A Distributed Trustable Framework for AI-Aided Anomaly Detection †
Abstract
1. Introduction
1.1. Contributions
- •
- We present and discuss DTE’s architecture and its building blocks, supporting data collection and management, AI/ML model training and deployment, and anomaly detection in accordance with NWDAF specifications.
- •
- To strengthen the privacy level across distributed 6G environments and avoid the drawbacks of centralized ML, an FL extension for DTE’s architecture is analyzed.
- •
- The attack classification accuracy of AI/ML-aided anomaly detection is thoroughly evaluated, providing, in detail, an ML model training framework to overcome dimensionality issues of datasets with a high number of features. For this purpose, we analyze and use two open datasets from diverse cyberattacks in the core and edge parts of the network and discuss the performance-complexity trade-off of different ML algorithms.
1.2. Structure
2. ML-Aided Anomaly Detection Review
2.1. Attack Types in 6G Networks
- Spoofing identity involves illegal access and the use of another user’s authentication information, such as the username and password.
- Tampering with data focuses on malicious data modification, including data alteration as it flows between two computers over the Internet and unauthorized changes to persistent data residing in a database.
- Repudiation threats are related to users who deny performing an action while, at the same time, other parties are not able to prove otherwise. For example, in this case, a user can perform an illegal operation in a system that is unable to trace the prohibited operations.
- Information disclosure includes information exposure of individuals who should not have access to it. More specifically, unauthorized users might access a file that they were not granted access to, or an intruder might read data transmitted between two devices.
- Denial-of-service attacks resulting in instances where valid users are denied requested services, e.g., by rendering a Web server temporarily unavailable or unusable.
- Elevation of privilege, where an unprivileged user obtains privileged access and threatens to compromise or destroy the entire system. An illustrative example involves an attacker that has penetrated through all system defenses, becoming part of the trusted system.
2.2. AI/ML-Aided Anomaly Detection
3. Distributed Trustable Engine Architecture
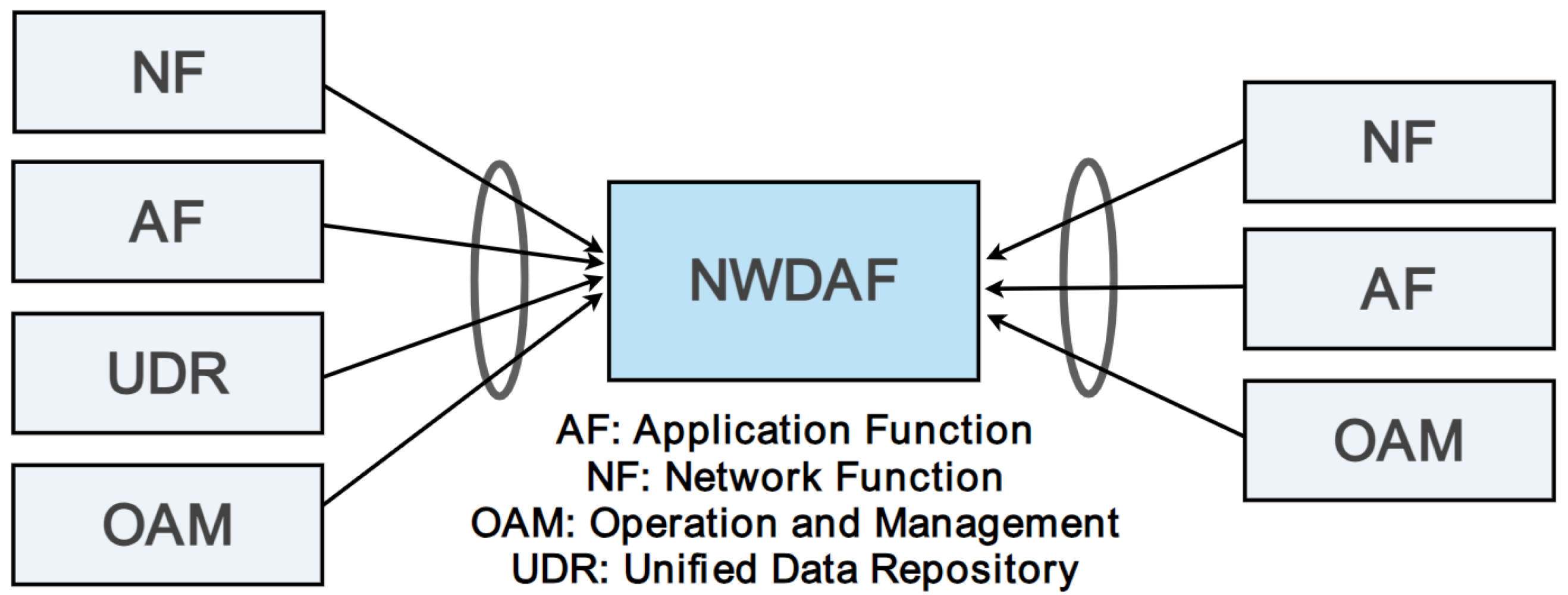
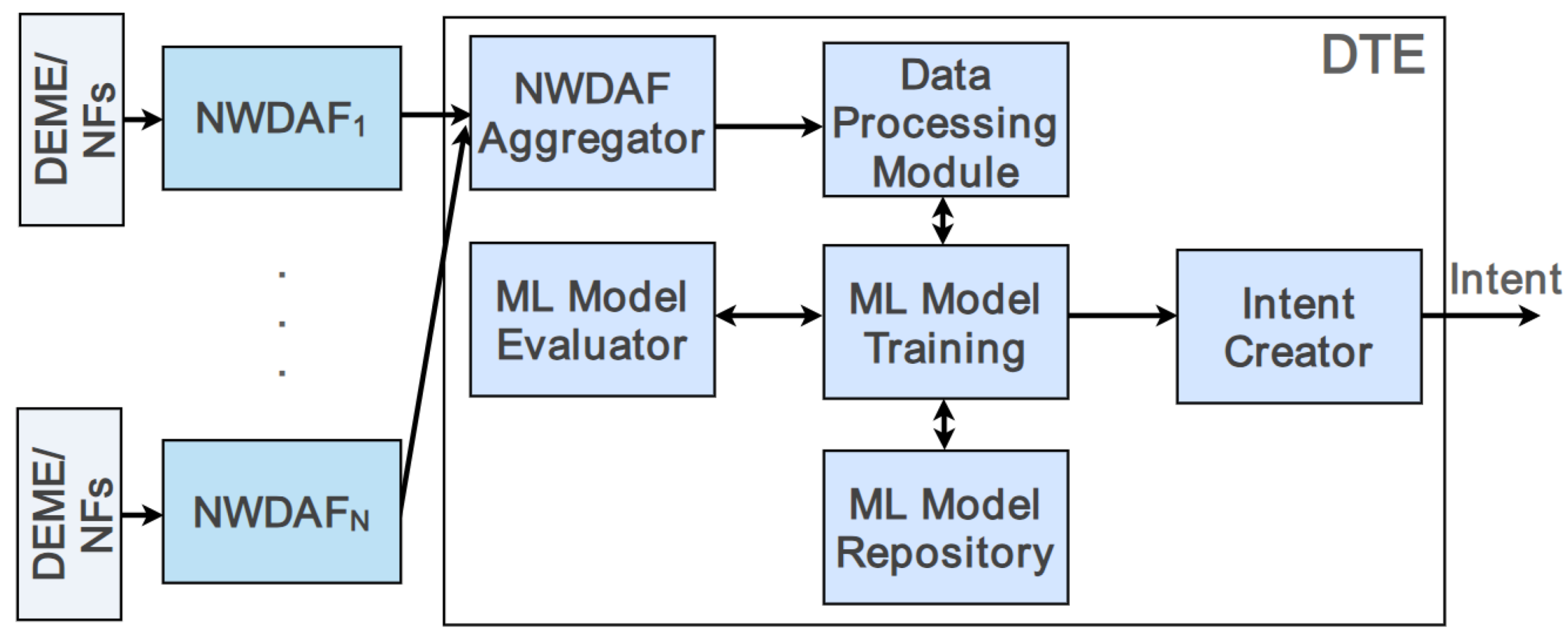
3.1. The Role of the DTE
3.2. Internal DTE Components
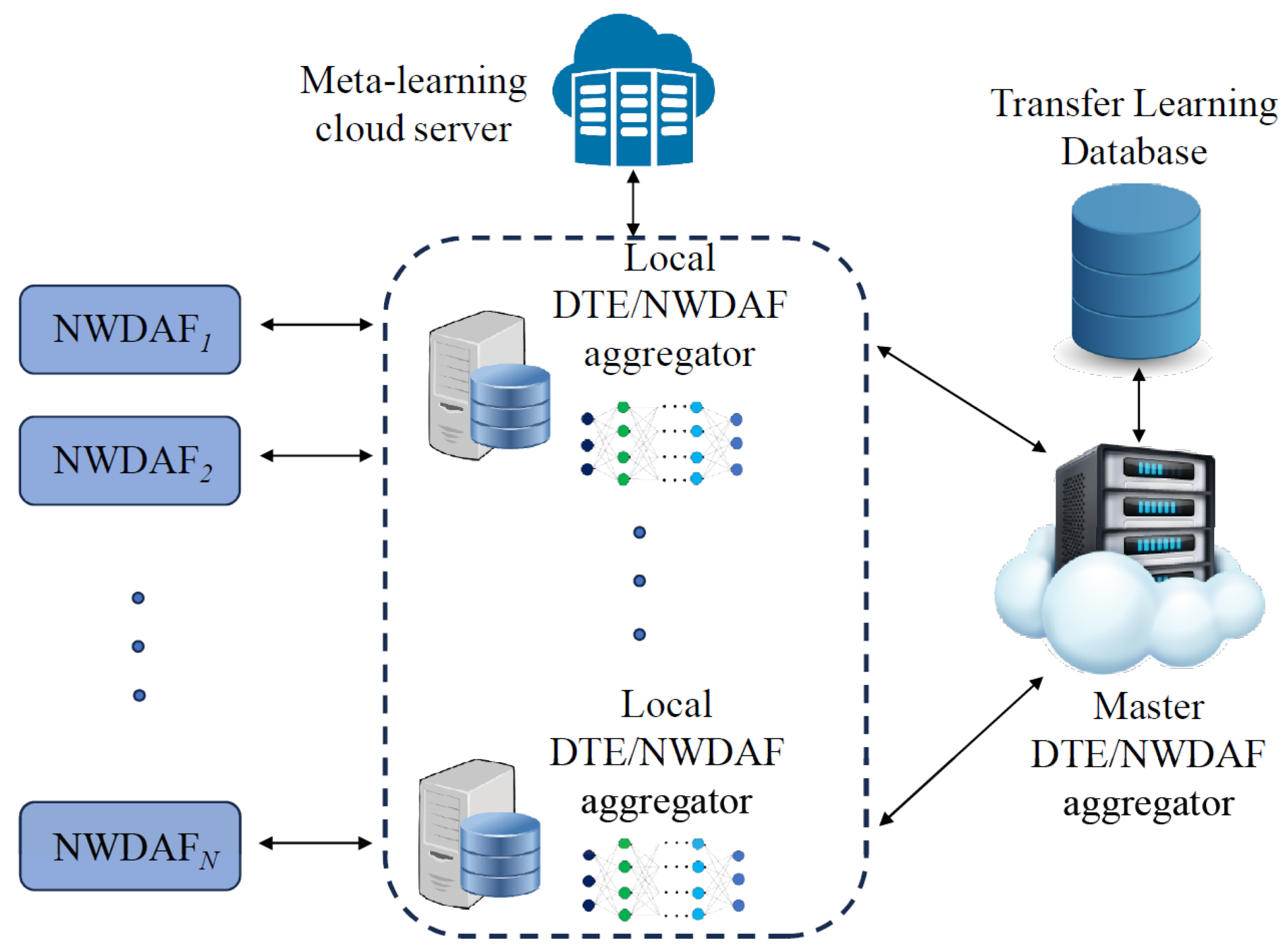
3.3. Federated DTE Architecture
4. Performance Evaluation
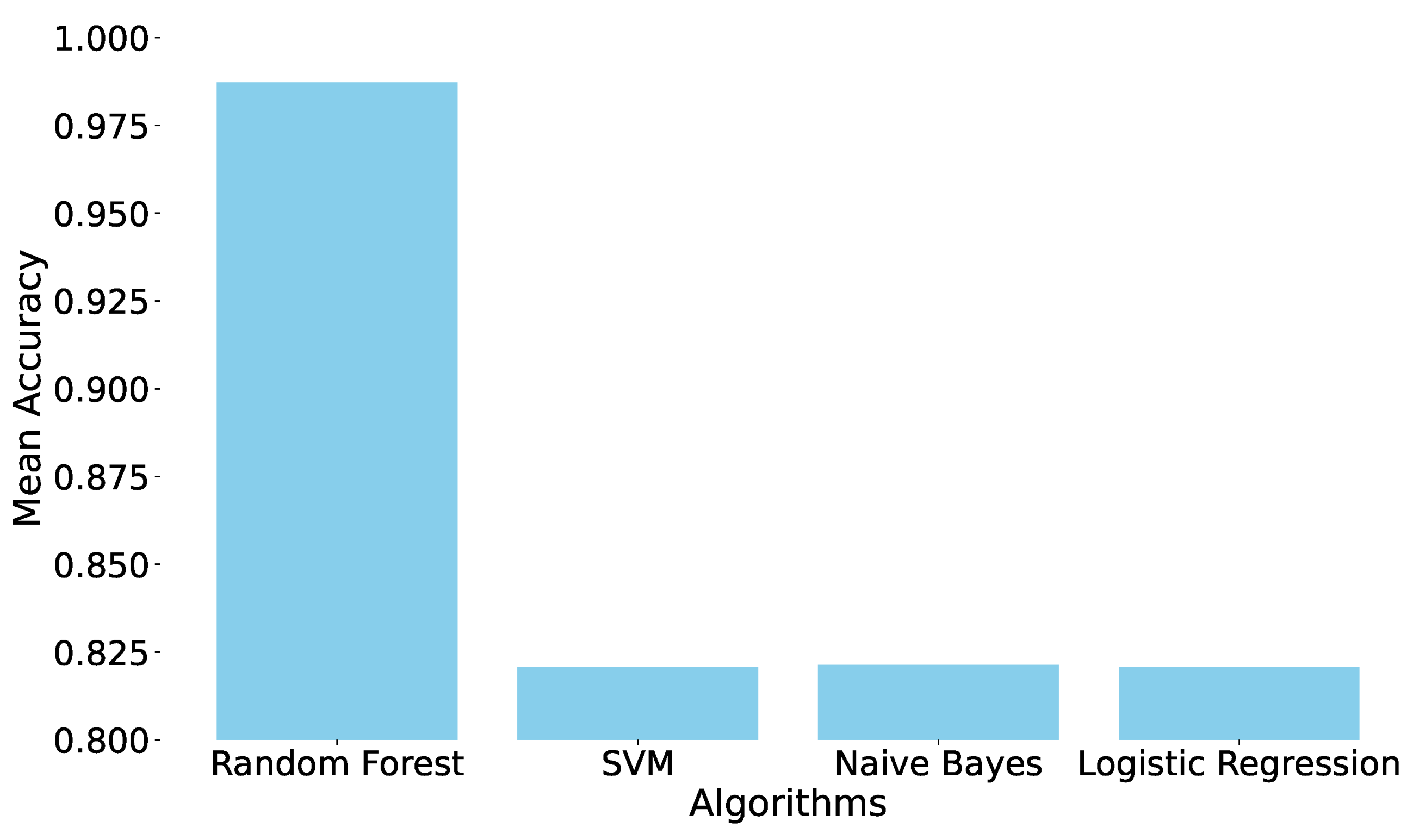
4.1. Core Network Attacks
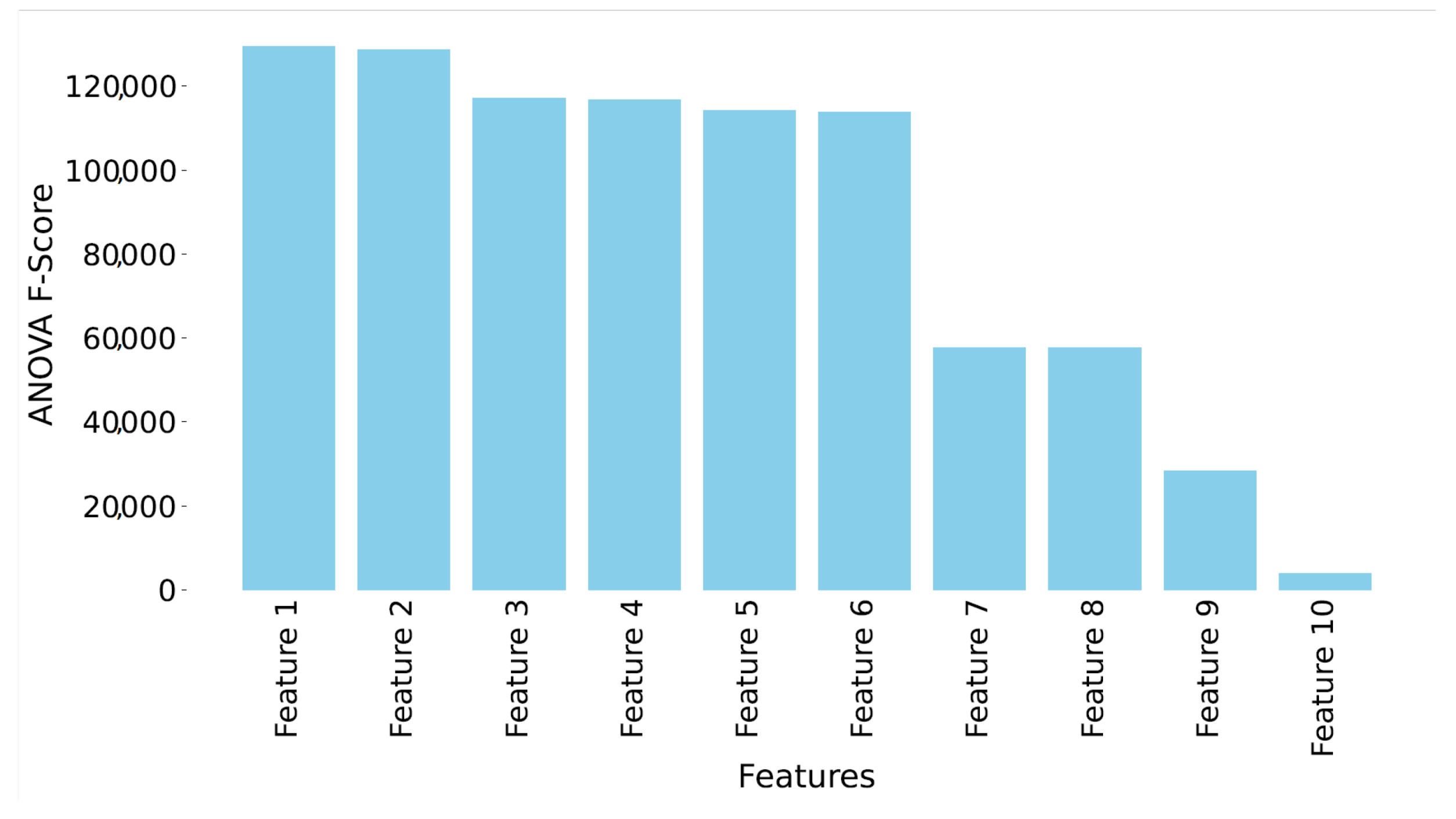
- Feature 1: Number of PFCP session modification request messages.
- Feature 2: Number of PFCP session modification response messages.
- Feature 3: Number of PFCP session establishment response messages.
- Feature 4: Number of PFCP session establishment request messages.
- Feature 5: Number of PFCP heartbeat request messages.
- Feature 6: Number of PFCP heartbeat response messages.
- Feature 7: Number of forwarding packets.
- Feature 8: Number of backward packets.
- Feature 9: Number of PFCP session deletion response messages.
- Feature 10: Duration of an active flow.
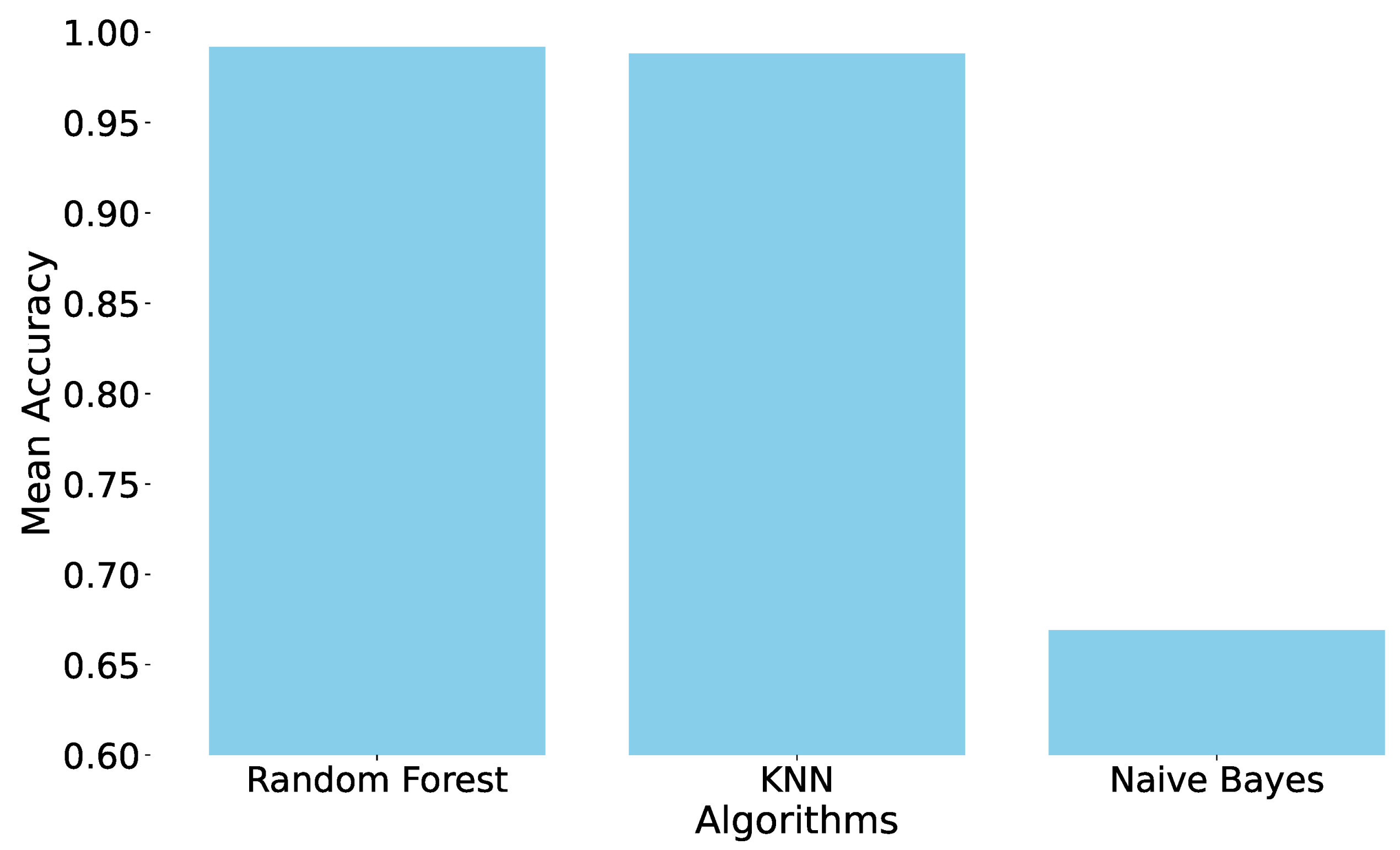
4.2. DDoS Edge Attacks
- ICMP Flood (1115 samples).
- HTTP Flood (140,812 samples).
- Slow Rate DDoS (73,124 samples).
- SYN Flood (9721 samples).
- SYN Scan (20,043 samples).
- TCP Connect Scan (20,052 samples).
- UDP Flood (457,340 samples).
- UDP Scan (15,906 samples).
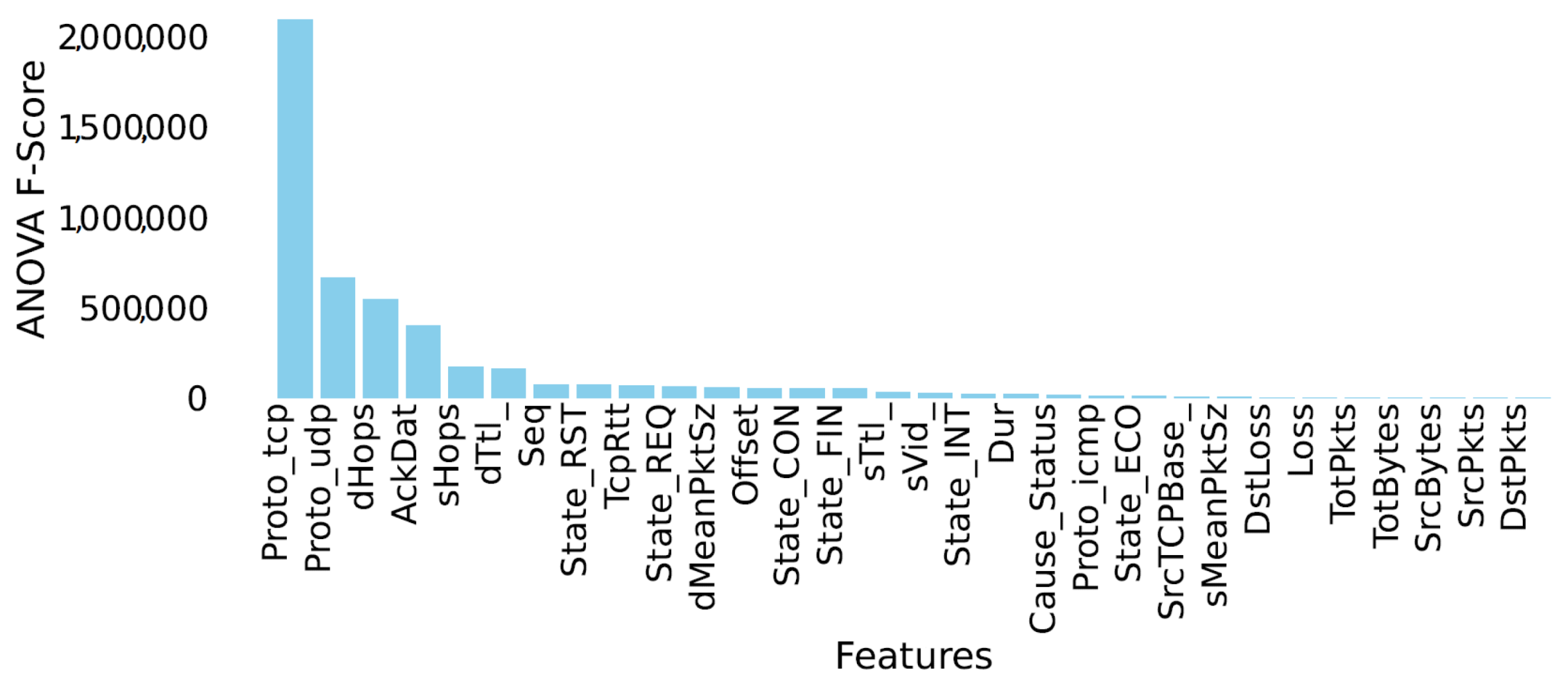
- Proto_tcp: TCP protocol is used.
- Proto_udp: UDP protocol is used.
- dHops: Estimation of the number of IP hops from the destination to this point.
- Ackdat: TCP connection setup time, the time between the SYN_ACK and the ACK packets.
- sHops: Estimation of the number of IP hops from the source to this point.
- dttl: Destination-to-source time to live (TTL) value.
- Seq: argus sequence number.
- State_RST: Indication of the principle state for the transaction report, being protocol dependent. For TCP connections, this is “RST”, i.e., a connection is reset.
- Tcprtt: TCP connection set up round-trip time, the sum of “synack” and “ackdat”.
- State_REQ: For TCP connections, this is denoted as “REQ”, indicating that a connection is being requested.
5. Conclusions and Future Directions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| 3GPP | Third generation partnership project |
| 5G | Fifth generation |
| 6G | Sixth generation |
| AI/ML | Artificial intelligence/Machine learning |
| ANOVA | Analysis of variance |
| DDoS | Distributed denial-of-service |
| DEME | Detector and mitigation engine |
| DL | Deep learning |
| DRL | Deep reinforcement learning |
| DTE | Distributed trustable engine |
| FL | Federated learning |
| GAN | Generative adversarial network |
| HORSE | Holistic, omnipresent, resilient services |
| IBI | Intent-based interface |
| K-NN | K-nearest neighbors |
| LR | Logistic regression |
| MEC | Multi-access edge |
| NF | Network function |
| NFV | Network function virtualization |
| NIDD | Network intrusion detection dataset |
| NWDAF | Network data analytics function |
| PFCP | Packet forwarding control protocol |
| PKI | Public key infrastructure |
| QoS | Quality-of-service |
| RF | Random forest |
| RL | Reinforcement learning |
| SMF | Session management function |
| SNS JU | Smart Networks and Services Joint Undertaking |
| TTL | Time-to-live |
| UPF | User plane function |
| ZTA | Zero trust architecture |
References
- Duan, X.D.; Wang, X.Y.; Lu, L.; Shi, N.X.; Liu, C.; Zhang, T.; Sun, T. 6G Architecture Design: From Overall, Logical and Networking Perspective. IEEE Commun. Mag. 2023, 61, 158–164. [Google Scholar] [CrossRef]
- Nomikos, N.; Poulimeneas, D.; Charalambous, T.; Krikidis, I.; Vouyioukas, D.; Johansson, M. Delay- and Diversity-Aware Buffer-Aided Relay Selection Policies in Cooperative Networks. IEEE Access 2018, 6, 73531–73547. [Google Scholar] [CrossRef]
- Kaloxylos, A.; Gavras, A.; Camps, D.; Ghoraishi, M.; Hrasnica, H. AI and ML–Enablers for beyond 5G Networks. 5G PPP Technol. Board 2021. [Google Scholar] [CrossRef]
- 3GPP. 3GPP SA 6G Planning and Progress Update. 2024. Available online: https://www.3gpp.org/ftp/Information/presentations/Presentations_2024/03_2024_09_17_Puneet_v03.pdf (accessed on 4 December 2024).
- Alhussien, N.; Aaron Gulliver, T. Toward AI-Enabled Green 6G Networks: A Resource Management Perspective. IEEE Access 2024, 12, 132972–132995. [Google Scholar] [CrossRef]
- Xu, Q.; Su, Z.; Li, R. Security and Privacy in Artificial Intelligence-Enabled 6G. IEEE Netw. 2022, 36, 188–196. [Google Scholar] [CrossRef]
- Je, D.; Jung, J.; Choi, S. Toward 6G Security: Technology Trends, Threats, and Solutions. IEEE Commun. Stand. Mag. 2021, 5, 64–71. [Google Scholar] [CrossRef]
- Mao, B.; Liu, J.; Wu, Y.; Kato, N. Security and Privacy on 6G Network Edge: A Survey. IEEE Commun. Surv. Tutor. 2023, 25, 1095–1127. [Google Scholar] [CrossRef]
- Kumar Korrai, P.; Lagunas, E.; Krishna Sharma, S.; Chatzinotas, S. Dynamic Resource Assignment for Heterogeneous Services in 5G Downlink Under Imperfect CSI. In Proceedings of the 2021 IEEE 93rd Vehicular Technology Conference (VTC2021-Spring), Virtual, 25 April–19 May 2021; pp. 1–7. [Google Scholar] [CrossRef]
- Hossain, M.A.; Hossain, A.R.; Ansari, N. AI in 6G: Energy-Efficient Distributed Machine Learning for Multilayer Heterogeneous Networks. IEEE Netw. 2022, 36, 84–91. [Google Scholar] [CrossRef]
- Khan, L.U.; Saad, W.; Niyato, D.; Han, Z.; Hong, C.S. Digital-Twin-Enabled 6G: Vision, Architectural Trends, and Future Directions. IEEE Commun. Mag. 2022, 60, 74–80. [Google Scholar] [CrossRef]
- You, S.D.; Liu, H.C.; Liu, C.H. Predicting Classification Accuracy of Unlabeled Datasets Using Multiple Deep Neural Networks. IEEE Access 2022, 10, 44627–44637. [Google Scholar] [CrossRef]
- Nomikos, N.; Talebi, M.S.; Charalambous, T.; Wichman, R. Bandit-Based Power Control in Full-Duplex Cooperative Relay Networks With Strict-Sense Stationary and Non-Stationary Wireless Communication Channels. IEEE Open J. Commun. Soc. 2022, 3, 366–378. [Google Scholar] [CrossRef]
- Li, T.; Sahu, A.K.; Talwalkar, A.; Smith, V. Federated Learning: Challenges, Methods, and Future Directions. IEEE Signal Process. Mag. 2020, 37, 50–60. [Google Scholar] [CrossRef]
- Giannopoulos, A.E.; Spantideas, S.T.; Zetas, M.; Nomikos, N.; Trakadas, P. FedShip: Federated Over-the-Air Learning for Communication-Efficient and Privacy-Aware Smart Shipping in 6G Communications. IEEE Trans. Intell. Transp. Syst. 2024, 25, 19873–19888. [Google Scholar] [CrossRef]
- 3GPP. TS 29.520, Network Data Analytics Services; Release 15 2019. Available online: https://www.etsi.org/deliver/etsi_ts/129500_129599/129520/15.03.00_60/ts_129520v150300p.pdf (accessed on 1 December 2024).
- Shen, S.; Yu, C.; Zhang, K.; Ni, J.; Ci, S. Adaptive and Dynamic Security in AI-Empowered 6G: From an Energy Efficiency Perspective. IEEE Commun. Stand. Mag. 2021, 5, 80–88. [Google Scholar] [CrossRef]
- 3GPP. 3GPP TR 33.926: Security Assurance Specification (SCAS) Threats and Critical Assets in 3GPP Network Product Classes (Release 18). 2023. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3002 (accessed on 1 December 2024).
- Dutta, I.K.; Ghosh, B.; Carlson, A.; Totaro, M.; Bayoumi, M. Generative Adversarial Networks in Security: A Survey. In Proceedings of the 2020 11th IEEE Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), Virtual, 28–31 October 2020; pp. 399–405. [Google Scholar] [CrossRef]
- Dixit, P.; Silakari, S. Deep Learning Algorithms for Cybersecurity Applications: A Technological and Status Review. Comput. Sci. Rev. 2021, 39, 100317. [Google Scholar] [CrossRef]
- Spantideas, S.; Giannopoulos, A.; Cambeiro, M.A.; Trullols-Cruces, O.; Atxutegi, E.; Trakadas, P. Intelligent Mission Critical Services over Beyond 5G Networks: Control Loop and Proactive Overload Detection. In Proceedings of the 2023 International Conference on Smart Applications, Communications and Networking (SmartNets), Istanbul, Türkiye, 25–27 July 2023; pp. 1–6. [Google Scholar]
- Jayasinghe, S.; Siriwardhana, Y.; Porambage, P.; Liyanage, M.; Ylianttila, M. Federated Learning based Anomaly Detection as an Enabler for Securing Network and Service Management Automation in Beyond 5G Networks. In Proceedings of the 2022 Joint European Conference on Networks and Communications & 6G Summit (EuCNC/6G Summit), Grenoble, France, 6–10 June 2022; pp. 345–350. [Google Scholar] [CrossRef]
- Sedjelmaci, H.; Kheir, N.; Boudguiga, A.; Kaaniche, N. Cooperative and smart attacks detection systems in 6G-enabled Internet of Things. In Proceedings of the ICC 2022-IEEE International Conference on Communications, Seoul, Republic of Korea, 16–20 May 2022; pp. 5238–5243. [Google Scholar] [CrossRef]
- Gkonis, P.; Nomikos, N.; Trakadas, P.; Sarakis, L.; Xylouris, G.; Masip-Bruin, X.; Martrat, J. Leveraging Network Data Analytics Function and Machine Learning for Data Collection, Resource Optimization, Security and Privacy in 6G Networks. IEEE Access 2024, 12, 21320–21336. [Google Scholar] [CrossRef]
- Yuan, Y.; Gehrmann, C.; Sternby, J.; Barriga, L. Insight of Anomaly Detection with NWDAF in 5G. In Proceedings of the 2022 International Conference on Computer, Information and Telecommunication Systems (CITS), Athens, Greece, 13–15 July 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Sevgican, S.; Turan, M.; Gökarslan, K.; Yilmaz, H.B.; Tugcu, T. Intelligent network data analytics function in 5G cellular networks using machine learning. J. Commun. Netw. 2020, 22, 269–280. [Google Scholar] [CrossRef]
- Liu, G.; Zhou, J.; Su, H.; Xiong, B.; Niu, X. Energy Conserved Failure Detection for NS-IoT Systems. In Proceedings of the 2024 IEEE Wireless Communications and Networking Conference (WCNC), Dubai, United Arab Emirates, 21–24 April 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Zhou, C.; Ansari, N. Securing Federated Learning Enabled NWDAF Architecture with Partial Homomorphic Encryption. IEEE Netw. Lett. 2023, 5, 299–303. [Google Scholar] [CrossRef]
- Rajabzadeh, P.; Outtagarts, A. Feedback-Driven Federated Learning for Distributed NWDAFs in 5G Core. In Proceedings of the 2024 IEEE 25th International Conference on High Performance Switching and Routing (HPSR), Pisa, Italy, 22–24 July 2024; pp. 106–111. [Google Scholar] [CrossRef]
- Zhang, W.; Sun, C.; Wang, X.; Li, L.; Cui, T.; Li, H. 5GC Enabled Lightweight Federated Learning under Communication Quality Constraint. In Proceedings of the 2024 IEEE/CIC International Conference on Communications in China (ICCC), Hangzhou, China, 7–9 August 2024; pp. 1633–1638. [Google Scholar] [CrossRef]
- SNS-JU. Holistic, Omnipresent, Resilient Services (HORSE) for Future 6G Wireless and Computing Ecosystems 2023. Available online: https://horse-6g.eu/ (accessed on 1 December 2024).
- Hu, S.; Chen, X.; Ni, W.; Hossain, E.; Wang, X. Distributed Machine Learning for Wireless Communication Networks: Techniques, Architectures, and Applications. IEEE Commun. Surv. Tutor. 2021, 23, 1458–1493. [Google Scholar] [CrossRef]
- Zhou, P.; Lin, Q.; Loghin, D.; Ooi, B.C.; Wu, Y.; Yu, H. Communication-efficient Decentralized Machine Learning over Heterogeneous Networks. In Proceedings of the 2021 IEEE 37th International Conference on Data Engineering (ICDE), Chania, Greece, 19–22 April 2021; pp. 384–395. [Google Scholar] [CrossRef]
- Tan, A.Z.; Yu, H.; Cui, L.; Yang, Q. Towards Personalized Federated Learning. IEEE Trans. Neural Netw. Learn. Syst. 2022, 34, 9587–9603. [Google Scholar] [CrossRef]
- Amponis, G.; Radoglou-Grammatikis, P.; Nakas, G.; Zevgara, M.; Giannakidou, S.; Ouzounidis, S.; Kakamoukas, G.; Sarigiannidis, A. 5GC PFCP Intrusion Detection Dataset. IEEE Dataport 2023. [Google Scholar] [CrossRef]
- Samarakoon, S.; Siriwardhana, Y.; Porambage, P.; Liyanage, M.; Chang, S.Y.; Kim, J.; Kim, J.; Ylianttila, M. 5G-NIDD: A Comprehensive Network Intrusion Detection Dataset Generated over 5G Wireless Network. IEEE Dataport 2022. [Google Scholar] [CrossRef]
- Elssied, N.O.F.; Ibrahim, O.; Osman, A.H. A novel feature selection based on one-way anova f-test for e-mail spam classification. Res. J. Appl. Sci. Eng. Technol. 2014, 7, 625–638. [Google Scholar] [CrossRef]
- Nomikos, N.; Giannopoulos, A.; Trakadas, P.; Karagiannidis, G.K. Uplink NOMA for UAV-Aided Maritime Internet-of-Things. In Proceedings of the 2023 19th International Conference on the Design of Reliable Communication Networks (DRCN), Vilanova i la Geltru, Spain, 17–20 April 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Zamanzadeh Darban, Z.; Webb, G.I.; Pan, S.; Aggarwal, C.; Salehi, M. Deep Learning for Time Series Anomaly Detection: A Survey. ACM Comput. Surv. 2024, 57. [Google Scholar] [CrossRef]
- Xiao, C.; Pang, S.; Xu, X.; Li, X.; Trajcevski, G.; Zhou, F. Counterfactual Data Augmentation With Denoising Diffusion for Graph Anomaly Detection. IEEE Trans. Comput. Soc. Syst. 2024, 11, 7555–7567. [Google Scholar] [CrossRef]
- Xiao, C.; Gou, Z.; Tai, W.; Zhang, K.; Zhou, F. Imputation-based Time-Series Anomaly Detection with Conditional Weight-Incremental Diffusion Models. In Proceedings of the KDD’ 23 29th ACM SIGKDD Conference on Knowledge Discovery and Data Mining, New York, NY, USA, 6–10 August 2023; pp. 2742–2751. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Nomikos, N.; Xylouris, G.; Patsourakis, G.; Nikolakakis, V.; Giannopoulos, A.; Mandilaris, C.; Gkonis, P.; Skianis, C.; Trakadas, P. A Distributed Trustable Framework for AI-Aided Anomaly Detection. Electronics 2025, 14, 410. https://doi.org/10.3390/electronics14030410
Nomikos N, Xylouris G, Patsourakis G, Nikolakakis V, Giannopoulos A, Mandilaris C, Gkonis P, Skianis C, Trakadas P. A Distributed Trustable Framework for AI-Aided Anomaly Detection. Electronics. 2025; 14(3):410. https://doi.org/10.3390/electronics14030410
Chicago/Turabian StyleNomikos, Nikolaos, George Xylouris, Gerasimos Patsourakis, Vasileios Nikolakakis, Anastasios Giannopoulos, Charilaos Mandilaris, Panagiotis Gkonis, Charalabos Skianis, and Panagiotis Trakadas. 2025. "A Distributed Trustable Framework for AI-Aided Anomaly Detection" Electronics 14, no. 3: 410. https://doi.org/10.3390/electronics14030410
APA StyleNomikos, N., Xylouris, G., Patsourakis, G., Nikolakakis, V., Giannopoulos, A., Mandilaris, C., Gkonis, P., Skianis, C., & Trakadas, P. (2025). A Distributed Trustable Framework for AI-Aided Anomaly Detection. Electronics, 14(3), 410. https://doi.org/10.3390/electronics14030410










