Lossless Thumbnail Preservation Encryption Based on Reversible Information Hiding
Abstract
1. Introduction
- (1)
- This TPE scheme is based on the DCT transform, which preserves its DC coefficients and encrypts its AC coefficients. The retained DC coefficients are the average values of pixels within an image block, which can satisfy the core points of thumbnail images: pixels within a block and invariant. Compared with the traditional TPE scheme that performs an encryption operation in the null domain and transforms the image to the frequency domain, it is more secure.
- (2)
- A compensated information embedding scheme based on reversible information hiding is proposed. By calculating the gap between the pre-decrypted image and the original image, the final encrypted image is obtained by compressing it and embedding it into the intermediate image with reversible information hiding. After downloading the encrypted image from the cloud, the compensation information is extracted and used for restoration, then lossless decryption can be achieved.
- (3)
- The compensation information embedding scheme has better generality than other lossless decryption schemes. Theoretically, other high-fidelity TPE schemes can optimize the algorithm through the idea of compensation information embedding to achieve the effect of lossless decryption.
- (1)
- Section 1: The background and research significance of the topic of TPE and our contribution are given.
- (2)
- Section 2: The encryption process, core algorithms, and techniques of the proposed scheme are introduced.
- (3)
- Section 3: The design objectives of the scheme are introduced, as well as the experiments and analysis based on it.
- (4)
- Section 4: Summary and Outlook. This chapter summarizes the main research work of the thesis and the superiority of the scheme.
2. Proposed TPE Scheme
2.1. Encryption Key Generation
2.2. DCT Transform Encryption
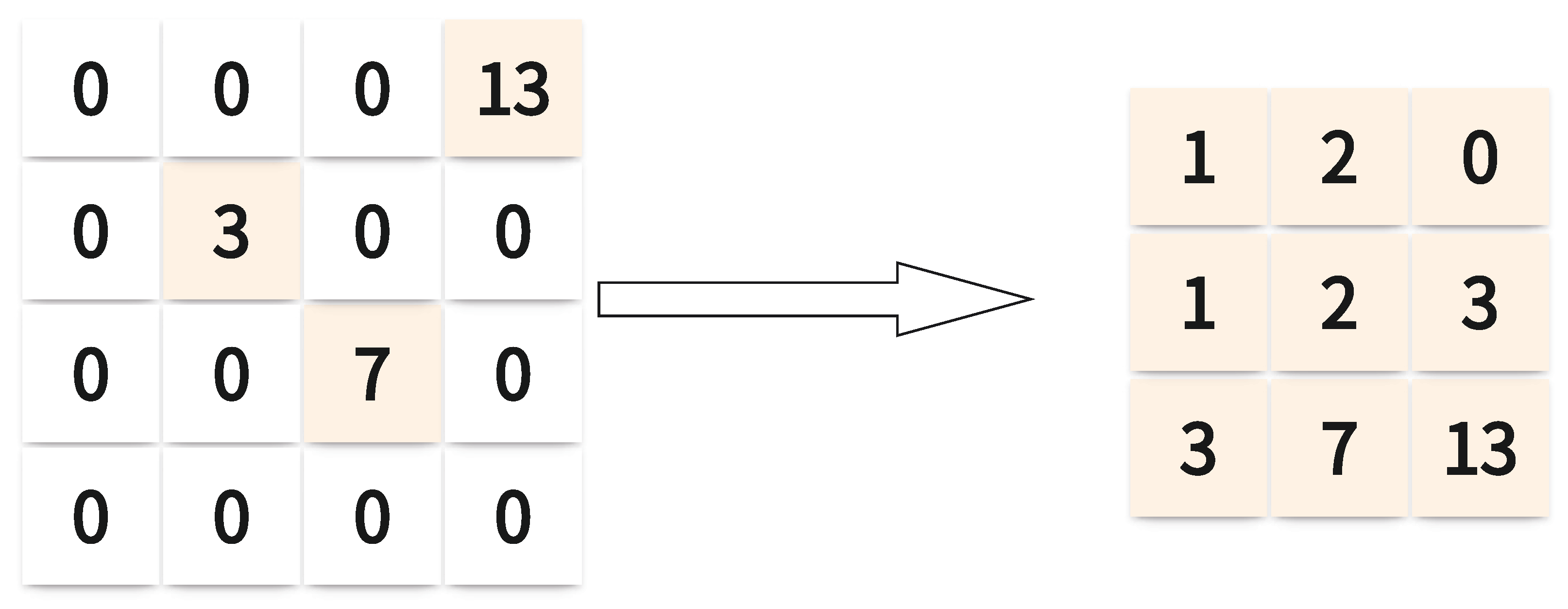
2.2.1. Direct Current Coefficient
2.2.2. Alternating Current Coefficient
2.3. Computation and Compression of Compensation Information
2.4. Reversible Embedding of Compensation Information
2.4.1. Embedding Process
2.4.2. Extraction Process
2.5. Thumbnail Generation
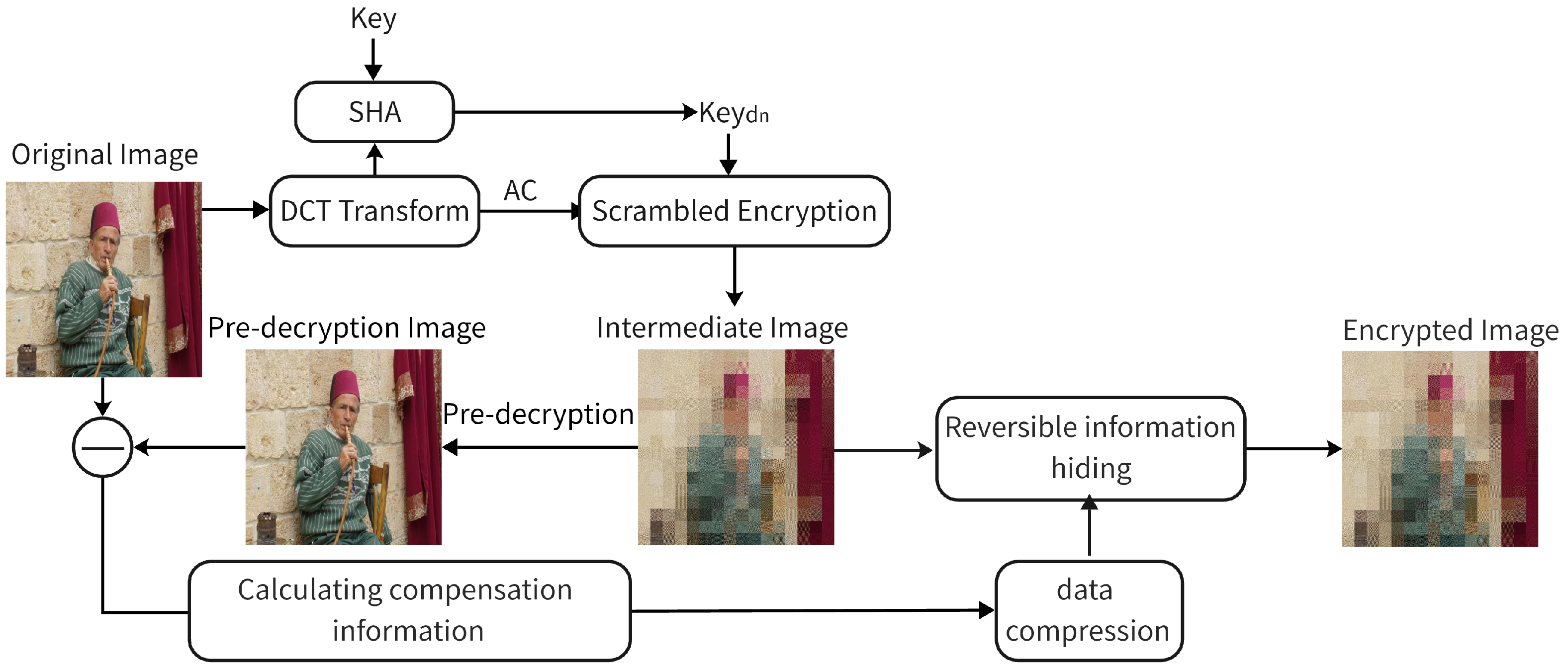
2.6. Encryption Process
- The original image is transformed by DCT, the AC coefficients are encrypted by substitution according to the key generated by Equation (1), and the intermediate encrypted image is obtained.
- Pre-decryption: according to the key, the AC coefficients are reduced to obtain the pre-decrypted image.
- According to Equation (6), the compensation information is obtained by making a difference between the original image and the pre-decrypted image.
- Compensation information is compressed by using block compression.
- According to Algorithm 1, the compensation information is embedded into the intermediate encrypted image to get its final encrypted image.
| Algorithm 1 Embedding Process |
| Input: Greyscale image h, binary tree level L, watermark bitstream b Output: Watermarked image
|
2.7. Lossless Image Decryption
- The received encrypted image is labeled as f, and the compensation information is extracted from the received image f according to Algorithm 2. From this, the intermediate encrypted image can be isolated.
- The DCT transform is performed on , the key-generated disambiguation sequence is used to restore the alignment of the AC coefficients, and an inverse DCT transform is performed to obtain the pre-decrypted image .
- By adding the compensation information D to the pre-decrypted image , a lossless restore to the original image is obtained.
| Algorithm 2 Extraction Process |
| Input: Watermarked image , binary tree level L Output: Original image h, watermark bitstream b
|
3. Experimental Results and Analysis
3.1. Design Objective
- Visualization: Ciphertext images need to retain a certain amount of visual information. Therefore, the thumbnail generated from a cipher image should be similar or identical to the thumbnail of the original image, which is important to maintain usability.
- Lossless Decryption: Lossless decryption ensures that the original image information is not lost throughout the encryption and decryption process, thus preserving the integrity of the original data. Even if the loss is minimal with each encryption, the overall image quality can be significantly degraded after multiple encryption and decryption processes. Data integrity ensures that in IoT devices containing critical information and control commands, data can be evaluated correctly and commands can be executed efficiently. Lossless decryption ensures that the image is accurate and thus the instructions given are reliable, avoiding the unforeseen consequences of even the smallest error.
- Privacy security: In the TPE field, the focus is on the balance between privacy and usability of the image, not confidentiality. Images should not reveal any details beyond the thumbnail.
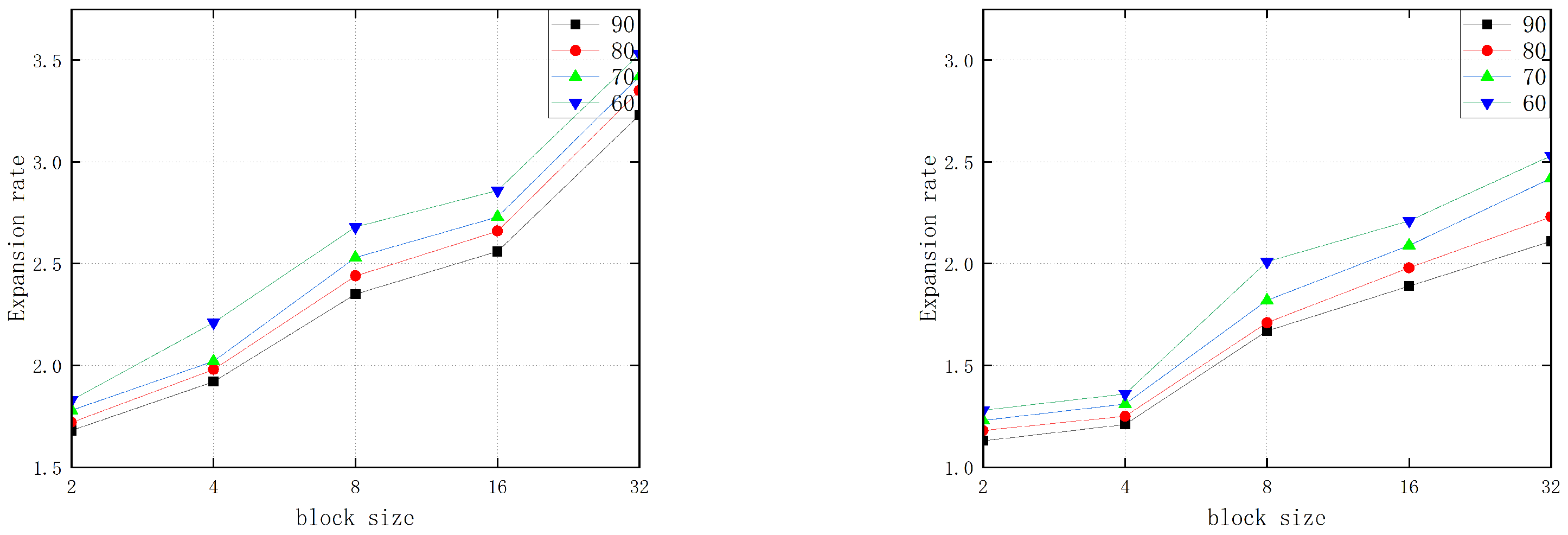
- Low File Extension: Ciphertext images cannot generate too large a file extension. In application areas where excessive information may be generated by uploading a large number of images at the same time, a small file extension size can result in a huge difference in storage space.
- Compatibility: The proposed TPE solution has good compatibility, which means that it can seamlessly work in harmony with all kinds of cloud storage services that are widely used in the market today. Users can easily utilize this solution without having to make any kind of modifications or adjustments to their existing cloud systems.
3.2. Visual Quality
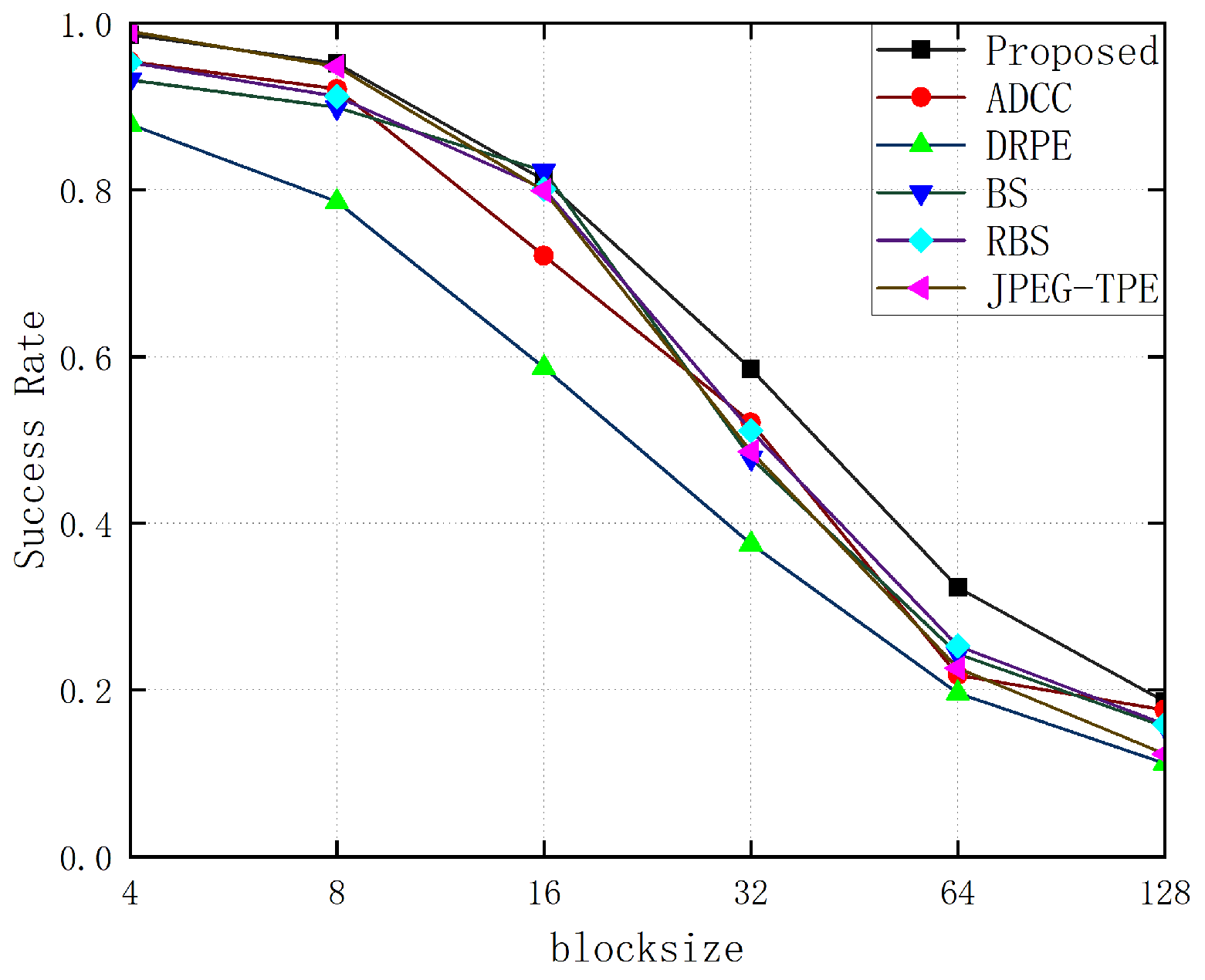
- Encrypted image quality:In this paper, we generate TPE encryption maps with different accuracies based on different encryption fast sizes. As shown in Figure 5, for different encryption block sizes from 4 to 128, as the encryption block size increases, the visibility decreases, the privacy becomes higher, and the usable information that can be obtained from the image becomes less and less. Specifically, when the encryption block is 4, the encrypted image is extremely similar to the original image, while when the encryption block reaches 64 and 128, the encrypted image usability has been reduced to such a low level that no usable information can be obtained from image analysis.
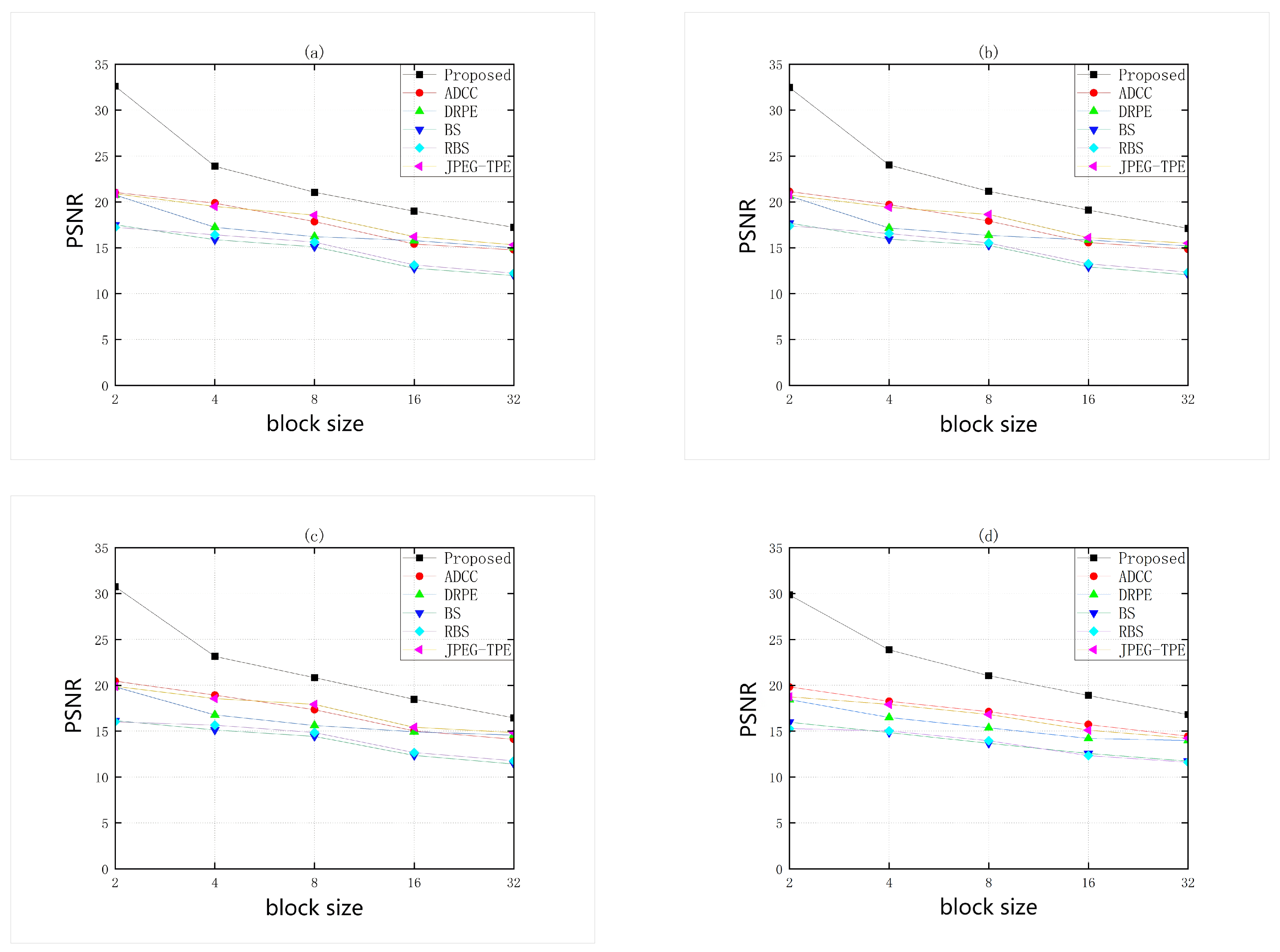
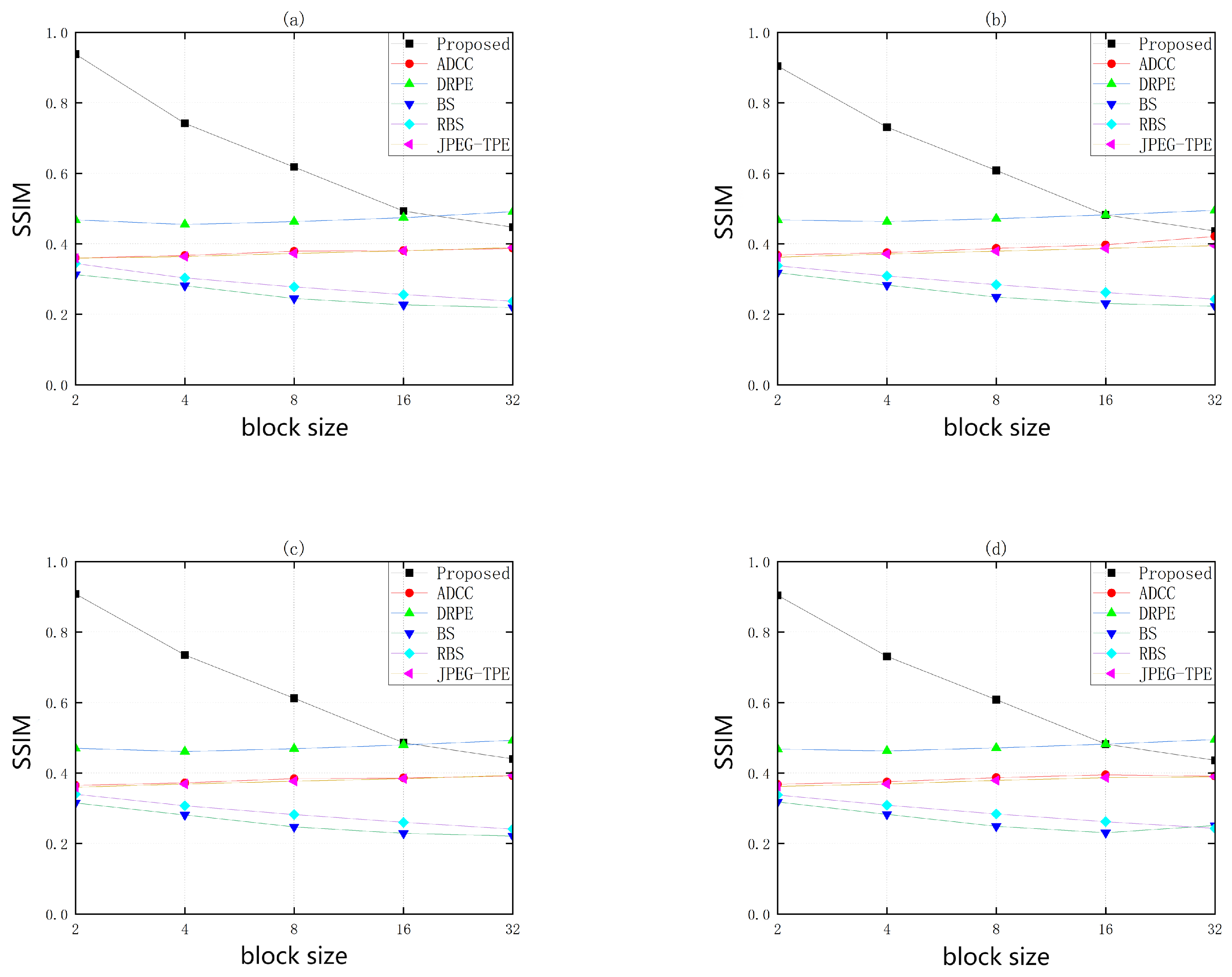
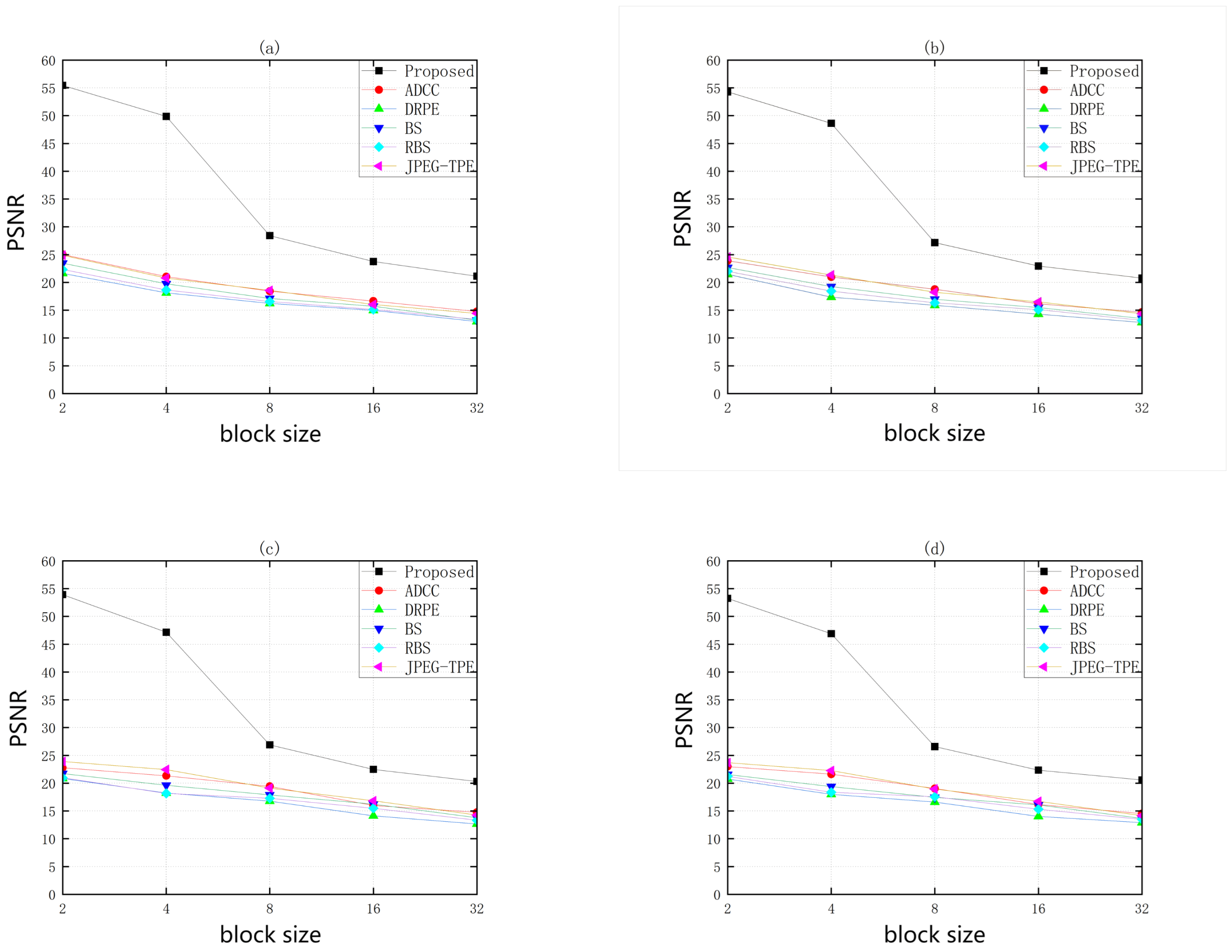
- Quantitative analysis of encrypted images:In order to better illustrate the encryption effect of this algorithm, the Peak Signal to Noise Ratio (PSNR) and Structural Similarity (SSIM) will be used to qualitatively assess the effectiveness of the abbreviated encryption.Figure 6 and Figure 7 show the encryption results tested on the Inria Holidays dataset. The experimental results show that the PSNR of this scheme is higher than all other schemes, and SSIM also performs better when the encryption blocks are from 2 to 16, and it is only countered by the DRPE scheme when the encryption blocks are greater than or equal to 32. Note that this TPE scheme is not a guarantee that illegal third parties cannot obtain any information from the ciphertext image. In fact, the scheme can expose less unimportant information to gain some usability, so that illegal third parties cannot learn more information from the encrypted thumbnail image. The specific encryption effect can be chosen according to different encryption block sizes.
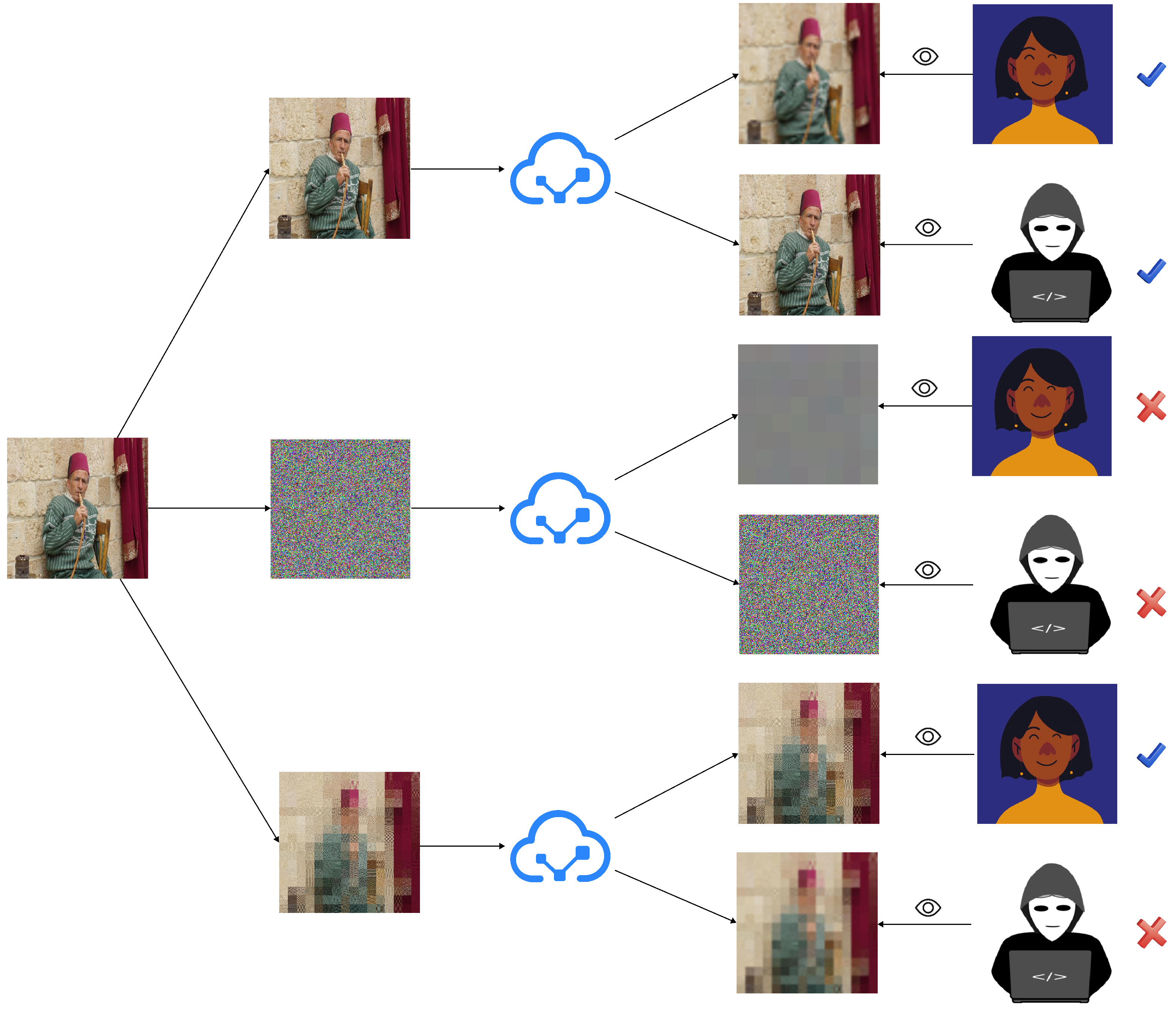
- Encrypted thumbnail image quality:It is more reasonable to compare the quality of thumbnails generated from encrypted images with the quality of the original image because the thumbnails provide the user with a quick preview to recognize the original image content. We have taken the thumbnails generated from encrypted images based on different encryption block sizes and reduced them to 512 × 512, as shown in Figure 8. The experimental results show that as the encryption block size increases, the thumbnail contains less and less meaningful content and the original image becomes more and more difficult to recognize. And, when the proper encryption block is chosen, the difference between the thumbnail of the encrypted image and the thumbnail of the original image is not very big, and the legitimate users are able to utilize the visibility to distinguish the images they need.
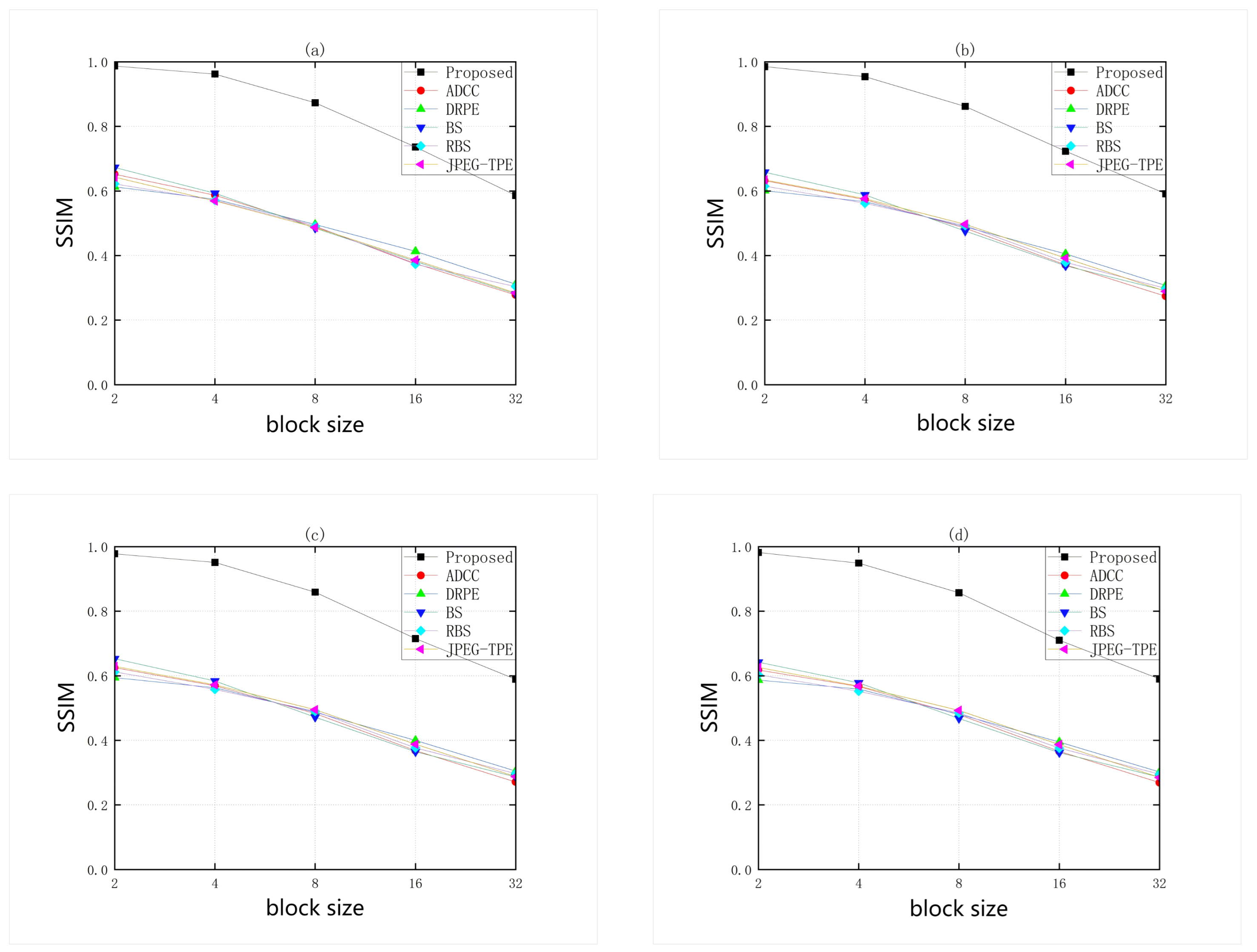
- Quantitative analysis of encrypted thumbnails:The thumbnail generated from the encrypted image is compared with the thumbnail generated from the original image, which is more in line with the practical application scenarios, as shown in Figure 9 and Figure 10. The PSNR and SSIM values of this scheme are higher than other schemes, indicating that it is more in line with practical application requirements. Legitimate users are able to browse quickly in the cloud to recognize the desired image. The higher PSNR and SSIM values indicate that the thumbnail images have high preservation capability.
3.3. Decryption Effects
3.4. Security Analysis
- Information entropy:Information entropy can be used to measure the uncertainty of the image information; the closer the information entropy of the image is to 8, the greater the uncertainty and the more effective the algorithm is. Table 4 shows the information entropy of the original and encrypted images, where the information entropy of all channels increases and is closer to 8.
- Correlation coefficient analysis:5000 pairs of neighboring pixels are randomly selected from the horizontal, vertical, and diagonal directions of the image, and the correlation coefficients between these pixels are calculated. The correlation coefficients obtained are shown in Table 5 and Figure 11, where red, green, and blue represent the horizontal, vertical, and diagonal random selection, respectively; the x-axis and y-axis denote the gray values; and the dots represent the relationship of gray values between a pair of neighboring pixels. The results show that this scheme can greatly reduce the correlation between pixels.
3.5. User Evaluation
3.6. Document Extension
3.7. Format Compatibility
4. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Milian, M. Digital Photos can reveal your location raise privacy fears. CNN.Com, 15 October 2010. [Google Scholar]
- Fan, L. A demonstration of image obfuscation with provable privacy. In Proceedings of the 2019 IEEE International Conference on Multimedia & Expo Workshops (ICMEW), Shanghai, China, 8–12 July 2019; IEEE: New York, NY, USA, 2019; p. 608. [Google Scholar]
- Greenberg, A. The police tool that pervs use to steal nude pics from Apple’s iCloud. Wired, 2 September 2014. [Google Scholar]
- Fallon, R. Celebgate: Two methodological approaches to the 2014 celebrity photo hacks. In Proceedings of the International Conference on Internet Science; Springer: Cham, Switzerland, 2015; pp. 49–60. [Google Scholar]
- Sengupta, S.; O’Brien, K.J. Facebook can ID faces, but using them grows tricky. New York Times, 21 September 2012. [Google Scholar]
- Schiffer, Z. The Big Facebook oUtage Offers a Behind-the-Scenes Look at How the Social Network’s AI “Sees” Your Photos and Interprets Them for Blind Users. 2019. Available online: https://www.businessinsider.com/facebooks-photo-outage-reveals-how-ai-sees-your-photos-2019-7 (accessed on 30 June 2024).
- Dance, G.J.; LaForgia, M.; Confessore, N. As Facebook raised a privacy wall, it carved an opening for tech giants. N. Y. Times 2018, 18, 1–9. [Google Scholar]
- Li, A.; Darling, D.; Li, Q. PhotoSafer: Content-based and context-aware private photo protection for smartphones. In Proceedings of the 2018 IEEE Symposium on Privacy-Aware Computing (PAC), Washington, DC, USA, 26–28 September 2018; IEEE: New York, NY, USA, 2018; pp. 10–18. [Google Scholar]
- Kang, X.; Tao, R. Color image encryption using pixel scrambling operator and reality-preserving MPFRHT. IEEE Trans. Circuits Syst. Video Technol. 2018, 29, 1919–1932. [Google Scholar] [CrossRef]
- Qin, C.; Zhou, Q.; Cao, F.; Dong, J.; Zhang, X. Flexible lossy compression for selective encrypted image with image inpainting. IEEE Trans. Circuits Syst. Video Technol. 2018, 29, 3341–3355. [Google Scholar] [CrossRef]
- Puteaux, P.; Puech, W. CFB-then-ECB mode-based image encryption for an efficient correction of noisy encrypted images. IEEE Trans. Circuits Syst. Video Technol. 2020, 31, 3338–3351. [Google Scholar] [CrossRef]
- Gregory, R.L. Knowledge in perception and illusion. Philos. Trans. R. Soc. Lond. Ser. B Biol. Sci. 1997, 352, 1121–1127. [Google Scholar] [CrossRef]
- Kinjo, H.; Snodgrass, J.G. Does the generation effect occur for pictures? Am. J. Psychol. 2000, 113, 95. [Google Scholar] [CrossRef]
- Denning, T.; Bowers, K.; Van Dijk, M.; Juels, A. Exploring implicit memory for painless password recovery. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems, Vancouver, BC, Canada, 7–12 May 2011; pp. 2615–2618. [Google Scholar]
- Kok, P.; Brouwer, G.J.; van Gerven, M.A.; de Lange, F.P. Prior expectations bias sensory representations in visual cortex. J. Neurosci. 2013, 33, 16275–16284. [Google Scholar] [CrossRef]
- Rousselet, G.A.; Thorpe, S.J.; Fabre-Thorpe, M. Processing of one, two or four natural scenes in humans: The limits of parallelism. Vis. Res. 2004, 44, 877–894. [Google Scholar] [CrossRef]
- Wright, C.V.; Feng, W.c.; Liu, F. Thumbnail-preserving encryption for JPEG. In Proceedings of the 3rd ACM Workshop on Information Hiding and Multimedia Security, Portland, OR, USA, 17–19 June 2015; pp. 141–146. [Google Scholar]
- Chen, J.; Chen, L.; Zhou, Y. Universal chosen-ciphertext attack for a family of image encryption schemes. IEEE Trans. Multimed. 2020, 23, 2372–2385. [Google Scholar] [CrossRef]
- Zhang, L.Y.; Liu, Y.; Wang, C.; Zhou, J.; Zhang, Y.; Chen, G. Improved known-plaintext attack to permutation-only multimedia ciphers. Inf. Sci. 2018, 430, 228–239. [Google Scholar] [CrossRef]
- Chen, J.; Chen, L.; Zhou, Y. Cryptanalysis of image ciphers with permutation-substitution network and chaos. IEEE Trans. Circuits Syst. Video Technol. 2020, 31, 2494–2508. [Google Scholar] [CrossRef]
- Jolfaei, A.; Wu, X.W.; Muthukkumarasamy, V. On the security of permutation-only image encryption schemes. IEEE Trans. Inf. Forensics Secur. 2015, 11, 235–246. [Google Scholar] [CrossRef]
- Marohn, B.; Wright, C.V.; Feng, W.c.; Rosulek, M.; Bobba, R.B. Approximate thumbnail preserving encryption. In Proceedings of the 2017 on Multimedia Privacy and Security, Dallas, TX, USA, 30 October 2017; pp. 33–43. [Google Scholar]
- Tajik, K.; Gunasekaran, A.; Dutta, R.; Ellis, B.; Bobba, R.B.; Rosulek, M.; Wright, C.V.; Feng, W.c. Balancing image privacy and usability with thumbnail-preserving encryption. IACR Cryptol. EPrint Arch. 2019, 2019, 295. [Google Scholar]
- Zhao, R.; Zhang, Y.; Xiao, X.; Ye, X.; Lan, R. TPE2: Three-pixel exact thumbnail-preserving image encryption. Signal Process. 2021, 183, 108019. [Google Scholar] [CrossRef]
- Zhang, Y.; Zhao, R.; Xiao, X.; Lan, R.; Liu, Z.; Zhang, X. HF-TPE: High-fidelity thumbnail-preserving encryption. IEEE Trans. Circuits Syst. Video Technol. 2021, 32, 947–961. [Google Scholar] [CrossRef]
- Chai, X.; Wang, Y.; Gan, Z.; Chen, X.; Zhang, Y. Preserving privacy while revealing thumbnail for content-based encrypted image retrieval in the cloud. Inf. Sci. 2022, 604, 115–141. [Google Scholar] [CrossRef]
- Zhang, Y.; Zhao, R.; Zhang, Y.; Lan, R.; Chai, X. High-efficiency and visual-usability image encryption based on thumbnail preserving and chaotic system. J. King Saud Univ.-Comput. Inf. Sci. 2022, 34, 2993–3010. [Google Scholar] [CrossRef]
- Zhao, R.; Zhang, Y.; Nan, Y.; Wen, W.; Chai, X.; Lan, R. Primitively visually meaningful image encryption: A new paradigm. Inf. Sci. 2022, 613, 628–648. [Google Scholar] [CrossRef]
- Zhang, Y.; Ye, X.; Xiao, X.; Xiang, T.; Li, H.; Cao, X. A reversible framework for efficient and secure visual privacy protection. IEEE Trans. Inf. Forensics Secur. 2023, 18, 3334–3349. [Google Scholar] [CrossRef]
- Yang, C.H.; Weng, C.Y.; Yang, Y.Z. TPEIP: Thumbnail preserving encryption based on sum preserving for image privacy. J. Inf. Secur. Appl. 2022, 70, 103352. [Google Scholar] [CrossRef]
- Ye, Z.; Zhao, R.; Zhang, Y.; Xiao, X.; Lan, R.; Xiang, Y. Noise-free thumbnail-preserving image encryption based on MSB prediction. Inf. Sci. 2022, 617, 395–415. [Google Scholar] [CrossRef]
- Ye, X.; Zhang, Y.; Zhao, R.; Lan, R.; Xiang, Y. PRA-TPE: Perfectly recoverable approximate thumbnail-preserving image encryption. J. Vis. Commun. Image Represent. 2022, 87, 103589. [Google Scholar] [CrossRef]
- An, D.; Hao, D.; Zhao, R.; Zhang, S.; Lu, J.; Zhang, Y. Visually semantic-preserving and people-oriented color image encryption based on cross-plane thumbnail preservation. Expert Syst. Appl. 2023, 233, 120931. [Google Scholar] [CrossRef]
- Ma, Y.; Chai, X.; Gan, Z.; Zhang, Y. Privacy-preserving TPE-based JPEG image retrieval in cloud-assisted internet of things. IEEE Internet Things J. 2023, 11, 4842–4856. [Google Scholar] [CrossRef]
- Wang, X.; Qu, L.; Wu, H.T.; Han, Y.; Tian, Z. Reversible image thumbnail preservation with high visual naturalness. IEEE Internet Things J. 2024, 11, 18739–18752. [Google Scholar] [CrossRef]
- Yuan, Y.; He, H.; Amirpour, H.; Qu, L.; Timmerer, C.; Chen, F. IoT privacy protection: JPEG-TPE with lower file size expansion and lossless decryption. IEEE Internet Things J. 2024, 11, 23485–23496. [Google Scholar] [CrossRef]
- Ahmed, N.; Natarajan, T.; Rao, K.R. Discrete cosine transform. IEEE Trans. Comput. 2006, 100, 90–93. [Google Scholar] [CrossRef]
- Ouyang, J.; Huang, J.; Wen, X. A semi-fragile reversible watermarking method based on qdft and tamper ranking. Multimed. Tools Appl. 2024, 83, 41555–41578. [Google Scholar] [CrossRef]





| Schemes | BS [17] | RBS [17] | DRPE [23] | ADCC [34] | JPEG-TPE [36] | Proposed |
|---|---|---|---|---|---|---|
| Frequency domain | × | × | × | ✓ | ✓ | ✓ |
| Decryption quality | × | × | × | ++ | +++ | +++ |
| Visual quality | ++ | ++ | ++ | ++ | ++ | +++ |
| File size expansion | + | + | + | ++ | +++ | ++ |
| Format compatibility | × | × | × | ++ | ++ | +++ |
| Security | + | + | × | ++ | +++ | ++ |
| Dataset | µ | PSNR | |||||
|---|---|---|---|---|---|---|---|
| Proposed | ADCC | DRPE | BS | RBS | JPEG-TPE | ||
| Inria Holiday | 2 | Inf | 68.14 | 22.68 | 39.76 | 40.32 | Inf |
| 4 | Inf | 68.14 | 22.29 | 39.24 | 40.32 | Inf | |
| 8 | Inf | 68.14 | 26.05 | 38.82 | 40.32 | Inf | |
| 16 | Inf | 68.14 | 29.97 | 38.47 | 40.32 | Inf | |
| 32 | Inf | 68.14 | 31.38 | 38.42 | 40.32 | Inf | |
| Dataset | µ | SSIM | |||||
|---|---|---|---|---|---|---|---|
| Proposed | ADCC | DRPE | BS | RBS | JPEG-TPE | ||
| Inria Holiday | 2 | 1 | 0.99 | 0.73 | 0.92 | 0.94 | 1 |
| 4 | 1 | 0.99 | 0.82 | 0.90 | 0.94 | 1 | |
| 8 | 1 | 0.99 | 0.89 | 0.87 | 0.94 | 1 | |
| 16 | 1 | 0.99 | 0.93 | 0.85 | 0.94 | 1 | |
| 32 | 1 | 0.99 | 0.92 | 0.85 | 0.94 | 1 | |
| Original | Proposed | |
|---|---|---|
| R | 7.27 | 7.37 |
| G | 7.58 | 7.69 |
| B | 7.00 | 7.38 |
| Original Image | Encrypted Image | ||||||
|---|---|---|---|---|---|---|---|
| Horizontal | Vertical | Diagonal | Horizontal | Vertical | Diagonal | ||
| R | 0.9769 | 0.9870 | 0.9637 | 0.4993 | 0.4679 | 0.4540 | |
| G | 0.9786 | 0.9902 | 0.9676 | 0.4856 | 0.4914 | 0.4721 | |
| B | 0.9531 | 0.9776 | 0.9307 | 0.4732 | 0.4728 | 0.4707 | |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ouyang, J.; Shi, T.; Wang, R. Lossless Thumbnail Preservation Encryption Based on Reversible Information Hiding. Electronics 2025, 14, 2060. https://doi.org/10.3390/electronics14102060
Ouyang J, Shi T, Wang R. Lossless Thumbnail Preservation Encryption Based on Reversible Information Hiding. Electronics. 2025; 14(10):2060. https://doi.org/10.3390/electronics14102060
Chicago/Turabian StyleOuyang, Junlin, Tingjian Shi, and Ruijie Wang. 2025. "Lossless Thumbnail Preservation Encryption Based on Reversible Information Hiding" Electronics 14, no. 10: 2060. https://doi.org/10.3390/electronics14102060
APA StyleOuyang, J., Shi, T., & Wang, R. (2025). Lossless Thumbnail Preservation Encryption Based on Reversible Information Hiding. Electronics, 14(10), 2060. https://doi.org/10.3390/electronics14102060






