Physical Layer Security in a Hybrid TPSR Two-Way Half-Duplex Relaying Network over a Rayleigh Fading Channel: Outage and Intercept Probability Analysis
Abstract
1. Introduction
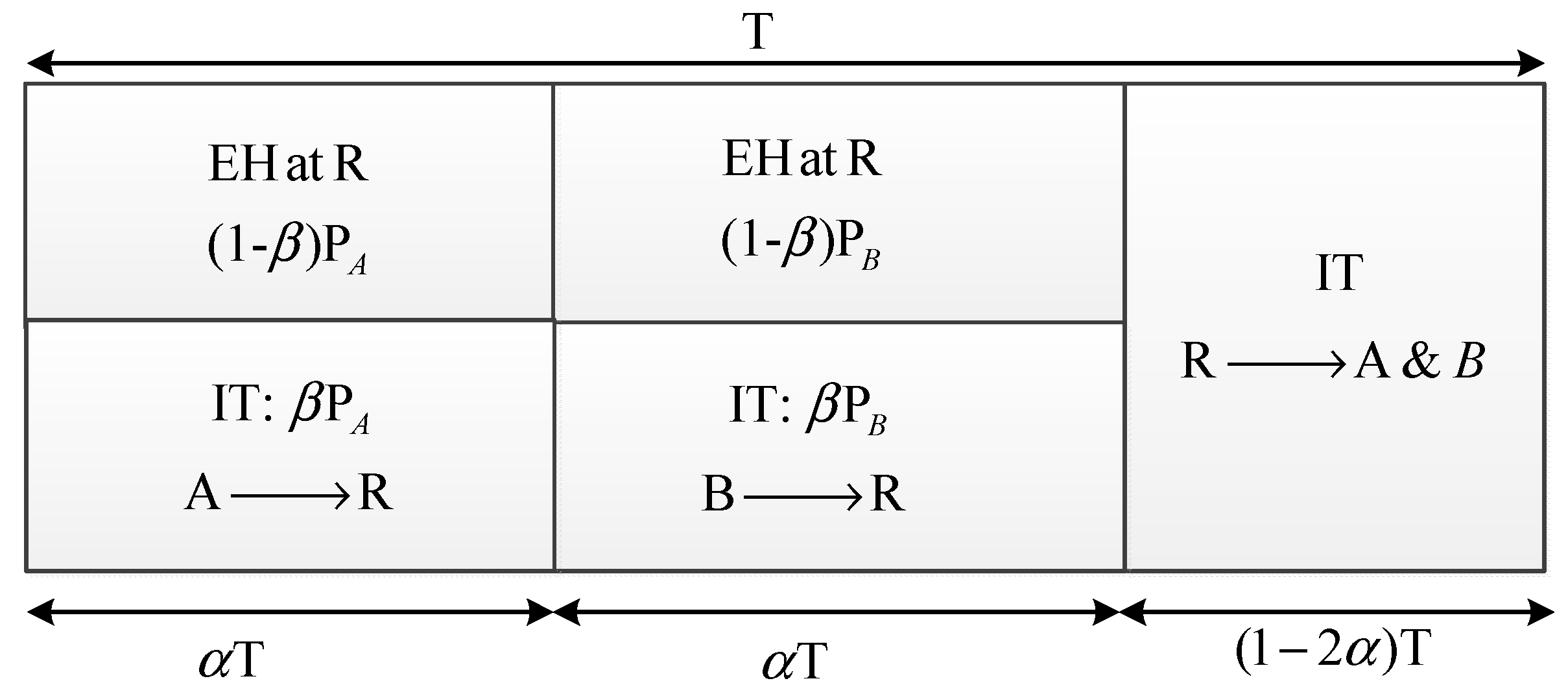
2. Network Model
2.1. Energy Harvesting Phase
2.2. Information Transmission Phase
3. Outage Probability and Throughput Analysis
3.1. Outage Probability (OP)
3.2. Intercept Probability
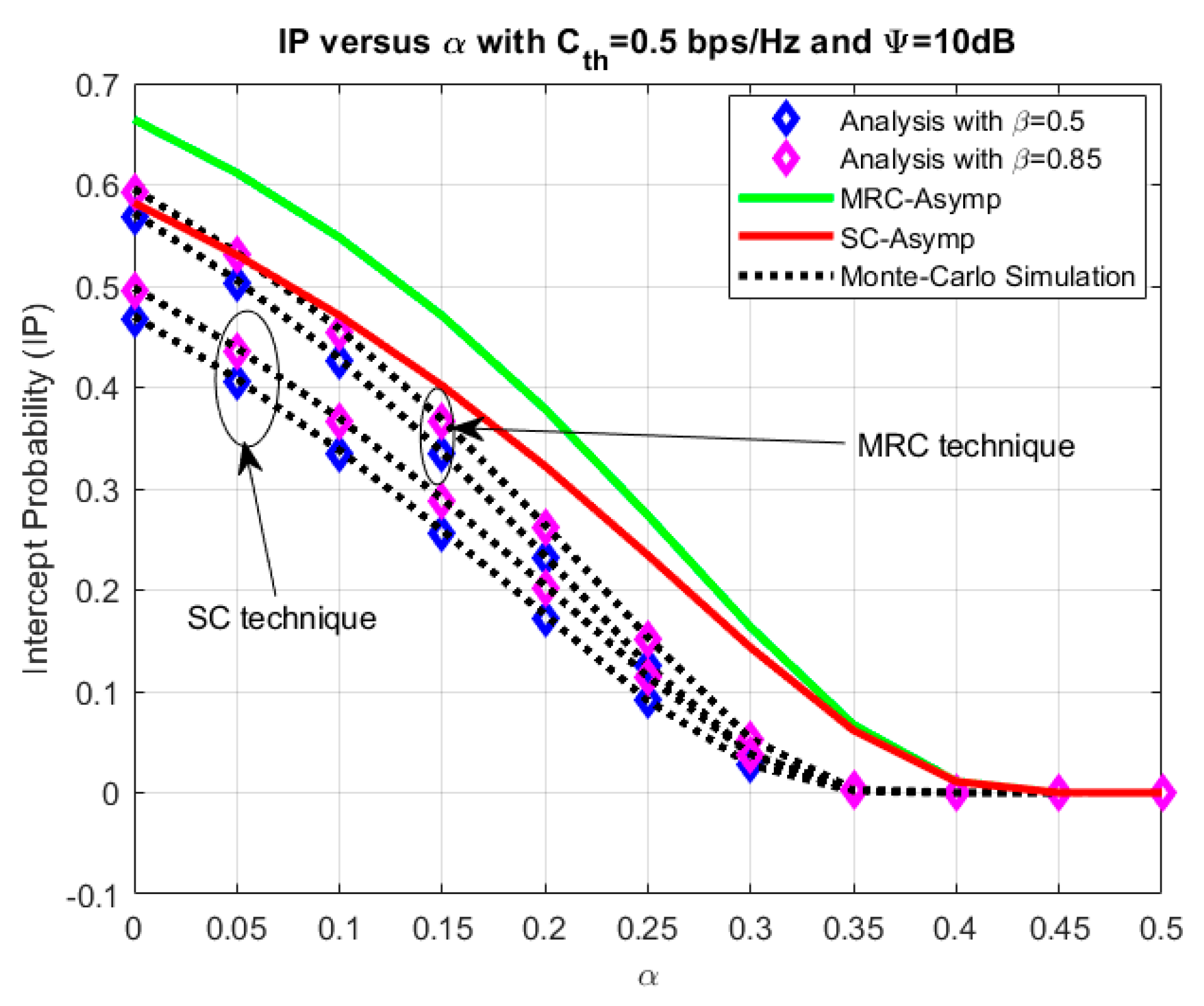
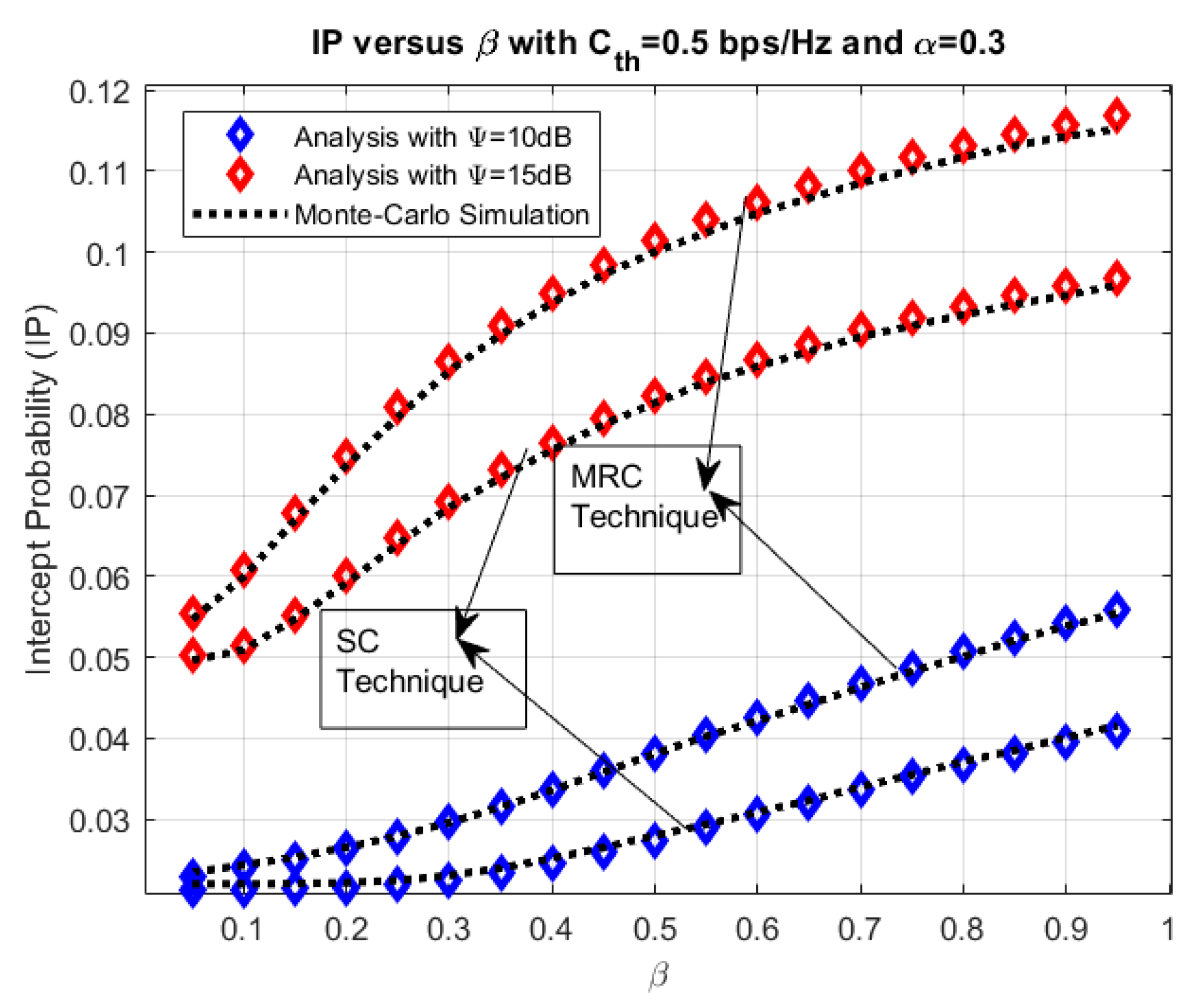
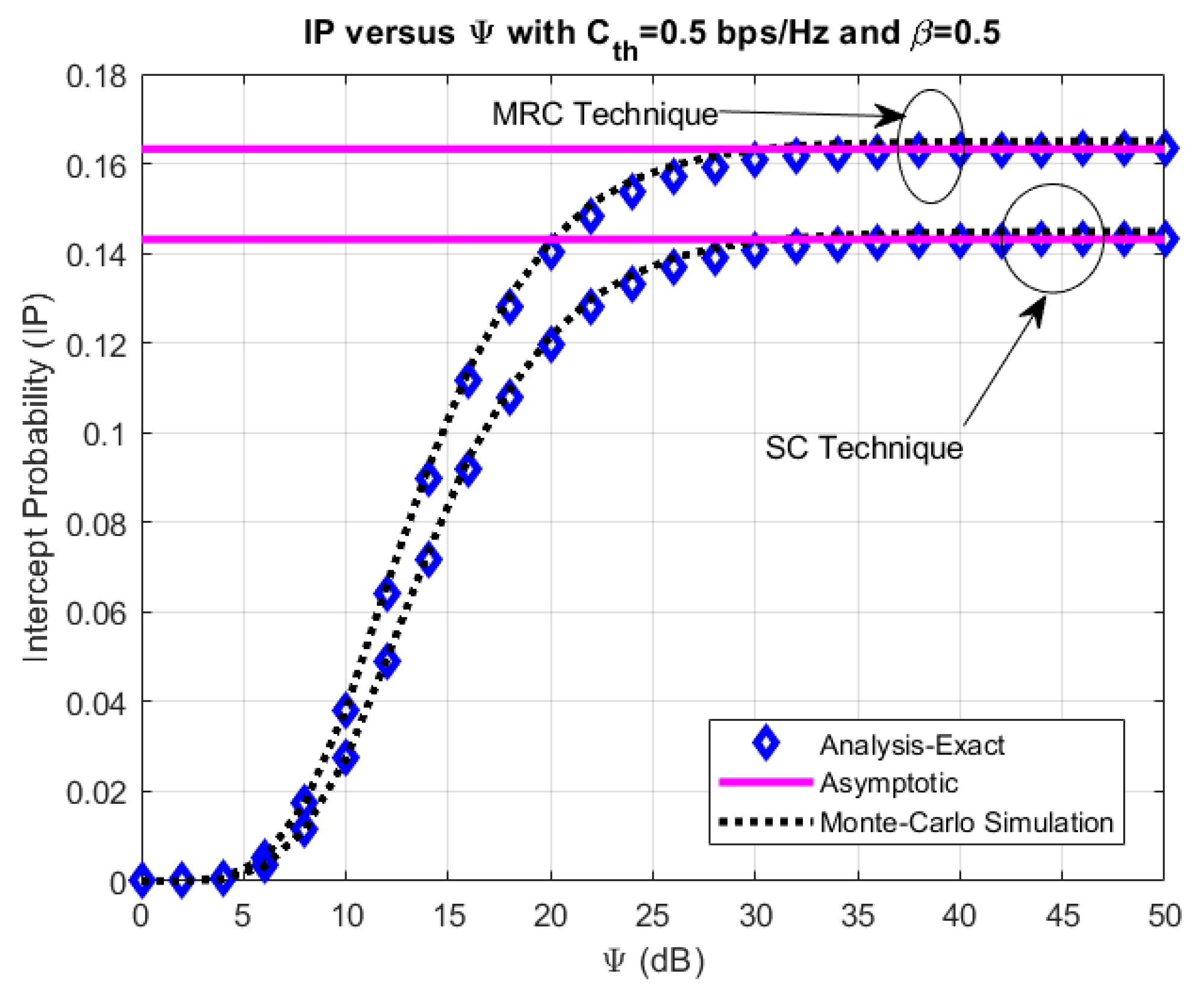
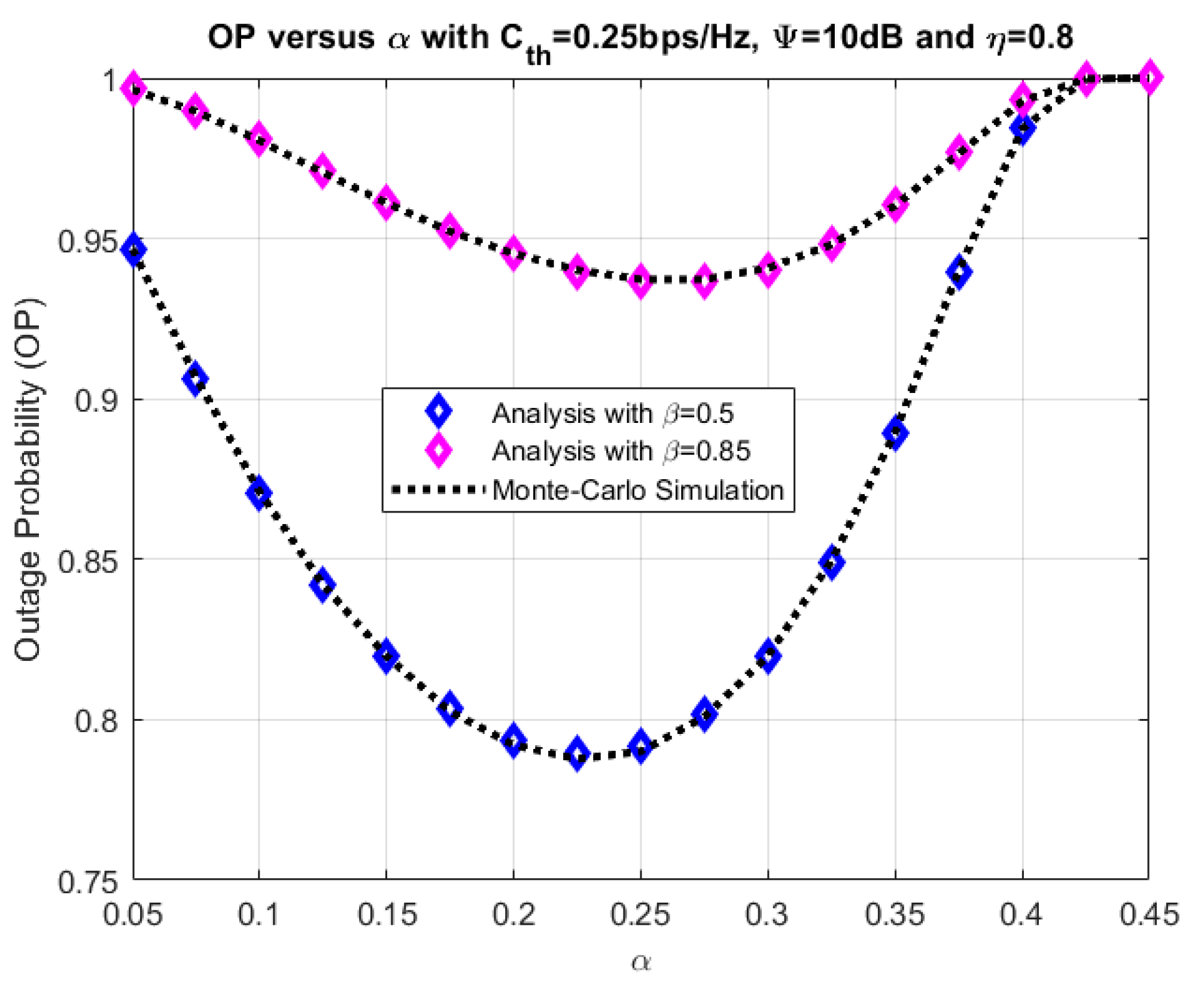
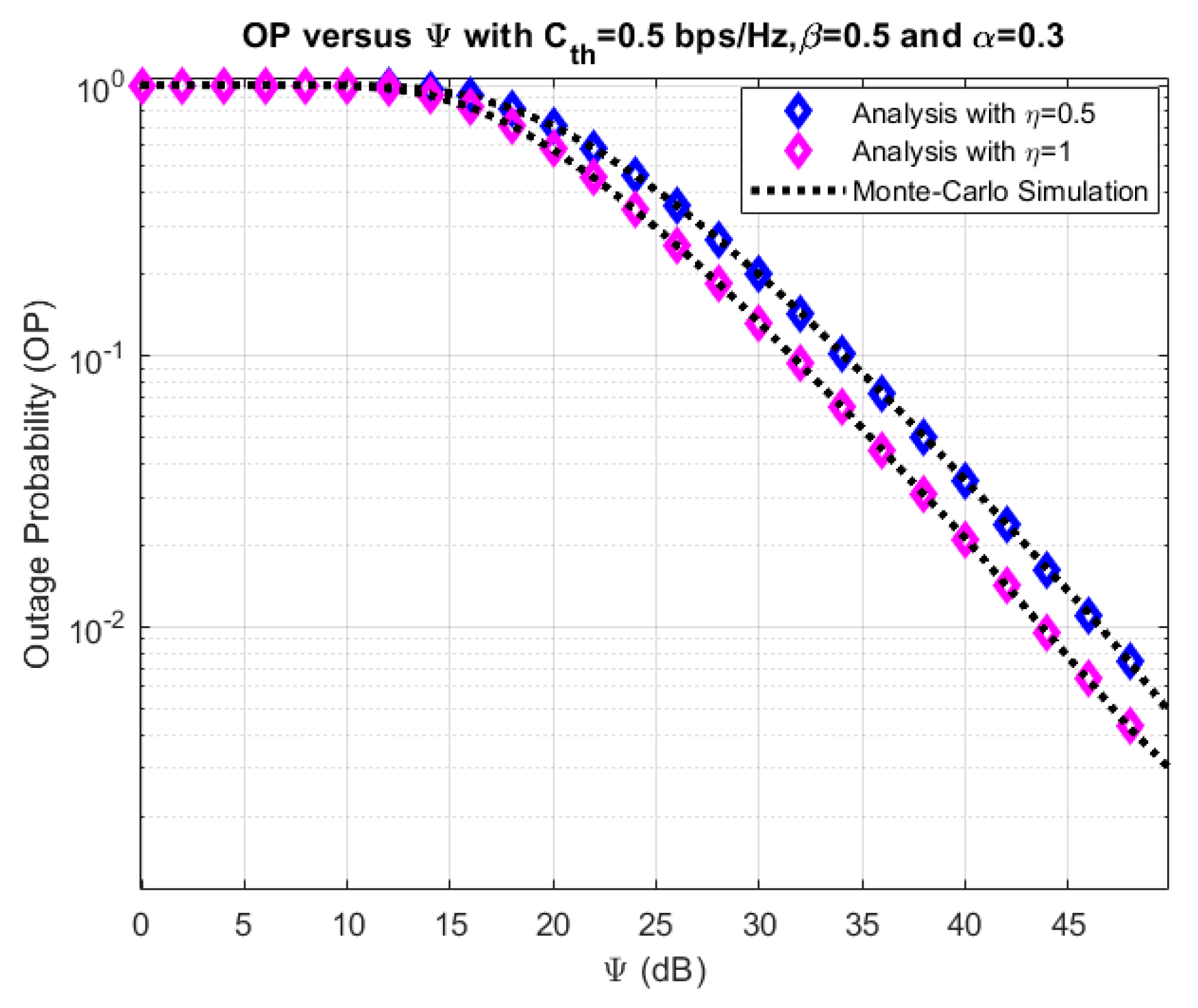
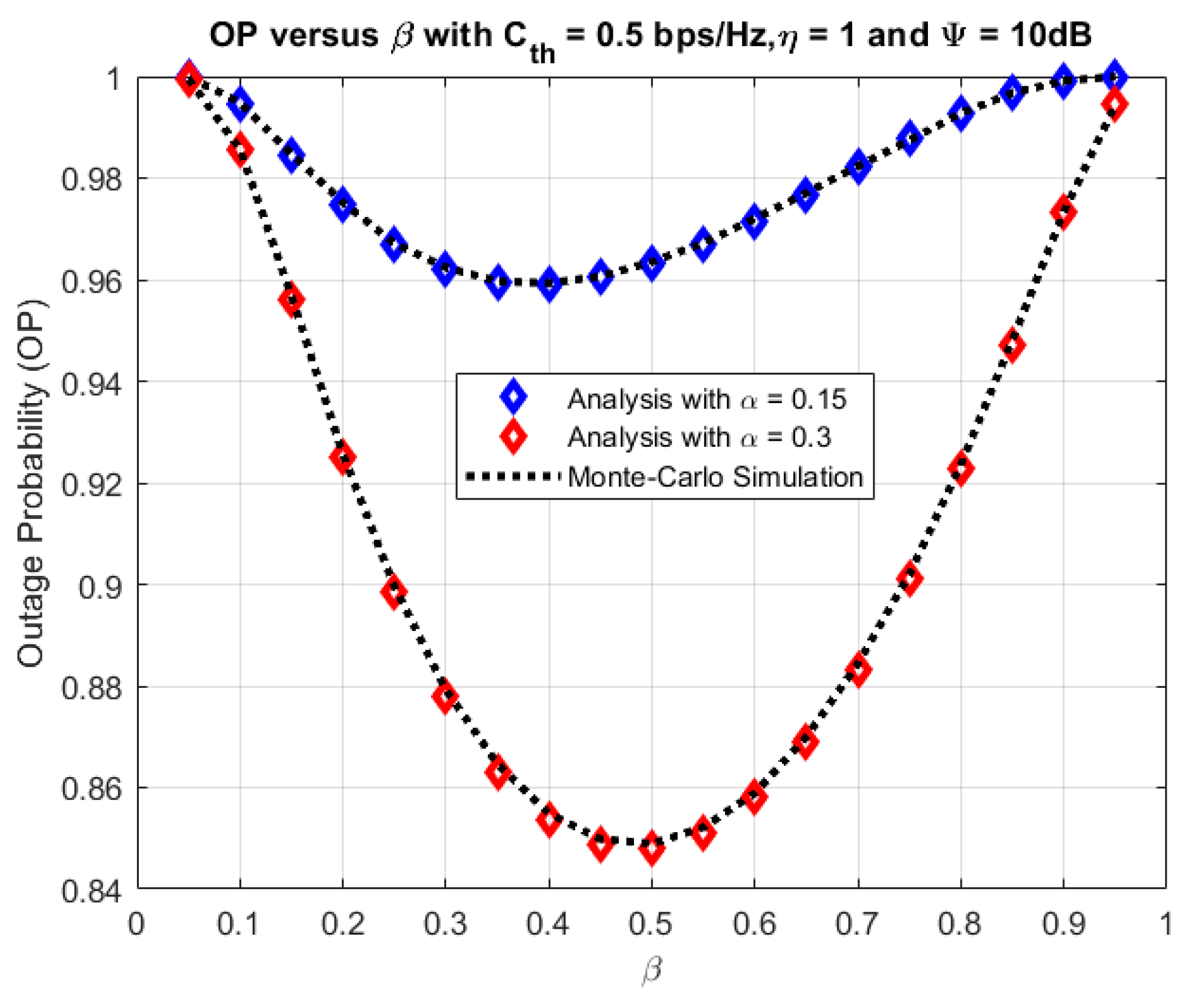
4. Numerical Results and Discussion
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Bi, S.; Ho, C.K.; Zhang, R. Wireless powered communication: Opportunities and challenges. IEEE Commun. Mag. 2015, 53, 117–125. [Google Scholar] [CrossRef]
- Niyato, D.; Kim, D.I.; Maso, M.; Han, Z. Wireless Powered Communication Networks: Research Directions and Technological Approaches. IEEE Wirel. Commun. 2017, 2–11. [Google Scholar] [CrossRef]
- Yu, H.; Lee, H.; Jeon, H. What is 5G? Emerging 5G Mobile Services and Network Requirements. Sustainability 2017, 9, 1848. [Google Scholar] [CrossRef]
- Zhou, X.; Zhang, R.; Ho, C.K. Wireless Information and Power Transfer: Architecture Design and Rate-Energy Tradeoff. IEEE Trans. Commun. 2013, 61, 4754–4767. [Google Scholar] [CrossRef]
- Nguyen, T.N.; Tran, M.; Ha, D.H.; Trang, T.T.; Vozňák, M. Multi-source in DF Cooperative Networks with the PSR Protocol Based Full-duplex Energy Harvesting over a Rayleigh Fading Channel: Performance Analysis. Proc. Est. Acad. Sci. 2019, 68, 264. [Google Scholar] [CrossRef]
- Nguyen, T.N.; Tran, M.; Nguyen, T.L.; Ha, D.H.; Voznak, M. Performance Analysis of a User Selection Protocol in Cooperative Networks with Power Splitting Protocol-Based Energy Harvesting Over Nakagami-m/Rayleigh Channels. Electronics 2019, 8, 448. [Google Scholar] [CrossRef]
- Nguyen, T.; Quang Minh, T.; Tran, P.; Vozňák, M. Energy Harvesting over Rician Fading Channel: A Performance Analysis for Half-Duplex Bidirectional Sensor Networks under Hardware Impairments. Sensors 2018, 18, 1781. [Google Scholar] [CrossRef]
- Nguyen, T.N.; Minh, T.H.Q.; Tran, P.T.; Voznak, M.; Duy, T.T.; Nguyen, T.L.; Tin, P.T. Performance Enhancement for Energy Harvesting Based Two-way Relay Protocols in Wireless Ad-hoc Networks with Partial and Full Relay Selection Methods. Ad Hoc Netw. 2019, 84, 178–187. [Google Scholar] [CrossRef]
- Liu, R.; Maric, I.; Spasojevic, P.; Yates, R.D. Discrete Memoryless Interference and Broadcast Channels with Confidential Messages: Secrecy Rate Regions. IEEE Trans. Inf. Theory 2008, 54, 2493–2507. [Google Scholar] [CrossRef]
- Gopala, P.K.; Lai, L.; El Gamal, H. On the Secrecy Capacity of Fading Channels. IEEE Trans. Inf. Theory 2008, 54, 4687–4698. [Google Scholar] [CrossRef]
- Zhang, J.; Duong, T.Q.; Woods, R.; Marshall, A. Securing Wireless Communications of the Internet of Things from the Physical Layer, An Overview. Entropy 2017, 19, 420. [Google Scholar] [CrossRef]
- Sun, L.; Qinghe, D. A Review of Physical Layer Security Techniques for Internet of Things: Challenges and Solutions. Entropy 2018, 20, 730. [Google Scholar] [CrossRef]
- Sun, L.; Qinghe, D. Physical Layer Security with Its Applications in 5G Networks: A Review. China Commun. 2017, 14, 1–14. [Google Scholar] [CrossRef]
- Yang, N.; Wang, L.; Geraci, G.; Elkashlan, M.; Yuan, J.; Di Renzo, M. Safeguarding 5G Wireless Communication Networks Using Physical Layer Security. IEEE Commun. Mag. 2015, 53, 20–27. [Google Scholar] [CrossRef]
- Kuhestani, A.; Abbas, M.; Mohammadali, M. Joint Relay Selection and Power Allocation in Large-Scale MIMO Systems with Untrusted Relays and Passive Eavesdroppers. IEEE Trans. Inf. Forensics Secur. 2017, 1. [Google Scholar] [CrossRef]
- Hu, L.; Wen, H.; Wu, B.; Pan, F.; Liao, R.F.; Song, H.; Tang, J.; Wang, X. Cooperative Jamming for Physical Layer Security Enhancement in Internet of Things. IEEE Internet Things J. 2018, 5, 219–928. [Google Scholar] [CrossRef]
- Ma, H.; Cheng, J.; Wang, X.; Ma, P. Robust MISO Beamforming with Cooperative Jamming for Secure Transmission from Perspectives of QoS and Secrecy Rate. IEEE Trans. Commun. 2018, 66, 767–780. [Google Scholar] [CrossRef]
- Tran Tin, P.; Nguyen, T.N.; Duy, T.T.; Voznak, M. Secrecy Performance Enhancement for Underlay Cognitive Radio Networks Employing Cooperative Multi-Hop Transmission with and without Presence of Hardware Impairments. Entropy 2019, 21, 217. [Google Scholar] [CrossRef]
- Zhao, R.; Yuan, Y.; Fan, L.; He, Y.-C. Secrecy Performance Analysis of Cognitive Decode-and-Forward Relay Networks in Nakagami-m Fading Channels. IEEE Trans. Commun. 2017, 65, 549–563. [Google Scholar] [CrossRef]
- Tin, P.T.; Minh Nam, P.; Trung Duy, T.; Tran, P.T.; Voznak, M. Secrecy Performance of TAS/SC-Based Multi-Hop Harvest-to-Transmit Cognitive WSNs under Joint Constraint of Interference and Hardware Imperfection. Sensors 2019, 19, 1160. [Google Scholar] [CrossRef]
- Zhao, R.; Lin, H.; He, Y.-C.; Chen, D.-H.; Huang, Y.; Yang, L. Secrecy Performance of Transmit Antenna Selection for MIMO Relay Systems with Outdated CSI. IEEE Trans. Commun. 2018, 2, 546–559. [Google Scholar] [CrossRef]
- Hieu, T.D.; Duy, T.T.; Kim, B.-S. Performance Enhancement for Multi-hop Harvest-to-Transmit WSNs with Path-Selection Methods in Presence of Eavesdroppers and Hardware Noises. IEEE Sens. J. 2018, 2, 5173–5186. [Google Scholar] [CrossRef]
- Liu, F.; Li, J.; Li, S.; Liu, Y.A. Physical Layer Security of Full-Duplex Two-Way AF Relaying Networks with Optimal Relay Selection. In Proceedings of the 2018 IEEE Globecom Workshops (GC Wkshps), Abu Dhabi, United Arab Emirates, 9–13 December 2018. [Google Scholar] [CrossRef]
- Ma, Z.; Lu, Y.; Shen, L.; Liu, Y.; Wang, N. Cooperative Jamming and Relay Beamforming Design for Physical Layer Secure Two-Way Relaying. In Proceedings of the 2018 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery (CyberC), Zhengzhou, China, 18–20 October 2018. [Google Scholar] [CrossRef]
- Ma, Z.; Wang, N.; Lu, Y.; Zhang, D. Relay Power Allocation for Security Enhancement in Three-phase AF Two-way Relaying Systems. In Proceedings of the 2017 9th International Conference on Wireless Communications and Signal Processing (WCSP), Nanjing, China, 11–13 October 2017. [Google Scholar] [CrossRef]
- Shukla, M.K.; Yadav, S.; Purohit, N. Secure Transmission in Cellular Multiuser Two-Way Amplify-and-Forward Relay Networks. IEEE Trans. Veh. Technol. 2018, 67, 11886–11899. [Google Scholar] [CrossRef]
- Xiang, L.; Ng, D.W.K.; Schober, R.; Wong, V.W. Cache-Enabled Physical Layer Security for Video Streaming in Backhaul-Limited Cellular Networks. IEEE Trans. Wirel. Commun. 2018, 17, 736–751. [Google Scholar] [CrossRef]
- Xiang, L.; Ng, D.W.K.; Schober, R.; Wong, V.W. Secure Video Streaming in Heterogeneous Small Cell Networks With Untrusted Cache Helpers. IEEE Trans. Wirel. Commun. 2018, 17, 2645–2661. [Google Scholar] [CrossRef]
- Moualeu, J.M.; Hamouda, W.; Takawira, F. Intercept Probability Analysis of Wireless Networks in the Presence of Eavesdropping Attack with Co-Channel Interference. IEEE Access 2018, 6, 41490–41503. [Google Scholar] [CrossRef]
- Nguyen, T.N.; Tran, P.T.; Voznak, M. Wireless energy harvesting meets receiver diversity: A successful approach for two-way half-duplex relay networks over block Rayleigh fading channel. Comput. Netw. 2020, 172, 107176. [Google Scholar] [CrossRef]
- Nguyen, T.N.; Tran, P.T.; Minh, T.H.Q.; Voznak, M.; Sevcik, L. Two-Way Half Duplex Decode and Forward Relaying Network with Hardware Impairment over Rician Fading Channel: System Performance Analysis. Elektron. Elektrotech. 2018, 24. [Google Scholar] [CrossRef]
- Gu, Y.; Chen, H.; Li, Y.; Vucetic, B. An adaptive transmission protocol for wireless-powered cooperative communications. In Proceedings of the IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 4223–4228. [Google Scholar]
- Ju, H.; Zhang, R. Throughput Maximization in Wireless Powered Communication Networks. IEEE Trans. Wirel. Commun. 2014, 13, 418–428. [Google Scholar] [CrossRef]
- Bhatnagar, M.R. On the Capacity of Decode-and-Forward Relaying over Rician Fading Channels. IEEE Commun. Lett. 2013, 17, 1100–1103. [Google Scholar] [CrossRef]
- Jeffrey, A.; Zwillinger, D. (Eds.) Table of Integrals, Series, and Products; Springer: New York, NY, USA, 2015. [Google Scholar] [CrossRef]
- Nasir, A.A.; Zhou, X.; Durrani, S.; Kennedy, R.A. Relaying Protocols for Wireless Energy Harvesting and Information Processing. IEEE Trans. Wirel. Commun. 2013, 12, 3622–3636. [Google Scholar] [CrossRef]
- Tan, N.; Nguyen, T.H.Q.; Minh, P.; Tran, T.; Voznak, M. Adaptive Energy Harvesting Relaying Protocol for Two-Way Half Duplex System Network over Rician Fading Channels. Wirel. Commun. Mob. Comput. 2018, 2018, 10. [Google Scholar]
- Nguyen, T.; Tin, P.T.; Ha, D.; Voznak, M.; Tran, P.; Tran, M.; Nguyen, T.-L. Hybrid TSR–PSR Alternate Energy Harvesting Relay Network over Rician Fading Channels: Outage Probability and SER Analysis. Sensors 2018, 18, 3839. [Google Scholar] [CrossRef] [PubMed]
- Tin, P.T.; Dinh, B.H.; Nguyen, T.N.; Ha, D.H.; Trang, T.T. Power Beacon-Assisted Energy Harvesting Wireless Physical Layer Cooperative Relaying Networks: Performance Analysis. Symmetry 2020, 12, 106. [Google Scholar] [CrossRef]
- Park, J.-H.; Jeon, Y.-S.; Han, S. Energy Beamforming for Wireless Power Transfer in MISO Heterogeneous Network with Power Beacon. IEEE Commun. Lett. 2017, 21, 1163–1166. [Google Scholar] [CrossRef]
- Tin, P.T.; Nguyen, T.N.; Tran, M.; Trang, T.T.; Sevcik, L. Exploiting Direct Link in Two-Way Half-Duplex Sensor Network over Block Rayleigh Fading Channel: Upper Bound Ergodic Capacity and Exact SER Analysis. Sensors 2020, 20, 1165. [Google Scholar] [CrossRef]
- Nguyen, T.N.; Tran, M.; Nguyen, T.L.; Voznak, M. Adaptive Relaying Protocol for Decode and Forward Full-Duplex System over Rician Fading Channel: System Performance Analysis. China Commun. 2019, 16, 92–102. [Google Scholar]
- Tin, P.T.; Nguyen, T.N.; Sang, N.Q.; Duy, T.T.; Tran, P.T.; Voznak, M. Rateless Codes-Based Secure Communication Employing Transmit Antenna Selection and Harvest-To-Jam under Joint Effect of Interference and Hardware Impairments. Entropy 2019, 21, 700. [Google Scholar] [CrossRef]
- Nguyen, T.N.; Tran, M.; Nguyen, T.-L.; Ha, D.-H.; Voznak, M. Multisource Power Splitting Energy Harvesting Relaying Network in Half-Duplex System over Block Rayleigh Fading Channel: System Performance Analysis. Electronics 2019, 8, 67. [Google Scholar] [CrossRef]
- Valenta, C.R.; Durgin, G.D. Harvesting wireless power: Survey of energy-harvester conversion efficiency infar-field, wireless power transfer systems. IEEE Microw. Microw. Mag. 2014, 15, 108–120. [Google Scholar]
- Phan, V.D.; Nguyen, T.N.; Tran, M.; Trang, T.T.; Voznak, M.; Ha, D.H.; Nguyen, T.L. Power Beacon-Assisted Energy Harvesting in a Half-Duplex Communication Network under Co-Channel Interference over a Rayleigh Fading Environment: Energy Efficiency and Outage Probability Analysis. Energies 2019, 12, 2579. [Google Scholar] [CrossRef]
- Nguyen, T.N.; Tran, M.; Ha, D.-H.; Nguyen, T.-L.; Voznak, M. Energy harvesting based two-way full-duplex relaying network over a Rician fading environment: performance analysis. P. Est. Acad. Sci. 2019, 68, 111. [Google Scholar] [CrossRef]
- Nguyen, T.N.; Tran, M.; Tran, P.T.; Tin, P.T.; Nguyen, T.-L.; Ha, D.-H.; Voznak, M. On the Performance of Power Splitting Energy Harvested Wireless Full-Duplex Relaying Network with Imperfect CSI over Dissimilar Channels. Security and Communication Networks 2018, 2018, 1–11. [Google Scholar] [CrossRef]

© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hoang An, N.; Tran, M.; Nguyen, T.N.; Ha, D.-H. Physical Layer Security in a Hybrid TPSR Two-Way Half-Duplex Relaying Network over a Rayleigh Fading Channel: Outage and Intercept Probability Analysis. Electronics 2020, 9, 428. https://doi.org/10.3390/electronics9030428
Hoang An N, Tran M, Nguyen TN, Ha D-H. Physical Layer Security in a Hybrid TPSR Two-Way Half-Duplex Relaying Network over a Rayleigh Fading Channel: Outage and Intercept Probability Analysis. Electronics. 2020; 9(3):428. https://doi.org/10.3390/electronics9030428
Chicago/Turabian StyleHoang An, Ngo, Minh Tran, Tan N. Nguyen, and Duy-Hung Ha. 2020. "Physical Layer Security in a Hybrid TPSR Two-Way Half-Duplex Relaying Network over a Rayleigh Fading Channel: Outage and Intercept Probability Analysis" Electronics 9, no. 3: 428. https://doi.org/10.3390/electronics9030428
APA StyleHoang An, N., Tran, M., Nguyen, T. N., & Ha, D.-H. (2020). Physical Layer Security in a Hybrid TPSR Two-Way Half-Duplex Relaying Network over a Rayleigh Fading Channel: Outage and Intercept Probability Analysis. Electronics, 9(3), 428. https://doi.org/10.3390/electronics9030428





