Emulation-Based Analysis of Multiple Cell Upsets in LEON3 SDRAM: A Workload-Dependent Vulnerability Study
Abstract
1. Introduction
- −
- Matrix multiplication (arithmetic- and memory-intensive),
- −
- FFT (iterative, alignment-sensitive signal processing), and
- −
- AES-128 (control-intensive, security-critical cryptographic kernel).
2. Related Work
3. MCU Fault Injection Methodology on SDRAM LEON3
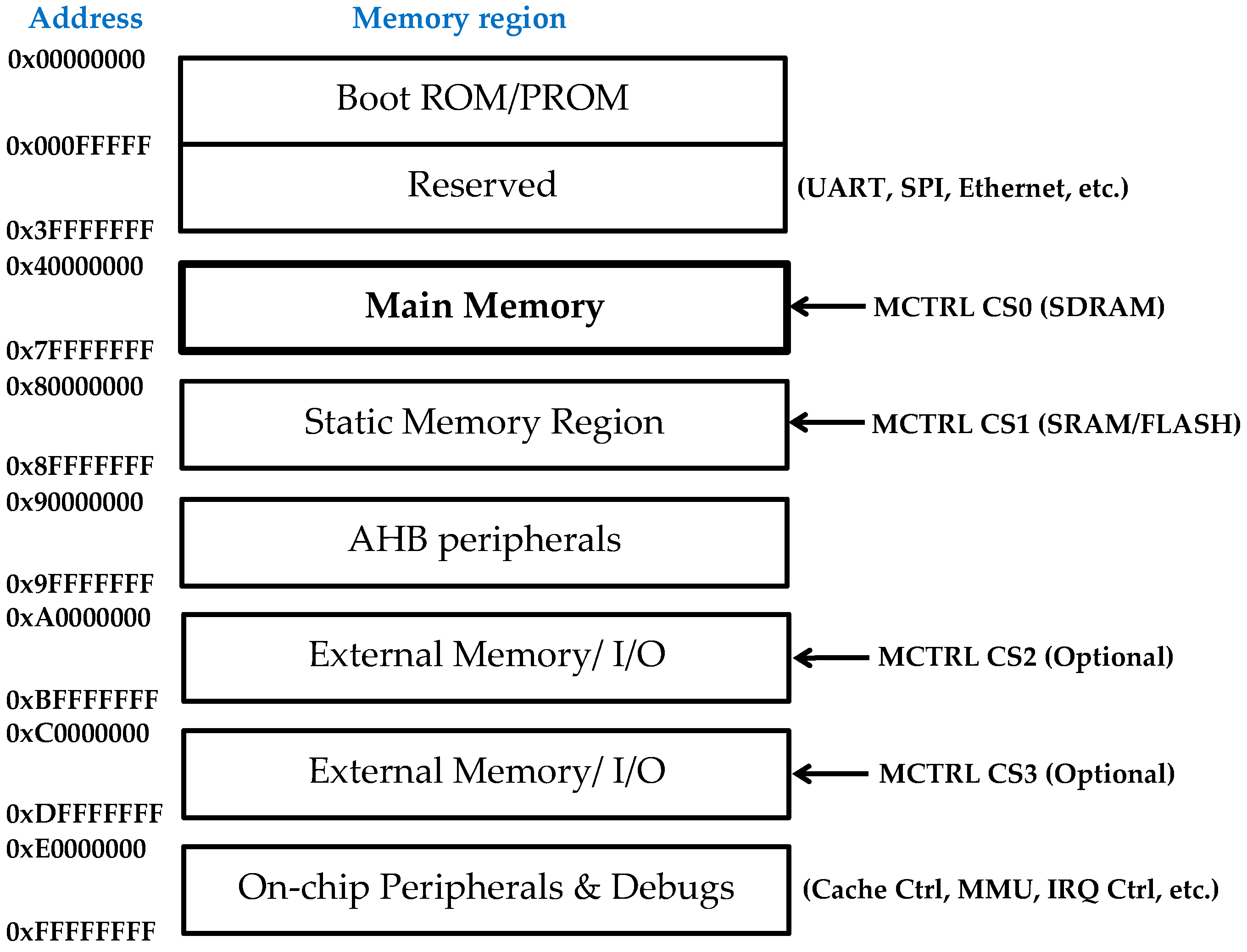
3.1. The LEON3 Soft-Core Processor and Its SDRAM Subsystem as a Case Study
- Instruction and data caches, typically configurable between 1 KB and 64 KB, implemented using FPGA block RAMs (BRAMs). These accelerate memory access by storing recently used instructions and data.
- Register file, holding general-purpose and control registers, implemented as SRAM-based structures in FPGA realizations.
- Scratchpad or tightly coupled memories (TCMs), optional on-chip SRAM memories used for deterministic data access in real-time or safety-critical applications.
- External memory subsystem, managed by the LEON3 memory controller (MCTRL), which supports several memory devices such as SRAM, PROM, and SDRAM.
3.2. Benhchmark Selection
- Matrix Multiplication (30 × 30 character-type matrices): an arithmetic- and memory-intensive workload that stresses sustained data movement and compute density. This benchmark is representative of numerical kernels in aerospace, scientific computing, and real-time control systems. In this benchmark, intermediate matrix elements are stored in SDRAM and repeatedly retrieved during computation, making the memory subsystem the dominant source of vulnerability.
- Fast Fourier Transform (FFT): a signal-processing workload characterized by iterative feedback, regular memory access patterns, and high sensitivity to address alignment. FFT is widely used in radar, communications, and sensor signal processing, where small perturbations can significantly alter output integrity. Even minor errors in intermediate results can propagate rapidly through the computation pipeline, making FFT an effective vehicle for exposing error propagation mechanisms.
- AES-128 encryption: a control-intensive, security-critical workload that stresses control logic, stateful round-based execution, and irregular memory access patterns through lookup tables (S-boxes). As a cryptographic standard in secure communications, AES is highly sensitive to data corruption, even single-bit errors in key schedule or state arrays can compromise correctness and enable fault-based attacks [52]. Both the key schedule and state arrays reside in SDRAM during execution, directly exposing security-critical data to memory faults.
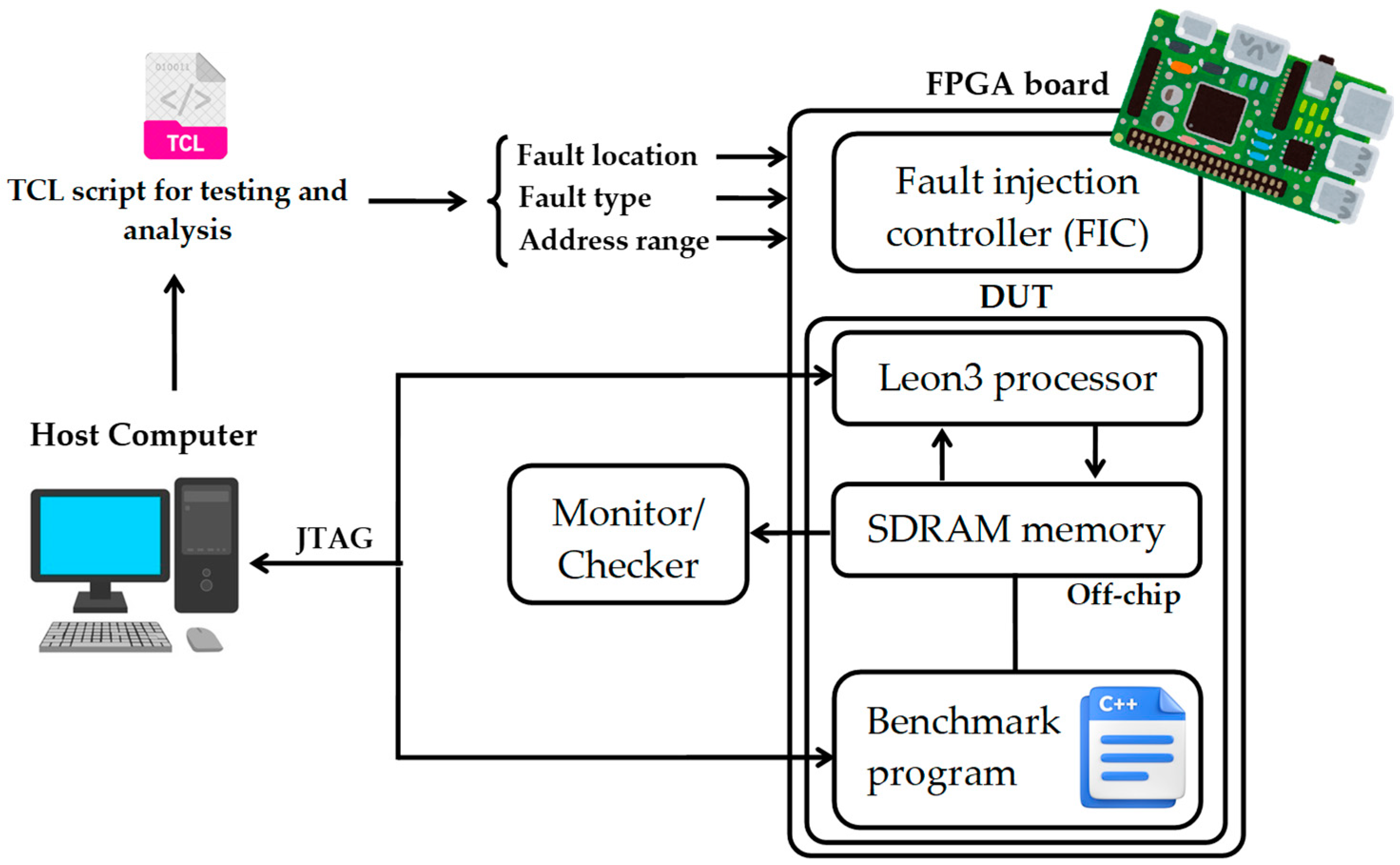
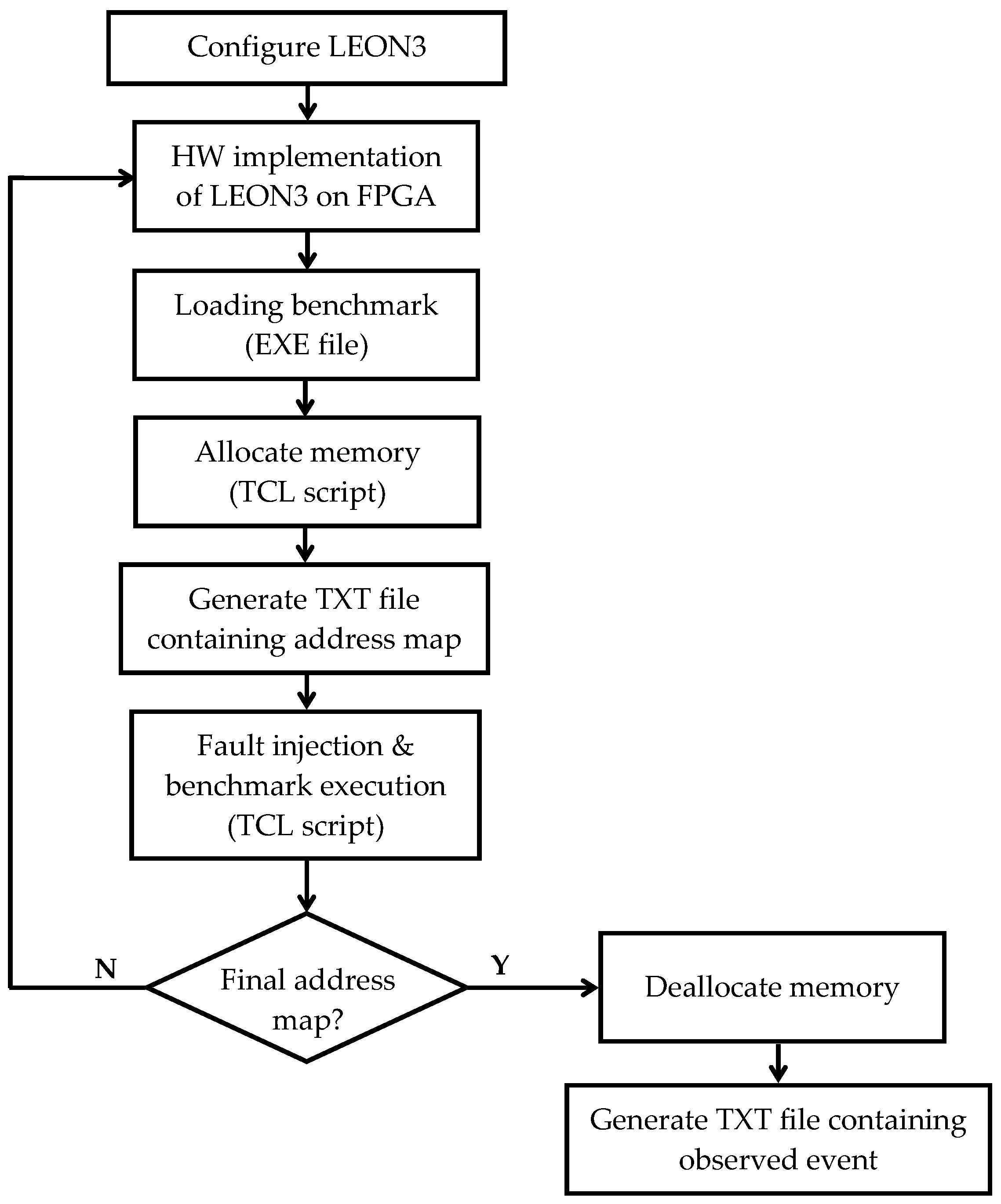
3.3. Proposed MCU Fault Injection Methodology
- Host computer: defines and controls injection campaigns, manages benchmark execution, and collects output data.
- Fault injection controller (FIC): injects MCU events into specified SDRAM addresses according to configurable parameters (e.g., fault type, address range, fault location).
- Monitor/Checker module: tracks processor activity during execution to identify erroneous outputs, exceptions, or system stalls.
- Benchmark suite: numerical and cryptographic workloads running on the LEON3 to represent distinct application domains.
- Timing: Faults were injected during active benchmark execution, after the completion of the initialization phase and before final output generation, ensuring perturbations affect only the computational core of each workload. Injections occurred across multiple clock cycles to capture timing-dependent vulnerabilities.
- Spatial location: The data segment resides in the SDRAM address range 0x40000000–0x7FFFFFFF, where each address corresponds to a 128-bit memory size. Each SDRAM address was partitioned into four words. Within each 128-bit, one bit was flipped in the least significant bit (LSB) position of the first word and one bit in the LSB of the second adjacent word, emulating a spatially correlated two-bit MCU within the same physical memory access unit. This pattern was applied exhaustively across all valid data-segment addresses.
- Total injection events: The experiments comprised 661,870 injections for MulMatrix, 662,870 for FFT, and 661,888 for AES, ensuring comprehensive coverage of the active memory footprint under each workload.
4. Experimental Results and Analysis
4.1. MCU Fault Manifestations in MulMatrix Execution
| FI Campaign (Total FI: 661,870) | Masked Faults | Silent Faults | Data Store Errors | Stopped Mode |
|---|---|---|---|---|
| 116,497 (Series 1) | 0 | 0 | 116,496 | 1 |
| 53,058 (Series 2) | 1 | 0 | 53,056 | 1 |
| 59,970 (Series 3) | 1 | 0 | 59,968 | 1 |
| 116,364 (Series 4) | 1 | 0 | 116,362 | 1 |
| 55,490 (Series 5) | 1 | 0 | 55,488 | 1 |
| 116,362 (Series 6) | 1 | 0 | 116,360 | 1 |
| 144,129 (Series 7) | 1 | 0 | 144,128 | 0 |
- −
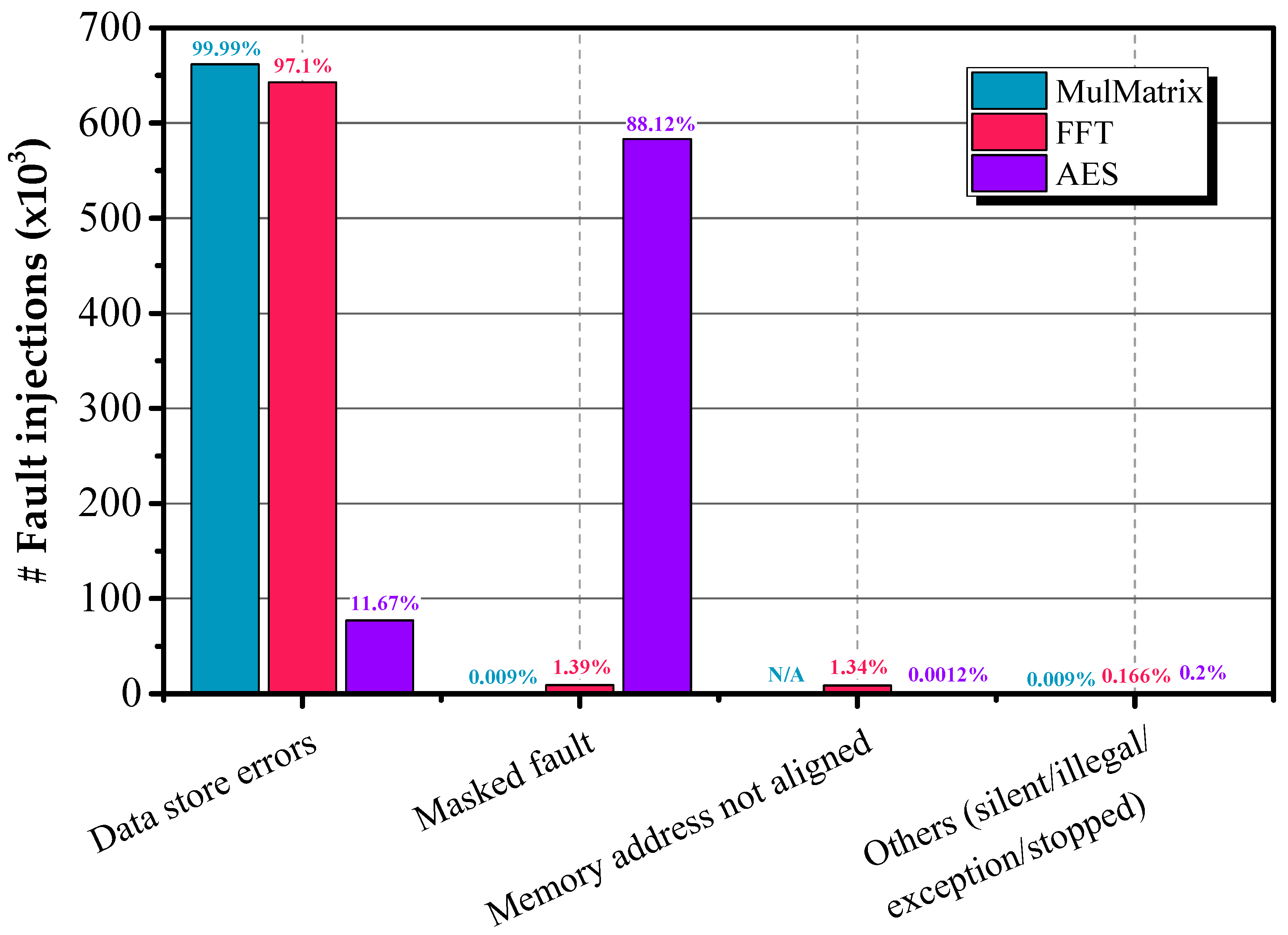
- data store errors (≈99.99% in each campaign);
- −
- stopped mode and masked faults (negligible for each type).
4.2. MCU Fault Manifestations in FFT Execution
- −
- data store errors (~93–99% of faults in Series 2–10; ~5% in Series 1);
- −
- stopped mode faults, silent faults (negligible for each type);
- −
- masked faults (~1–3%) and;
- −
- misaligned memory/data access exception (83% misaligned, 10% access in Series 1).
4.3. MCU Fault Manifestations in AES Execution
| FI Campaign (Total FI: 661,888) | Masked Faults | Silent Faults | Illegal Instruction | Data Access Exception | Data Store Errors | Mem. Address Not Aligned | Instruction Access | Stopped Mode |
|---|---|---|---|---|---|---|---|---|
| 83,139 (Series 1) | 4561 | 82 | 1 | 1273 | 77,212 | 8 | 1 | 1 |
| 578,695 (Series 2) | 578,695 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
- −
- data store errors (~12% of total faults; ~93% in Series 1);
- −
- masked faults (~88% of total faults; 100% in Series 2);
- −
- data access exception (~0.2%);
- −
- silent faults, illegal instructions, memory address not aligned, instruction access faults, and stopped mode (negligible for each type).
4.4. Contextual Comparison with Prior SEU-Centric Studies
4.5. Comparative Analysis: MulMatrix, AES and FFT
5. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| 3D | Three-Dimensional |
| ABFT | Algorithm-Based Fault Tolerance |
| AES | Advanced Encryption Standard |
| AHB | Advanced High-Speed Bus |
| AMBA | Advanced Microcontroller Bus Architecture |
| ASIC | Application-Specific Integrated Circuit |
| ARM | Advanced RISC Machines |
| BRAM | Block RAM |
| CPU | Central Processing Unit |
| CS | Chip-Select |
| DBI | Dynamic Binary Instrumentation |
| DED | Double Error Correction |
| DFA | Differential Fault Analysis |
| DFI | Direct Fault Injection |
| DFIA | Differential Fault Intensity Analysis |
| DRAM | Dynamic Random-Access Memory |
| DUT | Design Under Test |
| ECC | Error Correction Code |
| EXE | Executable File |
| FI | Fault Injection |
| FIC | Fault Injection Controller |
| FPGA | Field-Programmable Gate Array |
| GCC | GNI Compiler Collection |
| HDL | Hardware Description Language |
| I/O | Input/Output |
| ICAP | Internal Configuration Access Port |
| IP | Intellectual Propriety |
| IRQ | Interruption ReQuest |
| IU | Integer Unit |
| JCM | JTAG Configuration Manager |
| JTAG | Joint Test Access Group |
| LSB | Least Significant Bit |
| MBU | Multiple-Bit Upset |
| MCTRL | Memory Controller |
| MCU | Multiple-Cell Upset |
| MET | Multiple-Event Transient |
| MMU | Memory Management Unit |
| N/A | Not Applicable or Not Available |
| PC | Program Counter |
| PROM | Programmable Read-Only Memory |
| RAM | Random Access Memory |
| RISC | Reduced Instruction Set Computer |
| RTL | Register Level Transfer |
| S-Box | Substitution Box |
| SBU | Single Bit Upset |
| SDRAM | Synchronous Dynamic Random-Access Memory |
| SEC | Single Error Correction |
| SEM | Soft Error Mitigation |
| SEMT | Single-Event Multiple Transient |
| SET | Single-Event Transient |
| SEU | Single-Event Upset |
| SMT | Satisfiability Modulo Theory |
| SoC | System-on-Chip |
| SPARC | Scalable Processor Architecture |
| SPI | Serial Peripheral Interface |
| SRAM | Synchronous Random-Access Memory |
| TCL | Tool Command Language |
| TCM | Tightly Coupled Memories |
| TMR | Triple Modular Redundancy |
| TXT | Text |
| UART | Universal Asynchronous Receiver Transmitter |
| UNIMP | Unimplemented Instruction |
| VHDL | VHSIC Hardware Description Language |
| VHSIC | Very High Speed Integrated Circuit |
References
- Aranda, L.A.; Ruano, O.; Garcia-Herrero, F.; Maestro, J.A. Reliability analysis of asic designs with xilinx sram-based fpgas. IEEE Access 2021, 9, 140676–140685. [Google Scholar] [CrossRef]
- Shukla, S.; Ray, K.C. A low-overhead reconfigurable RISC-V quad-core processor architecture for fault-tolerant applications. IEEE Access 2022, 10, 44136–44146. [Google Scholar] [CrossRef]
- Hamada, E.; Igarashi, Y.; Ueno, K. A Hybrid Scrubber Based on the SEM and the PicoBlaze for Artix-7 FPGAs in the COMET Read-out Electronics. IEEE Trans. Nucl. Sci. 2024, 18, 240–248. [Google Scholar] [CrossRef]
- Siecha, R.T.; Alemu, G.; Prinzie, J.; Leroux, P. Analysis of the SEU Tolerance of an FPGA-Based Time-to-Digital Converter Using Emulation-Based Fault Injection. Electronics 2025, 14, 2176. [Google Scholar] [CrossRef]
- Lee, D.; Nam, T.; Park, D.; Kim, Y.; Na, J. Enhanced soft error rate estimation technique for aerospace electronics safety design via emulation fault injection. Appl. Sci. 2024, 14, 1470. [Google Scholar] [CrossRef]
- Gruwell, A.; Zabriskie, P.; Wirthlin, M. High-speed FPGA configuration and testing through JTAG. In Proceedings of the IEEE AUTOTESTCON, Anaheim, CA, USA, 12–15 September 2016; pp. 1–8. [Google Scholar]
- Ferlini, F.; Viel, F.; Seman, L.O.; Pettenghi, H.; Bezerra, E.A.; Leithardt, V.R.Q. A methodology for accelerating FPGA fault injection campaign using ICAP. Electronics 2023, 12, 807. [Google Scholar] [CrossRef]
- Abbasitabar, H.; Zarandi, H.R.; Salamat, R. Susceptibility analysis of LEON3 embedded processor against multiple event transients and upsets. In Proceedings of the 2012 IEEE 15th International Conference on Computational Science and Engineering, Paphos, Cyprus, 5–7 December 2012; pp. 548–553. [Google Scholar]
- Mansour, W.; Velazco, R. SEU fault-injection in VHDL-based processors: A case study. J. Electron. Test. 2013, 29, 87–94. [Google Scholar] [CrossRef]
- Da Silva, A.; Sanchez, S. LEON3 ViP: A virtual platform with fault injection capabilities. In Proceedings of the 13th Euromicro Conference on Digital System Design: Architectures, Methods and Tools, Lille, France, 1–3 September 2010; pp. 813–816. [Google Scholar]
- Lindoso, A.; Entrena, L.; García-Valderas, M.; Parra, L. A hybrid fault-tolerant LEON3 soft core processor implemented in low-end SRAM FPGA. IEEE Trans. Nucl. Sci. 2017, 64, 374–381. [Google Scholar] [CrossRef]
- Kchaou, A.; Youssef, W.E.H.; Tourki, R.; Bouesse, F.; Ramos, P.; Velazco, R. A deep analysis of SEU consequences in the internal memory of LEON3 processor. In Proceedings of the 17th Latin-American Test Symposium (LATS), Foz do Iguacu, Brazil, 6–8 April 2016; p. 178. [Google Scholar]
- Kchaou, A.; Youssef, W.E.H.; Velazco, R.; Tourki, R. An exhaustive analysis of SEU effects in the SRAM memory of soft processor. J. Eng. Sci. Technol. 2018, 13, 58–68. [Google Scholar]
- Sari, A.; Psarakis, M. A fault injection platform for the analysis of soft error effects in FPGA soft processors. In Proceedings of the IEEE 19th International Symposium on Design and Diagnostics of Electronic Circuits & Systems (DDECS), Kosice, Slovakia, 20–22 April 2016; pp. 1–6. [Google Scholar]
- Sari, A.; Psarakis, M. A flexible fault injection platform for the analysis of the symptoms of soft errors in FPGA soft processors. J. Circuits Syst. Comput. 2017, 26, 1740009. [Google Scholar] [CrossRef]
- Yuce, B.; Ghalaty, N.F.; Schaumont, P. Improving fault attacks on embedded software using RISC pipeline characterization. In Proceedings of the IEEE Workshop on Fault Diagnosis and Tolerance in Cryptography (FDTC), Saint-Malo, France, 13 September 2015; pp. 97–108. [Google Scholar]
- Chekmarev, S.A.; Khanov, V.K.; Antamoshkin, O.A. Modification of fault injection method via on-chip debugging for processor cores of systems-on-chip. In Proceedings of the IEEE International Siberian Conference on Control and Communications (SibCon), Omsk, Russia, 21–23 May 2015; pp. 1–4. [Google Scholar]
- Chekmarev, S.A.; Khanov, V.K. Fault injection via on-chip debugging in the internal memory of systems-on-chip processor. IOP Conf. Ser. Mater. Sci. Eng. 2015, 94, 012020. [Google Scholar] [CrossRef]
- Nethula, S.; Bansal, V.; Hamad, G.B.; Ait Mohamed, O. Layout-based Vulnerability Analysis of LEON3 Processor to Single Event Multiple Transients using Satisfiability Modulo Theories. In Proceedings of the 23rd International Symposium on Quality Electronic Design (ISQED), Santa Clara, CA, USA, 9–10 April 2022; pp. 1–6. [Google Scholar]
- Travessini, R.; Villa, P.R.; Vargas, F.L.; Bezerra, E.A. Processor core profiling for SEU effect analysis. In Proceedings of the IEEE 19th Latin-American Test Symposium (LATS), Sao Paulo, Brazil, 12–14 March 2018; pp. 1–6. [Google Scholar]
- Mannos, T.J.; Dziki, B.; Sharif, M. Fault testing a synthesizable embedded processor at gate level using ultrascale FPGA emulation. In Proceedings of the 2019 ACM/SIGDA International Symposium on Field-Programmable Gate Arrays, Seaside, CA, USA, 24–26 February 2019; p. 116. [Google Scholar]
- Kchaou, A.; Saad, S.; Garrab, H.; Machhout, M. Reliability of LEON3 Processor’s Program Counter Against SEU, MBU, and SET Fault Injection. Cryptography 2025, 9, 54. [Google Scholar] [CrossRef]
- Tsiligiannis, G.; Dilillo, L.; Bosio, A.; Girard, P.; Pravossoudovitch, S.; Todri, A.; Virazel, A.; Puchner, H.; Frost, C.; Wrobel, F.; et al. Multiple cell upset classification in commercial SRAMs. IEEE Trans. Nucl. Sci. 2014, 61, 1747–1754. [Google Scholar] [CrossRef]
- Alles, M.L. Radiation hardening by process. In Extreme Environment Electronics; CRC Press: Boca Raton, FL, USA, 2013; pp. 287–298. [Google Scholar]
- Perez-Celis, A.; Wirthlin, M.J. Statistical method to extract radiation-induced multiple-cell upsets in SRAM-based FPGAs. IEEE Trans. Nucl. Sci. 2019, 67, 50–56. [Google Scholar] [CrossRef]
- Fibich, C.; Rössler, P.; Tauner, S.; Taucher, H.; Matschnig, M. A netlist-level fault-injection tool for FPGAs. e & i Elektrotech Informat. 2015, 132, 274–281. [Google Scholar]
- Monopoli, M.; Biondi, M.; Nannipieri, P.; Moranti, S.; Fanucci, L. RADSAFiE: A Netlist-Level Fault Injection User Interface Application for FPGA-Based Digital Systems. IEEE Access 2025, 13, 28809–28823. [Google Scholar] [CrossRef]
- Khatri, A.R.; Hayek, A.; Börcsök, J. Development and Verification of Serial Fault Simulation for FPGA Designs using the Proposed RASP-FIT Tool. Int. J. Adv. Comput. Sci. Appl. 2020, 11, 35–40. [Google Scholar] [CrossRef]
- Khatri, A.R. Validation of Proposed Test Set Reduction Hybrid Compaction Schemes for FPGA-Based Designs. J. Hunan Univ. Nat. Sci. 2023, 50, 228–235. [Google Scholar] [CrossRef]
- Cai, C.; Fan, X.; Liu, J.; Li, D.; Liu, T.; Ke, L.; Zhao, P.; He, Z. Heavy-ion induced single event upsets in advanced 65 nm radiation hardened FPGAs. Electronics 2019, 8, 323. [Google Scholar] [CrossRef]
- Viera, R.; Dutertre, J.M.; Silva Lima, R.; Pommies, M.; Bertrand, A. Tampering with the flash memory of microcontrollers: Permanent fault injection via laser illumination during read operations. J. Cryptogr. Eng. 2024, 14, 207–221. [Google Scholar] [CrossRef]
- Jiang, W. Machine Learning Methods to Detect Voltage Glitch Attacks on IoT/IIoT Infrastructures. Comput. Intell. Neurosci. 2022, 1, 6044071. [Google Scholar] [CrossRef]
- Lopez-Ongil, C.; Garcia-Valderas, M.; Portela-Garcia, M.; Entrena, L. Autonomous fault emulation: A new FPGA-based acceleration system for hardness evaluation. IEEE Trans. Nucl. Sci. 2007, 54, 252–261. [Google Scholar] [CrossRef]
- Entrena, L.; Garcia-Valderas, M.; Fernandez-Cardenal, R.; Lindoso, A.; Portela, M.; Lopez-Ongil, C. Soft error sensitivity evaluation of microprocessors by multilevel emulation-based fault injection. IEEE Trans. Comput. 2010, 61, 313–322. [Google Scholar] [CrossRef]
- Alderighi, M.; Casini, F.; D’Angelo, S.; Mancini, M.; Pastore, S.; Sechi, G.R.; Weigand, R. Evaluation of single event upset mitigation schemes for SRAM based FPGAs using the FLIPPER fault injection platform. In Proceedings of the 22nd IEEE International Symposium on Defect and Fault-Tolerance in VLSI Systems (DFT 2007), Rome, Italy, 26–28 September 2007; pp. 105–113. [Google Scholar]
- Aranda, L.A.; Sánchez-Macián, A.; Maestro, J.A. ACME: A tool to improve configuration memory fault injection in SRAM-based FPGAs. IEEE Access 2019, 7, 128153–128161. [Google Scholar] [CrossRef]
- Aranda, L.A.; Ruano, O.; Garcia-Herrero, F.; Maestro, J.A. ACME-2: Improving the extraction of essential bits in Xilinx SRAM-based FPGAs. IEEE Trans. Circuits Syst. II Express Br. 2021, 69, 1577–1581. [Google Scholar] [CrossRef]
- The LogiCORE ™ IP Soft Error Mitigation. In Product Guide (PG036); Xilinx: San Jose, CA, USA, 2015.
- Ebrahimi, M.; Mohammadi, A.; Ejlali, A.; Miremadi, S.G. A fast, flexible, and easy-to-develop FPGA-based fault injection technique. Microelectron. Reliab. 2014, 54, 1000–1008. [Google Scholar] [CrossRef]
- Farooq, U.; Mehrez, H. Pre-silicon verification using multi-FPGA platforms: A review. J. Electron. Test. 2021, 37, 7–24. [Google Scholar] [CrossRef]
- Ruano, Ó.; García-Herrero, F.; Aranda, L.A.; Sánchez-Macián, A.; Rodriguez, L.; Maestro, J.A. Fault injection emulation for systems in fpgas: Tools, techniques and methodology, a tutorial. Sensors 2021, 21, 1392. [Google Scholar] [CrossRef]
- Hubert, G.; Velazco, R.; Federico, C.; Cheminet, A.; Silva-Cardenas, C.; Caldas, L.V.E.; Pancher, F.; Lacoste, V.; Palumbo, F.; Mansour, W.; et al. Continuous High-Altitude Measurements of Cosmic Ray Neutrons and SEU/MCU at Various Locations: Correlation and Analyses Based-On MUSCA SEP3. IEEE Trans. Nucl. Sci. 2013, 60, 2418–2426. [Google Scholar] [CrossRef]
- Franco, F.J.; Fabero, J.C.; Mecha, H.; Rezaei, M.; Hubert, G.; Clemente, J.A. Best-Fit Techniques to Estimate SBU/MCU Cross Sections From Radiation-Ground Tests in Memories. IEEE Trans. Nucl. Sci. 2025, 72, 1403–1411. [Google Scholar] [CrossRef]
- Kasap, S.; Wächter, E.W.; Zhai, X.; Ehsan, S.; Mcdonald-Maier, K. Survey of soft error mitigation techniques applied to LEON3 soft processors on SRAM-based FPGAs. IEEE Access 2020, 8, 28646–28658. [Google Scholar] [CrossRef]
- Wirthlin, M.J.; Keller, A.M.; McCloskey, C.; Ridd, P.; Lee, D.; Draper, J. SEU mitigation and validation of the LEON3 soft processor using triple modular redundancy for space processing. In Proceedings of the 2016 ACM/SIGDA International Symposium on Field-Programmable Gate Arrays, Monterey CA, USA, 21–23 February 2016; pp. 205–214. [Google Scholar]
- Keller, A.M.; Wirthlin, M.J. Benefits of complementary SEU mitigation for the LEON3 soft processor on SRAM-based FPGAs. IEEE Trans. Nucl. Sci. 2016, 1, 519–528. [Google Scholar] [CrossRef]
- Learn, M.W. Evaluation of the Leon3 Soft-Core Processor Within a Xilinx Radiation-Hardened Field-Programmable Gate Array (No. SAND2012-0454); Sandia National Laboratories (SNL): Albuquerque, NM, USA, 2012. [Google Scholar]
- Sari, A.; Psarakis, M. Scrubbing-based SEU mitigation approach for systems-on-programmable-chips. In Proceedings of the 2011 International Conference on Field-Programmable Technology, New Delhi, India, 12–14 December 2011; pp. 1–8. [Google Scholar]
- Lotfi-Kamran, P.; Sarbazi-Azad, H. Introduction to data prefetching. In Advances in Computers; Elsevier: Cambridge, MA, USA, 2022; Volume 125, pp. 1–17. [Google Scholar]
- Losa, B.; Parra, P.; Da Silva, A.; Polo, Ó.R.; Tejedor, J.I.G.; Martínez, A.; Sánchez, J.; Sánchez, S.; Guzmán, D. Memory management unit for hardware-assisted dynamic relocation in on-board satellite systems. IEEE Trans. Aerosp. Electron. Syst. 2023, 59, 6923–6939. [Google Scholar] [CrossRef]
- Losa, B.; Parra, P.; Da Silva, A.; Polo, Ó.R.; Tejedor, J.I.G.; Martínez, A.; Sánchez, S.; Guzmán, D. Hardware-assisted virtualization extensions for LEON processors in mixed-criticality systems. Microprocess. Microsyst. 2025, 112, 105130. [Google Scholar] [CrossRef]
- Mannos, T.; Plusquellic, J.; Dziki, B. Information Leakage Analysis Using Accelerated Fault Injection Emulation of a RISC-V Microprocessor, No. SAND2020-0503C; Sandia National Lab. (SNL-NM): Albuquerque, NM, USA, 2020. [Google Scholar]
- Vijay, M.; Mittal, R. Algorithm-based fault tolerance: A review. Microprocess. Microsyst. 1997, 21, 151–161. [Google Scholar] [CrossRef]
- Bosilca, G.; Delmas, R.; Dongarra, J.; Langou, J. Algorithm-based fault tolerance applied to high performance computing. J. Parallel Distrib. Comput. 2009, 69, 410–416. [Google Scholar] [CrossRef]
- Aeroflex Gaisler. Ut699 Leon 3ft/Sparctm v8 Microprocessor. Functional Manual; Aeroflex Gaisler: Gothenburg, Sweden, 2014. [Google Scholar]
- Aeroflex Gaisler. Handling of External Memory Edac Errors in Leon/Grlib Systems; Application note, Doc. No GRLIB-AN-0004; Aeroflex Gaisler: Gothenburg, Sweden, 2017. [Google Scholar]
- Piret, G.; Quisquater, J.J. A differential fault attack technique against SPN structures, with application to the AES and KHAZAD. In Proceedings of the International Workshop on Cryptographic Hardware and Embedded Systems, Cologne, Germany, 8–10 September 2003; Springer: Berlin/Heidelberg, Germany, 2003; pp. 77–88. [Google Scholar]
| Ref./Year | Methodology | Fault Model | Target | Main Findings |
|---|---|---|---|---|
| [8]/2012 | VHDL simulation + FPGA emulation | SETs, SEUs, MBUs, METs | Flip-flops, Register file, Registers, Cache memories, | Characterized soft error propagation and masking in integer and multiplier unit. |
| [9]/2013 | FPGA emulation campaigns | SEUs | Register-level units | Analyzed vulnerability of registers under SEUs |
| [10]/2015 | Structural pipeline analysis combined with experimental biased FI attacks | Fault attacks modeled via biased fault injection | 7-stage pipeline LEON3 (Spartan-6 FPGA) | Identified most vulnerable pipeline stages for AES; highlighted risks in cryptographic software |
| [11]/2017 | Hybrid design (SEC/DED codes, hardware monitors, software validation, scrubbing) on Artix-7 | SEUs + control-flow errors | Full LEON3 system | Demonstrated improved reliability with multi-layer mitigation |
| [12,13]/ 2018 | Large-scale FPGA-based emulation (>200 k injections) | SEUs | Xilinx SRAM-based FPGA hosting LEON3 focuses SRAM memories | Provided detailed characterization of error propagation, workload sensitivity, and limits of detection mechanisms |
| [14,15]/ 2017 | Open-source FI platform (RapidSmith) with on-chip microcontroller injects/monitors | SEUs injected at configuration bit/frame level | Xilinx SRAM-based FPGA hosting LEON3 focuses on configuration memory and per-component sensitivity | Estimates soft-error sensitivity per bit/frame |
| [16]/2015 | Structural pipeline analysis combined with experimental biased FI attacks | DFIA + clock glitch | 7-stage pipeline LEON3 (Spartan-6 FPGA) | Identified most vulnerable pipeline stages for AES; highlighted risks in cryptographic software |
| [17,18]/ 2015 | Embedded IP-core fault injector inside SoC | SEUs | LEON3 in SoC | Simplifies fault injection setup; enables autonomous, long campaigns |
| [19]/2022 | Formal SMT-based framework with layout-aware analysis | SEMTs (SEMT3, SEMT4) | LEON3 ASIC core | Estimated propagation probability. 30% (SEMT3), 54% (SEMT4); rigorous vulnerability assessment |
| [20]/2018 | Simulation-script-based FI | SBUs | LEON3 CPU registers | Identified small set of highly vulnerable registers |
| [21]/2019 | Gate-level FI using synthesizable saboteur + scan chain; hardware-accelerated on UltraScale FPGAs | Static faults (incl. delay faults) | LEON3 running AES-256 | Identified 22 faulty behaviors incl. crypto/memory leakage; delay faults most effective; ~7200× faster than simulation |
| [22]/2025 | Netlist fault injection based simulation | SEUs, MBUs, SETs | LEON3 Program Counter across pipeline stages | Early/middle stages (FE–EX) highly vulnerable; ME/XC resilient; SET mostly masked but risky. |
| Fault Category | Description | Detection Mechanisms | Example Behavior | Observed Frequency |
|---|---|---|---|---|
| Data store error | Incorrect value written to memory, Write buffer error | ECC, parity | Corrupted data in memory | Predominant (>99.99% of faults in each series) |
| Stopped mode | Processor enters halted state | Watchdog, exception flags | System stops execution | Always present (1 per campaign, negligible) |
| Masked fault | Fault that does not affect program output | N/A | No visible effect | Always present (1 per campaign, negligible) |
| FI Campaign (Total FI: 662,870) | Masked Faults | Silent Faults | Data Access Exception | Data Store Errors | Mem. Address Not Aligned | Stopped Mode |
|---|---|---|---|---|---|---|
| 10,622 (Series 1) | 146 | 3 | 1086 | 556 | 8830 | 1 |
| 66,818 (Series 2) | 830 | 0 | 0 | 65,987 | 0 | 1 |
| 78,018 (Series 3) | 2424 | 0 | 1 | 75,592 | 1 | 1 |
| 90,930 (Series 4) | 830 | 0 | 0 | 90,099 | 0 | 1 |
| 87,490 (Series 5) | 830 | 0 | 0 | 86,659 | 0 | 1 |
| 67,650 (Series 6) | 830 | 0 | 0 | 66,819 | 0 | 1 |
| 67,778 (Series 7) | 830 | 0 | 0 | 66,947 | 0 | 1 |
| 91,858 (Series 8) | 830 | 0 | 0 | 91,027 | 0 | 1 |
| 74,434 (Series 9) | 830 | 0 | 0 | 73,603 | 0 | 1 |
| 27,272 (Series 10) | 830 | 0 | 0 | 25,441 | 0 | 0 |
| Fault Category | Description | Detection Mechanisms | Example Behavior | Observed Frequency |
|---|---|---|---|---|
| Data store error | Corruption during write operations to SDRAM, leading to inconsistent or invalid data values | Detected through execution mismatches and exception handling | Incorrect FFT output values, rapid propagation of numerical errors | Dominant (~93–99% of faults in Series 2–10; ~5% in Series 1) |
| Stopped mode | System halts due to unrecoverable error or watchdog trigger | Requires manual reset of FPGA platform | Emulation stopped execution cannot proceed | Always present (1 per campaign, negligible fraction) |
| Masked fault | Faults that do not alter program state or output | Inherent masking through algorithm redundancy or unused resources | Execution proceeds normally without errors | Low (~1–3% across campaigns) |
| Silent faults | Errors that propagate without detection | Not detected by hardware/software mechanisms | Incorrect results without triggering exceptions | Rare (only 3 cases, ~0.03% in Series 1) |
| Data access exceptions/misalignment memory | Invalid memory addressing due to MCU-induced corruption | Exception handlers in LEON3 pipeline | Addressing trap, memory misalignment | Significant in Series 1 (83% not aligned, 10% access), absent later |
| Fault Category | Description | Detection Mechanisms | Example Behavior | Observed Frequency |
|---|---|---|---|---|
| Masked faults | Fault that does not affect program output | N/A | AES output remains correct; fault overwritten or unused memory | Overwhelmingly prevalent (100% of faults in Series 2) |
| Silent faults | Faults that occur without detection | N/A | Corrupted AES computation may produce incorrect cipher-text without errors | Extremely low (~0.01% of faults in Series 1) |
| Illegal instructions | Fault triggers in-valid opcode execution, UNIMP or other un-implemented instruction | CPU exception | Processor executes invalid instruction; may halt or trigger fault handler | Rare (only 1 case) |
| Data access exceptions | Memory access violation, Access error during load or store instruction | CPU exception, MMU | Program halts or triggers exception; AES execution interrupted | Very low (~2% of faults in Series 1) |
| Data store errors | Incorrect value written to memory, Write buffer error | ECC, parity | AES key or state corrupted; incorrect ciphertext generated | Predominant (~93% of faults in Series 1) |
| Memory address not aligned | Memory access to un-aligned address | CPU exception | Program halts due to misaligned memory access | Negligible (only 8 cases in Series 1) |
| Instruction access faults | Fault in instruction fetch, Error during instruction fetch | CPU exception, ECC | AES execution may halt or incorrect instructions executed | Rare (only 1 case) |
| Stopped mode | Processor halts completely | Watchdog, exception flags | AES execution stops entirely | Rare (only 1 case) |
| Workload | SEU in SRAM (Our Prior Work) | MCU in SDRAM (Our Work) |
|---|---|---|
| MulMatrix | >0.0099% masking | <0.01% masking |
| FFT | ~0.259% masking | ~2% masking; alignment traps emerge |
| AES | 93.34% masking | 88% non-propagating (inactive memory), but active faults enable DFA |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kchaou, A.; Saad, S.; Garrab, H. Emulation-Based Analysis of Multiple Cell Upsets in LEON3 SDRAM: A Workload-Dependent Vulnerability Study. Electronics 2025, 14, 4582. https://doi.org/10.3390/electronics14234582
Kchaou A, Saad S, Garrab H. Emulation-Based Analysis of Multiple Cell Upsets in LEON3 SDRAM: A Workload-Dependent Vulnerability Study. Electronics. 2025; 14(23):4582. https://doi.org/10.3390/electronics14234582
Chicago/Turabian StyleKchaou, Afef, Sehmi Saad, and Hatem Garrab. 2025. "Emulation-Based Analysis of Multiple Cell Upsets in LEON3 SDRAM: A Workload-Dependent Vulnerability Study" Electronics 14, no. 23: 4582. https://doi.org/10.3390/electronics14234582
APA StyleKchaou, A., Saad, S., & Garrab, H. (2025). Emulation-Based Analysis of Multiple Cell Upsets in LEON3 SDRAM: A Workload-Dependent Vulnerability Study. Electronics, 14(23), 4582. https://doi.org/10.3390/electronics14234582







