An Anonymous Mutual Authentication Scheme for RFID-Based Transportation System
Abstract
1. Introduction
- A new retrieval method is adopted by the server. For solving the aforementioned privacy problem, we design a new retrieval method to assist the server in searching for the authenticated information, which initially allows multiple readers to identify different tags at the same time. Based on this retrieval method, we can predefine the scope of the tags that each reader recognizes, which is also a method to protect data privacy. That is to say, the reader is only permitted to recognize authorized vehicles.
- An anonymous RFID authentication scheme is proposed for vehicles in a transportation system. To resist attack after losing a reader, the authentication protocol innovatively confirms the legitimacy of a reader’s identity. By requiring the reader to update its password periodically, the server can ensure the running condition of the reader after verifying the updated response. Thus, the lost reader cannot be used to attack our protocol and may be nullified. Considering that the tag is limited, the proposed protocol adopts some lightweight operations. In experimental comparisons with related protocols, we prove that the proposed scheme consumes fewer computing and communication resources in relation to tags.
- The new protocol is proven to be secure with the Burrows–Abadi–Needham (BAN) logic [12] proof method and security discussion. Firstly, we employ a formal analysis tool BAN logic to demonstrate the security of key agreement and mutual authentication. Secondly, we discuss that the protocol achieves multiple safety goals, including reader lost resistance, anonymity un-traceability, mutual authentication, forward security, replay attack, and de-synchronization attack resistance. Thirdly, we compare the secure property of our protocol with some related protocols.
2. Related Work
3. Problem Statement
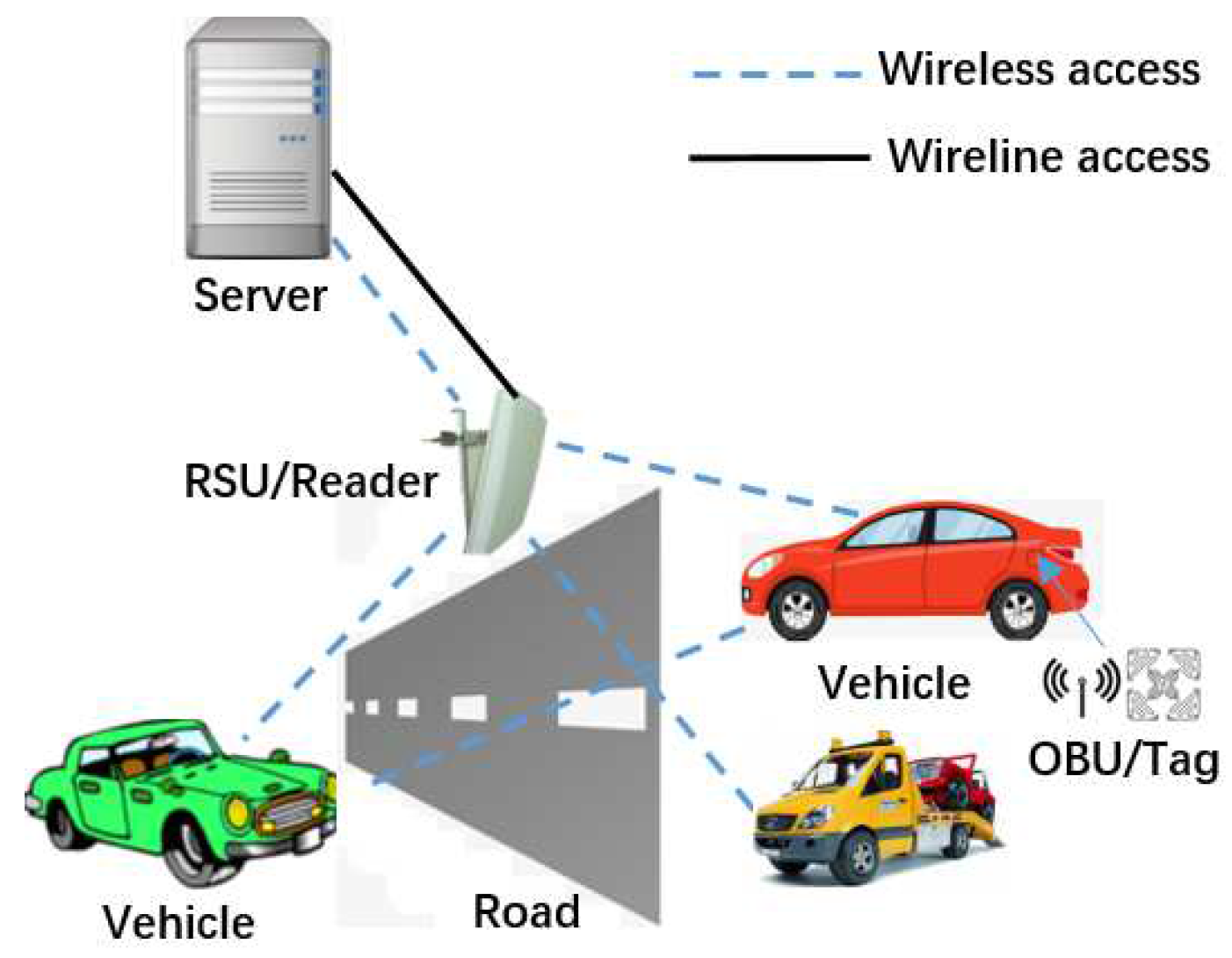
3.1. System Model
3.2. Security Goals
4. The Scheme
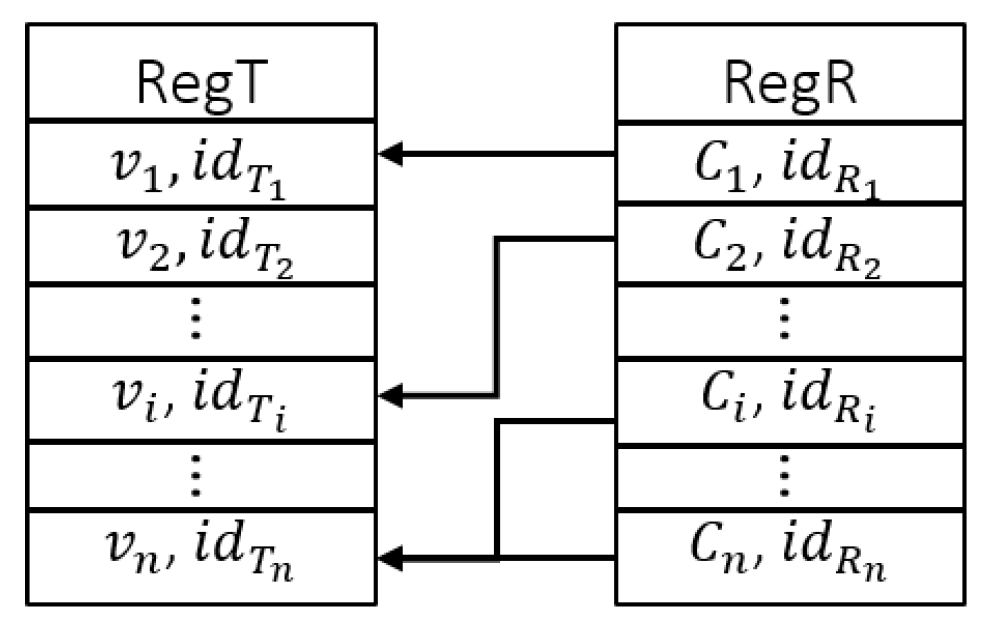
4.1. Initialization Phase
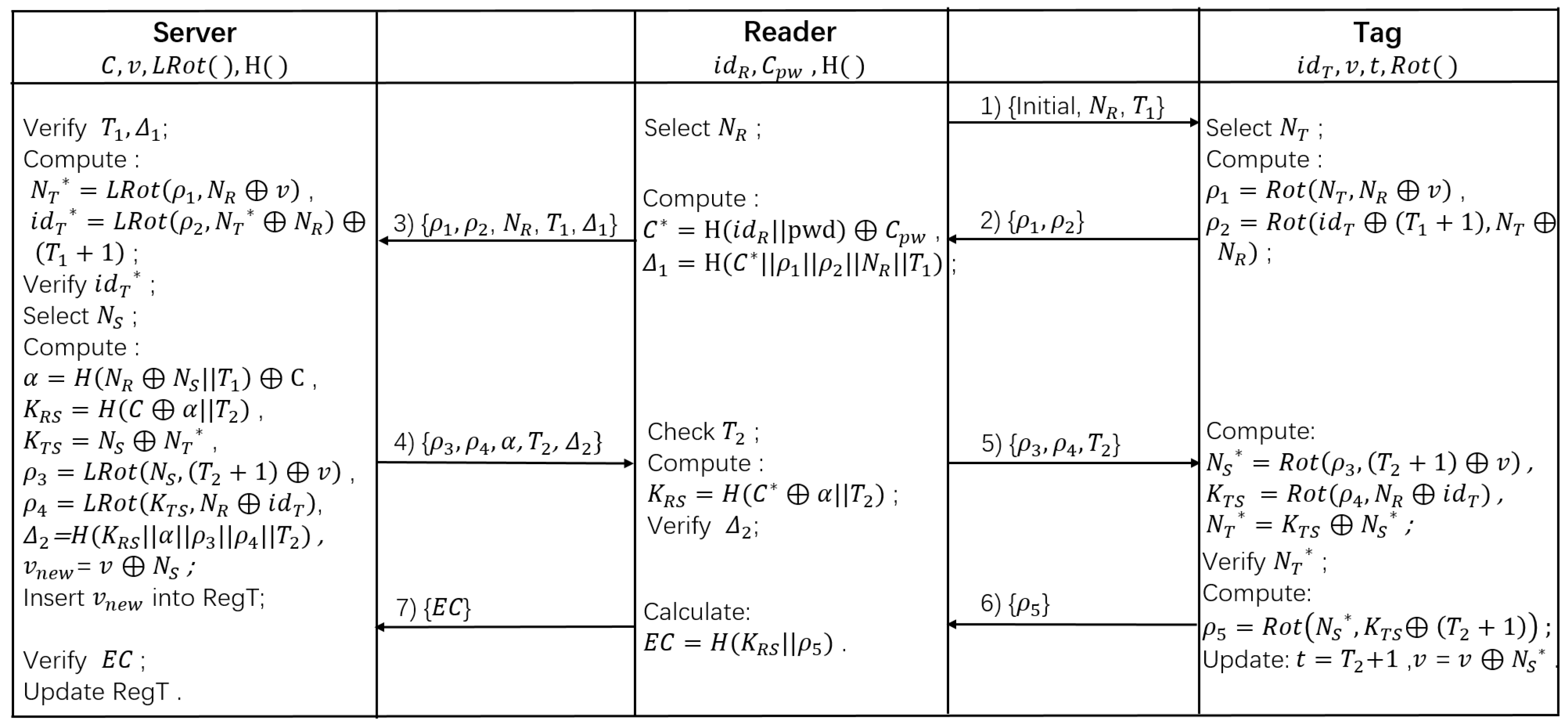
4.2. Authentication Phase
4.3. Password Updated Phase
5. Security Analysis
5.1. Security Proof
5.1.1. Notations
- : P believes that a statement X is authentic.
- : P sent the statement X before.
- : P once received that statement X.
- : P has jurisdiction over that statement or a notation X.
- : The statement or notation X that has never been sent is fresh.
- : This statement is obtained by using a secret key k to encrypt X or combining X with a secret value k.
- : P only shares the same secret value Y with Q and the others that P or Q believes.
- : There is a secret key k only known by P and Q.
5.1.2. Rules
5.1.3. Descriptions
5.1.4. Assumptions
5.1.5. Goals
5.1.6. Proof
5.2. Security Discussion
5.3. Property Comparison
6. Performance Analysis And Evaluation
6.1. Performance Analysis
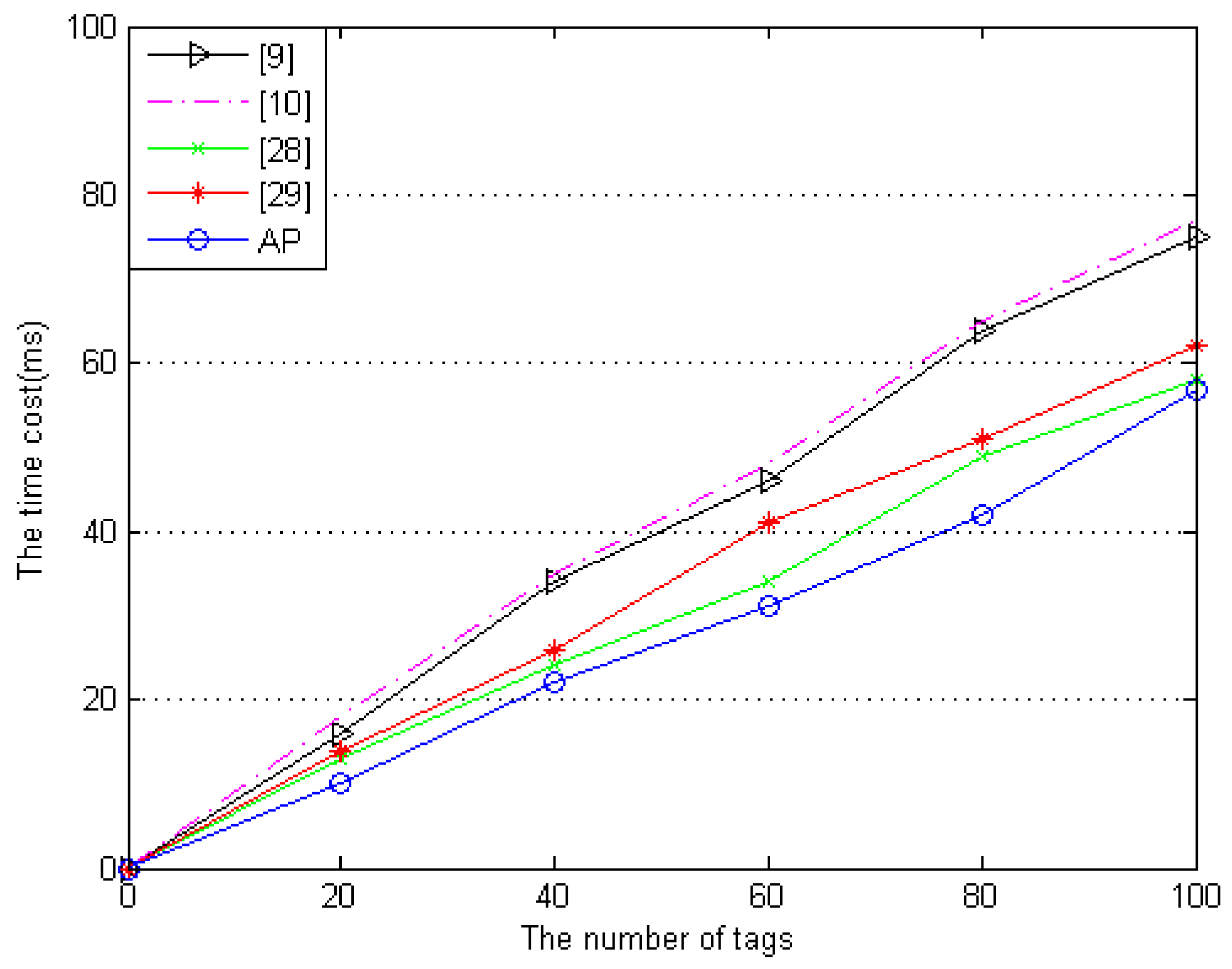
6.2. Performance Evaluation
7. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Chen, D.; Zhang, N.; Qin, Z.; Mao, X.; Qin, Z.; Shen, X.; Li, X. S2M: A Lightweight Acoustic Fingerprints-Based Wireless Device Authentication Protocol. IEEE Internet Things J. 2017, 4, 88–100. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S.; Xu, B.; Huang, X. An efficient identity-based conditional privacy-preserving authentication scheme for vehicular ad hoc networks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2681–2691. [Google Scholar] [CrossRef]
- Tan, C.C.; Sheng, B.; Li, Q. Secure and Serverless RFID Authentication and Search Protocols. IEEE Trans. Wirel. Commun. 2008, 7, 1400–1407. [Google Scholar] [CrossRef]
- Zhou, Z.; Wang, P.; Li, Z. A quadratic residue-based RFID authentication protocol with enhanced security for TMIS. J. Ambient Intell. Humaniz. Comput. 2019, 10, 3603–3615. [Google Scholar] [CrossRef]
- Fatty, M.S.; Ruhul, A. A privacy-preserving RFID authentication protocol based on El-Gamal cryptosystem for secure TMIS. Inf. Sci. 2020, 527, 382–393. [Google Scholar]
- Prosanta, G.; Amin, R.; Hafizul, S.; Neeraj, K.; Vinod, K.B. Lightweight and privacy-preserving RFID authentication scheme for distributed IoT infrastructure with secure localization services for smart city environment. Future Gener. Comput. Syst. 2018, 83, 629–637. [Google Scholar]
- Boursianis, A.; Samaras, T.; Polycarpou, A.; Sahalos, J. A UHF RFID reader antenna for searching tagged items. In Proceedings of the 2014 IEEE RFID Technology and Applications Conference (RFID-TA), Tampere, Finland, 8–9 September 2014; pp. 193–198. [Google Scholar]
- Guo, Z.; Ngai, E.; Yang, C.; Liang, X. An RFID-based intelligent decision support system architecture for production monitoring and scheduling in a distributed manufacturing environment. Int. J. Prod. Econ. 2015, 159, 16–28. [Google Scholar] [CrossRef]
- Xie, W.; Xie, L.; Zhang, C.; Zhang, Q.; Tang, C. Cloud-based RFID authentication. In Proceedings of the 2013 IEEE International Conference on RFID (RFID), Penang, Malaysia, 30 April–2 May 2013; pp. 168–175. [Google Scholar]
- Fan, K.; Jiang, W.; Li, H.; Yang, Y. Lightweight RFID Protocol for Medical Privacy Protection in IoT. IEEE Trans. Ind. Inform. 2018, 14, 1656–1665. [Google Scholar] [CrossRef]
- Sharma, S.; Kaul, A. VANETs Cloud: Architecture, Applications, Challenges, and Issues. Arch. Comput. Meth. Eng. 2020, 1–22. [Google Scholar] [CrossRef]
- Burrows, M.; Abadi, M.; Needham, R. A Logic of Authentication. ACM Trans. Comput. Syst. 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Fuad, A.G.; Anazida, Z.; Mohd, A.M.; Murad, A.R.; Faisal, S. Detecting Bogus Information Attack in Vehicular Ad Hoc Network: A Context-Aware Approach. Procedia Comput. Sci. 2019, 163, 180–189. [Google Scholar]
- Lu, Z.; Qu, G.; Liu, Z. A Survey on Recent Advances in Vehicular Network Security, Trust, and Privacy. IEEE Trans. Intell. Transp. Syst. 2019, 70, 760–776. [Google Scholar] [CrossRef]
- Tangade, S.; Manvi, S.S.; Pascal, L. Trust Management Scheme Based on Hybrid Cryptography for Secure Communications in VANETs. IEEE Trans. Veh. Technol. 2020, 69, 5232–5243. [Google Scholar] [CrossRef]
- Manik, L.D.; Pardeep, K.; Andrew, M. Secure and Privacy-Preserving RFID Authentication Scheme for Internet of Things Applications. Wirel. Pers. Commun. 2020, 110, 339–353. [Google Scholar]
- Ding, K.; Jiang, P.; Su, S. RFID-enabled social manufacturing system for inter-enterprise monitoring and dispatching of integrated production and transportation tasks. Robot. Comput. Integr. Manuf. 2018, 49, 120–133. [Google Scholar] [CrossRef]
- Jiang, Q.; Ni, J.; Ma, J.; Yang, L.; Shen, X. Integrated Authentication and Key Agreement Framework for Vehicular Cloud Computing. IEEE Netw. 2018, 32, 28–35. [Google Scholar] [CrossRef]
- Fan, K.; Jiang, W.; Luo, Q.; Li, H.; Yang, Y. Cloud-based RFID mutual authentication scheme for efficient privacy preserving in IoV. J. Frankl. Inst. 2019. [Google Scholar] [CrossRef]
- Pedro, P.L.; Agustin, O.; Mitrokotsa, A.; Lubbe, J. A comprehensive RFID solution to enhance inpatient medication safety. Int. J. Med. Inform. 2011, 80, 13–24. [Google Scholar]
- Liu, H.; Ning, H.; Zhang, Y.; He, D.; Xiong, Q.; Yang, L.T. Grouping-proofs-based authentication protocol for distributed RFID systems. IEEE Trans. Parallel Distrib. Syst. 2012, 24, 1321–1330. [Google Scholar] [CrossRef]
- Sun, H.M.; Ting, W.C.; Wang, K.H. On the security of Chien’s ultralightweight RFID authentication protocol. IEEE Trans. Dependable Secur. Comput. 2009, 8, 315–317. [Google Scholar] [CrossRef]
- Tian, Y.; Chen, G.L.; Li, J.H. A New Ultralightweight RFID Authentication Protocol with Permutation. IEEE Commun. Lett. 2012, 16, 702–705. [Google Scholar] [CrossRef]
- Li, N.; Mu, Y.; Susilo, W.; Guo, F.; Varadharajan, V. Privacy-preserving authorized RFID authentication protocols. In International Workshop on Radio Frequency Identification: Security and Privacy Issues; Springer: Cham, Switzerland, 2015; pp. 108–122. [Google Scholar]
- Song, B.; Mitchell, C.J. RFID authentication protocol for low-cost tags. In Proceedings of the First ACM Conference on Wireless Network Security, Alexandria, VA, USA, 31 March–2 April 2008; pp. 140–147. [Google Scholar]
- Chou, J.S. An efficient mutual authentication RFID scheme based on elliptic curve cryptography. J. Supercomput. 2014, 70, 75–94. [Google Scholar] [CrossRef]
- Zhang, Z.; Qi, Q. An efficient RFID authentication protocol to enhance patient medication safety using elliptic curve cryptography. J. Med. Syst. 2014, 38, 47–54. [Google Scholar] [CrossRef] [PubMed]
- Abughazalah, S.; Markantonakis, K.; Mayes, K. Secure improved cloud-based RFID authentication protocol. In Data Privacy Management, Autonomous Spontaneous Security, and Security Assurance; Springer: Cham, Switzerland, 2014; pp. 147–164. [Google Scholar]
- Xiao, H.; Alshehri, A.A.; Christianson, B. A cloud-based RFID authentication protocol with insecure communication channels. In Proceedings of the 2016 IEEE Trustcom/BigDataSE/ISPA, Tianjin, China, 23–26 August 2016; pp. 332–339. [Google Scholar]
- Chien, H.Y.; Chen, C.H. Mutual authentication protocol for RFID conforming to EPC Class 1 Generation 2 standards. Comput. Stand. Interfaces 2007, 29, 254–259. [Google Scholar] [CrossRef]
- Fan, K.; Gong, Y.; Liang, C.; Li, H.; Yang, Y. Lightweight and ultralightweight RFID mutual authentication protocol with cache in the reader for IoT in 5G. Secur. Commun. Netw. 2016, 9, 3095–3104. [Google Scholar] [CrossRef]
- Aghili, S.F.; Mala, H.; Kaliyar, P.; Conti, M. SecLAP: Secure and lightweight RFID authentication protocol for Medical IoT. Future Gener. Comput. Syst. 2019, 101, 621–634. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Kuseler, T.; Lami, I.A. Using geographical location as an authentication factor to enhance mCommerce applications on smartphones. Int. J. Comput. Sci. Secur. (IJCSS) 2012, 6, 277–287. [Google Scholar]
- Odelu, V.; Das, A.K.; Goswami, A. A Secure Biometrics-Based Multi-Server Authentication Protocol Using Smart Cards. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1953–1966. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P. Two Birds with One Stone: Two-Factor Authentication with Security Beyond Conventional Bound. IEEE Trans. Dependable Secur. Comput. 2018, 15, 708–722. [Google Scholar] [CrossRef]
- Zhang, J.; Zhang, F.T.; Huang, X.; Liu, X. Leakage-Resilient Authenticated Key Exchange for Edge Artificial Intelligence. IEEE Trans. Dependable Secur. Comput. 2020. [Google Scholar] [CrossRef]
- Dziembowski, S.; Faust, S. Leakage-Resilient Cryptography from the Inner-Product Extractor. In Advances in Cryptology—ASIACRYPT 2011; Lee, D.H., Wang, X., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 702–721. [Google Scholar]
| Symbol | Definition |
|---|---|
| A reader’s identity, a tag’s identity | |
| A reader, a tag, a server | |
| Reader’s next session key shared with a server | |
| Tag’s next session key shared with a server | |
| A number selected randomly by a server | |
| A number selected randomly by a reader | |
| A number selected randomly by a tag | |
| Calculate the number of non-zero bits in y | |
| The cyclic left shift bits operation | |
| The cyclic right shift bits operation | |
| A secure one-way hash function | |
| ⊕ | The exclusive or operation |
| The concatenation operation |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ji, S.; Liu, S.; Wang, C.; Qi, R.; Shen, J. An Anonymous Mutual Authentication Scheme for RFID-Based Transportation System. Electronics 2020, 9, 2167. https://doi.org/10.3390/electronics9122167
Ji S, Liu S, Wang C, Qi R, Shen J. An Anonymous Mutual Authentication Scheme for RFID-Based Transportation System. Electronics. 2020; 9(12):2167. https://doi.org/10.3390/electronics9122167
Chicago/Turabian StyleJi, Sai, Shuai Liu, Chen Wang, Rongxin Qi, and Jian Shen. 2020. "An Anonymous Mutual Authentication Scheme for RFID-Based Transportation System" Electronics 9, no. 12: 2167. https://doi.org/10.3390/electronics9122167
APA StyleJi, S., Liu, S., Wang, C., Qi, R., & Shen, J. (2020). An Anonymous Mutual Authentication Scheme for RFID-Based Transportation System. Electronics, 9(12), 2167. https://doi.org/10.3390/electronics9122167







