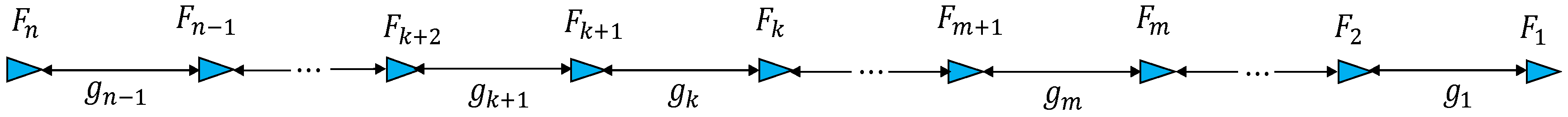1. Introduction
A self-organized dynamic vehicular network supports various types of communications [
1,
2]. The communication links between the vehicles can significantly improve the driving safety and traffic control [
3]. A vehicle-to-everything (V2X) network supports various types of safety applications which can be utilized to warn the drivers about potential dangers. All safety applications, however, rely on recent dynamic information exchanged between the vehicles via vehicle-to-vehicle (V2V) or vehicle-to-infrastructure (V2I) networks. This dynamic information can be represented as a map which is updated every predefined period to cope with dynamic nature of V2X network. This map is called as a local dynamic map (LDM) and its standard definition is given in [
4]. The LDM contains static and dynamic components of the roads. Using the LDM, each vehicle can discover its surrounding neighbors and identify the recent changes on the road. The LDM can be constructed at various scale using V2X technologies. V2X can also be considered as a key technology that enhances a driving safety.
Every year, road accidents cause approximately 1.35 million deaths worldwide (on the average 3700 people lose their lives every day on the roads) [
5]. In order to reduce the sudden maneuvers (lane change, abrupt speed change, emergency brake) that cause the accidents, each vehicle needs to share its mobility updates with other vehicles. According to IEEE 1609 and ETSI 102 687 standards [
1,
2], each vehicle periodically broadcasts a basic safety message (BSM) to announce the latest dynamic updates within one-hop communication range [
6]. Using the BSM messages, each vehicle can build its own one-hop range LDM dataset and exploit it while avoiding potential threats. However, one-hop range LDM data may not be sufficient to ensure road safety. In order to create a multi-hop range LDM dataset, vehicles can disseminate their one-hop range LDM data via a multi-hop process.
Both V2V and V2I can be used for data dissemination in the vehicular network [
7,
8]. In this paper, we consider only V2V communication for simplicity, while it can be easily extended to networks with both V2V and V2I. During the multi-hop LDM data dissemination, however, a standard V2V communication protocol may not guarantee an expected performance since it suffers from a hidden node collision—two vehicles transmitting packets at the same time cause collision at the common receivers.
To ensure the driving safety and enhance the traffic management, the proposed method propagates one-hop range LDM data to construct the multi-hop LDM data. In our method, we use a clustering method to propagate map information in a multi-hop fashion, so each vehicle can obtain the latest position and mobility information of all remote vehicles (vehicles located beyond the communication range). It introduces novel algorithms to avoid the hidden terminal collision and mitigates the interference between the clusters (hereafter, we call it inter-cluster interference). The main contributions of the proposed method are as follows:
It introduces a new efficient clustering method which significantly reduces data overhead in multi-hop LDM transmission.
It employs a low-cost forwarder election algorithm that elects the optimum set of forwarders.
To reduce an inter-cluster interference, it presents a cluster coloring algorithm that allocates optimal transmit windows to adjacent clusters.
It maximizes the inter-cluster transmit window (color) reuse factor by re-allocating their colors.
The proposed algorithm improves the range of multi-hop propagation and reduces the interference among hidden terminals.
The rest of the paper is organized as follows.
Section 2 provides a review for the related works.
Section 3 presents the network model for LDM construction, while
Section 4 introduces the proposed clustering method. In
Section 5, we describe a forwarder election algorithm; while in
Section 6, we explain a transmit window allocation algorithm based on cluster coloring. Simulation results are shown in
Section 7 followed by the conclusion and future work in
Section 8.
2. Related Work
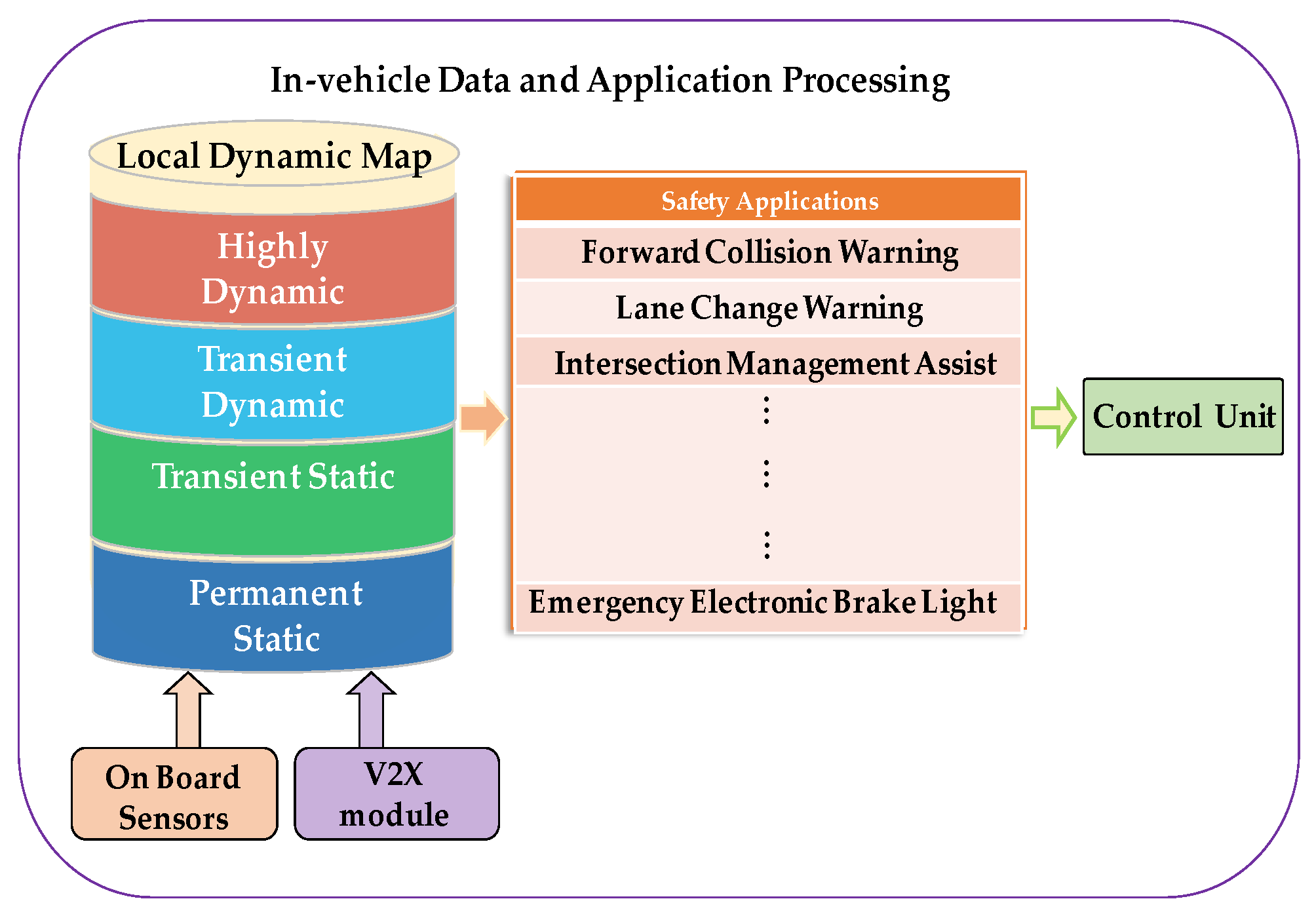
In vehicular network based on the ETSI 102 687 standard, each vehicle attempts to collect up-to-date information from surrounding vehicles. Then, the vehicle stores this information in LDM, which is employed while making driving decisions and avoiding accidents. The LDM is updated in every predefined period. Data stored in the LDM is divided into four levels: (1) permanent static, (2) transient static, (3) transient dynamic, and (4) highly dynamic [
9], as presented in
Figure 1. The first and second lowest levels represent the static map details such as roads, intersections, lanes, etc. The third and fourth levels contain the dynamic components of the map, such as a phase of a traffic signal, weather condition, and vehicles (position, speed, heading, etc.) on the road [
9].
Many previous methods are primarily focused on the algorithms to improve the propagation of emergency packets with a few hundred bytes. In [
10], the authors proposed a data propagation scheme that relies on V2V communications. In this work, the authors introduce so-called lateral crossing line (LCL) algorithm, which elects a set of relay vehicles to retransmit an emergency message in each hop. Based on the receivers’ location from the source of the emergency message, LCL calculates an overlapped area of the source’s and receiver’s wireless ranges and converts this area value into a back-off timer. If the receiver obtains the shortest back-off timer, then it becomes a relay vehicle for the corresponding hop. However, the authors of [
10] did not consider an aggregation of one-hop safety messages and construction of LDM data. Moreover, their method did not specify the inter- and intra-cluster communications. They considered only propagation of small emergency messages generated by the particular vehicles in specific segments of the road.
Another promising study was conducted by Rayeni et al. [
11]. Depending on the density, the authors proposed a dynamic partitioning scheme, which divides the backside of the transmitter’s wireless range into small partitions. These partitions associate with various forwarding priorities, which can be determined by assigning different back off timers. As the neighbor distance becomes further, it obtains a shorter back off timer. The length of each partition varies depending on the vehicle density. This scheme, however, assumes that there is always one spare radio which is utilized to generate a busy tone signal. This signal is expected to cover twice distance of the wireless range so that a hidden terminal problem can be resolved. Practically, this assumption can be considered as a waste of resources, and yet it may not provide a complete solution for a hidden node problem.
An infrastructure-based data propagation can enhance the coverage in a vehicular network. Therefore, the literature [
12,
13,
14,
15] contains many studies that introduce various approaches to use roadside units (RSUs) in message propagation. The authors of [
12] introduced a delay-bound RSU-based data dissemination algorithm. For a given delay bound, this algorithm identifies an optimum number of RSUs to propagate the data in the pre-defined region. Similarly, authors in [
13] developed heuristic algorithms to maximize the number of vehicles served by each RSUs in vehicular network. Some of the studies [
14,
15] formulated RSUs′ deployment problem as an integer linear problem (ILP). They proposed the particular configuration to enhance data propagation in a vehicular network. The authors of [
12,
13,
14,
15], however, made a tradeoff between the cost and data dissemination in the target region.
The authors of [
7] proposed a method that combines V2I- and V2V-based data propagation. They deploy RSUs far enough from one another so that data between them can be exchanged through the V2V-based multi-hop communication. If there is neither a single-hop nor multi-hop communication link between the vehicles and RSU, the message can still be delivered to other RSUs through a carry-store-forward scheme [
16]. An efficient data dissemination can also be organized through the clustering methods. The nodes can be grouped together into clusters, each of which contains one cluster head (CH) and group of member nodes. Normally, the CHs control data transmission and reception procedures. Authors in [
17] proposed a hybrid architecture which combines Cellular V2X (C-V2X) and IEEE 802.11p with goal of achieving high packet reception ratio and low dissemination latency in multihop communication among the clusters. They minimized the usage of cellular infrastructure while propagating data in a multi-hop fashion. Their cluster selection technique utilizes the mobility information of the vehicles and selects the one which has a minimum average relative speed with other vehicles. The inter-cluster communication is conducted whether through predefined intermediate nodes or directly (direct connection of cluster head with another cluster) using LTE base stations.
In [
18], authors introduced fuzzy inference system (FIS) to construct a clustered network to extend the network lifetime and reduce the packet loss. Their method applies a fuzzy logic to analyze various network parameters while choosing the CHs. Authors considered residual energy, moving speed, and pausing time of the nodes as the input parameters (descriptors) into FIS. Based on these descriptors, FIS outputs the probability (chance value) of nodes to be selected as CH. However, the clustering methods introduced in [
18] are designed for fixed and less dynamic WSNs and hence, it may not produce an expected results for the high dynamic networks. Moreover, it did not consider inter-cluster message exchange which is an important process for our target application.
An interesting clustering approach was introduced in [
19] where a distributed vehicular network was transformed into clustered network. The CHs are selected through the fitness value computed by each vehicle. In the initial stage, each vehicle discovers its neighbors by exchanging hello messages and then, each vehicle collects the following data: (1) time of transmission hello messages; (2) relative velocity; (3) an approximate link validity period; and (4) connectivity degree (density). Using this data, each vehicle calculates its fitness value and then broadcasts it to the neighbors. Then, the node with the smallest fitness value is selected as CH for the group of vehicles. In this method, the member vehicles may communicate with CHs directly or through relay nodes. It means the size of the cluster can be larger than the wireless range of the CH. However, the authors did not provide sufficient details about the intra-cluster communication process. In LDM construction, intra-cluster communication is a very crucial process.
Authors in [
20] proposed a clustering-based multichannel medium access control (MAC) protocol to broadcast the safety messages. The authors differentiated the data traffic into two classes: (1) real-time traffic and (2) non-real time traffic. The CHs are defined by the timer-based election procedure. A new vehicle joins to the existing cluster if it receives an advertisement message within this timer. It becomes an independent cluster otherwise. Their MAC protocol maintains four different channels: (1) inter-cluster control channel; (2) inter-cluster data channel; (3) cluster-range control channel; and (4) cluster-range data channel. Inter-cluster control and cluster-range control channels are used for transmission of real-time traffics while the remaining channels are used for non-real time traffic. The vehicles access the cluster-range control channel through contention-free accessing mechanism while access to the inter-cluster control channel is conducted via a contention-based scheme. The authors applied code division multiplexing access (CDMA) mechanism to organize interference-free intra-cluster data (non-real time traffic) communication. As we can see, their MAC protocol combines various access mechanisms which makes the process of practical implementation very complex. In addition, to reduce hidden terminal interference, this protocol employs twice as much transmission power to conduct inter-cluster communication. However, the hidden terminal interference still may occur in larger scale (while sending aggregated LDM message) due to contention-based access mechanism. In this method, CH should manage resource allocation process in four different channels at a time which may become very complex in reality.
In [
21], the authors presented a cluster-based beaconing algorithm that is aimed to provide local proximity maps to all vehicles. This local proximity map allows vehicles to detect the accidents in highway road. This algorithm aims to enhance the two criteria. First, the map used by the vehicles should have accurate details. Second, all vehicles in the vicinity should be coordinated with this map. It uses the cluster-based beaconing (aggregate-forward) scheme to distribute the vehicle proximity map. This scheme enhances the network performance since it uses different transmit windows during the data aggregation. After that, it selects a temporary forwarder that disseminates the map data in the common transmit window. Therefore, inter-cluster communication in this method degrades due to hidden terminal interference.
In most multi-hop data dissemination methods, vehicle information is disseminated through multiple transmissions conducted by selected forwarders. Since the transmissions are broadcast, the forwarders cannot verify whether their messages are successfully received by all target receivers. Moreover, in vehicular network, position of the vehicles frequently changes as they move with various velocity. Since vehicles’ data is propagated over the wireless channel, many factors can cause communication failure. One primary factor is the hidden terminal problem that creates severe interference and incurs significant packet reception loss. The hidden terminal problem often reduces the broadcast coverage by half [
22,
23].
Therefore, it is crucial to facilitate a robust and scalable propagation method to disseminate large-scale map data in multi-hop vehicular networks. Thus, we propose a dynamic map propagation (DMP) method which can cope with a hidden terminal effect and provides efficient LDM data propagation over the V2V links. It elects forwarders and constructs optimal clusters in a distributed vehicular network. We apply a cluster coloring technique that allocates colors to clusters as transmit window. Our proposed algorithm supports both the IEEE 1609 and ETSI 102 687 as underlying standard protocols.
3. Network Model
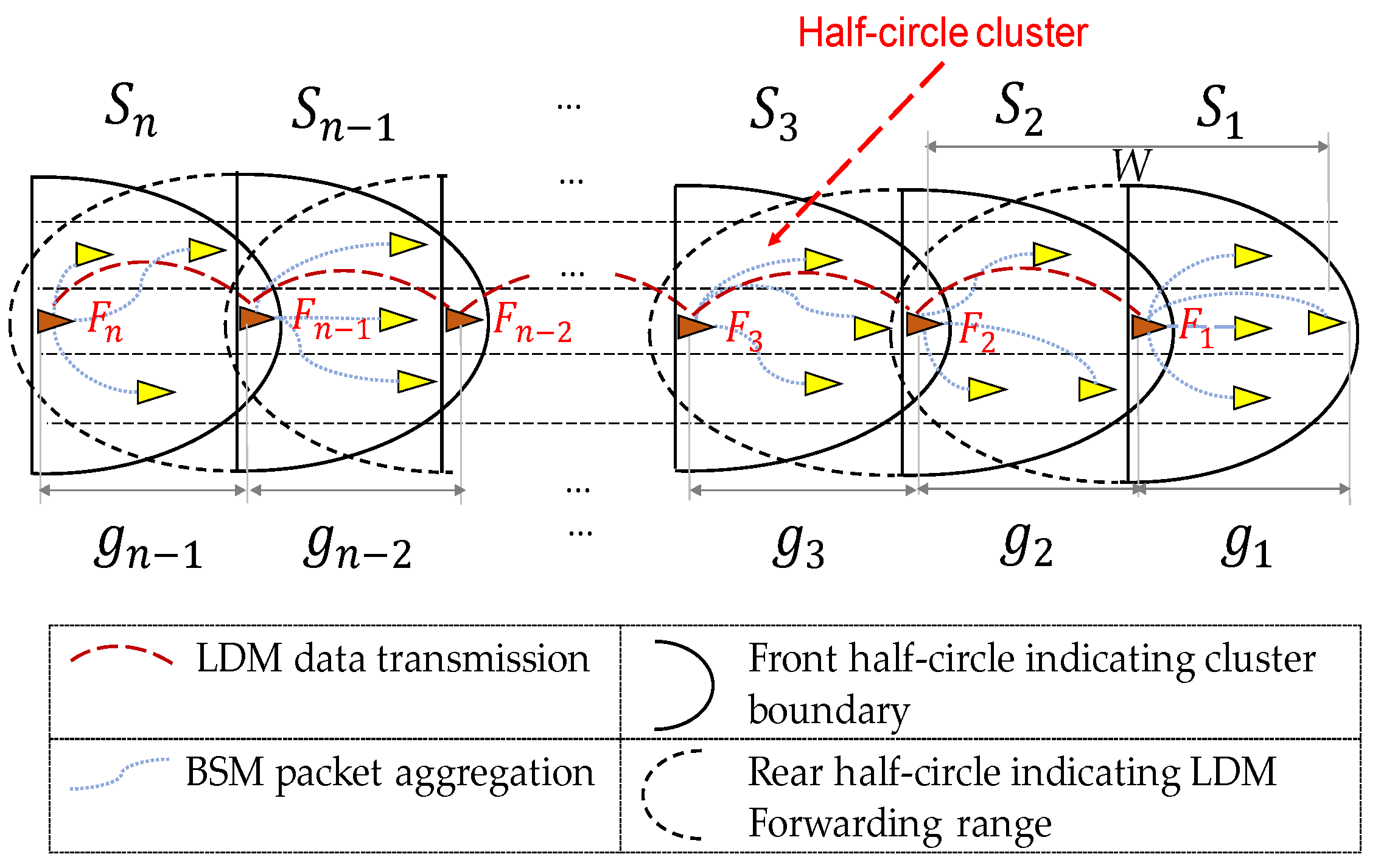
As a network model, we consider a multi-lane highway road shown in
Figure 2. In our highway network model, we consider one direction at a time to construct individual clustered networks.
Figure 2 considers only right direction lanes. The opposite direction can produce another clustered network in a similar fashion. To eliminate the interference, the vehicles travelling in the opposite direction may transmit their data over different channel. The road of
Figure 2 contains a set of vehicles defined as
, where
represents an individual vehicle. Then,
is divided into a set of clusters, which is represented by
In
Figure 2, our proposed clusters are denoted by solid half circles, whereas the full circle denotes the wireless range from each forwarder. A cluster
comprises two types of nodes: (1) member nodes
’s denoted by yellow triangles; and (2) forwarder node
Fi denoted by red triangles. The forwarder node is elected among the member nodes that is located in the rear end of the cluster, as presented in
Figure 2. The cluster size is denoted by the front half-circle of forwarder’s wireless range as indicated with the solid lines in
Figure 2. We assume that all member nodes in the cluster travel in the same direction (towards the right direction as indicated by the triangles of the nodes). The clusters are separated by a set of inter-cluster gaps,
where each
represents the gap (or distances) between the forwarder
of
and the forwarder
of
.
Each vehicle is equipped with a V2X communication device. This device includes a global positioning system (GPS) receiver which provides an accurate time synchronization information. Hasan et al. [
24] showed through real experiments that the GPS synchronization provides an accuracy of tens of nanoseconds which is sufficient to organize a slotted channel concept. The V2X device also broadcasts a basic safety message (BSM) over a predefined control channel using the IEEE 1609 standard [
1]. The BSM message contains mobility details (position, velocity, acceleration, heading, steering wheel angle, yaw rate, etc.) of the transmitter node. The BSM is sent with a period
(hereafter, it is referred as a beaconing period). Since each vehicle declares its mobility information inside the BSM message, the forwarders can easily identify the group of neighbors travelling in the same and opposite directions. From the received BSMs, each vehicle can also identify its leading and lagging (in behind) neighbors. Each forwarder
collects BSM packets from all member nodes in its cluster
indicated by solid half circles in
Figure 2. From the collected BSM packets,
of
constructs the LDM data. Then,
forwards this LDM data to the next (i.e., lagging) cluster
which are indicated by the dotted half circles in
Figure 2. This forwarding process is repeated through forwarders in multi-hops, so all vehicles in the lagging clusters can receive LDM data from the preceding neighbors. If a member vehicle
of the cluster
changes its heading, then
’s updated heading is included in its BSMs. Receiving the BSMs from
, forwarder
adds
’s new heading information in the LDM and then forwards it to lagging clusters. If
drastically changes its heading (
turns to different direction or road), then within the acceptable latency, this information is propagated to remote lagging vehicles inside the aggregated LDM packet. While transmitting the BSM packet, each member node conducts a contention-based broadcast within allocated transmit window. In this paper, we assume a fixed wireless range denoted as
for simplicity of presentation. For other notations used in this study, reader can refer to
Table 1.
LDM Data Construction
In this paper, we consider two levels of LDM data construction. The first level is the construction of a one-hop range LDM data. This LDM data represents the dynamics details of single cluster. The second level is multi-hop range LDM data which comprises a set of one-hop range LDM data aggregated through multiple clusters. A multi-hop range LDM data can be constructed via a multi-hop propagation of one-hop range LDM packets.
As we mentioned, in a vehicular network, every vehicle broadcasts BSM [
6] in every
period. Taking advantage of this feature, a forwarder of each cluster can act as an aggregator of BSM packets received from its members. We use
to denote the total number of member nodes within the cluster
. Then, in the first level, forwarder
collects BSM data of
members. Then,
constructs a local LDM data of cluster
. Before forwarding the data,
combines its LDM data with the one received from leading clusters. The LDM packet size is proportional to the number of vehicles
in each cluster. The number of vehicles in the cluster is constrained by predefined
, which is mathematically defined by Equation (12) in
Section 6. The aggregated LDM packet size is bounded by the acceptable range of the IEEE 1609 standard.
As the network density grows, the conventional protocols tend to suffer from serious performance loss due to hidden node problems. To reduce the hidden terminal interference, we partition
into multiple transmit windows where each transmit window is assigned to specific cluster to perform the communication. One window can be assigned to multiple clusters as long as these clusters are far enough, so they do not interfere. For instance, in
Figure 2, clusters
,
, and
can be allocated to different transmit windows. Then, these clusters conduct their communication in the different transmit windows, and therefore, interference between these clusters can be significantly reduced.
4. Proposed Clustering Method
In this section, we first describe our novel clustering method. We then prove that our clustering method can reduce communication overhead (the time to transmit the redundant data) compared with a conventional clustering method.
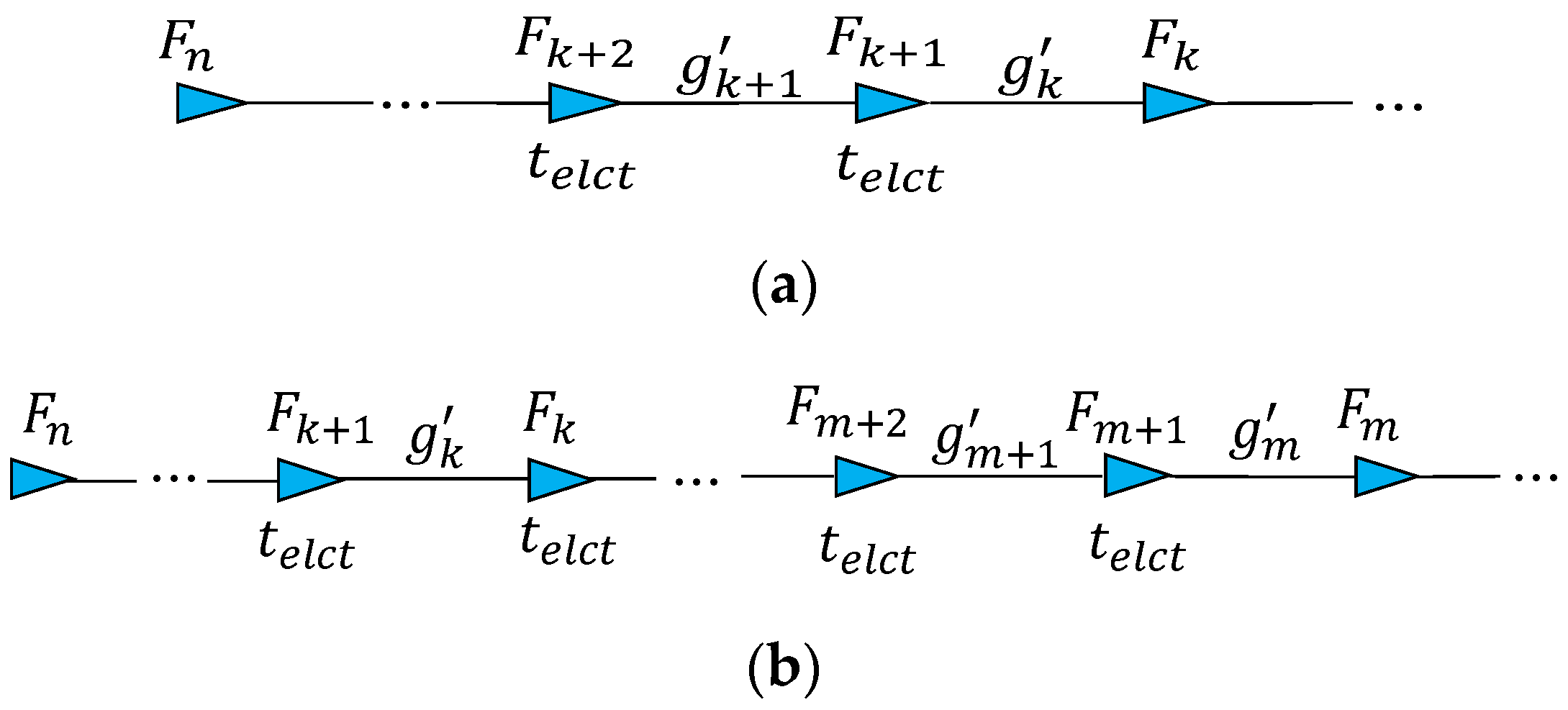
As shown in
Figure 3, our clustering method differs from the conventional clustering method utilized in [
21,
25]. In the conventional clustering method of
Figure 3a, a cluster head (CH) considers all nodes within the wireless range as the cluster member nodes. Therefore, we refer to it as ‘full-circle clustering method’, since the wireless range of CH is assumed to be in circular shape. The CH communicates with neighbor CHs through a pair of gateways (GW). The CH organizes an intra-cluster communication session to collect the periodic packets of all member nodes. Then, it generates the LDM packet and then broadcasts it to all its member nodes. Upon receiving this packet, each GW node executes additional broadcast to forward the received LDM packet to neighboring clusters. In the full-circle clustering method, the LDM packet of each cluster must be transmitted three times in order to deliver this LDM data to neighboring clusters.
Additionally, in the full-circle clustering method, the LDM data of lagging clusters is unnecessarily propagated to the leading clusters. To increase the safety, each vehicle should know a recent mobility information of its leading neighbors. Thus, a forward propagation of LDM data is considered as an unnecessary procedure that generates a large redundant data.
In the proposed clustering method shown in
Figure 3b, we elect one forwarder (FW) from each cluster to act as both the CH and the GW node. Then, we group all one-hop leading neighbors of FW into one cluster as shown in
Figure 3b. The FW aggregates all BSM packets received from its one-hop leading neighbors. Then, it forwards this aggregated data to the lagging cluster which is a set of one-hop lagging neighbors of that FW. Although the leading FWs receive the aggregated LDM from their lagging FWs, they do not propagate this data to the leading clusters. As all one-hop neighbors of the FW are divided into two different clusters, we name our proposed scheme the half-circle clustering method.
There are two significant benefits of using the half-circle clustering scheme over the full-circle clustering method. Firstly, each FW can support direct communication with neighbor (leading and lagging) FWs. Therefore, each FW can maintain both intra-cluster and inter-cluster links, as shown in
Figure 3b. Secondly, the half-circle clustering method allows FWs to transmit a redundant data much less than the full-circle clustering method. In the half-circle clustering scheme, LDM data is propagated only backward, and therefore data overhead is significantly reduced.
To have a fair comparison, let us assume that in both clustering methods the LDM data of cluster
is propagated only backward upto target distance
as shown
Figure 3. In order to complete this mission, in both clustering schemes, the LDM packet of
should be transmitted through
hops. Then, this target distance is divided into multiple road segments
, each of which represents the length of hop, as shown in
Figure 3. In each
, there are
number of nodes. Let
denotes a time it takes to transmit a mobility information of member vehicle
with a given link layer data rate. Since cluster
contains
nodes, it takes
time to transmit LDM data of single cluster
. As transmission of redundant data degrades the channel efficiency, in following paragraphs, we demonstrate how our clustering method can reduce the time to transmit the redundant data while constructing the multi-hop LDM. We define this time as communication overhead.
In
Figure 3,
,
,
,
,
, and
represent six different road segments each of which contains
,
,
,
,
, and
nodes respectively. In this example, the number of hops
is 5. Let us assume that there is no cluster in front of
. Then, in full-circle clustering method, a total time
it takes to transmit the aggregated LDM packet upto
distance is given as:
The time required to transmit LDM data in each hop is:
which is CH-1’s collection time for
messages from segment
and
messages from segment
.
which indicates the transmission time for CH-1 to forward its LDM to GW-1
which is the sum of transmission time for GW-1 and collection time for
and
which is the transmission time for CH-2 to forward its LDM to GW-2
which is the sum of transmission time for GW-2 and collection time for
and
.
Finally, the total time required to transmit all messages to construct and forward the LDMs to 5 hops in
Figure 3a is
In contrast, for the half-circle clustering method, the transmission time consumed by each hop is
which is FW-1’s collection time for
messages from segment
.
which is the sum of FW-2’s collection time for
messages and LDM message from FW-1.
which is the sum of FW-3’s collection time for
messages and LDM message from FW-2.
which is the sum of FW-4’s collection time for
messages and LDM message from FW-3.
which is the sum of FW-5’s collection time for
messages and LDM message from FW4.
The following equation gives the total transmission time
including all BSM messages and LDM messages for the five hops in
Figure 3b
while the half-circle method transmits only minimum messages needed to finish forwarding LDMs over five hops, the full-circle method transmits redundant messages repeatedly. For example, redundant messages of
,
, and
vehicles are retransmitted a substantial overhead that can be reduced by the half-circle method. In half-circle clustering, the messages from
are not transmitted since they have already been collected by the last forwarder.
To simplify the formula without loss of generality, suppose that the number of nodes in each cluster is
, the average number of nodes per cluster. This is an acceptable assumption, since in a high density scenario, the number of nodes in each cluster can be bounded with the maximum allowable number of nodes,
. By substituting
for
,
, and
for
Figure 3 can be generalized as functions of only the number of hops (h), respectively
Lemma 1: Given a very large h, a reduction of communication overhead, , approaches.
Proof:
The transmission time
and
with a large h can be represented by the series functions of
. These series functions are expressed by Equations (1) and (2).
Equation (1) can be reduced to , while Equation (2) can be reduced to . Therefore, approaches for a large h.
This proves that the proposed half-circle clustering method can reduce the communication overhead by compared with the conventional full-circle clustering method. □
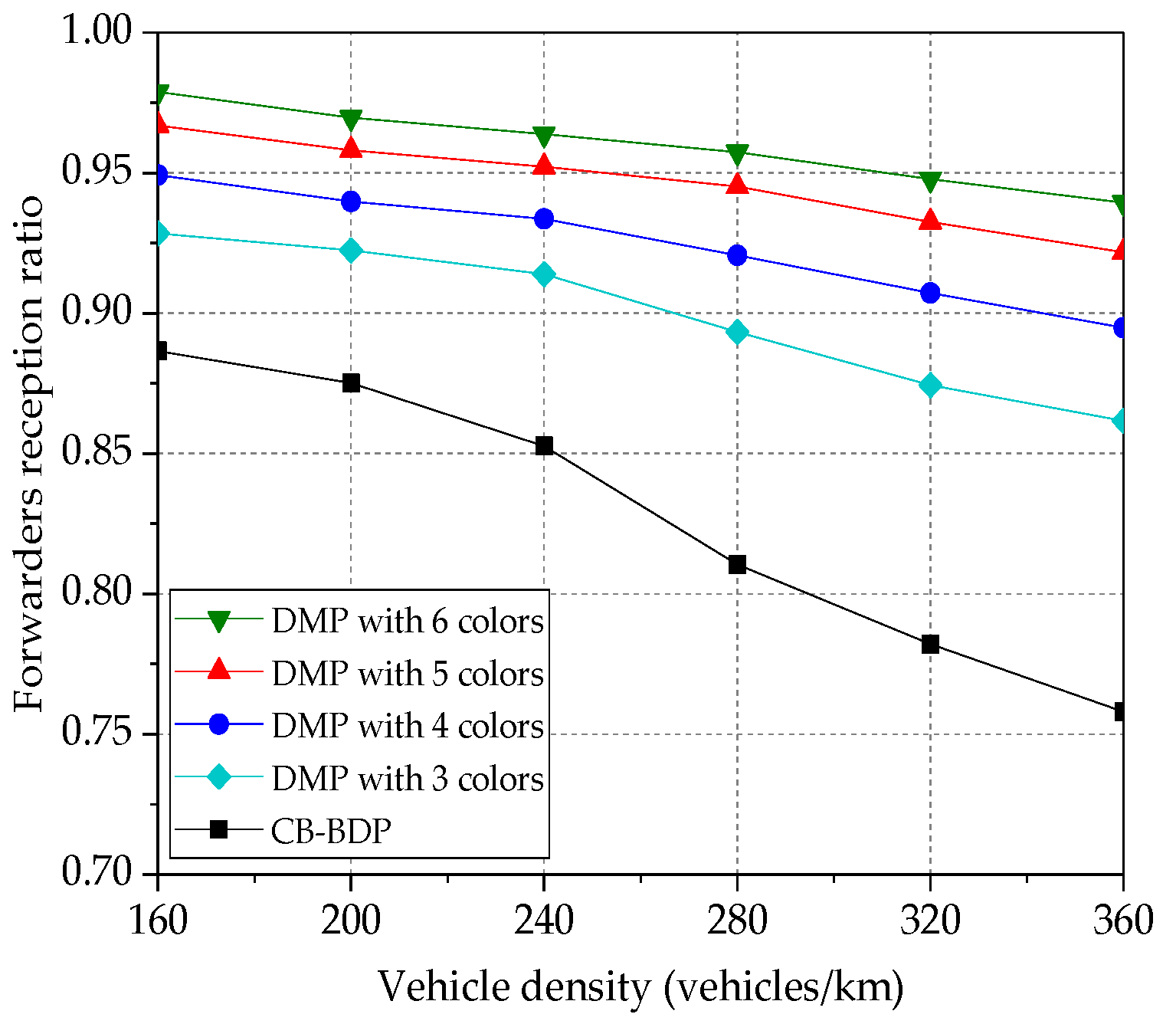
Figure 4 compares the communication overhead of the two methods for initial 10 hops. In the proposed method, clusters utilize different transmit windows to perform communication. Neighboring clusters are assigned with different windows, while clusters in far distance may reuse the same window.
5. Forwarder Election Algorithm
5.1. Problem Definition
To provide efficient and reliable LDM data dissemination, we propose a geographically optimized clustering topology. Within each cluster, we use a star topology for one-hop data aggregation. This topology requires one forwarder to cover the entire cluster population. In addition, to ensure channel resource allocation to all cluster members, we constrain the cluster size by
, the maximum allowable number of nodes as defined in
Section 4.
For a target vehicular network, we construct a set of half-circle clusters (described in
Section 4) by electing a set of forwarders. The forwarders are elected in a way that keeps the forwarders separated by a maximal distance called the ‘inter-forwarder gap’. By maximizing the inter-forwarder gaps, the objective of our forwarder election algorithm is to minimize the number of clusters in the target network, reduce inter-cluster interference, and maximize the channel utilization.
Let be a set of total possible forwarders in the network. We denote as a set of gaps between these forwarders where each represents the distance between and . The number of nodes in cluster is denoted by while indicates the wireless transmission range of V2X devices. For simplicity, we assume that is identical in all clusters. Then, we define the objective and constraints for the forwarder election algorithm as follows:
Objective:
Constraint 1: For each , .
Constraint 2: For all ,
In the remainder of this section, we present the procedure and performance of the forwarder election algorithm.
5.2. Forwarder Election
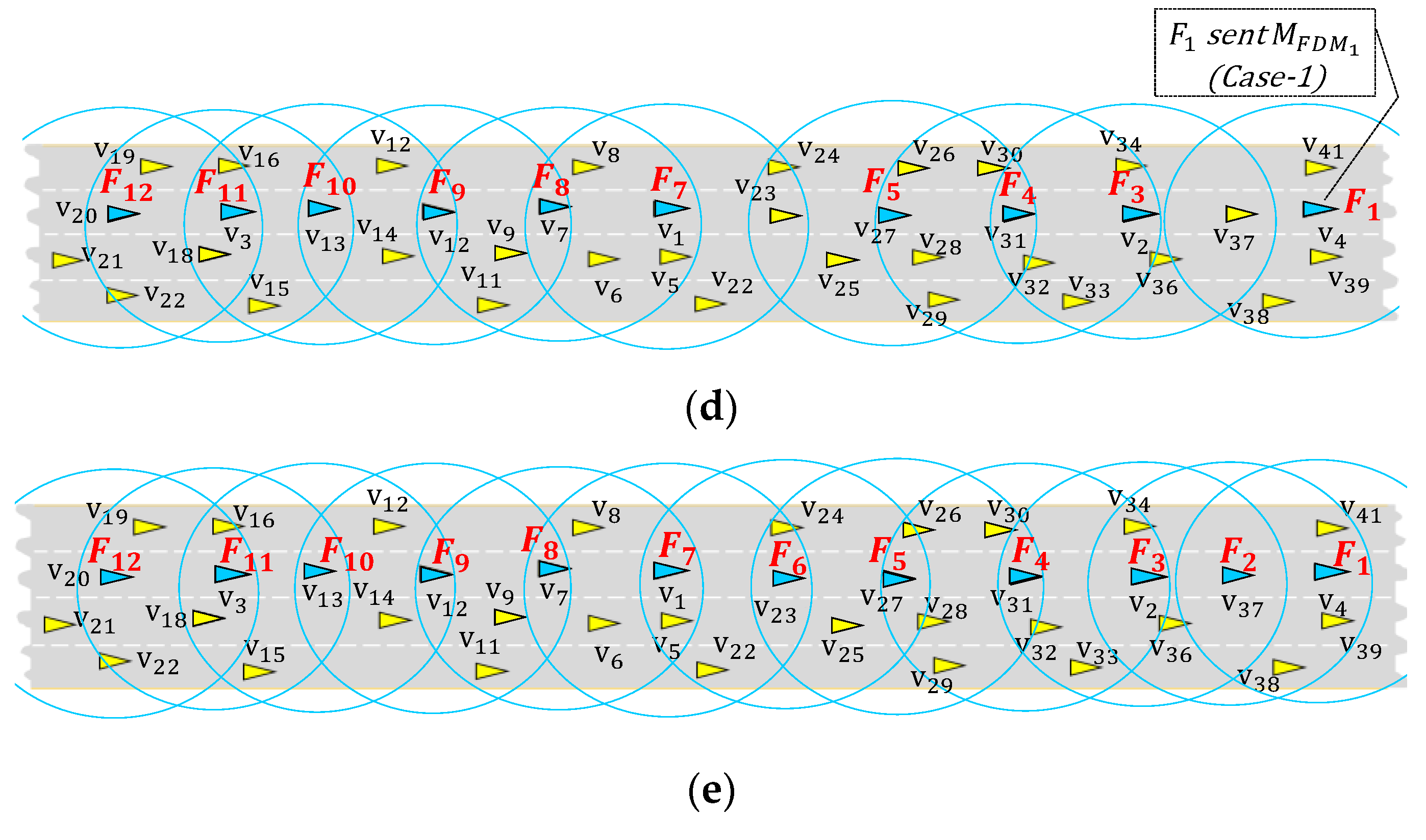
The proposed forwarder election algorithm is described in the following steps using a multilane highway network of
Figure 5. In this network, each vehicle can initiate forwarder election procedure at random time. In this procedure, vehicle can elect itself as forwarder and broadcast a forwarder designation message
. A vehicle broadcasts
message in the following two cases:
Case 1: When the current vehicle is a new vehicle with no leading forwarder, schedules a transmission of in randomly selected slot.
Case 2: When has a leading forwarder, schedules a transmission of using a distance-based back-off timer.
In Algorithm 1, we summarize the basic steps of the distributed forwarder election procedure. While running Algorithm 1 in each vehicle, when it elects itself as a forwarder, it broadcasts
, under the Case1 and Case2 conditions.
| Algorithm 1Distributed forwarder election algorithm |
Input: is host vehicle, is forwarder designation message, is distance-based back-off timer, is forwarder re-election timer
Output: leading forwarder , lagging forwarder
1 loop
2 //Case1:
3 if is new vehicle (with no in the neighbor)
4 if is not scheduled for then
5 Schedule in random slot from
6 else if time reaches selected slot then
7 Elect itself as forwarder and broadcast
8 end if
9 //Case2:
10 else if receives from or then
11 Record ID of or //forwarder that sent
12 Dismiss its own , if it was scheduled
13 if is undefined then
14 Schedule with back off timer of using Equation (3)
15 end if
16 end if
17 Decrement the back off timer
18 if timer expires then// is defined and is unknown
19 elects itself and sends
20 end if
21 end loop |
Case 1: (Algorithm 1 line 2–8) Using a contention window method like CSMA protocol, each vehicle randomly selects a time slot to transmit its message. We allocate a short contention time window for transmission. We partition the contention window into slots of time length . Then, each vehicle selects a random slot from [. Then, schedules its message to be sent in the selected slot.
If
selected earlier slot than other neighbors,
transmits
in its slot and then becomes forwarder
. On the other hand, if
selects later slot, other vehicle would transmit its
and become a forwarder. If
receives
from other vehicle, it dismisses its own transmission scheduled at randomly selected slot. For example,
Figure 5a,b,d show examples of initial forwarders elected in this way (
,
,
, and
select themselves as
,
,
, and
that selected the earliest time slots).
Lines 3–8 of Algorithm 1 describe Case-1, where a new vehicle which has no neighbor forwarder selects a random back off slot. Then, schedules a transmission of at selected slot in line 5 and decrements its back off timer.
Case 2: (Algorithm 1 line 9–20) The elected forwarders are denoted either by
or
. Here, the order of forwarders is opposite to traveling direction of vehicles. In other words,
denotes the previous forwarder for the leading cluster from the perspective of the current forwarder, while
is the next forwarder for the lagging cluster. For example, in
Figure 5b,
is
of
, while
is
of
. In Case2, the algorithm elects the lagging forwarder
only with respect to its previous forwarder
(backward of the vehicle travel direction).
The
message received from
initiates a forwarder election procedure which elects a
among the neighbors that are one-hop lagging from
. Our proposed algorithm uses a technique called a distance-based back-off procedure to elect
. Each lagging neighbor represented as a host vehicle
computes its distance-based back-off timer
using Equation (3).
Here,
denotes the location of host vehicle at
time. Similarly,
is the location of
(the forwarder of the previous cluster of
) at time
. The algorithm elects as
the neighbor
that has the shortest
or the farthest inter-vehicle distance from
. The
of
constantly decrements until it expires. Once
of
expires,
elects itself as a forwarder, and broadcasts
to notify all one-hop neighbors. Then, all receivers located in front of
’s wireless range become the member of current cluster, where
is self-designated forwarder. For example, in
Figure 5a,
from
(current
) initiates distance-based back-off procedures in the lagging neighbors
,
, and
. From Equation (3),
, since the distance from
is the farthest from
, and closest from
. Since
decrements to zero before
and
,
declares itself as the next forwarder
(an
of the current
). This procedure is repeated by
acting as a next
to elect the next
.
In this way, all forwarders are elected, and all vehicles are connected through the elected forwarders as shown in
Figure 5e. The current positions of the forwarders, however, may not be optimal, since initial forwarders are randomly elected, and vehicles continuously change their locations. To maximize the gaps between these forwarders, Algorithm 1 iteratively runs the forwarder re-election operation to find better forwarder positions. The forwarder re-election is an iterative procedure (executed every forwarder re-election cycle), which strives to discover the optimum forwarders in the continuously changing vehicular network. The re-election procedure is conducted by Case 2 in Algorithm 1 by repeatedly sending
with random back off timer to initiate election of optimal lagging forwarder. The forwarder re-election procedure is conducted from front to backward.
Each forwarder selects a random back off slot from and transmits message to elect a new . Each lagging vehicle that receive verifies following two conditions:
- (a)
, where is a threshold distance which triggers distance-based back off procedure for .
- (b)
, where is the number of nodes located between and .
Condition (a) avoid too frequent changes of forwarders, while condition (b) ensures that the cluster for does not exceed , the maximum number of vehicles.
If satisfies above two conditions, then it can contend to be by scheduling its at the back off slot based on Equation (3). The that has the shortest back-off timer is re-elected as a new , and sends to announce itself as a new lagging forwarder.
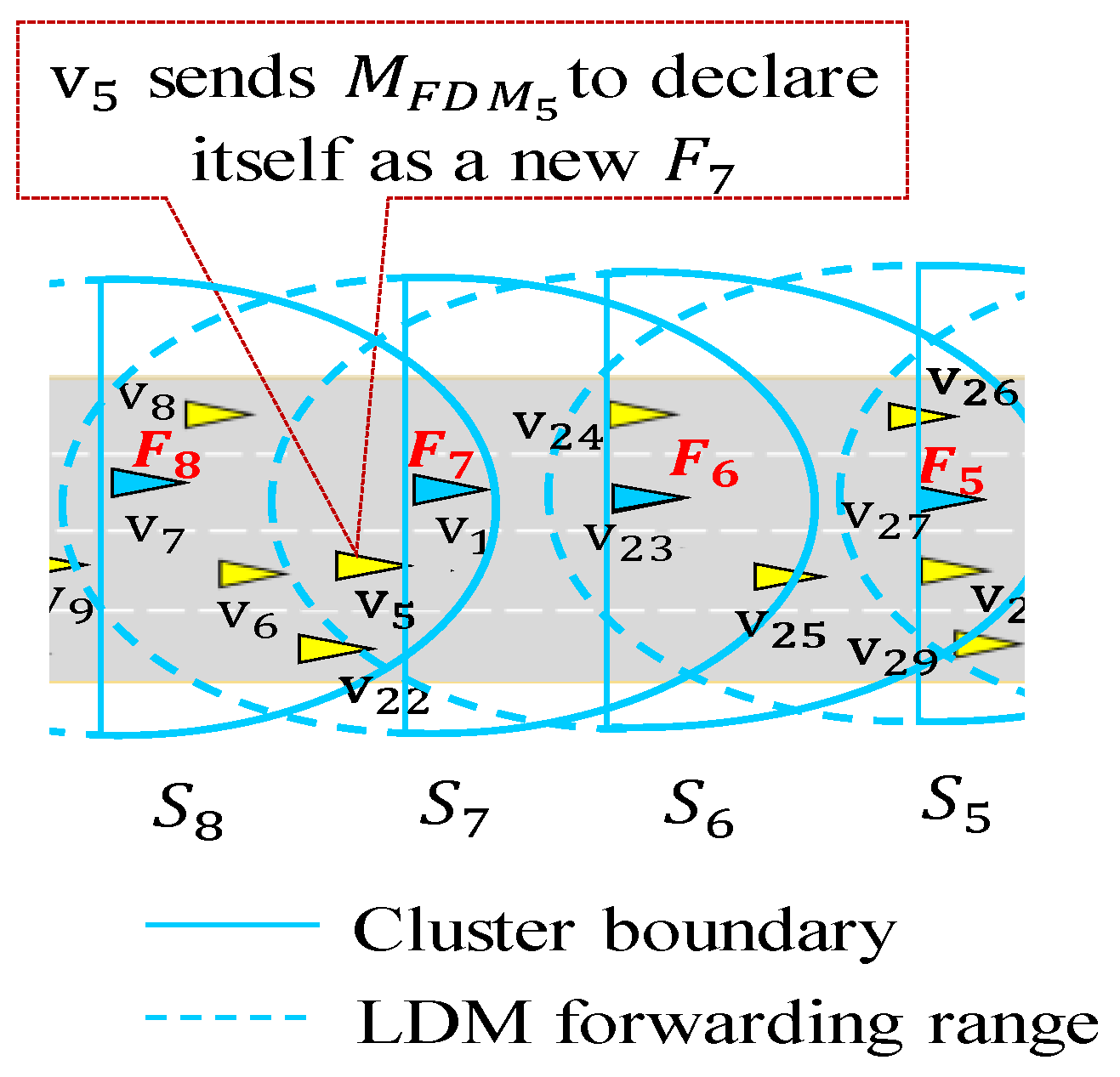
Figure 6 illustrates an example of re-election,
sends
to its lagging vehicles and initiates the re-election procedure. Since
is the farthest node from
,
sends
with the shortest timer
, before other vehicles announce themselves as a new
. Upon receiving
from
,
,
, and
cancel their distance-based back-off procedure.
changes its status from forwarder to a member vehicle. This procedure is iteratively done by each forwarder to maximize the inter-forwarder gap.
5.3. Analysis of Time Complexity
In this subsection, we analyze the upper bound time complexity of forwarder re-election procedure. For simplicity, we assume that all clusters (vehicles) are stationary within time interval
.
Figure 7 shows
forwarders indexed in ascending order from the right to the left. For the sake of simplicity, let us assume that it takes constant
time to announce a new forwarder in every re-election operation. Then, let is define a set of forwarders as
where
and
is separated by gap
. A set of gaps between each pair of the forwarders is denoted by
as shown in
Figure 7. In the worst case scenario, if any
starts re-election operation at random
, it causes
recursive re-election operations where each inter-forwarder gap
changes to
(maximum distance). Then, the time required to run
recursive re-election operations can be expressed by a time function
(see that in
Figure 8a).
Let
be the next forwarder that launches re-election at
. Then,
triggers
recursive re-election operations as shown in
Figure 8b. Since
leads
,
forwarders run re-election operation again. Then, the time it takes for
forwarders to complete re-election procedure becomes
Considering this recursive relation, we define the following lemma.
Lemma 2:
Letbe a set of inter-forwarder gaps for n forwarders. Then, each converges to the maximum gap after iterative forwarder re-election procedures conducted within the time bound.
Proof:
As described above, in the worst case, the forwarder re-election procedure repeatedly conducted by each forwarder from
to
in
iterations, which can be written as:
Note that the re-election time for
is zero, since
is the last forwarder. Then, the total time it takes to maximize all
inter-forwarder gaps in the worst case is the sum of all recursive re-election time
,
, …,
. We denote a total time as
.
By reversing the ordering, Equation (4) can be expressed by Equation (5).
Then, adding Equation (4) with Equation (5) produces Equation (6).
Then, Equation (6) is represented by
which leads to Equation (7).
The Equation (7) proves that the proposed algorithm takes time to maximize each of . □
The overall processing time of the proposed algorithm is dominated by the recursive re-election time, since the initial election time is given by , which is negligible. This proves that the proposed forwarder election algorithm can obtain optimal result in complexity of even in the worst case.
6. Transmit Window Allocation
This section describes the transmit window allocation algorithm based on coloring to maximize the channel utilization.
Figure 9 illustrates an example of cluster coloring on a road segment with four clusters, each of which selects one color out of predefined set
. We partition the transmission interval
into
of short transmit windows, which is represented as
. Then, each transmit window
corresponds to predefined color
. If forwarder
of cluster
selects a window
, then all member vehicles in
transmit their BSM packet and
forwards the LDM message within
window. For example,
Figure 9 illustrates a case of using three colors (red, green, blue), each of which indicates unique transmit window (
,
, and
). All vehicles in each cluster transmit messages only within allocated transmit window, while they receive messages all time. However, one transmit window can be reused by multiple clusters if the distance between these clusters is large enough, so their vehicles do not interfere. In
Figure 9, vehicles in two different clusters
and
are colored red. This means the members of these clusters access the channel within
of
. The forwarder
then receives all the packets sent by the member vehicles of
as indicated by the solid half circle around
. Then, it aggregates these packets to create the LDM data of
. Then,
forwards the LDM data to the cluster behind
. In the same way,
also creates the LDM data of
and aggregates it with the LDM data received from
. Then,
sends its aggregated LDM data to cluster
. Following the same procedure,
also builds the LDM data of
and adds it to the aggregated data received from
. Next,
transmits its aggregated LDM data to cluster
. In this way, the LDM data of reaches vehicles in cluster
through a multihop forwarding procedure indicated with dashed half circle of
Figure 9. When
transmits its LDM data to
,
also receives the LDM data of
since it is sent as a broadcast packet. Then,
verifies whether its LDM data is successfully received and aggregated in the LDM packet of
.
To color each cluster, we allocate a predefined contention period. This contention period is divided into
slots of time length
. Each forwarder select a random slot out of [
] to declare its selected color. Algorithm 2 describes the basic steps of distributed color selection procedure. Algorithm 2 starts by checking whether the host vehicle
is a forwarder or not (line 2). If
is a forwarder, then
verifies whether it has selected its own color (line 3). If color is undefined,
picks a random slot in which it declares its selected color (line 4). Meanwhile, in line 11–13, if
receives color from a neighbor forwarder
, then
records this color in a local color table denoted as
(later this table is shared with neighboring clusters). In
Figure 9, let us assume that
selects an earlier slot than
. Then,
receives color information from
before
picks its color, and,
records the color of
in
. Then, in the later slot,
transmits its selected color with its updated
. When
is received by
,
verifies whether its coloring details are recorded in
. If it is not recorded, then
concludes that there has happened when it transmitted its coloring details. Therefore,
selects another random slot to re-announce its selected color.
| Algorithm 2 Distributed color selection algorithm |
| Input: is neighbor forwarder, is a table that contains color information received from ’s |
| Output: color (transmit window) |
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19 | Loop
if is forwarder then//for forwarders
if Color is undefined then
if Color designation slot is undefined then
Select a random slot from
else if time reaches selected slot then
Select minimum cost color using Equation (8)//pick window
Broadcast coloring information//declare Tx Window
end if
end if
if Color designation message is received from then
Insert ’s coloring details in
end if
else//for member vehicles
if Color is received from forwarder then
Schedule BSM transmission within transmit window corresponds to received color
end if
end if
end loop |
In line 6 of Algorithm 2, once time reaches the selected slot of
,
runs line 7 to calculate the cost for each color and then select the one with minimum cost. Our cost calculation function relies on Friis free space propagation model [
26]. This model is defined as
, where a power of received signal
is inversely proportional to the square of
, the distance between transmitter and receiver.
,
, and
are constants representing transmission power, unitless coefficient, and reference distance, respectively [
20]. Therefore, we disregard these constant parameters while defining the cost function in Equation (8). We use
Cost(
Cj) to denote aggregated cost of color
.
Here, is the function which calculates a distance between (considering as a forwarder of current cluster) and neighbor .
The cost of free color (not occupied by any
) is zero, since the distance for free color represents infinite value in Equation (8). Once
selects a minimum cost color, then
broadcasts its color (and its color table) as shown in line 8 of Algorithm 2. In
Figure 9, let us assume that
is the next forwarder who selects color after
. Suppose that
received color information: red color from
and green color from
. Then,
picks blue color from (red, green, blue), since blue is unoccupied color and thus gives zero cost. Suppose that
is the next to select the color. Then,
selects green color since red and blue colors have higher cost due to the shorter distance of their
.
In case when is a member vehicle, it polls the color information of its forwarder. Once receives color from its forwarder, then schedules its BSM transmission within the transmit window corresponding to the forwarder’s color.
The proposed cluster coloring scheme can also be applied to grid structured crowded city roads with many intersections. To reduce the interference in the intersection area, we can extend , the beaconing period, to accommodate more colors. Then, the additional colors can be assigned to the clusters representing the roads crossing with the main road at the intersection. This way, we can minimize the potential inter-cluster interference in the intersection area.
The increased number of colors may degrade the channel reuse efficiency. In other words, if we increase the number of colors, a distance between the interfering clusters becomes larger. On the other hand, if we use the minimum number of colors, more vehicles can transmit their BSM packet in the same transmit window. Therefore, we should use the minimum colors to maintain better channel reuse efficiency.
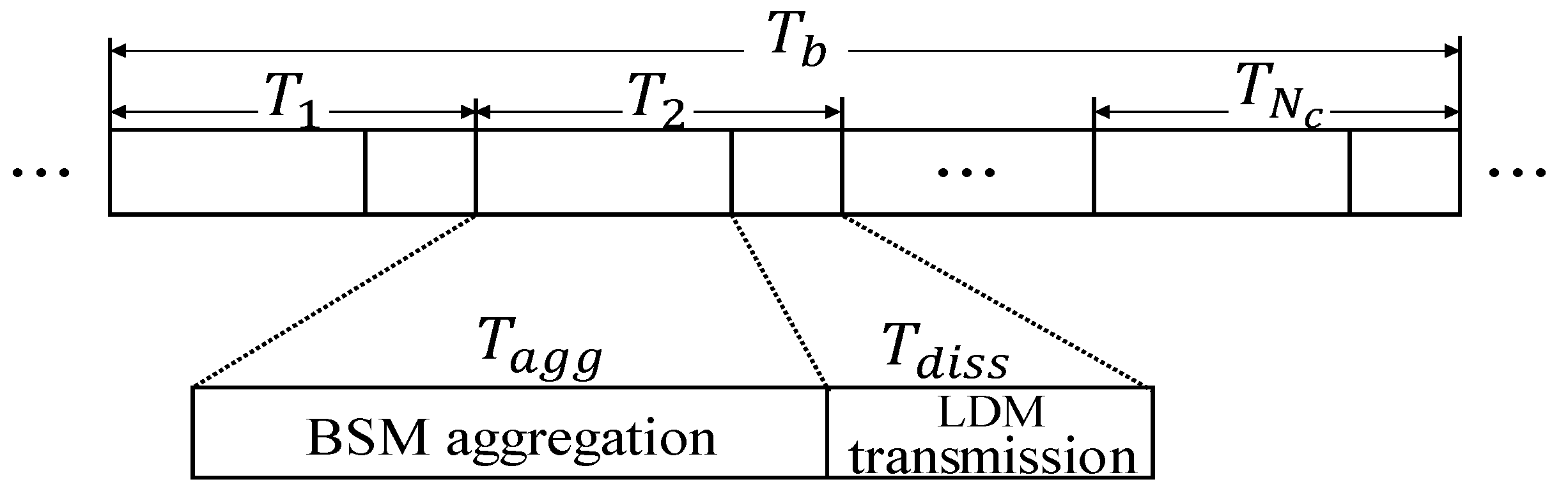
Requirement of Transmit Window
Each transmit window is divided into two sub-windows: (1) aggregation sub-window
and (2) dissemination sub-window
as shown in
Figure 10. The aggregation sub-window is defined as
Here, represents a time it takes to transmit single BSM packet while is a maximum time required to access the channel using the standard carrier sense multiple access (CSMA) scheme. By multiplying (a maximum number of members in a cluster), Equation (9) represents the maximum required aggregation sub-window.
In Equation (10), we define dissemination sub-window in which the forwarder transmits its aggregated LDM packet to the next cluster.
Here,
is a time required to send mobility information of each
, while
is the number of hops indicating that the LDM of
clusters is accumulated. By multiplying
, Equation (10) represents the upper limit of the LDM size. Equation (11) gives the maximum length of transmit window
.
Since
denotes the number of colors (transmit windows), we can identify
for each cluster using Equation (12).
In Equation (12), we can see the parameters and are inversely proportional to . We can observe the property that to increase , should be reduced. In this paper, we use a fixed number of colors to disseminate the LDM data up to a fixed number of hops for simplicity.