A Smart Proactive Forensic Meta-Model for Smart Homes in Saudi Arabia Using Metamodeling Approaches
Abstract
1. Introduction
2. Related Works
- Regulatory Misalignment: Models originating from (e.g., Europe or the United States) may not necessarily conform to the Saudi PDPL and NCA frameworks, potentially resulting in legal challenges concerning forensic evidence. It is imperative to recognize these differences to ensure compliance and maintain the integrity of the evidence.
- Infrastructure Assumptions: Numerous models presume the integration of pre-existing systems; however, Saudi Arabia’s remarkable giga-projects demonstrate significant large-scale innovations that genuinely necessitate a specialized framework tailored for ‘greenfield’ development environments.
- Lack of Regional Threat Context: They do not consider the unique device ecosystems, user habits, and environmental conditions such as extreme climates that are specific to the region.
3. Methodology
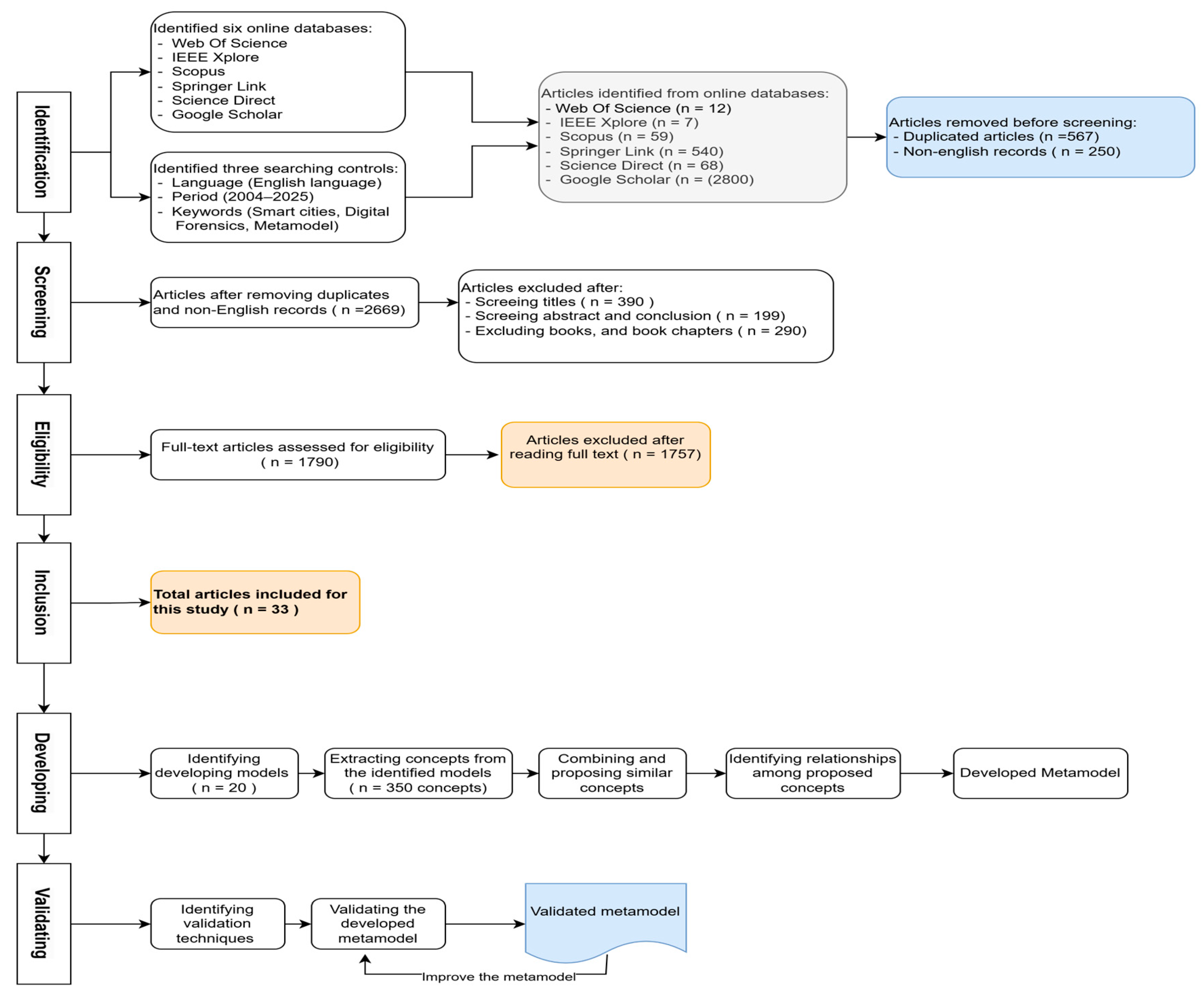
- Identification stage: This stage aims to identify the online databases and search protocols for gathering articles. Six central online databases are identified: Web of Science, IEEE Xplore, Scopus, Springer Link, ScienceDirect, and Google Scholar. The search protocols guiding this study include the language (English), time (2004–2025), and keywords (Smart cities, Digital forensics, and metamodel). A total of 3486 articles has been gathered from the identified online databases, as illustrated in Figure 2. This stage eliminates 567 duplicate articles and 250 non-English articles. A total of 2669 articles has been moved to the screening stage.
- Screening stage: During this stage, the 2669 articles are sorted according to their eligibility for inclusion in this study by filtering. As part of the screening process, 290 books and book chapters were removed, 199 articles were removed after evaluating the abstracts, and 390 articles were removed after considering the titles.
- Eligibility stage: In this stage, 1790 articles are thoroughly reviewed to select the eligible articles for this study. Many articles were excluded due to issues with quality, validation, implementation, and the reliability of the results. A total of 1757 articles were removed, leaving only 33 articles eligible for this study.
- Inclusion stage: The inclusion stage was completed by choosing 33 articles for detailed analysis in the study. These articles, listed in Table 2, were selected because they directly address the research focus on smart homes, cities, digital forensics, and metamodeling. They cover a broad spectrum of topics, including domain-specific frameworks for smart homes and drones, organizational IoT security strategies, technical data analyses, and high-level modeling approaches using metamodeling and MDE. This curated collection of literature forms the foundational knowledge base from which the core concepts for developing the new SPFMSH were derived and synthesized.
- 5.
- Developing stage: this stage aims to develop a Smart Proactive Forensic Metamodel for Smart Homes in Saudi Arabia. It consists of several steps, as shown in Figure 1:
- ✓
- Identifying developing models: As discussed in Section 2, there are several models for forensic investigations of smart cities. The selection of models in this study was based on factors identified in previous research [37,38] to evaluate coverage. To propose common investigation concepts for smart city forensic models, it is essential to gather diverse perspectives that can be widely applied. The author meticulously selected 21 models from the initial set of 33, ensuring their suitability for the development of a metamodel. The chosen models emphasized proactive and forensic readiness, maintained direct connections to IoT or smart environments, and encompassed sufficiently detailed concepts for practical applications. This selection criterion led to the exclusion of models that were purely reactive, overly abstract, outdated, or excessively narrow in focus, as they were deemed less effective for conveying broader concepts. The term “high coverage” refers to a model that encompasses all aspects of smart city forensics, offering a comprehensive view. On the other hand, a model with lower coverage reflects only a partial or specific aspect of smart city functions. Using these categories, this study found that 21 models belonged to the full-coverage group, while 12 models were identified as partial-coverage. Table 3 displays the 21 models that were assigned to develop the metamodel.
- ✓
- Extracting concepts from the identified models: In this step, concepts from the 21 models are extracted based on criteria adapted from [37,38]:
- ✓
- Excluding the title, abstract, introduction, related works, and conclusion: The concept must be extracted from the main body of a textual or graphical model.
- ✓
- Excludes any concept that is not related to the domain: The fundamental guideline for extracting concepts is: “If it is not relevant to the domain, then it should not be included in the case domain model”.
- ✓
- Exclusion of specific concepts related to the domain: The concept, which possesses a particular meaning or function, should be excluded. According to a more common concept, the name is easier to reuse than that of a more specific concept name.
- ✓
- Combining and proposing similar concepts: A process of combining and proposing common concepts from extracted concepts is based on the similarity of their meanings or functions, regardless of their names [39]. Therefore, to candidate common concepts that vary in naming, synonyms, definitions, and meaning is laborious and may lead to incorrect results. For this purpose, this study employed three techniques to assist in filtering, combining, and proposing familiar concepts from the extracted ones. The methods include an interview with a digital forensic expert, a synonyms check using Wordnet2 [42], and the extraction of the semantic functioning or meaning of each concept. The standard concepts that have similar meanings or functions, regardless of their names or synonyms, are combined and developed as common concepts, as illustrated in Table 5.
- ✓
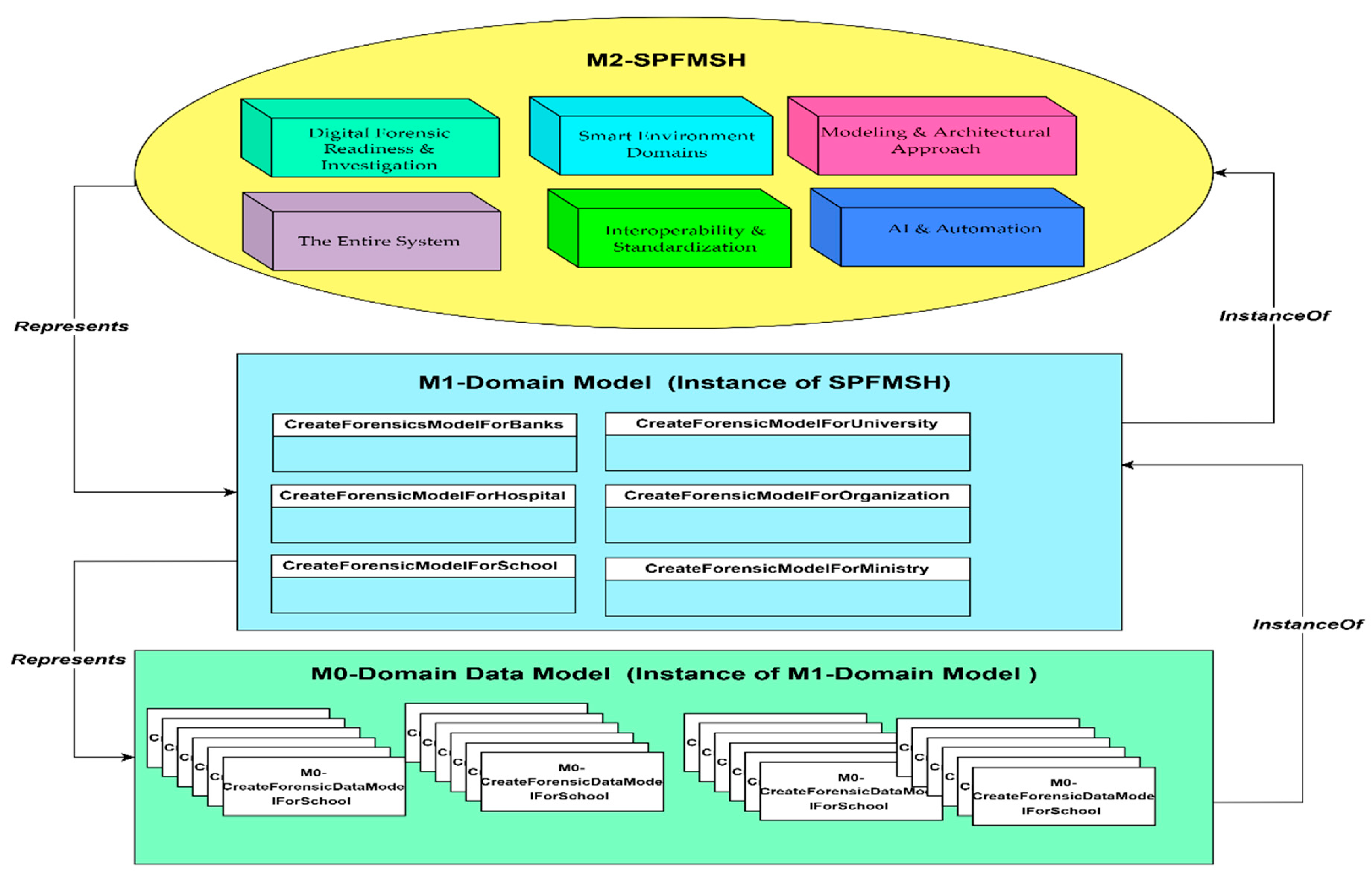
- Identifying relationships among developed concepts: Creates a structured network of interactions among the eight common concept groups developed from literature. These relationships define how each concept influences or supports others within the proactive forensic metamodel for smart homes. Table 6 shows the relationships among these concepts. The output of this step is the developed SPFMSH, which is illustrated in Figure 3.
- ✓
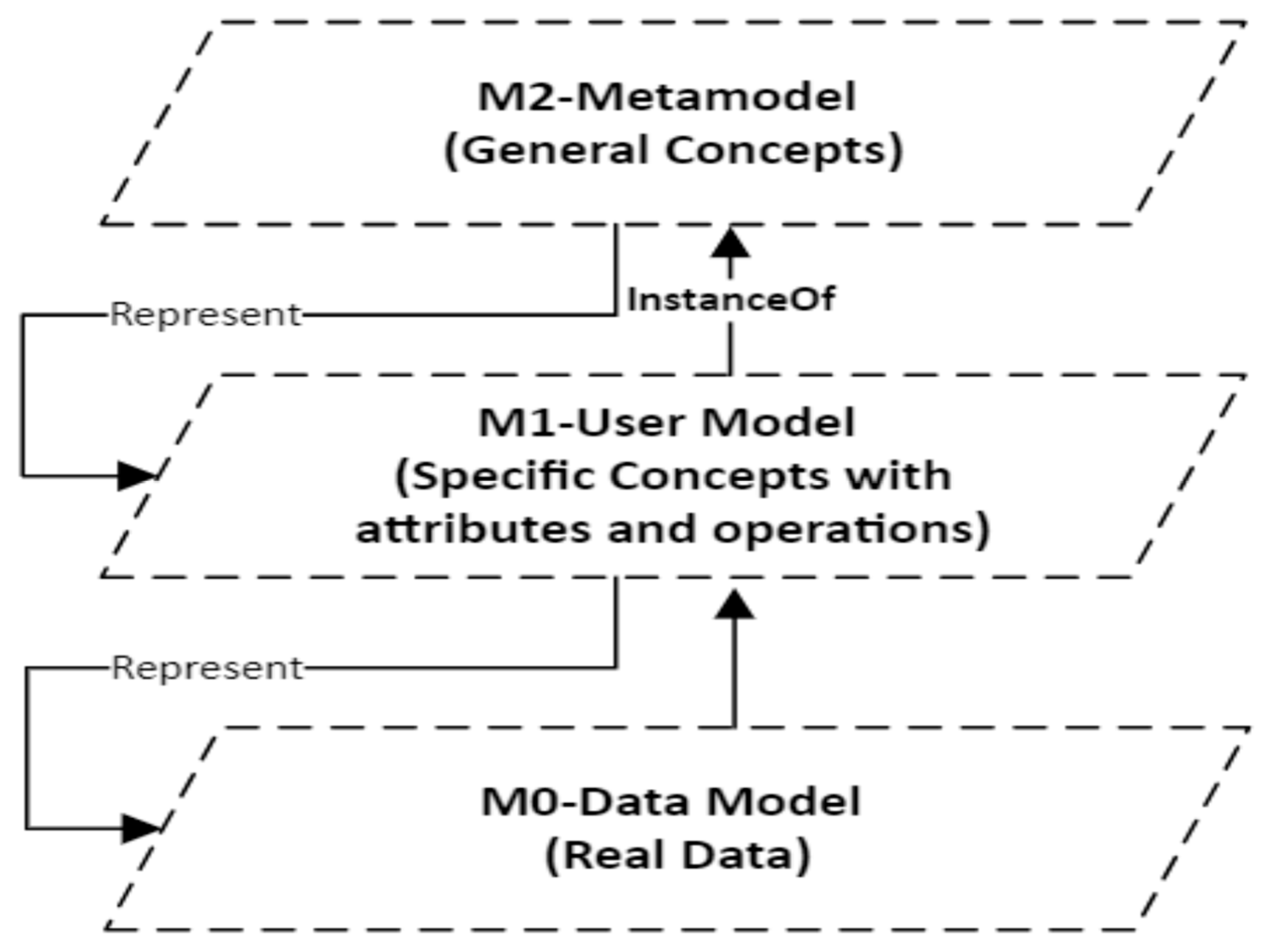
- Level 1 (M1-Instance Level): The actual runtime data, specific devices, and individual forensic cases (e.g., a specific log file from a specific camera).
- ✓
- Level 2 (M2-Model Level): The models that define the structure for Level 1 (e.g., the SPFMSH concepts and their relationships defined in this paper).
- ✓
- Level 3 (M3-Metamodel Level): The language used to define the models at Level 2 (e.g., the rules of metamodeling itself, like using concepts and relationships).
- 6.
- Validating stage: The validation of the SPFMSH was meticulously designed to thoroughly assess its practicality and efficacy, addressing the common concern that new models often lack comprehensive evaluation. Our approach was systematic: initially, by conducting a detailed comparison with existing models to highlight improvements; secondly, by implementing it in real-world contexts to evaluate its operational effectiveness and feasibility; and ultimately, by soliciting expert reviews to verify its relevance and face validity. This comprehensive strategy ensures the model is robust, reliable, and well-prepared for subsequent development phases. The validation process involves three strong techniques: comparison with existing models [43], real-world scenarios [44], and face validity [45].
- (1)
- Comparison with existing models: This comparison highlights that the developed SPFMSH is designed to be a practical, holistic, and specialized solution that directly addresses the key gaps identified in Section 2. It moves beyond theoretical proposals and narrow applications by offering a validated, ready, interoperable, and proactive framework specifically tailored for Saudi Arabia’s ambitious digital transformation in the smart home environment. Table 9 compares the developed SPFMSH with existing models.
- (2)
- Real-World Scenarios: The validation of SPFMSH would be grounded in applying it to realistic, high-impact scenarios within the Saudi smart home context. This approach tests the model’s practical effectiveness, moving beyond theoretical comparison. The developed SPFMSH would be tested against a range of standard and sophisticated cyberattack scenarios relevant to smart homes, such as:
- (a)
- Scenario 1: Unauthorized Access and Intrusion: To evaluate the SPFMSH within an authentic Saudi context, the author simulate an unauthorized access and intrusion on a smart home configuration representative of typical residential compounds in Riyadh, incorporating devices that are prevalent in the Saudi market. This scenario is designed to assess SPFMSH’s core proactive and forensic capabilities during a realistic smart home breach. It aims to simulate an attacker gaining access through a typical IoT device vulnerability and then move laterally within the network. SPFMSH’s performance will be assessed based on its early breach detection, automatic preservation of forensic evidence, and ability to generate a detailed investigative timeline. The attack narrative and technical execution involve exploiting a known vulnerability (e.g., CVE-2021-28372) in a popular IP-based smart indoor security camera that uses weak default credentials (admin/admin), which the homeowner never changed. There are three steps to the attack:
- ▪
- Step 1: Initial Compromise: The attacker uses a scanning tool (e.g., Shodan) to locate internet-exposed cameras in Saudi Arabia and then successfully performs a brute-force or default credential login on the target camera.
- ▪
- Step 2: Foothold and Persistence: The attacker exploits the camera’s firmware vulnerability to upload a malicious script, establishing a reverse shell connection to a command-and-control (C2) server they control. The script is configured to persist across device reboots.
- ▪
- Step 3: Lateral Movement: From the compromised camera, the attacker performs network reconnaissance (e.g., using nmap) to discover other devices on the home Wi-Fi network. The attacker identifies a network-attached storage (NAS) device containing personal family documents and photos. They attempt to exploit another vulnerability or use credentials harvested from the camera’s memory to access the NAS.
- (b)
- Scenario 2: Data Exfiltration and Privacy Breach: To evaluate the SPFMSH within an authentic Saudi context, the author simulate a data exfiltration and privacy breach on a smart home configuration representative of typical residential compounds in Riyadh, incorporating devices that are prevalent in the Saudi market. This scenario tests the Smart Proactive Forensic Meta-model for Smart Homes (SPFMSH) against a sophisticated, covert privacy breach: sensitive data theft. Unlike brute-force or destructive ransomware, data exfiltration is often stealthy, posing a significant challenge to traditional security. The aim is to evaluate the model’s capacity not just to detect these threats but to do so proactively, prevent data loss, and automatically ensure a forensically sound evidence chain for investigations and legal purposes. The attack starts with a clever initial compromise, where the attacker exploits a vulnerability in a central smart home device, such as a smart hub or an insecure IoT device like a voice assistant or thermostat. Access may be compromised by phishing, credential stuffing, or exploiting unpatched software. This step is vital, as it establishes a foothold in the trusted home network often without triggering basic security alarms. Once inside the network, the attacker engages in lateral movement to locate high-value targets. Using network reconnaissance tools, they scan the network to identify devices that store sensitive personal data. The primary target in this scenario is a Network-Attached Storage (NAS) device, which typically contains a treasure trove of personal information such as financial records, family photos, identity documents, and private communications. The attacker may then employ privilege escalation techniques to acquire the necessary access rights to read and copy data from this device, subsequently moving laterally from a low-privilege IoT device to a critical data repository. The core of the attack involves the stealthy exfiltration of the data. To avoid detection by traditional security measures that might flag large, unencrypted transfers, the attacker employs advanced techniques. These include encrypting the stolen files before transmission and using covert channels to send the data to an external server under their control. Typical methods involve hiding data within encrypted HTTPS traffic, which appears normal to simple inspection, or using DNS tunneling, where data is encoded into DNS query and response packets. This stealth makes exfiltration very hard to detect without advanced, AI-driven behavioral measures analysis.
- (c)
- Scenario 3: Device Hijacking and Ransomware: To enhance our understanding of the SPFMSH in a real Saudi environment, the author simulate device hijacking and ransomware attacks on a smart home setup that reflects typical residential compounds in Riyadh, including devices commonly found in the Saudi market. This scenario is designed to evaluate SPFMSH’s core proactive and forensic capabilities during a realistic smart home breach. It aims to mimic an attacker gaining access through a typical IoT device vulnerability and then moving laterally within the network. SPFMSH’s performance will be assessed based on its early breach detection, automatic preservation of forensic evidence, and ability to generate a comprehensive investigative timeline. This scenario was created to test SPFMSH’s ability to defend against one of the most disruptive and damaging types of cyberattacks: ransomware. The goal is to determine how effectively SPFMSH detects, responds to, and investigates an attack that attempts to take control of smart home devices, encrypt their data or functionality, and hold them hostage for ransom. This scenario is vital for smart homes because it extends beyond data privacy to threaten the core principles of availability and integrity, which could render essential home systems inoperable and cause significant inconvenience to residents.
- (3)
- Expert Evaluation: The third validation method is face validity. During SPFMSH validation, an expert assessment was carried out to assess the SPFMSH’s applicability, robustness, and relevance to the Saudi smart home setting. This evaluation was led by two distinguished specialists: Dr. Arafat Aldhaqm, a digital forensics expert, and Dr. Abdulaleem Ali, a specialist in cybersecurity and model-driven engineering. The process involved a comprehensive approach, including structured interviews to assess conceptual integrity and a checklist review of criteria such as completeness, applicability, and relevance to Saudi Arabia. Additionally, the experts conducted a scenario-based walkthrough to test the model’s performance against specified cyberattacks. The feedback from the experts was overwhelmingly positive, acknowledging SPFMSH’s novelty and comprehensiveness. Key strengths highlighted included its holistic design, which successfully integrates multiple domains like security, forensics, and AI into a unified framework. The proactive focus on automated evidence collection and AI-driven threat detection was praised as a forward-looking approach. A significant strength noted was the SPFMSH’s cultural and regional alignment with Saudi Arabia’s specific infrastructure and Vision 2030 objectives, making it more actionable than a generic international framework.
- (4)
- Tracing/Traceability [43]: This technique is devised to evaluate the degree of alignment between the metamodel and the domain, ensuring that all components integrate coherently into models. The SPFMSH metamodel serves not only as a figure depicting the concepts and their relationships but also as a semantic language for the mobile forensics domain. This allows domain forensic practitioners to derive/instantiate several solution models from the SPFMSH metamodel. Therefore, the metamodel transformation is a technique used to validate the logicalness and correctness of the developed metamodel. Transformation is the process of creating a solution model based on a metamodel [46]. Transformation definitions enable a solution model to be transferred from a metamodel to solve a specific problem. The transformation rule describes how a concept in the source metamodel can be translated into a concept in the target metamodel. For metamodels to be useful in practice, transformations on an abstraction hierarchy should be accepted [47]. A vertical transformation is a metamodel transformation that instantiates solution models from the metamodel.
4. Findings and Discussion
5. Conclusions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Albaqami, S.; Nekovee, M.; Khan, I. Identifying and Resolving Cybersecurity Challenges in the IoT in Saudi Arabian Startups Using Blockchain Technology. In Proceedings of the 2024 International Conference on IT Innovation and Knowledge Discovery (ITIKD), Manama, Bahrain, 13–15 April 2025; IEEE: New York, NY, USA, 2025; pp. 1–13. [Google Scholar][Green Version]
- Sharma, M.; Kohli, R.K.; Sharma, K. Tomorrow’s Shields: Exploring Future Trends in Cyber Security and Forensics. In Securing the Digital Frontier: Threats and Advanced Techniques in Security and Forensics; Wiley-Scrivener Publishing LLC: Beverly, MA, USA, 2025; pp. 367–385. [Google Scholar][Green Version]
- Ma, Q.; Kaczmarek-Heß, M.; de Kinderen, S. Validation and verification in domain-specific modeling method engineering: An integrated life-cycle view. Softw. Syst. Model. 2023, 22, 647–666. [Google Scholar] [CrossRef]
- Alotibi, G. A High Abstract Digital Forensic Readiness Metamodel for Securing Smart Cities. IEEE Access 2024, 12, 187427–187443. [Google Scholar] [CrossRef]
- Alotaibe, D.Z. IoT Security Model for Smart Cities based on a Metamodeling Approach. Eng. Technol. Appl. Sci. Res. 2024, 14, 14109–14118. [Google Scholar] [CrossRef]
- Houghton, J.T.; Ding, Y.; Griggs, D.J.; Noguer, M.; van der Linden, P.J.; Dai, X.; Maskell, K.; Johnson, C.A. Climate Change 2001; Cambridge University Press: Cambridge, UK, 2001. [Google Scholar]
- ISO/IEC 27043: 2015; Information Technology—Security Techniques—Incident Investigation Principles and Processes. International Organization for Standardization: Geneva, Switzerland, 2015.
- Bajramovic, E.; Waedt, K.; Ciriello, A.; Gupta, D. Forensic readiness of smart buildings: Preconditions for subsequent cybersecurity tests. In Proceedings of the 2016 IEEE International Smart Cities Conference (ISC2), Trento, Italy, 12–15 September 2016; IEEE: New York, NY, USA, 2016; pp. 1–6. [Google Scholar]
- Philomin, S.; Singh, A.; Ikuesan, A.; Venter, H. Digital forensic readiness framework for smart homes. In Proceedings of the 15th International Conference on Cyber Warfare and Security, ICCWS 2020, Norfolk, VA, USA, 12–13 March 2020. [Google Scholar]
- Kebande, V.R.; Mudau, P.P.; Ikuesan, R.A.; Venter, H.S.; Choo, K.-K.R. Holistic digital forensic readiness framework for IoT-enabled organizations. Forensic Sci. Int. Rep. 2020, 2, 100117. [Google Scholar] [CrossRef]
- Oriwoh, E.; Sant, P. The forensics edge management system: A concept and design. In Proceedings of the 2013 IEEE 10th International Conference on Ubiquitous Intelligence and Computing and 2013 IEEE 10th International Conference on Autonomic and Trusted Computing, Washington, DC, USA, 18–21 December 2013; IEEE: New York, NY, USA, 2013; pp. 544–550. [Google Scholar]
- Kebande, V.R.; Ray, I. A generic digital forensic investigation framework for internet of things (iot). In Proceedings of the 2016 IEEE 4th International Conference on Future Internet of Things and Cloud (FiCloud), Vienna, Austria, 22–24 August 2016; IEEE: New York, NY, USA, 2016; pp. 356–362. [Google Scholar]
- Ngobeni, S.; Venter, H.; Burke, I. A forensic readiness model for wireless networks. In Proceedings of the IFIP International Conference on Digital Forensics, Hong Kong, China, 4–6 January 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 107–117. [Google Scholar]
- Cebe, M.; Erdin, E.; Akkaya, K.; Aksu, H.; Uluagac, S. Block4forensic: An integrated lightweight blockchain framework for forensics applications of connected vehicles. IEEE Commun. Mag. 2018, 56, 50–57. [Google Scholar] [CrossRef]
- Kim, S.; Park, M.; Lee, S.; Kim, J. Smart home forensics—Data analysis of IoT devices. Electronics 2020, 9, 1215. [Google Scholar] [CrossRef]
- Kim, S.; Jo, W.; Lee, J.; Shon, T. AI-enabled device digital forensics for smart cities. J. Supercomput. 2022, 78, 3029–3044. [Google Scholar] [CrossRef]
- Cicirelli, F.; Fortino, G.; Guerrieri, A.; Spezzano, G.; Vinci, A. Metamodeling of smart environments: From design to implementation. Adv. Eng. Inform. 2017, 33, 274–284. [Google Scholar] [CrossRef]
- Afroze, F.M.; Poornima, V. Comparative Study of the IoT Forensics Framework Using AI/ML Approaches for the Detection and Prevention of Cyberattacks. In Proceedings of the International Conference on Computing and Communication Networks, Bangkok, Thailand, 20–22 December 2024; Springer: Berlin/Heidelberg, Germany, 2024; pp. 659–668. [Google Scholar]
- Alhussan, A.A.; Al-Dhaqm, A.; Yafooz, W.M.S.; Razak, S.B.A.; Emara, A.-H.M.; Khafaga, D.S. Towards development of a high abstract model for drone forensic domain. Electronics 2022, 11, 1168. [Google Scholar] [CrossRef]
- Alotaibi, F.M.; Al-Dhaqm, A.; Al-Otaibi, Y.D.; Alsewari, A.A. A Comprehensive Collection and Analysis Model for the Drone Forensics Field. Sensors 2022, 22, 6486. [Google Scholar] [CrossRef]
- Alotaibi, F.; Al-Dhaqm, A.; Al-Otaibi, Y.D. A Conceptual Digital Forensic Investigation Model Applicable to the Drone Forensics Field. Eng. Technol. Appl. Sci. Res. 2023, 13, 11608–11615. [Google Scholar] [CrossRef]
- Bashir, M.R.; Gill, A.Q.; Beydoun, G.; Mccusker, B. Big data management and analytics metamodel for IoT-enabled smart buildings. IEEE Access 2020, 8, 169740–169758. [Google Scholar] [CrossRef]
- Melo, P.C.F. A model-driven middleware approach to reduce the semantic gap between application domains and the generic infrastructure of smart cities. In Proceedings of the 2021 ACM/IEEE International Conference on Model Driven Engineering Languages and Systems Companion (MODELS-C), Virtual, 10–15 October 2021; IEEE: New York, NY, USA, 2021; pp. 672–677. [Google Scholar]
- Rossi, M.T. Supporting Smart Cities Quality Evaluation Exploiting Model-Driven Engineering. Ph.D. Thesis, Scuola Normale Superiore, Pisa, Italy, 2023. [Google Scholar]
- Fortino, G.; Guerrieri, A.; Russo, W.; Savaglio, C. Towards a development methodology for smart object-oriented IoT systems: A metamodel approach. In Proceedings of the 2015 IEEE International Conference on Systems, Man, and Cybernetics, Hong Kong, China, 9–12 October 2015; IEEE: New York, NY, USA, 2015; pp. 1297–1302. [Google Scholar]
- Benaddi, L.; Souha, A.; Ouaddi, C.; Jakimi, A.; Ouchao, B. Towards a unified metamodel for developing the conversational agents for smart tourism. Procedia Comput. Sci. 2024, 236, 241–247. [Google Scholar] [CrossRef]
- Mercuri, A.; Spezzano, G.; Vinci, A. Exploiting the SEM Framework for Modeling Smart Cities. In Internet and Distributed Computing Systems, Proceedings of the 10th International Conference, IDCS 2017, Mana Island, Fiji, 11–13 December 2017; Springer: Berlin/Heidelberg, Germany, 2018; p. 95. [Google Scholar]
- Basciani, F.; Rossi, M.T.; De Sanctis, M. Supporting smart cities modeling with graphical and textual editors. In Proceedings of the {STAF} 2020 Workshop Proceedings: 4th Workshop on Model-Driven Engineeringfor the Internet-of-Things, 1st International Workshop on ModelingSmart Cities, and 5th International Workshop on Open and OriginalProblems in Software Language Engineering Co-Locat; CEUR-WS.org, Bergen, Norway, 22–26 June 2020; Volume 2707, pp. 9–19. [Google Scholar]
- dos Santos, P.; Campos-Rebelo, R.; Mesquita, R. IoT Sensor-Node Generic Metamodel Supporting Real Time Device Emulation. In Proceedings of the 2025 9th International Young Engineers Forum on Electrical and Computer Engineering (YEF-ECE), Lisbon, Portugal, 4 July 2025; IEEE: New York, NY, USA, 2025; pp. 86–91. [Google Scholar]
- Gondhalekar, G.; Tewari, D.; Bhardwaj, I.; Ponnusamy, S. Internet of Things Integration in Smart Cities Enhancing Urban Living through Connected Technologies. ITM Web Conf. 2025, 76, 3001. [Google Scholar] [CrossRef]
- Horalek, J.; Otcenaskova, T.; Sobeslav, V.; Tucnik, P. A business process and data modelling approach to enhance cyber security in smart cities. In Proceedings of the International Conference on Nature of Computation and Communication, Ho Chi Minh City, Vietnam, 26–27 October 2023; Springer: Berlin/Heidelberg, Germany, 2023; pp. 70–84. [Google Scholar]
- Bastidas, V.; Reychav, I.; Ofir, A.; Bezbradica, M.; Helfert, M. Concepts for modeling smart cities: An ArchiMate extension. Bus. Inf. Syst. Eng. 2022, 64, 359–373. [Google Scholar] [CrossRef]
- Afonso, R.A. Smartcluster: A Metamodel of Indicators for Smart and Human Cities. Master’s Thesis, Universidade Federal de Pernambuco, Recife, Brazil, 2017. [Google Scholar]
- Rowlingson, R. A ten step process for forensic readiness. Int. J. Digit. Evid. 2004, 2, 1–28. [Google Scholar]
- Sarkis-Onofre, R.; Catalá-López, F.; Aromataris, E.; Lockwood, C. How to properly use the PRISMA Statement. Syst. Rev. 2021, 10, 117. [Google Scholar] [CrossRef]
- Peffers, K.; Tuunanen, T.; Rothenberger, M.A.; Chatterjee, S. A design science research methodology for information systems research. J. Manag. Inf. Syst. 2007, 24, 45–77. [Google Scholar] [CrossRef]
- Gómez, A.A.; Caro, M.F. Meta-Modeling process of pedagogical strategies in intelligent tutoring systems. In Proceedings of the 2018 IEEE 17th International Conference on Cognitive Informatics & Cognitive Computing (ICCI* CC), Berkeley, CA, USA, 16–18 July 2018; IEEE: New York, NY, USA, 2018; pp. 485–494. [Google Scholar]
- Bogen, A.C.; Dampier, D.A. Unifying computer forensics modeling approaches: A software engineering perspective. In Proceedings of the First International Workshop on Systematic Approaches to Digital Forensic Engineering (SADFE’05), Washington, DC, USA, 7–9 November 2005; IEEE: New York, NY, USA, 2005; pp. 27–39. [Google Scholar]
- Ali, A.; Abd Razak, S.; Othman, S.H.; Mohammed, A. Extraction of common concepts for the mobile forensics domain. In Proceedings of the International Conference of Reliable Information and Communication Technology, Johor Bahru, Malaysia, 23–24 April 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 141–154. [Google Scholar]
- Othman, S.H.; Beydoun, G. A metamodel-based knowledge sharing system for disaster management. Expert Syst. Appl. 2016, 63, 49–65. [Google Scholar] [CrossRef][Green Version]
- Salem, M.; Othman, S.H.; Al-Dhaqm, A.; Ali, A. Development of Metamodel for Information Security Risk Management. In Kids Cybersecurity Using Computational Intelligence Techniques; Springer: Berlin/Heidelberg, Germany, 2023; pp. 243–253. [Google Scholar][Green Version]
- Fellbaum, C. WordNet. In Theory and Applications of Ontology: Computer Applications; Springer: Berlin/Heidelberg, Germany, 2010; pp. 231–243. [Google Scholar][Green Version]
- Sargent, R.G. Verification and validation of simulation models. In Proceedings of the 2010 Winter Simulation Conference, Ithaca, NY, USA, 5–8 December 2010; IEEE: New York, NY, USA, 2010; pp. 166–183. [Google Scholar][Green Version]
- Beattie, J.R. Reflections of the real-world in the unreal, using simulation to design complex real-world validation studies for spectroscopy. J. Raman Spectrosc. 2021, 52, 2683–2698. [Google Scholar] [CrossRef]
- Ahmad, M.N.; Colomb, R.M.; Sadiq, S.W. A UML profile for perdurant ontology of domain interlocking Institutional Worlds. Int. J. Internet Enterp. Manag. 2010, 6, 213–232. [Google Scholar] [CrossRef]
- Mens, T.; Van Gorp, P. A taxonomy of model transformation. Electron. Notes Theor. Comput. Sci. 2006, 152, 125–142. [Google Scholar] [CrossRef]
- Falkenberg, E.; Hesse, W.; Lindgreen, P.; Nilsson, B.; Oei, H.; Rolland, C.; Stamper, R.; Van Assche, F.; Verrijn-Stuart, A.; Voss, K. A Framework of Information System Concepts; International Federation for Information Processing: Laxenburg, Austria, 1998. [Google Scholar]
- Rose, L.M.; Kolovos, D.S.; Paige, R.F.; Polack, F.A.C. Model migration with epsilon flock. In Proceedings of the International Conference on Theory and Practice of Model Transformations, Malaga, Spain, 2–28 July 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 184–198. [Google Scholar]




| ID | References | Advantages | Disadvantages | Methodology |
|---|---|---|---|---|
| 1 | [6] | Offers a thorough, peer-reviewed scientific consensus on climate change, establishing it as a highly trustworthy source. | Since 2001, significant progress has been made in science. It is more helpful in understanding historical context than for current data. | Synthesis of scientific assessment reports (IPCC). |
| 2 | [7] | Provides an internationally recognized standard for investigation processes, ensuring consistency, reliability, and the legal admissibility of evidence. | Generic and High-level: As a standard, it describes principles and processes but does not provide specific technical implementations or tools. | Standards development (ISO working group). |
| 3 | [8] | One of the first papers to apply forensic readiness principles specifically to the smart building/IoT context. | Focuses on preconditions for testing rather than a whole, implemented framework or model. | Conceptual analysis and framework proposal. |
| 4 | [9] | Develops a dedicated Digital Forensic Readiness (DFR) framework tailored for the complex environment of smart homes. | As a developed framework, its practical effectiveness and real-world validation may not be fully detailed or proven. | Framework design for a specific domain. |
| 5 | [10] | Proposes a comprehensive DFR framework designed for entire IoT-enabled organizations, promoting a top-down strategy. | A holistic organizational framework can be complex and potentially difficult to implement in its entirety. | Holistic framework design. |
| 6 | [11] | An early attempt to design a system (FEMS) for managing forensic data in ubiquitous computing environments. | The concept may not account for the scale and diversity of modern IoT ecosystems. Likely not validated through implementation. | Concept and system design (FEMS). |
| 7 | [12] | Presents a generic digital forensic investigation framework specifically designed for the Internet of Things. | Generic Nature: Being “generic” means it may lack specific details required for particular IoT sub-domains (e.g., smart grids, vehicles). | Generic investigative framework design. |
| 8 | [13] | Early research has adapted DFR principles to the specific challenges of wireless networks. | Wireless technology and security threats have evolved dramatically since 2010, likely limiting its current applicability. | Model development for wireless contexts. |
| 9 | [14] | Proposes integrating blockchain technology to enhance evidence integrity and tamper-resistance for vehicle forensics. | Incorporating blockchain may introduce significant computational, storage, and complexity overhead. | Lightweight blockchain framework design and implementation. |
| 10 | [15] | Provides practical analysis of data from real IoT devices, moving beyond theoretical models to actual evidence. | Findings are likely based on a specific set of devices and may not be fully generalized to all smart home products. | Empirical data analysis from IoT devices. |
| 11 | [16] | Explores the application of AI to automate forensic processes, addressing future scalability challenges in smart cities. | The AI-enabled approach may be developed conceptually without extensive real-world testing or validation. | AI-enabled framework proposal. |
| 12 | [5] | Applies a metamodeling approach to IoT security, providing a high-level, unified method for designing security models. | As a metamodel, it is a design tool rather than an implemented solution; it requires further instantiation to be practical. | Metamodeling approach for security design. |
| 13 | [4] | Proposes a high-abstraction DFR metamodel specifically for smart cities, providing a reusable and flexible design template. | The high level of abstraction means it lacks technical specifics and must be tailored and implemented for concrete use cases. | Metamodel development. |
| 14 | [17] | Demonstrates how metamodeling can effectively connect high-level design with concrete implementation in smart environments. | Technical Complexity: The metamodeling approach may require expertise in MDE, which can be a barrier to adoption. | Metamodeling and model-driven engineering. |
| 15 | [18] | Comparative study focusing on AI/ML for detection and prevention within IoT forensics, a proactive approach. | As a comparative study of frameworks, it may not propose a new, validated solution itself. | Comparative study of AI/ML frameworks. |
| 16 | [19] | Applies structured modeling to the emerging and specific field of drone forensics, addressing a clear gap. | The high abstract model is specific to drones and not directly transferable to other IoT or smart city domains. | High-abstraction model development. |
| 17 | [20] | Proposes a comprehensive model for the drone forensics field, covering collection and analysis. | Similarly to [19], its primary advantage is also its limitation: it is highly specialized for a single domain. | Comprehensive model development. |
| 18 | [21] | Applicable Model: Presents a conceptual investigation model directly applicable to drone forensics, providing a practical methodology. | Conceptual Stage: Labeled as “conceptual,” it may require further validation and testing in real-world investigative scenarios. | Conceptual model development. |
| 19 | [22] | Addresses Big Data Challenge: Focuses on the critical issue of managing and analyzing large data volumes in smart buildings via a metamodel. | Complexity: Big data metamodels can be complex to design and implement effectively within existing building management systems. | Metamodel development for data management. |
| 20 | [22] | Reduces Semantic Gap: Aims to solve interoperability issues in smart cities by using MDE to align domain-specific needs with generic infrastructure. | Academic Focus: The middleware approach might be a theoretical contribution that requires further development for widespread industry adoption. | MDE, and Middleware Design. |
| 21 | [23] | Standardization: Proposes an extension to the widely used ArchiMate standard, allowing for standardized visual modeling of innovative city enterprises. | Modeling Overhead: Requires users to learn and adopt the extended ArchiMate language, which may not be ideal for all stakeholders. | ArchiMate language extension. |
| 22 | [32] | Quality Focus: Uses Model-Driven Engineering to support quality evaluation, a crucial but often overlooked aspect of smart city solutions. | Likely Conceptual: As a conference publication, the approach might be presented as a concept or early work without full validation. | Model-Driven Engineering for evaluation. |
| 23 | [32] | Structured Development: An early proposal for a structured software engineering methodology (based on metamodels) for IoT systems. | Dated and Early stage: The IoT landscape was less mature in 2015; the approach may need updating for current complexities. | Metamodel-based development methodology. |
| 24 | [24] | Human-Centric Metrics: Focuses on defining indicators for measuring smart and human aspects of cities, not just technology. | Theoretical Framework: The “Smart cluster” metamodel is likely a theoretical contribution that requires application and testing in real cities. | Metamodel development (Smart cluster). |
| 25 | [25] | Application-Specific Standardization: Aims to develop a unified metamodel for conversational agents in smart tourism, supporting progress and efficiency. | Very Narrow Focus: The utility of the metamodel is confined to the specific application of conversational agents in tourism. | Unified metamodel development. |
| 26 | [33] | This study developed a comprehensive metamodel, bringing together technology-focused “smart city” indicators with quality-of-life-oriented “human city” indicators. This creates a well-rounded urban assessment framework that moves beyond a purely technocratic view. | However, it is mostly theoretical and conceptual in nature. Although it offers a clear set of clustered indicators, it has not been tested with real-world case studies, so its practical use, scalability, and handling of data challenges remain to be seen. | Framework exploitation (SEM). |
| 27 | [26] | This study offered a practical examination of a conversational agent developed for smart tourism, utilizing Bot Framework Composer, and presents a valuable comparison of development tools. | Although it demonstrated strengths in real-world application, it also exhibits certain limitations, including a focus on a single tool, the theoretical nature of the proposed metamodel without empirical validation or user data, and the lack of a validated, unified Domain-Specific Language (DSL), which warrants further investigation in future research. | Development of graphical/textual editors. |
| 28 | [27] | This study introduced the SEM framework as a UML-based methodology that integrates both functional and data perspectives to address design deficiencies for complex Smart Cities. | However, it cannot evaluate the framework’s application, implementation, or validation, as well as its effectiveness. | Generic metamodel design for emulation. |
| 29 | [28] | Offers a recent overview of the benefits of IoT integration, serving as a valuable introductory reference for enhancing urban living. | As a conference paper, it probably offers a summary or perspective rather than a novel technical or methodological contribution. | Integrative review/discussion. |
| 30 | [29] | Integrates business process modeling with data modeling to enhance cybersecurity, connecting technical and organizational views. | Successfully merging business processes and technical security models can be a complex undertaking for organizations. | Business process and data modeling. |
| 31 | [34] | One of the first to propose a straightforward, step-by-step process for implementing forensic readiness, making the concept actionable. | Pre-dates the complexities of modern IoT and smart cities. It is a high-level guide that lacks specifics for contemporary digital environments. | Procedural model development (10-step process). |
| 32 | [30] | Provides a comprehensive, peer-reviewed scientific consensus on climate change, making it a highly credible source. | Science has advanced significantly since 2001. It is more helpful in establishing historical context than current data. | Synthesis of scientific assessment reports (IPCC). |
| 33 | [31] | Pioneering and Practical: One of the first to propose a straightforward, step-by-step process for implementing forensic readiness, making the concept actionable. | Pre-dates the complexities of modern IoT and smart cities. It is a high-level guide that lacks specifics for contemporary digital environments. | Procedural model development (10-step process). |
| ID | References | Scope | Perspective |
|---|---|---|---|
| 1 | [6] | Global climate change. | Scientific, Environmental. |
| 2 | [7] | General incident investigation processes. | Standardization, Best Practices. |
| 3 | [8] | IoT-enabled Smart Buildings. | Research, Proactive Security. |
| 4 | [9] | Smart Home environments. | Academic, Domain-Specific. |
| 5 | [10] | Organizational-level IoT security. | Strategic, Organizational. |
| 6 | [11] | Ubiquitous computing environments. | Architectural, Conceptual. |
| 7 | [12] | Internet of Things (IoT) ecosystems. | Investigative, Generic. |
| 8 | [13] | Wireless Networks. | Academic, Network Security. |
| 9 | [14] | Connected Vehicles. | Technical, Cryptographic. |
| 10 | [15] | IoT Devices in Smart Homes. | Technical, Data-Centric. |
| 11 | [16] | IoT devices within Smart Cities. | Futuristic, Automation. |
| 12 | [5] | Smart City IoT Security. | Design, Abstract Modeling. |
| 13 | [4] | Smart City Security and Forensics. | Strategic, Abstract Modeling. |
| 14 | [17] | Smart Environments design-to-implementation. | Software Engineering, MDE. |
| 15 | [18] | IoT Forensics Frameworks. | Analytical, Comparative. |
| 16 | [19] | Drone Forensics Domain. | Domain-Specific Modeling. |
| 17 | [20] | Drone Forensics Field. | Domain-Specific, Process-Oriented. |
| 18 | [21] | Drone Forensics Investigations. | Conceptual, Investigative. |
| 19 | [22] | IoT-enabled Smart Buildings (Big Data). | Data-Centric, Architectural. |
| 20 | [22] | Smart City Infrastructure and Applications. | Software Engineering, Interoperability. |
| 21 | [23] | Smart City Enterprise Architecture. | Enterprise Architecture, Standardization. |
| 22 | [32] | Smart City Quality Evaluation. | Evaluative, MDE. |
| 23 | [32] | Smart Object-Oriented IoT Systems. | Software Development, Methodological. |
| 24 | [24] | Smart and Human Cities (Indicator metrics). | Metric-Based Urban Planning. |
| 25 | [25] | Conversational Agents for Smart Tourism. | Domain-Specific, Application Design. |
| 26 | [33] | Smart City Modeling. | Modeling, Conceptual. |
| 27 | [26] | Smart City Modeling Tools. | Tool-Oriented, Practical MDE. |
| 28 | [27] | IoT Sensor-Node Emulation. | Development, Testing. |
| 29 | [28] | IoT integration in Smart Cities. | Overview, Urban Living. |
| 30 | [29] | Smart City Cybersecurity. | Business-Centric, Holistic Security. |
| 31 | [34] | General organizational digital forensics. | Organizational, Process-oriented. |
| 32 | [30] | Global climate change. | Scientific, Environmental. |
| 33 | [31] | General organizational digital forensics. | Organizational, Process-oriented. |
| ID | References | Scope | Perspective |
|---|---|---|---|
| 1 | [8] | IoT-enabled Smart Buildings. | Research, Proactive Security. |
| 2 | [9] | Smart Home environments. | Academic, Domain-Specific. |
| 3 | [10] | Organizational-level IoT security. | Strategic, Organizational. |
| 4 | [15] | IoT Devices in Smart Homes. | Technical, Data-Centric. |
| 5 | [16] | IoT devices within Smart Cities. | Futuristic, Automation. |
| 6 | [5] | Smart City IoT Security. | Design, Abstract Modeling. |
| 7 | [4] | Smart City Security and Forensics. | Strategic, Abstract Modeling. |
| 8 | [18] | IoT Forensics Frameworks. | Analytical, Comparative. |
| 9 | [20] | Drone Forensics Field. | Domain-Specific, Process-Oriented. |
| 10 | [21] | Drone Forensics Investigations. | Conceptual, Investigative. |
| 11 | [22] | IoT-enabled Smart Buildings (Big Data). | Data-Centric, Architectural. |
| 12 | [22] | Smart City Infrastructure and Applications. | Software Engineering, Interoperability. |
| 13 | [23] | Smart City Enterprise Architecture. | Enterprise Architecture, Standardization. |
| 14 | [32] | Smart City Quality Evaluation. | Evaluative, MDE. |
| 15 | [32] | Smart Object-Oriented IoT Systems. | Software Development, Methodological. |
| 16 | [24] | Smart and Human Cities (Indicator metrics). | Metric-Based Urban Planning. |
| 17 | [33] | Smart City Modeling. | Modeling, Conceptual. |
| 18 | [26] | Smart City Modeling Tools. | Tool-Oriented, Practical MDE. |
| 19 | [28] | IoT integration in Smart Cities. | Overview, Urban Living. |
| 20 | [29] | Smart City Cybersecurity. | Business-Centric, Holistic Security. |
| 21 | [34] | General organizational digital forensics. | Organizational, Process-oriented. |
| ID | References | Extracted Concepts |
|---|---|---|
| 1 | [8] | IoT, Smart Buildings, Forensic Readiness, Proactive Security, Cybersecurity Tests, Preconditions |
| 2 | [9] | Smart Home, Digital Forensic Readiness Framework, Domain-Specific, Academic |
| 3 | [10] | Organizational-level, IoT Security, Holistic Framework, Digital Forensic Readiness, Strategic |
| 4 | [15] | IoT Devices, Smart Homes, Data Analysis, Technical, Data-Centric Forensics |
| 5 | [16] | Smart Cities, AI-enabled, Device Digital Forensics, Automation, Futuristic |
| 6 | [5] | IoT Security, Smart Cities, Metamodeling Approach, Abstract Modeling, Design |
| 7 | [4] | Smart City Security, Digital Forensic Readiness, Metamodel, High Abstract, Strategic |
| 8 | [18] | IoT Forensics Framework, AI, Machine Learning, Cyberattacks, Detection, Prevention, Comparative Study, Analytical |
| 9 | [20] | Drone Forensics, Collection Model, Analysis Model, Domain-Specific, Process-Oriented |
| 10 | [21] | Drone Forensics, Digital Forensic Investigation Model, Conceptual, Investigative |
| 11 | [22] | Smart Buildings, Big Data, Data Management, Analytics Metamodel, IoT-enabled, Architectural, Data-Centric |
| 12 | [22] | Smart City Infrastructure, Applications, Software Engineering, Interoperability, Model-Driven Middleware, Semantic Gap |
| 13 | [23] | Smart City, Enterprise Architecture, Standardization, Architectural Framework |
| 14 | [32] | Smart City, Quality Evaluation, Model-Driven Engineering (MDE), Evaluative |
| 15 | [32] | Smart Object-Oriented, IoT Systems, Software Development, Methodological |
| 16 | [24] | Smart Cities, Human Cities, Indicator Metrics, Metric-Based, Urban Planning |
| 17 | [33] | Smart City Modeling, Conceptual Modeling, Urban Development |
| 18 | [26] | Smart City Modeling Tools, Tool-Oriented, Practical MDE, Development Tools |
| 19 | [28] | IoT Integration, Smart Cities, Overview, Urban Living, Technology Adoption |
| 20 | [29] | Smart City Cybersecurity, Business-Centric, Holistic Security, Risk Management |
| 21 | [34] | Organizational Digital Forensics, Process-oriented, Forensic Investigation, Readiness |
| Proposed Common Concept | Description | Related Extracted Concepts |
|---|---|---|
| Digital Forensic Readiness and Investigation | Frameworks and processes are designed to prepare for, support, and proactively conduct digital forensic analyses. | Forensic Readiness, Proactive Security, Digital Forensic Investigation Model, Process-Oriented, Collection Model, Analysis Model, Conceptual, Investigative |
| Smart Environment Domains | The specific IoT-enabled domains where the frameworks and models are applied. | Smart Buildings, Smart Homes, Smart Cities, Drone Forensics, IoT Devices |
| Modeling and Architectural Approach | The methodology used to design, conceptualize, and structure the solutions often focuses on abstraction and standardization. | Metamodeling Approach, Abstract Modeling, Holistic Framework, Architectural Framework, Conceptual Modeling, Model-Driven Engineering (MDE), Enterprise Architecture |
| Security and Risk Management | Proactive and strategic measures to protect systems, detect threats, and manage cybersecurity risks. | Cybersecurity Tests, Preconditions, Proactive Security, Holistic Security, Risk Management, Cyberattacks, Detection, Prevention |
| Data-Centric Processing | Methods focused on the management, analysis, and extraction of intelligence from data generated within smart environments. | Data Analysis, Data Management, Analytics, Data-Centric Forensics, Big Data |
| AI and Automation | The use of advanced computational techniques enables automation, enhances analysis, and improves system capabilities. | AI-enabled, Automation, Machine Learning, AI |
| Interoperability and Standardization | Efforts to ensure systems and components can work together through common standards, models, and semantic understanding. | Standardization, Interoperability, Model-Driven Middleware, Semantic Gap, Indicator Metrics, Quality Evaluation |
| The Entire System | Represents the holistic framework from all seven conceptual groups, embodying a proactive forensic ecosystem for smart homes that ensures cybersecurity, automated evidence preservation, and forensic readiness through interoperability and automation. | Holistic Framework, Integrated System, Proactive Ecosystem, Forensic Readiness, Cybersecurity, Interoperability, Automation, Smart Home Environment |
| Source Concept | Relationship | Target Concept |
|---|---|---|
| Modeling and Architectural Approach | Provides The Blueprint For | Interoperability and Standardization |
| Interoperability and Standardization | Defines Standards For | Modeling and Architectural Approach |
| Modeling and Architectural Approach | Guides The Design Of | Smart Environment Domains |
| Smart Environment Domains | Generate | Data-Centric Processing |
| Smart Environment Domains | Are Protected By | Security and Risk Management |
| Data-Centric Processing | Provides Input For | AI and Automation |
| Security and Risk Management | Enhances The Capabilities Of | AI and Automation |
| AI and Automation | Is Leveraged By | Security and Risk Management |
| Data-Centric Processing | Provides Evidence For | Digital Forensic Readiness and Investigation |
| Security and Risk Management | Provides Alerts For | Digital Forensic Readiness and Investigation |
| AI and Automation | Automates Tasks For | Digital Forensic Readiness and Investigation |
| Digital Forensic Readiness and Investigation | Is The Ultimate Goal Of | The Entire System |
| Concept | Main Function | Reusability Assessment |
|---|---|---|
| Digital Forensic Readiness and Investigation | To provide the processes, protocols, and tools to proactively collect evidence and conduct effective investigations after a security incident. | High. This concept is agnostic to the specific domain. The core idea of “readiness” can be reused across IoT domains (smart grids, medical IoT, industrial systems) by instantiating it with domain-specific tools and procedures at Level 1. |
| Smart Environment Domains | It represents the specific IoT-enabled environment (e.g., smart home, smart city, drone ecosystem) where the metamodel is applied. | Medium. While the concept can be reused at Levels 2 and 3, its implementation at Level 1 is specific to the domain. You can apply the idea to a new domain, but the device types, data formats, and threats relevant to a smart home do not directly transfer to, for instance, a smart power grid. |
| Modeling and Architectural Approach | To provide the blueprint. It offers high-level, abstract design principles and structural rules for building secure and forensically ready systems. | Very High. This is the most reusable concept. It exists at Level 3/Metamodel level. The approach of using abstraction, standardization, and metamodeling to manage complexity can be applied to design systems for virtually any complex IoT domain. |
| Security and Risk Management | To enable proactive defense. It encompasses the policies, tools, and processes for threat detection, risk assessment, and triggering incident response. | High. The core principles of proactive security (monitoring, alerting, risk assessment) are highly reusable across domains. Level 1 instantiations (e.g., using a specific AI-based IDS tool) might need configuration for the new domain, but the concept remains the same. |
| Data-Centric Processing | To handle evidentiary data. It defines how the vast amounts of data generated by IoT devices are collected, managed, stored, and pre-processed for forensic analysis. | High. The need to collect, normalize, and preserve data from heterogeneous sources is universal across IoT domains. The protocols and tools defined at Level 2 can be reused; only the data schemas and sources at Level 1 would change. |
| AI and Automation | To provide intelligence and speed. It leverages machine learning and automation to correlate data, detect sophisticated anomalies, and execute automated responses without human intervention. | Very High. The function of using AI for analytics and automation is a cross-cutting concern, highly reusable in any cybersecurity or forensic context. The models at Level 2 might need retraining on new domain data at Level 1, but the architectural concept is perfectly reusable. |
| Interoperability and Standardization | To ensure cohesion. It focuses on ensuring that diverse systems, devices, and data formats can work together through common standards and a shared understanding of semantics. | Very High. This is a foundational, abstract concept (Level 3) crucial for any complex, heterogeneous system like IoT. The drive for standardization and semantic alignment is 100% reusable across all domains. |
| The Entire System | To demonstrate how all seven conceptual groups (like DFR, Smart Domains, AI, etc.) work together synergistically. This integrated system aims to ensure proactive digital forensic readiness, enabling effective investigations following a security incident. This is the fundamental purpose of the entire model. | Very high. The concept constitutes a meta-framework. The idea of integrating security, data management, AI, and forensic processes into a cohesive, proactive system is a universal principle applicable to any complex IoT domain (e.g., smart grids, industrial IoT, healthcare IoT), not solely limited to smart homes. |
| ID | Validation Technique | Evaluation Criteria | Metrics/Measurement Scale |
|---|---|---|---|
| 1 | Comparison with Existing Models | Scope and Applicability: Distinction between practical domain specificity and being overly generic or excessively specialized. Theoretical versus Practical: Inclusion of implementation details and validation within real-world contexts. Proactive Focus: Incorporation of threat anticipation strategies and automated evidence preservation. Integration and Interoperability: Design considerations for managing heterogeneity within the Internet of Things (IoT) ecosystem. Data Handling: Implementation of robust mechanisms for forensic-ready IoT data management. Validation Rigor: Extent and depth of the evaluation methodology. Regional Relevance: Compliance with regulations in the Kingdom of Saudi Arabia (KSA), including NCA and PDPL, and alignment with Vision 2030. | Scale: Low, Medium, High |
| 2 | Real-World Scenario Simulation | Detection Time: Speed of threat identification. Evidence Preservation Rate: Completeness of automatic data capture. Containment Action Efficacy: Success of automated responses in limiting damage. Investigation Timeline Completeness: Accuracy of the automated attack reconstruction. Evidence Integrity: Maintenance of a verifiable chain of custody. | Metrics: Time (e.g., seconds). Metric: Percentage (%) of critical data captured. Metric: Success/Failure for scenario goal. Metric: Percentage (%) of attack kill-chain reconstructed. Scale: Fully Achieved/Partially Achieved/Not Achieved |
| 3 | Expert Evaluation (Face Validity) | Completeness: Encompasses all necessary concepts and relationships. Clarity and Understandability: Concepts and model are well-defined and comprehensible. Relevance: Addresses critical smart home cybersecurity and forensic challenges. Practical Applicability: Can be realistically implemented in KSA smart home infrastructures. Proactive Focus: Effectively shifts the paradigm from reactive to proactive. Cultural and Regulatory Alignment: Adequately addresses KSA standards and Vision 2030. | Scale: Likert Scale (1—Strongly Disagree to Agree 5—Strongly) |
| Aspect | Existing Models | Developed SPFMSH |
|---|---|---|
| Scope and Applicability | Often too generic (e.g., [6,11]) or overly specialized for a single domain like drones (e.g., [20,21]) or smart tourism ([33]), limiting broader applicability. | Unlike models that are either too general, like [6,10], or too focused on a specific area, such as drones [19,20] or smart tourism [25], the SPFMSH is carefully designed and tailored specifically for the smart home environment in SA. This ensures it remains widely applicable and practical, without becoming overly narrow in scope. |
| Theoretical vs. Practical | Many are purely conceptual or theoretical (e.g., [16,17,22]), lacking implementation details or real-world validation. | Although numerous frameworks remain predominantly conceptual or theoretical [15,16,22], the SPFMSH was meticulously developed employing the Design Science Research (DSR) methodology, with an emphasis on the development and evaluation of a functional artifact. Our validation process, which incorporates real-world scenarios and expert feedback, underscores a pronounced focus on practical implementation that is occasionally neglected in prior studies. |
| Proactive Focus | Some early models introduce forensic readiness concepts ([6,30,35]), but they are outdated and not designed for the scale of modern IoT and the proactive AI-driven threats it poses. | Although initial models incorporated forensic readiness concepts [6,34], they often become obsolete and may not adequately accommodate the extensive scope of modern Internet of Things (IoT) environments. The SPFMSH adopts a proactive approach, integrating AI-driven threat detection with automated forensic evidence preservation to intervene before issues escalate. This innovative integration surpasses the capabilities of preceding frameworks. |
| Integration and Interoperability | Struggle with the heterogeneity and complexity of IoT environments. Many solutions are either siloed ([8,23]) or lack technical specifics for integration ([17]). | The metamodeling approach inherently addresses interoperability. It provides a unifying high-level abstraction that can be instantiated across diverse smart home devices and systems. |
| Data Handling | Often, they lack robust mechanisms for the volume, velocity, and variety of IoT data; some address data management ([23]), but not specifically for forensic readiness. | Data-Centric Processing is a core concept. The model explicitly defines how data flows from smart devices to be processed for both security and forensic purposes. |
| Validation | Frequently not validated or validated only in limited, academic settings ([8,15]). | A notable deficiency in the existing literature is the absence of empirical validation of proposed models within practical environments. Conversely, this study employed a comprehensive validation methodology that encompassed a detailed comparison (refer to Table 8), testing across three authentic cyberattack scenarios, and expert assessment. This meticulous approach offers a more robust basis for affirming the efficacy of the model. |
| Technical Complexity | Frameworks using MDE/metamodeling ([18,23]) can be complex and require specialized expertise, creating a barrier to adoption. | Aims to balance abstraction with usability. The goal is to provide a clear template and common concepts that practitioners can understand and use, not just academics. |
| Cultural and Regional Relevance | Almost all are generic and not tailored to specific national infrastructures, regulations, or digital transformation visions like Saudi Vision 2030. | Most importantly, current models are often too generic and fail to adequately account for specific national contexts. Consequently, the SPFMSH was developed explicitly for Saudi Arabia. It considers the nation’s unique infrastructure, the directives issued by the National Cybersecurity Authority (NCA), the Personal Data Protection Law (PDPL), and the ambitious digital transformation objectives outlined in Vision 2030. These regional factors make it a more pertinent and applicable framework for Saudi Arabia than more general international models. |
| SPFMSH Concept | Action and Validation Process |
|---|---|
| Smart Environment Domains | The compromised camera and target NAS are identified as assets within the model’s domain map. Their normal behavioral baselines (in terms of network traffic and access patterns) have been previously established. |
| Security and Risk Management | Proactive Detection: The model’s AI-driven monitoring tools detect the anomaly:
|
| Data-Centric Processing |
|
| AI and Automation | Orchestration and Analysis: Automated scripts correlate the alerts from the security module with the evidence being collected by the data module. The system automatically generates a preliminary severity score (e.g., “High”) and notifies the homeowner via a secure mobile alert. |
| Digital Forensic Readiness and Investigation | Investigation Support: The model provides a pre-structured forensic timeline for an investigator. All preserved evidence (PCAP, logs, memory dumps) is packaged with associated hash values and timestamps. The timeline clearly shows:
|
| Challenge | How SPFMSH Provides a Solution |
|---|---|
| Reactive Digital Forensics | SPFMSH is inherently proactive, integrating AI-driven threat detection with automatic evidence preservation. This method transforms a security incident into an immediate, thorough investigation rather than just a retrospective response. |
| Lack of Regional and Regulatory Alignment | The framework is meticulously designed to align seamlessly with NCA regulations and the PDPL in the Saudi context. It considers local infrastructure, innovative projects such as NEOM, and regional user behaviors, thereby maintaining relevance and full compliance with legal standards. |
| The Theory-Practice Gap | Developed employing the Design Science Research (DSR) methodology, the SPFMSH constitutes a validated and practically applicable artifact. Its efficacy was corroborated through real-world cyberattack scenarios and expert evaluation, thereby linking the theoretical concept with practical application. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alsulami, M.H. A Smart Proactive Forensic Meta-Model for Smart Homes in Saudi Arabia Using Metamodeling Approaches. Electronics 2025, 14, 4319. https://doi.org/10.3390/electronics14214319
Alsulami MH. A Smart Proactive Forensic Meta-Model for Smart Homes in Saudi Arabia Using Metamodeling Approaches. Electronics. 2025; 14(21):4319. https://doi.org/10.3390/electronics14214319
Chicago/Turabian StyleAlsulami, Majid H. 2025. "A Smart Proactive Forensic Meta-Model for Smart Homes in Saudi Arabia Using Metamodeling Approaches" Electronics 14, no. 21: 4319. https://doi.org/10.3390/electronics14214319
APA StyleAlsulami, M. H. (2025). A Smart Proactive Forensic Meta-Model for Smart Homes in Saudi Arabia Using Metamodeling Approaches. Electronics, 14(21), 4319. https://doi.org/10.3390/electronics14214319







