Infimum and Supremum of Thresholds for Reversible Data Hiding
Abstract
1. Introduction
2. Related Work
3. Overflow and Underflow Reduction
3.1. Common Techniques of RDH
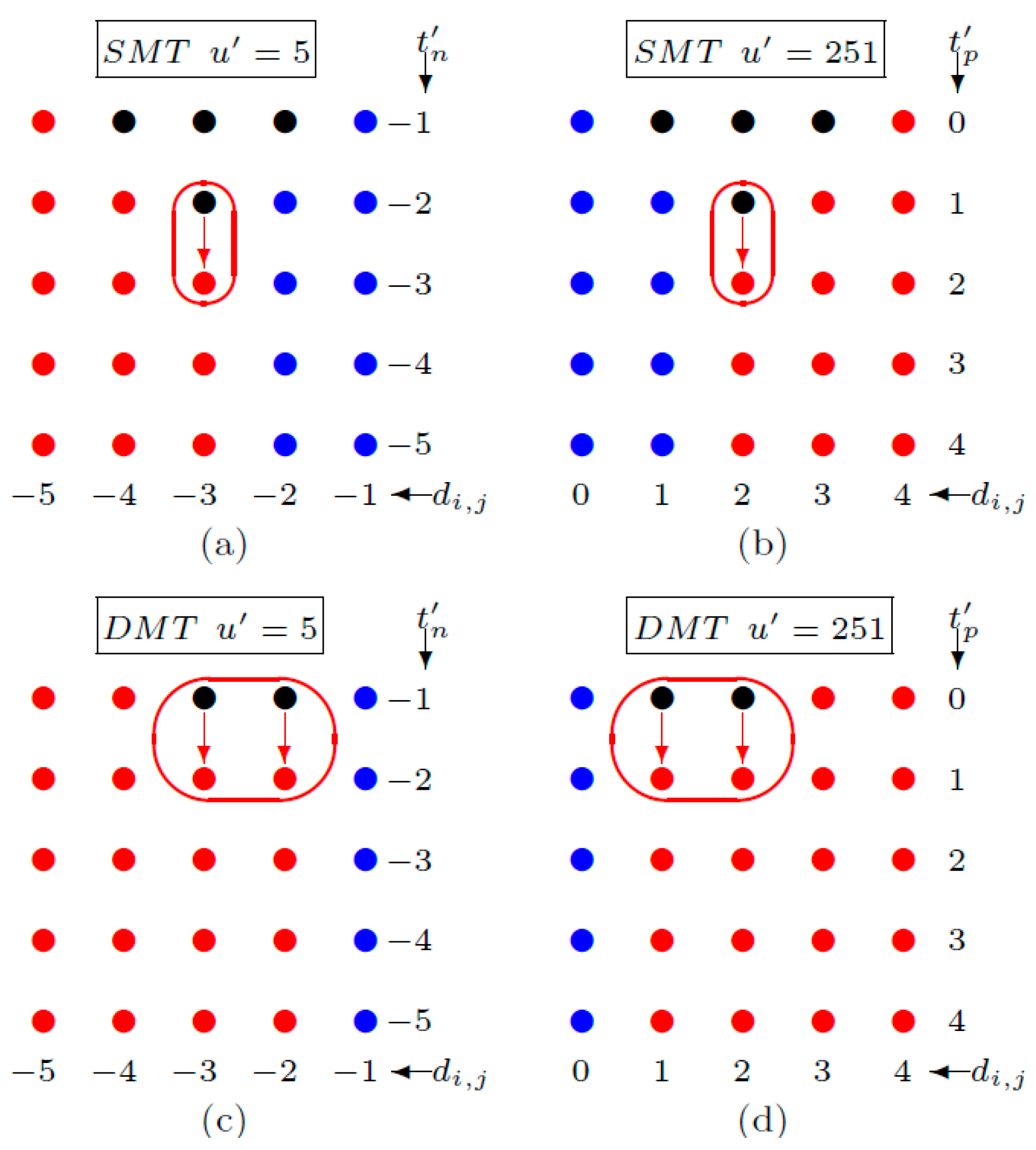
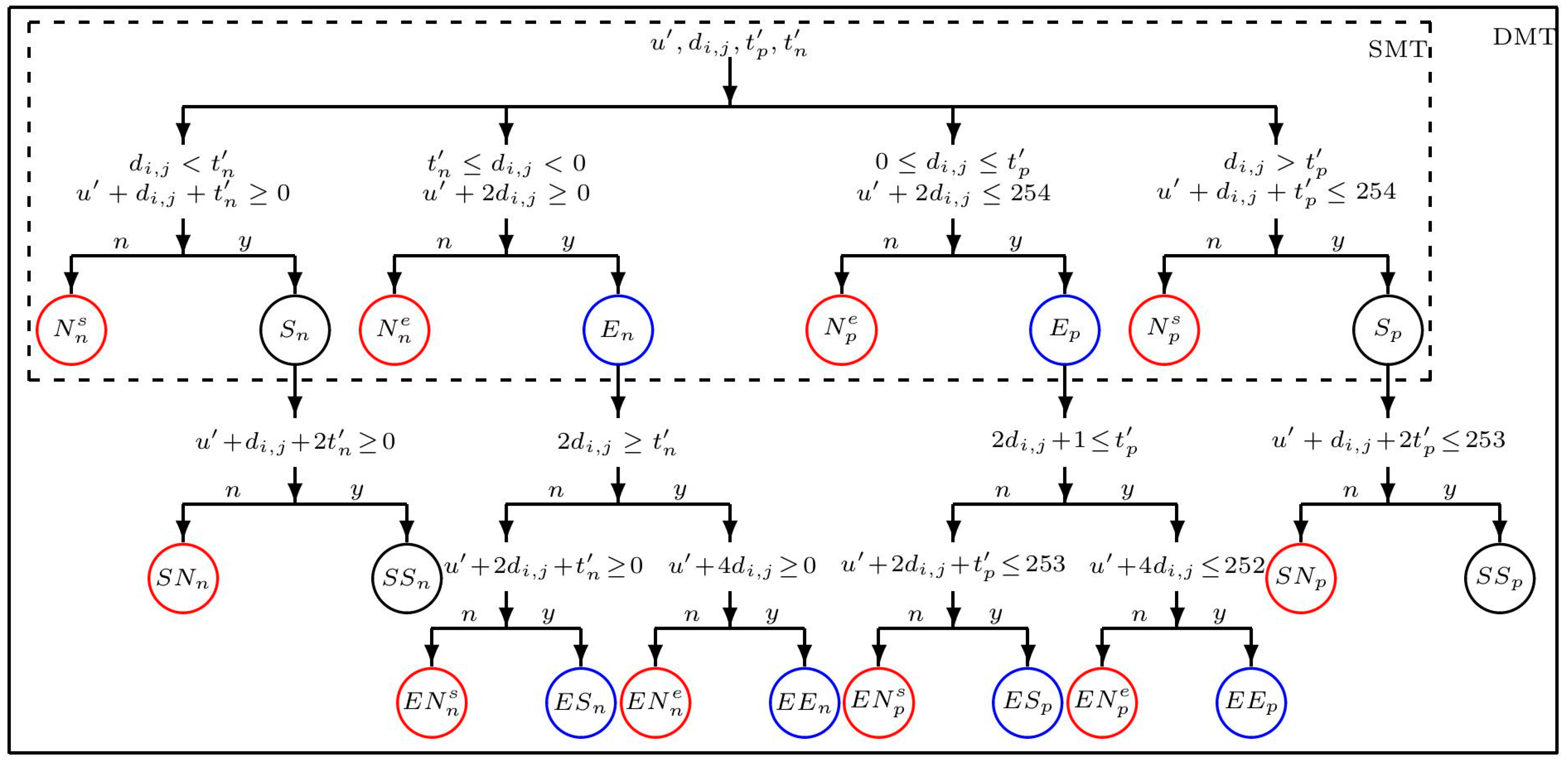
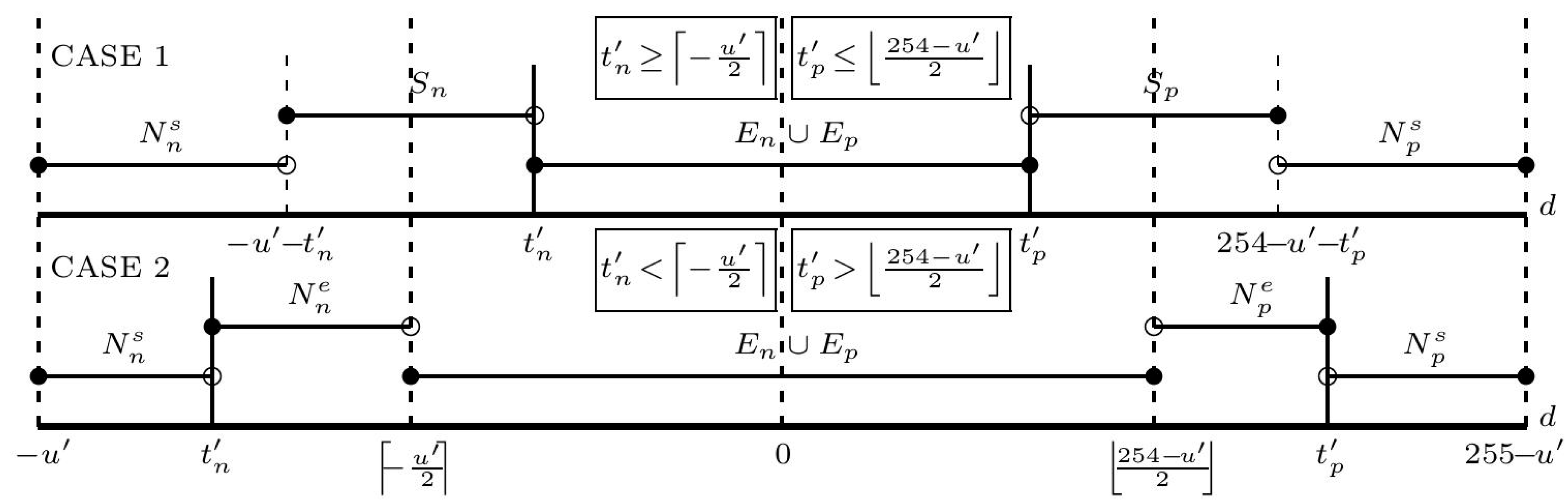
3.2. The Supremum and Infimum for SMT
- Case 1: If , here , where r {0,1} is a remainder of u′ divided by 2, then and
- Case 1: If , here , where r {0,1} is a remainder of 254 − u’ divided by 2, then and
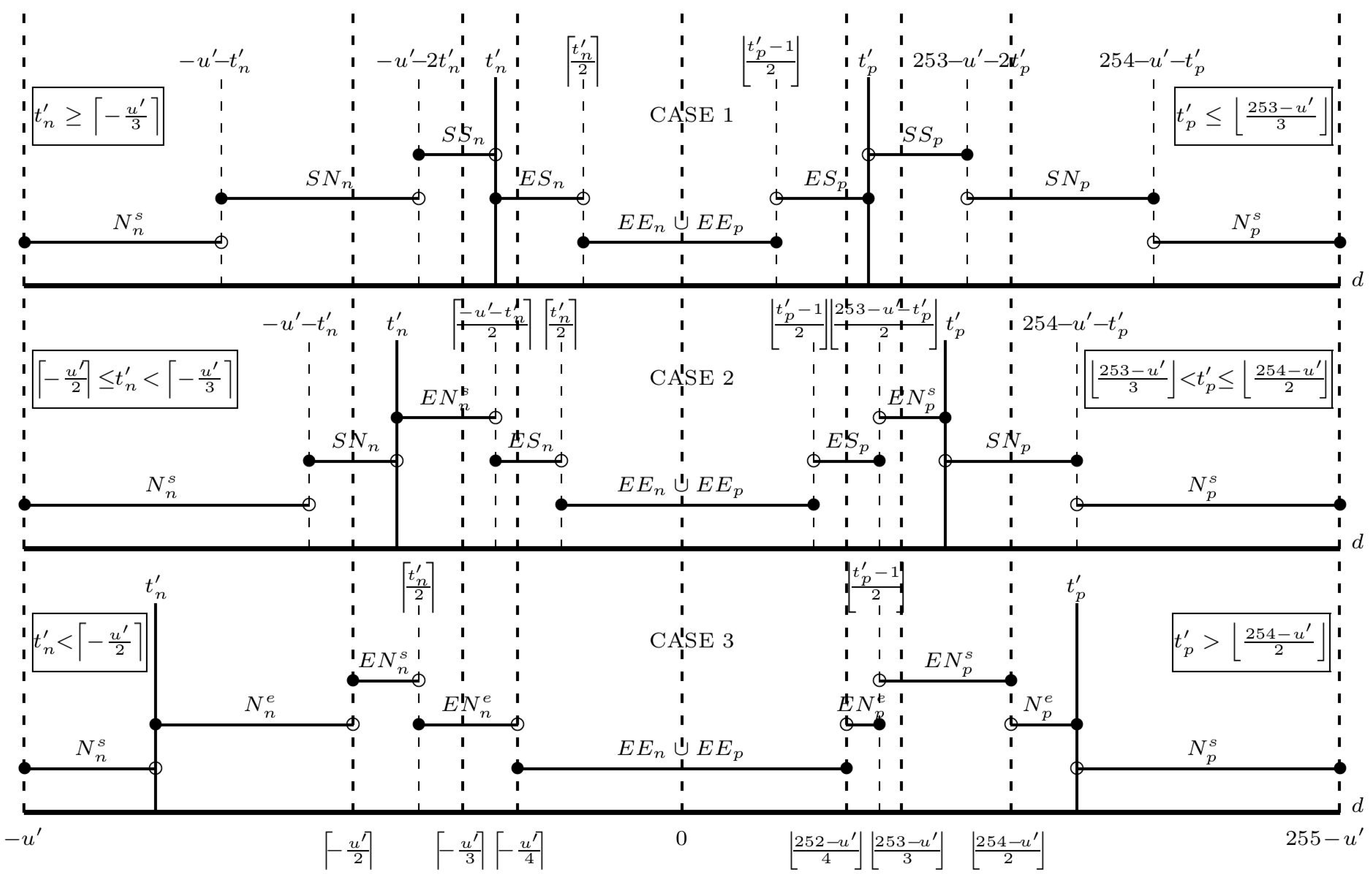
3.3. The Supremum and Infimum for DMT
- Case 1: If , here , where r {0,1,2} is a remainder of u′ divided by 3, then and
- Case 1: for ,
- Case 2: for
- Case 3: If
- Case 1:
- Case 2:
- Case 3: If
- Case 1: If , here , where r {0,1,2} is a remainder of 253 − u’ divided by 3, then and
4. Advantage of the Supremum and Infimum
4.1. Determining the First Operating Threshold
| Algorithm 1 The algorithm to determine the first operating threshold. |
| Comment: Array A is initialized with zero values. t = 0, ne = 0, nm = 0 while ne < nm + P + Q and t < 170 do ne = 0, nm = 0, k = 0, t = t + 1 while ne < nm + P + Q and k < N do k = k + 1 if A(k) = 1 then ne = ne + 1 else if A(k) = 2 then nm = nm + 1 else if d(k) < 0 and tn − u′(k)/3 then if d(k) tn then ne = ne +1, A(k) = 1 else if d(k) < −u′(k) − 2tn then nm = nm + 1, A(k) = 2 end if else if d(k) 0 and tp (253 − u′(k))/3 then if d(k) tp then ne = ne + 1, A(k) = 1 else if d(k) > 253 − u′(k) − 2tp then nm = nm + 1, A(k) = 2 end if end if end while end while if ne = = nm + P + Q then tf = t end if |
4.2. The Formulas for Decoding and Encoding
5. Encoding and Decoding
- -
- Step 1: For each pixel, calculate the predicted values, prediction errors, and local variance values according to [17].
- -
- Step 2: Sort the local variance values in ascending order to establish the pixel processing order. This order will be used for Steps 3 through 7.
- -
- Step 3: Set aside the last 28 pixels and gather their LSB (least significant bit) values.
- -
- Step 4: Determine the first operating threshold using the procedure outlined in algorithm 1.
- -
- Step 5: Use Equation (2) to embed the payload, the last 28 LSBs, and the location map. The location map is created with Equation (3), and this step is applied pixel by pixel.
- -
- Step 6: Create the footer, insert it into the last 28 LSBs, and then calculate the PSNR (Peak Signal-to-Noise Ratio).
- -
- Step 7: Increase the threshold t and return to Step 5. Stop the process when the PSNR starts decreasing.
- -
- Step 1: Calculate the local variance values.
- -
- Step 2: Sort the local variance values in ascending order to establish the operating order for processing the pixels. This order is used for Steps 3 through 7.
- -
- Step 3: Extract the footer from the last 28 LSBs, which contains the operating threshold and the final embedding position.
- -
- Step 4: Compute the predicted values and prediction errors.
- -
- Step 5: Use Equation (5) to extract the payload, location map, and the original 28 LSBs.
- -
- Step 6: Recover the original pixel values using Equation (4).
- -
- Step 7: Restore the original 28 LSBs.
6. Experiments
6.1. Test Images
- (1)
- Normally, the problematic pixels have intensities closer to the minimum or maximum. Hence, Man, Tiffany, Grass (D9), Sand, Car and APCs, Kodim06, Kodim10, and Kodim20 are considered to be elements of this group. To facilitate comparison, Man is resized into 512 × 512.
- (2)
- There are eight images in this group, Lena, Barbara, Baboon, Peppers, Fishing boat, Sailboat, Elaine, Airplane (F-16), Kodim12, Kodim14, Kodim16, and Kodim22. The intensities of these images are not close to the minimum or maximum. Thus, we can usually dispense with the location map from these images, unlike the first group.
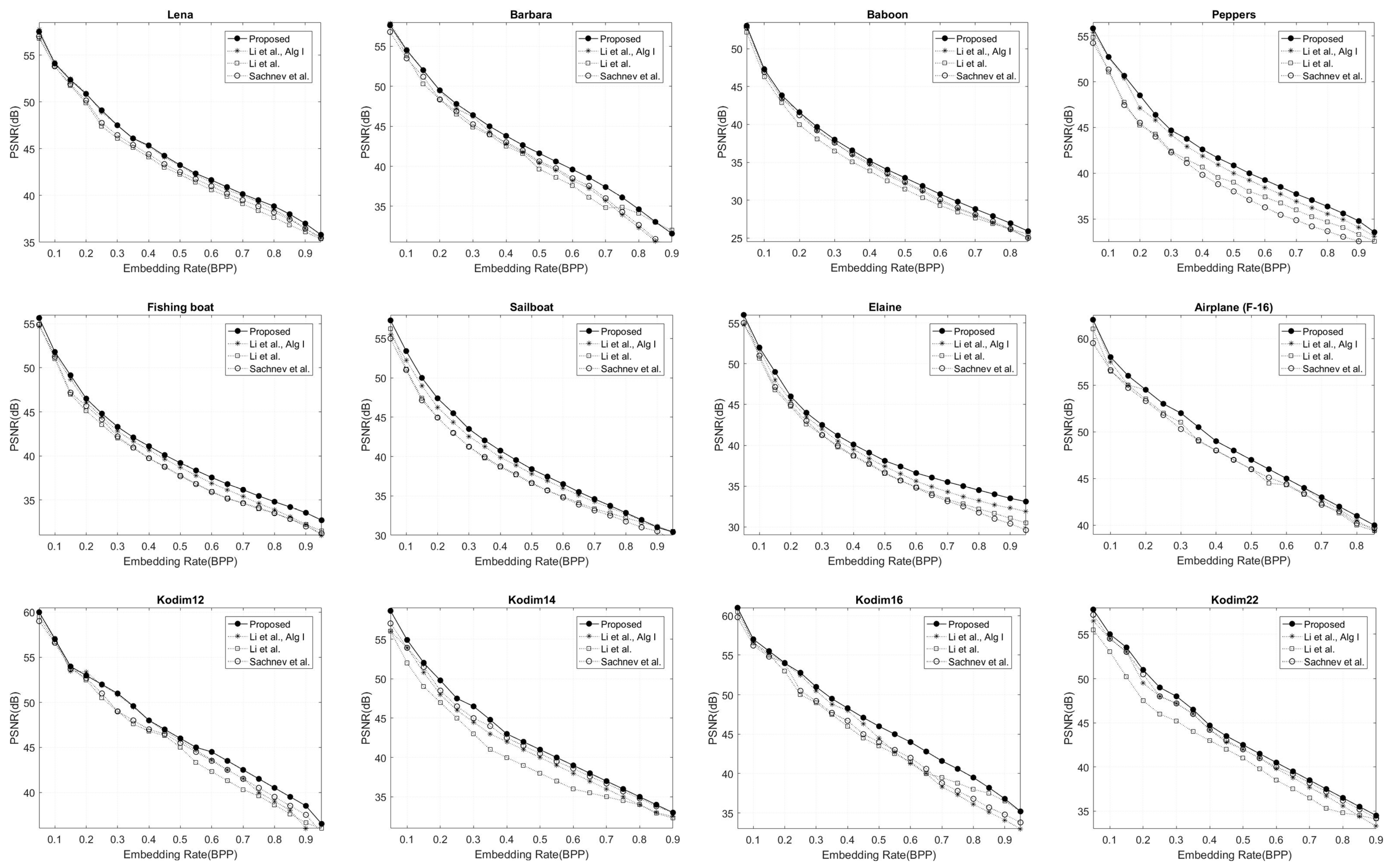
6.2. Experimental Results
7. Conclusions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Fridrich, J.; Goljan, M.; Du, R. Lossless data embedding—New paradigm in digital watermarking. EURASIP J. Adv. Signal Process. 2002, 2002, 185–196. [Google Scholar] [CrossRef]
- Kalker, T.; Willems, F.M.J. Capacity bounds and constructions for reversible data hiding. In Proceedings of the 2002 14th International Conference on Digital Signal Processing Proceedings, Santorini, Greece, 1–3 July 2002. [Google Scholar]
- Celik, M.U.; Sharma, G.; Tekalp, A.M.; Saber, E. Lossless generalized-LSB data embedding. IEEE Trans. Image Process. 2005, 14, 253–266. [Google Scholar] [CrossRef] [PubMed]
- Celik, M.U.; Sharma, G.; Tekalp, A.M. Lossless watermarking for image authentication: A new framework and an implementation. IEEE Trans. Image Process. 2006, 15, 1042–1049. [Google Scholar] [CrossRef]
- Tian, J. Reversible data embedding using a difference expansion. IEEE Trans. Circuits Syst. Video Technol. 2003, 13, 890–896. [Google Scholar] [CrossRef]
- Alattar, A.M. Reversible watermark using the difference expansion of a generalized integer transform. IEEE Trans. Image Process. 2004, 13, 1147–1156. [Google Scholar] [CrossRef]
- Kamstra, L.; Heijmans, H.J.A.M. Reversible data embedding into image using wavelet techniques and sorting. IEEE Trans. Image Process. 2005, 14, 2082–2090. [Google Scholar] [CrossRef]
- Kim, H.J.; Sachnev, V.; Shi, Y.Q.; Nam, J.; Choo, H.G. A novel difference expansion transform for reversible data embedding. IEEE Trans. Inf. Forensics Secur. 2008, 4, 456–465. [Google Scholar]
- Lee, S.; Yoo, C.D.; Kalker, T. Reversible image watermarking based on integer-to-integer wavelet transform. IEEE Trans. Inf. Forensics Secur. 2007, 2, 321–330. [Google Scholar] [CrossRef]
- Coltuc, D. Low distortion transform for reversible watermarking. IEEE Trans. Image Process. 2012, 21, 412–417. [Google Scholar] [CrossRef]
- Wang, X.; Shao, C.; Xu, X.; Niu, X. Reversible Data-Hiding Scheme for 2-D Vector Maps Based on Difference Expansion. IEEE Trans. Inf. Forensics Secur. 2007, 2, 311–320. [Google Scholar] [CrossRef]
- Ni, Z.; Shi, Y.Q.; Ansari, N.; Su, W. Reversible data hiding. IEEE Trans. Circuits Syst. Video Technol. 2006, 16, 354–362. [Google Scholar]
- Thodi, D.M.; Rodriguez, J.J. Prediction-error-based reversible watermarking. In Proceedings of the 2004 IEEE International Conference on Image Processing, Singapore, 24–27 October 2004. [Google Scholar]
- Thodi, D.M.; Rodriguez, J.J. Reversible watermarking by prediction-error expansion. In Proceedings of the 2004 IEEE Southwest Symposium on Image Analysis and Interpretation, Lake Tahoe, NV, USA, 28–30 March 2004. [Google Scholar]
- Thodi, D.M.; Rodriguez, J.J. Expansion embedding techniques for reversible watermarking. IEEE Trans. Image Process. 2007, 16, 721–730. [Google Scholar] [CrossRef] [PubMed]
- Hu, Y.; Lee, H.K.; Li, J. DE-based Reversible data hiding with improved overflow location map. IEEE Trans. Circuits Syst. Video Technol. 2009, 19, 250–260. [Google Scholar]
- Sachnev, V.; Kim, H.J.; Nam, J.; Suresh, S.; Shi, Y.Q. Reversible watermarking algorithm using sorting and prediction. IEEE Trans. Circuits Syst. Video Technol. 2009, 19, 989–999. [Google Scholar] [CrossRef]
- Lou, L.; Chen, Z.; Chen, M.; Zeng, X.; Xiong, Z. Reversible image watermarking using interpolation technique. IEEE Trans. Inf. Forensics Secur. 2010, 5, 187–193. [Google Scholar]
- Hwang, H.J.; Kim, H.J.; Sachnev, V.; Joo, S.H. Reversible watermarking method using optimal histogram pair shifting based on prediction and sorting. KSII Trans. Internet Inf. Syst. 2010, 4, 655–670. [Google Scholar] [CrossRef]
- Coltuc, D. Improved embedding for prediction-based reversible watermarking. IEEE Trans. Inf. Forensics Secur. 2011, 6, 873–882. [Google Scholar] [CrossRef]
- Li, X.; Yang, B.; Zeng, T. Efficient reversible watermarking based on adaptive prediction-error expansion and pixel selection. IEEE Trans. Image Process. 2011, 20, 3524–3533. [Google Scholar]
- Dragoi, C.; Coltuc, D. Improved rhombus interpolation for reversible watermarking by difference expansion. In Proceedings of the 20th European Signal Processing Conference (EUSIPCO), Bucharest, Romania, 27–31 August 2012. [Google Scholar]
- Li, X.; Li, B.; Yang, B.; Zeng, T. General Framework to Histogram-Shifting-Based Reversible Data Hiding. IEEE Trans. Image Process. 2013, 22, 2181–2191. [Google Scholar] [CrossRef]
- Ou, B.; Li, X.; Zhao, Y.; Ni, R. Reversible data hiding based on PDE predictor. J. Syst. Softw. 2013, 86, 2700–2709. [Google Scholar] [CrossRef]
- Coatrieux, G.; Pan, W.; Cuppens-Boulahia, N.; Cuppens, F.; Roux, C. Reversible watermarking based on invariant image classication and dynamic histogram shifting. IEEE Trans. Inf. Forensics Secur. 2013, 8, 111–120. [Google Scholar] [CrossRef]
- Panyindee, C.; Pintavirooj, C. Optimal gaussian weight predictor and sorting using genetic algorithm for reversible watermarking based on PEE and HS. IEICE Tran. Inf. Syst. 2016, E99, 2306–2319. [Google Scholar] [CrossRef]
- Yin, Z.; Chen, L.; Lyu, W.; Luo, B. Reversible attack based on adversarial perturbation and reversible data hiding in YUV colorspace. Pattern Recognit. Lett. 2023, 166, 1–7. [Google Scholar] [CrossRef]
- Qin, C.; Zhang, W.; Cao, F.; Zhang, X.; Chang, C.-C. Separable reversible data hiding in encrypted images via adaptive embedding strategy with block selection. Signal Process. 2018, 153, 109–122. [Google Scholar] [CrossRef]
- Qin, C.; Jiang, C.; Mo, Q.; Yao, H.; Chang, C.-C. Reversible data hiding in encrypted image via secret sharing based on GF(p) and GF(28). IEEE Trans. Circuits Syst. Video Technol. 2022, 32, 1928–1941. [Google Scholar]
- Li, Q.; Ma, B.; Wang, X.; Wang, C.; Gao, S. Image steganography in color conversion. IEEE Trans. Circuits Syst. 2024, 71, 106–110. [Google Scholar] [CrossRef]
- Li, Q.; Ma, B.; Fu, X.; Wang, X.; Wang, C.; Li, X. Robust image steganography via color conversion. IEEE Trans. Circuits Syst. Video Technol. 2024, 35, 1399–1408. [Google Scholar] [CrossRef]
- He, J.; Chen, J.; Tang, S. Reversible data hiding in JPEG images based on negative influence models. IEEE Trans. Inf. Forensics Secur. 2020, 15, 2121–2133. [Google Scholar] [CrossRef]
- Yin, Z.; Ji, Y.; Luo, B. Reversible data hiding in JPEG images with multi-objective optimization. IEEE Trans. Circuits Syst. Video Technol. 2020, 30, 2343–2352. [Google Scholar]
- Xiao, M.; Li, X.; Ma, B.; Zhang, X.; Zhao, Y. Efficient reversible data hiding for JPEG images with multiple histograms modification. IEEE Trans. Circuits Syst. Video Technol. 2021, 31, 2535–2546. [Google Scholar] [CrossRef]
- Qiu, Y.; Qian, Z.; He, H.; Tian, H.; Zhang, X. Optimized lossless data hiding in JPEG bitstream and relay transfer-based extension. IEEE Trans. Circuits Syst. Video Technol. 2021, 31, 1380–1394. [Google Scholar] [CrossRef]
- Du, Y.; Yin, Z.; Zhang, X. High capacity lossless data hiding in JPEG bitstream based on general VLC mapping. IEEE Trans. Dependable Secur. Comput. 2022, 19, 1420–1433. [Google Scholar] [CrossRef]
- Weng, S.; Zhang, T. Adaptive reversible data hiding for JPEG images with multiple two-dimensional histograms. J. Vis. Commun. Image Represent. 2022, 85, 103487. [Google Scholar] [CrossRef]
- Yu, C.; Cheng, S.; Zhang, X.; Zhang, X.; Tang, Z. Reversible Data Hiding in Shared JPEG Images. ACM Trans. Multimed. Comput. Commun. Appl. 2024, 20, 1–24. [Google Scholar] [CrossRef]
- Yang, X.; Wang, Y.; Huang, F. CNN-Based Reversible Data Hiding for JPEG Images. IEEE Trans. Circuits Syst. Video Technol. 2024, 34, 11798–11809. [Google Scholar] [CrossRef]
- Lyu, W.-L.; Cheng, L.; Yin, Z. High-capacity reversible data hiding in encrypted 3D mesh models based on multi-MSB prediction. Signal Process. 2022, 201, 108686. [Google Scholar] [CrossRef]
- Peng, F.; Liao, T.; Long, M. A semi-fragile reversible watermarking for authenticating 3D models in dual domains based on variable direction double modulation. IEEE Trans. Circuits Syst. Video Technol. 2022, 32, 8394–8408. [Google Scholar] [CrossRef]
- Qu, L.; Lu, H.; Chen, P.; Amirpour, H.; Timmerer, C. Ring Co-XOR encryption based reversible data hiding for 3D mesh model. Signal Process. 2024, 217, 109357. [Google Scholar] [CrossRef]
- Wu, H.-T.; Cao, X.; Jia, R.; Cheung, Y.-M. Reversible data hiding with brightness preserving contrast enhancement by two-dimensional histogram modification. IEEE Trans. Circuits Syst. Video Technol. 2022, 32, 7605–7617. [Google Scholar] [CrossRef]
- Zhang, T.-C.; Hou, T.-S.; Weng, S.-W.; Zou, F.-M.; Zhang, H.-C.; Chang, C.-C. Adaptive reversible data hiding with contrast enhancement based on multi-histogram modification. IEEE Trans. Circuits Syst. Video Technol. 2022, 32, 5041–5054. [Google Scholar] [CrossRef]
- Qi, W.; Guo, S.; Hu, W. Generic reversible visible watermarking via regularized graph fourier transform coding. IEEE Trans. Image Process. 2022, 31, 691–705. [Google Scholar] [CrossRef] [PubMed]
- Tang, X.; Wang, H.; Chen, Y. Reversible data hiding based on a modified difference expansion for H.264/AVC video streams. Multimed. Tools Appl. 2020, 79, 28661–28674. [Google Scholar] [CrossRef]
- Xu, D.; Liu, Y. Reversible data hiding in H.264/AVC videos based on hybrid-dimensional histogram modification. Multimed. Tools Appl. 2022, 81, 29305–29319. [Google Scholar] [CrossRef]
- Yang, Y.; Zou, T.; Huang, G.; Zhang, W. A high visual quality color image reversible data hiding scheme based on B-R-G embedding principle and CIEDE2000 assessment metric. IEEE Trans. Circuits Syst. Video Technol. 2022, 32, 1860–1874. [Google Scholar] [CrossRef]
- Zhang, C.; Ou, B.; Li, X.; Xiong, J. Human visual system guided reversible data hiding based on multiple histograms modification. Comput. J. 2023, 66, 888–906. [Google Scholar] [CrossRef]
- The USC-SIPI Image Database, Miscellaneous. Available online: http://sipi.usc.edu/database/database.php?volume=misc (accessed on 11 October 2024).
- Miscelaneous Gray Level Images (512 × 512). Available online: http://decsai.ugr.es/cvg/dbimagenes/g512.php (accessed on 11 October 2024).
- Kodak Lossless True Color Image Suite. Available online: http://r0k.us/graphics/kodak/ (accessed on 18 March 2024).

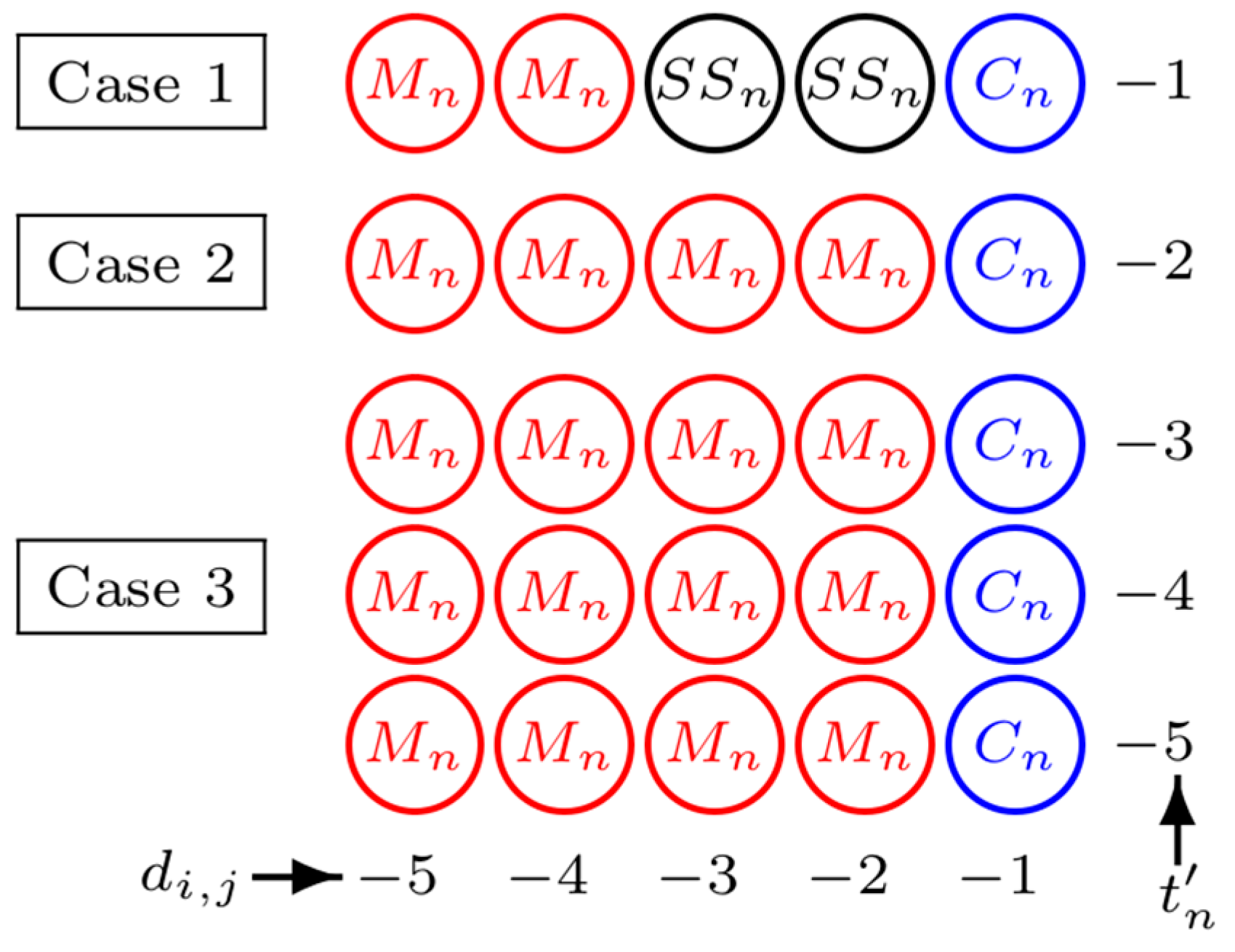


| Criteria | Proposed Method | SMT [16,21,23] | DMT [17,19,26] |
|---|---|---|---|
| Location Map Size | Smaller or may not be required | Requires compression | Very small or not needed |
| Overflow/Underflow Handling | Effectively minimizes issues | Excludes problematic pixels | Encounters issues with extreme values |
| Embedding Efficiency | Higher due to reduced overhead | Limited by excluded pixels | Affected by second modification |
| Computational Complexity | Moderate | Low | High |
| Need for Compression Tool | Not required | Required | Not required for non-extreme images |
| Performance on Images with Extreme Intensity Values | More stable | Avoids modification of critical pixels | Faces significant issues |
| PSNR (dB) | ||||||||
|---|---|---|---|---|---|---|---|---|
| 0.2 BPP | 0.8 BPP | |||||||
| Image | Ours | [17] | [21] | [23] | Ours | [17] | [21] | [23] |
| Lena | 50.81 | 50.50 | 50.44 | 50.80 | 38.76 | 38.16 | 37.64 | 38.45 |
| Barbara | 49.71 | 48.52 | 49.17 | 49.43 | 35.03 | 33.73 | 31.17 | 32.07 |
| Baboon | 41.72 | 41.58 | 40.98 | 41.43 | 27.14 | 26.30 | 23.80 | 26.07 |
| Peppers | 48.90 | 45.63 | 49.11 | 47.02 | 36.87 | 33.73 | 36.81 | 35.49 |
| Sailboat | 47.75 | 45.23 | 47.85 | 46.21 | 33.32 | 31.66 | 32.72 | 32.78 |
| Fishing boat | 46.71 | 45.57 | 45.94 | 46.19 | 35.16 | 33.24 | 33.50 | 33.82 |
| Elaine | 45.94 | 44.52 | 45.61 | 45.34 | 34.01 | 31.01 | 33.58 | 32.69 |
| Airplane(F-16) | 54.34 | 53.20 | 53.95 | 54.29 | 41.18 | 40.94 | 39.25 | 40.42 |
| Grass(D9) | 37.58 | 35.47 | 32.03 | 32.74 | - | - | - | - |
| Car and APCs | 47.45 | 46.95 | 46.55 | 45.90 | 36.77 | 36.71 | 35.18 | 35.48 |
| Sand | 45.95 | 44.34 | 41.49 | 42.97 | 32.26 | 31.71 | - | - |
| Tiffany | 51.41 | 51.09 | 51.25 | 48.46 | 38.61 | 37.78 | 37.26 | - |
| Man | 50.98 | 50.66 | 48.97 | 36.83 | 34.88 | 35.37 | 30.89 | - |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Panyindee, C. Infimum and Supremum of Thresholds for Reversible Data Hiding. Electronics 2025, 14, 1017. https://doi.org/10.3390/electronics14051017
Panyindee C. Infimum and Supremum of Thresholds for Reversible Data Hiding. Electronics. 2025; 14(5):1017. https://doi.org/10.3390/electronics14051017
Chicago/Turabian StylePanyindee, Chaiyaporn. 2025. "Infimum and Supremum of Thresholds for Reversible Data Hiding" Electronics 14, no. 5: 1017. https://doi.org/10.3390/electronics14051017
APA StylePanyindee, C. (2025). Infimum and Supremum of Thresholds for Reversible Data Hiding. Electronics, 14(5), 1017. https://doi.org/10.3390/electronics14051017






