Design and Evaluation of Device Authentication and Secure Communication System with PQC for AIoT Environments
Abstract
1. Introduction
2. Related Works
2.1. AIoT
2.2. Post-Quantum Cryptosystem
2.3. NTRU
2.4. Falcon Signature Mechanism
3. Proposed Scheme
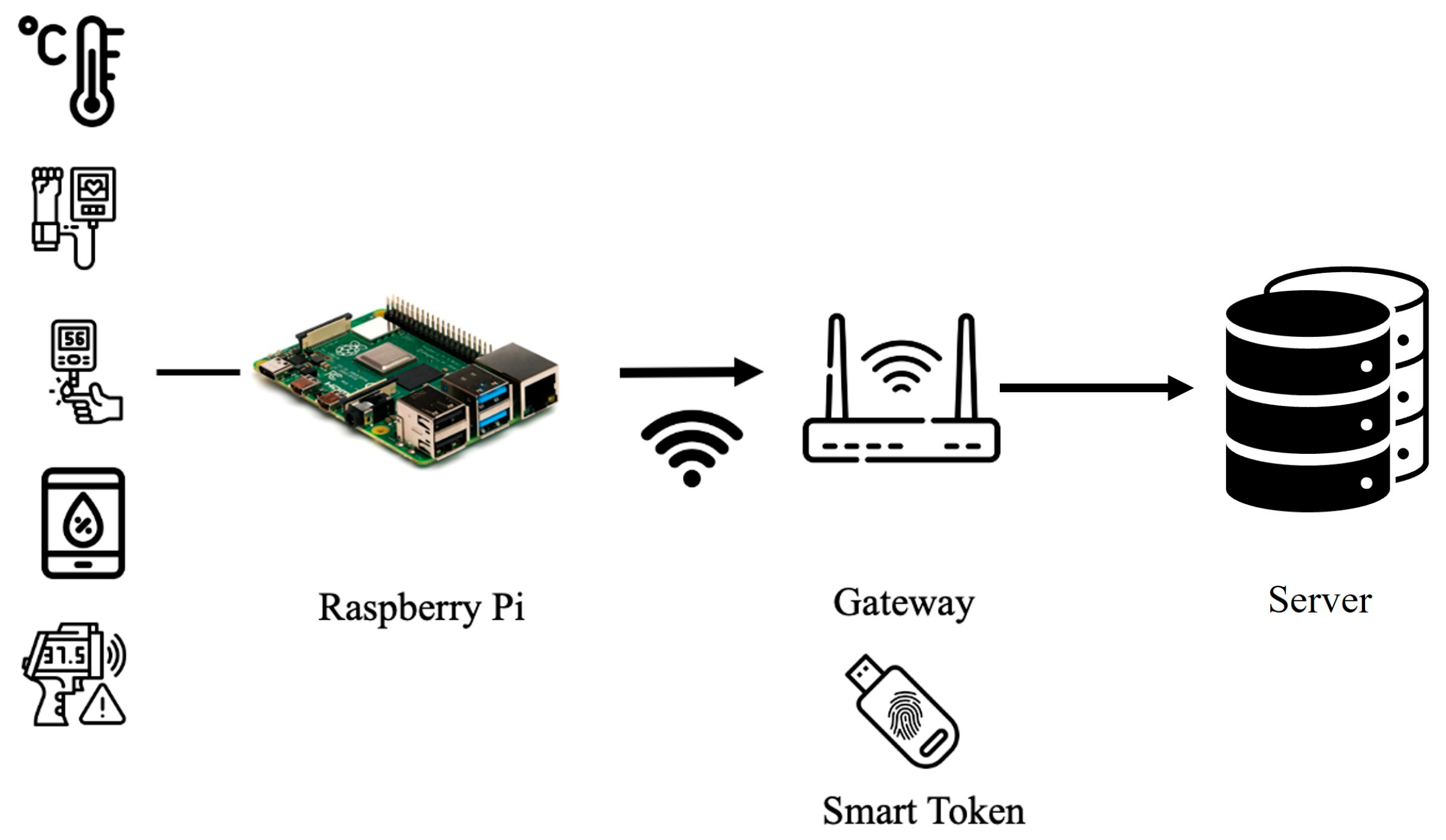
3.1. System Structure
3.2. Preliminary
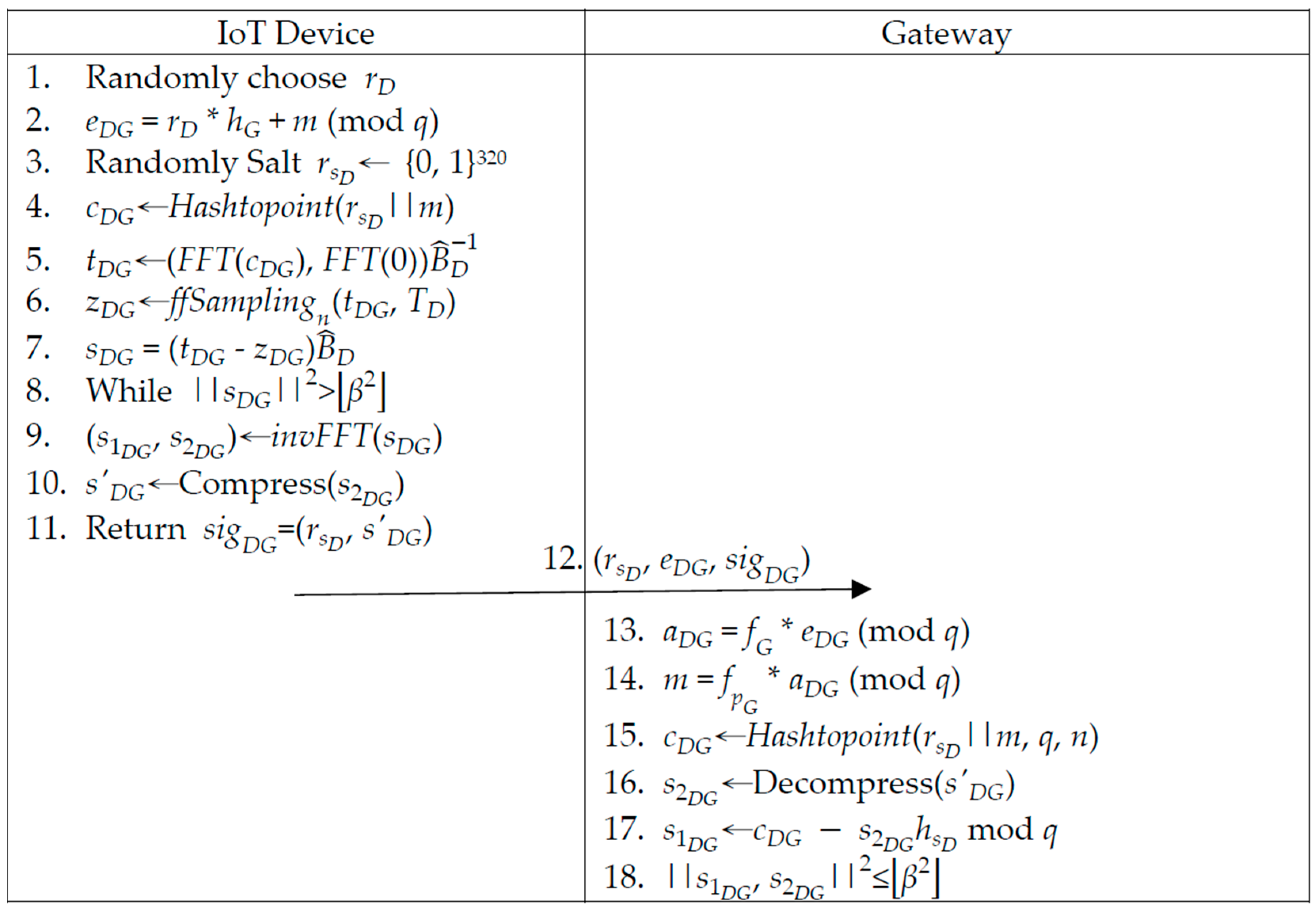
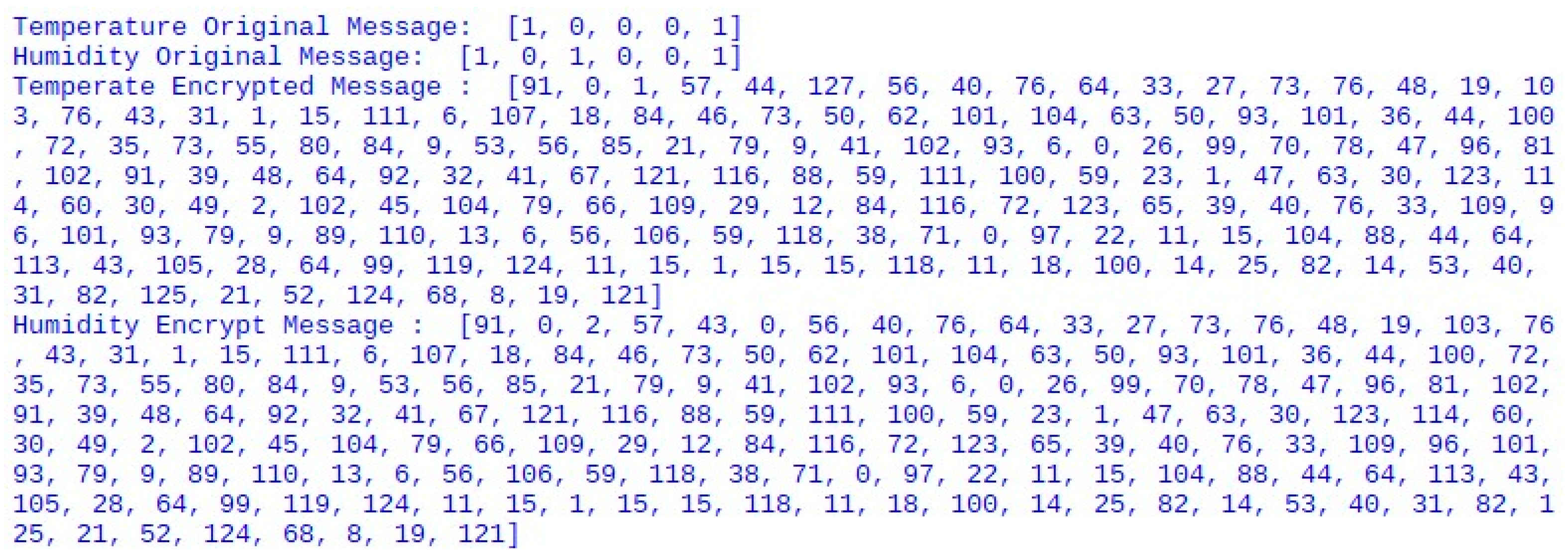
3.3. IoT Devices’ Gateway Communication Phase
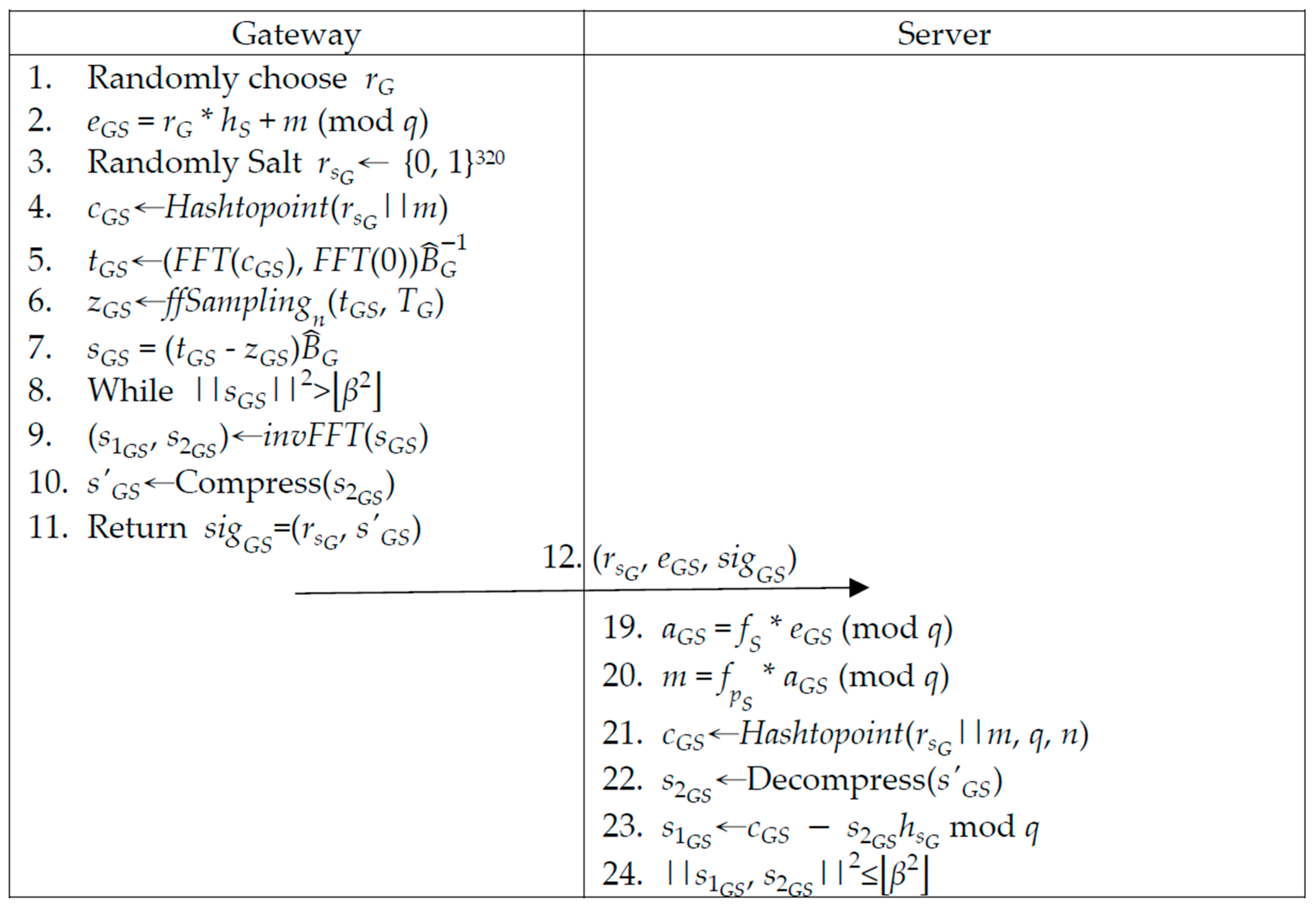
3.4. Gateways’ Server Communication Phase
4. Security Analysis
4.1. Correctness
4.2. Confidentiality
4.3. Integrity
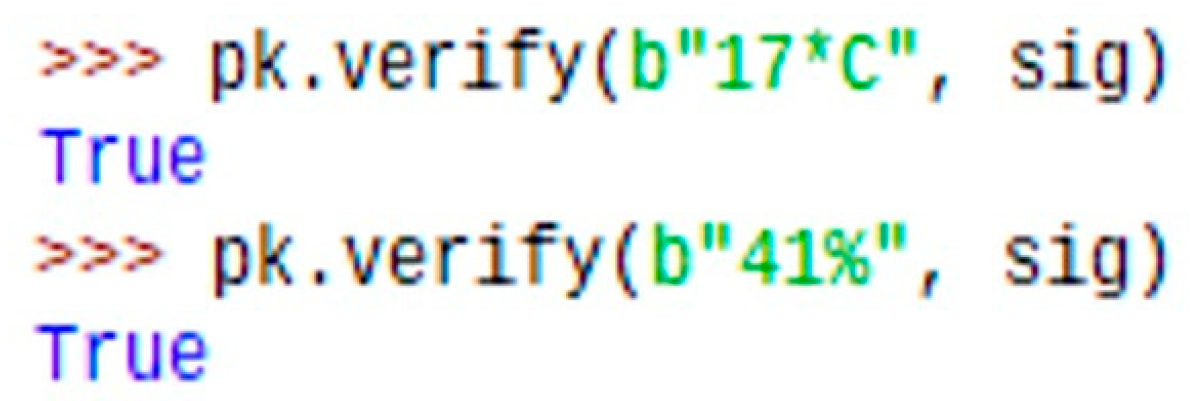
4.4. Non-Repudiation
5. Performance Analysis
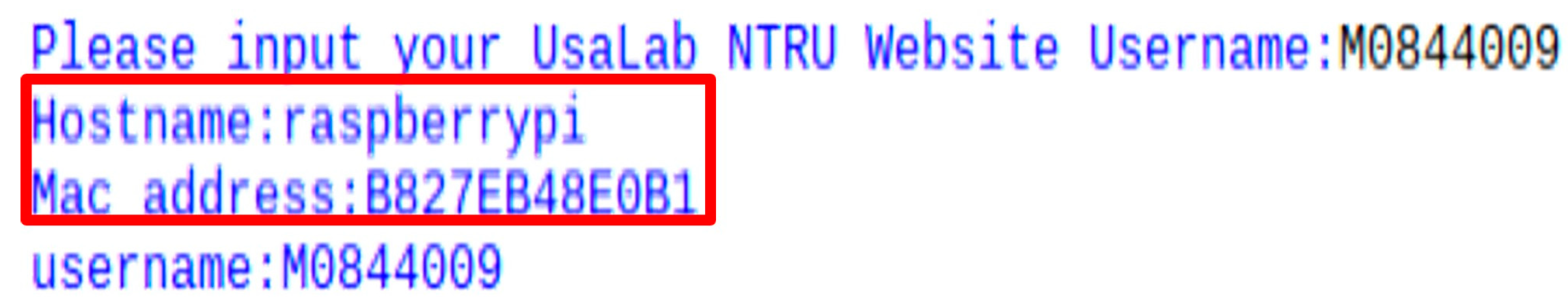
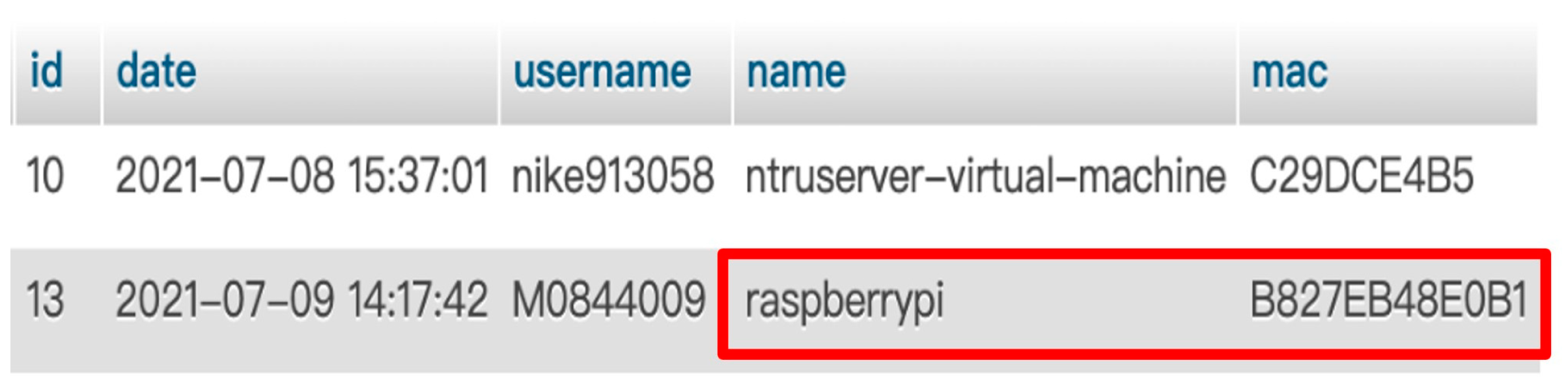
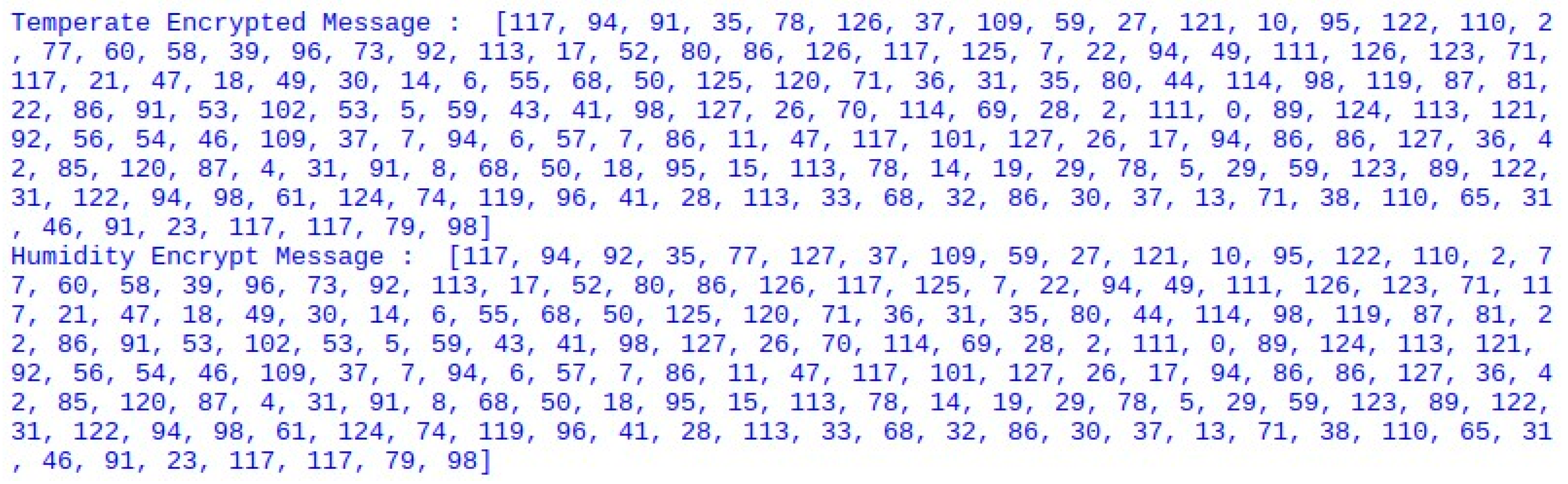
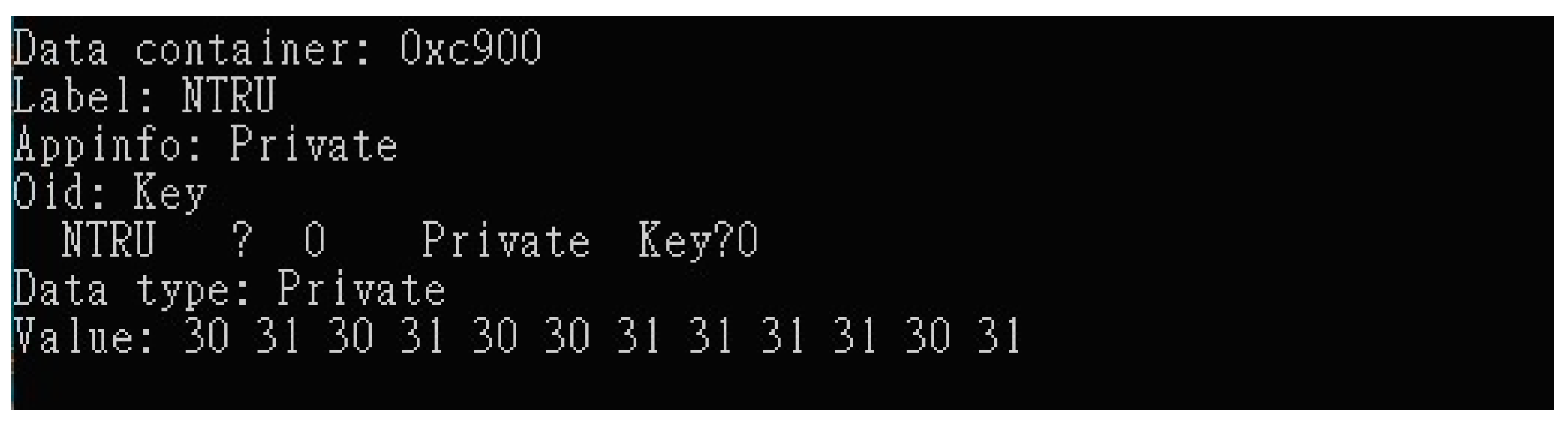
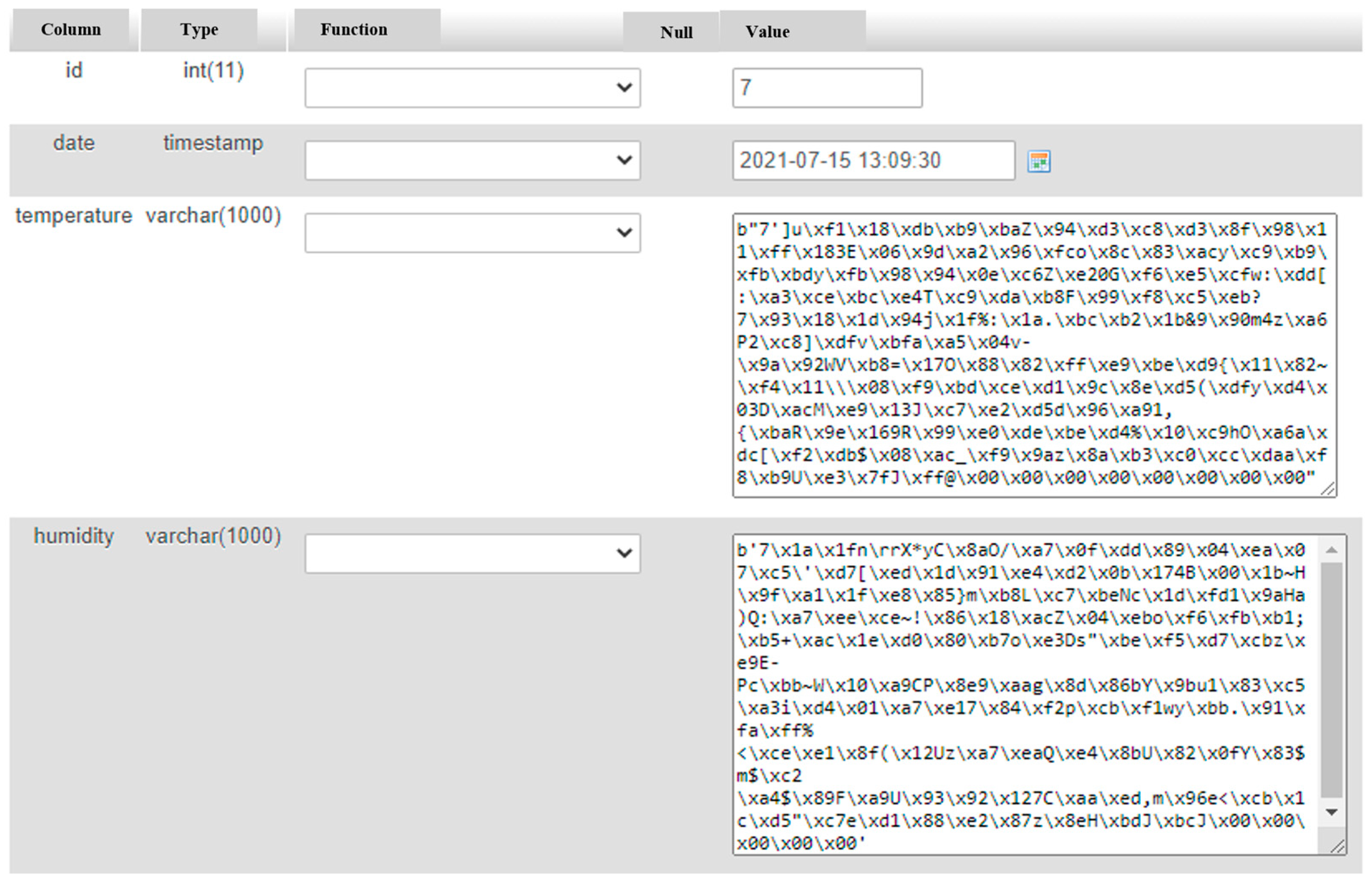
6. System Implementation
7. Result and Discussions
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Murphy, K.; Di Ruggiero, E.; Upshur, R.; Willison, D.J.; Malhotra, N.; Cai, J.C.; Malhotra, N.; Lui, V.; Gibson, J. Artificial intelligence for good health: A scoping review of the ethics literature. BMC Med. Ethics 2021, 22, 14. [Google Scholar] [CrossRef] [PubMed]
- Lin, T.-W.; Hsu, C.-L. Privacy-Preserved Hierarchical Authentication and Key Agreement for AI-Enabled Telemedicine Systems. In Proceedings of the 2021 International Conference on Security and Information Technologies with AI, Internet Computing and Big-Data Applications, Taichung City, Taiwan, 18–20 November 2021; pp. 134–142. [Google Scholar]
- Li, S.; Xu, L.D.; Zhao, S. 5G Internet of Things: A survey. J. Ind. Inf. Integr. 2018, 10, 1–9. [Google Scholar] [CrossRef]
- Wong, A.M.; Hsu, C.-L.; Le, T.-V.; Hsieh, M.-C.; Lin, T.-W. Three-Factor Fast Authentication Scheme with Time Bound and User Anonymity for Multi-Server E-Health Systems in 5G-Based Wireless Sensor Networks. Sensors 2020, 20, 2511. [Google Scholar] [CrossRef] [PubMed]
- Cheng, S.M.; Hong, B.K.; Hung, C.F. Attack Detection and Mitigation in MEC-Enabled 5G Networks for AIoT. IEEE Internet Things Mag. 2022, 5, 76–81. [Google Scholar] [CrossRef]
- Nozari, H.; Szmelter-Jarosz, A.; Ghahremani-Nahr, J. Analysis of the Challenges of Artificial Intelligence of Things (AIoT) for the Smart Supply Chain (Case Study: FMCG Industries). Sensors 2022, 22, 2931. [Google Scholar] [CrossRef] [PubMed]
- Dyakonov, M. When will useful quantum computers be constructed? Not in the foreseeable future, this physicist argues. Here’s why: The case against: Quantum computing. IEEE Spectr. 2019, 56, 24–29. [Google Scholar] [CrossRef]
- Shor, P.W. Polynomial-Time Algorithms for Prime Factorization and Discrete Logarithms on a Quantum Computer. SIAM J. Comput. 1997, 26, 1484–1509. [Google Scholar] [CrossRef]
- Hoffstein, J.; Pipher, J.; Silverman, J.H. NTRU: A ring-based public key cryptosystem. In Proceedings of the Algorithmic Number Theory, Third International Symposium, ANTS-III, Portland, OR, USA, 21–25 June 1998; pp. 267–288. [Google Scholar]
- Fouque, P.-A.; Hoffstein, J.; Kirchner, P.; Lyubashevsky, V.; Pornin, T.; Prest, T.; Ricosset, T.; Seiler, G.; Whyte, W.; Zhang, Z. Falcon: Fast-Fourier Lattice-Based Compact Signatures over NTRU. Available online: https://falcon-sign.info/falcon.pdf (accessed on 22 December 2023).
- Lei, X.; Liao, X. NTRU-KE: A Lattice-based Public Key Exchange Protocol. IACR Cryptol. ePrint Arch. 2013, 2013, 718. [Google Scholar]
- Rong, G.; Xu, Y.; Tong, X.; Fan, H. An edge-cloud collaborative computing platform for building AIoT applications efficiently. J. Cloud Comput. 2021, 10, 36. [Google Scholar] [CrossRef]
- Ricquebourg, V.; Menga, D.; Durand, D.; Marhic, B.; Delahoche, L.; Loge, C. The Smart Home Concept: Our immediate future. In Proceedings of the 2006 1ST IEEE International Conference on e-Learning in Industrial Electronics, Hammamet, Tunisia, 18–20 December 2006; pp. 23–28. [Google Scholar]
- Lucke, D.; Constantinescu, C.; Westkämper, E. Smart Factory—A Step towards the Next Generation of Manufacturing. In Proceedings of the Manufacturing Systems and Technologies for the New Frontier: The 41st CIRP Conference on Manufacturing Systems, Tokyo, Japan, 26–28 May 2008; pp. 115–118. [Google Scholar]
- Schaffers, H.; Komninos, N.; Pallot, M.; Trousse, B.; Nilsson, M.; Oliveira, A. Smart Cities and the Future Internet: Towards Cooperation Frameworks for Open Innovation. In The Future Internet: Future Internet Assembly 2011: Achievements and Technological Promises; Springer: Berlin/Heidelberg, Germany, 2011; pp. 431–446. [Google Scholar]
- Fernández-Caramés, T.M.; Fraga-Lamas, P. A Review on the Use of Blockchain for the Internet of Things. IEEE Access 2018, 6, 32979–33001. [Google Scholar] [CrossRef]
- Panarello, A.; Tapas, N.; Merlino, G.; Longo, F.; Puliafito, A. Blockchain and IoT Integration: A Systematic Survey. Sensors 2018, 18, 2575. [Google Scholar] [CrossRef]
- Dai, H.N.; Zheng, Z.; Zhang, Y. Blockchain for Internet of Things: A Survey. IEEE Internet Things J. 2019, 6, 8076–8094. [Google Scholar] [CrossRef]
- Ray, P.P.; Dash, D.; De, D. Edge computing for Internet of Things: A survey, e-healthcare case study and future direction. J. Netw. Comput. Appl. 2019, 140, 1–22. [Google Scholar] [CrossRef]
- Post-Quantum Cryptography. Available online: https://csrc.nist.gov/Projects/Post-Quantum-Cryptography (accessed on 18 March 2024).
- Kim, J.; Park, J.H. NTRU+: Compact Construction of NTRU Using Simple Encoding Method. IEEE Trans. Inf. Forensics Secur. 2023, 18, 4760–4774. [Google Scholar] [CrossRef]
- Perlner, R.A.; Cooper, D.A. Quantum resistant public key cryptography: A survey. In Proceedings of the 8th Symposium on Identity and Trust on the Internet, Gaithersburg, MD, USA, 14–16 April 2009; pp. 85–93. [Google Scholar]
- Mailloux, L.O.; Lewis, C.D., II; Riggs, C.; Grimaila, M.R. Post-Quantum Cryptography: What Advancements in Quantum Computing Mean for IT Professionals. IT Prof. 2016, 18, 42–47. [Google Scholar] [CrossRef]
- Bi, J.; Han, L. Lattice Attacks on NTRU Revisited. IEEE Access 2021, 9, 66218–66222. [Google Scholar] [CrossRef]
- Ahmed Othman, K.; Shaimaa Khudhair, S.; Hind Jumaa, S.; Zainab Khyioon, A. Subject Review: Comparison between RSA, ECC & NTRU Algorithms. Int. J. Eng. Res. Adv. Technol. 2019, 5, 11–15. [Google Scholar] [CrossRef]
- Loriya, H.T.; Kulshreshta, A.; Keraliya, D.R. Security analysis of various public key cryptosystems for authentication and key agreement in wireless communication network. Int. J. Adv. Res. Comput. Commun. Eng. 2017, 6, 267–274. [Google Scholar]
- Singh, G. NTRU-Python3. Available online: https://github.com/topShotZexN/NTRU-Python3 (accessed on 22 December 2023).
- Prest, T. falcon.py. Available online: https://github.com/tprest/falcon.py (accessed on 22 December 2023).
- Shang, Z.; Ma, M.; Li, X. A Secure Group-Oriented Device-to-Device Authentication Protocol for 5G Wireless Networks. IEEE Trans. Wirel. Commun. 2020, 19, 7021–7032. [Google Scholar] [CrossRef]
- Zhang, Y.; Li, B.; Wu, J.; Liu, B.; Chen, R.; Chang, J. Efficient and Privacy-Preserving Blockchain-Based Multifactor Device Authentication Protocol for Cross-Domain IIoT. IEEE Internet Things J. 2022, 9, 22501–22515. [Google Scholar] [CrossRef]
- Schwabe, P.; Avanzi, R.; Bos, J.; Ducas, L.; Kiltz, E.; Lepoint, T.; Lyubashevsky, V.; Schanck, J.M.; Seiler, G.; Stehle, D. CRYSTALS-Kyber Algorithm Specifications and Supporting Documentation (Version 3.02). 2021. Available online: https://www.pq-crystals.org/kyber/data/kyber-specification-round3-20210804.pdf (accessed on 1 February 2024).
- Ducas, L.; Kiltz, E.; Lepoint, T.; Lyubashevsky, V.; Schwabe, P.; Seiler, G.; Stehlé, D. CRYSTALS-Dilithium: A Lattice-Based Digital Signature Scheme. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2018, 2018, 238–268. [Google Scholar] [CrossRef]
- Xie, J.; Zhao, W.; Lee, H.; Roy, D.B.; Zhang, X. Hardware Circuits and Systems Design for Post-Quantum Cryptography—A Tutorial Brief. IEEE Trans. Circuits Syst. II Express Briefs 2024, 71, 1670–1676. [Google Scholar] [CrossRef]









| Algorithms | RSA | ECC | NTRU |
|---|---|---|---|
| Properties | |||
| Encryption | O | O | O |
| Signature | O | O | O |
| Key exchange | X | O | O |
| Encryption speed | Slow | Fast | Fastest |
| Key distribution | Easy | Difficult | Easy |
| Quantum-resistant | X | X | O |
| Algorithms | RSA | ECC | NTRU |
|---|---|---|---|
| Security Level (bits) | |||
| 80 | 1024 | 160 | 2008 |
| 112 | 2048 | 224 | 3033 |
| 128 | 3072 | 256 | 3501 |
| 192 | 7680 | 384 | 5193 |
| 256 | 15,360 | 521 | 7690 |
| Items | Security Level (bits) | Key Generation (ms) | Encryption (ms) | Decryption (ms) |
|---|---|---|---|---|
| Algorithms | ||||
| NTRU-251 | 80 | 75.65 | 1.68 | 8.22 |
| ECC-192 | 80 | 57.87 | 37.81 | 19.15 |
| NTRU-347 | 112 | 144.16 | 3.11 | 15.70 |
| ECC-224 | 112 | 234.11 | 52.52 | 26.35 |
| NTRU-397 | 128 | 188.92 | 3.97 | 20.26 |
| ECC-256 | 128 | 478.22 | 68.72 | 35.00 |
| NTRU-587 | 192 | 412.10 | 8.42 | 44.42 |
| ECC-384 | 192 | 947.43 | 182.35 | 90.61 |
| NTRU-787 | 256 | 738.75 | 14.49 | 79.48 |
| ECC-521 | 256 | 2055.04 | 423.25 | 211.35 |
| Notations | Definitions |
|---|---|
| Public key polynomial vectors for encryption and decryption of IoT devices, gateway, and server respectively. | |
| Private key polynomial vectors for encryption and decryption of IoT devices. | |
| Private key polynomial vectors for encryption and decryption of gateway. | |
| Private key polynomial vectors for encryption and decryption of server. | |
| Random polynomials. | |
| Message, which is a polynomial. | |
| Encrypted data, which are polynomials. | |
| Public key polynomial vectors for signatures of IoT devices, gateway, and server respectively. | |
| ) | Private key polynomial vectors for signatures of IoT devices. |
| ) | Private key polynomial vectors for signatures of gateway. |
| Random polynomials for signatures. | |
| Signatures. | |
| Q | Random integer for signature. |
| n | Degree of lattice polynomial. |
| Bound of vector. |
| Hardware | PC (s) | Raspberry Pi 3B (s) |
|---|---|---|
| Security Level | ||
| Medium | 0.2812 | 4.405 |
| Standard (80 bits) | 0.5312 | 8.688 |
| High (128 bits) | 0.8118 | 11.345 |
| Highest (160 bits) | 1.8266 | 17.993 |
| Hardware | PC (s) | Raspberry Pi 3B (s) |
|---|---|---|
| Security Level | ||
| Falcon-64 | 1.277 | 20.004 |
| Falcon-128 | 1.273 | 20.820 |
| Falcon-256 | 1.334 | 39.242 |
| Falcon-512 | 2.808 | 211.747 |
| Phase | IoT Devices-Gateways Communication Phase | Gateways-Server Communication Phase |
|---|---|---|
| Role | ||
| IoT Device | N/A | |
| Gateway | ||
| Server | N/A | |
| Total |
| Devices | IoT Device | Gateway | Server |
|---|---|---|---|
| Specification | |||
| Module | Raspberry Pi 3B | PC | Server |
| CPU | ARM Cortex-A53 1.4 GHz 4-core | i7-7000 3.60 GHZ 8-core | E5-2620v3 6-core |
| RAM | 1 GB | 32 GB | 32 GB |
| OS | Raspberry Pi | Windows 10 Education | VMWare ESXi-6.7.0 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, Y.-J.; Hsu, C.-L.; Lin, T.-W.; Lee, J.-S. Design and Evaluation of Device Authentication and Secure Communication System with PQC for AIoT Environments. Electronics 2024, 13, 1575. https://doi.org/10.3390/electronics13081575
Chen Y-J, Hsu C-L, Lin T-W, Lee J-S. Design and Evaluation of Device Authentication and Secure Communication System with PQC for AIoT Environments. Electronics. 2024; 13(8):1575. https://doi.org/10.3390/electronics13081575
Chicago/Turabian StyleChen, Yu-Jen, Chien-Lung Hsu, Tzu-Wei Lin, and Jung-San Lee. 2024. "Design and Evaluation of Device Authentication and Secure Communication System with PQC for AIoT Environments" Electronics 13, no. 8: 1575. https://doi.org/10.3390/electronics13081575
APA StyleChen, Y.-J., Hsu, C.-L., Lin, T.-W., & Lee, J.-S. (2024). Design and Evaluation of Device Authentication and Secure Communication System with PQC for AIoT Environments. Electronics, 13(8), 1575. https://doi.org/10.3390/electronics13081575









