Efficient and Scalable Authentication Framework for Internet of Drones (IoD) Networks
Abstract
:1. Introduction
1.1. Problem Statement
1.2. Novelty and Contributions
- It is a Secure and Efficient Three-Way Key Exchange scheme specifically designed for IoD environments.
- It provides rigorous mathematical security proofs against a variety of attacks, ensuring provable security.
- It is optimized for resource-constrained devices, enabling lightweight implementation suitable for drones.
- It offers comprehensive security guarantees against man-in-the-middle attacks, perfect forward secrecy, session state disclosure, privacy violations, stolen verifier attacks, unknown key sharing, and excessive computational overhead.
- It prioritizes security and privacy, contributing to the reliable operation of IoD systems.
- It is a key agreement protocol where the session key is decided by the two clients, making it fairer.
2. Related Work
3. System Model and Security Assumptions
- 1.
- Drone (Service Requester—SR): In the registration phase, the SR sends and receives secret credentials from S. Subsequently, the SR requests mutual authentication with the SP and establishes a common session key for secure future communications with the SP.
- 2.
- Drone (Service Provider—SP): The SP receives secret credentials from S during registration before deployment. The SP then receives access requests from the SR for mutual authentication and establishes a common session key with the SR with the help of S. The SP is remotely controlled by S.
- 3.
- Trusted Control Server (S): S is a trusted entity, representing the ground station server. Authorized external mobile users can monitor and access drones in specific zones via S. S is responsible for various tasks, including monitoring, facilitating communication among drones, and ensuring only legitimate drones access the network. S generates credentials for each entity and registers SR and SP. S acts as a bridge for mutual authentication between SR and SP over a public channel. S’s database is considered secure and immune to compromise by SR or SP.
Adversary Model
4. A Variation of the BR1995 Model and BPR2000 Model for the SETKE Protocol
4.1. Participants
4.2. Adversary
- : Sends message m to instance and returns the response.
- : Prompts an honest execution between instances and returns the transcript. Represents passive eavesdropping.
- : Returns the session key . Exposure of some keys should not affect others.
- : Returns the long-term secret key of U. Damage should be limited to future sessions.
- : Returns the hash of m in the random oracle model.
- : Returns the real session key or a random key based on a hidden bit b. Can only be queried once to a fresh instance.
4.3. Security Definition
- 1.
- Partnership: Two instances are partners if they participate together and share a session key, and no other instance holds that key.
- 2.
- Freshness: An instance is fresh if is true, no one in was corrupted before was true, and neither nor its partner was queried with Reveal.
- 3.
- AKE security: The adversary wins if they issue a Test query to a fresh instance and correctly guess the hidden bit b. The AKE advantage is defined as . SETKE is AKE-secure if is negligible.
5. Proposed SETKE Protocol
5.1. Preliminaries
- 1.
- Elliptic Curve over a Finite Field: An elliptic curve E over a finite field is defined by , where . Points on the curve and the point at infinity (O) form an additive abelian group.
- 2.
- Base Point (Generator): A publicly known point P on E generating a cyclic subgroup of prime order n.
- 3.
- Scalar Multiplication: Computing (public key) from an integer k (private key) and point P. Easy to compute Q from k and P, but infeasible to compute k from Q and P (ECDLP).
- 4.
- Elliptic Curve Diffie–Hellman (ECDH): Allows two parties with ECC key pairs ( and ) to establish a shared secret .
- 5.
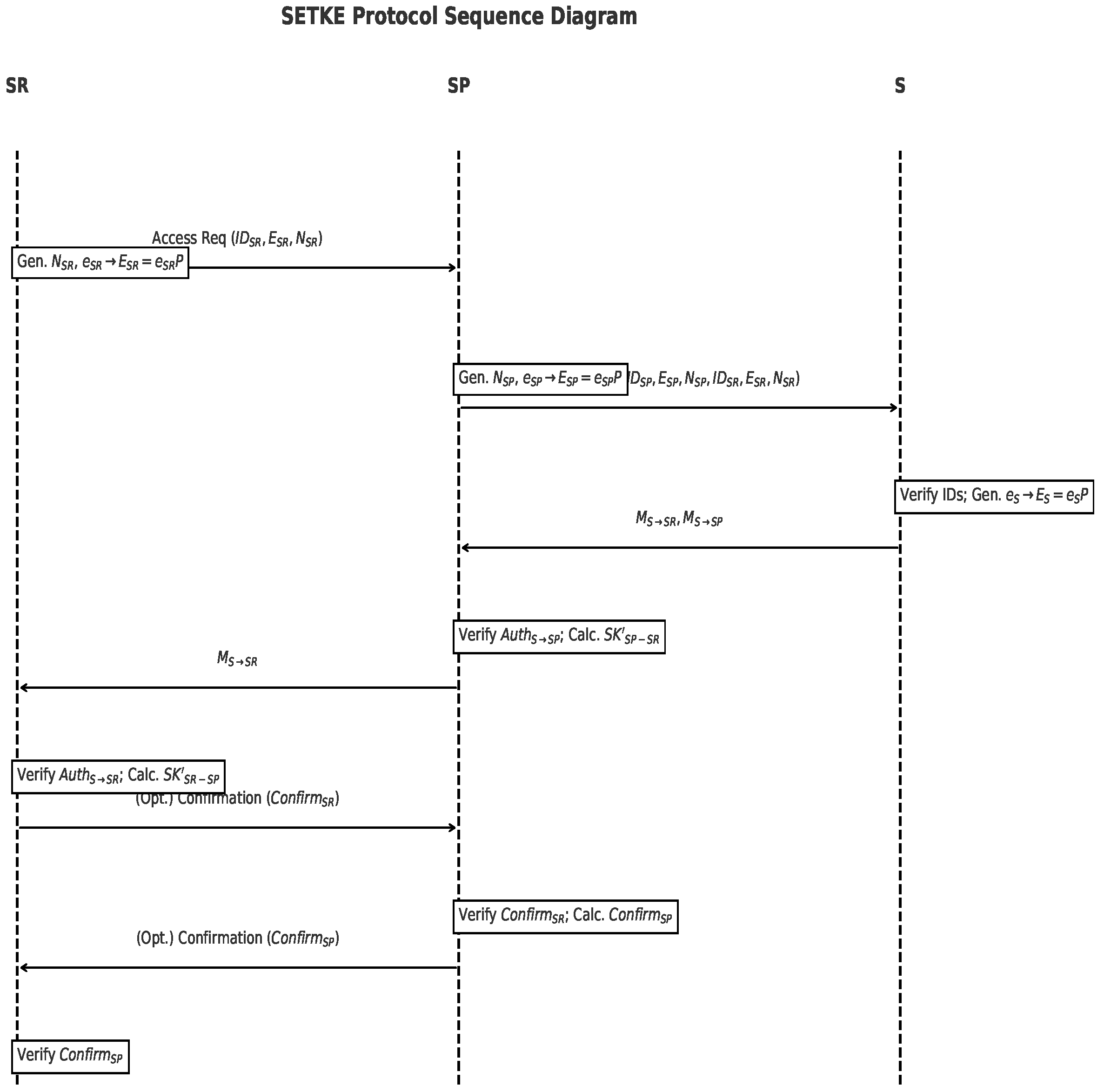
5.2. The Proposed Protocol
- Phase 1: Registration (Pre-Protocol)
- Phase 2: Key Exchange and Authentication
- 1.
- Access Request then :
- SR generates nonce and ephemeral key pair ().
- SR sends to SP: .
- SP receives the request, generates nonce and ephemeral key pair ().
- SP forwards to S: . (Optionally protected with or pre-shared key).
- 2.
- Server Authentication and Key Material Generation indirectly via SP):
- S verifies .
- S generates ephemeral key pair ().
- S computes partial shared secrets: and .
- S prepares messages: , with . , with .
- S sends and to SP. (Optionally protected).
- 3.
- Relay and Session Key Computation , and finalization):
- SP receives messages from S. Verifies using . If valid, trusts .
- SP computes and .
- SP forwards to SR.
- SR receives . Verifies using . If valid, trusts .
- SR computes .
- 4.
- Session Key Derivation and Confirmation:
- SR derives .
- SP derives . SR and SP share (which equals ).
- (Optional Confirmation) SR sends to SP. SP verifies . If correct, SP may send to SR. SR verifies .
- Elaboration on Optional Confirmation: This step is optional as its necessity depends on the IoD application’s reliability requirements. It is useful in scenarios demanding explicit confirmation of successful key establishment before sensitive data transmission, or for diagnosing key derivation issues. Performance impacts include two additional small messages, two extra hash computations per party involved in full confirmation, and an added round-trip latency. For highly resource-constrained scenarios or where the underlying transport is reliable enough, it might be omitted.
6. Security Analysis
6.1. Security Comparisons
- Robustness Against Man-in-the-Middle (MITM) Attacks: SETKE incorporates mutual authentication mediated by the trusted server S. The exchange of ephemeral public keys and signed/hashed authenticators from S makes it difficult for an adversary to impersonate any legitimate party or manipulate the key exchange process without detection. The formal verification using AVISPA further supports its resilience against MITM attacks.
- Protection Against Impersonation Attacks: SETKE mitigates this by requiring entities to prove knowledge of their long-term private keys and by using fresh ephemeral keys for each session.
- User/Drone Anonymity: While not explicitly detailed, SETKE can be extended to support anonymity using temporary or encrypted identities.
- Forward Secrecy: The use of ephemeral ECC key pairs ensures that compromise of long-term private keys does not affect the confidentiality of past session keys.
- Resistance to Stolen Verifier/Smart Card Attacks: SETKE’s security is primarily based on the intractability of ECDLP and the security of the server S, not on vulnerable stored verifiers.
- Efficiency and Scalability: By leveraging ECC, SETKE aims for lightweight implementation. The three-party model with a central server S can facilitate scalability.
- Mutual Authentication: SETKE ensures mutual authentication between SR and SP, with S as the authenticator.
- Key Agreement vs. Key Transport: SETKE is a key agreement protocol, which is generally considered more secure than key transport.
6.2. Formal Security Proof
6.3. Formal Verification (AVISPA)
7. Performance Evaluation
7.1. Computational Cost Analysis
- Service Requester (SR): 3 ECCSM, multiple hash operations.
- Service Provider (SP): 4 ECCSM, multiple hash operations.
- Control Server (S): 3 ECCSM, multiple hash operations.
7.2. Communication Overhead Analysis
7.3. Energy Consumption Analysis
7.4. Scalability Analysis
- SPOF Mitigation: Server redundancy (e.g., primary–backup clusters) and data replication can ensure high availability.
- Bottleneck Avoidance: Load balancing across multiple server instances can distribute high request volumes. Efficient server-side implementation and scalable infrastructure are also crucial.
- Geographical Distribution: For very large or geographically widespread networks, distributing server instances can reduce latency and further distribute load, though this may require data synchronization strategies.
7.5. Summary
8. Discussion
9. Conclusions
Funding
Data Availability Statement
Conflicts of Interest
References
- Mozaffari, M.; Saad, W.; Bennis, M.; Nam, Y.-H.; Debbah, M. A tutorial on UAVs for wireless networks: Applications, challenges, and open problems. IEEE Commun. Surv. Tutor. 2018, 21, 2334–2360. [Google Scholar] [CrossRef]
- Motlagh, N.H.; Taleb, T.; Arouk, O. Low-Altitude Unmanned Aerial Vehicles-Based Internet of Things Services: Comprehensive Survey and Future Perspectives. IEEE Internet Things J. 2016, 3, 899–922. [Google Scholar] [CrossRef]
- Das, A.K.; Wazid, M.; Yannam, A.R.; Rodrigues, J.J.; Park, Y. Provably secure ECC-based device access control and key agreement protocol for IoT environment. IEEE Access 2019, 7, 55382–55397. [Google Scholar] [CrossRef]
- Banerjee, S.; Das, A.K.; Chattopadhyay, S.; Jamal, S.S.; Rodrigues, J.J.; Park, Y. Lightweight failover authentication mechanism for IoT-based fog computing environment. Electronics 2021, 10, 1417. [Google Scholar] [CrossRef]
- Terminology for Constrained-Node Networks. Available online: https://datatracker.ietf.org/doc/draft-bormann-lwig-7228bis/06/ (accessed on 2 June 2025).
- Diffie, W.; Hellman, M. New directions in cryptography. IEEE Trans. Inf. Theory 1976, 22, 644–654. [Google Scholar] [CrossRef]
- Farash, M.S.; Turkanovic, M.; Kumari, S.; Höll, M. An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the Internet of Things environment. Ad Hoc Netw. 2016, 36, 152–176. [Google Scholar] [CrossRef]
- Tanveer, M.; Khan, A.U.; Kumar, N.; Hassan, M.M. RAMP-IoD: A robust authenticated key management protocol for the Internet of Drones. IEEE Internet Things J. 2022, 9, 1339–1353. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Yahya, K.; Karuppiah, M.; Kharel, R.; Bashir, A.K.; Zikria, Y.B. GCACS-IOD: A certificate based generic access control scheme for Internet of Drones. Comput. Netw. 2021, 191, 107999. [Google Scholar] [CrossRef]
- Das, A.K.; Bera, B.; Wazid, M.; Jamal, S.S.; Park, Y. IGCACS-loD: An improved certificate-enabled generic access control scheme for Internet of Drones deployment. IEEE Access 2021, 9, 87024–87048. [Google Scholar] [CrossRef]
- Lu, R.; Cao, Z. Simple three-party key exchange protocol. Comput. Secur. 2007, 26, 94–97. [Google Scholar] [CrossRef]
- Nam, J.; Lee, Y.; Kim, S.; Won, D. Security weakness in a three-party pairing-based protocol for password authenticated key exchange. Inf. Sci. 2007, 177, 1364–1375. [Google Scholar] [CrossRef]
- Shim, K.; Woo, S.S. Cryptanalysis of tripartite and multi-party authenticated key agreement protocols. Inf. Sci. 2007, 177, 1143–1151. [Google Scholar] [CrossRef]
- Turkanovic, M.; Brumen, B.; Hölbl, M. A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Netw. 2014, 20, 96–112. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.K.H.; Biswas, G.P.; Khan, M.K.; Leng, L.; Kumar, N. Design of an anonymity-preserving three-factor authenticated key exchange protocol for wireless sensor networks. Comput. Netw. 2016, 101, 42–62. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Lee, J.H. Authentication protocol for the internet of drones: Taxonomy, analysis, and future directions. J. Ambient Intell. Humaniz. Comput. 2020, 11, 2617–2640. [Google Scholar] [CrossRef]
- Yaacoub, J.P.; Noura, H.; Salman, O.; Chehab, A. Security analysis of drones systems: Attacks, limitations, and recommendations. Internet Things 2020, 11, 100218. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Kumar, N.; Rodrigues, J.J.P.C. TCALAS: Temporal credential-based anonymous lightweight authentication scheme for Internet of Drones environment. IEEE Trans. Veh. Technol. 2019, 68, 6903–6916. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Nebhen, J.; Irshad, A.; Bashir, A.K.; Kharel, R.; Yu, K.; Zikria, Y.B. A physical capture resistant authentication scheme for the Internet of Drones. IEEE Commun. Stand. Mag. 2021, 5, 62–67. [Google Scholar] [CrossRef]
- Tanveer, M.; Alkhayyat, A.; Naushad, A.; Khan, A.U.; Alharbi, A.G. RUAM-IOD: A Robust User Authentication Mechanism for the Internet of Drones. IEEE Access 2022, 10, 19836–19851. [Google Scholar] [CrossRef]
- Tanveer, M.; Zahid, A.H.; Ahmad, M.; Baz, A.; Alhakami, H. LAKE-IoD: Lightweight Authenticated Key Exchange Protocol for the Internet of Drone Environment. IEEE Access 2020, 8, 155645–155659. [Google Scholar] [CrossRef]
- Alladi, T.; Chamola, V.; Naren; Kumar, N. PARTH: A two-state lightweight mutual authentication protocol for UAV surveillance networks. Comput. Commun. 2020, 160, 81–90. [Google Scholar] [CrossRef]
- Zhang, M.; Xu, C.; Li, S.; Jiang, C. On the security of an ECC-based authentication scheme for Internet of Drones. IEEE Syst. J. 2022, 16, 6425–6428. [Google Scholar] [CrossRef]
- Nikooghadam, M.; Amintoosi, H.; Islam, S.H.; Moghadam, M.F. A provably secure and lightweight authentication scheme for Internet of Drones for smart city surveillance. J. Syst. Archit. 2021, 115, 101955. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inform. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Universally composable notions of key exchange and secure channels. In International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2002; pp. 337–351. [Google Scholar]
- Wen, H.A.; Lin, C.L.; Hwang, T. Provably secure authenticated key exchange protocols for low power computing clients. Comput. Secur. 2006, 25, 106–113. [Google Scholar] [CrossRef]
- Bellare, M.; Rogaway, P. Provably secure session key distribution: The three party case. In Proceedings of the 27th ACM Symposium on the Theory of Computing, Las Vegas, NV, USA, 29 May–1 June 1995; pp. 57–66. [Google Scholar]
- Bellare, M.; Pointcheval, P.; Rogaway, P. Authenticated key exchange secure against dictionary attacks. In Proceedings of the Eurocrypt ’00, LNCS, Bruges, Belgium, 14–18 May 2000; Volume 1807, pp. 139–155. [Google Scholar]
- Bellare, M.; Rogaway, P. Random oracles are practical: A paradigm for designing efficient protocols. In Proceedings of the First ACM Annual Conference on Computer and Communications Security, Fairfax, VA, USA, 3–5 November 1993; pp. 62–73. [Google Scholar]
- Bellare, M.; Rogaway, P. Entity authentication and key distribution. In Proceedings of the Crypto93, LNCS, Santa Barbara, CA, USA, 22–26 August 1993; Volume 773, pp. 232–249. [Google Scholar]
- Kantharaju, V.; Basavaraj, N.C.; Byatarayanapura, V.S.; Kumar, N.H. Elliptic Curve Cryptography and Password Based Key Derivation Function with Advanced Encryption Standard Method for Cloud Data Security. Int. J. Intell. Eng. Syst. 2024, 17, 814–823. [Google Scholar]
- Hankerson, D.; Menezes, A.; Vanstone, S. Guide to Ellipic Curve Cryptography; Springer: New York, NY, USA, 2004. [Google Scholar]
- Kim, J.S.; Biryukov, A.; Preneel, B.; Hong, S.H. On the Security of HMAC and NMAC Based on HAVAL, MD4, MD5, SHA-0 and SHA-1. In Proceedings of the SCN06, Maiori, Italy, 6–8 September 2006; Volume 4116, pp. 241–253. [Google Scholar]
- Marie Wright, A. The Advanced Encryption Standard. Netw. Secur. 2001, 20, 11–13. [Google Scholar] [CrossRef]
- Vigano, L. Automated security protocol analysis with the avispa tool. Electron. Notes Theor. Comput. Sci. 2006, 155, 61–86. [Google Scholar] [CrossRef]
- Banerjee, S.; Odelu, V.; Das, A.; Srinivas, J.; Kumar, N.; Chattopadhyay, S.; Choo, K. A provably secure and lightweight anonymous user authenticated session key exchange scheme for internet of things deployment. IEEE Internet Things J. 2019, 6, 8739–8752. [Google Scholar] [CrossRef]
- Kumar, D.; Jain, S.; Khan, A.; Pathak, P. An improved lightweight anonymous user authenticated session key exchange scheme for Internet of Things. J. Ambient Intell. Humaniz. Comput. 2020, 14, 5067–5083. [Google Scholar] [CrossRef]
- Aghili, S.; Mala, H.; Shojafar, M.; Peris-Lopez, P. LACO: Lightweight three-factor authentication, access control and ownership transfer scheme for e-health systems in IoT. Futur. Gener. Comp. Syst. 2019, 96, 410–424. [Google Scholar] [CrossRef]
- Ever, Y.K. A secure authentication scheme framework for mobile-sinks used in the internet of drones applications. Comput. Commun. 2020, 155, 143–149. [Google Scholar] [CrossRef]


| Notation | Description |
|---|---|
| P | Base point on the elliptic curve |
| Cryptographic hash function | |
| Ephemeral private key for entity X (where X can be SR, SP, or S) | |
| Ephemeral public key for entity X | |
| Long-term private key for entity X | |
| Long-term public key for entity X | |
| Message from Server (S) to entity U (where U is SR or SP) | |
| Structure of message , including server’s ephemeral key, peer’s ID, and an authenticator |
| Attacks | Srinivas et al. | Banerjee et al. | Kurmar et al. | Aghili et al. | Ever | Our |
|---|---|---|---|---|---|---|
| [18] | [37] | [38] | [39] | [40] | ||
| MITM | S | S | S | S | S | S |
| Impersonation | S | U | S | U | S | S |
| Anonymity | S | U | S | S | S | S |
| Perfect forward | S | U | U | U | - | S |
| secrecy | ||||||
| Session state | U | U | S | U | - | S |
| reveal | ||||||
| Privacy | S | S | S | S | U | S |
| Stolen-verifier | U | U | S | U | - | S |
| Unknown-key | U | U | S | U | - | S |
| sharing |
| Protocol | Comp. Cost | Comm. Overhead | Energy | Scalability |
|---|---|---|---|---|
| SETKE | Low | Low | Low | High |
| Srinivas et al. [18] | High | Moderate | High | Moderate |
| Banerjee et al. [37] | High | Moderate | High | Moderate |
| Kumar et al. [38] | Moderate | High | Moderate | Low |
| Aghili et al. [39] | Moderate | High | Moderate | Low |
| Ever [40] | Moderate | High | High | Moderate |
| Feature | SETKE (This Work) | Srinivas et al. [18] | Ever [40] | Banerjee et al. [37] | Kumar et al. [38] |
|---|---|---|---|---|---|
| Protocol Type | Three-Party AKE | Two-Party AKE | Three-Party AKE | Three-Factor AKE | Three-Factor AKE |
| Primary Crypto. Primitives | ECC, Hash | RSA, Hash, Symmetric | ECC, Hash | RSA, Hash, Symmetric | ECC, Hash, Symmetric |
| Key Agreement Method | ECDH-based (mediated) | DH-like/Symmetric | ECDH-based | DH-like/Symmetric | ECDH-based |
| Authentication Basis | Long-term Keys, Server-mediated | Temporal Credentials | Long-term Keys | Long-term Keys, Bio. | Smart Card, Bio. |
| No. of Parties Involved | 3 (SR, SP, S) | 2 (User, Drone) | 3 (User, Sink, S) | 3 (User, GWN, SN) | 3 (User, GWN, SN) |
| Key Confirmation | Optional Explicit | Implicit/Specific | Explicit | Explicit | Explicit |
| Forward Secrecy | Yes | Yes | Yes | No | Yes |
| Anonymity Support | Extensible | Yes (Temporal ID) | No explicit | Partial | Yes |
| Trust Model | Trusted Third Party (S) | Trusted Authority | Trusted Server | Trusted GWN | Trusted GWN |
| Suitability for Resource-Constrained | High (Low ECC ops) | Moderate-High (RSA) | Moderate (More ECC ops) | High (RSA) | Moderate |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, H. Efficient and Scalable Authentication Framework for Internet of Drones (IoD) Networks. Electronics 2025, 14, 2435. https://doi.org/10.3390/electronics14122435
Kim H. Efficient and Scalable Authentication Framework for Internet of Drones (IoD) Networks. Electronics. 2025; 14(12):2435. https://doi.org/10.3390/electronics14122435
Chicago/Turabian StyleKim, Hyunseok. 2025. "Efficient and Scalable Authentication Framework for Internet of Drones (IoD) Networks" Electronics 14, no. 12: 2435. https://doi.org/10.3390/electronics14122435
APA StyleKim, H. (2025). Efficient and Scalable Authentication Framework for Internet of Drones (IoD) Networks. Electronics, 14(12), 2435. https://doi.org/10.3390/electronics14122435







