Performance Analysis and Security Preservation of DSRC in V2X Networks
Abstract
1. Introduction and Background
1.1. V2X Technologies and Standards
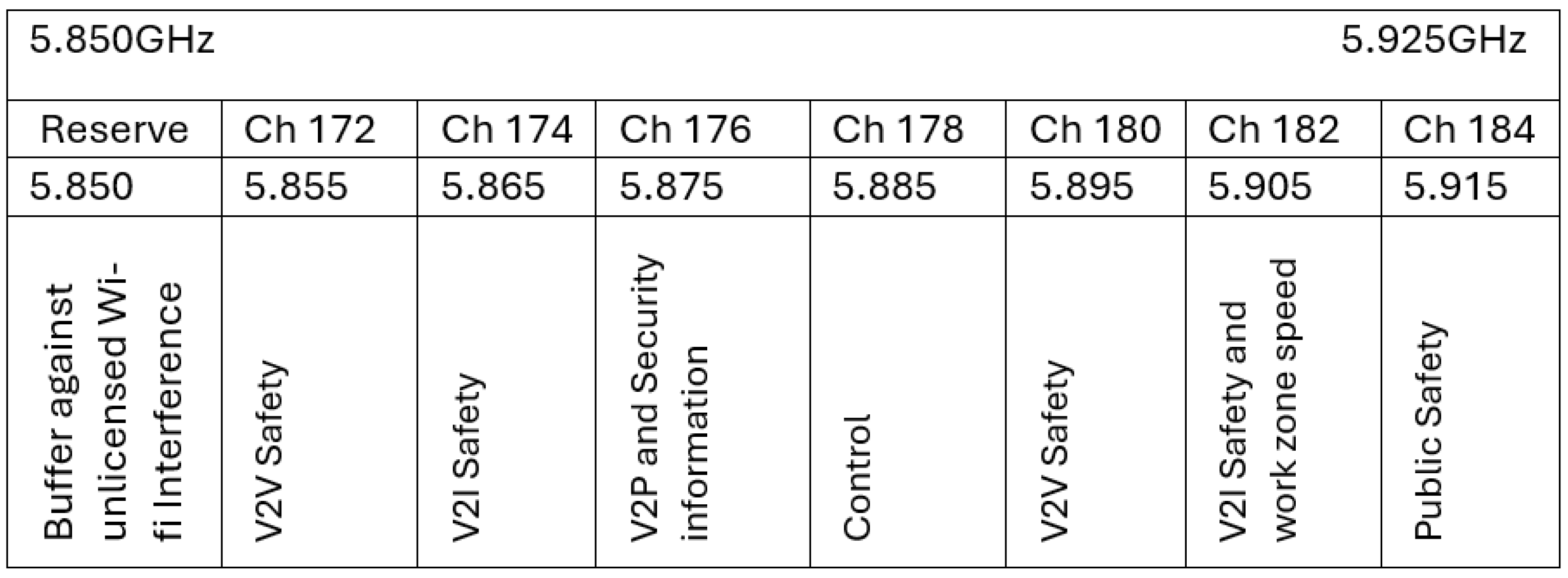
1.2. DSRC
- It presents an open-source tool that implements an OBU-RSU communication based on the 802.11p protocol;
- It proposes an open-source SDR-based tool to test the robustness of DSRC against cyber attacks, to personalize the performed security tests and the implemented cyber attacks;
- It presents the results obtained by the security assessment tests performed by implementing jamming and replay attacks against two V2X testbeds.
2. Related Works
3. Materials and Methods
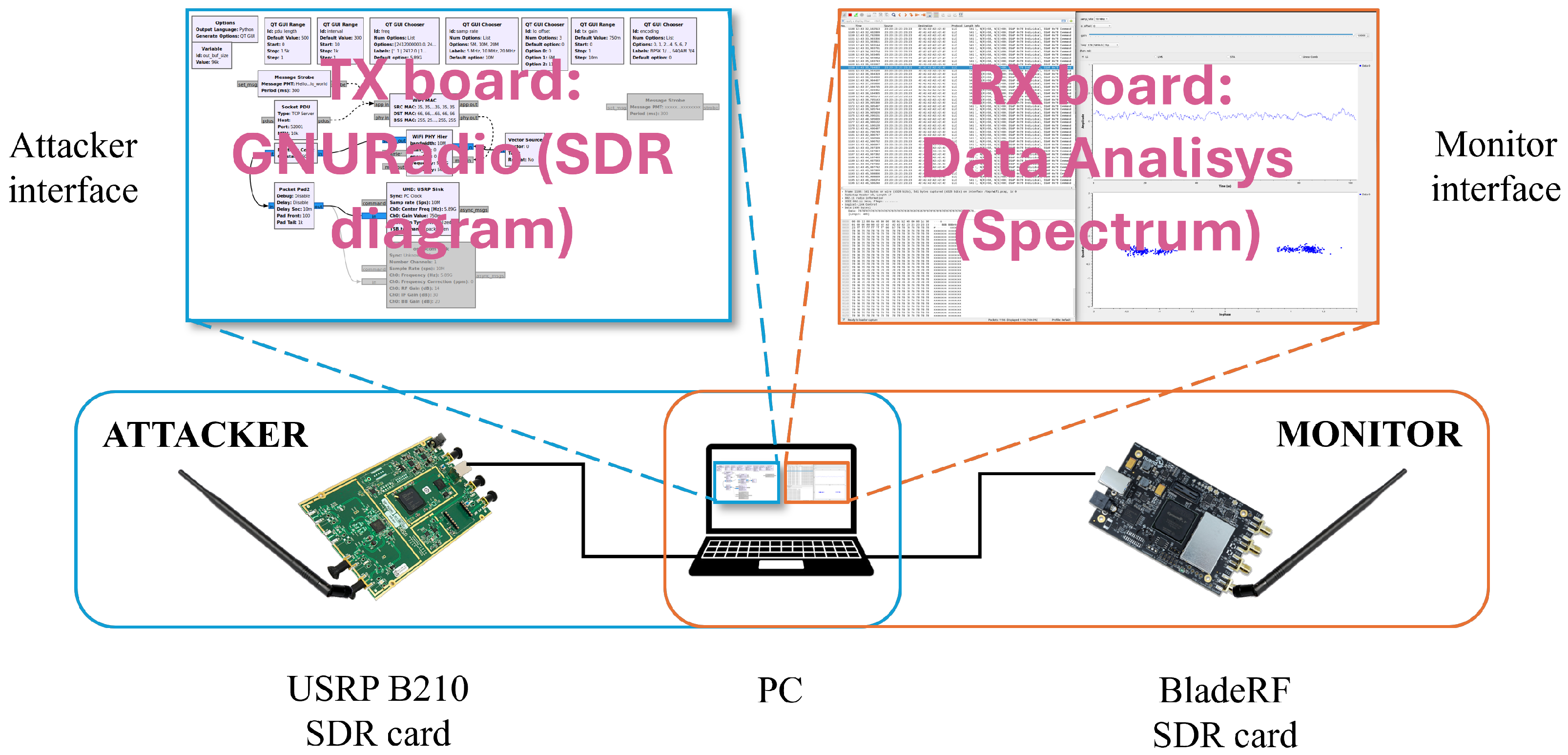
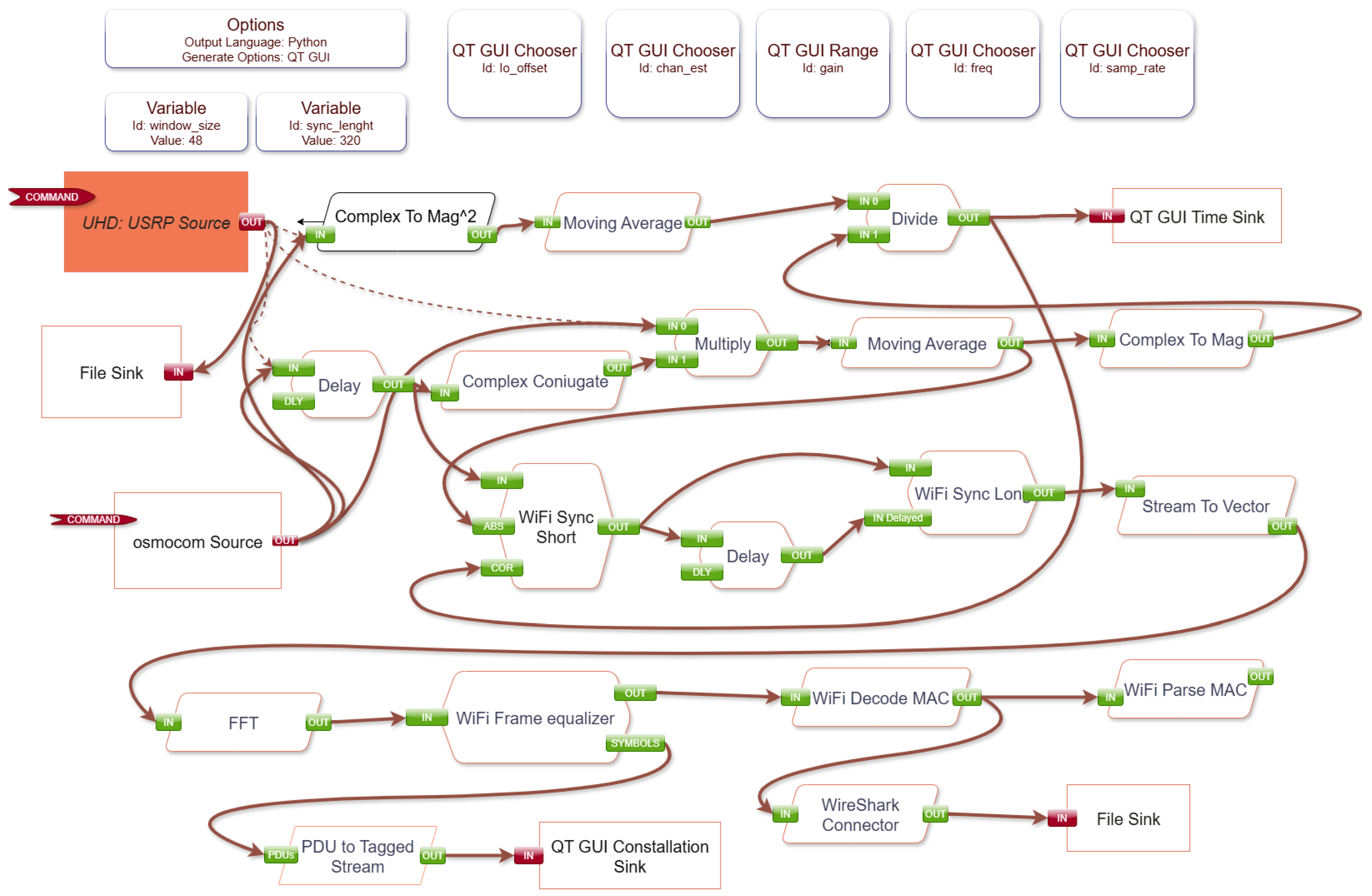
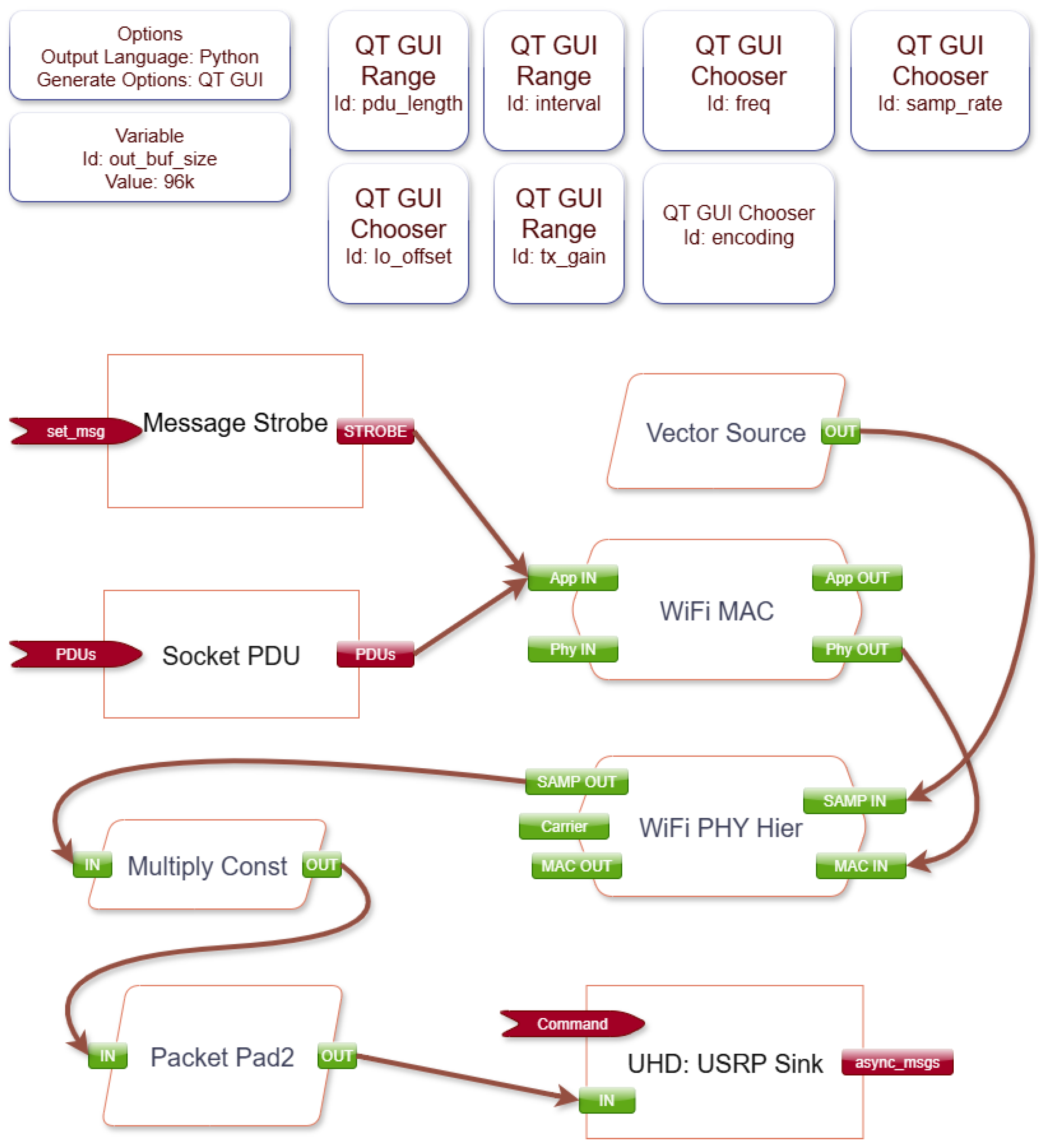
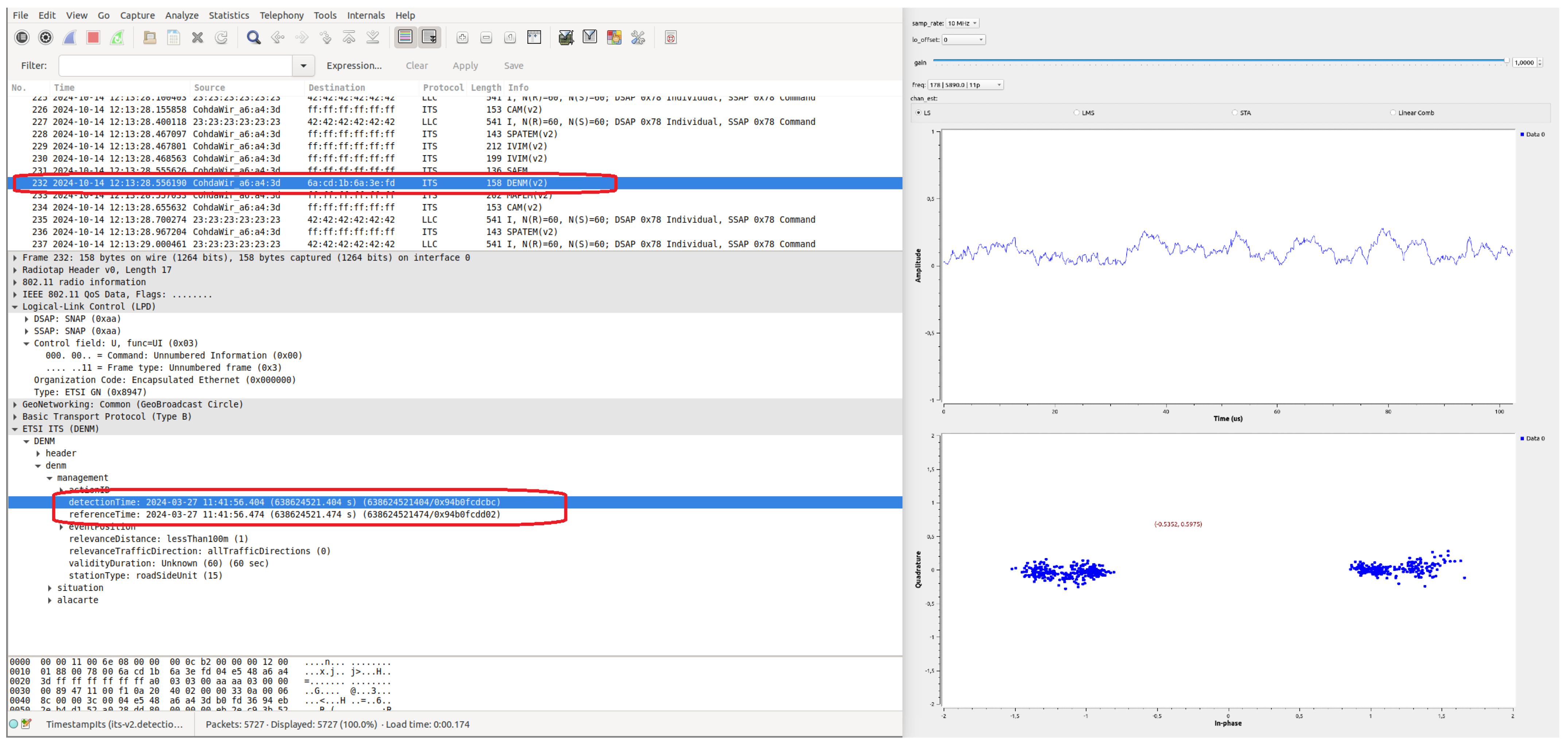
3.1. SDR-Based Security Assessment Tool
3.2. Reproducibility and Open Source Implementation
- Core GNU Radio flowgraph files: wifi_tx_RSU.grc (RSU transmitter), wifi_rx_OBU.grc (OBU receiver), jamming_attack.grc (jamming implementation), capture_for_replayattack.grc and transmitter_replay.grc (replay attack phases), and transmitter_108.11p_cohdawireless_replayattack.grc (Cohda Wireless compatibility);
- Environment setup script (setup_env.sh) for GNU Radio 3.8.5 configuration;
- Hardware requirements and system configuration details (checklist.txt);
- Detailed receiver operation instructions (INSTRUCTION_RX.txt).
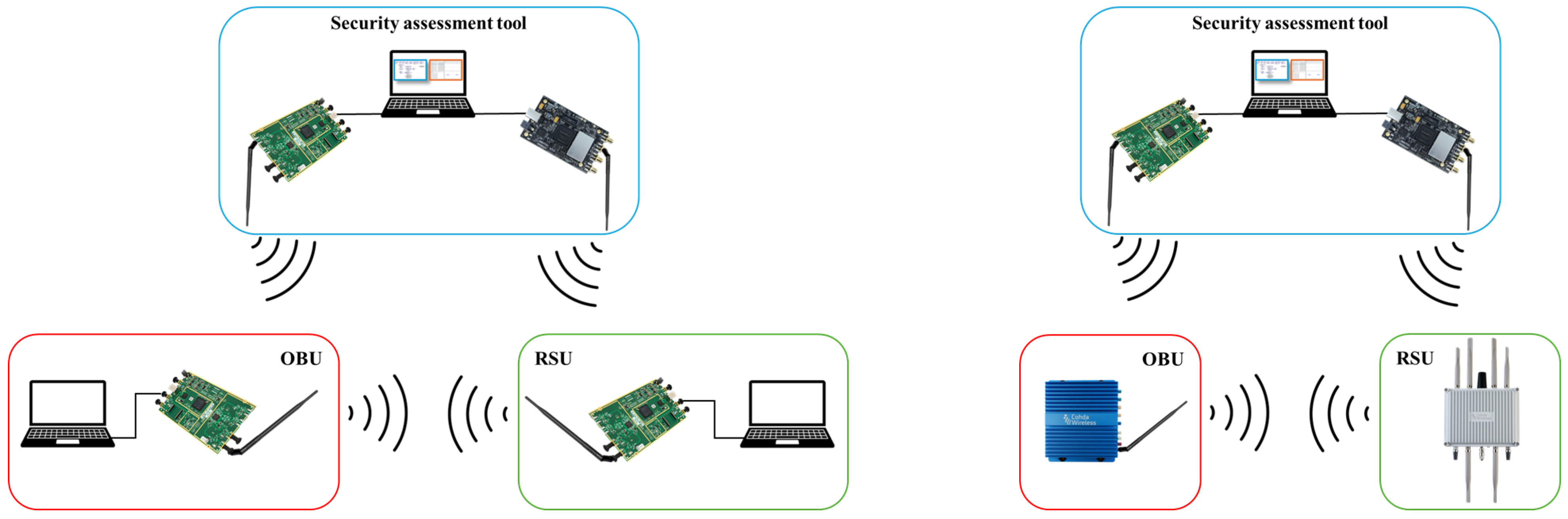
3.3. V2X Reference Scenario and Testbeds
3.4. Security Assessment Tests
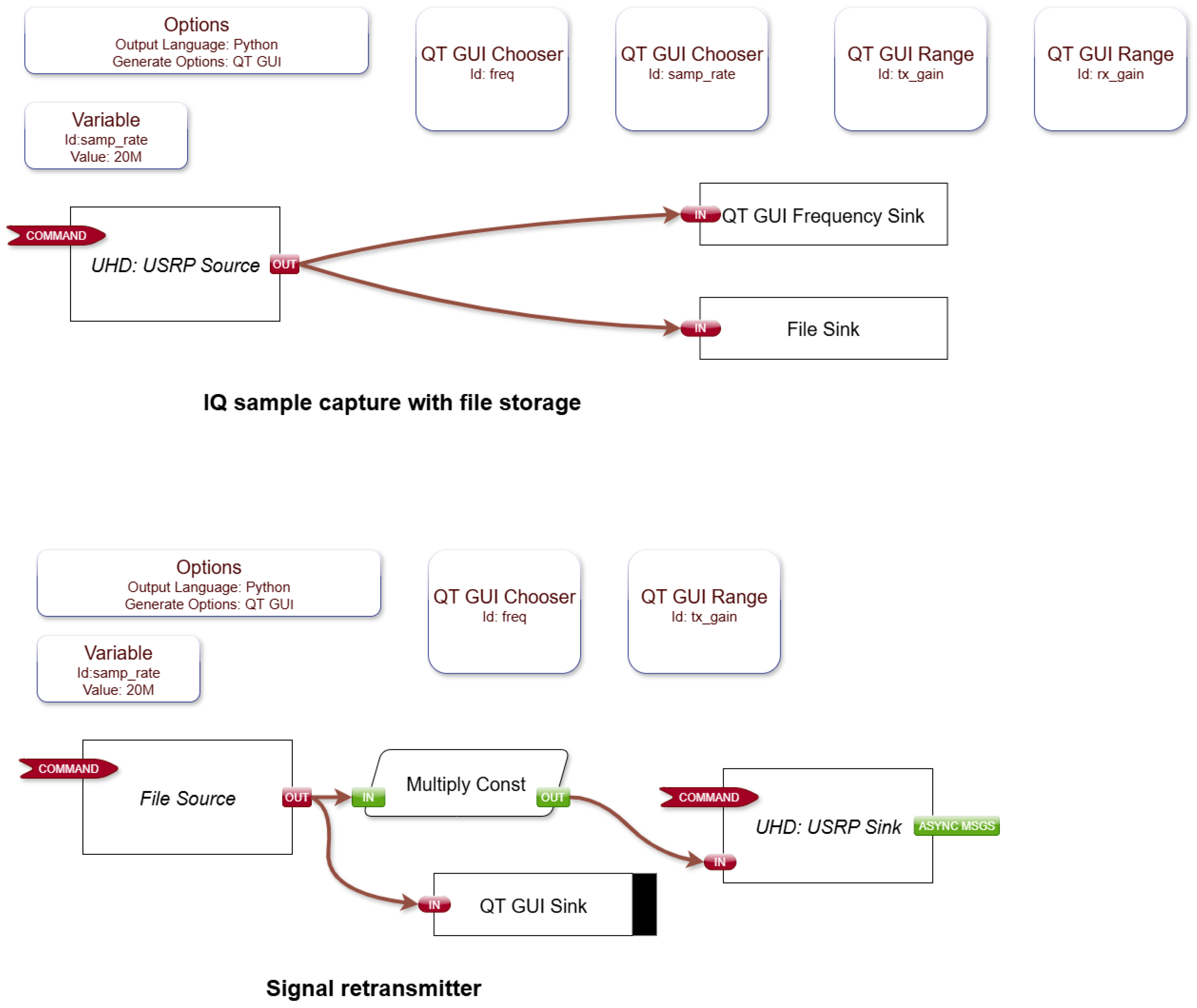
3.4.1. Jamming Attack
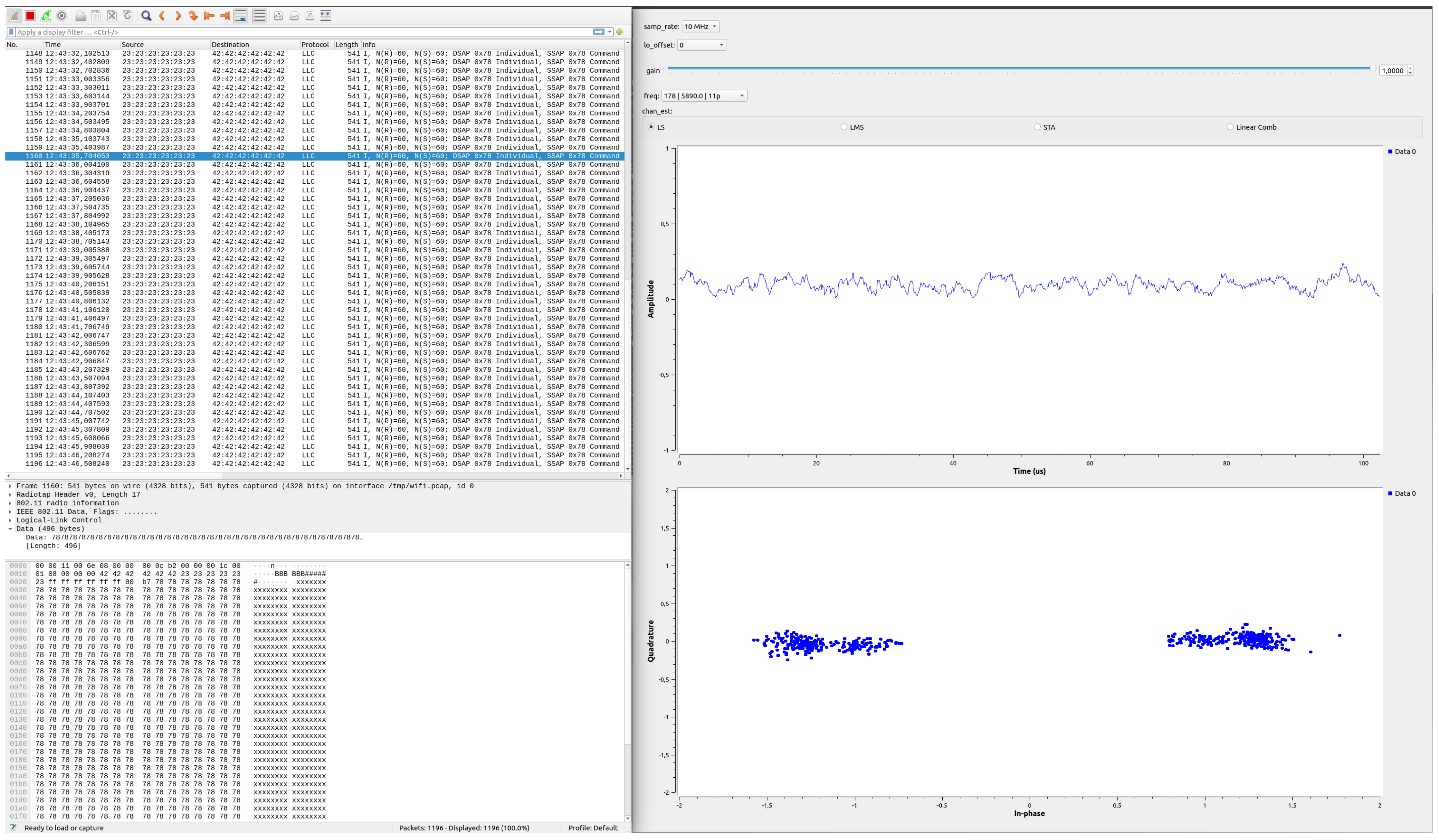
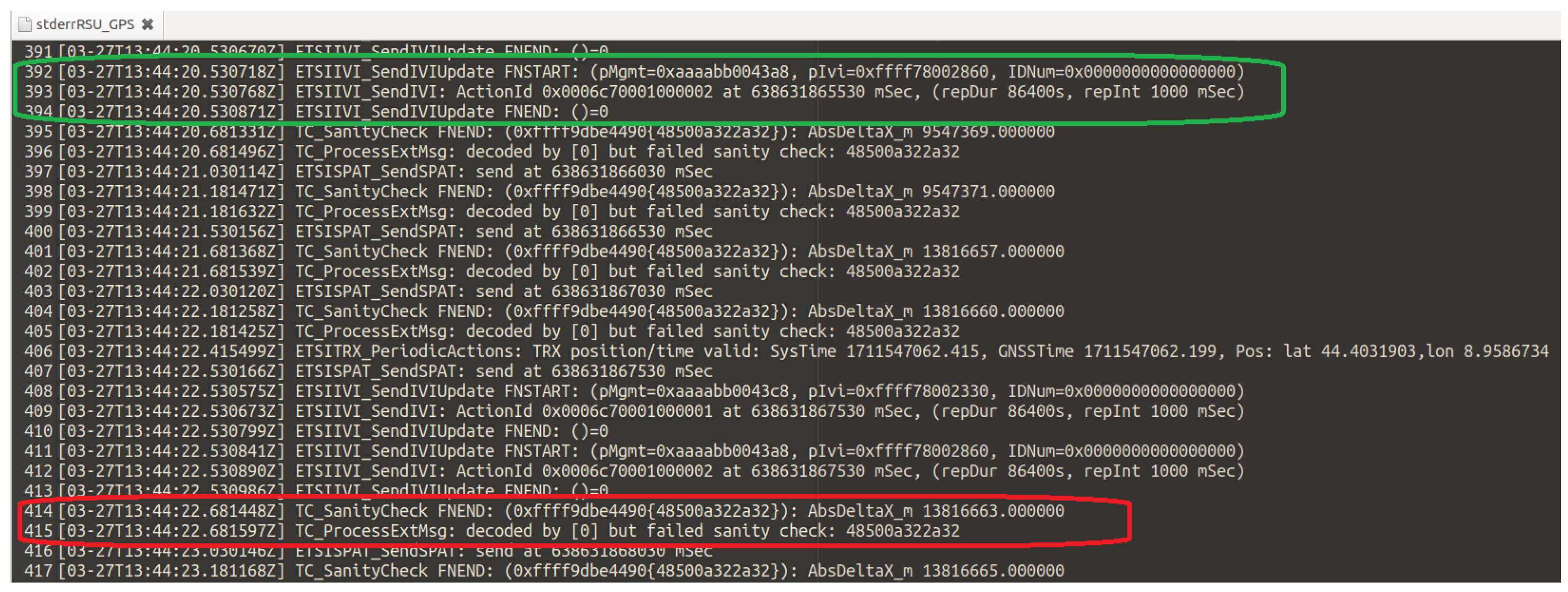
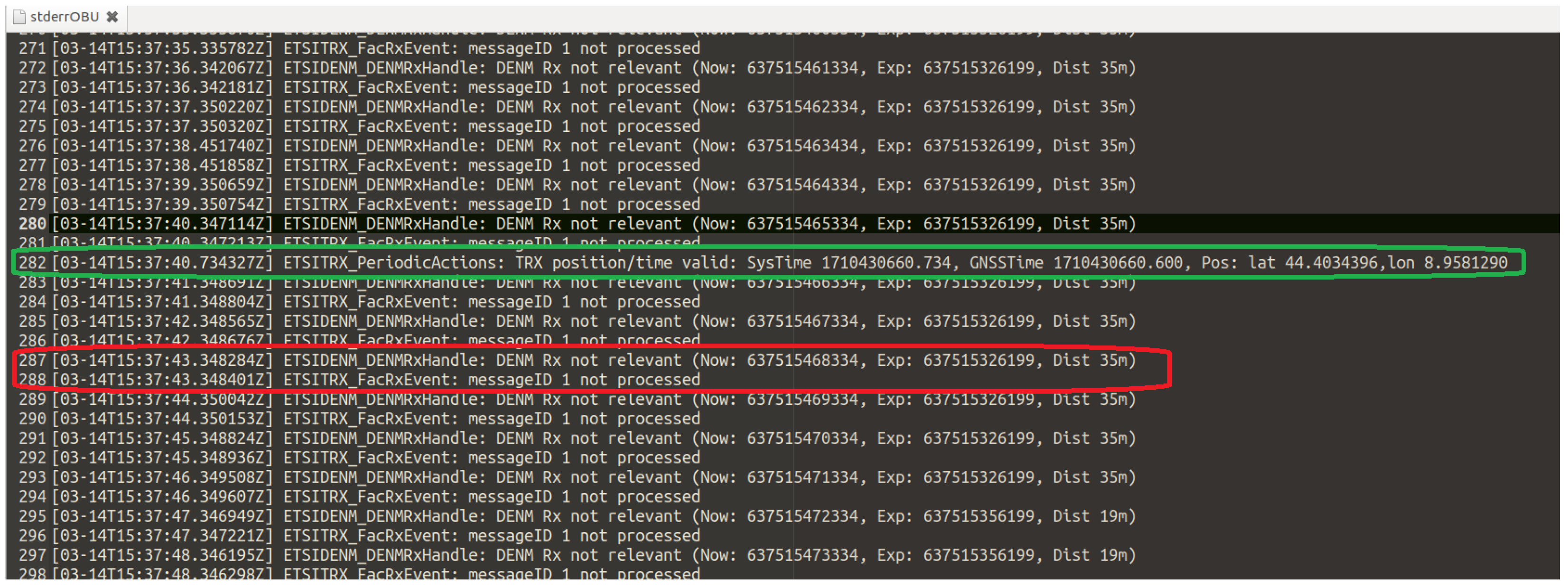
3.4.2. Replay Attack
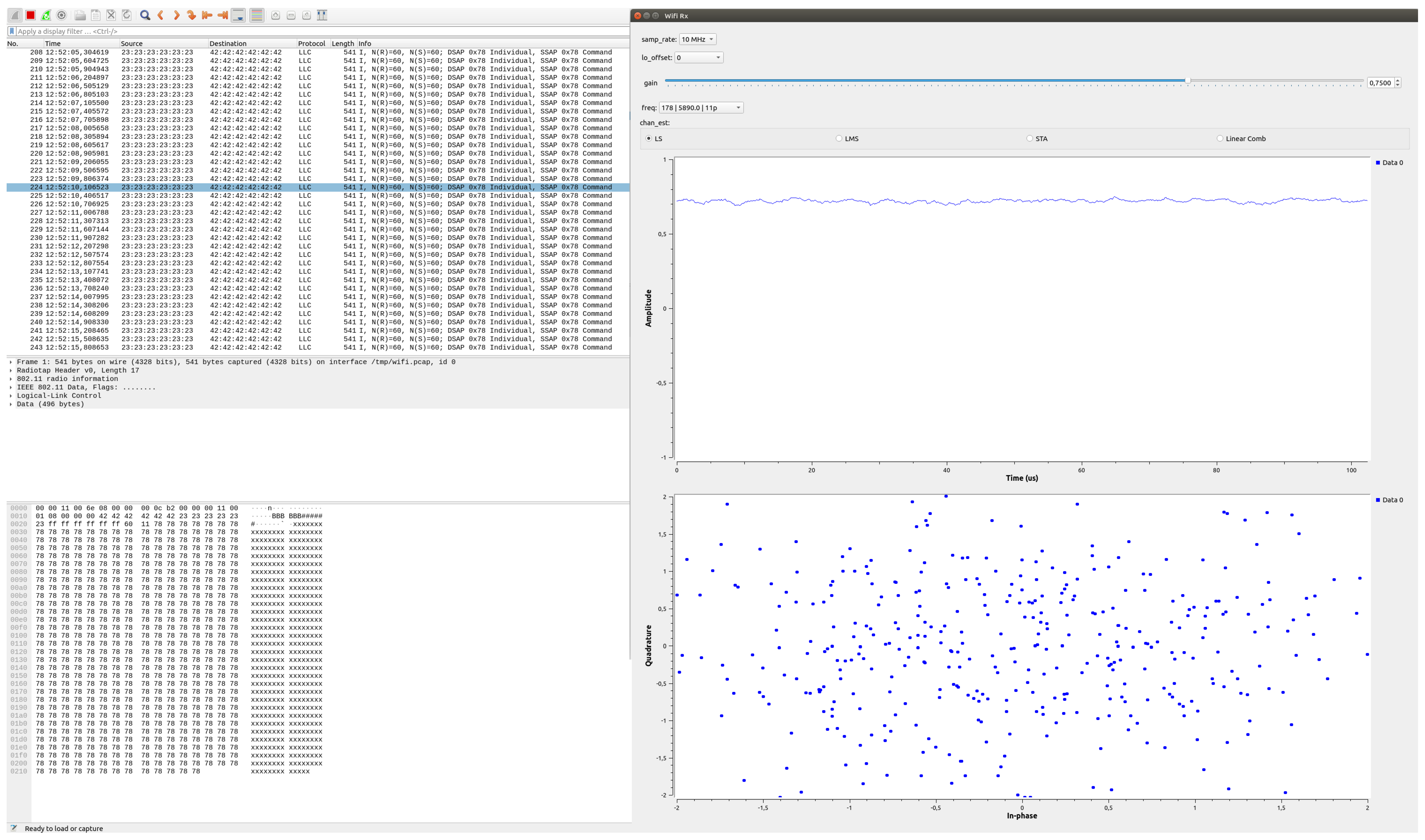
4. Results
4.1. Jamming Attack
4.2. Replay Attack
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| V2X | Vehicle-to-Everything |
| DSRC | Dedicated Short-Range Communications |
| SDR | Software-Defined Radio |
| V2V | Vehicle-to-Vehicle |
| V2I | Vehicle-to-Infrastructure |
| OBU | On-Board Unit |
| RSU | Road-Side Unit |
| ITS | Intelligent Transportation Systems |
| CAM | Cooperative Awareness Message |
| DENM | Decentralized Environmental Notification Message |
| SPaT | Signal Phase and Timing |
| IVI | In-Vehicle Information |
| OFDM | Orthogonal Frequency Division Multiplexing |
| BPSK | Binary Phase Shift Keying |
| SNR | Signal-to-Noise Ratio |
| C-V2X | Cellular V2X |
| SINR | Signal-to-Interference-plus-Noise Ratio |
| EIRP | Effective Isotropic Radiated Power |
| INR | Interference-to-Noise Ratio |
References
- Ahmed, S.; Hossain, M.A.; Ray, S.K.; Bhuiyan, M.M.I.; Sabuj, S.R. A study on road accident prediction and contributing factors using explainable machine learning models: Analysis and performance. Transp. Res. Interdiscip. Perspect. 2023, 19, 100814. [Google Scholar] [CrossRef]
- Pali, I.; Amin, R.; Abdussami, M. Autonomous vehicle security: Current survey and future research challenges. Secur. Priv. 2024, 7, e367. [Google Scholar] [CrossRef]
- Ward, L.; Simon, M. Intelligent transportation systems using IEEE 802.11 p. Rohde Schwarz-Appl. 2019. Available online: https://www.techonline.com/tech-papers/intelligent-transportation-systems-using-ieee-802-11p/ (accessed on 16 September 2025).
- Molinaro, A.; Campolo, C.; Marsan, M.; Melazzi, N.; Buzzi, S.; Palazzo, S. 5G for V2X Communications. In 5G Italy White eBook; CNIT: Pisa, Italy, 2019; pp. 1–10. [Google Scholar]
- Li, J.; Zhou, H.; Wu, S.; Luo, X.; Wang, T.; Zhan, X.; Ma, X. FOAP: Fine-Grained Open-World Android App Fingerprinting. In Proceedings of the 31st USENIX Security Symposium (USENIX Security ’22), Boston, MA, USA, 10–12 August 2022; pp. 1579–1596. [Google Scholar]
- Ni, T.; Lan, G.; Wang, J.; Zhao, Q.; Xu, W. Eavesdropping Mobile App Activity via Radio-Frequency Energy Harvesting. In Proceedings of the 32nd USENIX Security Symposium (USENIX Security ’23), Anaheim, CA, USA, 9–11 August 2023; pp. 3511–3528. [Google Scholar]
- Mir, Z.H.; Toutouh, J.; Filali, F.; Ko, Y.B. Enabling DSRC and C-V2X Integrated Hybrid Vehicular Networks: Architecture and Protocol. IEEE Access 2020, 8, 180909–180927. [Google Scholar] [CrossRef]
- Zhou, H.; Xu, W.; Chen, J.; Wang, W. Evolutionary V2X Technologies Toward the Internet of Vehicles: Challenges and Opportunities. Proc. IEEE 2020, 108, 308–323. [Google Scholar] [CrossRef]
- Garcia, M.H.C.; Molina-Galan, A.; Boban, M.; Gozalvez, J.; Coll-Perales, B.; Şahin, T.; Kousaridas, A. A Tutorial on 5G NR V2X Communications. IEEE Commun. Surv. Tutorials 2021, 23, 1972–2026. [Google Scholar] [CrossRef]
- Moradi-Pari, E.; Tian, D.; Bahramgiri, M.; Rajab, S.; Bai, S. DSRC Versus LTE-V2X: Empirical Performance Analysis of Direct Vehicular Communication Technologies. IEEE Trans. Intell. Transp. Syst. 2023, 24, 4889–4903. [Google Scholar] [CrossRef]
- Wang, J.; Shao, Y.; Ge, Y.; Yu, R. A Survey of Vehicle to Everything (V2X) Testing. Sensors 2019, 19, 334. [Google Scholar] [CrossRef]
- El-Rewini, Z.; Sadatsharan, K.; Selvaraj, D.F.; Plathottam, S.J.; Ranganathan, P. Cybersecurity challenges in vehicular communications. VEhicular Commun. 2020, 23, 100214. [Google Scholar] [CrossRef]
- P802.11-REVmd/D2.0; December 2018—IEEE Draft Standard for Information Technology—Telecommunications and Information Exchange Between Systems Local and Metropolitan Area Networks—Specific Requirements—Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications. IEEE: New York, NY, USA, 2019; pp. 1–4601. Available online: https://ieeexplore.ieee.org/document/8624660/versions#versions (accessed on 16 September 2025).
- Khan, A.R.; Jamlos, M.F.; Osman, N.; Ishak, M.I.; Dzaharudin, F.; Yeow, Y.K.; Khairi, K.A. DSRC Technology in Vehicle-to-Vehicle (V2V) and Vehicle-to-Infrastructure (V2I) IoT System for Intelligent Transportation System (ITS): A Review. In Proceedings of the Recent Trends in Mechatronics Towards Industry 4.0; Ab Nasir, A.F., Ibrahim, A.N., Ishak, I., Mat Yahya, N., Zakaria, M.A., Abdul Majeed, A.P.P., Eds.; Springer: Singapore, 2022; pp. 97–106. [Google Scholar]
- Moradi, A.; Zhang, W.; Liu, Y. Comparative analysis of DSRC and C-V2X technologies for vehicular communications. IEEE Trans. Veh. Technol. 2023, 72, 9876–9890. [Google Scholar]
- ETSI EN 303 797; Intelligent Transport Systems; Access Layer for ITS-G5 Including IEEE 802.11bd, Physical Layer and MAC Layer. ETSI: Sophia Antipolis, France, 2024. Available online: https://www.etsi.org/deliver/etsi_en/303700_303799/303797/02.01.01_60/en_303797v020101p.pdf (accessed on 16 September 2025).
- Electronic Communications Committee ECC Report 269: Least Restrictive Technical Conditions for Mobile/Fixed Communication Networks (MFCN), Including IMT, in the 1427–1518 MHz Frequency Band. Technical Report, CEPT, Copenhagen, Denmark, November 2017. Available online: https://docdb.cept.org/download/1309 (accessed on 16 September 2025).
- Fitah, A.; Badri, A.; Moughit, M.; Sahel, A. Performance of DSRC and Wi-Fi for Intelligent Transport Systems in VANET. Procedia Comput. Sci. 2018, 127, 360–368. [Google Scholar] [CrossRef]
- Wu, X.; Subramanian, S.; Guha, R.; White, R.G.; Li, J.; Lu, K.W.; Bucceri, A.; Zhang, T. Vehicular Communications Using DSRC: Challenges, Enhancements, and Evolution. IEEE J. Sel. Areas Commun. 2013, 31, 399–408. [Google Scholar] [CrossRef]
- ElHalawany, B.M.; El-Banna, A.A.A.; Wu, K. Physical-Layer Security and Privacy for Vehicle-to-Everything. IEEE Commun. Mag. 2019, 57, 84–90. [Google Scholar] [CrossRef]
- 1609.2-2016; IEEE Standard for Wireless Access in Vehicular Environments-Security Services for Applications and Management Messages. IEEE: New York, NY, USA, 2016; 1609, p. 30. [CrossRef]
- Vasudev, H.; Das, D. A Lightweight Authentication Protocol for V2V Communication in VANETs. In Proceedings of the IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computing, Scalable Computing & Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation (SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI), Guangzhou, China, 8–12 October 2018; pp. 1237–1242. [Google Scholar]
- Alnasser, A.; Sun, H.; Jiang, J. Cyber security challenges and solutions for V2X communications: A survey. Comput. Netw. 2019, 151, 52–67. [Google Scholar] [CrossRef]
- Lee, Y.; Woo, S.; Song, Y.; Lee, J.; Lee, D.H. Practical vulnerability-information-sharing architecture for automotive security-risk analysis. IEEE Access 2020, 8, 120009–120018. [Google Scholar] [CrossRef]
- Samara, G.; Hussein, M.; AL-Qawasmi, K. Alarm System at Street Junctions (ASSJ) to Avoid Accidents Using VANET System. In Proceedings of the Global Congress on Electrical Engineering (GC-ElecEng), Valencia, Spain, 10–12 December 2021; pp. 37–41. [Google Scholar] [CrossRef]
- Hasan, M.; Mohan, S.; Shimizu, T.; Lu, H. Securing Vehicle-to-Everything (V2X) Communication Platforms. IEEE Trans. Intell. Veh. 2020, 5, 693–713. [Google Scholar] [CrossRef]
- Pham, M.; Xiong, K. A survey on security attacks and defense techniques for connected and autonomous vehicles. Comput. Secur. 2021, 109, 102269. [Google Scholar] [CrossRef]
- Le, V.H.; Hartog, J.; Zannone, N. Security and privacy for innovative automotive applications: A survey. Comput. Commun. 2018, 132, 17–41. [Google Scholar] [CrossRef]
- Caviglia, R.; Gaggero, G.; Portomauro, G.; Patrone, F.; Marchese, M. An SDR-Based Cybersecurity Verification Framework for Smart Agricultural Machines. IEEE Access 2023, 11, 54210–54220. [Google Scholar] [CrossRef]
- Picod, J.M.; Lebrun, A.; Demay, J.C. Bringing software defined radio to the penetration testing community. In Proceedings of the Black Hat USA Conference, Baltimore, MD, USA, 13 August 2018. [Google Scholar]
- Pohl, J.; Noack, A. Automatic wireless protocol reverse engineering. In Proceedings of the USENIX Workshop on Offensive Technologies (WOOT), Santa Clara, CA, USA, 12–13 August 2019. [Google Scholar]
- Pohl, J.; Noack, A. Universal Radio Hacker: A Suite for Analyzing and Attacking Stateful Wireless Protocols. In Proceedings of the WOOT @ USENIX Security Symposium, Baltimore, MD, USA, 13 August 2018. [Google Scholar]
- Topman, N.; Adnane, A. Mobile applications for connected cars: Security analysis and risk assessment. In Proceedings of the IEEE Network Operations and Management Symposium (NOMS), Budapest, Hungary, 25–29 April 2022; pp. 1–6. [Google Scholar]
- Ivanov, I.; Maple, C.; Watson, T.; Lee, S. Cyber security standards and issues in V2X communications for Internet of Vehicles. In Proceedings of the Living in the Internet of Things: Cybersecurity of the IoT, London, UK, 28–29 March 2018. [Google Scholar]
- Cong, X.; Yu, Z.; Fanti, M.P.; Mangini, A.M.; Li, Z. Predictability Verification of Fault Patterns in Labeled Petri Nets. IEEE Trans. Autom. Control 2025, 70, 1973–1980. [Google Scholar] [CrossRef]
- Cong, X.; Zhu, H.; Cui, W.; Zhao, G.; Yu, Z. Critical Observability of Stochastic Discrete Event Systems Under Intermittent Loss of Observations. Mathematics 2025, 13, 1426. [Google Scholar] [CrossRef]
- Bloessl, B.; Segata, M.; Sommer, C.; Dressler, F. An IEEE 802.11 a/g/p OFDM Receiver for GNU Radio. In Proceedings of the Workshop on Software Radio Implementation Forum, Hong Kong, China, 12 August 2013; pp. 9–16. [Google Scholar]
- Pirayesh, H.; Zeng, H. Jamming Attacks and Anti-Jamming Strategies in Wireless Networks: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2022, 24, 767–809. [Google Scholar] [CrossRef]
- Nguyen-Minh, H.; Hoàng, T.; Giang, P. Machine Learning-Based Jamming Detection for Safety Applications in Vehicular Networks: Individual Detection? Secur. Commun. Netw. 2023, 2023, 1–12. [Google Scholar] [CrossRef]
- Krayani, A.; Barabino, G.; Marcenaro, L.; Regazzoni, C. Integrated Sensing and Communication for Joint GPS Spoofing and Jamming Detection in Vehicular V2X Networks. arXiv 2023, arXiv:2302.00576. [Google Scholar] [CrossRef]
- To, T.A.; Tran, T.; Le, T.; Doan, N.; Nguyen-Minh, H. Jamming Attack in Vehicular Networks: Adaptively Probabilistic Channel Surfing Scheme. Wirel. Commun. Mob. Comput. 2022, 2022, 1–8. [Google Scholar] [CrossRef]
- BK, S.; Azam, F. Ensuring Security and Privacy in VANET: A Comprehensive Survey of Authentication Approaches. J. Comput. Netw. Commun. 2024, 2024, 1818079. [Google Scholar] [CrossRef]

| Parameter | Emulation Testbed | Industrial Testbed |
|---|---|---|
| Center Frequency | 5.89 GHz | 5.89 GHz |
| Bandwidth | 10 MHz | 10 MHz |
| Sample Rate | 20 Msps | N/A (Commercial) |
| TX Gain (OBU) | 30 dB | Auto-controlled |
| RX Gain (RSU) | 40 dB | Auto-controlled |
| Antenna Type | Omnidirectional | Integrated |
| Distance (OBU-RSU) | 5–50 m | 5–50 m |
| Packet Rate (CAM) | 10 Hz | 10 Hz |
| Jammer EIRP | 20 dBm | 20 dBm |
| SNR (Normal Operation) | 15–20 dB | 20–25 dB |
| INR (During Jamming) | −10 to −5 dB | −5 to 0 dB |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sohail, M.S.; Portomauro, G.; Gaggero, G.B.; Patrone, F.; Marchese, M. Performance Analysis and Security Preservation of DSRC in V2X Networks. Electronics 2025, 14, 3786. https://doi.org/10.3390/electronics14193786
Sohail MS, Portomauro G, Gaggero GB, Patrone F, Marchese M. Performance Analysis and Security Preservation of DSRC in V2X Networks. Electronics. 2025; 14(19):3786. https://doi.org/10.3390/electronics14193786
Chicago/Turabian StyleSohail, Muhammad Saad, Giancarlo Portomauro, Giovanni Battista Gaggero, Fabio Patrone, and Mario Marchese. 2025. "Performance Analysis and Security Preservation of DSRC in V2X Networks" Electronics 14, no. 19: 3786. https://doi.org/10.3390/electronics14193786
APA StyleSohail, M. S., Portomauro, G., Gaggero, G. B., Patrone, F., & Marchese, M. (2025). Performance Analysis and Security Preservation of DSRC in V2X Networks. Electronics, 14(19), 3786. https://doi.org/10.3390/electronics14193786









