attacks in the presence of heating. In Proceedings of the 2014 Workshop on Fault Diagnosis and Tolerance in Cryptography (FDTC 2014), Busan, Korea, 23 September 2014; pp. 104–114. [Google Scholar] [CrossRef]
- Obermaier, J.; Specht, R.; Sigl, G. Fuzzy-glitch: A practical ring oscillator based clock glitch attack. In Proceedings of the 2017 International Conference on Applied Electronics, Pilsen, Czech Republic, 5–6 September 2017. [Google Scholar] [CrossRef]
- Agoyan, M.; Dutertre, J.M.; Naccache, D.; Robisson, B.; Tria, A. When clocks fail: On critical paths and clock faults. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer Science+Business Media: Berlin, Germany, 2010; Volume 6035 LNCS, pp. 182–193. [Google Scholar] [CrossRef]
- Endo, S.; Sugawara, T.; Homma, N.; Aoki, T.; Satoh, A. An on-chip glitchy-clock generator for testing fault injection attacks. J. Cryptogr. Eng. 2011, 265–270. [Google Scholar] [CrossRef]
- Fukunaga, T.; Takahashi, J. Practical fault attack on a cryptographic LSI with ISO/IEC 18033-3 block ciphers. In Proceedings of the Fault Diagnosis and Tolerance in Cryptography (FDTC 2009), Lausanne, Switzerland, 6 September 2009; pp. 84–92. [Google Scholar] [CrossRef]
- Yuce, B.; Ghalaty, N.F.; Schaumont, P. Improving fault attacks on embedded software using RISC pipeline characterization. In Proceedings of the 2015 Workshop on Fault Diagnosis and Tolerance in Cryptography (FDTC 2015), St. Malo, France, 13 September 2015; pp. 97–108. [Google Scholar] [CrossRef]
- Barenghi, A.; Bertoni, G.M.; Breveglieri, L.; Pelosi, G. The Journal of Systems and Software A fault induction technique based on voltage underfeeding with application to attacks against AES and RSA. J. Syst. Softw. 2013, 86, 1864–1878. [Google Scholar] [CrossRef]
- Zussa, L.; Dutertre, J.-M.; Clediere, J.; Tria, A. Power supply glitch induced faults on FPGA: An in-depth analysis of the injection mechanism. In Proceedings of the 2013 IEEE 19th International On-Line Testing Symposium (IOLTS), Chania, Greece, 8–10 July 2013; pp. 110–115. [Google Scholar] [CrossRef]
- Zussa, L.; Dutertre, J.; Cledieret, J.; Robissont, B.; Nationale, E.; Ensm, M.D.S. Analysis of the fault injection mechanism related to negative and positive power supply glitches using an on-chip voltmeter. In Proceedings of the 2014 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), Arlington, VA, USA, 6–7 May 2014; pp. 130–135. [Google Scholar] [CrossRef]
- Zussa, L.; Dutertre, J.-M.; Clediere, J.; Robisson, B.; Tria, A. Investigation of timing constraints violation as a fault injection means. In Proceedings of the 27th Conference on Design of Circuits and Integrated Systems (DCIS), Avignon, France, 28 November 2012. [Google Scholar]
- Breveglieri, L.; Koren, I. (Eds.) Round Reduction Using Faults. FDTC 2005, 5, 13–24. [Google Scholar]
- Korczyc, J.; Krasniewski, A. Evaluation of Susceptibility of FPGA-based Circuits to Fault Injection Attacks Based on Clock Glitching. In Proceedings of the 2012 IEEE 15th International Symposium on Design and Diagnostics of Electronic Circuits & Systems (DDECS), Tallinn, Estonia, 18–20 April 2012; pp. 2–5. [Google Scholar] [CrossRef]
- Selmke, B.; Hauschild, F.; Obermaier, J. Peak clock: Fault injection into PLL-based systems via clock manipulation. In Proceedings of the ACM Conference on Computer and Communications Security, London, UK, 11–15 November 2019; pp. 85–94. [Google Scholar] [CrossRef]
- Romailler, Y.; Pelissier, S. Practical fault attack against the Ed25519 and EdDSA signature schemes. In Proceedings of the 2017 Workshop on Fault Diagnosis and Tolerance in Cryptography (FDTC), Taipei, Taiwan, 25 September 2017. [Google Scholar] [CrossRef]
- Hutter, M.; Schmidt, J.M.; Plos, T. Contact-based fault injections and power analysis on RFID tags. In Proceedings of the European Conference on Circuit Theory and Design Conference Program (ECCTD 2009), Antalya, Turkey, 23–27 August 2009; pp. 409–412. [Google Scholar] [CrossRef]
- Xilinx Inc. Spartan-6 FPGA Data Sheet: DC and Switching Characteristics. 30 January 2015. Available online: https://www.xilinx.com/support/documentation/data_sheets/ds162.pdf (accessed on 14 July 2020).
- Tatsukawa, J.; MMCM and PLL Dynamic Reconfiguration MMCM and PLL Configuration Bit Groups. Application Note: 7 Series, UltraScale, and UltraScale+ FPGAs; 2019; Volume xapp888, pp. 1–20. Available online: http://www.xilinx.com/support/documentation/application_notes/xapp888_7Series_DynamicRecon.pdf (accessed on 14 July 2020).
- 7Series FPGAs Clocking Resources User Guide, UG472 (v1.14). 2018. Available online: https://www.xilinx.com/support/documentation/user_guides/ug472_7Series_Clocking.pdf (accessed on 14 July 2020).
- Riscure VC Glitcher. Available online: https://www.riscure.com/product/vc-glitcher/ (accessed on 14 July 2020).





| Technique | Spatial Precision | Temporal Precision | Controlling the Intensity | Equipment Costs | Required Expertise |
|---|---|---|---|---|---|
| Over-clocking | Low (global) | Not Applicable | Clock frequency | Low | Low |
| Clock glitch | Low (global) | High (local) | Glitch parameters | Low | Moderate |
| Technique | Spatial Precision | Temporal Precision | Controlling the Intensity | Equipment Costs | Required Expertise |
|---|---|---|---|---|---|
| Under-powering | Moderate | Not applicable | Voltage amplitude | Low | Low |
| Voltage glitch | Moderate | Moderately synchronization | Voltage amplitude and glitch width/delay | Low | Moderate |
| Methods | Fault Attack by Tampering Clock Input | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| CSC | CDCF | |||||||||
| Characteristics | Using FPGA Features | Using External Clock Sources | Using External Sources | Using FPGA Features | ||||||
| [39] | [19] | [37] | [29] | [40] | [41] | [11] | [38] | [27] | ||
| Evaluation Platform | Equipment | Xilinx Virtex5 FPGA | Spartan6 FPGA | Spartan6 FPGA | Spartan6 FPGA | FPGA on SASEBO-G VirtexII-Pro XC2VP30 | Agilent 11152 Pulse generator and SASEBO-G | Agilent E4438C 6GHz Waveform generator DE2-115 development board | Ring Oscillators on Spartan-3E FPGA | Virtex-II Pro XC2VP30 FPGA |
| System Complexity | Moderate | Moderate | Moderate-High (PCB designing) | Moderate-High (PCB designing) | Moderate-High (evaluation platform) | Moderate-High (evaluation platform) | Moderate | Moderate-High | Moderate | |
| Cost | Moderate | Moderate-High * | Moderate | Moderate | Moderate-High * (evaluation platform) | Moderate-High * (evaluation platform) | Moderate | Moderate | Moderate | |
| Minimum Glitch Width | No Info. (100 MHz) | 3 ns for (10 MHz) | 7 ns for (10 and 20 MHz) | 5.9 ns for (24 MHz) | 4.9 ns (24 MHz) | 5.6 ns (24 MHz) | 8 ns in (114 MHz) and 2 ns (2 GHz) | 100 ns for 8 MHz | 27 ns (8 MHz) | |
| Capability to Inject Glitch into Specific Clock Cycle | Yes | Yes | Yes | Yes | Yes | Yes | Yes | No | Yes | |
| Capability to Perform Run-Time Configuration | No | Partial reconfiguration | No | No | No | No | Yes | No | No | |
| Capability to Control Generated Faulty Clock Frequency | Yes but Limited to DLL | Yes but Limited to DLL | Yes but Limited to DLL | Yes but Limited to DLL | Yes | Yes | Yes | Yes | Yes | |
| Reproducibility of Glitchy Clock | Yes | Yes | Yes | Yes | Yes | Yes | Yes | No | Yes | |
| Desired Randomness | No | No | No | No | No | No | No | Yes | No | |
| Target Platform | Xilinx Spartan 3AN fpga | AVR, XMEGA, smart cart | AVR atmega 162 | ARM Cortex-M0, ATxmega 256 | SASEBO-G VirtexII-Pro XC2VP7) | SASEBO-R | Altera DE2-115 EP4CE115F29C7 | STM32F030 | ATMEGA 163 | |
| Application | 128-bit AES | 128-bit AES and authentication | Arithmetic instructions | arithmetical/logical instructions, branch instruction, and memory instructions | AES | AES | AES | Infinite-loop | Smartcard application SOSS | |
| Methods | Fault Attack by Tampering Voltage Input | ||||||||
|---|---|---|---|---|---|---|---|---|---|
| VM | VSC | VGPG | |||||||
| Characteristics | Using FPGA Features | Using a Transistor | Using a Pulse Generator | ||||||
| [10] | [51] | [19] | [8] | [32] | [44] | [50] | [45] | ||
| Evaluation Platform | Equipment | XILINX Spartan-6 XC6SLX45 | Standard Evaluation Board (SASEBO) that includes two Xilinx VirtexTM-II Pro devices | Chipwhisperer evaluation platform | Dedicated high-speed hardware | Arbitrary Waveform generator and glitch amplifier | Agilent 814A AND Picosecond 10,3000B | PCB and a pulse generator | Agilent 8114A pulse generator |
| System complexity | Moderate | High (evaluation platform) + RF measurements | Moderate-High (evaluation platform) And Open source | Moderate | Moderate-High (stm32 to controlling and I/O) | Moderate | Moderate | Moderate | |
| Cost | Moderate | Moderate-High (evaluation platform) | Moderate-High (evaluation platform) | Moderate | Moderate | Moderate | Moderate | Moderate | |
| Minimum Glitch Width | - | - | - | - | - | - | - | 10 ns | |
| Voltage Glitch Placement | Synchronous with trigger | Synchronous with trigger | Synchronous with trigger | Synchronous with trigger | Synchronous with trigger | Synchronous with trigger | Synchronous with trigger | Synchronous with trigger | |
| Capability to Perform Run-Time Configuration | Limited to MUX (on the FPGA) | Limited to MUX (on the FPGA) | Limited to the voltage source | Limited to the FPGA | Limited to the voltage source | Limited to the voltage source | Limited to the voltage source | Limited to the voltage source | |
| Reproducibility of Glitchy Clock | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | |
| Desired Randomness | No | No | No | No | No | No | No | No | |
| Target | FPGA Xilinx Spartan3 and Spartan6 | Tag Chip | AVR–STMF103 | ARM | Different targets form ST, Texas instrument and Rennes | FPGA Xilinx Spartan 3A | Arduino board | FPGA Xilinx Spartan3 | |
| Application | STRNG | Radio Frequency Identification (RFID) tags | Authentication/boot loader | Secure boot attack/secure runtime attack | Different Fault models | AES | The Ed25519 and EdDSA signature schemes | AES | |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kazemi, Z.; Hely, D.; Fazeli, M.; Beroulle, V. A Review on Evaluation and Configuration of Fault Injection Attack Instruments to Design Attack Resistant MCU-Based IoT Applications. Electronics 2020, 9, 1153. https://doi.org/10.3390/electronics9071153
Kazemi Z, Hely D, Fazeli M, Beroulle V. A Review on Evaluation and Configuration of Fault Injection Attack Instruments to Design Attack Resistant MCU-Based IoT Applications. Electronics. 2020; 9(7):1153. https://doi.org/10.3390/electronics9071153
Chicago/Turabian StyleKazemi, Zahra, David Hely, Mahdi Fazeli, and Vincent Beroulle. 2020. "A Review on Evaluation and Configuration of Fault Injection Attack Instruments to Design Attack Resistant MCU-Based IoT Applications" Electronics 9, no. 7: 1153. https://doi.org/10.3390/electronics9071153
APA StyleKazemi, Z., Hely, D., Fazeli, M., & Beroulle, V. (2020). A Review on Evaluation and Configuration of Fault Injection Attack Instruments to Design Attack Resistant MCU-Based IoT Applications. Electronics, 9(7), 1153. https://doi.org/10.3390/electronics9071153






