Abstract
Semantic communication based on deep learning technology extracts the meaning of the transmitted source to achieve spectrum resource savings and enhance anti-interference capabilities. The black-box nature of deep learning models increases the difficulty for eavesdroppers in intercepting information, thereby significantly improving transmission security under normal circumstances. However, eavesdroppers may utilize model theft techniques to acquire models that have similar functionality and performance to the victim’s model. Moreover, even if all users are legitimate, the private information of a specific legitimate user should not be accessible to other users, and this issue also requires attention. As the lowest layer of wireless communication, the physical layer has been proven to enhance the security performance of communication systems by leveraging the randomness of physical channels. Unlike traditional communication, which transmits bit streams, semantic communication transmits semantic streams. Therefore, this paper converts semantic streams into bit streams to analyze the security performance of semantic communication using traditional communication metrics. Specifically, this paper assumes that the performance of the eavesdropper’s stolen model is consistent with that of the original model (although this assumption is impossible) and conducts a derivation analysis of the Secrecy Outage Probability (SOP).
1. Introduction
With the advancement of communication technology, the transmission rate and capacity of communication systems have now approached Shannon’s limit. Particularly, the rapid development of Internet of Things (IoT) technologies has led to emerging applications such as autonomous driving, telemedicine, and intelligent transportation, which place higher demands on low latency and high reliability. Semantic communication, which utilizes deep learning techniques to compress information sources and improve the transmission efficiency of wireless communication, is considered one of the key technologies for the future of communication [1,2,3,4].
Currently, semantic communication has been widely applied to the transmission of text, speech, and video signals. For example, Xie et al. [5] proposed a communication system that combines semantics with channel coding, called DeepSC. This system measures performance using semantic similarity, and experimental results show that DeepSC outperforms traditional bit-based transmission systems under conditions of low signal-to-noise ratio and limited bandwidth. Additionally, Yan et al. [6] introduced semantic rate as a performance metric and studied the resource allocation problem in text semantic communication. To mathematically describe the performance of semantic communication, Mu et al. [7] proposed a semantic similarity function based on a generalized logical function and derived the optimal resource allocation scheme. Furthermore, Lil et al. [8] optimized the joint problem of delay and efficiency by introducing secrecy rate, while Mu et al. [9] considered semantic communication as an artificial auxiliary noise, thereby enhancing the security of traditional communication systems.
As deep learning technology has improved the efficiency of semantic communication systems, the risk of model theft has also increased. Therefore, ensuring the security of semantic communication data has become an important research focus. Existing studies primarily focus on enhancing system robustness while incorporating traditional security technologies to strengthen data transmission protection. For example, refs. [10,11,12] ensure semantic security through methods such as semantic symbol encryption and secure coding. However, these traditional solutions often introduce additional system overhead, limiting their widespread application.
In contrast, the physical layer security scheme proposed by Chorti et al. [13] has become a competitive security solution due to its low complexity and low latency. Additionally, Zheng et al. [14] and Saleem et al. [15] developed adversarial interference and RIS interaction vectors within the Reconfigurable Intelligent Surface (RIS) framework, significantly improving signal detection accuracy. Compared to traditional methods, these approaches not only enhance system security but also effectively reduce computational overhead.
Furthermore, Li et al. [16] proposed a Deep Semantic Communication (DeepSSC) system based on deep neural networks, while Wang et al. [17] introduced a noise interference-based hybrid deep reinforcement learning (NdeHDRL) resource allocation scheme. These methods integrate physical layer security metrics into model training, improving the overall security of semantic communication. Additionally, Li et al. [16] suggest that moderately sacrificing semantic similarity can enhance physical layer security.
Although traditional security methods, such as encryption, can enhance system security, they introduce additional overhead, limiting their application in efficient semantic communication. Physical layer security schemes, by optimizing model training, can significantly reduce overhead and improve transmission efficiency, which has garnered increasing attention. Current research primarily focuses on joint training of physical layer models with coding models to enhance system robustness. However, existing solutions simply incorporate physical layer security metrics into model training without analyzing the relationship between the physical channel and semantic similarity. As a result, there is a lack of a comprehensive evaluation metric that can effectively balance security and system performance.
This paper provides a comprehensive analysis of the physical layer security in semantic communication systems and introduces new metrics to measure the system’s effectiveness and security. The main contributions of this paper are as follows:
- Adopting the Conversion from Semantic Flow to Bitstream: This paper adopts the method of converting semantic flow to bitstream in order to calculate the Secrecy Outage Probability (SOP) of semantic communication systems and perform a mathematical analysis of their security.
- Deriving a New Evaluation Metric through Security Analysis: Through an in-depth analysis of the system’s security, this paper proposes the semantic reliability index (SRI) as a metric for evaluating the system’s security and effectiveness.
2. System Model and Problem Formulation
In Figure 1, we analyze a secure communication system under different fading scenarios. The system consists of three main components: the transmitter (BS), the legitimate user (bu), and multiple eavesdroppers (eve). We assume that both the legitimate user and the eavesdroppers can perform semantic decoding with the same decoding performance. In the system, the link distance between the base station and the legitimate user is denoted as , while the link distance between the base station and the i-th eavesdropper is denoted as (where ). Additionally, represents the channel model from the base station to the legitimate user, and (where ) denotes the channel model between the base station and each of the eavesdroppers.
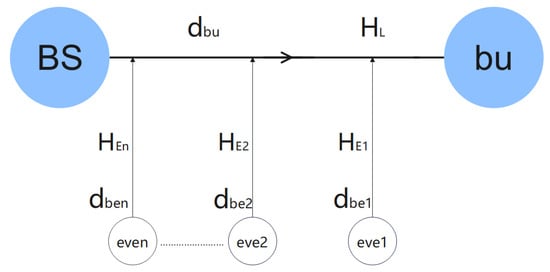
Figure 1.
System model formatting.
For the analysis, we assume that all channel state information (CSI) is known and that the channels follow Rayleigh fading and large-scale fading models. In this system, represents the lower bound for secure transmission. We define the security outage probability (secrecy outage probability, SOP) as the probability that the actual transmission rate is less than , which can be expressed as
2.1. Semantic Rate Converted to Bit Rate
According to [6], the semantic rate can be used to quantify the communication performance of semantic communication systems. It is assumed that, after semantic encoding, each sentence contains an average of L words and has I semantic information (measured in semantic units or suts). Additionally, each word generates an average of semantic symbols through DeepSC. Therefore, the achievable semantic rate for the user and the eavesdropper can be expressed as
and
where represents the semantic similarity, which quantifies the similarity between the original text and the reconstructed text in semantic communication. This value depends on the semantic rate K and the SNR and can only be obtained through experimentation using the SC tool. A closed-form expression for is provided in [6] for theoretical analysis. The function is given
Here, , , , and . To convert the semantic flow of semantic communication into traditional bitstreams, the following is obtained from [5]
and
where = 40 (bits/word) represents the average number of bits required for transmitting one word if ASCII code is used for bit-oriented source-channel encoder/decoder, and the semantic similarity achieved by bit transmission is assumed to be 1 [5]. The confidentiality rate for legitimate users is given by the following formula:
2.2. Derivation of the SOP Expression
2.2.1. Rayleigh Fading
The analysis process of the SOP expression for the single eavesdropper and multiple eavesdroppers user is as follows: For the Rayleigh fading channel with a single eavesdropper, let represent the information symbol of the semantic channel encoder, with a transmission power of p and as the normalized additive Gaussian white noise. Therefore, under fading conditions, the semantic signals of the legitimate user and the eavesdropping user can be expressed as
and
The SNR of the legitimate channel and the eavesdropping channel can be expressed as
and
When both legitimate users and eavesdropping users experience Rayleigh fading in their channels, the parameters , , , and in the semantic similarity will be fixed values. Therefore, the calculation of the outage probability is as follows:
where and , and represent the channel state parameters for legitimate users and eavesdropping users, respectively, which follow an exponential distribution.
The Rayleigh fading channel with multiple eavesdroppers is shown in Figure 1. Since all eavesdropping channels are independent of each other, the semantic signals of the legitimate user and the eavesdropping user can be expressed as
and
where represents the i-th eavesdropping channel. The SNR of the legitimate channel and the eavesdropping channel can be expressed as
and
By combining Equations (1)–(4), (8) and (9), the expression for the SOP in the case of multiple eavesdroppers can be derived as
where represents the joint probability distribution of the eavesdroppers under multiple eavesdropping and . . and represent the channel state parameters for legitimate users and eavesdropping users, respectively, which follow an exponential distribution.
2.2.2. Large-Scale Fading
For the large-scale fading channel with a single eavesdropper, the transmission power is p, and n represents the normalized additive Gaussian white noise. c is the path loss constant, and denotes the path loss exponent. represents the corresponding link distances in meters for legitimate users and eavesdropping users, respectively, and the channel gain is denoted as . Therefore, the semantic signals for legitimate users and eavesdropping users can be expressed as
and
The SNR of the legitimate channel and the eavesdropping channel can be expressed as
and
From the joint Formulas (3)–(6), the security probability under large-scale fading can be obtained as
where and , and represent the channel state parameters for legitimate users and eavesdropping users, respectively, which follow an exponential distribution.
3. Experimental Results and Analysis
3.1. Rayleigh Fading
To calculate the outage probability, we perform numerical simulations using MATLAB (R2024b). In reference [9], is set, meaning that each word is represented by 5 semantic symbols, typically determined through the DeepSC model. The parameters , , , and are obtained by running the DeepSC tool to obtain the semantic similarity and SNR curves, which are then fitted by the generalitzed logistic function. This method is used in [6]. In order to simulate the worst-case scenario, we set , and the transmission power p starts at 10 W and gradually increases, while the noise power n remains constant at 10 W. The simulation results are consistent with the numerical method, verifying the correctness of the formula. The outage probability decreases initially and then increases as the power changes. The results are shown in Figure 2.
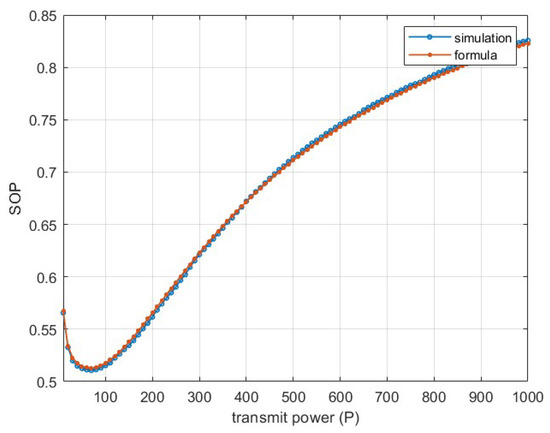
Figure 2.
The legitimate user and the eavesdropping user have the same .
The minimum outage probability occurs at approximately , indicating the best system secrecy efficiency. At this point, the SNR converted to dB is . It can be observed that under low-SNR conditions, the secrecy outage probability (SOP) of the semantic communication system gradually decreases. This is because when the SNR is low, the SNR has a significant impact on the system; thus, appropriately increasing the SNR can enhance the secrecy performance. However, as the SNR continues to increase, the influence of the semantic communication model also gradually increases. Eventually, it may surpass the impact of the physical channel on the security performance, leading to a downward trend in security performance at this point. Figure 3 illustrates the variation of SOP at different values of . It can be seen that SOP generally shows a downward trend as increases. When is small, increasing is more effective in reducing SOP compared to when is larger. This indicates that while increasing can enhance the security of the system, this method also has its limitations. In other words, it is not possible to infinitely enhance the security of the semantic communication system by compressing semantic information.
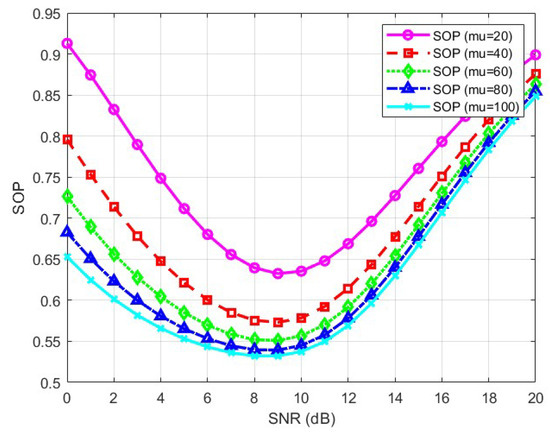
Figure 3.
SOP for different values.
Considering that legitimate users can always choose the best channel for transmission, we analyzed the changes in the secrecy outage probability (SOP) under different values of , as shown in Figure 4. It can be concluded that if the legitimate channel improves, the security performance increases. At the same time, as the legitimate channel improves, the optimal transmission power required to achieve the best security performance will also decrease. By running the DeepSC tool, we can obtain the relationship between semantic similarity and SNR under a fixed K condition, while also analyzing the changes in semantic similarity and SOP when , as shown in Figure 5. It can be observed that semantic similarity cannot reach its optimal point simultaneously with SOP. Therefore, we employ the semantic reliability index to evaluate the overall performance of the semantic communication system, described as follows:
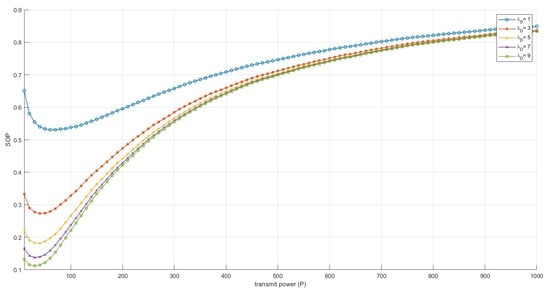
Figure 4.
SOP under different transmit power levels and multipliers.
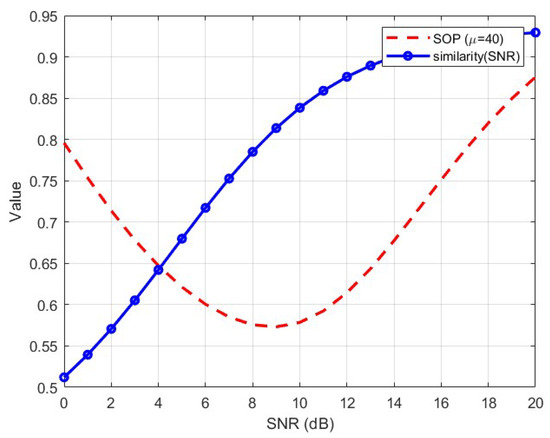
Figure 5.
Semantic similarity and SOP.
Here, the value of SRI ranges from (0, 1). The closer this value is to 1, the closer the system’s semantic similarity and security probability are to 1. Thus, the system performs better in terms of effectiveness and reliability. Conversely, if the value is close to 0, it indicates that the system’s performance in either effectiveness or reliability is poor.
Figure 6 shows the variation in SRI as a function of . Overall, compressing semantic information improves the SRI index; however, under the assumed conditions, the SRI is relatively low. This is because, when the SNR is low, the system’s effectiveness is not well guaranteed. As the SNR increases, semantic similarity gradually rises, but at that point, security performance significantly decreases.
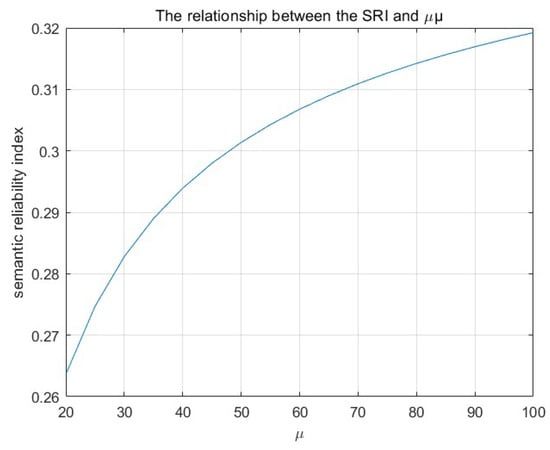
Figure 6.
The relationship between the SRI and .
3.2. Large-Scale Fading
To perform numerical integration and simulation using MATLAB, we set the following parameters: the path loss constant denotes the reference path loss at 1 m, the path loss exponent , and . The values of m, . The value of increases from 10 m to 20 m, as shown in Figure 7. The results indicate that:
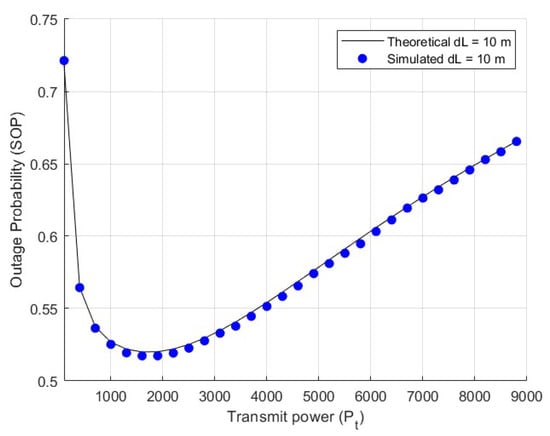
Figure 7.
SOP for large-scale fading at different values of .
From Equation (10), it can be seen that the SOP is related to the fading parameters and of the Rayleigh fading as well as the link distance. When validating the relationship between SOP and link distance, we set to 10 m, and increases from 10 m to 20 m. We increase the Rayleigh fading parameter for legitimate users from 2 to 10 to verify the relationship between SOP and the Rayleigh fading parameter. All the results are shown in Figure 8 and Figure 9. The SOP initially decreases, and then increases. The closer the link distance for legitimate users, the better the confidentiality performance. The better the channel conditions for legitimate users, the lower the SOP value. This indicates that the system achieves better security performance; however, as shown in Figure 9, there is still an upper limit to the effect of channel conditions on SOP. this upper limit is more easily reached at higher transmission power levels. (1) our derivation of the formula is correct; (2) the SOP still decreases and then increases; (3) when the transmission power is low, increasing the transmission power significantly enhances the security performance of the semantic system.
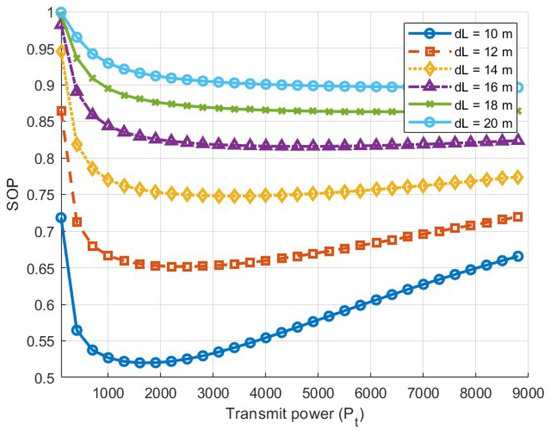
Figure 8.
Variation in SOP with respect to .
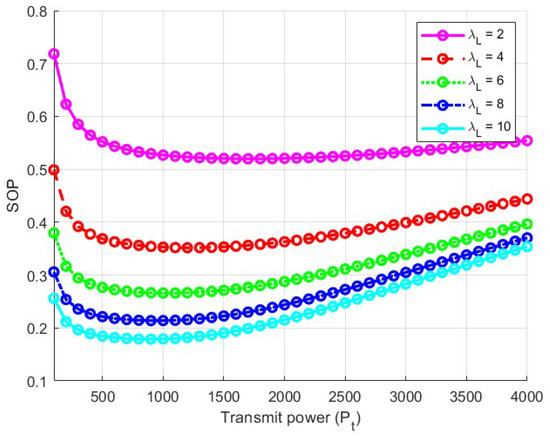
Figure 9.
Variation in SOP with respect to .
3.3. Multiple Eavesdropping Rayleigh Fading
To perform numerical integration and simulation using MATLAB, we set the following parameters: the legitimate users follow an exponential distribution with a rate parameter of 5, while the eavesdropping users follow an exponential distribution with a rate parameter of 1. Additionally, the number of eavesdropping users is set to 5.
The simulation results are shown in Figure 10, which indicates that the derived formula is correct. When the communication link is being eavesdropped on by multiple users, the transmission power should not be too high. Additionally, SOP increases as the number of eavesdropping users rises. As mentioned earlier, when the transmission power is low, legitimate users are unable to obtain highly accurate information. Therefore, it is necessary to design the transmission power reasonably to ensure that both message accuracy and security are maintained at a high level.
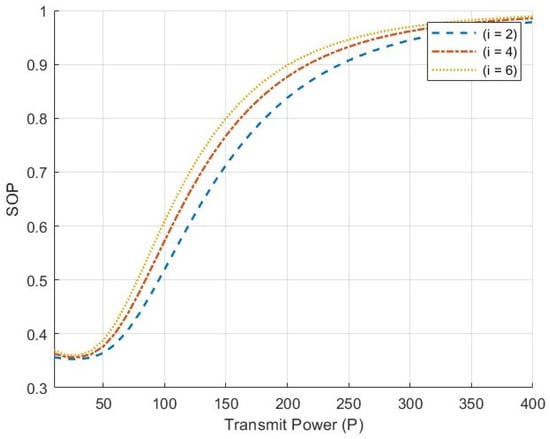
Figure 10.
SOP of the system with multiple eavesdropper users.
4. Discussion and Conclusions
4.1. Discussion
In this study, we investigate the security performance of semantic communication systems when the semantic model is compromised or sensitive information is transmitted. The focus of the research is to analyze the impact of factors such as transmission power, channel conditions, the number of eavesdroppers, and link distances on system security. Through a comprehensive analysis of these factors, we derive several valuable conclusions: when the transmission power is low, the security outage probability (SOP) shows a decreasing trend, while at higher transmission power, the SOP increases. Additionally, improved channel conditions for legitimate users help enhance system security, whereas an increase in the number of eavesdroppers leads to a decline in system confidentiality. Notably, when the link distance between the legitimate user and the base station is short, and the link distance between the eavesdropper and the base station is long, the system exhibits better security performance.
It is worth mentioning that in this study, we used two main metrics—semantic similarity and security outage probability—to evaluate the effectiveness and reliability of the semantic system. The results show that these two metrics cannot achieve optimal performance simultaneously, especially under high transmission power, where the impact of the semantic model on system security becomes more significant. This indicates that there is a trade-off between confidentiality and system performance in semantic communication systems. This phenomenon was also observed in [16]. The researchers attempted to introduce physical-layer security metrics into model training, dividing the training process into two phases: the first phase focuses on semantic recovery for legitimate users, and the second phase aims to minimize semantic information leakage to eavesdroppers. The study successfully improved the security of the training model under high-signal-to-noise ratio (SNR) conditions but also encountered a performance degradation. However, ref. [16] did not provide a mathematical explanation for this phenomenon, while our study offers a reasonable explanation: under high-SNR conditions, the physical channel conditions are particularly advantageous for eavesdroppers. Once the eavesdropper acquires the model, they can approach the legitimate user’s decoding performance, significantly weakening the system’s security. Therefore, to restore system security, some decoding performance must be sacrificed, which leads to a decline in system effectiveness.
4.2. Conclusions
This study provides an in-depth analysis of the security performance of semantic communication systems when the semantic model is stolen or sensitive information is transmitted. We derive and solve the security communication outage probability (SOP) under Rayleigh fading and large-scale fading conditions, and validate the correctness of the formulas through numerical methods. Our research shows that factors such as transmission power, channel conditions, the number of eavesdroppers, and link distances have a significant impact on system security. At the same time, we find that semantic similarity and SOP cannot both reach their optimal values simultaneously, especially under high-SNR conditions. Improving the system’s security performance leads to a loss of decoding capability for the legitimate user. Therefore, the focus of our future research will be on how to better balance semantic similarity and security performance, in order to enhance the effectiveness and reliability of semantic communication systems in a synchronized manner.
Author Contributions
Conceptualization and formal analysis, F.P. and X.W.; methodology, X.W.; software, F.P.; validation, F.P.; investigation, F.P.; writing—original draft preparation, F.P.; writing—review and editing, F.P. and X.W. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
No new data were created or analyzed in this study.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Atzori, L.; Iera, A.; Morabito, G. The internet of things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar]
- Gündüz, D.; Qin, Z.; Aguerri, I.E.; Dhillon, H.S.; Yang, Z.; Yener, A.; Wong, K.K.; Chae, C.B. Beyond transmitting bits: Context, semantics, and task-oriented communications. IEEE J. Sel. Areas Commun. 2022, 41, 5–41. [Google Scholar]
- Qin, Z.; Tao, X.; Lu, J.; Li, G.Y. Semantic communications: Principles and challenges. arXiv 2021, arXiv:2201.01389. [Google Scholar]
- Oracevic, A.; Dilek, S.; Ozdemir, S. Security in internet of things: A survey. In Proceedings of the 2017 International Symposium on Networks, Computers and Communications (ISNCC), Marrakech, Morocco, 16–18 May 2017. [Google Scholar]
- Xie, H.; Qin, Z.; Li, G.Y.; Juang, B.-H. Deep learning enabled semantic communication systems. IEEE Trans. Signal Process. 2021, 69, 2663–2675. [Google Scholar] [CrossRef]
- Yan, L.; Qin, Z.; Zhang, R.; Li, Y.; Li, G.Y. Resource allocation for text semantic communications. IEEE Wirel. Commun. Lett. 2022, 11, 1394–1398. [Google Scholar] [CrossRef]
- Mu, X.; Liu, Y.; Guo, L.; Al-Dhahir, N. Heterogeneous semantic and bit communications: A semi-NOMA scheme. IEEE J. Sel. Areas Commun. 2023, 41, 155–169. [Google Scholar] [CrossRef]
- Lil, Y.; Zhou, X.; Zhao, J. Resource Allocation for Semantic Communication Under Physical-layer Security. In Proceedings of the GLOBECOM 2023—2023 IEEE Global Communications Conference, Kuala Lumpur, Malaysia, 4–8 December 2023. [Google Scholar]
- Mu, X.; Liu, Y. Semantic Communication-Assisted Physical Layer Security Over Fading Wiretap Channels. In Proceedings of the ICC 2024—IEEE International Conference on Communications, Denver, CO, USA, 9–13 June 2024. [Google Scholar]
- Tung, T.-Y.; Gündüz, D. Deep joint source-channel and encryption coding: Secure semantic communications. In Proceedings of the ICC 2023—IEEE International Conference on Communications, Rome, Italy, 28 May–1 June 2023. [Google Scholar]
- Luo, X.; Chen, Z.; Tao, M.; Yang, F. Encrypted semantic communication using adversarial training for privacy preserving. IEEE Commun. Lett. 2023, 27, 1486–1490. [Google Scholar] [CrossRef]
- Liu, X.; Nan, G.; Cui, Q.; Li, Z.; Liu, P.; Xing, Z.; Mu, H.; Tao, X.; Quek, T.Q.S. SemProtector: A unified framework for semantic protection in deep learning-based semantic communication systems. IEEE Commun. Mag. 2023, 61, 56–62. [Google Scholar] [CrossRef]
- Chorti, A.; Barreto, A.N.; Kopsell, S.; Zoli, M.; Chafii, M.; Sehier, P.; Fettweis, G.; Poor, H.V. Context-Aware Security for 6G Wireless: The Role of Physical Layer Security. IEEE Commun. Stand. Mag. 2022, 6, 102–108. [Google Scholar] [CrossRef]
- Zheng, J.; Tian, H.; Ni, W.; Ni, W.; Zhang, P. Balancing accuracy and integrity for reconfigurable intelligent surface-aided over-the-air federated learning. IEEE Trans. Wirel. Commun. 2022, 21, 10964–10980. [Google Scholar] [CrossRef]
- Saleem, R.; Ni, W.; Ikram, M.; Jamalipour, A. Deep-reinforcement-learning-driven secrecy design for intelli-gent-reflecting-surface-based 6G-IoT networks. IEEE Internet Things J. 2022, 10, 8812–8824. [Google Scholar] [CrossRef]
- Li, Y.; Shi, Z.; Hu, H.; Fu, Y.; Wang, H.; Lei, H. Secure Semantic Communications: From Perspective of Physical Layer Security. IEEE Commun. Lett. 2024, 28, 2243–2247. [Google Scholar] [CrossRef]
- Wang, L.; Wu, W.; Zhou, F.; Qin, Z.; Wu, Q. IRS-Enhanced Secure Semantic Communication Networks: Cross-Layer and Context-Awared Resource Allocation. IEEE Trans. Wirel. Commun. 2024, 24, 494–508. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).