Building Traceable Redactable Blockchain with Time-Verifiable Chameleon Hash
Abstract
1. Introduction
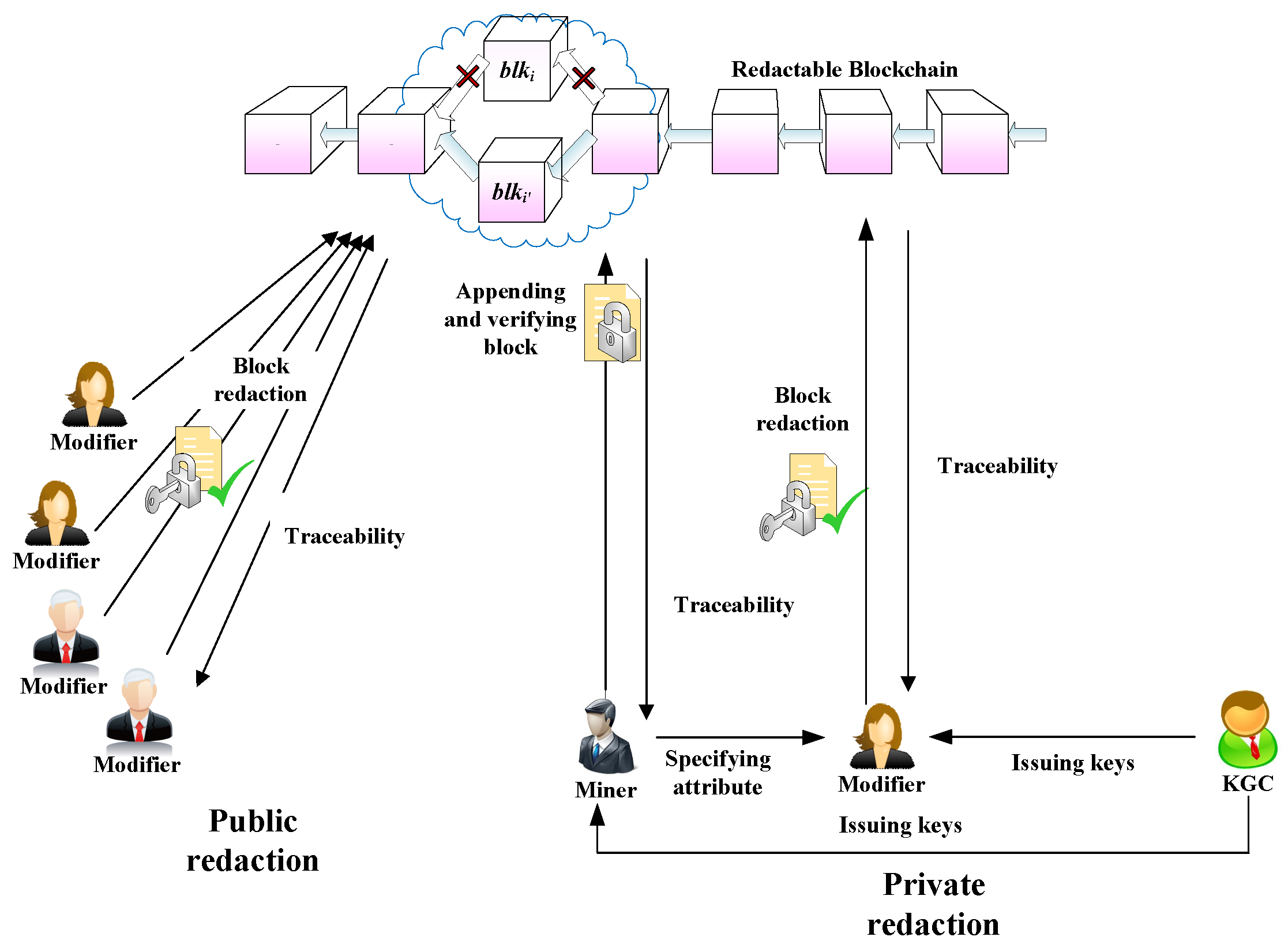
1.1. System Framework
- Key Generation Center (KGC): A trusted entity responsible for assigning a key pair to each user.
- Miner: Trusted entities with privilege to specify an access structure and write a block.
- User: Untrusted entities with read-only access to the blockchain; he cannot modify its contents.
- Modifier: An authorized user who possesses the required attributes according to the access structure, allowing them to rewrite the blockchain.
1.2. Motivations and Challenges
1.3. Contribution
- We propose the time-verifiable PCH to achieve practical redaction with traceability and scalable performance. To address the aforementioned issues, we adopt timed-release public key encryption (TPKE) as an alternative solution in our TPCH while also incorporating the ABE-based design. The resulting scheme offers private redaction via ABE for authorized users with the desired attributes and public redaction via TPKE after a given time period for all users (like the way to “mine” a block during the Proof-of-Work consensus [1]). Meanwhile, our underlying CH provides traceability and introduces a new trapdoor collision-finding algorithm, Update, as security enhancements. The former addresses regulation and traceability requirements, while the latter serves as a confirmation mechanism to address misbehaviors in redaction.
- We formally introduce time-verifiable policy-based chameleon hash (TPCH) and utilize the generic transformation proposed by Derler et al. (NDSS 2019) to build a secure time-verifiable policy-based chameleon hash for fine-grained blockchain redaction. We present a formal model, a generic construction, and concrete instantiations of the TPCH scheme. Our experimental and theoretical analyses demonstrate the feasibility of our proposal.
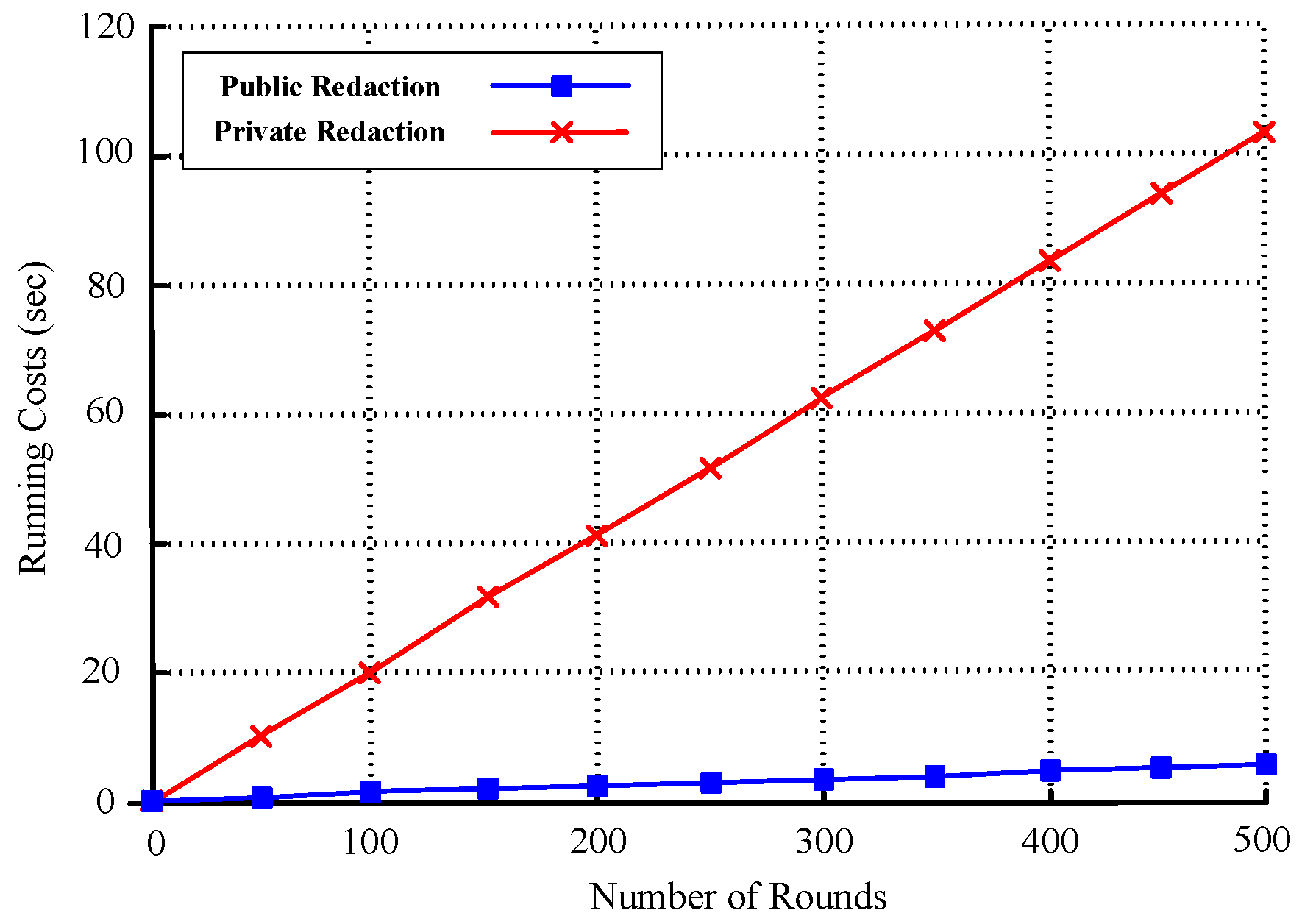
- For the quantitative analysis, the results show that for public redaction, our hashing takes 40 ms for 150 attributes, Adapt takes 290 ms for 100 attributes, and Update takes 295 ms for 50 attributes. For private redaction, our update cost averages 28 ms, and it increases from 0 to 4 s as the number of rounds increases from 0 to 500. These results demonstrate the efficiency of our proposed.
1.4. Related Works
2. Preliminaries and Building Blocks
2.1. Groups and Bilinear Maps
2.2. Non-Interactive Zero-Knowledge
- GenZK Input the security parameter ; output a common reference string .
- Prove : Input and ; output a proof .
- Ver : Input , x, and , and output indicating acceptance or rejection.
- SimGen : Input the security parameter and output a and a trapdoor .
- SimProve : Input x and ; output a proof .
2.3. Definitions of Timed-Release Public-Key Encryption
- KeyGen: Input the security parameter λ, the KGC runs this algorithm to output a pair of keys . is an implicit input hereafter.
- Enc: Input a public key and a message m; the user runs this algorithm to output a ciphertext . It runs at most time.
- FDec: The fast decryption algorithm takes as input a secret key and and outputs a message m. It runs in time at most .
- SDec: The slow decryption algorithm takes as input a public key and a and outputs a message m. It runs in time at least .
- Setup: runs Setup and returns to .
- Pre-processing Phase: launches adaptive queries to oracle controlled by during pre-processing phase. replies with FDec.
- Online Phase: submits two equal-length messages and and sends them to . He flips a random coin and returns Enc to . continues to query the oracle in the online phase except for the target ciphertext .
- Guess: makes a guess and wins if .
2.4. Definitions of Attribute-Based Encryption
- Setup: Given a security parameter and a universe description U, the KGC runs this algorithm to output the public parameter and the master key .
- KeyGen: Upon input of a master key and an attribute set , the KGC runs this algorithm to output the secret (attribute) key .
- Enc: Upon input of an access structure and a message m, the user runs this algorithm to output a ciphertext .
- Dec: Upon input of a secret key and a ciphertext , the user runs this algorithm to output the plaintext m.
- Initiation: The adversary declares the challenge access structure and sends it to .
- Setup: runs Setup and returns to .
- Query Phase: launches adaptive queries to oracle controlled by regarding an attribute , calls KeyGen and sends to . The restriction is that each query should not satisfy the challenge access structure, i.e., .
- Challenge: submits two equal-length messages and and sends them to . He flips a random coin and returns Enc to .
- Guess: makes a guess and wins if .
2.5. Definitions of Time-Verifiable Chameleon Hash
- Setup: Upon input of a security parameter , output the public parameter .
- KeyGen: Upon input of a public parameter , output the public and private keys and . For brevity, let be implicit hereafter.
- Hash: Upon input of a message m and a time period t, output a chameleon hash and a randomness .
- Ver: Upon input of a triple , and a time period t, output a decision if is valid. Else, output .
- Adapt: Upon input of a triple , a time period t, a new message , and a private key , output a new randomness .
- Update: Upon input of a triple , two time periods , and a private key , output a new randomness .
- Correctness: All hash and adapt results that are properly conducted should pass verification.
- Indistinguishability: The distribution of randomness (from Adapt) is computationally indistinguishable from that of (from Hash).
- Collision resistance (including key exposure freeness): No PPT adversary who has access to the adapt oracle should efficiently find two distinct tuples and such that VerVerwith non-negligible probability.
3. Security Requirements of Time-Verifiable and Policy-Based Chameleon Hash
3.1. Scheme Overview
- Setup: Input a security parameter and a universe description U. KGC runs ABE.Setup, CH.Setup and TPKE.Setup. Letand . Output the public parameters and master key .
- KeyGen: Input a master key and an attribute set S. Parse . KGC runs ABE.KeyGen and TVCH.KeyGen. Letand . Output secret and public hash key pair . is an implicit input hereafter.
- Hash: Input a redaction request , an auxiliary input , and a message m. The user runs TVCH. Hash and TVCH.Hash. Run ABE.Enc. Let , . Let be an ephemeral trapdoor. Output a tuple including a chameleon hash, a randomness and an encrypted ephemeral trapdoor .
- Ver: Input a public key , a chameleon tuple and a time . User runs TVCH.Ver and TVCH.Ver. If , return 1. Otherwise, return .
- Adapt: Input a secret key , a redaction request , a tuple , a time t, a new message and an ephemeral trapdoor . Run ABE.Dec. Then, run TVCH.Adapt and TVCH.Adaptwhere . Run ABE.Enc. Let . Output the new chameleon randomness .
- Update: Input a secret key , a redaction request , a tuple , two time periods and an ephemeral trapdoor . Run ABE.Dec. Then, run TVCH.Update and TVCH.Updatewhere . Run ABE.Enc. Let . Output the new chameleon randomness .
3.2. Indistinguishability
- Init: declares the target redaction mode and attribute set . We have
- Setup: runsSetup and returns to .Query Phase: picks random . In addition, issues the following queries to .
- -
- : , can query the decryption key oracle of ABE previously mentioned in .
- -
- : If , can issue a query on the TPKE ciphertext to this oracle during the pre-processing phase. is allowed to query in time at most in the pre-processing phase and time at most in the subsequent online phase. To respond, runs FDec and returns M to . One restriction should apply: the challenged ciphertext should not be queried.
- -
- issues a hash or adapt query on two messages ( is the message space), redaction request and auxiliary hash input . runs Hash, Hash. Further, sets Adapt. Then, run Ver on and under time period , respectively; if either of the outputs is 0, return . Otherwise, it flips a coin and returns the tuple .
- Guess: makes a guess for b.
3.3. Other Securities
4. Construction of Time-Verifiable Policy-Based Chameleon Hash
4.1. Design Goals
- Public Redaction: Adopts TPKE to encrypt the one-time private key (i.e., ephemeral trapdoor key) for redaction. TPKE offers IND-CCA security for the ciphertext for a given time period. After that, anyone can obtain this ephemeral private key for redaction.
- Private Redaction: Adopts ABE to encrypt the one-time private key for redaction. Only authorized users with designated attributes can obtain the private key to perform redaction.
4.2. Concrete Design
- Setup The KGC runs ABE.Setup and TPKE.Setup to initiate ABE and TPKE, respectively. Initiate in the following manner: choose two cyclic groups with order p and generator g. Let be a bilinear map. Let be a -keyed collision-resilient hash. Run NIZK.GenZK to derive . Let . Output the public parameters and master key as:
- KeyGen: Given an attribute set S, the KGC runs ABE.KeyGen. Then, KGC picks ; compute . Run NIZK.Prove. Output and .
- Hash: Set the auxiliary input according to redaction request asNext, run NIZK.Verify. If output 0, return . Check if . If not, return ⊥. Pick and ephemeral trapdoor . Generate and NIZK.Prove. Then, computeProceed differently:
- If = “private”: Set . Run ABE.Enc and let .
- If = “public”: Run . Run TPKE.Enc and let .
LetThe hashing algorithm outputs . - Ver: The user runs this algorithm for verification:
- If , or , or , return ⊥.
- Check if NIZK.VerNIZK.VerNIZK.Ver holds. If no, return ⊥.
- Check if holds. If yes, output 1. Otherwise, check if and . If yes, output 0. Otherwise, output ⊥.
- Adapt: The modifier runs this algorithm. If , return . Otherwise, proceed differently according to the redaction request as
- -
- = “private”:
- Run TPCH.Ver. If output 0, return ⊥.
- Compute and . If , return directly.
- Run ABE.Dec and to recover the encrypted chameleon randomness .
- Computeand . Run encode1 and ABE.Enc to obtain a new ciphertext . Then, run NIZK.Prove to obtain . Let .
- -
- = “public”:
- Run Ver. Output ⊥ if the output is not 1. Otherwise, compute . If , return directly. Otherwise, run to obtain . If outputs ⊥, return ⊥. Otherwise, run to obtain .
- Compute and .
- Run encode2 and TPKE.Enc to obtain the new ciphertext . Run NIZK.Prove to obtain . Let .
The adaption algorithm outputs a new randomness set, . Note that we sometimes ignore the subscript in long equations for brevity, i.e., for . It should be clear based on the context., - Update: The modifier runs this algorithm for update. If , return . Else, proceed:
- -
- = “private”:
- Run TVCH.Ver. If output 0 or ⊥, return ⊥. Then, compute . If , return .
- Run ABE.Dec and to recover the encrypted chameleon randomness .
- Computeand .
- Run encode1 and ABE.Enc to obtain a new ciphertext . Then, run NIZK.Prove to obtain , respectively. Let .
- -
- = “public”:
- Run Ver. If output 0 or ⊥, return ⊥. Else, compute . If , return .
- Run TPKE.SDec to obtain . If outputs ⊥, return ⊥. Otherwise, run to obtain .
- Compute .
- Run encode2 and TPKE.Enc to obtain the new ciphertext . Run to obtain . Let .
This update algorithm outputs .
4.3. Instantiations
4.4. Security Analysis of TPCH
5. Performance Evaluations
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Satoshi Nakamoto. 2008. Available online: http://bitcoin.org/bitcoin.pdf (accessed on 19 February 2025).
- Maesa, D.D.F.; Mori, P. Blockchain 3.0 applications survey. J. Parallel Distrib. Comput. 2020, 138, 99–114. [Google Scholar] [CrossRef]
- Ateniese, G.; Magri, B.; Venturi, D.; Andrade, E. Redactable blockchain–or–rewriting history in bitcoin and friends. In Proceedings of the 2017 IEEE European Symposium on Security and Privacy (EuroS&P), Paris, France, 26–28 April 2017; pp. 111–126. [Google Scholar]
- Politou, E.; Casino, F.; Alepis, E.; Patsakis, C. Blockchain mutability: Challenges and proposed solutions. IEEE Trans. Emerg. Top. Comput. 2019, 9, 1972–1986. [Google Scholar] [CrossRef]
- Ye, T.; Luo, M.; Yang, Y.; Choo, K.K.R.; He, D. A Survey on Redactable Blockchain: Challenges and Opportunities. IEEE Trans. Netw. Sci. Eng. 2023, 10, 1669–1683. [Google Scholar] [CrossRef]
- Derler, D.; Samelin, K.; Slamanig, D.; Striecks, C. Fine-Grained and Controlled Rewriting in Blockchains: Chameleon-Hashing Gone Attribute-Based. In Proceedings of the 26th Annual Network and Distributed System Security Symposium (NDSS 2019), San Diego, CA, USA, 24–27 February 2019. [Google Scholar]
- Xu, S.; Ning, J.; Ma, J.; Xu, G.; Yuan, J.; Deng, R.H. Revocable policy-based chameleon hash. In Proceedings of the 26th European Symposium on Research in Computer Security, ESORICS 2021, Darmstadt, Germany, 4–8 October 2021; pp. 327–347. [Google Scholar]
- Camenisch, J.; Derler, D.; Krenn, S.; Pöhls, H.C.; Samelin, K.; Slamanig, D. Chameleon-hashes with ephemeral trapdoors. In Proceedings of the 20th IACR International Conference on Practice and Theory in Public-Key Cryptography, Amsterdam, The Netherlands, 28–31 March 2017; pp. 152–182. [Google Scholar]
- Tian, Y.; Li, N.; Li, Y.; Szalachowski, P.; Zhou, J. Policy-based Chameleon Hash for Blockchain Rewriting with Black-box Accountability. In Proceedings of the ACSAC ’20: Annual Computer Security Applications Conference, Austin, TX, USA, 7–11 December 2020; pp. 813–828. [Google Scholar]
- Jia, M.; Chen, J.; He, K.; Du, R.; Zheng, L.; Lai, M.; Wang, D.; Liu, F. Redactable Blockchain From Decentralized Chameleon Hash Functions. IEEE Trans. Inf. Forensics Secur. 2022, 17, 2771–2783. [Google Scholar] [CrossRef]
- Ma, J.; Xu, S.; Ning, J.; Huang, X.; Deng, R.H. Redactable Blockchain in Decentralized Setting. IEEE Trans. Inf. Forensics Secur. 2022, 17, 1227–1242. [Google Scholar] [CrossRef]
- Xu, S.; Huang, X.; Yuan, J.; Li, Y.; Deng, R.H. Accountable and Fine-Grained Controllable Rewriting in Blockchains. IEEE Trans. Inf. Forensics Secur. 2022, 18, 101–116. [Google Scholar] [CrossRef]
- Xu, J.; Li, X.; Yin, L.; Lu, Y.; Tang, Q.; Zhang, Z. Redactable Blockchain Protocol with Instant Redaction. IACR Cryptol. ePrint Arch. 2021, 2021, 223. [Google Scholar]
- Huang, K.; Mu, Y.; Rezaeibagha, F.; Zhang, X.; Li, X. Monero with Multi-Grained Redaction. IEEE Trans. Dependable Secur. Comput. 2023, 21, 241–253. [Google Scholar] [CrossRef]
- Katz, J.; Loss, J.; Xu, J. On the security of time-lock puzzles and timed commitments. In Proceedings of the 18th International Conference, TCC 2020, Durham, NC, USA, 16–19 November 2020; pp. 390–413. [Google Scholar]
- Deuber, D.; Magri, B.; Thyagarajan, S.A.K. Redactable blockchain in the permissionless setting. In Proceedings of the 2019 IEEE Symposium on Security and Privacy (S&P), San Francisco, CA, USA, 19–23 May 2019; pp. 124–138. [Google Scholar]
- Xu, S.; Ning, J.; Ma, J.; Huang, X.; Deng, R.H. K-Time modifiable and mpoch-Based redactable blockchain. IEEE Trans. Inf. Forensics Secur. 2021, 16, 4507–4520. [Google Scholar] [CrossRef]
- Shen, J.; Chen, X.; Liu, Z.; Susilo, W. Verifiable and Redactable Blockchains with Fully Editing Operations. IEEE Trans. Inf. Forensics Secur. 2023, 18, 3787–3802. [Google Scholar] [CrossRef]
- Li, J.; Ma, H.; Wang, J.; Song, Z.; Xu, W.; Zhang, R. Wolverine: A Scalable and Transaction-Consistent Redactable Permissionless Blockchain. IEEE Trans. Inf. Forensics Secur. 2023, 18, 1653–1666. [Google Scholar] [CrossRef]
- Liu, Z.; Cao, Z.; Wong, D.S. Blackbox traceable CP-ABE: How to catch people leaking their keys by selling decryption devices on ebay. In Proceedings of the CCS ’13: Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, Berlin, Germany, 4–8 November 2013; pp. 475–486. [Google Scholar]
- Matzutt, R.; Henze, M.; Ziegeldorf, J.H.; Hiller, J.; Wehrle, K. Thwarting unwanted blockchain content insertion. In Proceedings of the 2018 IEEE International Conference on Cloud Engineering (IC2E), IEEE, Orlando, FL, USA, 17–20 April 2018; pp. 364–370. [Google Scholar]
- Goyal, V.; Kothapalli, A.; Masserova, E.; Parno, B.; Song, Y. Storing and retrieving secrets on a blockchain. In Proceedings of the 25th IACR International Conference on Practice and Theory of Public-Key Cryptography, Virtual Event, 8–11 March 2022; pp. 252–282. [Google Scholar]
- Xu, S.; Zhang, Y.; Li, Y.; Liu, X.; Yang, G. Generic construction of elgamal-type attribute-based encryption schemes with revocability and dual-policy. In Proceedings of the Security and Privacy in Communication Networks: 15th EAI International Conference, SecureComm 2019, Orlando, FL, USA, 23–25 October 2019; Proceedings, Part II 15. Springer: Cham, Switzerland, 2019; pp. 184–204. [Google Scholar]
- Agrawal, S.; Chase, M. FAME: Fast attribute-based message encryption. In Proceedings of the CCS ’17: Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017; pp. 665–682. [Google Scholar]
- Rouselakis, Y.; Waters, B. Practical constructions and new proof methods for large universe attribute-based encryption. In Proceedings of the CCS ’13: Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, Berlin, Germany, 4–8 November 2013; pp. 463–474. [Google Scholar]
- Guo, L.; Wang, Q.; Yau, W.C. Online/Offline Rewritable Blockchain with Auditable Outsourced Computation. IEEE Trans. Cloud Comput. 2021, 11, 499–514. [Google Scholar] [CrossRef]
- Ning, J.; Cao, Z.; Dong, X.; Liang, K.; Ma, H.; Wei, L. Auditable σ-time outsourced attribute-based encryption for access control in cloud computing. IEEE Trans. Inf. Forensics Secur. 2017, 13, 94–105. [Google Scholar] [CrossRef]



| Scheme | Key Component | Redaction Security | Performance | Practical Functionality | |||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Hyb | Revo | FR | Trace | Anony | MPC | Efficiency | Fine-Grained | Decentralization |
Applying with Coin | ||
| AMV+ 17 [3] | CH | ✕ | ✕ | ✕ | ✓ | ✕ | ✓ | Ideal | ✕ | ✓ | Bitcoin |
| TLL+17 [9] | ABE+CH | ✕ | ✕ | ✕ | ✓ | ✕ | ✕ | Acceptable | ✕ | ✕ | ✕ |
| DMT+19 [16] | Consensus-based voting | ✕ | ✕ | ✕ | ✓ | ✕ | ✕ | Fast | ✕ | ✓ | Bitcoin |
| DSS+19 [6] | ABE and CHET | ✕ | ✕ | ✕ | ✓ | ✕ | ✕ | Not Ideal | ✓ | ✓ | ✕ |
| XNM+21a [7] | PCH | ✕ | ✓ | ✕ | ✕ | ✓ | ✕ | Ideal | ✓ | ✕ | ✕ |
| XNM+21b [17] | Time-locked deposit penalty | ✕ | ✕ | ✕ | ✕ | ✕ | ✕ | Efficient | ✕ | ✕ | ✕ |
| JCH+22 [10] | RSA accumulator | ✕ | ✕ | ✕ | ✕ | ✕ | ✓ | Efficient | ✓ | ✓ | ✕ |
| MXN+22 [11] | ABE and CHET | ✕ | ✕ | ✕ | ✕ | ✕ | ✓ | Acceptable | ✓ | ✓ | ✕ |
| XHY+22 [12] | Attribute-based traitor tracing | ✕ | ✕ | ✕ | ✓ | ✕ | ✕ | Efficient | ✓ | ✕ | ✕ |
| HMR+23 [14] | Trapdoor cryptography | ✕ | ✕ | ✕ | ✓ | ✓ | ✓ | Acceptable | ✓ | ✓ | Monero |
| SCL+23 [18] | Double-trapdoor CH | ✕ | ✕ | ✕ | ✕ | ✕ | ✕ | Acceptable | ✕ | ✕ | ✓ |
| LMW+23 [19] | Non-interactive threshold CH | ✕ | ✕ | ✕ | ✕ | ✕ | ✕ | Efficient | ✕ | ✓ | UTXO |
| Our TPCH | ABE and TPKE [15] | ✓ | ✓ | ✓ | ✓ | ✕ | ✕ | Efficient (Online) | ✓ | ✓ | ✕ |
| Reference | Scheme | Properties | Costs (User-Side) | ||||
|---|---|---|---|---|---|---|---|
| Revoc | Fine-Grained | On/Off | Delegation | Hash | Adapt | ||
| DSS+19 [6] | FAME [24] + RSA-based CH [8] | ✕ | ✓ | ✕ | ✕ | ||
| TLL+20 [9] | FAME [24] + DL-based CH [8] | ✓ | ✓ | ✕ | ✕ | ||
| GWY+21 [26] | AB-KEM [27] (from CP-ABE [25]) + RSA-based CH [8] | ✕ | ✓ | ✕ | ✕ | ||
| XNM+21 [7] | RABE (from FAME [24]) + RSA-based CH [8] | ✓ | ✓ | ✕ | ✕ | ||
| XHY+22 [12] | PCH from the Fujisaki–Okamoto transformation | ✕ | ✓ | ✕ | ✕ | ||
| Our TPCH | CP-ABE [25] + DL-based CH [8] | ✕ | ✓ | ✕ | ✕ | ||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, M.; Xie, G.; Pan, B.; Fang, J.; Xu, Z.; Zhao, Z. Building Traceable Redactable Blockchain with Time-Verifiable Chameleon Hash. Electronics 2025, 14, 846. https://doi.org/10.3390/electronics14050846
Chen M, Xie G, Pan B, Fang J, Xu Z, Zhao Z. Building Traceable Redactable Blockchain with Time-Verifiable Chameleon Hash. Electronics. 2025; 14(5):846. https://doi.org/10.3390/electronics14050846
Chicago/Turabian StyleChen, Mingliang, Guoqiang Xie, Benren Pan, Jinyan Fang, Zaide Xu, and Zhen Zhao. 2025. "Building Traceable Redactable Blockchain with Time-Verifiable Chameleon Hash" Electronics 14, no. 5: 846. https://doi.org/10.3390/electronics14050846
APA StyleChen, M., Xie, G., Pan, B., Fang, J., Xu, Z., & Zhao, Z. (2025). Building Traceable Redactable Blockchain with Time-Verifiable Chameleon Hash. Electronics, 14(5), 846. https://doi.org/10.3390/electronics14050846






