DeepOP: A Hybrid Framework for MITRE ATT&CK Sequence Prediction via Deep Learning and Ontology
Abstract
1. Introduction
- (1)
- We developed the Cybersecurity Ontology for Attack Sequence Extraction (COASE) and an ontology-based attack sequence knowledge reasoning method, enabling the automated extraction of attack sequences with causal relationships, thereby providing a theoretical foundation for attack behavior modeling.
- (2)
- By extracting data from real APT attack cases and integrating ontology reasoning techniques, we generated a dataset that reflects the causal relationships and parallel attack paths among different attack techniques in cyber threat intelligence, providing standardized data support for fine-grained attack prediction research.
- (3)
- We designed an attack prediction model incorporating causal window attention (CWA), capable of capturing local causal relationships and global features in APT attack sequences, offering an efficient and accurate solution for complex multi-step attack prediction tasks.
- (4)
- We conducted extensive experiments on the constructed dataset, and the results demonstrate that the proposed model significantly outperforms existing methods in multi-step attack prediction tasks, showcasing substantial advantages in prediction accuracy and robustness.
2. Related Work and Background
2.1. Modeling APT Attack
2.2. Attack Prediction
2.3. Threat Intelligence Extraction and Ontology Reasoning
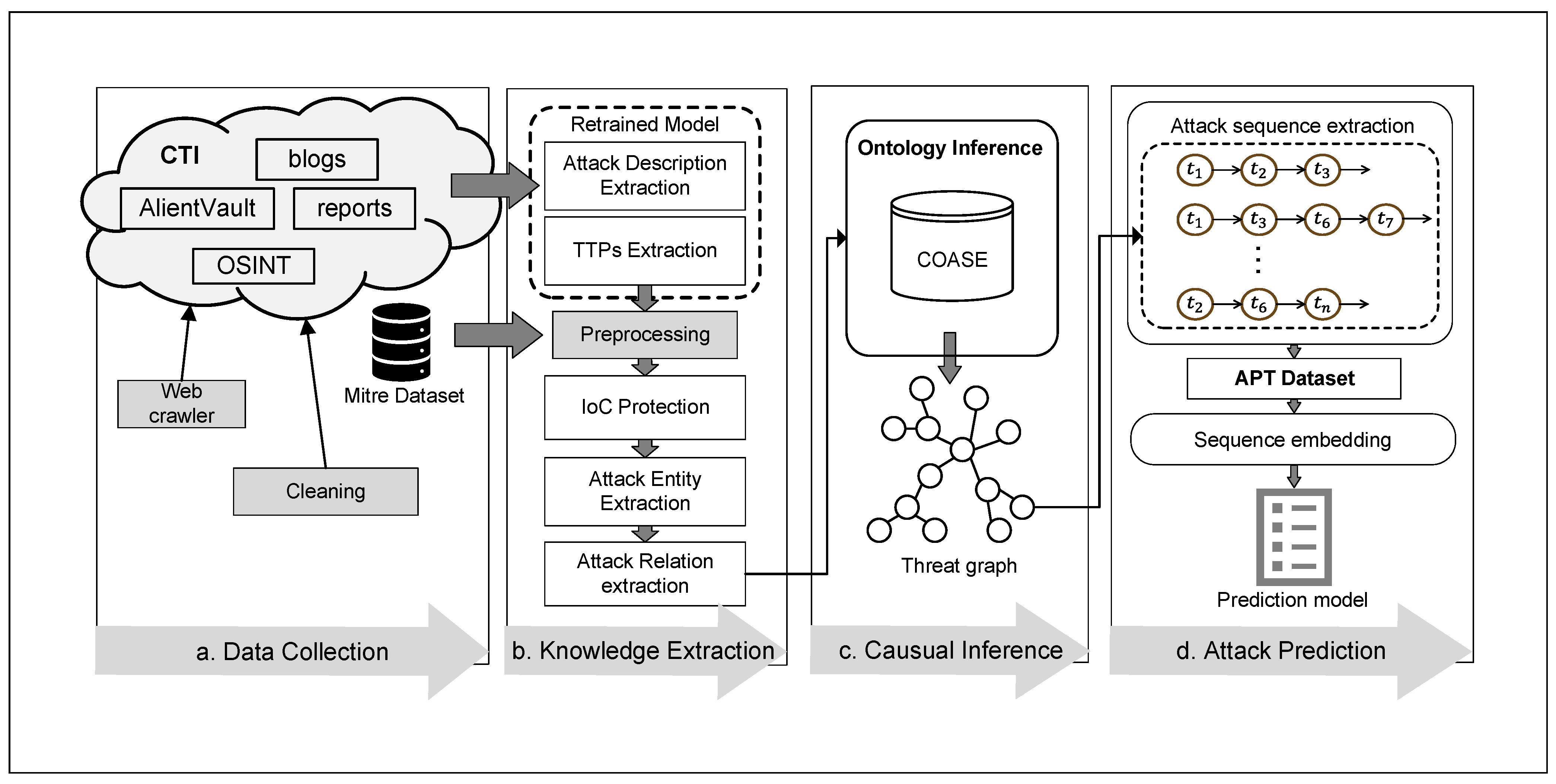
3. Materials and Methods
- (1)
- Data Collection: the initial stage involves using web crawlers to collect CTI from various sources as the data foundation.
- (2)
- Knowledge Extraction: CTI is processed to identify specific cybersecurity attack techniques and related sentences, and extract key “query nodes” of the ontology.
- (3)
- Causal Reasoning: ontology reasoning is used to connect different causally related attack techniques to form complete attack event representations, which are stored in a graph database.
- (4)
- Attack Prediction: in the final stage, we extract all attack sequences to construct the dataset, which provides the necessary data foundation for predicting specific attack techniques. We designed an attack prediction module within the DeepOP framework, which leverages a novel window-based causal attention mechanism to extract multi-scale information from attack sequences, enhancing performance in multi-step attack prediction.
3.1. Data Collection
3.2. Information Extraction from CTI
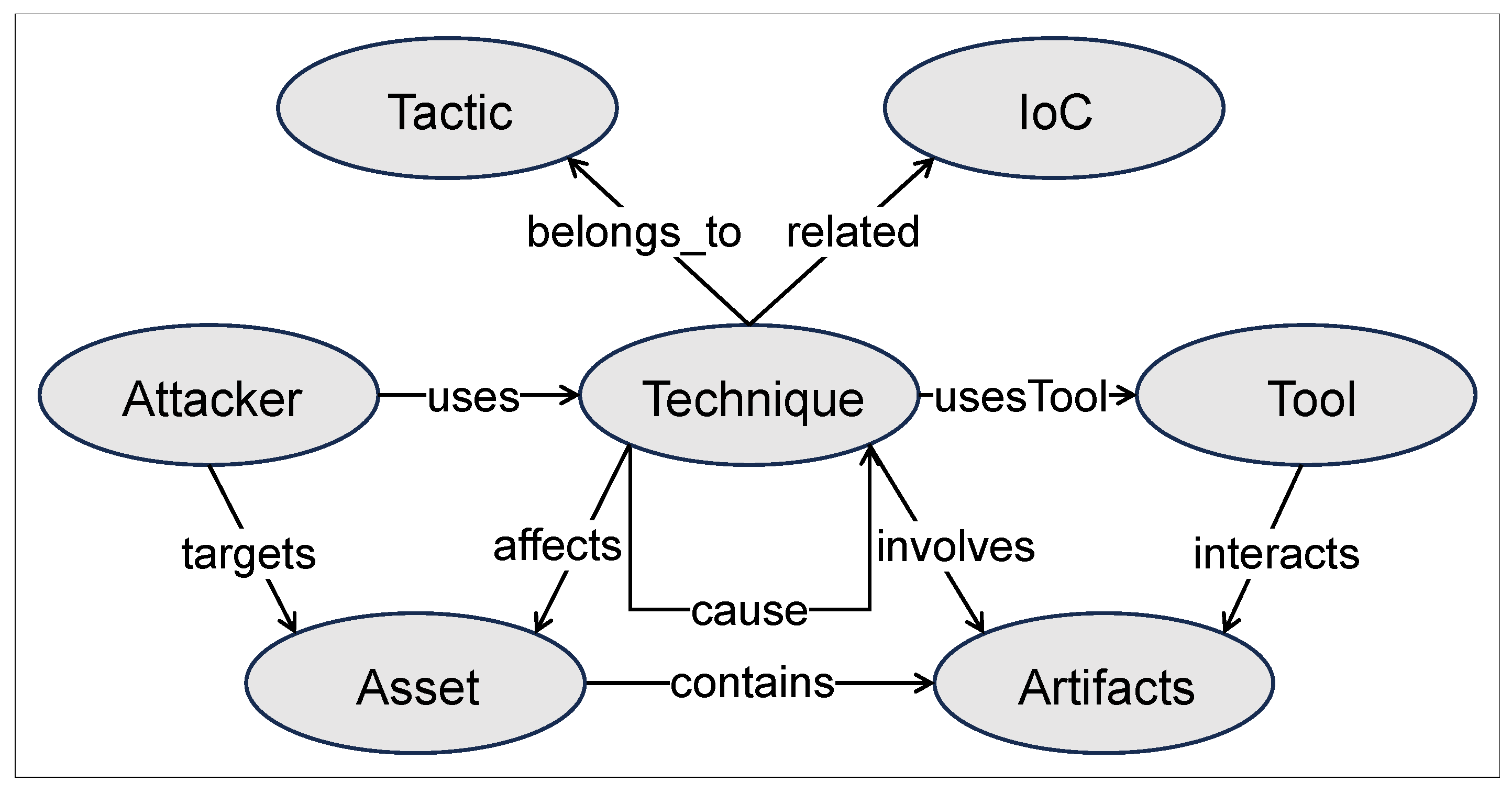
3.3. Ontology Inference
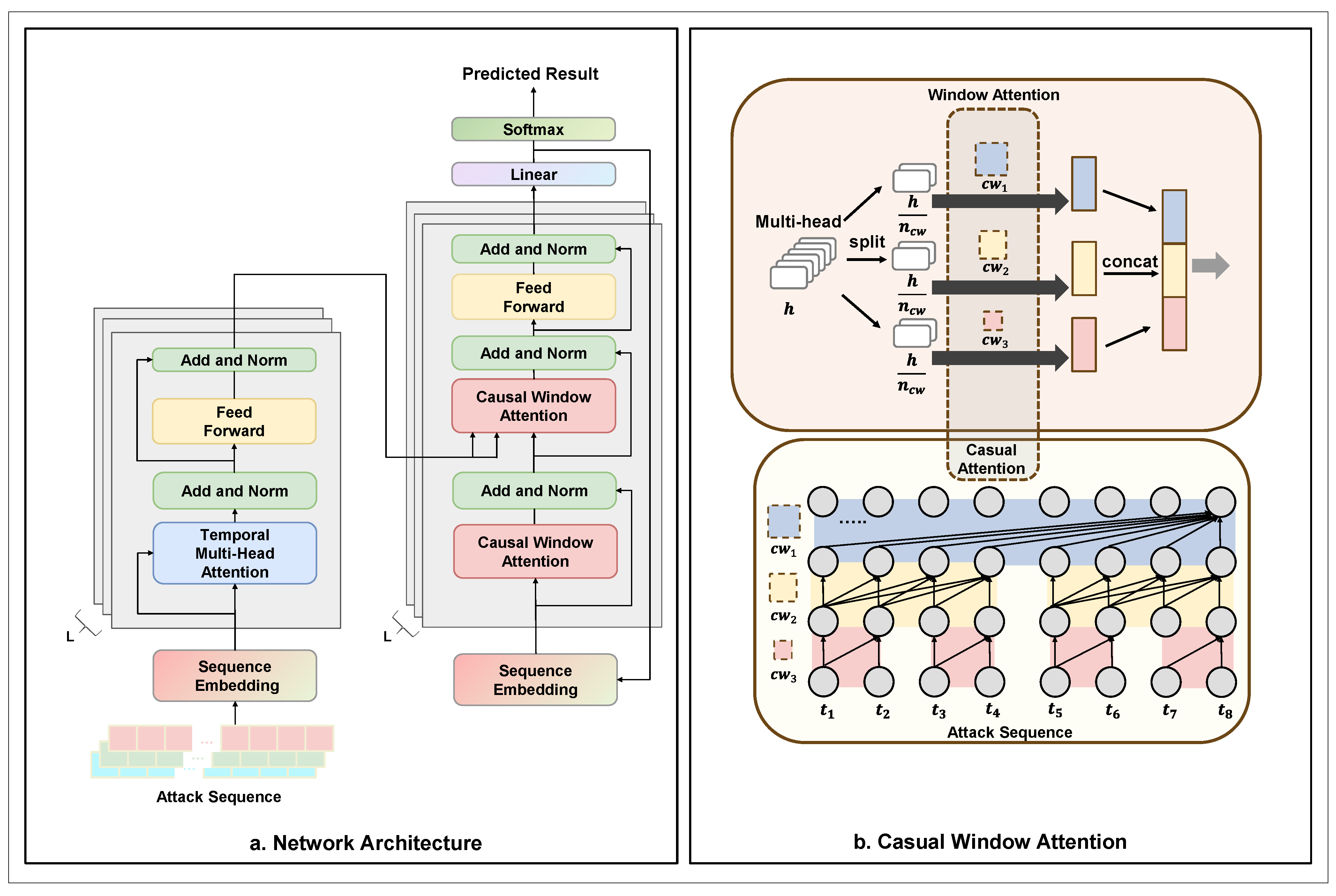
3.4. Attack Prediction Module
4. Experiments
4.1. Dataset
4.2. Experiments Settings
| Algorithm 1 Training based on attack prediction model. |
Input:
Output: Trained DeepOP attack prediction model Process:
|
4.3. Complexity Analysis
4.4. Comparison with Other Methods
4.5. Ontology Module Validation
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Alladi, T.; Chamola, V.; Zeadally, S. Industrial control systems: Cyberattack trends and countermeasures. Comput. Commun. 2020, 155, 1–8. [Google Scholar] [CrossRef]
- Khan, R.; Maynard, P.; McLaughlin, K.; Laverty, D.; Sezer, S. Threat analysis of blackenergy malware for synchrophasor based real-time control and monitoring in smart grid. In Proceedings of the 4th International Symposium for ICS & SCADA Cyber Security Research 2016, ICS-CSR, Belfast, UK, 23–25 August 2016; pp. 53–63. [Google Scholar]
- Friedberg, I.; Skopik, F.; Settanni, G.; Fiedler, R. Combating advanced persistent threats: From network event correlation to incident detection. Comput. Secur. 2015, 48, 35–57. [Google Scholar] [CrossRef]
- Zohrevand, Z.; Glässer, U. Should i raise the red flag? A comprehensive survey of anomaly scoring methods toward mitigating false alarms. arXiv 2019, arXiv:1904.06646. [Google Scholar]
- Khan, I.A.; Pi, D.; Khan, Z.U.; Hussain, Y.; Nawaz, A. HML-IDS: A hybrid-multilevel anomaly prediction approach for intrusion detection in SCADA systems. IEEE Access 2019, 7, 89507–89521. [Google Scholar] [CrossRef]
- GhasemiGol, M.; Ghaemi-Bafghi, A.; Takabi, H. A comprehensive approach for network attack forecasting. Comput. Secur. 2016, 58, 83–105. [Google Scholar] [CrossRef]
- Polatidis, N.; Pimenidis, E.; Pavlidis, M.; Papastergiou, S.; Mouratidis, H. From product recommendation to cyber-attack prediction: Generating attack graphs and predicting future attacks. Evol. Syst. 2020, 11, 479–490. [Google Scholar] [CrossRef]
- Sun, N.; Zhang, J.; Rimba, P.; Gao, S.; Zhang, L.Y.; Xiang, Y. Data-driven cybersecurity incident prediction: A survey. IEEE Commun. Surv. Tutor. 2018, 21, 1744–1772. [Google Scholar] [CrossRef]
- Huang, L. Design of an IoT DDoS attack prediction system based on data mining technology. J. Supercomput. 2022, 78, 4601–4623. [Google Scholar] [CrossRef]
- Holgado, P.; Villagrá, V.A.; Vazquez, L. Real-time multistep attack prediction based on hidden markov models. IEEE Trans. Dependable Secur. Comput. 2017, 17, 134–147. [Google Scholar] [CrossRef]
- Liu, Y.; Guo, Y. CL-AP2: A composite learning approach to attack prediction via attack portraying. J. Netw. Comput. Appl. 2024, 230, 103963. [Google Scholar] [CrossRef]
- Kim, Y.; Lee, I.; Kwon, H.; Lee, K.; Yoon, J. BAN: Predicting APT Attack Based on Bayesian Network With MITRE ATT&CK Framework. IEEE Access 2023, 11, 91949–91968. [Google Scholar] [CrossRef]
- Strom, B.E.; Applebaum, A.; Miller, D.P.; Nickels, K.C.; Pennington, A.G.; Thomas, C.B. Mitre ATT&CK: Design and Philosophy; Technical Report; The MITRE Corporation: McLean, VA, USA, 2018. [Google Scholar]
- Al-Mohannadi, H.; Mirza, Q.; Namanya, A.; Awan, I.; Cullen, A.; Disso, J. Cyber-attack modeling analysis techniques: An overview. In Proceedings of the 2016 IEEE 4th International Conference on Future Internet of Things and Cloud Workshops (FiCloudW), Vienna, Austria, 22–24 August 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 69–76. [Google Scholar]
- Naik, N.; Jenkins, P.; Grace, P.; Song, J. Comparing attack models for IT systems: Lockheed Martin’s Cyber Kill Chain, MITRE ATT&CK Framework and Diamond Model. In Proceedings of the 2022 IEEE International Symposium on Systems Engineering (ISSE), Vienna, Austria, 24–26 October 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–7. [Google Scholar]
- Bartos, V.; Zadnik, M.; Habib, S.M.; Vasilomanolakis, E. Network entity characterization and attack prediction. Future Gener. Comput. Syst. 2019, 97, 674–686. [Google Scholar] [CrossRef]
- Ansari, M.S.; Bartoš, V.; Lee, B. GRU-based deep learning approach for network intrusion alert prediction. Future Gener. Comput. Syst. 2022, 128, 235–247. [Google Scholar] [CrossRef]
- Wang, W.; Yi, P.; Jiang, J.; Zhang, P.; Chen, X. Transformer-based framework for alert aggregation and attack prediction in a multi-stage attack. Comput. Secur. 2024, 136, 103533. [Google Scholar] [CrossRef]
- Zhao, J.; Tang, T.; Bu, B.; Li, Q. Graph neural network-based attack prediction for communication-based train control systems. CAAI Trans. Intell. Technol. 2024, 1–13. [Google Scholar] [CrossRef]
- Li, T.; Jiang, Y.; Lin, C.; Obaidat, M.S.; Shen, Y.; Ma, J. Deepag: Attack graph construction and threats prediction with bi-directional deep learning. IEEE Trans. Dependable Secur. Comput. 2022, 20, 740–757. [Google Scholar] [CrossRef]
- Al-Shaer, R.; Spring, J.M.; Christou, E. Learning the associations of MITRE ATT&CK adversarial techniques. In Proceedings of the 2020 IEEE Conference on Communications and Network Security (CNS), Held Virtually, 29 June–1 July 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–9. [Google Scholar]
- Niakanlahiji, A.; Wei, J.; Chu, B.T. A natural language processing based trend analysis of advanced persistent threat techniques. In Proceedings of the 2018 IEEE International Conference on Big Data (Big Data), Seattle, WA, USA, 10–13 December 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 2995–3000. [Google Scholar]
- Satvat, K.; Gjomemo, R.; Venkatakrishnan, V. Extractor: Extracting attack behavior from threat reports. In Proceedings of the 2021 IEEE European Symposium on Security and Privacy (EuroS&P), Held Virtually, 6–10 September 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 598–615. [Google Scholar]
- Husari, G.; Al-Shaer, E.; Ahmed, M.; Chu, B.; Niu, X. Ttpdrill: Automatic and accurate extraction of threat actions from unstructured text of cti sources. In Proceedings of the 33rd Annual Computer Security Applications Conference, Orlando, FL, USA, 4–8 December 2017; pp. 103–115. [Google Scholar]
- Li, Z.; Zeng, J.; Chen, Y.; Liang, Z. AttacKG: Constructing technique knowledge graph from cyber threat intelligence reports. In Proceedings of the European Symposium on Research in Computer Security; Springer: Berlin/Heidelberg, Germany, 2022; pp. 589–609. [Google Scholar]
- Myneni, S.; Jha, K.; Sabur, A.; Agrawal, G.; Deng, Y.; Chowdhary, A.; Huang, D. Unraveled—A semi-synthetic dataset for Advanced Persistent Threats. Comput. Netw. 2023, 227, 109688. [Google Scholar] [CrossRef]
- Bagui, S.S.; Mink, D.; Bagui, S.C.; Ghosh, T.; Plenkers, R.; McElroy, T.; Dulaney, S.; Shabanali, S. Introducing uwf-zeekdata22: A comprehensive network traffic dataset based on the mitre att&ck framework. Data 2023, 8, 18. [Google Scholar]
- Monitor, C. APT Cyber Criminal Campaign Collections. 2024. Available online: https://github.com/CyberMonitor/APT_CyberCriminal_Campagin_Collections (accessed on 30 November 2024).
- Orbinato, V.; Barbaraci, M.; Natella, R.; Cotroneo, D. Automatic mapping of unstructured cyber threat intelligence: An experimental study (practical experience report). In Proceedings of the 2022 IEEE 33rd International Symposium on Software Reliability Engineering (ISSRE), Charlotte, NC, USA, 31 October–3 November 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 181–192. [Google Scholar]
- Legoy, V.; Caselli, M.; Seifert, C.; Peter, A. Automated retrieval of att&ck tactics and techniques for cyber threat reports. arXiv 2020, arXiv:2004.14322. [Google Scholar]
- Marchiori, F.; Conti, M.; Verde, N.V. Stixnet: A novel and modular solution for extracting all stix objects in cti reports. In Proceedings of the 18th International Conference on Availability, Reliability and Security (ARES), Benevento, Italy, 29 August–1 September 2023; ACM: New York, NY, USA, 2023; pp. 1–11. [Google Scholar]
- Lei, G.; Ruibin, S.; Yu, T. Research on key technologies of ontology based threat modeling for cyber range. J. CAEIT 2020, 15, 1139–1144. [Google Scholar]
- Rastogi, N.; Dutta, S.; Zaki, M.J.; Gittens, A.; Aggarwal, C. Malont: An ontology for malware threat intelligence. In Proceedings of the International Workshop on Deployable Machine Learning for Security Defense; Springer: Berlin/Heidelberg, Germany, 2020; pp. 28–44. [Google Scholar]
- Wang, F.; Zhang, Y.; Luo, X. Semantic query of ontology knowledge base based on SQWRL. Comput. Technol. Dev. 2017, 2, 24–29. [Google Scholar]
- Vaswani, A.; Shazeer, N.; Parmar, N.; Uszkoreit, J.; Jones, L.; Gomez, A.N.; Kaiser, Ł.; Polosukhin, I. Attention is all you need. Adv. Neural Inf. Process. Syst. 2017, 30, 5998–6008. [Google Scholar] [CrossRef]
- He, K.; Zhang, X.; Ren, S.; Sun, J. Deep residual learning for image recognition. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, Las Vegas, NV, USA, 27–30 June 2016; pp. 770–778. [Google Scholar]
- Lei Ba, J.; Kiros, J.R.; Hinton, G.E. Layer normalization. arXiv 2016, arXiv:1607.06450. [Google Scholar]
- Church, K.W. Word2Vec. Nat. Lang. Eng. 2017, 23, 155–162. [Google Scholar] [CrossRef]
- Ahn, G.; Kim, K.; Park, W.; Shin, D. Malicious file detection method using machine learning and interworking with MITRE ATT&CK framework. Appl. Sci. 2022, 12, 10761. [Google Scholar] [CrossRef]
- Corporation, M. Frankenstein Campaign (C0001), Online Resource. 2023. Available online: https://attack.mitre.org/campaigns/C0001/ (accessed on 27 April 2024).
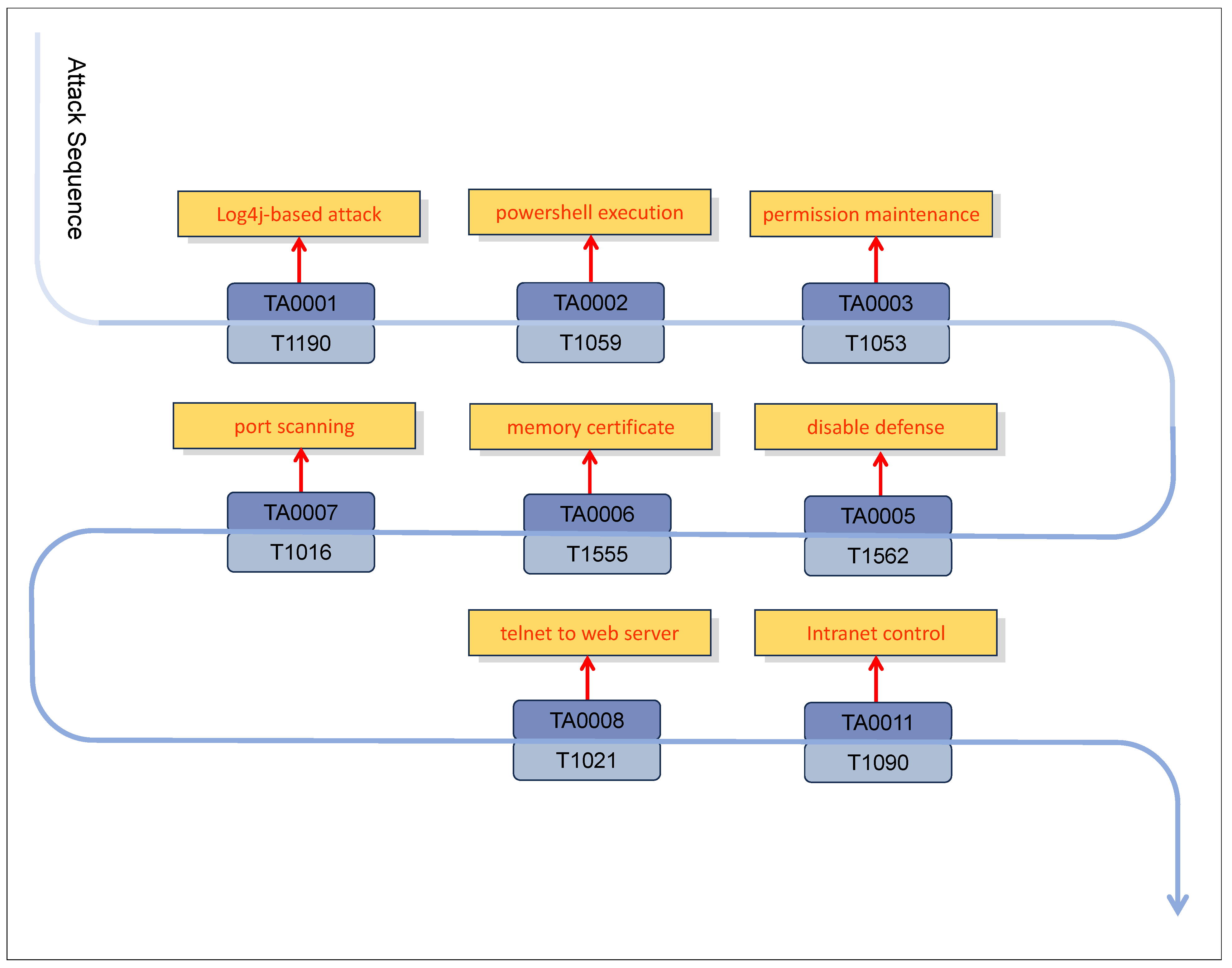

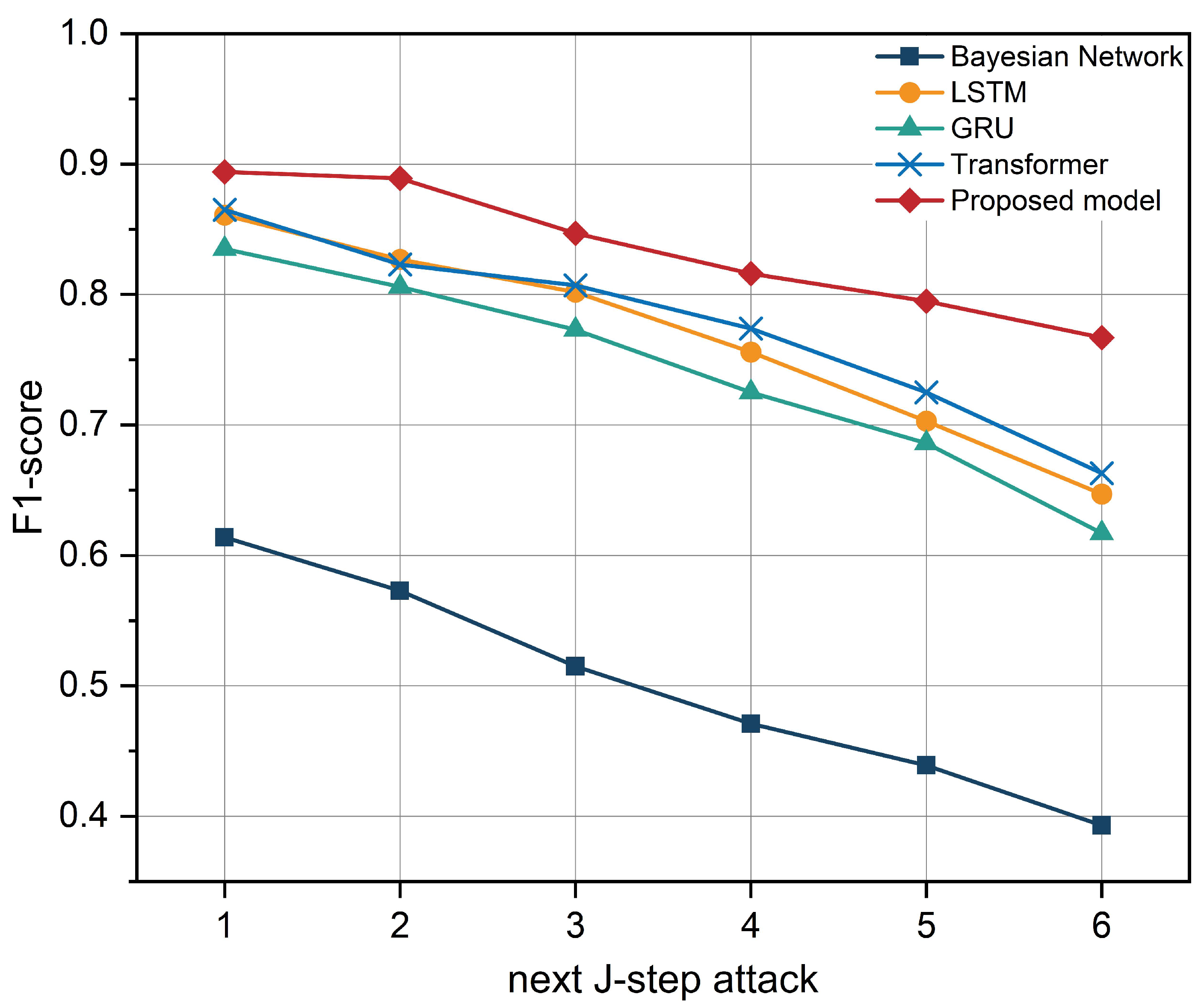
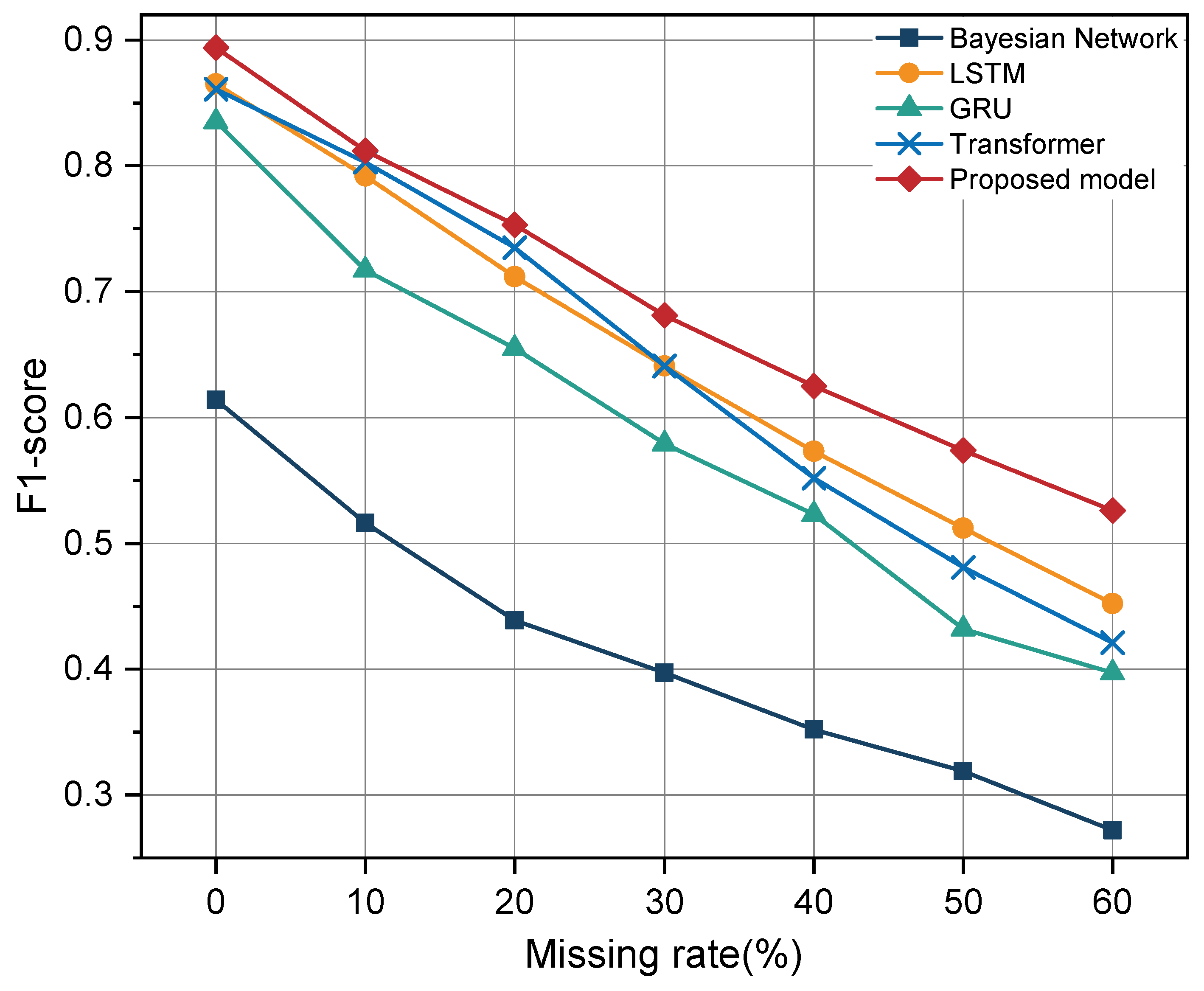
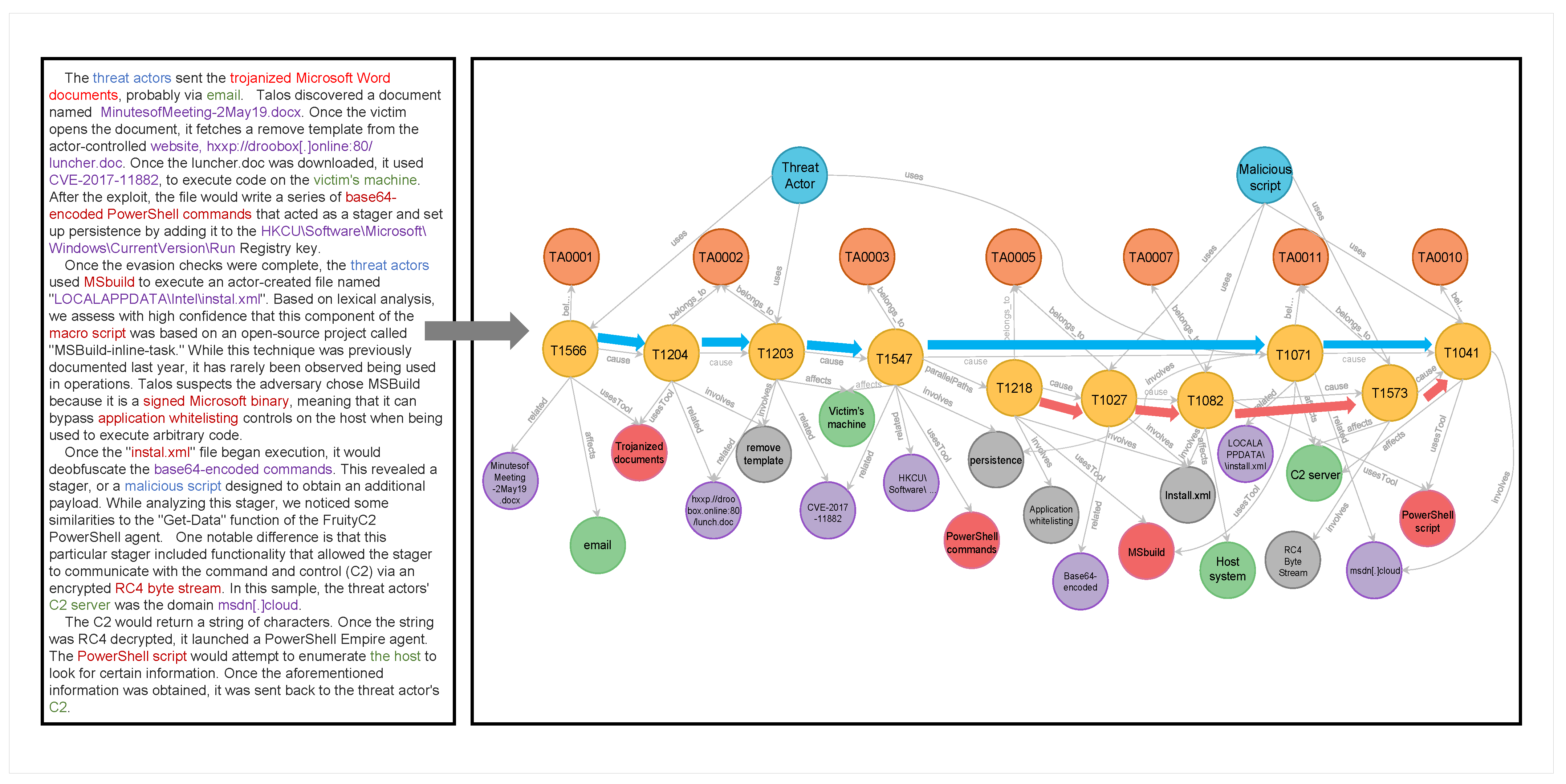
| Tactic | TA0001 | TA0002 | TA0003 | TA0004 | TA0005 | TA0006 | TA0007 | TA0008 | TA0009 | TA0011 | TA0010 | TA0040 | Total |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Number | 583 | 1776 | 2471 | 2432 | 4759 | 1562 | 2517 | 572 | 1257 | 1659 | 357 | 425 | 17,302 |
| Class | Regular Expression |
|---|---|
| IP | (?:[0-9]1,3\.)3[0-9]1,3(?:\/[0-9]1,2)? |
| URL | h[tx]2ps?:\/\/(?:[a-zA-Z0-9\-._ %!$&’()*+,;=:@\/\ [\]]+) |
| Domain | ((?:[a-zA-Z0-9-]+\.)+(?!exe|dll)[a-zA-Z]2,4) |
| [a-zA-Z0-9._%+-]+@[a-zA-Z0-9.-]+\.[a-zA-Z]2,4 | |
| Registry | (HKLM|HKCU|HKCR|HKU|HKCC)\\[\\A-Za-z0-9-_]+ |
| Method | Accuracy | Precision | Recall | F1-Score |
|---|---|---|---|---|
| LSTM [20] | 0.867 | 0.779 | 0.972 | 0.865 |
| GRU [17] | 0.841 | 0.769 | 0.913 | 0.835 |
| Bayesian network [12] | 0.608 | 0.549 | 0.695 | 0.614 |
| Transformer [35] | 0.857 | 0.783 | 0.956 | 0.861 |
| Proposed model | 0.898 | 0.822 | 0.978 | 0.894 |
| Proposed model | AS1: TA0001.T1566-TA0002.T1204-TA0002.T1203-TA0003.T1547-TA0011.T1071 |
| TA0010.T1041 | |
| AS2: TA0005.T1218-TA0005.T1027-TA0007.T1082-TA0011.T1573-TA0010.T1041 | |
| BAN [12] | TA0001.T1566-TA0002.T1204-TA0002.T1203-TA0003.T11547-TA0005.T1218- |
| TA0005.T1027-TA0007.T1082-TA0011.T1573-TA0011.T1071-TA0010.T1041 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, S.; Xue, X.; Su, X. DeepOP: A Hybrid Framework for MITRE ATT&CK Sequence Prediction via Deep Learning and Ontology. Electronics 2025, 14, 257. https://doi.org/10.3390/electronics14020257
Zhang S, Xue X, Su X. DeepOP: A Hybrid Framework for MITRE ATT&CK Sequence Prediction via Deep Learning and Ontology. Electronics. 2025; 14(2):257. https://doi.org/10.3390/electronics14020257
Chicago/Turabian StyleZhang, Shuqin, Xiaohang Xue, and Xinyu Su. 2025. "DeepOP: A Hybrid Framework for MITRE ATT&CK Sequence Prediction via Deep Learning and Ontology" Electronics 14, no. 2: 257. https://doi.org/10.3390/electronics14020257
APA StyleZhang, S., Xue, X., & Su, X. (2025). DeepOP: A Hybrid Framework for MITRE ATT&CK Sequence Prediction via Deep Learning and Ontology. Electronics, 14(2), 257. https://doi.org/10.3390/electronics14020257







