1. Introduction
The Internet of Things (IoT) has emerged as a foundational pillar for next-generation industrial and smart infrastructure systems, enabling ubiquitous sensing, actuation, and autonomous decision-making across diverse domains such as smart cities, intelligent transportation, and industrial automation [
1,
2,
3]. Wireless communication technologies serve as the critical bridge between distributed IoT nodes and cloud or application servers, driving demand for scalable, power-efficient, and cost-effective connectivity solutions [
4]. Among these, low-power wide-area networks (LPWANs) have become the preferred communication substrate for long-range and low-bandwidth IoT applications, offering kilometer-level coverage with minimal energy consumption [
5]. NB-IoT, a 3GPP-standardized LPWAN protocol, operates within licensed cellular spectrum and provides optimized performance for deep indoor penetration, low power consumption, and massive device connectivity [
6,
7]. Unlike unlicensed technologies such as LoRaWAN or Sigfox, NB-IoT benefits from tight integration with existing LTE and 5G core networks, leveraging carrier-grade reliability and standardized security mechanisms. These features make NB-IoT a strong candidate for large-scale IoT deployments in mission-critical and infrastructure-sensitive scenarios [
8].
Despite the maturity of NB-IoT in terms of radio and core-network integration, its native security mechanisms do not provide end-to-end (E2E) protection. In cellular architectures, security is partitioned across two domains: Access Stratum (AS) protections between the User Equipment (UE) and the base station, and Non Access Stratum (NAS) protections between the UE and the Mobility Management Entity (MME) [
9]. However, both AS and NAS protections terminate before reaching the application server. Specifically, NAS ciphering and integrity verification are terminated at the MME, where signaling is decrypted in core network operations. This architectural design exposes user data to potential compromise within untrusted infrastructure, highlighting the necessity for E2E security to ensure confidentiality, integrity, and authentication across the entire communication path.
To address these limitations, Transport Layer Security (TLS) has been widely adopted as a modular and standardized framework to provide secure communication over NB-IoT stacks [
10]. Nevertheless, most commercial TLS deployments rely on classical public-key primitives such as RSA and Elliptic Curve Cryptography (ECC), both of which are vulnerable to quantum adversaries capable of executing Shor’s algorithm [
11]. In response to this emerging threat, the U.S. National Institute of Standards and Technology (NIST) [
12,
13] has recently standardized post-quantum cryptographic (PQC) schemes, including the lattice-based key encapsulation mechanism Kyber [
14] and the digital signature algorithm Dilithium [
15], to ensure future-proof cryptographic resilience.
Post-quantum cryptography (PQC) algorithms, while promising, are still in the early stages of deployment and have yet to undergo extensive real world testing. Although these algorithms are designed to resist quantum computing attacks, their long-term performance and robustness against a wide range of potential threats are still being validated. During this transitional phase, it is safer to adopt a hybrid cryptographic approach that combines both classical cryptographic algorithms (e.g., ECC) and PQC schemes (e.g., Kyber, Dilithium). This hybrid strategy ensures the security of communication systems against both current classical threats and future quantum threats, providing a safeguard in case either component is compromised.
Recent studies have explored various security enhancements for NB-IoT. Ref. [
16] proposed an anti-quantum, group-oriented access scheme that replaces the 3GPP AKA handshake with lattice-based homomorphic encryption, achieving around 60% computation savings and significantly lower latency under massive access conditions. Ref. [
17] introduced a lightweight hybrid public and private blockchain overlay for NB-IoT, enabling decentralized authentication via SHA-256 hash chains and digital signatures, with a prototype showing sub-second join latency and approximately 7 kB of additional traffic. Ref. [
18] investigated the integration of PQC algorithms into TLS and measured their impact on NB-IoT payload latency. However, these works did not focus on the edge side of the resource-constrained user device and analyze the performance impact on the overall system.
IoT applications generate large amounts of data and require complex computations. Edge computing solutions place IoT devices close to data sources to facilitate real-time processing [
19]. Sharaf et al. [
20] implemented a compact ASIC co-processor that unifies SNOW 3G and ZUC stream-cipher datapaths to meet 3GPP EEA/EIA security for NB-IoT UEs. The co-processor was characterized using a 65 nm technology at a 2 Gbps rate, achieving 47% area reduction for the cipher core without sacrificing average power consumption. Jung et al. [
21] proposed a secure platform model for low-end IoT devices based on ARM platform security architecture. It consisted of system security services and application security services and provided APIs for easy and fast development. However, there were no post-quantum security modules integrated on the hardware modules in these works, and they failed to protect against quantum computing attacks.
Field-Programmable Gate Arrays (FPGAs) are reconfigurable hardware devices composed of an array of programmable logic blocks and interconnects. Unlike fixed-function ASICs, FPGAs can be reprogrammed after manufacturing to implement customized digital circuits, making them ideal for prototyping. RISC-V is an open-source instruction set architecture (ISA) with flexible instruction set customization. It is can therefore be tailored for specific applications, such as IoT systems, based on existing designs. PULPino is an open-source platform based on the RISC-V architecture. It is based on 32-bit RISC-V cores developed at ETH Zurich [
22,
23]. It supports two core variants: the RISCY core that features a four-stage pipeline, and the zero-riscy core that is a more compact in-order, two-stage pipeline processor optimized for low-power and low-area applications.
To enhance the security of the NB-IoT protocol and provide a reliable E2E guarantee for IoT applications, we propose a hardware platform for the NB-IoT security communication system. The main contributions are summarized as follows.
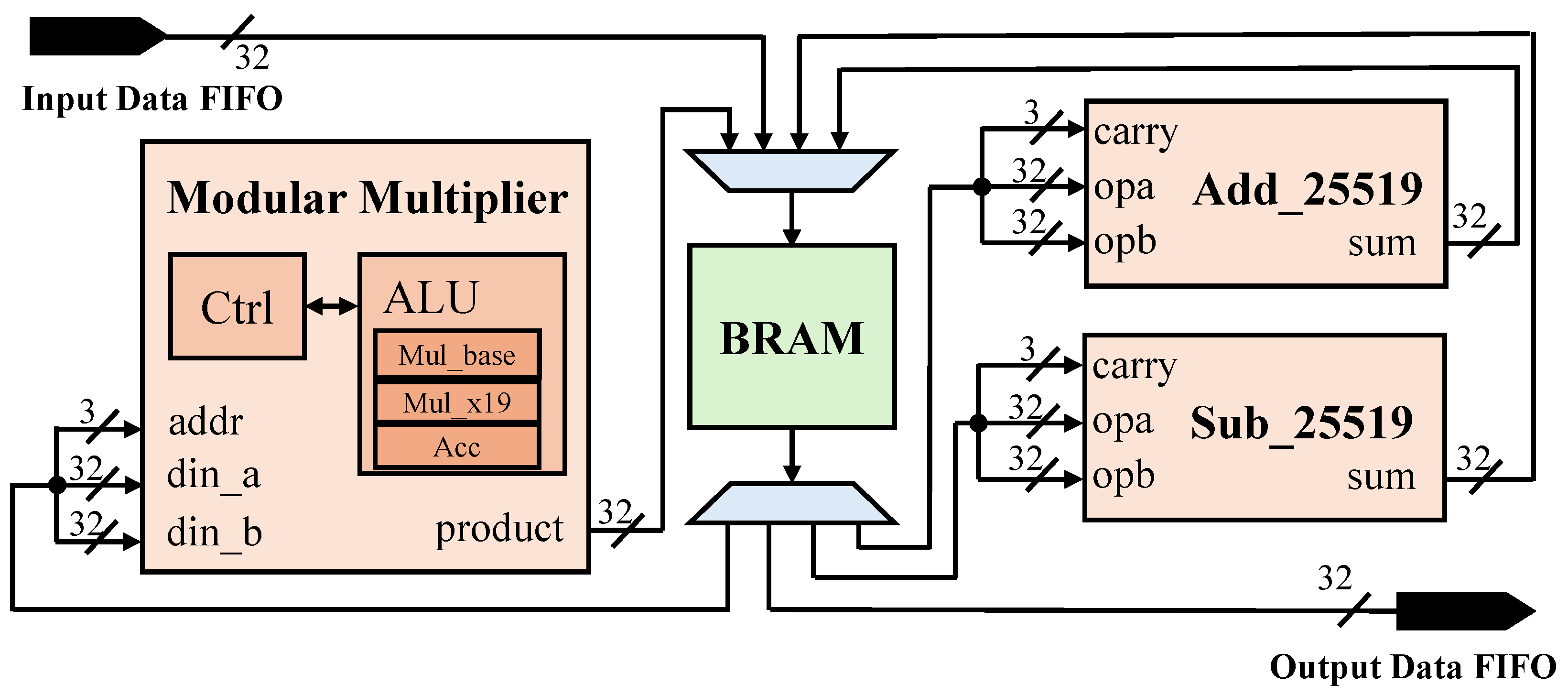
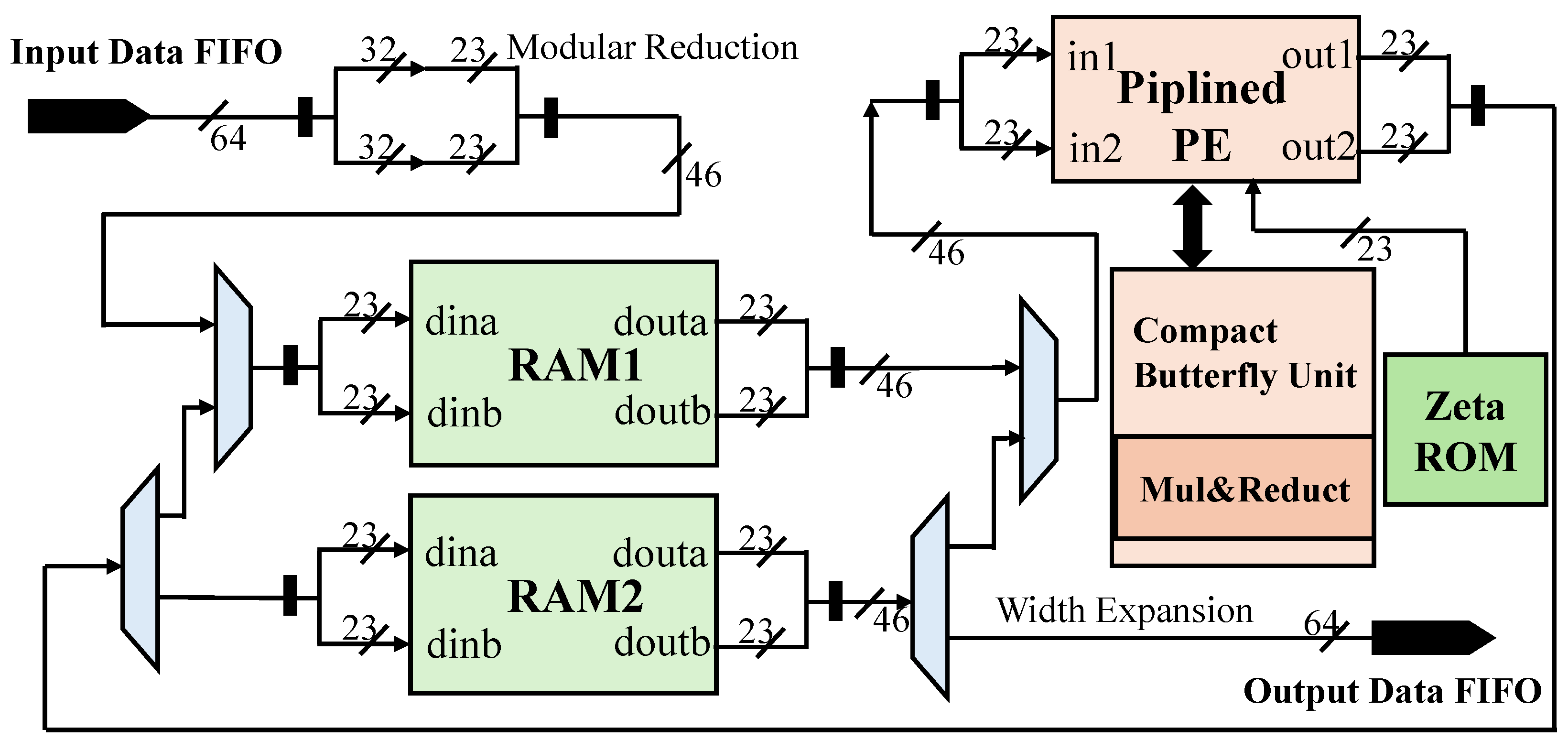
An FPGA-based hardware platform is implemented to support NB-IoT applications. The time-consuming functions of the cryptographical process are offloaded to hardware accelerators. The security modules, including the ECC point multiplication module, the hybrid NTT/INTT module, and the Kyber module, are integrated into the platform. A high-speed DMA is applied for the data communication between the RISC-V core and the security accelerators. The speedup of cryptography functions ranges from 32.2× to 145.4×. The platform is implemented with reconfigurable logic on the FPGA, with an estimated static power of 0.18 W and a dynamic power of 0.53 W.
The security of the NB-IoT protocol is enhanced with both post-quantum and classic cryptography. The elliptic-curve cryptography algorithms, including X25519 and Ed25519, are adopted as well as NIST-standardized PQC algorithms. Specifically, the ECDH and Kyber algorithms are selected to enhance the key exchange process, while the EdDSA and Dilithium algorithms are chosen to add the digital signature. The NB-IoT network stack is not modified, and it can gain support from LTE with existing base stations and evolved packet cores. The optimized protocol is thus compatible with the NB-IoT standard.
An NB-IoT network systematic model is evaluated, from the FPGA-based UE platform to the simulation of NB-IoT handshake communication. The communication of a set of different numbers of user devices with the application server is simulated for the enhanced protocol with end-to-end protection, including encryption, authenticity, and integrity. The results provide valuable insights into the latency and throughput overhead of the hybrid protocol, empirically validating the feasibility of the solution and low operational cost under realistic NB-IoT configurations.
The remainder of this paper is organized as follows.
Section 2 presents the background, including NB-IoT architecture, cryptographic preliminaries, and the threat model.
Section 3 introduces the proposed system model that integrates FPGA-based security modules with NB-IoT communication.
Section 4 details the hardware implementation, describing the secure processor architecture and the individual accelerators for ECC, NTT/INTT, and Kyber.
Section 5 explains the NB-IoT security enhancement, covering the hybrid handshake, authentication, and trust model.
Section 6 provides evaluation and discussion, reporting both FPGA hardware measurements and NS-3 network simulations, followed by a comparison with related works. Finally,
Section 7 concludes the paper and outlines limitations and directions for future research.
2. Background
2.1. List of Acronyms
To enhance readability and ensure consistency, the principal acronyms employed in this paper are summarized in
Table 1. This collection of definitions provides a unified reference for the terminology used across the protocol specification.
2.2. NB-IoT Network and Its Security Protocol
The architecture of NB-IoT is derived from the LTE system, specifically the Evolved Packet System, which is an IP-based network infrastructure that was introduced with 3GPP LTE Release 8 and has since evolved to support IoT applications [
24]. NB-IoT is integrated into the 3GPP Cellular IoT framework, leveraging the existing LTE radio access and core network components.
To establish a secure connection between NB-IoT User Equipment devices and the NB-IoT network, both parties must authenticate each other and then start the communication as shown in
Figure 1:
Deployment: Each UE has a unique identifier consisting of the IMSI and a 128-bit master key K. The HSS stores every valid IMSI together with its master key.
Attach Request: The UE sends an attach request containing its IMSI and network information. This request is forwarded by the eNodeB and MME to the HSS.
Response: The HSS uses the IMSI to retrieve the master key K. Then, HSS generates a random number (RAND), an authentication token (AUTN), the expected response (XRES), and the session root key K_ASME. The MME passes RAND and AUTN to the UE.
Verification: The UE verifies the AUTN, computes the response (RES), and sends it back to MME. The MME compares RES with XRES; if they match, authentication is successful.
Communication: The UE derives K_ASME and uses it to generate encryption and integrity keys for secure data transmission.
Figure 1.
Security protocol of the NB-IoT network.
Figure 1.
Security protocol of the NB-IoT network.
In NB-IoT, payloads can be transmitted through three distinct data paths: the user-plane IP path, the control-plane IP path, and the control-plane non-IP path [
25]. The classical user-plane IP approach establishes a dedicated data radio bearer following RRC setup, enabling the full IP protocol stack to deliver packets from the UE through the eNodeB and gateways SGW and PGW to the Application Server. This method is suitable for high-throughput scenarios such as firmware updates. Alternatively, NB-IoT supports control-plane data transmission optimized for small, infrequent payloads. In the control-plane non-IP mode, payloads are embedded directly in NAS signaling messages and sent to the MME, then forwarded by the Service Capability Exposure Function (SCEF) to the application server. This mode eliminates the overhead of IP encapsulation, making it highly efficient for power-efficient low-end IoT devices.
To secure data transmission, the Access Stratum (AS) security protocol ensures confidentiality and integrity between the UE and eNodeB. Simultaneously, the Non Access Stratum (NAS) security protects messages exchanged between the UE and MME. Therefore, the control-plane data can be secured by two layers of protection. However, since the NAS primitive terminates at the MME, it leaves the payload exposed within the core network. Therefore, an E2E protection mechanism is essential to preserve confidentiality and integrity across the entire communication path between the UE and the application server.
2.3. Classical Cryptography
Public-key cryptographic systems rely on asymmetric key pairs: a public key that can be openly distributed and a private key that must remain confidential. This paradigm enables secure communication over untrusted channels and forms the basis for many modern security protocols. Among public-key cryptographic schemes, Elliptic Curve Cryptography offers equivalent security to traditional methods such as RSA, with significantly reduced key sizes and computational overhead. For instance, achieving a 128-bit security level requires a 3072-bit key in RSA, whereas ECC only requires a 256-bit key [
26]. The security of ECC depends on the properties of the selected elliptic curve. The Montgomery family Curve25519 [
27], in particular, has gained popularity due to its high performance, improved security, and implementation simplicity.
ECC supports both key exchange and digital signature primitives, which can be applied to NB-IoT security. The Elliptic-curve Diffie–Hellman (ECDH) key exchange protocol can generate a shared secret key through insecure environments. The resulting shared key from ECDH can be used as a symmetric AES encryption key, providing lightweight yet robust confidentiality. In the context of NB-IoT, this provides a means to establish strong E2E encryption, compensating for security gaps inherent in existing key management mechanisms. Similarly, the Edwards-curve Digital Signature Algorithm (EdDSA) offers high-performance, compact digital signatures suitable for constrained environments. These signatures can be appended to NB-IoT network to ensure authenticity and integrity. In this work, we adopt X25519 for ECDH based on RFC 7748 [
28], and Ed25519 for digital signatures based on RFC 8032 [
29]. The security, efficiency, and lightweight properties make ECC a practical choice for securing constrained applications, particularly in IoT systems.
2.4. Post-Quantum Cryptography
Post-quantum cryptographic systems are designed to remain secure against quantum adversaries capable of executing Shor’s or Grover’s algorithms [
30]. Among these, lattice-based cryptography has emerged as a promising class due to its strong security foundations and practical efficiency. The CRYSTAL-Kyber KEM, selected in the final round of the NIST PQC standardization process, offers quantum-resistant public-key encryption and secure key exchange. Kyber is based on the Module Learning With Errors (MLWE) problem, which is believed to be hard even for quantum computers. Compared to ECC, Kyber achieves similar or better performance in terms of speed and communication overhead, with parameter sets designed to meet standardized security levels. Its design supports efficient hardware implementation and is highly suitable for bandwidth-constrained applications such as NB-IoT.
CRYSTAL-Dilithium is a lattice-based digital signature algorithm also selected by NIST for standardization. Dilithium is based on the Module Lattice problem with rejection sampling and uses structured ring arithmetic to enable high-throughput signature generation and verification. It offers strong quantum resistance, simple implementation, and efficient resource utilization, making it attractive for IoT scenarios where authenticity and message integrity must be ensured with minimal computational and memory costs. The Dilithium signature sizes are larger than the ECC scheme EdDSA, but remain acceptable within many NB-IoT use cases, especially when payload sizes are limited and security is paramount.
In this work, we integrate Kyber and Dilithium as post-quantum security solutions, along with ECC-based key exchange and signature mechanisms, within the NB-IoT communication network to provide a hybrid security scheme.
2.5. Threat Model
In the NB-IoT communication architecture, data transmitted between the UE and the application server traverses multiple intermediate network entities, such as the eNodeB, MME, and gateways. Standard NB-IoT security mechanisms, including AS and NAS protections, terminate within the core network. Consequently, sensitive payloads are exposed in plaintext at these intermediary nodes, preventing the realization of true end-to-end confidentiality and authenticity.
In addition to vulnerabilities from the network level, NB-IoT user equipment devices are frequently deployed in physically exposed environments, making them susceptible to side-channel attacks. Adversaries with physical proximity can exploit power consumption patterns, timing variations, or electromagnetic emissions to recover secret keys. Furthermore, fault injection techniques can be used to disrupt cryptographic computations and leak internal states. These attacks directly compromise the hardware implementation of security primitives, bypassing protocol-layer defenses.
A further concern arises in the context of hybrid post-quantum cryptography. During the transitional coexistence of classical and quantum-safe algorithms, downgrade attacks become feasible. An active adversary may attempt to suppress one component, such as forcing the system to rely solely on classical ECC, thereby degrading the security guarantees of the hybrid scheme. This emphasizes the need for robust protocols and strict enforcement of hybrid configurations to ensure cryptographic resilience.
3. System Model
The overall system encompasses multiple functional layers, including embedded hardware, secure computation modules, wireless communication protocols, and network infrastructure. To systematically evaluate and enhance E2E NB-IoT security, we construct a decoupled architecture that integrates FPGA-based cryptographic processing platform with software-level NB-IoT communication simulation. The proposed system model is illustrated in
Figure 2.
Each end device is represented by a UE FPGA platform consisting of a RISC-V processor and dedicated security modules. The RISC-V core handles control logic and data transmission tasks, while the cryptographic modules are implemented as coprocessors that accelerate key exchange, encryption, and digital signature operations. These security functions form the cryptographic guarantee and are implemented in hardware. On the server side, a corresponding software module performs verification and session management, acting as a trusted network endpoint. Security extensions such as hybrid signature operations and key primitives computation are integrated into this module to support secure interaction with FPGA-based UEs.
The NB-IoT communication framework is modeled in NS-3, which implements protocol procedures such as attach and data transfer. For each cryptographic operation, the FPGA execution latency and the corresponding output size (e.g., signature or public key) are exported via UART and injected into the simulation. As a result, the evaluation captures the joint behavior of hardware performance and network communication, yielding a holistic view of end-to-end NB-IoT security under realistic operating conditions.
5. NB-IoT Security Enhancement
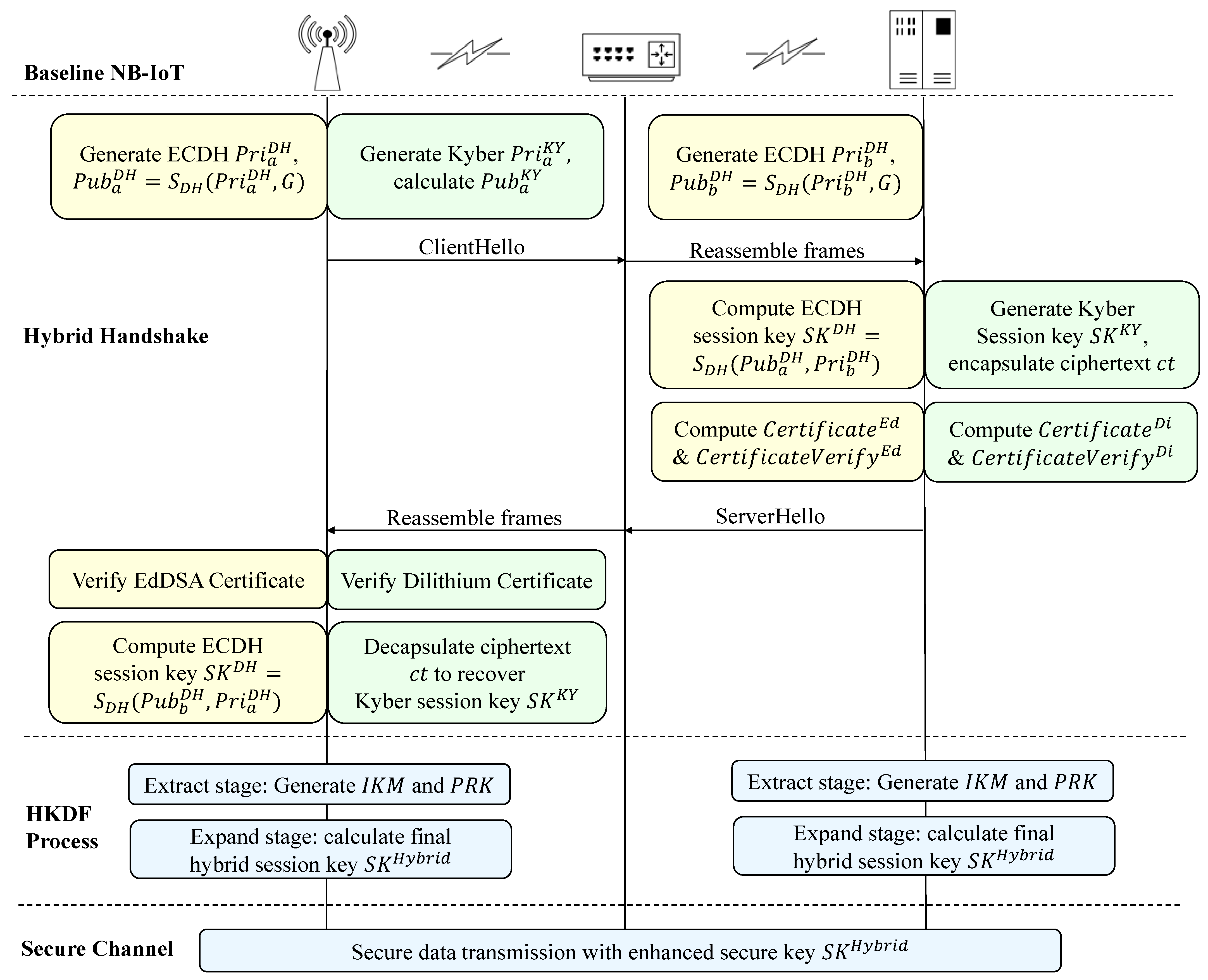
After the NB-IoT connection, the handshake process between the UE and the server establishes the foundation for secure end-to-end communication, shown in
Figure 7. It begins with the ClientHello, where the UE transmits its cryptographic key shares, including the ECDH public key and Kyber public key, to the server. This step provides the material needed for both classical and post-quantum key exchange. In response, the server issues a ServerHello, which contains its own ECDH and Kyber key shares, along with the certificate chain and certificate verification data, signed by both EdDSA and Dilithium algorithms.
After exchanging and verifying these cryptographic materials, both the UE and the server combine the secrets through the HKDF procedure to generate a single hybrid session key. Once key agreement and certificate verification are successful, the handshake is finalized in the Finished Handshake message. The application data transfer commences over the established secure channel, encrypted by the hybrid session key. This process ensures that confidentiality, authenticity, and integrity are preserved under both classical and quantum threat models while remaining compatible with NB-IoT communication flows.
5.1. Enhanced Hybrid Handshake with ECC and PQC
Figure 8 illustrates the hybrid handshake procedure in sequential flow. Firstly, the process begins with the establishment of a baseline NB-IoT connection between the UE and the server. In the second stage, the UE generates an ECDH key pair along with a Kyber public key, while the server simultaneously creates its own ECDH key pair on the same elliptic curve. Upon receiving the ECDH and Kyber public keys from the UE, the server computes the classical ECDH session key, encapsulates the Kyber ciphertext, and derives the associated Kyber shared secret. To ensure authenticity, the server also computes and transmits both a classical and a PQ certificate chain, and the UE verifies them before proceeding. The UE then calculates its own ECDH session key and decapsulates the ciphertext to recover the Kyber shared secret. In the third stage, both the UE and the server execute the HKDF procedure to combine the ECDH and Kyber secrets into a single hybrid session key, for the final communication in the secure channel.
The handshake protocol employs a counter-based mechanism for robust replay protection against both the ClientHello and ServerHello messages. The UE initiates the process by including a monotonically increasing Client Counter (C_client). The server validates the C_client by confirming it is strictly greater than the last recorded value for that UE; if successful, the server updates its stored C_client record and the handshake continues; otherwise, the handshake is aborted. Subsequently, the server includes its own incremented Server Counter (C_server) within the ServerHello. The UE performs a symmetric check on C_server. This validation approach ensures the freshness of both the initiation and response phases, effectively preventing the successful retransmission of any prior handshake message.
In the ECDH procedure, the UE is denoted as party
a, and the server is denoted as party
b. Each selects a private key
and
and computes their corresponding public keys
and
by the scalar multiplication of the private keys with the common base point
G on the elliptic curve. After exchanging public keys over the insecure channel, both sides compute the same shared secret
by scalar multiplication.
In the Kyber process, the UE samples a secret vector
and a noise vector
from a small distribution, and computes the public key
, where
A is a public matrix over the polynomial ring modulo
q. During encapsulation, the server executes the encapsulation algorithm, generating a ciphertext
along with the session key
. The components
u and
v are polynomial vectors that incorporate randomness and error terms, thereby concealing the secret and ensuring semantic security. The UE then applies decapsulation by using its private key
to process the ciphertext and recover the same shared secret
. This procedure ensures security by the hardness of the learning with errors problem. Extract stage:
Expand stage:
In the extract stage of the HKDF procedure, the input keying material is obtained by concatenating the shared secrets from ECDH and Kyber, ensuring that both classical and post-quantum contributions are integrated into the derivation process. A pseudorandom key is generated to prevent key reuse and strengthen entropy across sessions. The serves as a fixed-length intermediate secret with uniform distribution. In the expand stage, is iteratively combined with the application-specific context string, denoted as , and a counter to generate output blocks . The parameter provides binding to protocol context, and it is a concatenation of IMSI, device identifier, and , thereby linking the derived key to a specific device and session. The final hybrid session key is formed by concatenating these output blocks and truncating them to the required length suitable for secure communication.
The security of this hybrid scheme holds as long as at least one of the two primitives, ECC or PQC, remains unbroken. If ECC is compromised by quantum adversaries, the PQC component ensures post-quantum security. Conversely, if lattice-based cryptography is compromised in the future, ECDH still provides a classical fallback. This redundancy ensures authenticity, protocol agility, and robust confidentiality for NB-IoT deployment in mission-critical or delay-tolerant use cases.
5.2. Hybrid Authentication with Certificate and CertificateVerify
As illustrated in the
Figure 9, a hierarchical trust model is established through the root and intermediate certificate authority (CA). There are two distinct certificate chains, one for classical EdDSA and the other for post-quantum Dilithium. The root CA signs the intermediate CA, which in turn signs the server certificate. The server EdDSA certificate includes its EdDSA public key, along with standard metadata such as its unique identifier, certificate validity period, and usage constraints. A parallel process creates the Dilithium certificate, which contains the server Dilithium public key and similar metadata.
Along with the certificates, the server signs the handshake message using both EdDSA and Dilithium, and attaches the concatenated signatures to the response, which are the CertificateVerify. During the handshake, the server sends both EdDSA and Dilithium certificates and signatures to the UE.
The client UE extracts the public keys from the two certificate chains and then verifies both signatures using the corresponding public keys. The message is only accepted if both the classical and post-quantum verifications are successful, ensuring robustness against both current and future adversaries.
In the EdDSA process, the nonce
r is generated by hashing the upper half of the private key
together with the message
, reduced modulo
q, where
. The value
R is then obtained as the scalar multiplication of
r with the base point
G on Curve25519. A challenge
h is computed by hashing the concatenation of
R, the public key
, and the message
. The scalar
s combines the nonce
r, the challenge
h, and the lower half of the private key
, again reduced modulo
q. The final signature
is represented by the pair
, which binds the message, the signer keys, and the curve parameters to ensure authenticity and integrity.
For Dilithium, the signing process operates over a lattice structure using Module-LWE and rejection sampling to process the . The public key component t is defined by multiplying the matrix A with the secret vector and adding another secret vector under modulus q. To sign a message, the signer samples a short random vector y and computes w. This result is decomposed into two parts, where the higher order part and the message are used to derive a challenge polynomial c through the hash function. The signature vector z is then computed. A rejection sampling step verifies that the coefficients of both z and the residual term remain within strict bounds; otherwise, the process aborts and repeats. The final Dilithium signature is .
By requiring both EdDSA and Dilithium signatures to be valid, our enhanced certificate verification mechanism provides authenticity and integrity during the handshake process.
5.3. Trust Model
To address the absence of E2E security in NB-IoT, the proposed hybrid handshake protocol establishes direct cryptographic protection between the UE and the application server. Both parties present authenticated credentials under Ed25519 and Dilithium, issued by a trusted certificate authority. The key exchange secrets generated via X25519 and Kyber are securely combined using HKDF, which binds the session key to both the authenticated identities and the cryptographic contributions of each sides. This design ensures strong E2E confidentiality and authenticity, even in untrusted network infrastructures.
To mitigate the threat of side-channel attacks arising from physical access to deployed NB-IoT devices outside, the cryptographic hardware accelerators are implemented in an FPGA using constant-time execution principles. This approach ensures that critical operations, such as scalar multiplication and modular reduction, do not exhibit timing variation dependent on secret data. This approach provides a simple and effective solution to defend against physical adversaries monitoring the time variations of hardware operations.
To defend against downgrade attacks in hybrid post-quantum deployments, the protocol mandates the simultaneous presence and successful validation of both ECC and PQC components. During the handshake, HKDF derives the final session key only when both shared secrets of X25519 and Kyber are available and authenticated. Likewise, message verification requires valid signatures from both Ed25519 and Dilithium. If either the classical or quantum element is missing, malformed, or unverifiable, the handshake is aborted. This strict coupling enforces downgrade resistance by design and ensures that the final hybrid session key inherits the security assurances of both cryptographic security.
6. Evaluation and Discussion
6.1. Hardware Experiment Setup and Results
A customized cryptographic prototype is implemented on a Genesys 2 development board featuring a Kintex-7 XC7K325T FPGA. The hardware design is written in Verilog HDL and implemented using Xilinx Vivado 2020.2. The complete design includes the RISC-V core, DMA controller, peripherals, and dedicated cryptographic accelerators for ECC, hybrid NTT/INTT, and Kyber. Each security module is first synthesized and validated independently before being integrated into the full processor system. The resource utilization is summarized in
Table 2. The estimated static power is 0.18 W, and the dynamic power is 0.53 W.
The platform is configured to operate at a clock frequency of 50 MHz, with its bitstream programmed via JTAG interface. A USB-UART interface is connected to the serial port for runtime debugging. During execution, control messages, performance results, and intermediate values are printed from the development board to the host terminal. The application software is written in C and compiled with the RISC-V GCC toolchain, producing ELF binaries that are converted into memory initialization files, which are programmed into the board memory through the UART port.
To evaluate the performance benefits of hardware acceleration, both software-only (Pure SW) and SW/HW co-design implementations are tested on the platform. In the pure SW setup, all cryptographic functions execute entirely on the RISC-V processor. In contrast, the SW/HW co-design invokes dedicated hardware modules to offload critical operations such as key exchange and digital signatures.
The performance comparison is summarized in
Table 3. The ECDH scalar multiplication function, based on X25519, achieves a 145.4× speedup, reducing execution time from 642.5 ms in software to 4.42 ms in the co-design. EdDSA, which involves both SHA512 hashing and two scalar multiplications, achieves a 129.3× speedup.
For post-quantum functions, Kyber512 achieves a 118.9× speedup, with ciphertext encapsulation and shared key derivation executed in a single hardware pipeline. Dilithium2, which includes polynomial multiplication and hash-based rejection sampling, achieves a 32.2× speedup. The modular arithmetic, NTT, and hashing stages are all accelerated in hardware, significantly reducing processor load.
The energy cost per operation is calculated as , where W is the measured dynamic power and t is the FPGA function execution latency. Based on this method, the energy per operation is approximately 2.3 mJ for X25519, 1.3 mJ for Kyber512, 4.3 mJ for Ed25519, and 20.2 mJ for Dilithium2, yielding approximately 28 mJ for a complete hybrid handshake. While our measurements are obtained on an FPGA prototype rather than a battery powered node, the reported energy values provide a practical reference: assuming ten handshakes per day, the annual consumption is on the order of 100 J, which is acceptable compared to the tens of kilojoules typically available from IoT batteries. The analysis substantiates the viability of the proposed scheme for long-term deployment under NB-IoT constraints.
6.2. NS-3 NB-IoT Network Simulation Test
To evaluate the network-level behavior of hybrid cryptographic schemes in NB-IoT, we employ the NS-3 network simulator [
33], a widely adopted tool for packet-level simulation in wireless communication research. NS-3 supports 4G LTE networks through the LENA module and can be extended to emulate NB-IoT behavior [
34]. In our experiment, a single eNodeB is positioned at the center of a circular simulation area with a radius of one kilometer. A configurable number of UE nodes (e.g., 1 to 50) are randomly deployed within the coverage region and maintain fixed positions using a constant position mobility model. Each UE represents a constrained IoT terminal and initiates a connection to the core network via NB-IoT attach procedures.
On the server side, a remote host is instantiated to simulate the CIoT application server. Each UE runs a custom socket-based client application that mimics the behavior of handshake and payload transmission. Corresponding server applications are hosted on the remote node to receive the data and respond accordingly. The eNodeB and core network components are configured with a single 180 kHz PRB channel (CE0 level) to reflect constrained NB-IoT bandwidth. To accommodate multi-kilobyte handshake payloads, including public keys, ciphertexts, and digital signatures, the simulation uses NB-IoT User Plane (UP) transmission, with the NB-IoT stack handling fragmentation and reassembly. This setup enables analysis of latency, scheduling contention, and throughput degradation under varying UE densities.
Table 4 summarizes the handshake traffic for ECC, PQC, and the hybrid scheme. ECC exchanges very small key shares of 38 bytes and 36 bytes, and short certificates and signatures. The traffic size of PQC scheme increases significantly due to the lattice-based construction, with Dilithium signatures (690 bytes) being an order of magnitude larger than their ECC counterparts. The total traffic exceeds the direct sum of cryptographic outputs, because handshake messages also include protocol headers, as well as framing and concatenation overhead. As a result, the hybrid handshake reaches the most significant traffic volume of about 18.5 kB.
In our evaluation, FPGA-based accelerators are abstracted as cryptographic service APIs interfaced with the host. Each cryptographic operation is independently executed on the FPGA, and the measured hardware latency is injected into NS-3 as an event delay. In this way, the handshake latency accounts for both the simulated handshake communication period (from ns-3) and the hardware computation period (from FPGA). The simulated communication process is defined as the sequence diagram shown in
Figure 7, and the hardware computation process is summarized as the SW/HW co-design time in
Table 3. Payload sizes used in NS-3 are configured to match the actual byte lengths of ECC and PQC cryptographic outputs. For our evaluation objectives, this timing abstraction offers a practical yet accurate means to capture the end-to-end performance impact of cryptographic processing.
We simulate the cryptographic handshake process for NB-IoT using NS-3, and evaluate the performance of three schemes under varying device densities: classical ECC (X25519 + Ed25519), post-quantum PQC (Kyber512 + Dilithium2), and HYBRID (ECC + PQC) construction.
Figure 10a illustrates the measured handshake latency for each cryptographic scheme. As expected, the ECC-based method consistently achieves the lowest latency due to its smaller payload size and simpler packet structure. In contrast, the PQC and Hybrid methods introduce larger handshake payloads, resulting in increased latency as network congestion increases. Nevertheless, both remain practical for NB-IoT, with hybrid latency only slightly exceeding that of PQC alone. The throughput results calculated as the ratio of the handshake traffic size to the latency, are shown in
Figure 10b. Although the PQC and HYBRID schemes exhibit a slightly steeper decline in throughput as the number of UEs increases, their overall throughput does not differ significantly from that of the ECC scheme. This indicates that even with the larger payloads, both PQC and HYBRID solutions maintain acceptable performance for NB-IoT networks.
6.3. Comparison with Similar Works
In our enhanced NB-IoT system, post-quantum and classical public-key cryptographic algorithms are integrated into the end device platform through a lightweight RISC-V-based processor and dedicated hardware accelerators prototyped on an FPGA. Compared to standard NB-IoT security, which terminates encryption at the MME and lacks end-to-end security, our system introduces ECDH and Kyber for key exchange and supports EdDSA and Dilithium for digital signatures. The system enables secure session key derivation and payload authentication for safe data transmission. NS-3 simulation results further validate the feasibility of integrating hybrid schemes in NB-IoT, demonstrating acceptable latency and throughput across an increasing number of UEs.
Table 5 summarizes recent works on the hardware accelerations for security algorithms. Turan and Verbauwhede [
35] present a unified ECC accelerator, implemented on the Xilinx Zynq-7020, and their design supports both X25519 key exchange and Ed25519 signatures within a shared datapath architecture. To enhance flexibility, the accelerator integrates microcode programmability, enabling the reuse of arithmetic units across operations, and it also explores optional countermeasures against side-channel and fault injection attacks. While the unified architecture is similar to ours, our ECC design is more lightweight, requiring nearly half the resources but incurring about three times the computation cycles.
For the NTT work, Zhou et al. [
36] designed a hardware architecture for polynomial vector operations, including NTT, INTT, point-wise multiplication, and point-wise addition. Twiddle factors are generated on the fly and processed simultaneously with butterfly operations, with separate computation flows for CT-NTT and GS-INTT. In contrast, our work implements a hybrid architecture for both NTT and INTT, adopting symmetry in the twiddle factors and storing precomputed values in ROM. By combining control logic and reusing computing resources, we achieve a more compact design. Our implementation requires more cycles but consumes only one-third of the resources, which is more suitable for lightweight NB-IoT application scenarios.
Ref. [
37] presents a fully hardware implementation of Kyber with higher computation speed and a lower ATP compared to our work. In contrast, our design is more lightweight in resource usage, making it more suitable for resource-constrained NB-IoT devices.
Some works also tried to enhance the security of IoT network communication, as summarized in
Table 6. Sabanci et al. [
18] investigated the feasibility of integrating post-quantum cryptographic schemes into the TLS 1.3 handshake in NB-IoT networks. Their approach remains software-based and simulates the behavior of Kyber, Falcon, and Dilithium within the TLS context. Their work ensures end-to-end security using standardized cryptographic libraries (e.g., OpenSSL with libOQS), while maintaining compatibility with the existing NB-IoT stack. However, they did not explore the hybrid ECC + PQC scheme. In addition, their cryptographic operations are performed in software on a general-purpose processor, and no hardware acceleration is considered. By contrast, we provide a hybrid system solution. In our system, the post-quantum and classical primitives are accelerated in hardware using modular ECC, NTT, and Kyber modules.
The work by Cavo et al. [
38] focuses on an area- and power-efficient crypto processor tailored for 3GPP-LTE NB-IoT devices. They propose a unified crypto architecture with shared datapath and control logic to support the confidentiality and integrity algorithms defined in LTE Release 13, including SNOW 3G, AES, and ZUC. Their implementation achieves significant area and power savings, with a total processor footprint of 53.6 kGE in 65 nm CMOS and an estimated SNOW 3G cipher power consumption of 0.81 mW. However, their solution is limited to standard NB-IoT and does not support end-to-end (E2E) cryptographic guarantees. In comparison, our work presents a hybrid cryptographic platform that integrates both classical ECC-based and post-quantum schemes to protect payloads directly, independent of the underlying network stack.
Mao et al. [
39] propose the REALISE framework, a RISC-V-based secure processor for LoRaWAN communication that integrates ECC cryptographic primitives, including ECDH and EdDSA, into a customized FPGA-based SoC. Their architecture is built upon the PULPino platform and supports lightweight key exchange and digital signature operations with hardware accelerators. The work achieves significant speedups compared to software-only execution, and demonstrates the feasibility of public-key cryptography in low-power IoT nodes. Their work focuses on single-mode ECC and targets LoRaWAN limited payload and protocol stack. Our work builds upon this architecture and extends it to support a broader and more future-proof cryptographic landscape. Specifically, we introduce hybrid post-quantum and classical schemes, including Kyber and Dilithium alongside ECDH and EdDSA, to enhance security against both classical and quantum threats. Furthermore, our work explored the handshake process simulation. We simulate real NB-IoT conditions using NS-3 and perform controlled experiments with increasing UE density, providing insights into latency and throughput.
The work by Hanna [
40] presents a comprehensive performance evaluation of post-quantum TLS in consumer IoT environments. Their main strength lies in building a realistic IoT testbed that integrates PQ KEMs and digital signatures into TLS over both Wi-Fi and Bluetooth Low Energy, while also incorporating certificate chains, revocation mechanisms (CRL/OCSP), and mutual authentication. This allows them to measure handshake latency, communication overhead, and energy consumption under practical constraints, and they further propose a dynamic PQ algorithm switching mechanism to adapt cryptographic choices to device interfaces and resource conditions. Compared with this approach, our contribution emphasizes a hardware solution. We design and implement a hybrid FPGA platform that integrates PQC and ECC primitives, achieving a hardware computation speed that is faster than their work running on a Raspberry Pi.
7. Conclusions
This work presents a hybrid cryptographic architecture that integrates both classical and post-quantum primitives for long-term secure communication in NB-IoT systems. By leveraging a RISC-V-based processor and three hardware accelerators, supporting ECC, CRYSTALS-Dilithium, and Kyber, the proposed platform achieves significant improvements in both performance and cryptographic agility. Hardware/software co-design allows the system to offload computation-intensive cryptographic operations, resulting in up to 145.4× speedup compared to software-only implementations. In addition, we introduce protocol-level enhancements that provide end-to-end encryption and robust digital signatures using hybrid key exchange and signing schemes. These enhancements are implemented at the top of the network stack, preserving full compatibility with existing NB-IoT infrastructure. Experimental results validate that the proposed solution not only offers robust protection against quantum and classical threats but also ensures lightweight and scalable performance suitable for resource-constrained IoT devices. This work paves the way for deploying practical hybrid post-quantum and classical cryptography in next-generation IoT networks.
7.1. Limitations
While our proposed hybrid cryptographic architecture demonstrates promising performance and quantum resilience, this initial study highlights several technical areas requiring further investigation to achieve a fully deployed system. Firstly, this paper provides a preliminary analysis of the security properties; however, formal security proofs and a comprehensive security analysis against known cryptographic attacks are necessary for complete validation. Secondly, the network layer evaluations are performed solely through simulations, which may not fully capture the inherent complexities and dynamic behavior of real-world NB-IoT environments. Furthermore, the current prototype primarily focuses on the initial secure channel establishment. Integrating a complete certificate life cycle management solution remains a critical next step. Finally, the current implementation lacks the integration of advanced session resumption capabilities, which are essential for frequently sleeping or roaming devices in NB-IoT networks.
7.2. Future Work
Our future work will focus on two main aspects: hardware and software advancements, with the goal of transitioning this conceptual work into a robust, deployable solution. On the hardware side, we aim to develop an application-specific integrated circuit (ASIC) for the proposed cryptographic architecture to further reduce power consumption and optimize performance beyond the current RISC-V platform. This will include dedicated efforts to analyze and minimize the energy footprint of the hybrid cryptographic operations. On the software side, our next steps involve conducting real-world testing with NB-IoT devices to thoroughly evaluate the system performance, resilience, and security in practical deployment scenarios. This includes a comprehensive security analysis of the entire system and the implementation of robust session resumption strategies for asleep devices and roaming cells. Additionally, it is better to further develop lightweight certificate revocation methods to ensure full certificate life cycle management.