A New Card-Linked Loyalty Program: Estimated and Anticipated Benefits for Payment Transaction Parties
Abstract
1. Introduction
- Hard (tangible) benefits: financial incentives like discounts, free hotel stays, vouchers (coupons, see [7]), tickets,
- Soft (intangible) rewards: non-financial like preferential treatment, special events, an elevated sense of status, services, entertainment, priority check-in, and so on.
2. An Evolution Towards Card-Linked Loyalty Programs
- Type I, where members take an additional discount at register,
- Type II, where members take 1 free when they buy n units,
- Type III, where members receive rebates or points based on cumulative purchase,
- Type IV, where members receive targeted offers and mailings.
- It does not interrupt a payment process; Loyalty should be a part of the payment process and should not interrupt it [24],
- It will work with payment card emulated via a smartphone through the NFC interface,
- It does not need to enroll manually or online: sign up to the Loyalty Program during your payment,
- It does not require to download dedicated applications, carry another plastic card or print off rewards or coupons (rewards can be redeemed during the payment process).
- Reward attribution; the ability to attribute rewards to the customer immediately, such as discounts or free items,
- Customer knowledge generation; the ability to generate useful knowledge about the customer and to make it instantly available at the payment terminal,
- Relationship building; the ability to establish a long-term relationship that is not necessarily based on financial rewards, but rather on soft benefits like preferential treatment.
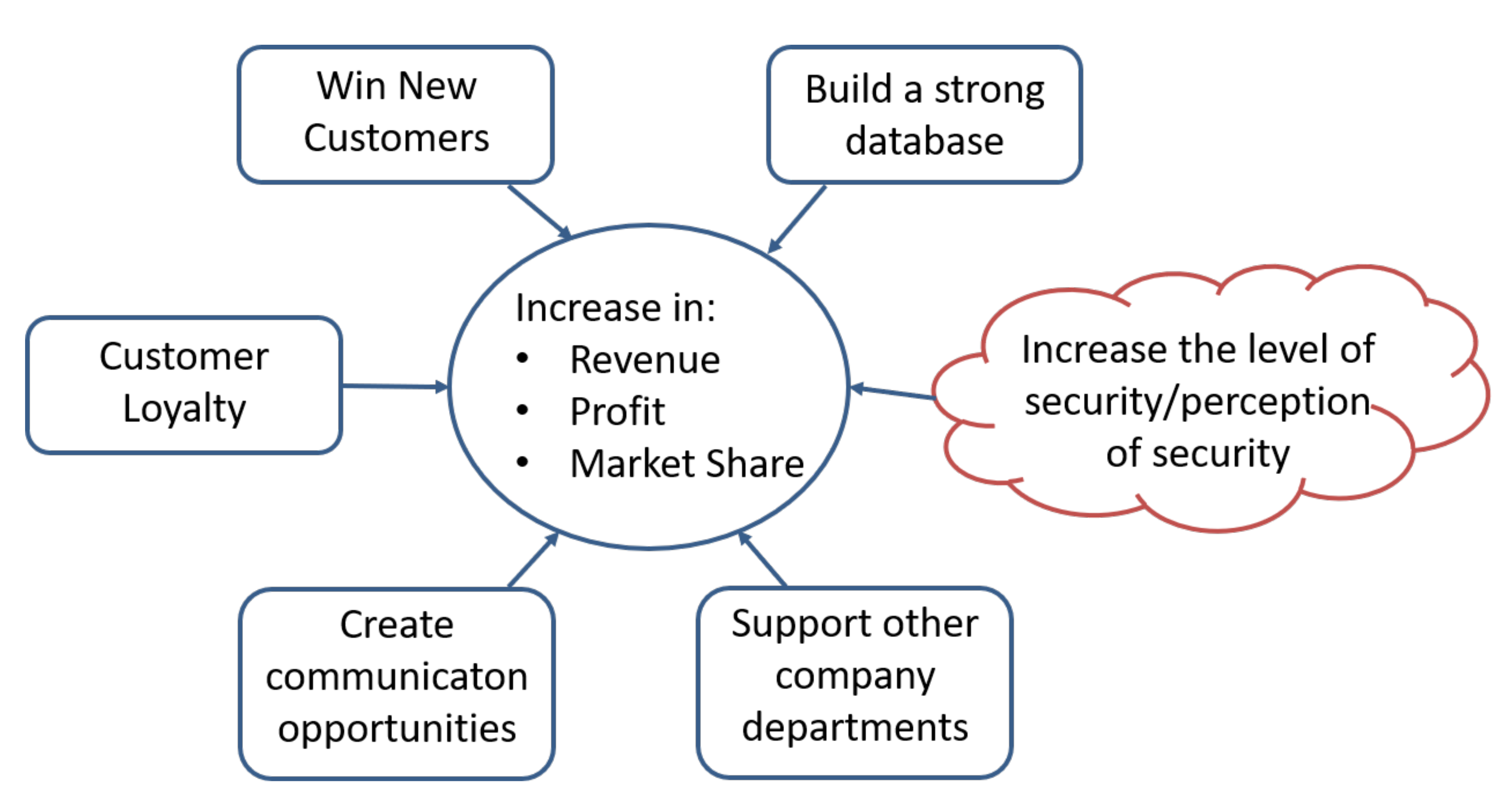
- Win a new customer. This can be done in two ways [18]. Firstly, satisfied LP members increase their word of mouth advertising. Secondly, the value of the LP benefits themselves is so attractive that non–customers join the loyalty program. These new members will eventually try the product and will continue using it after a satisfactory initial experience.
- Build a strong database. A correctly designed loyalty program allows building a valuable database containing socio-demographic data together with information on purchase behavior (purchase frequency, brand usage) and preference data. This information is normally very difficult to obtain and used in a professional way can be a strategic weapon,
- Support other company departments. The database created in the scope of the previous point can assist other departments such as R&D, product marketing, or market research,
- Create communication opportunities. It allows for creating direct and personalized communication to the customer.
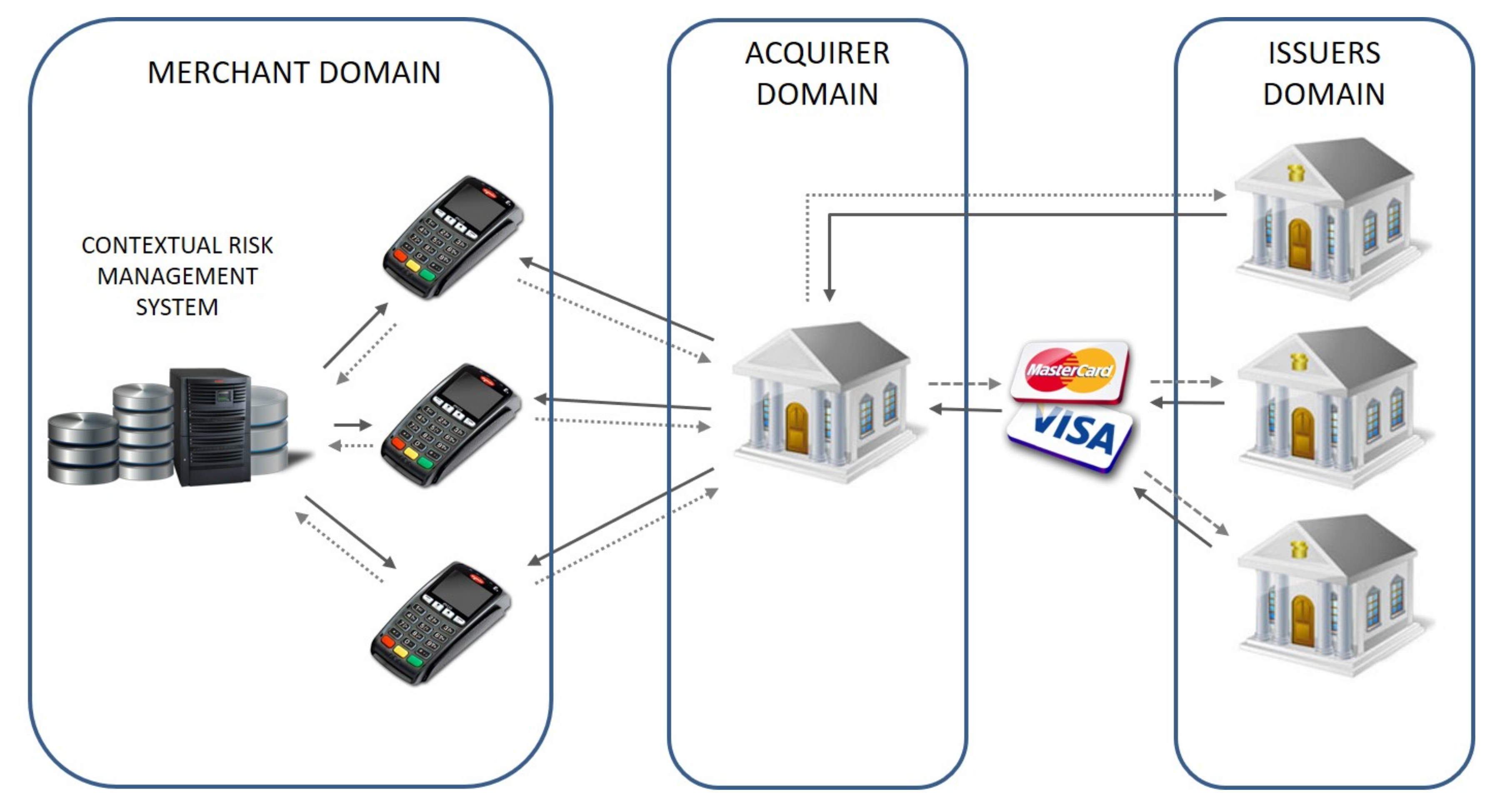
3. Contextual Risk Management System for Card-Present Payment Transactions
- What you have—a payment card that cannot be cloned (in case of modern chip cards),
- What you know—a secret PIN code.
- The number of transactions made with lost or stolen cards accounts for approximately 13% of all fraudulent transactions recorded by Issuers,
- According to acquirers, the number of fraudulent transaction accounts for 0.001% of all processed transactions.
- The system is responsible for making the dynamic decision whether the cardholder verification should be performed during the certain transaction or not,
- It must be able to use some contextual factors in the decision-making process,
- It must maintain the level of risk caused by the usage of the system,
- The solution must be able to work with transactions performed using the contact and contactless payment cards,
- The whole solution must operate on tokenized card data ([53]). Thanks to that it would not be a subject of Payment Card Industry Data Security Standard (PCI DSS, [54]) and requirements caused by General Data Protection Regulation (GDPR, [55]) are less strict because tokens are treated as pseudonymized personal data.
- Payment terminal reads card’s data, tokenizes it and sends a request containing transaction amount and card token to the CRMS,
- CRMS runs the decision-making algorithm and decides whether the cardholder verification step should be performed or not,
- CRMS sends the response to the terminal, and the transaction is processed according to the system’s decision.
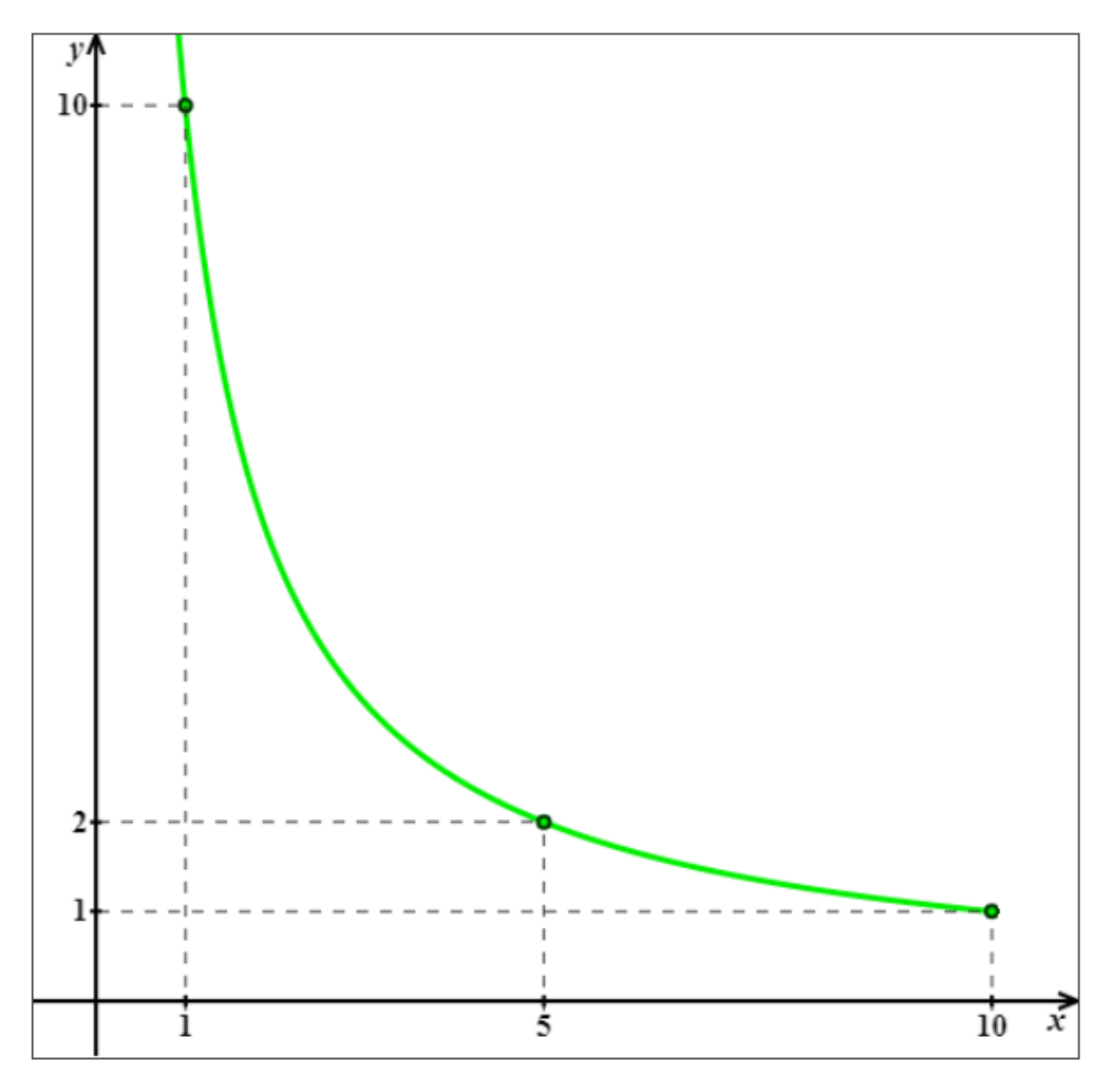
- Should approach infinity for ,
- Should have its minimum value for .
- For which R, : it means for what reputation, the calculated risk is equal to the estimated one?
- What is : e.g., if , it means that maximal reputation causes that calculated risk is half of the estimated one?
3.1. Fraud Probability
- An average amount of fraudulent transaction is 830.40 PLN,
- The number of transactions made with lost or stolen cards accounts for approximately 13% of all fraudulent transactions recorded by Issuers,
- According to Acquirers, the number of fraudulent transaction accounts for 0.001% of all processed transactions.
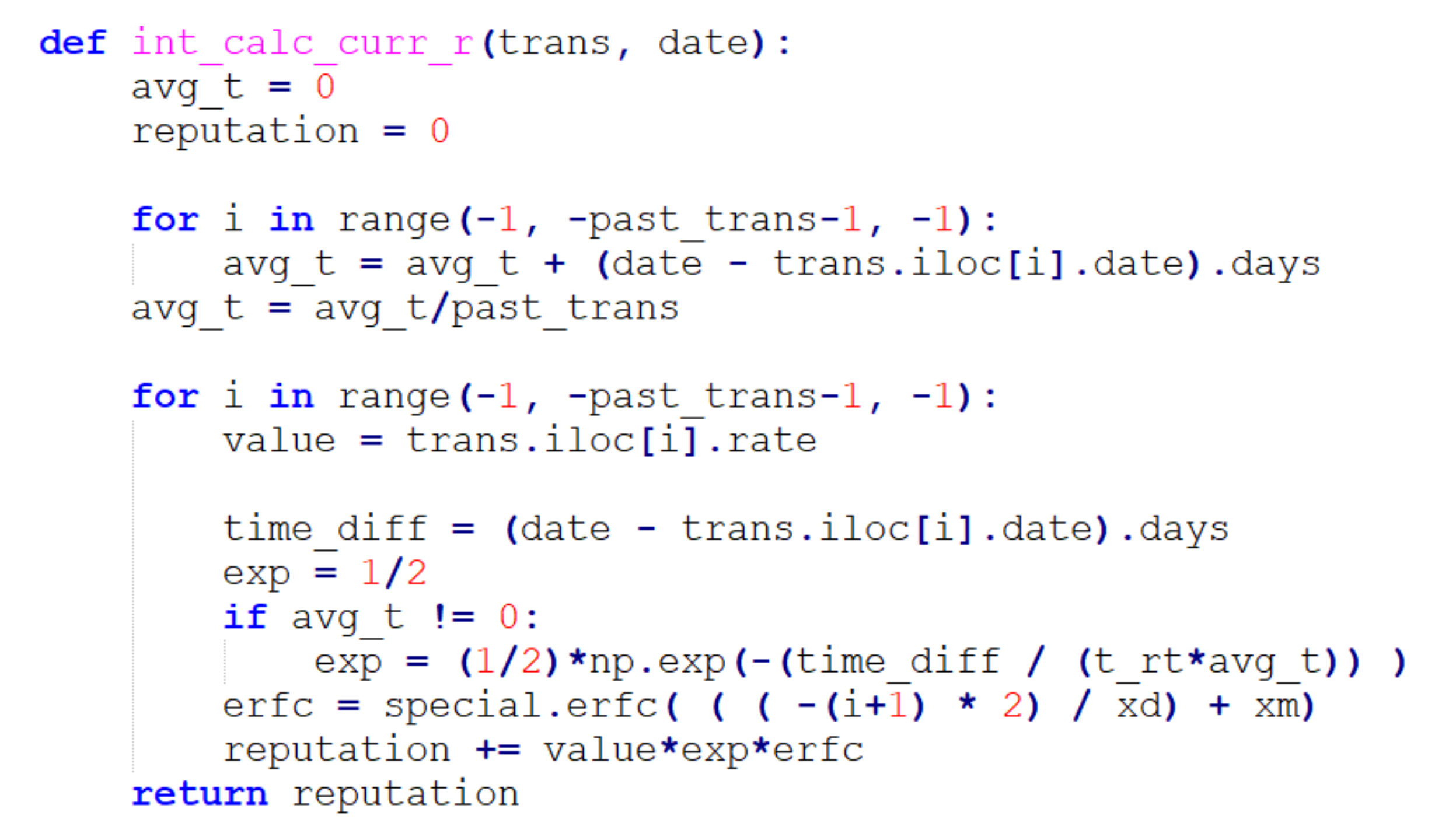
3.2. Cardholder’s Reputation System
4. The Experiment
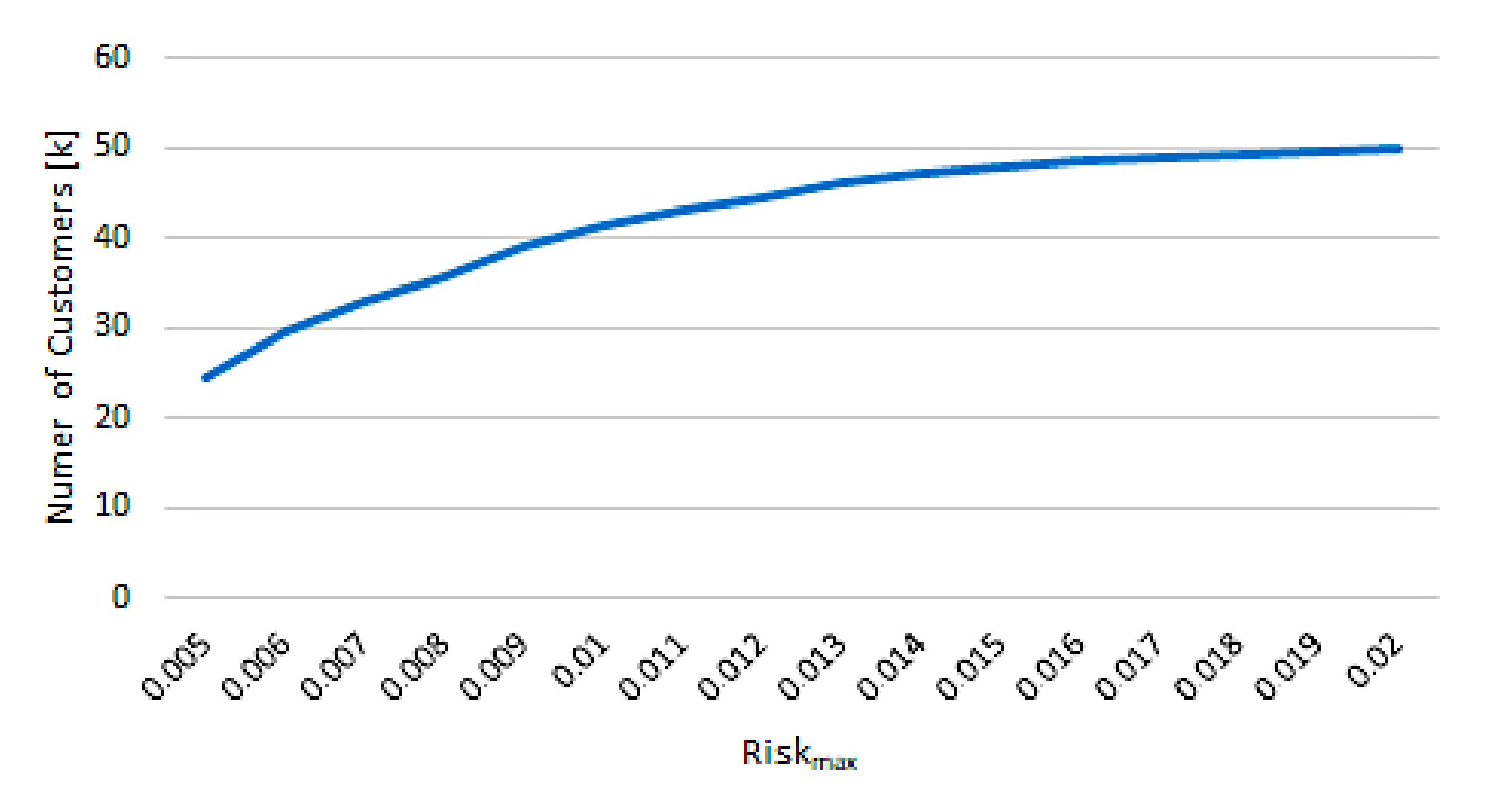
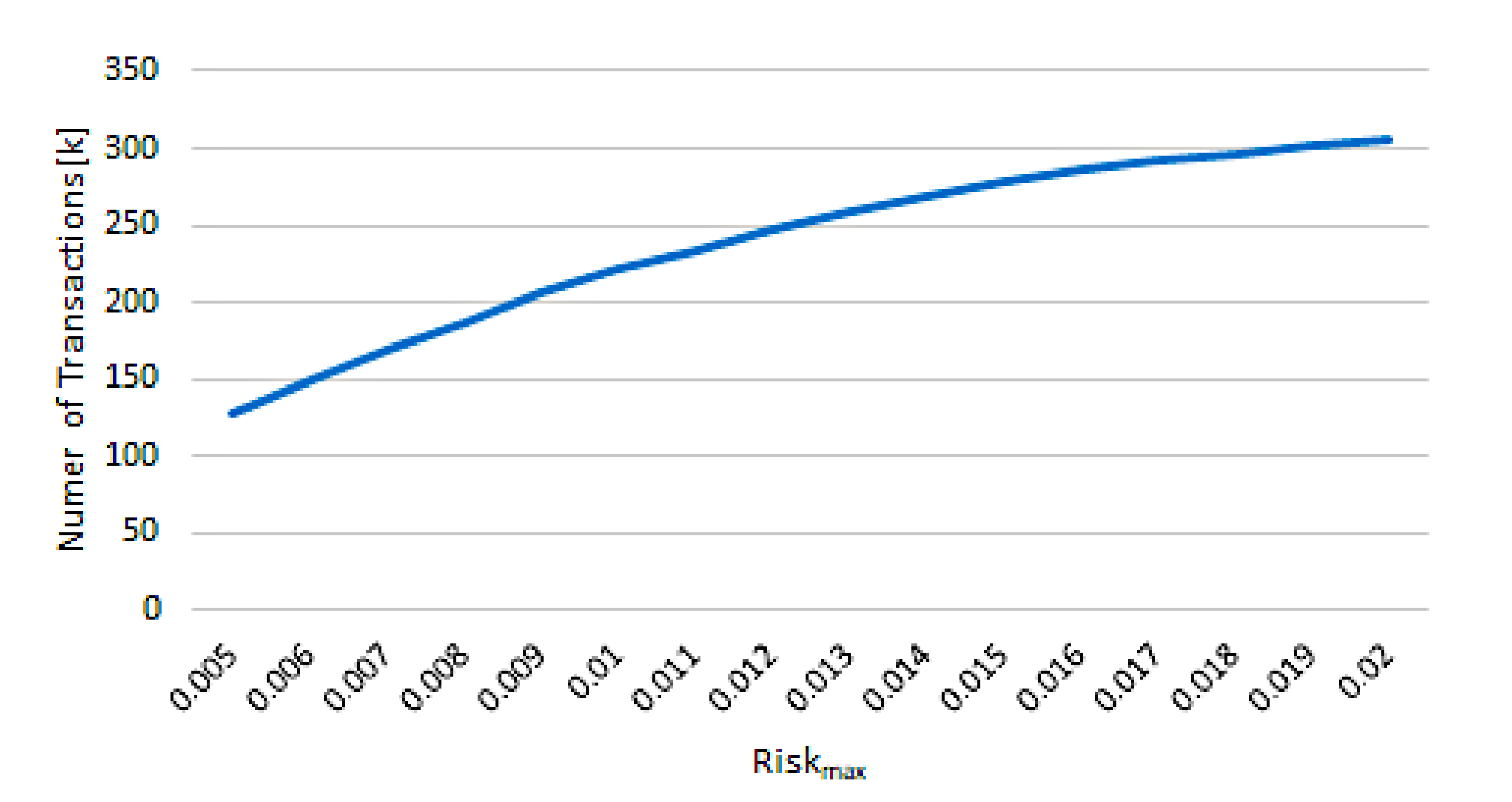
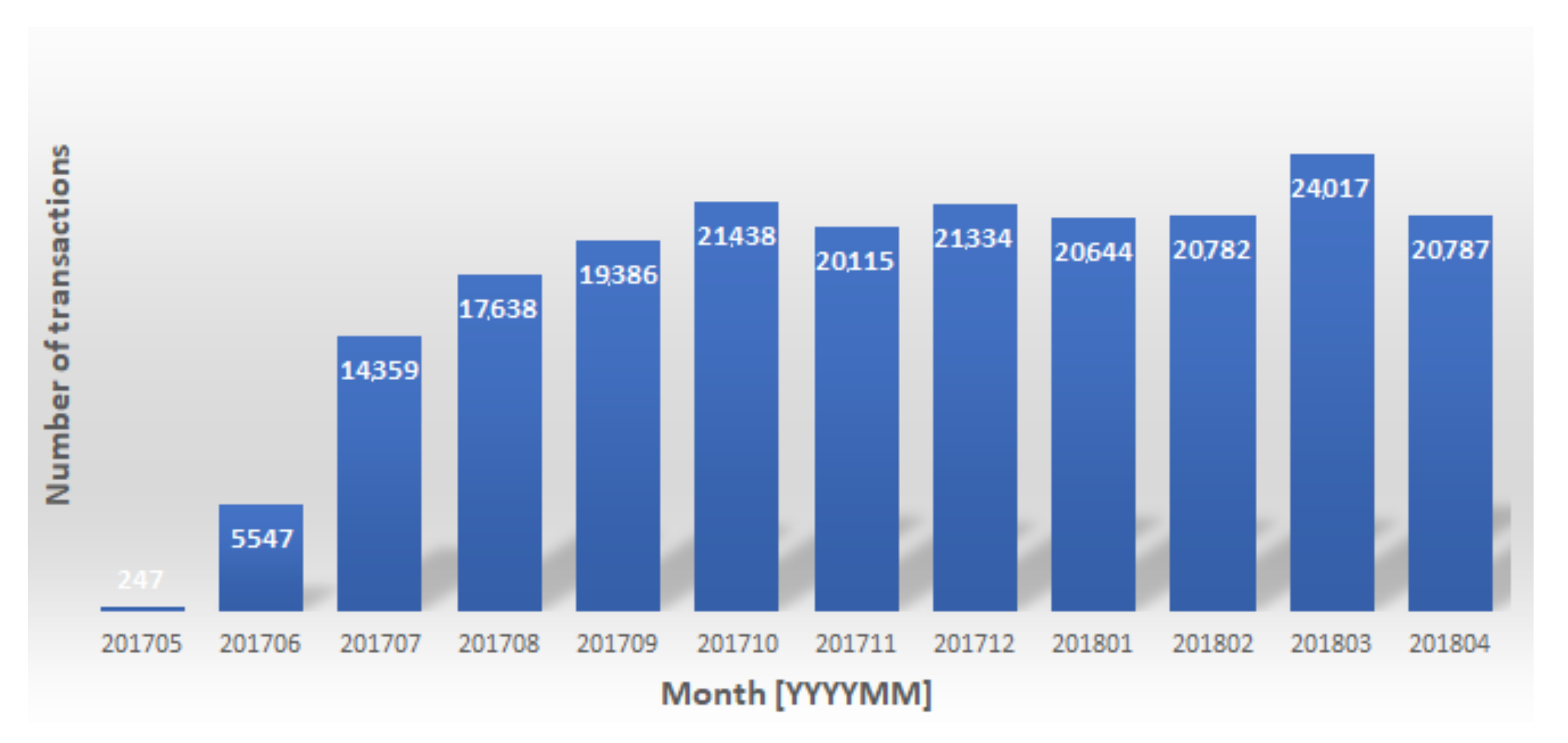
- What was the number of transactions selected to be processed without cardholder verification?
- What was the summary amount of the transactions above?
- What was the number of cardholders with almost one transaction promoted by the CRMS?
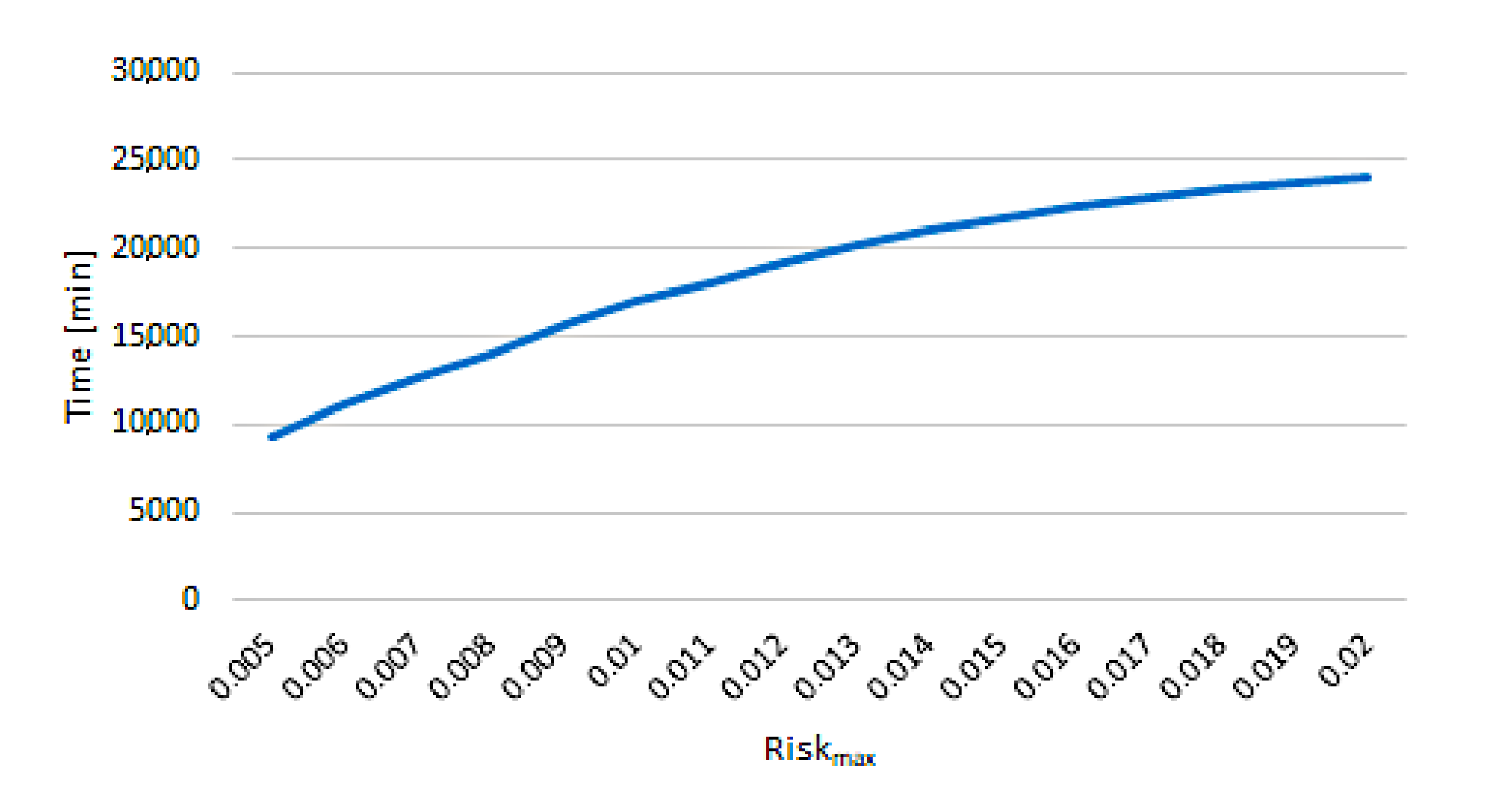
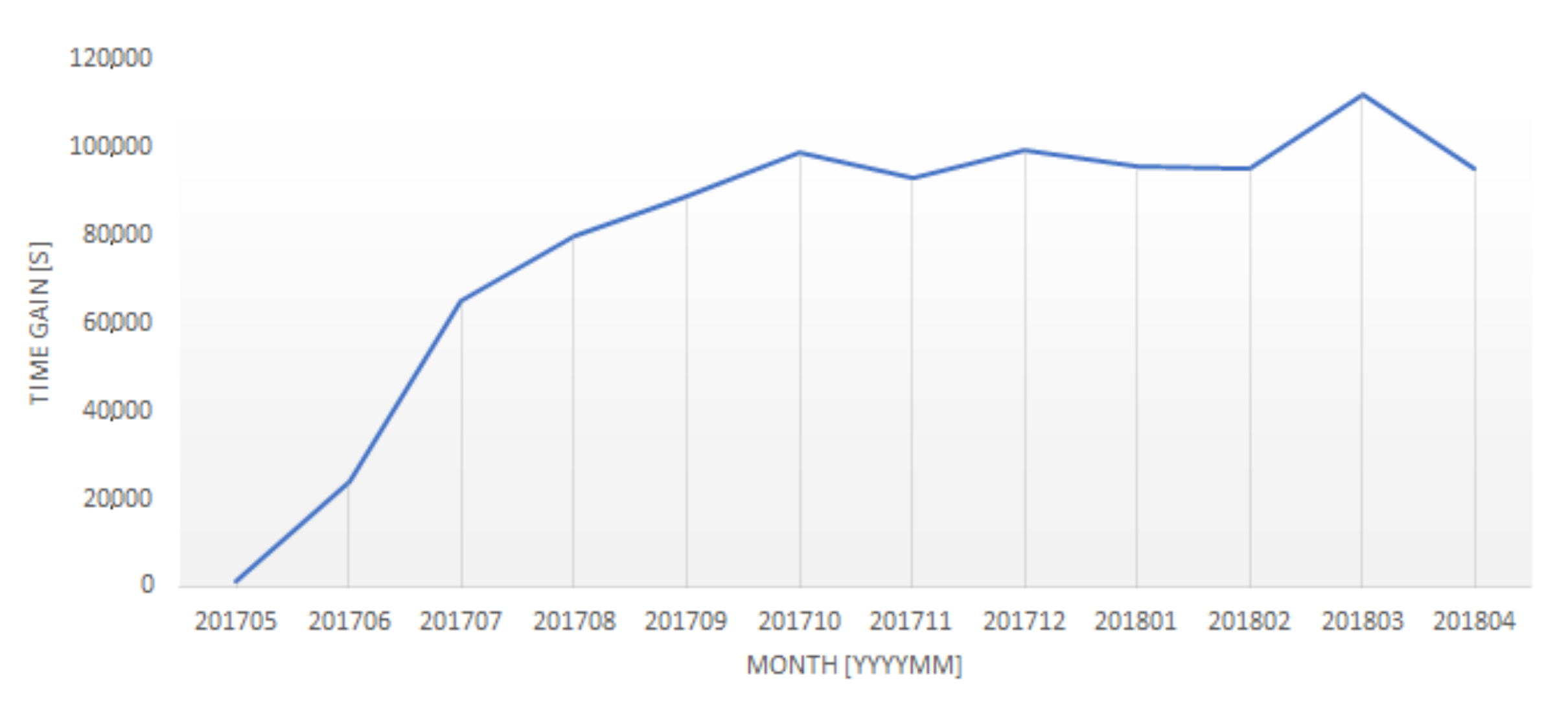
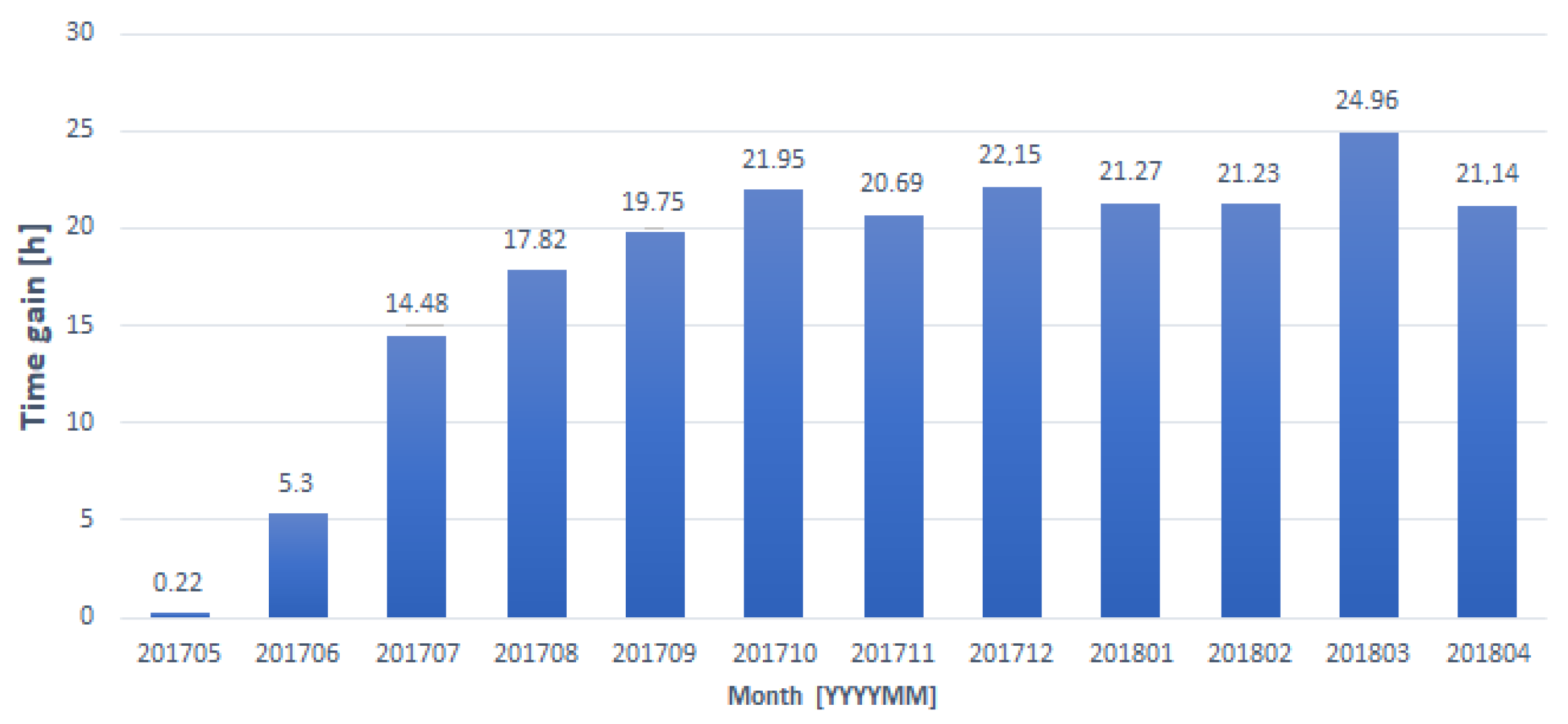
- What was the total gain in time caused by the usage of the system?
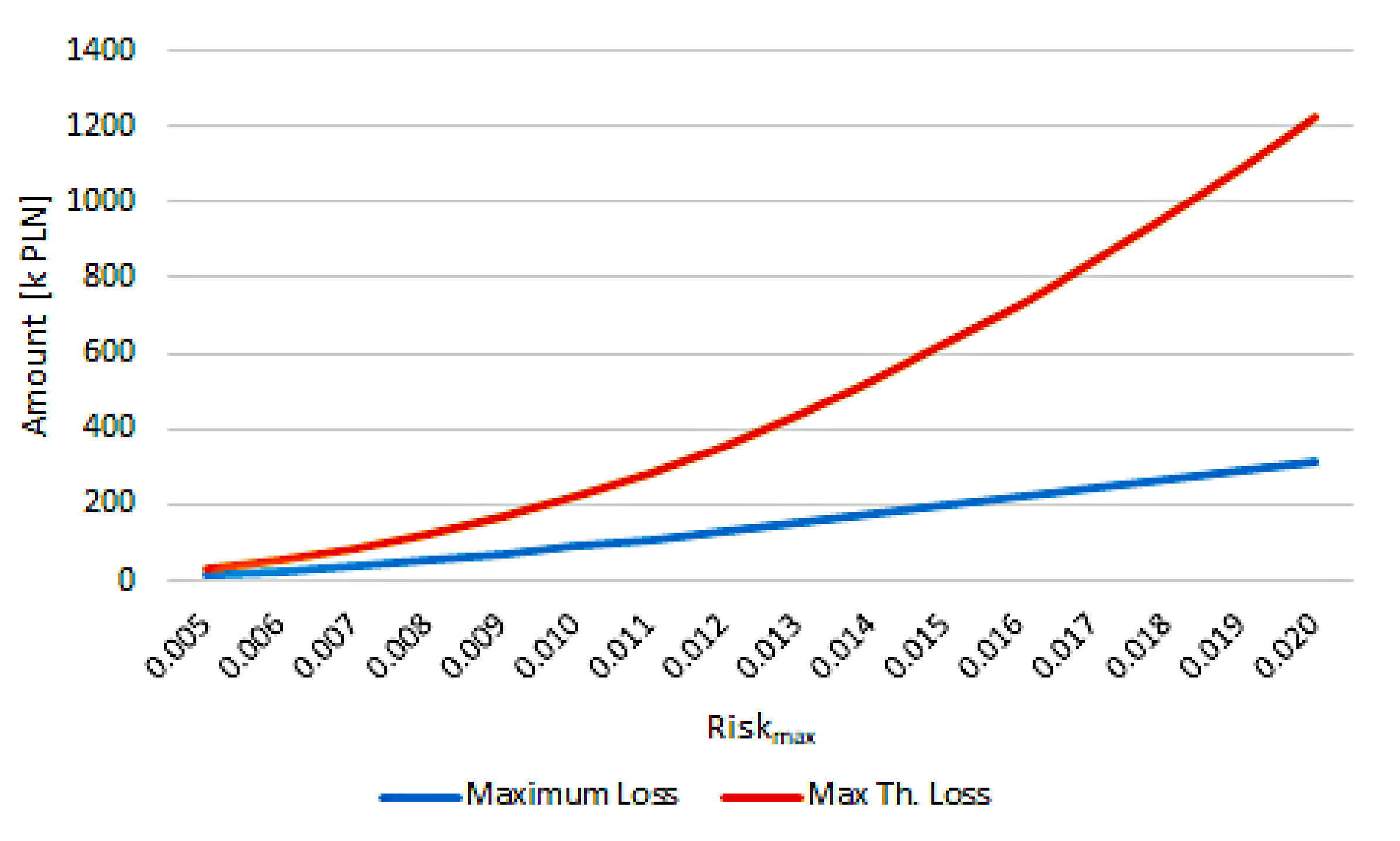
- What was the maximum loss caused by the usage of the system versus maximum loss when no cardholder’s reputation was taken into account?
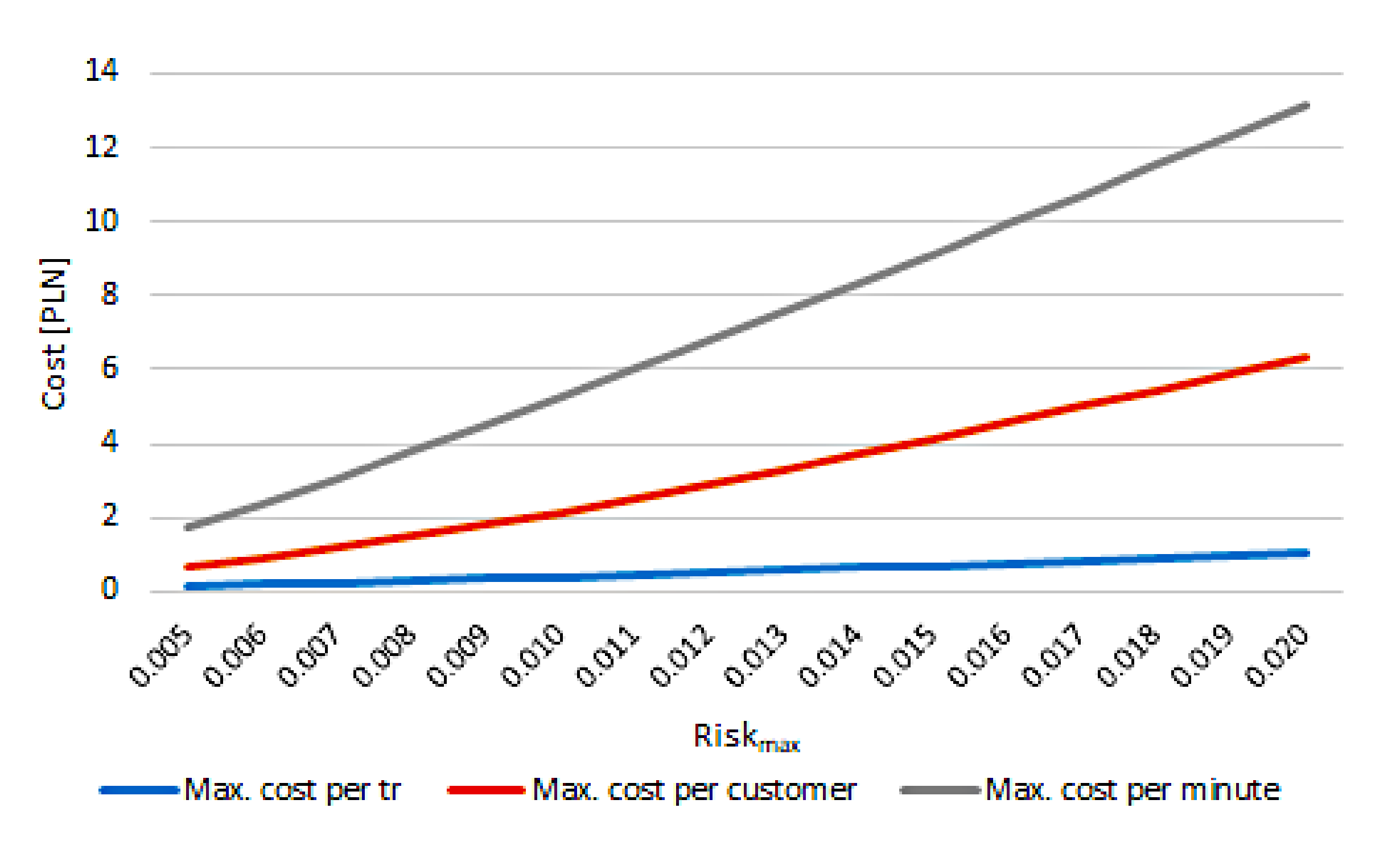
- What was the maximum cost for the merchant to gain one minute of time, to promote one transaction, and to promote one cardholder?
5. Profits Estimation
- The time required for the CRMS to achieve a destined number of selected transactions to be processed without cardholder verification is about 3–4 months,
- During the first month since the CRMS started, the profits are negligibly low.
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Meyer-Waarden, L. The effects of loyalty programs on customer lifetime duration and share of wallet. J. Retail. 2007, 83, 223–236. [Google Scholar] [CrossRef]
- Bond Brand Loyalty; Visa. The Loyalty Report 2018. Available online: https://info.bondbrandloyalty.com/loyalty-report-2018 (accessed on 10 October 2020).
- 13 Brand Loyalty Statistics You Need to Know to Keep Your Customers Coming Back. Available online: https://www.fundera.com/resources/brand-loyalty-statistics (accessed on 9 February 2019).
- Theng So, J.; Danaher, T.; Gupta, S. What do customers get and give in return for loyalty program membership? Aust. Mark. J. 2015, 23, 196–206. [Google Scholar]
- Butscher, S.A. Customer Loyalty Programmes and Clubs; Taylor & Francis: Abingdon, UK, 2017. [Google Scholar]
- Meyer-Waarden, L. Effects of loyalty program rewards on store loyalty. J. Retail. Consum. Serv. 2015, 24, 22–32. [Google Scholar] [CrossRef]
- Ferrer-Gomila, J.L.; Hinarejos, M.F.; Huguet-Rotger, L. A survey on electronic coupons. Comput. Secur. 2018, 77, 106–127. [Google Scholar] [CrossRef]
- Xie, K.L.; Chen, C.C. Progress in Loyalty Program Research: Facts, Debates, and Future Research. J. Hosp. Mark. Manag. 2013, 22, 463–489. [Google Scholar] [CrossRef]
- Uncles, M.D.; Dowling, G.; Hammond, K. Customer Loyalty and Customer Loyalty Programs. J. Consum. Mark. 2003, 20, 294–316. [Google Scholar] [CrossRef]
- Dorotic, M.; Bijmolt, T.; Verhoef, P. Loyalty Programmes: Current Knowledge and Research Directions. Int. J. Manag. Rev. 2011, 14. [Google Scholar] [CrossRef]
- McCall, M.; Voorhees, C. The Drivers of Loyalty Program Success. Cornell Hosp. Q. 2010, 51, 35–52. [Google Scholar] [CrossRef]
- Keh, H.T.; Lee, Y.H. Do reward programs build loyalty for services?: The moderating effect of satisfaction on type and timing of rewards. J. Retail. 2006, 82, 127–136. [Google Scholar] [CrossRef]
- Walker Information. Customers 2020: A Progress Report; Walker Information: Indianapolis, IN, USA, 2019. [Google Scholar]
- The Deloitte Consumer Review Customer Loyalty: A Relationship, Not Just a Scheme. 2017. Available online: https://www2.deloitte.com/content/dam/Deloitte/uk/Documents/consumer-business/deloitte-uk-consumer-review-customer-loyalty.pdf (accessed on 9 February 2019).
- Sitek, A.; Kotulski, Z. On a New Intangible Reward for Card-Linked Loyalty Programs. In Proceedings of the Advances in Soft and Hard Computing: 21th International Multi-Conference on Advanced Computer Systems, ACS 2018, Miedzyzdroje, Poland, 24–26 September 2018; Advances in Intelligent Systems and Computing; Pejaś, J., El Fray, I., Hyla, T., Kacprzyk, J., Eds.; Springer International Publishing: Berlin/Heidelberg, Germany, 2019; Volume 889. [Google Scholar] [CrossRef]
- Turner, M.A. Credit Card Rewards: Context, History, and Value; PERC Press: London, UK, 2012; Available online: https://www.perc.net/wp-content/uploads/2013/12/WP-2-Layout.pdf (accessed on 10 April 2019).
- Larson, J.; McClellan, B.C.L. Capturing Loyalty: How to Measure, Generate, and Profit from Highly Satisfied Customers; Praeger: Westport, CT, USA, 2017. [Google Scholar]
- Varma, A.J. Effectiveness of Customer Loyalty Programs a Study on Select Retailers in Bangalore and Mysore City. Ph.D. Thesis, University of Mysore, Mysore, India, 2015. [Google Scholar]
- Berman, B. Developing an Effective Customer Loyalty Program. Calif. Manag. Rev. 2006, 49, 123–148. [Google Scholar] [CrossRef]
- Smets, J.; Ergeerts, G.; Beyers, R.; Schrooyen, F.; Ceulemans, M.; Wante, L.; Renckens, K. An NFC-based Customer Loyalty System 2011. In Proceedings of the First International Conference on Resource, Services and User Mobility, Barcelona, Spain, 23–28 October 2011; Available online: https://www.semanticscholar.org/paper/An-NFC-based-Customer-Loyalty-System-Smets-Ergeerts/df882ff5c00729881cd1c1234f987f9cd76f07c6 (accessed on 19 November 2020).
- Stocard Homepage. Available online: https://stocardapp.com/en/au (accessed on 9 February 2019).
- Antoniadis, I.; Kontsas, S.; Spinthiropoulos, K. Blockchain and Brand Loyalty Programs: A Short Review of Applications and Challenges. In Proceedings of the International Conference on Economic Sciences and Business Administration, Bucharest, Romania, 15–16 November 2019. [Google Scholar] [CrossRef]
- Wang, L.; Luo, R.; Hua, Y. Exploring How Blockchain Impacts Loyalty Program Participation Behaviors: An Exploratory Case Study. In Proceedings of the 52nd Hawaii International Conference on System Sciences, Grand Wailea, HI, USA, 8–11 January 2019. [Google Scholar] [CrossRef]
- vPromos. How Does Card-Linking Loyalty Work? 2016. Available online: https://www.vpromos.com/ (accessed on 26 February 2019).
- Chien, E.; Sanchez, T.; Saunders, D.; Wiseman, J.; Balagopal, C.R.; Kinderknecht, A.; Parson, J.W.; Preston, R. System and Method for Using Loyalty Rewards as Currency. U.S. Patent 8,265,993 B2, 25 October 2012. [Google Scholar]
- Hessburg, M.B.; Rappleyea, A.W.; Rodriguez, S.; Sanoff, J.; Silverstein, A.N. System and Method for Exchanging Loyalty Points for Acquisitions. U.S. Patent 7,686,218 B2, 9 November 2010. [Google Scholar]
- Aloni, R.L.; Axelrod, B.T.; Bowman, J.L.; Funda, J.J.; Polon, J.S.; Tiku, S.V.; American Express Travel Related Services Co Inc. Loyalty Incentive Program Using Transaction Cards. U.S. Patent 9,665,880 B2, 30 August 2017. [Google Scholar]
- Robison, S.K. Customer Loyalty Program. U.S. Patent 2003/0200141 A1, 10 October 2003. [Google Scholar]
- Friday, G.; Leece, R.; Snyder, L.; Turnbull, A.; Pearce, G.; Madden, R.; Panayotopoulos, C.; Castle, A.; Bank of Nova Scotia ScotiaBank; InfiStar Corp; et al. Cardholder Loyalty Program with Rebate. U.S. Patent 2005/0240477 A1, 27 October 2005. [Google Scholar]
- Trzcinski, J.R. Generic Universal Rewards Loyalty Card. U.S. Patent 2011/0238471 A1, 29 September 2011. [Google Scholar]
- Fontana, A.J.; Onay, O.; Tabachnick, G.; Switchly Inc.; Topguest. Loyalty Program Systems and Methods. U.S. Patent 2012/0284108 A1, 8 November 2012. [Google Scholar]
- Fordyce, E.W., III; Amaro, L.; Winters, M.E.; Griggs, A.W.; DiGioacchino, L.; Salmon, D.C.; Siegel, K.P.; Subramanian, K.; VonDerheide, J.A.; Visa USA Inc. Systems and Methods to Provide Loyalty Programs. WO Patent 2012/0284108 A1, 14 April 2011. [Google Scholar]
- Haddad, A. Using Smart Cards to Gain Market Share; Gower: Swansea, UK, 2000. [Google Scholar]
- Cabaj, K.; Domingos, D.; Kotulski, Z.; Respicio, A. Cybersecurity education: Evolution of the discipline and analysis of master programs. Comput. Secur. 2018, 75. [Google Scholar] [CrossRef]
- Goode, S.; Hoehle, H.; Venkatesh, V.; Brown, S. User Compensation as a Data Breach Recovery Action: An Investigation of the Sony PlayStation Network Breach. MIS Q. 2017, 41, 703–727. [Google Scholar] [CrossRef]
- Goode, S.; Lacey, D. Detecting complex account fraud in the enterprise: The role of technical and non-technical controls. Decis. Support Syst. 2011, 50, 702–714. [Google Scholar] [CrossRef]
- Chang, H.H.; Chen, S.W. Consumer perception of interface quality, security, and loyalty in electronic commerce. Inf. Manag. 2009, 46, 411–417. [Google Scholar] [CrossRef]
- Sepczuk, M.; Kotulski, Z. A new risk-based authentication management model oriented on user’s experience. Comput. Secur. 2018, 73, 17–33. [Google Scholar] [CrossRef]
- Weir, C.S.; Douglas, G.; Carruthers, M.; Jack, M. User perceptions of security, convenience and usability for ebanking authentication tokens. Comput. Secur. 2009, 28, 47–62. [Google Scholar] [CrossRef]
- Gunson, N.; Marshal, D.; Morton, H.; Jack, M. User perceptions of security and usability of single-factor and two-factor authentication in automated telephone banking. Comput. Secur. 2011, 30, 208–220. [Google Scholar] [CrossRef]
- Department of Payment System, National Bank of Poland. An Assessment of the Functioning of Polish Payment System in 1st q. 2017; Department of Payment System, National Bank of Poland: Warsaw, Poland, 2017. (In Polish)
- MacDonald, N. The Future of Information Security Is Context Aware and Adaptive; Gartner Research: Hong Kong, China, 2010. [Google Scholar]
- IEC/FDIS 31010:2009 Risk Management—Risk Assessment Techniques; ISO: Geneva, Switzerland, 2009.
- BS/ISO 31000:2018 Risk Management—Guidelines; ISO: Geneva, Switzerland, 2018.
- Sitek, A. One-time code cardholder verification method in electronic funds transfer transactions. In Annales UMCS ser. Informatica; Universitatis Mariae Curie-Skłodowska: Lublin, Poland, 2014; Volume 14, pp. 46–59. [Google Scholar]
- Sitek, A.; Kotulski, Z. Contextual management of off-line authorisation in contact EMV transactions. Telecommun. Rev. Telecommun. News 2015, 88, 953–959. (In Polish) [Google Scholar]
- Sitek, A.; Kotulski, Z. Cardholder’s Reputation System for Contextual Risk Management in Payment Transactions. In Proceedings of the Computer Network Security: 7th International Conference on Mathematical Methods, Models, and Architectures for Computer Network Security, MMM-ACNS 2017, Warsaw, Poland, 28–30 August 2017; Lecture Notes in Computer Science; Rak, J., Bay, J., Kotenko, I., Popyack, L., Skormin, V., Szczypiorski, K., Eds.; Springer International Publishing: Berlin/Heidelberg, Germany, 2017; Volume 10446, pp. 158–170. [Google Scholar] [CrossRef]
- Tomasofsky, C.P.; Hubbard, S.E.; Gerber, J.; Salazar, C.; Hafner, M.; Mastercard International Inc. Systems and Methods for Providing Risk Based Decisioning Service to the Merchants. U.S. Patent 10,614,452 B2, 7 April 2020. [Google Scholar]
- Bounie, D.; Francois, A. Cash, Check or Bank Card? The Effects of Transaction Characteristics on the Use of Payment Instruments. In Proceedings of the FMG & CASS Business School Conference (Workshop on Financial Regulation and Payment Systems), Milan, Italy, 6–10 May 2009; SciTePress: Setúbal, Portugal, 2009; Available online: https://www.semanticscholar.org/paper/Cash%2C-Check-or-Bank-Card-The-Effects-of-Transaction-Bounie-Fran%C3%A7ois/b121c7b212ffb4097a2c3a3e994086662ae7bf7 (accessed on 10 October 2020).
- Chiou, J.S.; Ting, C.C. Will you spend more money and time on internet shopping when the product and situation are right? Comput. Hum. Behav. 2011, 27, 203–208. [Google Scholar] [CrossRef]
- Zhang, H.; Li, H. Factors affecting payment choices in online auctions: A study of eBay traders. Decis. Support Syst. 2006, 42, 1076–1088. [Google Scholar] [CrossRef]
- Sitek, A.; Kotulski, Z. POS-originated transactions traces as a source of contextual information for Risk Management Systems in EFT transactions. EURASIP J. Inf. Secur. 2018, 2018, 5. [Google Scholar] [CrossRef]
- Tokenization Taskforce, PCI Security Standards Council. PCI DSS Tokenization Guidelines, 2011. Available online: https://www.pcisecuritystandards.org/documents/Tokenization_Guidelines_Info_Supplement.pdf (accessed on 18 November 2020).
- PCI DSS Homepage. Available online: https://www.pcisecuritystandards.org/ (accessed on 26 January 2019).
- European Parliament. REGULATION (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the Protection of Natural Persons with Regard to the Processing of Personal Data and on the Free Movement of Such Data, and Repealing DIRECTIVE 95/46/EC (General Data Protection Regulation). Off. J. Eur. Union 2016. Available online: https://www.europarl.europa.eu/portal/en (accessed on 26 January 2019).
- Kotulski, Z.; Szczepinski, W. Error Analysis with Application in Engineering; Springer: Dordrecht, The Netherlands, 2010. [Google Scholar]
- Numpy Homepage. Available online: https://numpy.org (accessed on 26 January 2019).
- Pandas Homepage. Available online: https://pandas.pydata.org (accessed on 26 January 2019).
- Matplotlib Homepage. Available online: https://matplotlib.org (accessed on 26 January 2019).
- Pérez, F.; Granger, B.E. IPython: A System for Interactive Scientific Computing. Comput. Sci. Eng. 2007, 9, 21–29. [Google Scholar] [CrossRef]
- Jupyter IDE Homepage. Available online: https://jupyter.org (accessed on 26 January 2019).
- ZenCard. Homepage. Available online: https://www.finat.pl/narzedzia-marketingowe/ (accessed on 26 January 2019).
- Fiserv’s STAR to Increase PINless Transaction Approval Limits to USD 100. Available online: https://thepaypers.com/digital-identity-security-online-fraud/fiservs-star-to-increase-pinless-transaction-approval-limits-to-usd-100–1242113 (accessed on 10 October 2020).
- PIN-Less Payments Limit Goes Up as Coronavirus Countermeasure. Available online: https://polandin.com/47285858/pinless-payments-limit-goes-up-as-coronavirus-countermeasure (accessed on 10 October 2020).

Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sitek, A.; Kotulski, Z. A New Card-Linked Loyalty Program: Estimated and Anticipated Benefits for Payment Transaction Parties. Electronics 2020, 9, 1956. https://doi.org/10.3390/electronics9111956
Sitek A, Kotulski Z. A New Card-Linked Loyalty Program: Estimated and Anticipated Benefits for Payment Transaction Parties. Electronics. 2020; 9(11):1956. https://doi.org/10.3390/electronics9111956
Chicago/Turabian StyleSitek, Albert, and Zbigniew Kotulski. 2020. "A New Card-Linked Loyalty Program: Estimated and Anticipated Benefits for Payment Transaction Parties" Electronics 9, no. 11: 1956. https://doi.org/10.3390/electronics9111956
APA StyleSitek, A., & Kotulski, Z. (2020). A New Card-Linked Loyalty Program: Estimated and Anticipated Benefits for Payment Transaction Parties. Electronics, 9(11), 1956. https://doi.org/10.3390/electronics9111956





