Trusted Traceability Service: A Novel Approach to Securing Supply Chains
Abstract
1. Introduction
- Establishing a unified supply chain traceability mechanism for packaged products.
- Incorporating SSI for authentication between the involved supply chain entities in a blockchain-based decentralized environment.
- Analyzing the potential of the Fantom blockchain by comparing it with other smart-contract-based blockchain platforms.
2. Related Work
3. Preliminaries
3.1. Fantom Blockchain and Consensus Protocol
3.2. Self Sovereign Identity
- Verifiable credentials are digital documents that contain claims or assertions about an individual’s identity, attributes, or other relevant information.
- The trust triangle is a concept used in the context of SSI systems to establish trust between different entities involved in identity verification and authentication processes. The triangle comprises three key components: the issuer, the holder, and the verifier. Figure 1 shows an overview of the trust triangle.
- Digital wallets, also known as e-wallets or mobile wallets, are software applications or platforms that allow individuals to store, manage, and use their financial assets and payment information digitally.
- Digital agents, also known as autonomous agents or intelligent agents, are software programs or systems that are designed to perform tasks or make decisions on behalf of individuals or organizations.
- Decentralized identifiers s are unique identifiers that are globally unique and resolvable across different networks and platforms. They serve as the foundation for establishing and managing decentralized digital identities.
- Blockchains are shared databases protected by cryptography. They can provide a reliable foundation for public keys and s. They are not vulnerable to attack or having a single point of failure.
- Governance frameworks are issued by governance authorities. They provide a set of rules, principles, and mechanisms that govern an SSI ecosystem’s operation, management, and decision-making processes.
3.3. Decentralized Key Management System (DKMS)
3.4. Database Clustering
4. System Model
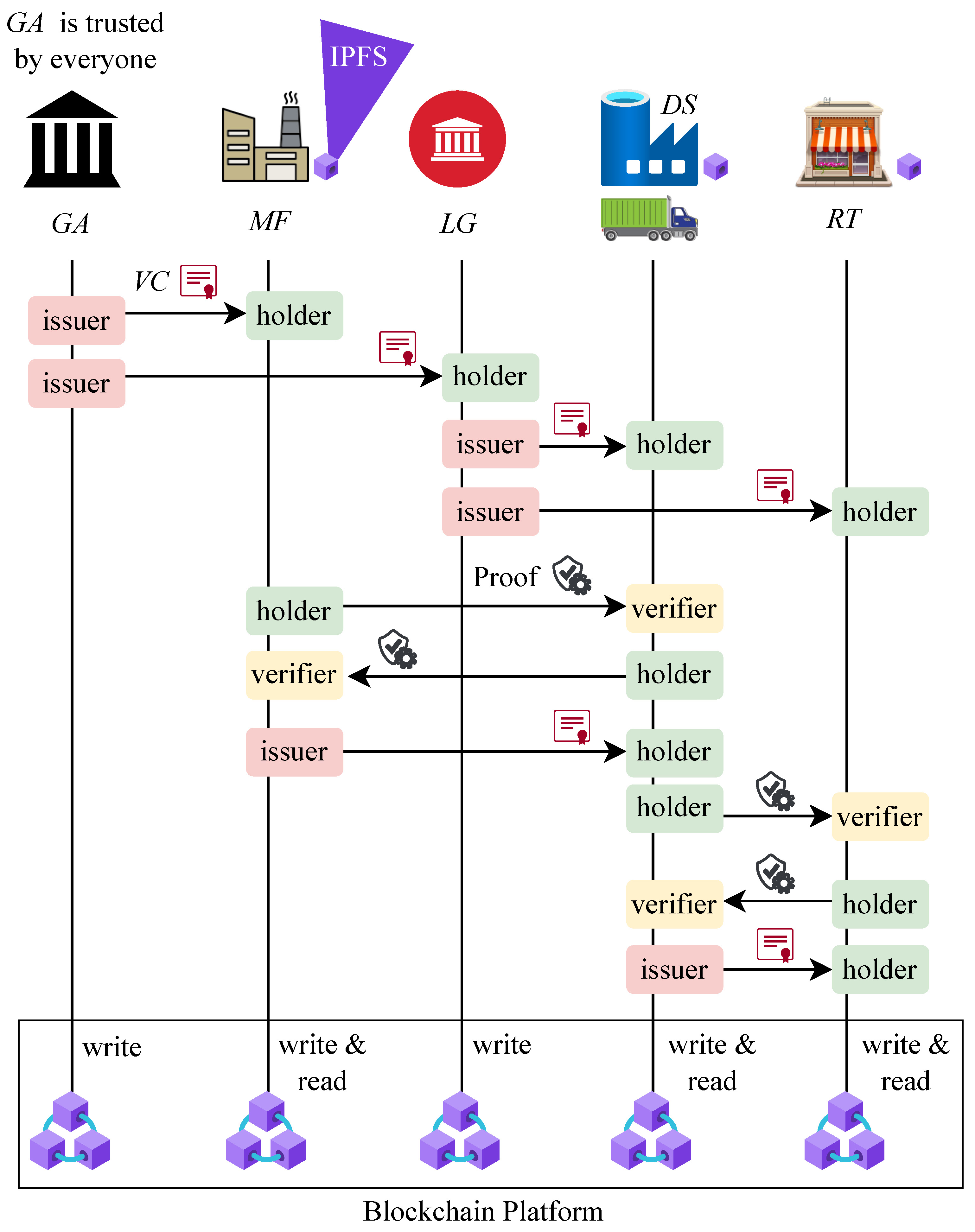
4.1. System Overview
- Governance Authority : Provide verifiable credentials () to Manufacturer and Local Government (). is the root of trust.
- Local Government : Provide a trade license as a verifiable credential to Distributor and Retailer .
- Manufacturer : Provide verifiable credentials to Distributor after verification and sell product pallets to the .
- Distributor : Provide verifiable credentials to Retailer after verification. Purchase pallets from the and sell cases to the .
- Retailer : Purchase cases from the D and sell unit products to the End User
- End User : Purchase the unit product from the Retailer after checking its authenticity.
4.2. Threat Model
4.3. Security Goals
5. Model Construction
5.1. Establishing SSI for TTS
5.2. Establishing TTS
| Algorithm 1: QR code generation by |
 |
| Algorithm 2: Pallet issuing by |
 |
| Algorithm 3: Pallet issuing verification by |
 |
| Algorithm 4: Product verification by |
 |
5.3. Security Analysis
6. Experiment and Result Evaluation
6.1. Testbed
6.2. Evaluation Metrics
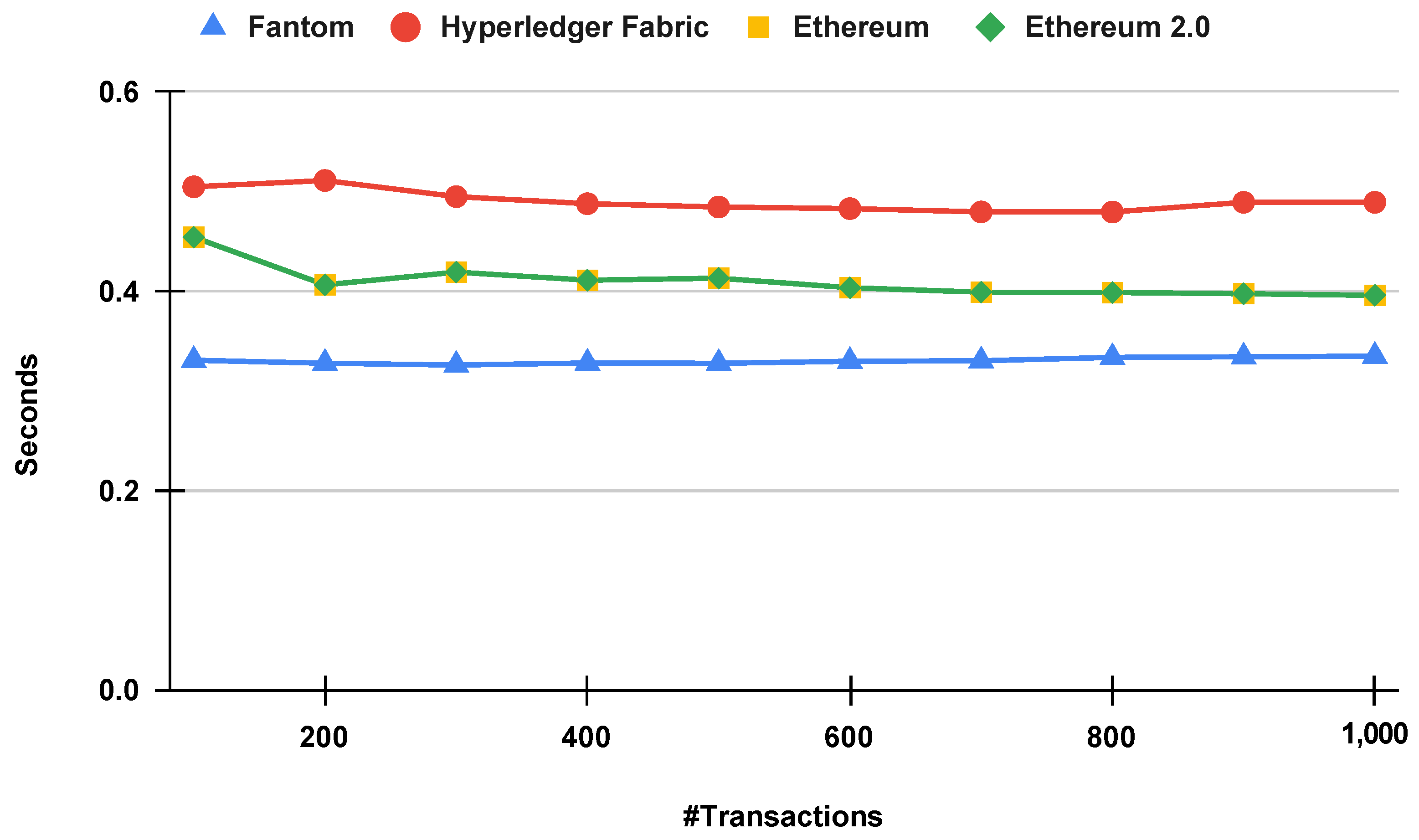
6.3. Execution Time ()
6.4. Average Latency ()
6.5. Average Throughput ()
6.6. Result Evaluation
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Serdarasan, S. A review of supply chain complexity drivers. Comput. Ind. Eng. 2013, 66, 533–540. [Google Scholar] [CrossRef]
- Putro, P.A.W.; Purwaningsih, E.K.; Sensuse, D.I.; Suryono, R.R. Model and implementation of rice supply chain management: A literature review. Procedia Comput. Sci. 2022, 197, 453–460. [Google Scholar] [CrossRef]
- Gayialis, S.P.; Kechagias, E.P.; Papadopoulos, G.A.; Masouras, D. A review and classification framework of traceability approaches for identifying product supply chain counterfeiting. Sustainability 2022, 14, 6666. [Google Scholar] [CrossRef]
- Uddin, M. Blockchain Medledger: Hyperledger fabric enabled drug traceability system for counterfeit drugs in pharmaceutical industry. Int. J. Pharm. 2021, 597, 120235. [Google Scholar] [CrossRef]
- Homeland Security. Available online: https://www.ice.gov/features/dangers-counterfeit-items (accessed on 12 June 2023).
- Semiconductor Industry Association. Detecting and Removing Counterfeit Semiconductors in the US Supply Chain; Semiconductor Industry Association: Washington, DC, USA, 2022. [Google Scholar]
- Statista. Available online: https://www.statista.com/statistics/1117921/sales-losses-due-to-fake-good-by-industry-worldwide/ (accessed on 12 June 2023).
- OECD. Available online: https://www.oecd.org/newsroom/trade-in-fake-goods-is-now-33-of-world-trade-and-rising.htm (accessed on 12 June 2023).
- Casino, F.; Kanakaris, V.; Dasaklis, T.K.; Moschuris, S.; Stachtiaris, S.; Pagoni, M.; Rachaniotis, N.P. Blockchain-based food supply chain traceability: A case study in the dairy sector. Int. J. Prod. Res. 2021, 59, 5758–5770. [Google Scholar] [CrossRef]
- Feng, H.; Wang, X.; Duan, Y.; Zhang, J.; Zhang, X. Applying blockchain technology to improve agri-food traceability: A review of development methods, benefits and challenges. J. Clean. Prod. 2020, 260, 121031. [Google Scholar] [CrossRef]
- Kumar, R.; Tripathi, R. Traceability of counterfeit medicine supply chain through Blockchain. In Proceedings of the 2019 11th IEEE International Conference on Communication Systems & Networks (COMSNETS), Bengaluru, India, 7–11 January 2019; pp. 568–570. [Google Scholar]
- Demestichas, K.; Peppes, N.; Alexakis, T.; Adamopoulou, E. Blockchain in agriculture traceability systems: A review. Appl. Sci. 2020, 10, 4113. [Google Scholar] [CrossRef]
- Chen, J.; Huang, Y.; Xia, P.; Zhang, Y.; Zhong, Y. Design and implementation of real-time traceability monitoring system for agricultural products supply chain under Internet of Things architecture. Concurr. Comput. Pract. Exp. 2019, 31, e4766. [Google Scholar] [CrossRef]
- Fantom Foundation. Understanding Fantom Transaction Fees. Blog Post. 11 August 2022. Available online: https://blog.fantom.foundation/understanding-fantom-transaction-fees/ (accessed on 3 May 2025).
- Nguyen, Q.; Cronje, A.; Kong, M.; Lysenko, E.; Guzev, A. Lachesis: Scalable asynchronous BFT on DAG streams. arXiv 2021, arXiv:2108.01900. [Google Scholar]
- Eyaa, S.; Sridharan, R.; Ryan, S. Categorising supply chain opportunism: A framework. In Proceedings of the ANZAM Conference, Sydney, Australia, 3–5 December 2014. [Google Scholar]
- Fan, Y.; Stevenson, M. A review of supply chain risk management: Definition, theory, and research agenda. Int. J. Phys. Distrib. Logist. Manag. 2018, 48, 205–230. [Google Scholar] [CrossRef]
- Nayyar, G.M.; Breman, J.G.; Mackey, T.K.; Clark, J.P.; Hajjou, M.; Littrell, M.; Herrington, J.E. Falsified and substandard drugs: Stopping the pandemic. Am. J. Trop. Med. Hyg. 2019, 100, 1058–1065. [Google Scholar] [CrossRef] [PubMed]
- Qian, J.P.; Yang, X.T.; Wu, X.M.; Zhao, L.; Fan, B.L.; Xing, B. A traceability system incorporating 2D barcode and RFID technology for wheat flour mills. Comput. Electron. Agric. 2012, 89, 76–85. [Google Scholar] [CrossRef]
- Conti, M. Food traceability in fruit and vegetables supply chain. In Proceedings of the 2020 IEEE International Symposium on Circuits and Systems (ISCAS), Seville, Spain, 12–14 October 2020; pp. 1–5. [Google Scholar]
- Zhao, G.; Yu, H.; Wang, G.; Sui, Y.; Zhang, L. Applied research of IOT and RFID technology in agricultural product traceability system. In Computer and Computing Technologies in Agriculture VIII, Proceedings of the 8th IFIP WG 5.14 International Conference, CCTA 2014, Beijing, China, 16–19 September 2014; Revised Selected Papers 8; Springer International Publishing: Berlin/Heidelberg, Germany, 2015; pp. 506–514. [Google Scholar]
- Dong, Y.; Ding, B.; Zhang, G.; Jin, G.; Zhao, X. Quality and safety traceability system based on agricultural product supply chain. Trans. Chin. Soc. Agric. Eng. 2016, 32, 280–285. [Google Scholar]
- Sunny, J.; Undralla, N.; Pillai, V.M. Supply chain transparency through blockchain-based traceability: An overview with demonstration. Comput. Ind. Eng. 2020, 150, 106895. [Google Scholar] [CrossRef]
- Mistry, I.; Tanwar, S.; Tyagi, S.; Kumar, N. Blockchain for 5G-enabled IoT for industrial automation: A systematic review, solutions, and challenges. Mech. Syst. Signal Process. 2020, 135, 106382. [Google Scholar] [CrossRef]
- Kouhizadeh, M.; Saberi, S.; Sarkis, J. Blockchain technology and the sustainable supply chain: Theoretically exploring adoption barriers. Int. J. Prod. Econ. 2021, 231, 107831. [Google Scholar] [CrossRef]
- Madumidha, S.; Ranjani, P.S.; Vandhana, U.; Venmuhilan, B. A theoretical implementation: Agriculture-food supply chain management using blockchain technology. In Proceedings of the 2019 TEQIP III Sponsored International Conference on Microwave Integrated Circuits, Photonics and Wireless Networks (IMICPW), Tiruchirappalli, India, 22–24 May 2019; pp. 174–178. [Google Scholar]
- Aniello, L.; Halak, B.; Chai, P.; Dhall, R.; Mihalea, M.; Wilczynski, A. Towards a supply chain management system for counterfeit mitigation using blockchain and PUF. arXiv 2019, arXiv:1908.09585. [Google Scholar]
- Akhtar, M.M.; Rizvi, D.R. Traceability and detection of counterfeit medicines in pharmaceutical supply chain using blockchain-based architectures. In Sustainable and Energy Efficient Computing Paradigms for Society; Springer: Berlin/Heidelberg, Germany, 2021; pp. 1–31. [Google Scholar]
- Yang, X.; Li, M.; Yu, H.; Wang, M.; Xu, D.; Sun, C. A trusted blockchain-based traceability system for fruit and vegetable agricultural products. IEEE Access 2021, 9, 36282–36293. [Google Scholar] [CrossRef]
- Dong, Y.; Zhang, X.; Xu, J.; Wang, X.Y.; Kong, J.L.; Sun, P.C. Blockchain-based traceability model for grains and oils whole supply chain. Food Sci. 2020, 41, 30–36. [Google Scholar]
- Sabah, S.; Hasan, A.T.; Daria, A. A Blockchain-based Approach to Detect Counterfeit Drugs in Medical Supply Chain. In Proceedings of the International Conference on Big Data, IoT, and Machine Learning: BIM 2021, Cox’s Bazar, Bangladesh,, 23–25 September 2021; Springer: Singapore, 2021; pp. 609–621. [Google Scholar]
- Salah, K.; Nizamuddin, N.; Jayaraman, R.; Omar, M. Blockchain-based soybean traceability in agricultural supply chain. IEEE Access 2019, 7, 73295–73305. [Google Scholar] [CrossRef]
- Shahid, A.; Almogren, A.; Javaid, N.; Al-Zahrani, F.A.; Zuair, M.; Alam, M. Blockchain-based agri-food supply chain: A complete solution. IEEE Access 2020, 8, 69230–69243. [Google Scholar] [CrossRef]
- Wang, L.; Xu, L.; Zheng, Z.; Liu, S.; Li, X.; Cao, L.; Li, J.; Sun, C. Smart contract-based agricultural food supply chain traceability. IEEE Access 2021, 9, 9296–9307. [Google Scholar] [CrossRef]
- Bumblauskas, D.; Mann, A.; Dugan, B.; Rittmer, J. A blockchain use case in food distribution: Do you know where your food has been? Int. J. Inf. Manag. 2020, 52, 102008. [Google Scholar] [CrossRef]
- Cocco, L.; Mannaro, K. Blockchain in agri-food traceability systems: A model proposal for a typical italian food product. In Proceedings of the 2021 IEEE International Conference on Software Analysis, Evolution and Reengineering (SANER), Honolulu, HI, USA, 9–12 March 2021; pp. 669–678. [Google Scholar]
- Hasan, A.T.; Sabah, S.; Haque, R.U.; Daria, A.; Rasool, A.; Jiang, Q. Towards convergence of iot and blockchain for secure supply chain transaction. Symmetry 2022, 14, 64. [Google Scholar] [CrossRef]
- Cocco, L.; Tonelli, R.; Marchesi, M. Blockchain and self-sovereign identity to support quality in the food supply chain. Future Internet 2021, 13, 301. [Google Scholar] [CrossRef]
- Ehsan, I.; Irfan Khalid, M.; Ricci, L.; Iqbal, J.; Alabrah, A.; Sajid Ullah, S.; Alfakih, T.M. A conceptual model for blockchain-based agriculture food supply chain system. Sci. Program. 2022, 2022, 7358354. [Google Scholar] [CrossRef]
- Rahman, M.N.A.; Kadir, M.F.A.; Awang, M.K.; Safei, S.; Saany, S.I.A.; Kamarudin, A.S. Distributed Ledger Model for Agriculture Product Supply Chain. In Human Centred Intelligent Systems: Proceedings of KES-HCIS 2022 Conference; Springer Nature: Singapore, 2022; pp. 161–170. [Google Scholar]
- Chatterjee, K.; Singh, A. A blockchain-enabled security framework for smart agriculture. Comput. Electr. Eng. 2023, 106, 108594. [Google Scholar] [CrossRef]
- European Commission. European Blockchain Services Infrastructure (EBSI): Architecture and Vision. 2022. Available online: https://ec.europa.eu/digital-building-blocks/wikis/display/EBSI/Home (accessed on 3 May 2025).
- Cocco, L.; Marchesi, M. Blockchain and self-sovereign identity for supply chain traceability. Future Internet 2022, 14, 44. [Google Scholar] [CrossRef]
- Choi, S.M.; Park, J.; Nguyen, Q.; Cronje, A. Fantom: A scalable framework for asynchronous distributed systems. arXiv 2018, arXiv:1810.10360. [Google Scholar]
- Kaur, G.; Gandhi, C. Scalability in blockchain: Challenges and solutions. In Handbook of Research on Blockchain Technology; Academic Press: Cambridge, MA, USA, 2020; pp. 373–406. [Google Scholar]
- Satybaldy, A.; Nowostawski, M.; Ellingsen, J. Self-sovereign identity systems: Evaluation framework. In Privacy and Identity Management. Data for Better Living: AI and Privacy, Proceedings of the 14th IFIP WG 9.2, 9.6/11.7, 11.6/SIG 9.2. 2 International Summer School, Windisch, Switzerland, 19–23 August 2019; Revised Selected Papers 14; Springer: Berlin/Heidelberg, Germany, 2020; pp. 447–461. [Google Scholar]
- Ryu, T.W.; Eick, C.F. A database clustering methodology and tool. Inf. Sci. 2005, 171, 29–59. [Google Scholar] [CrossRef]





| Study | Technologies | Analysis | Security Properties | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| SSI | IPFS | Light Weight Blockchain | IoT | Scalability | Efficiency | Security | |||||||
| [19] | - | - | - | - | - | - | - | - | - | ✓ | - | - | ✓ |
| [21] | - | - | - | - | - | - | - | - | - | ✓ | - | - | ✓ |
| [22] | - | - | - | - | - | - | - | - | - | ✓ | - | - | ✓ |
| [13,26] | - | - | - | ✓ | - | - | - | - | - | ✓ | - | - | ✓ |
| [27] | - | - | - | - | - | - | - | - | - | ✓ | - | - | ✓ |
| [32] | - | ✓ | - | - | - | - | - | - | - | ✓ | - | - | ✓ |
| [24] | - | - | - | ✓ | - | - | - | - | - | ✓ | - | - | ✓ |
| [10,12,20] | - | - | - | - | - | - | - | - | - | ✓ | - | - | ✓ |
| [23,30,35] | - | - | - | - | - | - | - | - | - | ✓ | - | - | ✓ |
| [9,25] | - | - | - | - | - | - | - | - | - | ✓ | - | - | ✓ |
| [29] | - | - | - | ✓ | ✓ | - | - | - | - | ✓ | - | - | ✓ |
| [33,34,36] | - | ✓ | - | - | - | - | - | - | - | ✓ | - | - | ✓ |
| [38] | ✓ | - | - | - | - | - | - | ✓ | ✓ | ✓ | - | - | ✓ |
| [31] | - | - | ✓ | ✓ | ✓ | - | - | - | - | ✓ | - | - | ✓ |
| [37] | - | - | ✓ | ✓ | ✓ | ✓ | ✓ | - | ✓ | ✓ | ✓ | - | - |
| [39,40] | - | - | - | - | - | - | - | - | - | ✓ | - | - | ✓ |
| [41] | - | - | - | - | - | - | - | - | - | ✓ | - | - | ✓ |
| This study | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Notation | Description | Notation | Description |
|---|---|---|---|
| governance authority | distributor | ||
| manufacturer | retailer | ||
| public key | private key | ||
| end-user | local government | ||
| hash function | verifiable credential |
| Studies | |||||||
|---|---|---|---|---|---|---|---|
| [19] | 0 | - | - | - | 5+ | No | No |
| [23] | 1 | - | - | - | 5+ | No | No |
| [37] | 2 | 238.8 | 2 | 0.004 | 5+ | Yes | No |
| [29] | 1 | - | 23 | 0.2 | 5+ | No | No |
| TTS | 4 | 100 | 1 | 0.07 | 5 | Yes | Yes |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hasan, A.S.M.T.; Haque, R.U.; Wigger, L.; Vatterott, A. Trusted Traceability Service: A Novel Approach to Securing Supply Chains. Electronics 2025, 14, 1985. https://doi.org/10.3390/electronics14101985
Hasan ASMT, Haque RU, Wigger L, Vatterott A. Trusted Traceability Service: A Novel Approach to Securing Supply Chains. Electronics. 2025; 14(10):1985. https://doi.org/10.3390/electronics14101985
Chicago/Turabian StyleHasan, A S M Touhidul, Rakib Ul Haque, Larry Wigger, and Anthony Vatterott. 2025. "Trusted Traceability Service: A Novel Approach to Securing Supply Chains" Electronics 14, no. 10: 1985. https://doi.org/10.3390/electronics14101985
APA StyleHasan, A. S. M. T., Haque, R. U., Wigger, L., & Vatterott, A. (2025). Trusted Traceability Service: A Novel Approach to Securing Supply Chains. Electronics, 14(10), 1985. https://doi.org/10.3390/electronics14101985





