1. Introduction
The rapid development of wireless communications requires advanced communications techniques that can provide massive connectivity, high spectral efficiency, high energy efficiency, and low latency in support of the fast proliferation of the Internet of Things (IoT), mobile devices, and so on. Therefore, integration of promising technologies, such as cognitive radio (CR) and non-orthogonal multiple-access (NOMA) techniques, has been investigated by the industry and by academics to enable future wireless networks [
1,
2]. Specifically, CR tackles spectrum scarcity issues and improves spectrum efficiency based on its strategy of dynamic spectrum access, which permits the use of licensed spectrum by unlicensed users, called secondary users (SUs), without interfering with licensed users [
3,
4]. There are two types of spectrum sharing in accordance with access technology: underlay and overlay spectrum sharing. Underlay spectrum sharing permits SUs to use the licensed spectrum while keeping their power levels below a certain threshold to prevent unacceptable interference with licensed users, also known as primary users (PUs) [
5,
6]. On the other hand, overlay spectrum sharing tries to minimize the risk of any interference with the PUs at the expense of spectrum use, allowing SUs to use the licensed spectrum in the absence of the PUs [
7,
8].
Meanwhile, NOMA has surged as another powerful technology to enhance spectrum efficiency while providing high transmission rates and high user densities for future mobile communications [
9,
10]. NOMA can be categorized into code-domain and power-domain NOMA. Complex encoding or decoding techniques are required in code-domain NOMA, while the key idea of power-domain NOMA is to assign different power levels to users according to their channel strength, such that higher transmission power is assigned to users with weaker channels. Moreover, on the receiver side, users with stronger channels apply successive interference cancelation (SIC) to first decode the signals of the weaker users, and then, they decode their own signals. In this paper, we focus on power-domain NOMA, which can be further combined with other communications technologies (multiple-input single-output (MISO), multiple-input multiple-output (MIMO), cooperative communications) to reach a better yield [
11,
12,
13,
14,
15,
16].
Furthermore, energy-efficient techniques have been investigated for future wireless networks in support of environmental concerns and battery-limited devices, such as sensors and wearables [
17]. In this sense, achieving high energy efficiency and recycling energy are the main goals of energy-efficient techniques, where simultaneous wireless information and power transfer (SWIPT) brings technological innovations and plays a key role in energy and information transmission [
18,
19,
20]. In contrast to the conventional energy-harvesting (EH) technologies that rely on unpredictable natural sources, or where the communications nodes are only able to recharge from electromagnetic radiation, such as wireless power transfer (WPT), SWIPT enables users to perform information decoding (ID) and radio-frequency (RF) EH simultaneously [
21,
22]. Hence, the study of SWIPT in NOMA with CR networks is of meaningful importance in supporting massive numbers of mobile devices with limited battery power [
23,
24,
25].
However, a NOMA-CR network assisted by SWIPT technology operates in a wireless transmission environment, which is vulnerable to malicious receivers that can intercept confidential information transmitted from the sources to either the legitimate or the unlicensed users. Therefore, security is a critically challenging issue that must be handled for the suitable deployment of wireless communications networks. In this sense, physical-layer security (PLS) has emerged as a complementary technology to address the eavesdropping security issue by exploiting the physical characteristics of wireless channels, e.g., propagation delay, multipath fading, and so on. Although traditional cryptographic encryption and decryption techniques have been pointed out to secure communication systems using complex algorithms and encryption keys. They require key management, maintenance and distribution procedures that use network resources and may become an issue in large-scale decentralized and heterogeneous wireless network. Moreover, the encryption keys are prone to being broken by high computational capabilities of an eavesdropper [
26,
27]. These drawbacks are the motivations for the study and research on PLS to complement cryptographic techniques. PLS is independent of complex algorithms and key management of which initial idea was investigated in Wyner’s work [
28]. Wyner et al. explained that it is possible to achieve secure communication between legal users without sharing a secret key if the eavesdropper’s channel is a much noisier version than the legitimate user’s channel. In addition, PLS metrics include secrecy channel capacity or secrecy rate, secrecy outage probability, secrecy throughput, bit error rate-based and packet error rate-based metrics. One of the most common metric used in various research works is the secrecy channel capacity which indicates the maximum secrecy rate at which the message is retrieved safely at the legitime user while preventing it to be recovered at the eavesdropper. This metric is calculated by the difference between the legitimate and eavesdropper’s channel capacities.
1.1. Related Work
In the literature, to further improve the secure performance of wireless transmissions, different strategies have been proposed, such as multiple antennas, beamforming designs, artificial noise (AN) or jamming, and resource allocation schemes [
29,
30,
31]. For instance, security in cooperative single-input single-output (SISO) NOMA networks has been investigated in [
29,
30], aiming to maximize the secrecy sum rate (SSR) and secrecy energy efficiency, respectively, by applying a low-complexity solution based on particle swarm optimization (PSO). Recently, PLS in NOMA mobile edge computing (MEC) system was studied in [
31] to maximize the secure computation efficiency by jointly optimizing the resource allocations such as the transmission power, the computation time, and the central processing unit frequency. The results showed the superiority of NOMA over the time-division multiple-access (TDMA) conventional scheme. However, none of these studies previously discussed consider MISO and SWIPT technology which can increase the spectral efficiency of the network. Secure NOMA transmission in a MISO scenario was investigated [
32,
33,
34,
35,
36] via joint beamforming and AN optimization. The authors of both [
32,
33] maximized the SSR by using joint precoding optimization, while in [
34], the authors provided secure NOMA transmission by maximizing the jamming power, and they applied SIC at the receiver to avoid affecting legitimate transmissions. In [
32], the authors considered downlink MISO-NOMA system with the presence of an eavesdropper. The objective was to obtain the optimal precoder vectors to maximize the SSR of the users subject to the constraints of maximum available power and rate requirement in each user. The solution was an iterative algorithm based on the second-order cone programming. However, the authors did not consider the SWIPT technology, EH users, AN along with an underlying CR system, which involves extra constraints related to EH requirements and maximum interference allowed to the primary network. Therefore, the solution proposed in [
32] cannot be used to solve the optimization problem proposed in this paper. Another optimization approach to improve the SSR of a MISO-NOMA network has been studied in [
35] which is based on a dynamic user scheduling, grouping strategy, and the application of efficient algorithms such as outer polyblock approximation and Dinkelbach. The authors considered the zero-forcing (ZF) criteria to define the beamforming vectors and investigated the minimum secrecy rate maximization problem to design the optimal power allocation strategy under three main constrains: QoS requirements, secrecy outage probability (SOP) and maximum available power. However, they did not consider EH users and an underlying CR system, which entails new EH constraints and maximum interference constraints in the optimizations problem. In addition, the proposed approach optimized the beamforming vectors and considered an scheme. Therefore, the algorithm in [
35] cannot be used for the proposed system model in this paper.
Security for the primary network of a NOMA-CR system assisted by SWIPT was studied in [
36]. The authors considered SU users with the ability to only decode information and several EH users which are considered to be eavesdropper, where the secondary base station (BS) transmits a jamming signal to increase the security of the primary network. The objective was to minimize the total transmission power under the constraints of minimum secrecy rates and EH requirements, in which the solution was based on the successive convex approximation (SCA) algorithm and the semidefinite relaxation (SDR) technique. It was shown that application of NOMA consumed lower transmission power than baseline schemes and satisfied quality of service (QoS) requirements such as the minimum secrecy rate of legitimate users. Although this paper opened doors to future secure wireless systems integrated with SWIPT in CR-NOMA networks, the authors did not consider SUs with the ability to simultaneously receive information and harvest energy, and it was assumed that channel vectors to the eavesdroppers are known at the secondary BS, which is not always possible in practical scenarios where eavesdroppers are hidden from the secondary BS. Please note that the PS structure considered in this paper involves the optimization of PS ratios, which are coupled to the beamforming vectors in the optimization problem.
In general, the mathematical algorithms used to solve optimization problems are problem-dependent. The proposed algorithms to solve the optimization problems in the aforementioned literature are developed based on specific characteristic of the problems such as objective function, type of users, type of constraints and so on. For instance, the procedures and techniques used to transform non-convex problems to convex ones will differ from system to system and depend on the assumptions and elements considered for the optimization problem. When a system model includes new elements with other applications such as SWIPT users or CR capabilities, the previous proposed algorithms cannot be used anymore directly, and a novel algorithm needs to be developed to solve the new problem. Therefore, previous proposed algorithms for a PLS in MISO-NOMA system cannot be applied for the proposed cognitive MISO SWIPT NOMA system with AN.
None of the research described above was specifically proposed to enhance the security of the secondary network in a SWIPT-assisted NOMA-CR with EH users. In addition, the proposed scheme in the paper can be applied for the security in different scenarios such as IoT systems with RF EH user where spectrum scarcity is a critical issue due to the massive deployment of IoT devices. Here, NOMA is used to achieve better connectivity and to enhance spectrum use while EH can be used for improving the energy efficiency of IoT systems [
37].
Furthermore, in the case that malicious EH users exist in the system as the work in [
36], where a secondary transmitter sends information signals to SUs and energy to EH user, the EH user can eavesdrop the information transmitted to secondary users because of the broadcast nature of NOMA. In this scenario, a channel state information (CSI) of the EH user is available at the secondary transmitter, which can be used for a more precise beamforming design of the AN to interfere with the malicious EH user. In addition, the SSR for the secondary users can be directly maximized in the optimization problem to improve the security in the network. On the other hand, in the paper we propose a more challenging scenario when the eavesdropper is completely hidden from the secondary transmitter and the CSI of the eavesdropper is not available. In this case, the transmission power for legitimate users is minimized to use the remaining available power to maximize the AN. In addition, there is no any impact on the system even though the eavesdropper performs energy-harvesting since the eavesdropper is not a legitimate user and the secondary transmitter does not transfer extra energy signals to satisfy some EH requirement at the eavesdropper.
1.2. Contributions and Organization
The main contributions of this paper are summarized as follows.
Secure transmission for a MISO-NOMA-CR network applying SWIPT and assisted by AN is studied to enhance the security of the secondary network. We jointly optimize the precoder vectors and power-splitting (PS) ratios to minimize the transmit power to the SUs and EH users, subject to the constraints of minimum signal-to-interference-plus-noise ratio (SINR) at the SUs, minimum EH for EH users, maximum available power at the secondary transmitter, denoted as SU-Tx, and maximum permissible interference with the PUs. By minimizing the transmit power for SUs and EH users, we can assign the residual power to AN to generate interference against the eavesdropper, by which the security can be improved in the underlying network.
The formulated non-convex minimization problem is challenging to solve due to coupling between the PS ratios and transmission beamforming vectors. The proposed solution consists of two steps. First, an SDR-based algorithm converts the formulated problem into a semidefinite programming (SDP) problem. Second, a Gaussian randomization technique is applied to obtain the approximate rank-one solutions for beamforming vectors, and a linear program problem is used to guarantee the feasibility of the candidate solutions of the Gaussian randomization technique.
The space-division multiple-access (SDMA) method and the ZF technique are studied as a comparative schemes to solve the minimization problem in which the solution to the non-convex problems are based on the SDR technique. In addition, a MISO-NOMA-CR without AN is considered to be the baseline scheme to prove the advantages of AN.
Numerical simulations prove the superiority of the proposed approach based on NOMA with AN for increasing the security of the secondary network, in comparison with NOMA without AN, SDMA and ZF schemes. In particular, the proposed AN method shows a significant improvement in SSR over the no-AN scheme under several studied scenarios.
The rest of this paper is organized as follows. The MISO-NOMA-CR network model with SWIPT and EH users is described in
Section 2. In
Section 3, the beamforming optimization with AN is presented along with the proposed solution, and the comparison SDMA and ZF schemes are formulated. The numerical results are presented in
Section 4. Finally, the conclusions are presented in
Section 5.
Table 1 lists the main abbreviations used throughout the paper.
2. System Model
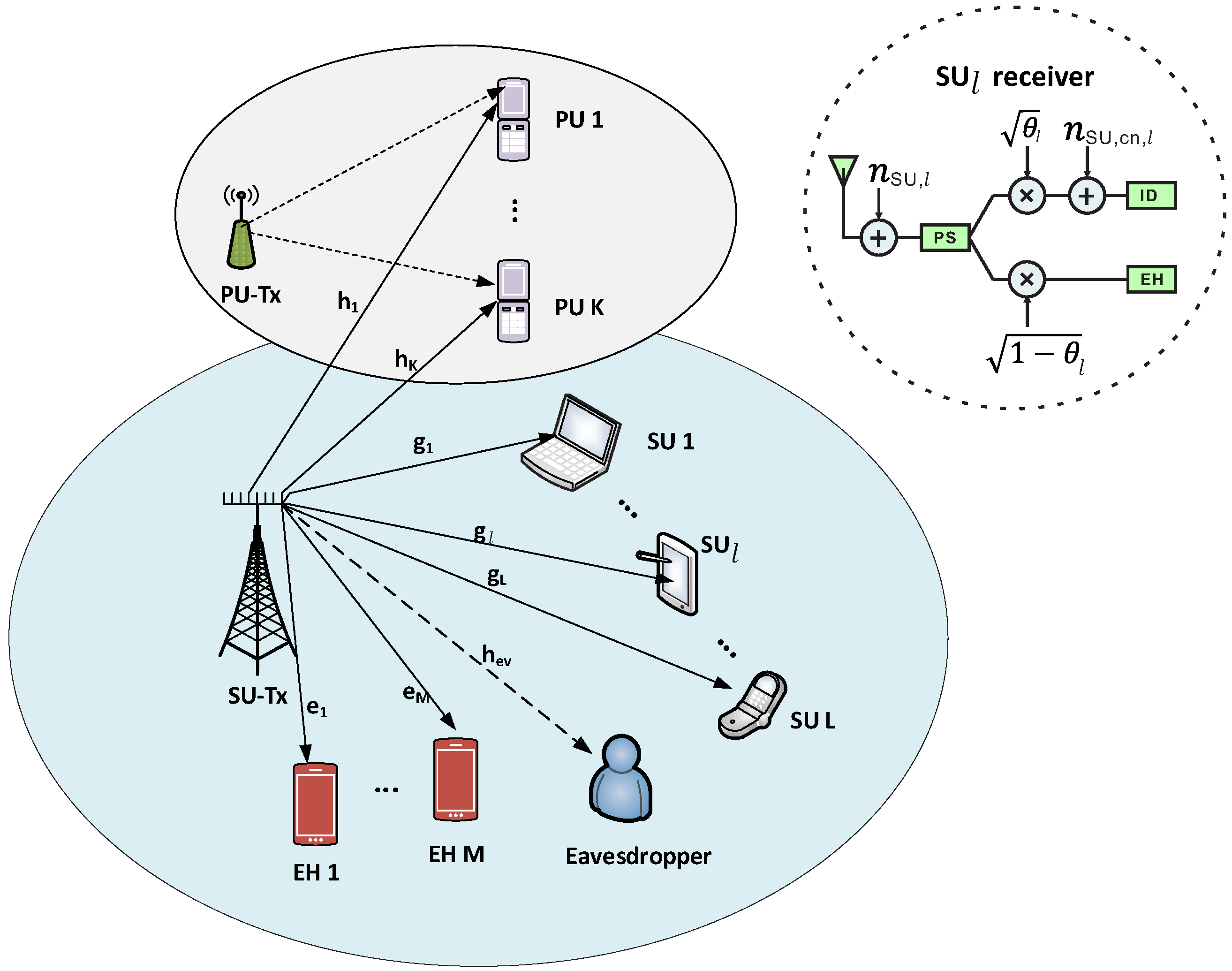
In this paper, we investigate downlink transmissions in a cognitive MISO SWIPT NOMA system with
L SUs, and
M EH receivers that coexist with
K PUs via the underlay scheme, as shown in
Figure 1. In the proposed underlying CR system, the secondary network can operate in the same frequency band as the primary network, provided that the interference towards the primary users is kept at a tolerable level. We also consider the presence of one malicious eavesdropper that attempts to intercept confidential information of the SUs. Furthermore, the SU-Tx is equipped with
N antennas, while there are single antennas for the PU, SU, and EH receivers, and for the eavesdropper. Moreover, we consider the SUs to be hybrid users capable of decoding information and harvesting energy at the same time by employing a PS structure in the receiver, while energy is harvested by the EH receivers. Moreover, the SU-Tx transmits AN to cause interference with the eavesdropper while improving information secrecy. The SU-Tx is in charge of transmitting the signals towards the SU and the EH receivers, as well as, design the beamforming vectors for the multi-antenna scheme. Then, the signal transmitted from the SU-Tx can be expressed as:
where
represents the beamforming vector for the
l-th SU with
,
is the transmitted signal of the
l-th SU with unit power
,
denotes the beamforming vector for the
m-th EH receivers with
,
is the energy signal of the
m-th EH receiver with unit power
,
corresponds to the beamforming vector for the AN, and
r is a zero-mean Gaussian random variable with unit power
, which is artificial jamming. Beamforming vector
is used to prevent anything from affecting legal transmissions, and artificial jamming
r is randomly generated to effectively disturb any eavesdropping [
14].
Accordingly, the received signal at the
l-th SU is written as
where
is the channel vector from the SU-Tx to the
l-th SU,
is the additive white Gaussian noise (AWGN) at the
l-th SU, with zero mean and variance denoted as
. In addition, we assume the SU-Tx has perfect CSI.
Without loss of generality, we consider the first SU to have the strongest channel strength, whereas the
L-th SU has the weakest. As such, the order for channel gain between the SU-Tx and the SUs can be expressed as follows:
In NOMA systems, by using the successive interference cancelation procedure, the
l-th SU
should be capable of successively extracting and decoding the signal intended for the weaker SUs
from the received signal. Therefore, the following condition for SIC in MISO-NOMA networks with different channel strengths should be satisfied:
The condition expressed in (4) will be referred to as the SIC constraint in the rest of the paper. The condition (4) guarantees that at the
l-th SU, we have a higher SINR from messages of more distant users since these messages need to be decoded prior to decode the
l-th user’s own message. Accordingly, the received signal after removing the last
user signals can be given by
where the first term in (5) denotes the intended signal for the
l-th SU, whereas the second term represents the interference caused by the first
signals intended for the SUs
. The PS structure at the SUs is based on a PS factor which divides the incoming RF signals into two streams; one to be used for ID and another to harvest energy. It is noteworthy that optimizing the PS factor is required to achieve an optimal trade-off. Then, the achievable SINR for the
l-th SU when decoding the signal intended for the
i-th SU can be expressed as
where
is the PS factor to divide the incoming signal into the ID and EH modules, and the additive circuit noise in the ID module of the
l-th SU is defined as
. It is worth highlighting that (6) is true only after performing SIC on the preceding
signals.
Moreover, the energy harvested by the EH module in the
l-th SU can be written as follows:
In (7),
is the energy-harvesting efficiency for the
l-th SU. For simplicity, we assume that energy-harvesting efficiency is always equal to 1,
. The energy harvested by the
m-th EH user is given by
where
is the channel vector from the SU-Tx to the
m-th EH user, and
is the variance of the antenna noise
at the m-th EH user, i.e.,
.
The power of the SU-Tx causing interference with the
k-th PU can be defined as
where
is the channel vector from the SU-Tx to the
k-th PU.
Moreover, the SINR for information signals of the SUs overheard by the eavesdropper is given by
where
is the channel vector from the SU-Tx to the eavesdropper, and
is the variance of the antenna noise
at the eavesdropper i.e.,
. Moreover, we assume that
dBm.
3. Beamforming Optimization with AN
In this paper, we propose a beamforming optimization scheme to provide security in a MISO SWIPT CR-NOMA network. We consider a practical scenario where the SU-Tx does not have the CSI of the eavesdropper. To further increase the secrecy performance of the network, AN is generated to tackle eavesdropping and guarantee the security of the confidential information of the unlicensed users. In particular, we minimize the transmit power for the SUs and EH users, subject to the constraints of a minimum SINR for the SUs, minimum EH by the SUs and EH users, maximum available power for the SU-Tx, and maximum interference power to ensure the PUs’ legitimate transmissions are not affected. The idea of minimizing transmit power for the SUs and EH users is to use the rest of the available power at the SU-Tx to maximize AN and protect transmitted messages against an eavesdropper. In addition, SDMA and ZF baseline schemes are developed along with MISO CR and SWIPT for comparison purposes.
3.1. Beamforming Optimization with AN in the MISO SWIPT CR-NOMA Network
The SU-Tx power for transmitting to SUs and EH users is minimized in the proposed network by satisfying the QoS requirements of each user and in accordance with the decoding order of the SIC indicated in (4), as follows:
where
is the minimum targeted SINR for the
i-th message,
,
is the minimum harvested energy required by the
l-th SU,
is the minimum harvested energy required by the
m-th EH user,
denotes the maximum available power at the SU-Tx, and
denotes the maximum permissible interference with the k-th PU. Constraint (11b) is to guarantee a minimum SINR for the messages from
to
at the
l-th SU, while constraints (11c) and (11d) represent the minimum harvested energy required by the SUs and the EH users, respectively. Constraint (11e) indicates the maximum available power,
that can be consumed by the SUs, the EH users, and AN. Constraint (11f) indicates that the transmit power for the SUs, the EH users, and for AN must not exceed the maximum permissible interference with the
k-th PU, given by
. Problem (11) is not convex or challenging to solve due to the coupling between the PS ratios,
, and the precoding vectors,
,
, and
, in constraint (11b). Therefore, problem (11) cannot be solved directly.
We derive an optimal solution via SDR [
38] for problem (11). Define
,
,
,
,
, and
,
. Based on the properties
,
, and
, we can derive the following expressions:
,
,
,
,
, and
. Moreover, a matrix variable,
, is equivalent to
being a rank-one symmetric positive semidefinite (PSD) matrix, i.e.,
, and
. Thus, we can express problem (11) in the following equivalent form:
Problem (12) is still non-convex due to the rank-one constraints. Then, we can drop the rank-one constraints to get an SDP problem denoted as (12)-SDR, which is convex and can be solved by using the CVX toolbox of MATLAB. To define the computational complexity to solve the (12)-SDR problem, we define as the number of matrix variables of size , and is the linear constraint. Then, we can denote the computational complexity to solve problem (12)-SDR as ) with a solution accuracy of χ > 0. The solution to problem (12)-SDR is denoted as {, , }, F*, which is unlikely to satisfy the following constraints: rank (Vl) = 1, rank (Wm) = 1, rank (F) = 1, ∀l, ∀m. Therefore, we propose a Gaussian randomization technique to obtain the close-to-optimal solutions for problem (11).
In the Gaussian randomization technique [
13,
14,
39], the first step is to perform eigen decomposition of the precoder matrices obtained from problem (12)-SDR, i.e., we evaluate
,
, and
. Next, we generate candidate solutions based on vectors
,
, and
, where the elements follows a complex, circularly symmetric Gaussian distribution,
, i.e.,
,
and
. However, there exists the possibility that the obtained candidate precoder vectors are not feasible for problem (11). Then, we can adjust the value of the candidate precoded vectors based on scalar factors,
, which can be obtained through the solution to the following optimization problem:
Problem (13) is a linear program that can be solved with the CVX module of MATLAB. In the Gaussian randomization technique, we generate
candidate precoder vectors, where the final solution is the one that achieves the lower transmit power. The proposed algorithm with SDR and the Gaussian randomization technique is summarized in Algorithm 1.
| Algorithm 1: The proposed algorithm based on SDR and Gaussian randomization to solve problem (11). |
![Electronics 09 01948 i001 Electronics 09 01948 i001]() |
3.2. Beamforming Optimization with AN in the MISO SWIPT CR-SDMA Network
In this subsection, we describe the baseline scheme based on SDMA for the MISO SWIPT CR system. In SDMA, the messages from other users are considered interference, and no SIC procedure exists at the receiver. Therefore, the SINR at the
l-th user is as follows:
Although the energy harvested by the SUs and the EH users, as well as the power interfering with the PUs, are expressed in the same way as NOMA, and are defined in (7)–(9), respectively. Then, the minimization of the transmit power for the SUs and EH users under the constraints of minimum SINR, minimum EH required, and maximum interference with the PUs can be expressed as follows:
Problem (15) is non-convex and can be solved by using the SDR technique described in
Section 3.1. Then, problem (15) can be reformulated as follows:
After removing the rank-one constraints, the problem is denoted as (16)-SDR, which is convex and can be solved with the CVX toolbox of MATLAB. Then, the Gaussian randomization technique can be used if the precoder matrices, , do not satisfy the rank-one condition.
3.3. Beamforming Optimization with AN in the MISO SWIPT CR-ZF Network
In this section, we include a comparative scheme based on ZF to solve the power minimization problem in the cognitive MISO SWIPT system. The ZF scheme allows the nullification of the interference signals from other users, which is considered to be a common approach used to simplify the system design [
35,
40]. At the
l-th SU user, we design the ZF scheme to null the interference from other SU’s messages and from the energy signals. At the
k-th PU user, the ZF scheme nulls the interference from the SU’s messages and from the energy signals. However, to increase the harvested energy at the EH users, we allow interference signals at the EH users. Then, we define
and
. Therefore, we denote the beamforming vectors as follows:
where
and
are the power variables to be optimized,
is the orthogonal basis of the null space of
and
is the orthogonal basis of the null space of
. Based on the ZF scheme, the transmit power minimization problem (11) can be transformed into the following problem:
Next, we solve the problem (21) by using the SDR technique. We denote
,
,
,
,
,
,
and
.
where
,
and
. Then, we drop the constraint (22i) and obtain an SDP problem denoted as (22)-SDR, which is convex. The solution of (22)-SDR can be obtained through the CVX toolbox. The Gaussian randomization technique, detailed in
Section 3.1, is used to obtain the approximate rank-one solution for the ZF-based problem (21).
4. Numerical Results
In this section, simulation results are provided to assess the performance of the proposed MISO-NOMA-CR aided by SWIPT with EH users, in comparison with an SDMA approach and with a scheme without AN. We used MATLAB software on a Core i7-6700K CPU with 16 GB of main memory to perform the simulations over several channel realizations. The simulation parameters listed in
Table 2 were selected based on the work in [
15,
41,
42]. More specifically, the transmission power of the SU-Tx is set to 30 dBm since it is a common value used in the literature for CR systems [
30,
41]. In addition, the channel vectors parameters such as the channel gain and the Rician factor were set to
and 5 dB, respectively, based on the work in [
15]. The number of SUs and the value for the path-loss exponent are stablished according to the reference [
42].
In the considered paper, we consider a quasi-static channel condition, which is usually assumed for indoor channels where the degree of time variation in the signal strength is small compared with the symbol duration. The channel model used in the simulations considers different distances from the SU-TX to the users, as well as different angle directions. The channel vectors were modeled based on an independent Rician fading, which is composed of a line-of-sight component and scattering components, and it is given as follows [
15]:
where
is the Rayleigh fading component, which follows a circularly symmetric complex Gaussian random variable with zero mean and unit variance, and
is the line-of-sight component. The line-of-sight component is based on a uniform linear array from [
16] with a wavelength equal to the double of the spacing between successive antenna elements, and it is given as follows:
where
denotes the direction from the SU-Tx to the
l-th SU, set at
and
. Channel vectors
from the SU-Tx to the
m-th EH user were generated by following the aforementioned procedure, with the directions
and
pointed out in
Table 2. Moreover, channels vectors
and
follow Rayleigh fading with an attenuation equal to
and the distances from the SU-Tx to SUs, EH users, PUs, and the eavesdropper are defined in
Table 2.
Furthermore, the proposed model can be adapted to several scenarios since we do not consider a fixed number of users. Instead we assume that there exist L SUs and M EH receivers. It is worth highlighting that the proposed approach is valid for other channel model because in a real deployment the inputs are channel state information (CSI), which can be obtained by a feedback process between the transmitter and the users and by cooperation between the primary and secondary network.
The simulation results in this section are the average over several independent channel realizations, where the Rayleigh fading component of the channel vectors varies in each channel realization. Please note that new beamforming vectors and PS ratios should be obtained each time the channel conditions changes, which is not the best solution in fast time-varying channels because of the computational complexity of solving the optimization problem.
First, we investigated the results for problem (11) by using the SDR technique. Furthermore, we compared the results with the SDMA scheme, ZF technique and with the scheme without using AN.
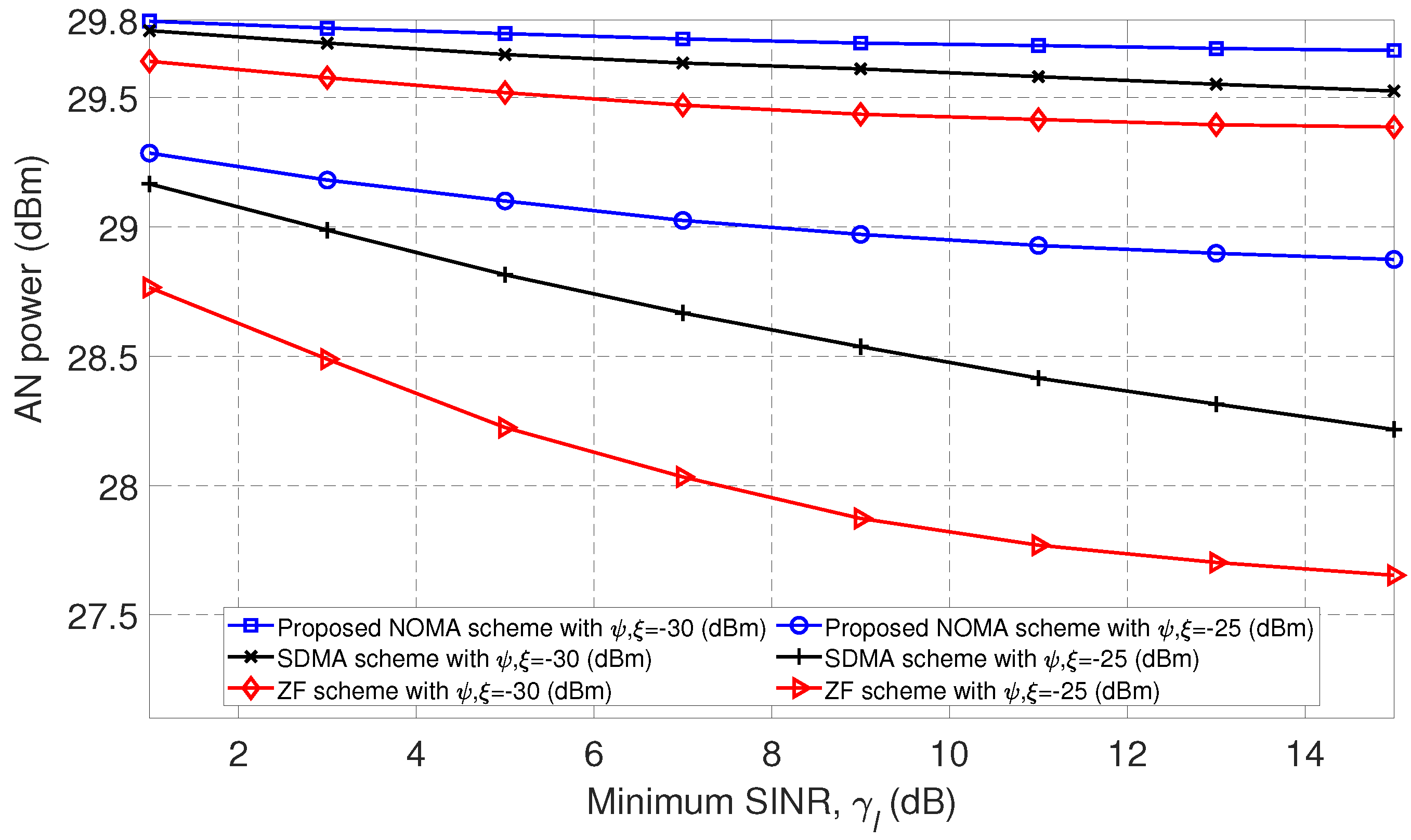
Figure 2 shows AN power,
according to the minimum SINR required at the SUs when minimum EH requirements of the SUs and EH users are given as
dBm and
dBm, respectively. We observed that the radiated AN power is decreased as the minimum required SINR increases, because the SU-Tx needs to allocate more power to satisfy the SINR constraint while reducing the available power for the artificial noise. In addition, the proposed scheme based on the NOMA technique outperforms the SDMA method and ZF scheme for two considered cases of minimum EH. The improvement from the NOMA technique is due to the ability to decode part of the interference from other messages via the SIC procedure, which allows an increase in the achievable SINR at the SUs while reducing the required transmit power to satisfy the minimum SINR constraint. Subsequently, the NOMA technique can provide a high level of PLS, because the interference with the eavesdropper increases as the AN power increases, which makes it difficult for the eavesdropper to decode the SU’s messages. The SDMA method outperforms the ZF scheme because ZF nulls the interference from other SU’s and EH’s messages at the
l-th SU which permits an increase of the SINR but affects the harvested energy. Subsequently, the ZF scheme harvests lower energy than that harvested by the SDMA approach, which makes that the SU-Tx increases the transmission power to satisfy the EH constraint while reducing the available power to allocate to the AN.
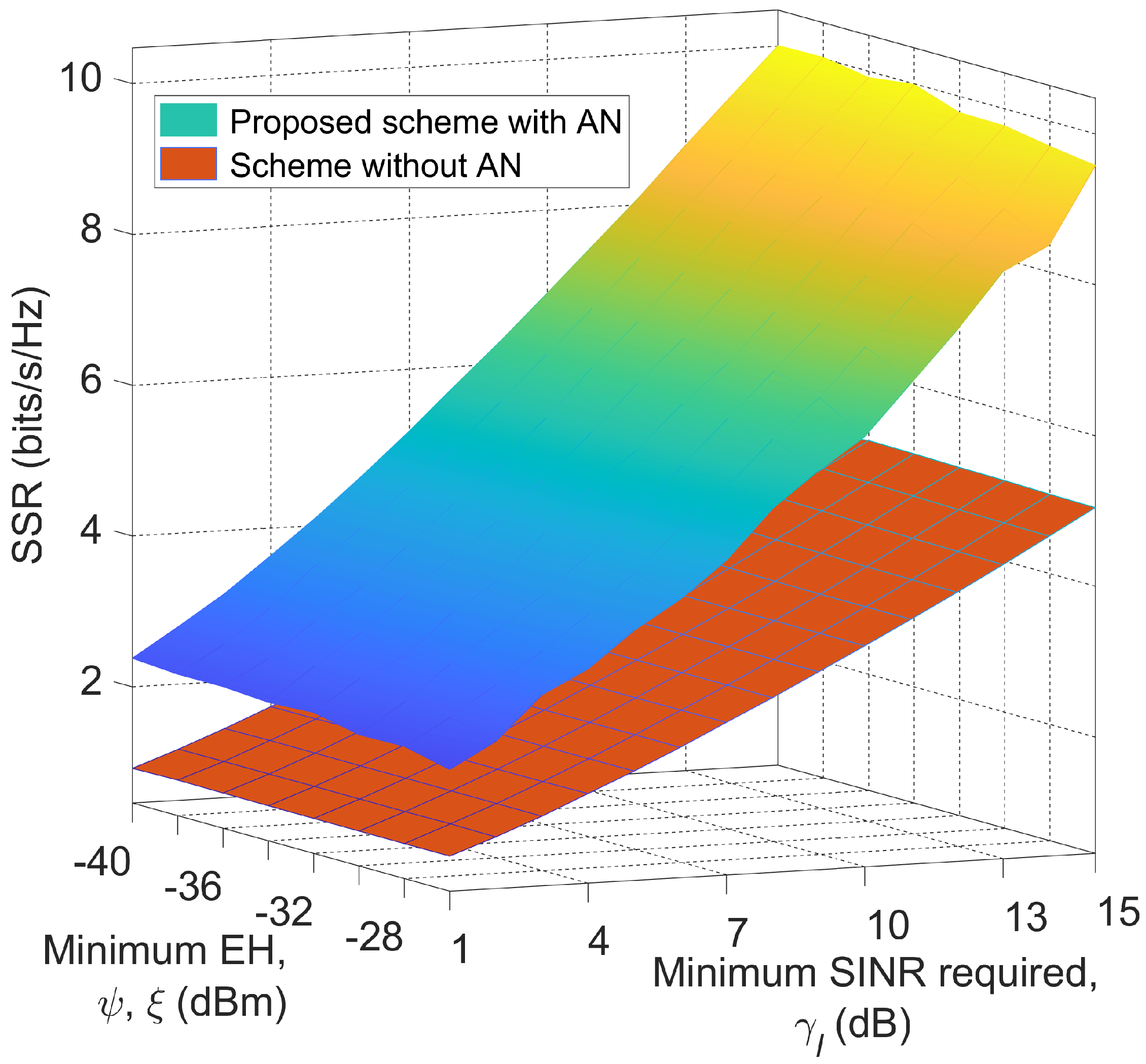
Figure 3 illustrates the SSR achieved with the proposed approach and with the scheme without AN, according to the minimum SINR and minimum EH requirements, with maximum permissible interference with the PUs equal to
dBm. From
Figure 3, we can observe the benefit of the proposed approach with AN on increasing the achievable SSR, because AN can effectively generate interference with the eavesdropper while the beamforming technique minimizes that interference at the SUs. We note that the SSR grows as the minimum SINR increases, and this trend coincides with previous research [
13,
14] because the achievable transmission rate at the SUs increases. In addition, the SSR reduces as the minimum EH requirement increases because more power needs to be allocated to satisfy the EH requirements while reducing the available power for AN.
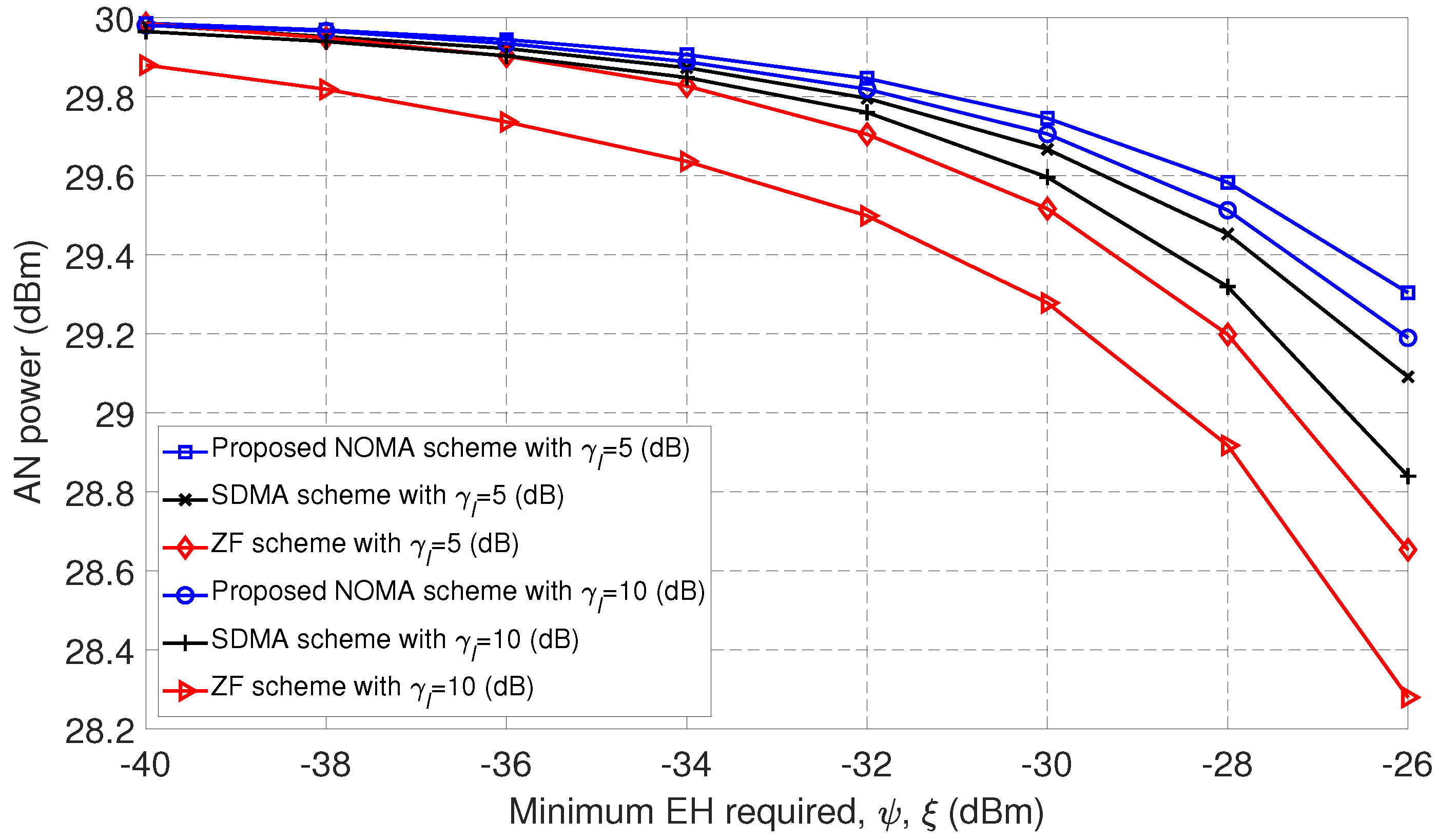
Figure 4 shows AN power according to the minimum harvested energy by the SUs and the EH users when the minimum SINR of the SUs is given as
dB and
dB, respectively. From
Figure 4, we can see that AN power decreases for all the considered schemes as the minimum EH requirement increases. The reason is because as the minimum EH increases, more transmission power should be allocated to the users to satisfy their EH requirements. Subsequently, less power is assigned for the AN. Furthermore, we can see that the proposed scheme outperforms SDMA and ZF, since NOMA can achieve higher values of AN power due to the SIC application to nullify interference with other users while causing interference with the eavesdropper to improve network security. Similar to
Figure 2, the ZF condition of canceling the interference makes it necessary to transmit more power to satisfy the EH requirements at SUs.
Figure 5 shows the AN power according to the interference threshold when the minimum EH requirements of the SUs and EH users are given as
dBm, and the minimum SINR for the SUs are
dB and
dB. From
Figure 5, we can see that the AN power increases along with increasing interference threshold values for the PUs. As the interference threshold increases, the SU-Tx can transmit more power to the SUs and EH users that includes AN power to tackle the eavesdropper’s wiretap. Moreover,
Figure 5 also verifies that the proposed scheme outperforms the other baseline schemes. This can be explained as follows: Unlikely to SDMA and ZF, NOMA can perform SIC to decode part of the interference caused by other users, which allows transmitting less power to satisfy the QoS requirements of the users and more AN power which results in better PLS in the network. The results obtained by ZF are due to the condition of designing the beamforming vectors to null the interference at the PUs, where the constraint (21f) of maximum interference allowed to the PUs only depends on the beamforming vector of the AN.