1. Introduction
As software-defined vehicles (SDVs) move from concept to reality, modern automobiles are evolving into sophisticated computer systems, integrating complex network communication, both internally and externally. In-vehicle network systems serve as crucial interfaces connecting diverse subsystems within the vehicles and facilitating interactions with the external environment. However, the safety and reliability requirements need to be carefully addressed for communication within automotive in-vehicle networks to ensure the quality of vehicles.
Functional safety, as defined by ISO 26262 [
1], addresses the safety needs associated with the electrical and electronic systems within vehicles. This standard emphasizes hazard and risk assessment, demanding the implementation of safety measures designed to mitigate to acceptable levels the risks associated with system failures. It underscores the importance of identifying potential hazards early in the design process, ensuring that system responses to failures are both timely and accurate, to prevent harm.
Popularly used communication protocols within automotive in-vehicle networks include automotive Ethernet (AE) and controller area networks (CAN). The CAN bus, a long-standing backbone for in-vehicle communications, facilitates real-time data exchange between various electronic control units (ECUs), supporting essential vehicle functions from engine management systems to brake control systems. Its simplicity and robustness have made it a standard. However, its lack of encryption and authentication exposes it to cybersecurity risks, potentially compromising vehicle safety. On the other hand, AE caters to the increasing demand for higher bandwidth and faster data transmission rates required by modern vehicles’ advanced features, such as infotainment systems and advanced driver assistance systems (ADAS). Despite its advantages, AE inherits the vulnerabilities of standard Ethernet technology. It lacks security designs, such as access control. Once hackers gain internal access, AE may become vulnerable to attacks such as frame injection or denial-of-service (DoS) attacks [
2]. To address the problems mentioned above, many researchers have used intrusion-detection systems (IDSs) to identify and mitigate cyber threats in these vehicular networks. The role of an IDS is to monitor network traffic for signs of suspicious activities. Extensive research has been conducted on IDSs tailored for CANs, audio/video transport protocol (AVTP), scalable service-oriented middleware over IP (SOME/IP), and generalized precision time protocol (gPTP) protocols. The following presents a summary of the pertinent research in this field.
Many scholars have researched the enhancement of integrity and confidentiality of the CAN bus. Given the CAN bus maximum data payload of only 8 bytes, implementing security countermeasures poses a significant challenge. Such countermeasures can lead to additional data processing and computational burdens, exacerbated by the bus’s inherent packet size constraints, resulting in unacceptable communication delays in in-vehicle networks with high real-time requirements. Consequently, this scenario has prompted a considerable amount of research into IDSs for the CAN bus, aiming to enhance security, without compromising on the essential real-time requirements. As early as 2013, Miller et al. [
3] pioneered the field of CAN network security by introducing message rate analysis as a technique for intrusion detection, employing a straightforward analytical approach. Building on this foundation, Gmiden et al. [
4] and Song et al. [
5] further advanced the field by proposing methods that leveraged the time interval characteristics of CAN bus messages for intrusion detection. Additionally, Choi et al. [
6] unveiled VoltageIDS, an innovative system that capitalizes on the unique electronic signal characteristics of the CAN bus for enhanced intrusion detection capabilities. While these methods have proven effective, their inability to detect unknown attacks has been a notable limitation, steering the research community toward exploring deep-learning-based solutions. Kang et al. [
7] responded to this challenge by introducing a deep neural network (DNN)-based IDS that analyzes statistical features of CAN messages. Despite their promise, such deep learning approaches have encountered barriers in maintaining consistent performance and computational efficiency across varying scenarios. To overcome these obstacles, Hossain introduced a long short-term memory (LSTM)-based IDS that aimed to address the shortcomings of earlier methods. Following this, Seo et al. [
8] proposed a novel generative adversarial network (GAN)-based system focusing on the sequence features of the identifier, and Gao et al. [
9] developed a hybrid intrusion detection approach that combined empirical knowledge structures, decisional DNA, and deep learning techniques. Consequently, significant advancements have been achieved in research focused on the CAN bus.
In recent years, the adoption of Ethernet in automotive applications has gained popularity. AE supports high-bandwidth data transmission and is well suited to the real-time transmission of large data volumes. However, as its use has expanded, security vulnerabilities have increasingly come to light. To enhance AE’s security, several scholars have developed IDSs for its various protocols. For instance, Buscemi et al. [
10] introduced a machine-learning-based IDS for the gPTP protocol. Koyama et al. [
11] proposed a whitelist-based IDS for the SOME/IP protocol, addressing the need for systems that can adapt to new network attacks. Alkhatib et al. [
12] developed an offline IDS using a sequential deep learning model for intrusion detection, although this method lacked real-time performance analysis. Following this, Luo et al. [
13] proposed a multi-layer IDS that improved accuracy and evaluated real-time performance, albeit without considering the false alarm rate. Additionally, Jeong et al. [
14] created a feature generator and a convolutional neural network-based intrusion detection model for the AVTP protocol. They also explored a convolutional autoencoder-based IDS for the AVTP protocol [
15], but it suffered from poor accuracy.
Recently, hybrid automotive in-vehicle networks have been increasingly used in modern gateways based on high-performance computing platforms. These networks combine multiple communication protocols (such as AE and CANs) to support various functionalities and data exchange requirements. This integration facilitates seamless information exchange through the gateway, while coping with the technological differences and operational variations inherent to the real-time operational and data processing requirements of various network types. As illustrated above, the IDSs proposed by these scholars addressed the security concerns of a single network protocol. However, traditional IDSs designed for specific protocols may not be directly applicable or effective within this multifaceted environment. As far as we know, there has been little research addressing the concerns of hybrid automotive in-vehicle networks. In terms of current research, only Han et al. [
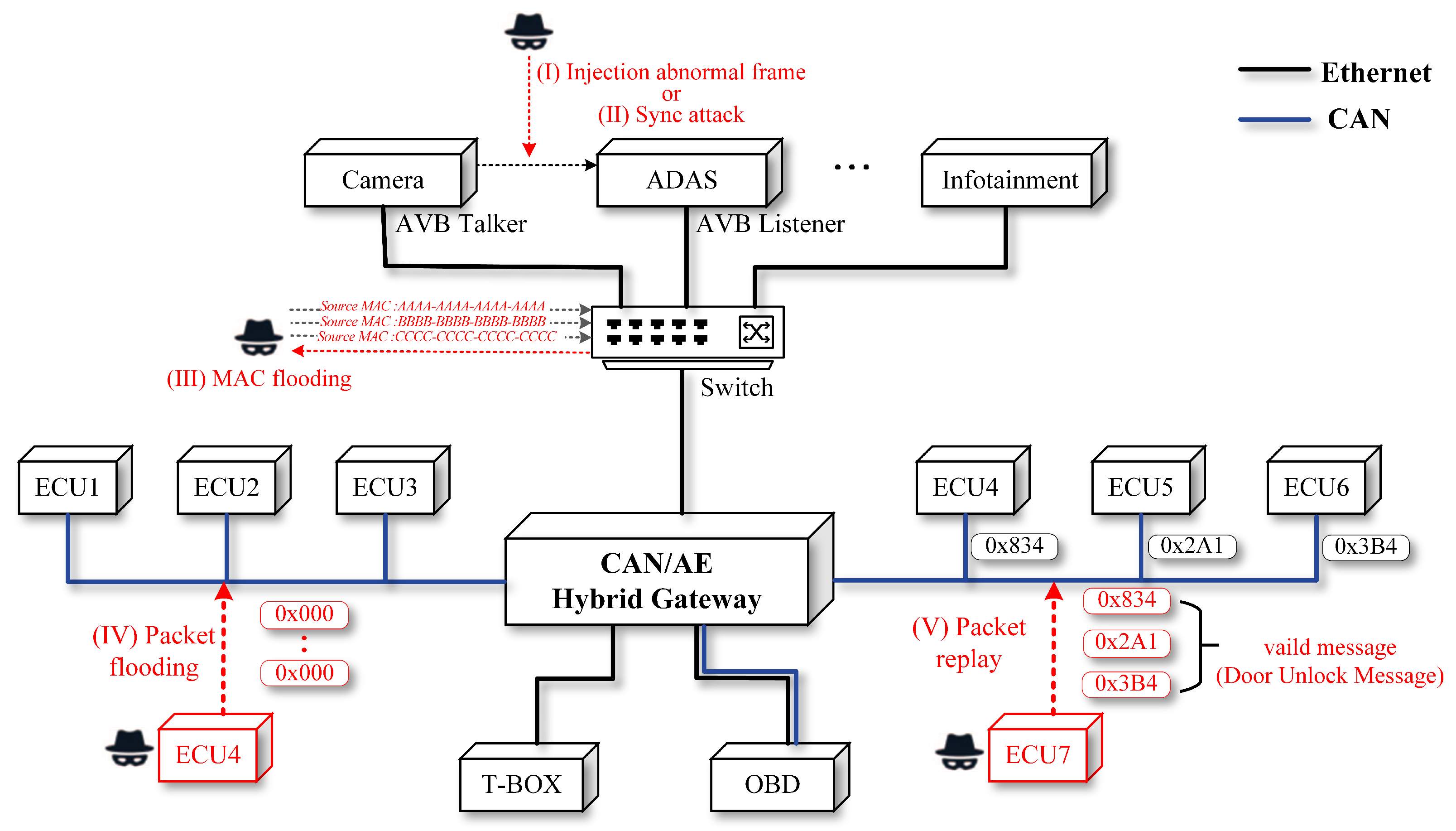
16] proposed a DNN model based TOW-IDS for hybrid automotive networks, in which they disclosed a dataset that contained the traffic of three protocols (AVTP, gPTP, CAN) and encompassed five distinct attack scenarios: (i) frame injection attack, (ii) gPTP synchronization attack, (iii) switch attack (media access control (MAC) flooding), (iv) CAN DoS attack, and (v) replay attack. Their efforts are commendable, but it is noteworthy that the issue of false positives remained unaddressed.
Given this, we propose an IDS based on the Swin Transformer model [
17], and the dataset used was the one proposed by [
16]. This approach can adapt to the characteristics of different network protocols and differences in message lengths to effectively identify and respond to a wide range of potential security threats, without significantly affecting the real-time data transmission of hybrid automotive in-vehicle networks. Specifically, our main contributions can be summarized as follows:
- (1)
To ensure the real-time capability of the IDS, we propose a preprocessing method involving packet imaging and 2D DWT compression of images. We validated the scalability of the model using images of varying resolutions. Experimental results demonstrated an 80 ms reduction in response time after compression.
- (2)
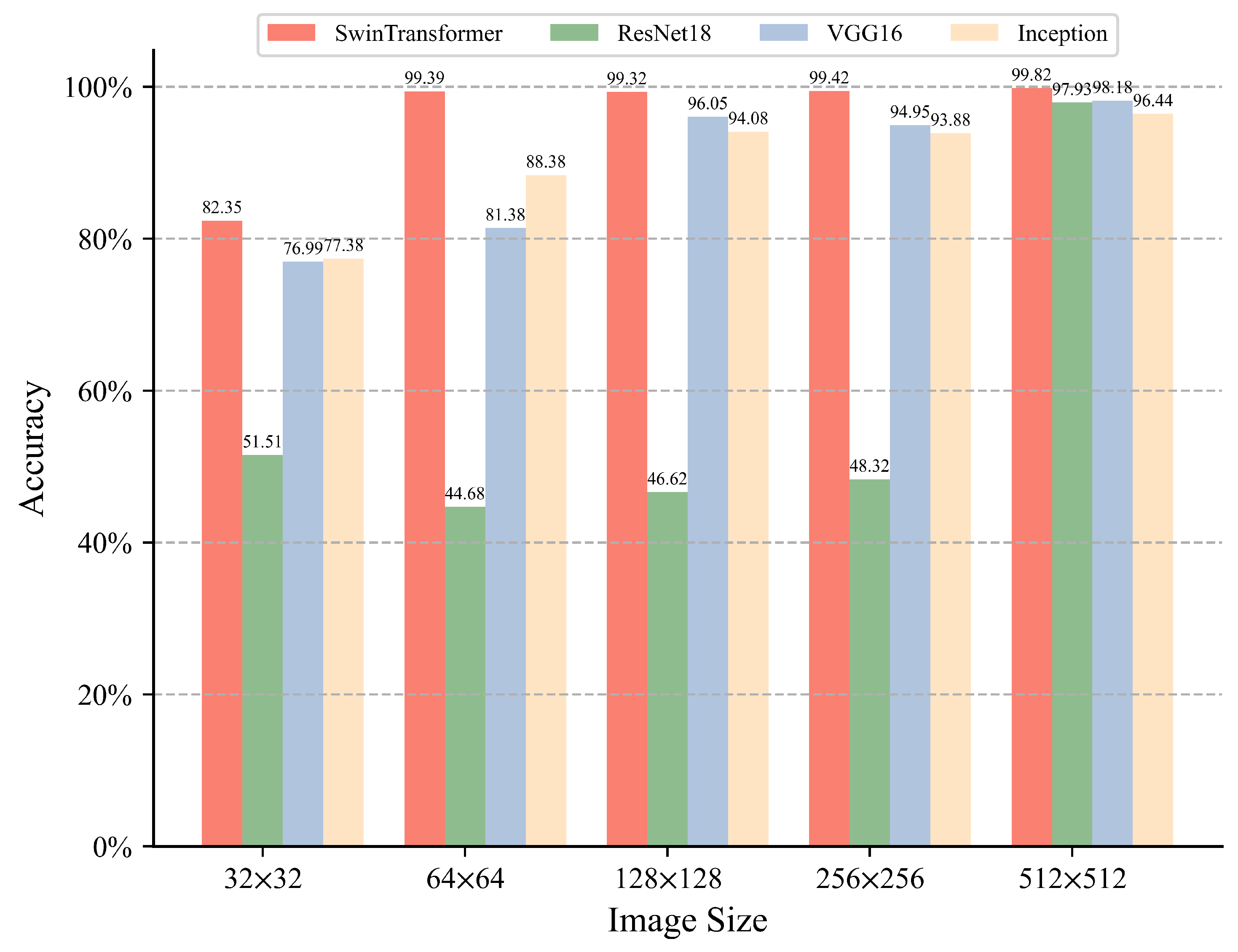
We propose a Swin Transformer-based intrusion detection method for AE and CAN hybrid automotive in-vehicle networks. The experimental results indicated a detection accuracy of up to 99% starting from a 64 × 64 image size, with a false-positive rate (FPR) of 0 at a 512 × 512 image size, thereby enhancing the security of hybrid automotive in-vehicle networks.
- (3)
To comprehensively validate the model’s effectiveness, we compared it with classical network models, including ResNet18, VGG16, and Inception. Our evaluation encompassed various metrics, including accuracy, precision, F1 score, recall, and FPR.
The rest of this paper is organized as follows:
Section 2 reviews AE and CAN network fundamentals and provides an example to explain the types of attacks considered in this study. In
Section 3, we introduce the Swin-Transformer-based intrusion detection method. A detailed implementation description and evaluation follow this in
Section 4. Finally,
Section 5 provides a summary of our work.
3. Proposed Method
This section presents the methodology used for implementing Swin-Transformer-based IDS for AE and CANs and its experiment analysis. The method comprises three key steps: (i) extraction of AE and CAN packets, (ii) normalization of the raw image data and compression using 2D DWT to generate the final image dataset, and (iii) intrusion detection and identification using the Swin Transformer deep learning algorithm. An overview of the proposed intrusion detection approach is outlined in
Figure 5.
Section 4.1 provides a brief overview of the dataset design and the experimental environment. Subsequently, the experimental results are presented, followed by a detailed analysis of the model’s performance based on comparative experiments.
3.1. Data Extraction
3.1.1. AE, CAN, and User Datagram Protocol (UDP) Message Formats
To enhance comprehension of the message traffic within the original dataset (comprising AE and UDP, where CAN messages were converted to UDP), the following presents a detailed description of the AE, CAN, and UDP message formats.
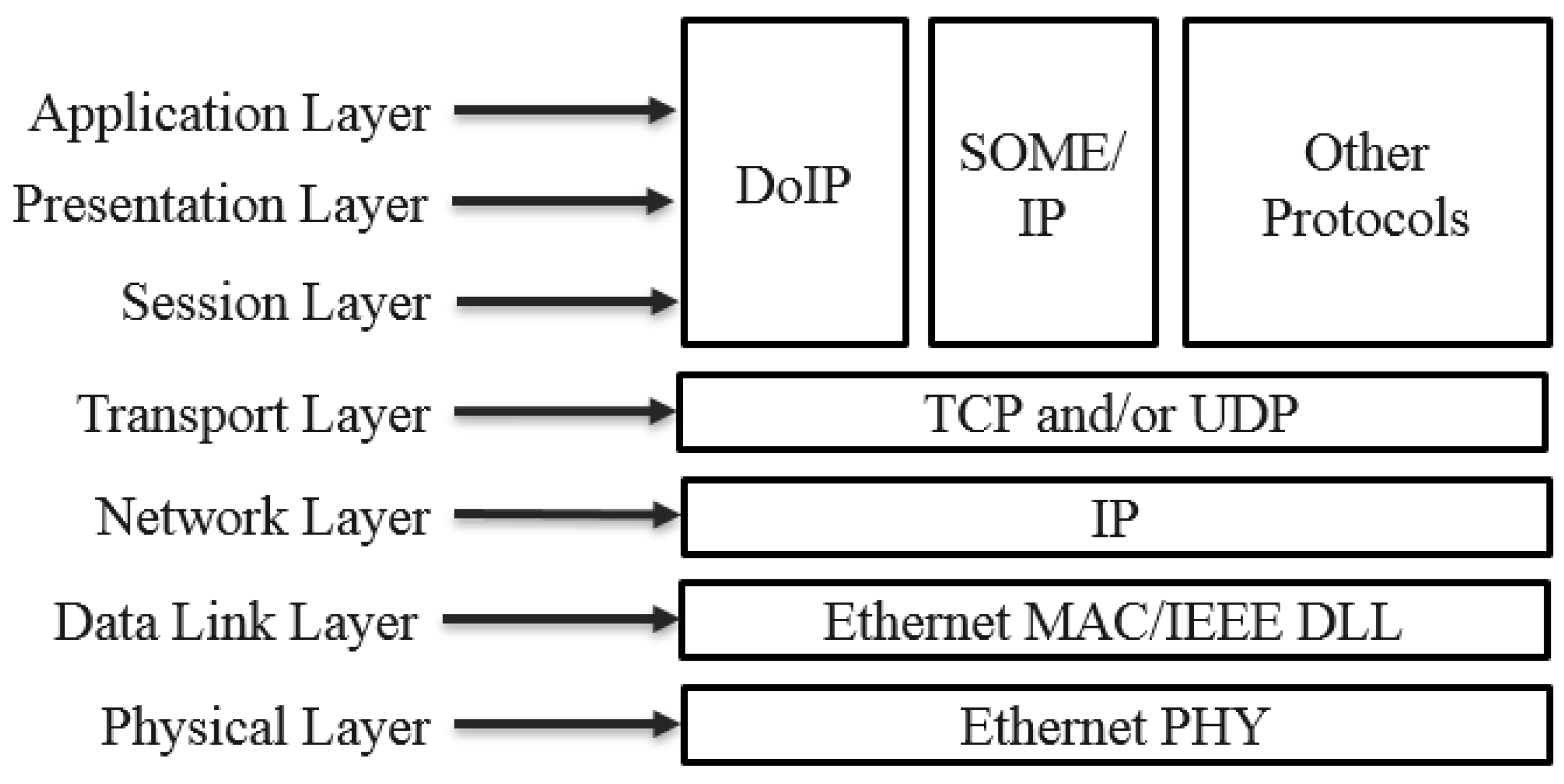
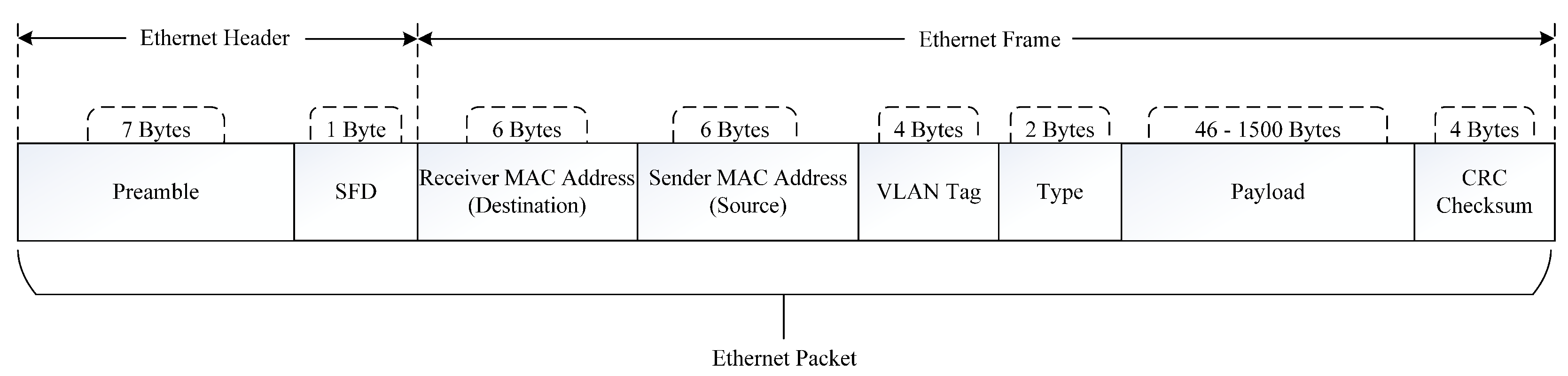
AE is based on the TCP/IP network model. When data are received at the application layer, they are assigned with a UDP header when passing through the transport layer, an IP header when passing through the network layer, and then MAC address and other information when passing through the data link layer. Finally, they are converted into a binary data stream by the physical chip to facilitate data interaction between the sender and the receiver. The complete structure of the AE packet is illustrated in
Figure 6.
The frame contains destination and source MAC addresses, each occupying 6 bytes. Additionally, the frame contains a VLAN tag to partition the LAN for virtual work data exchange. The VLAN tag occupies 4 bytes, to indicate priority and network segment information. The AE type of the frame occupies two bytes to specify the format used in the frame, which involved the AVTP (0x22F0) and gPTP (0x88F7) protocols in this study. The data segment comprises a UDP header, IP header, and data field, capable of occupying up to 1500 bytes at maximum and 46 bytes at minimum. Finally, the frame sequence detection occupies 4 bytes, to ensure the integrity of the frame during transmission.
In the CAN 2.0B protocol [
23], CAN messages are classified into four types: data frames, remote frames, error frames, and overload frames. Typically, data frames are utilized to transmit actual data. These frames are further divided into standard and extended frames, depending on the number of bits in the identifier used.
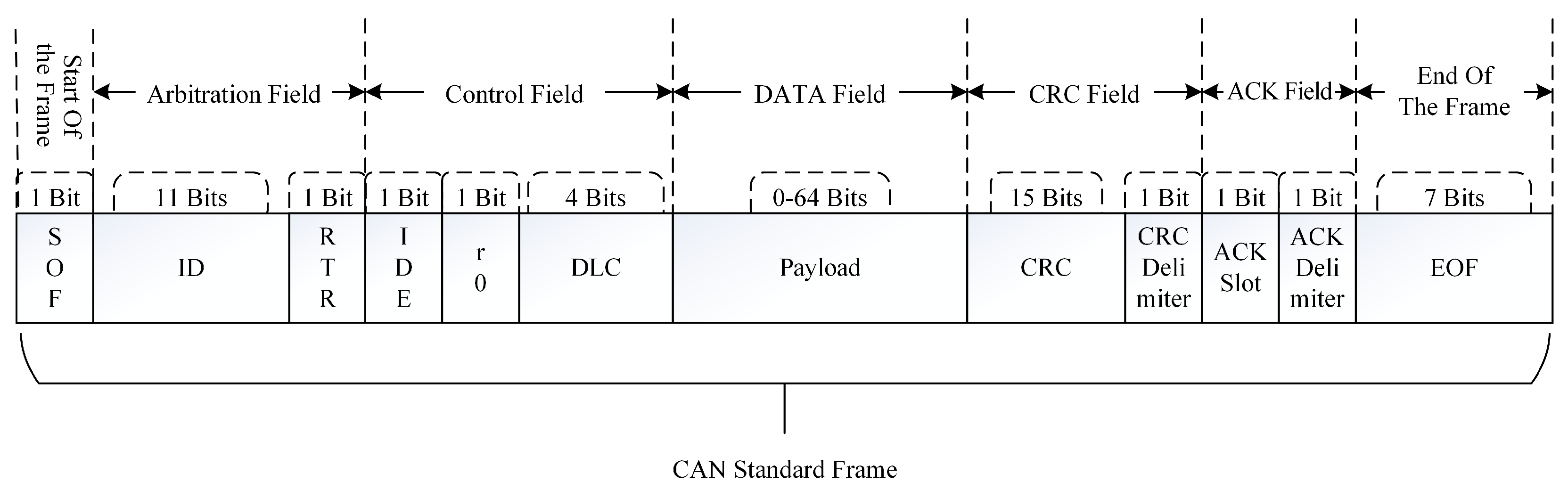
Figure 7 illustrates the CAN standard data frame format comprising seven key parts.
First, there is the 1-bit start of frame identifier (SOF), signaling the frame’s initiation. Following this is the 11-bit identifier (ID), where a smaller ID indicates a higher priority. The IDE bit determines whether the standard or extended frame format is employed; setting the IDE bit to 0 indicates usage of the extended frame format with a 29-bit ID. Additionally, there are 1-bit remote frame flags (RTRs), indicating if the frame is a remote frame, along with a 6-bit control field, a 64-bit data field, and a 16-bit cyclic redundancy check (CRC) field used for data integrity verification. Lastly, there is a 2-bit acknowledgment (ACK) field and a seven-bit end-of-frame character to signify the frame’s conclusion. Only standard frames are covered in this study.
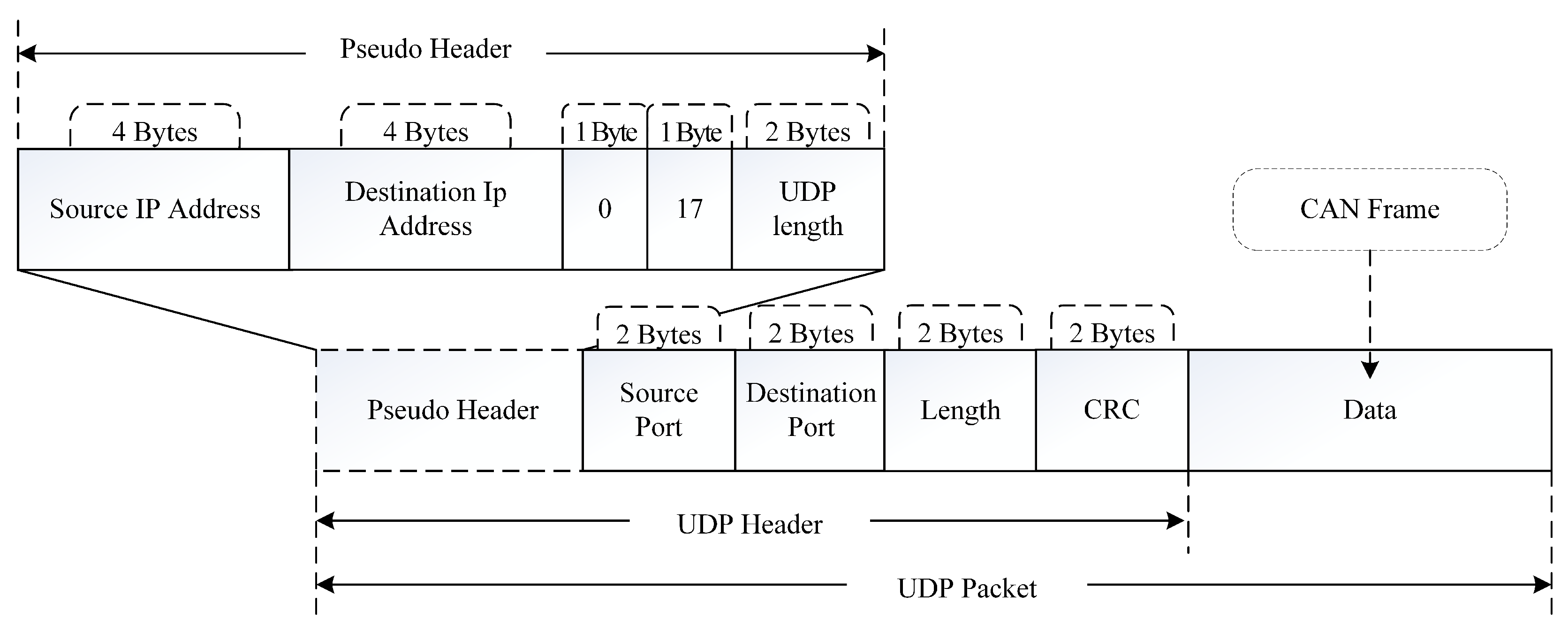
To enable the transmission of CAN messages over AE, Han and his team converted CAN to UDP. UDP provides basic services like multiplexing, splitting, and error detection atop the datagram services of IP. The complete format is illustrated in
Figure 8.
UDP datagrams consist of a header section and a user data section [
24]. The UDP header is 8 bytes in size, with the source and destination port number fields, the length field, and the checksum field each occupying 2 bytes. The data payload (CAN message) follows. When UDP checksum is required, a pseudo-header is appended before the UDP header, comprising 4 bytes of source IP address, 4 bytes of destination IP address, 1 byte of all zeros, 1 byte of protocol number, and finally 2 bytes of UDP length.
3.1.2. Introduction to the Dataset
The IDS utilizes an AE and CAN dataset comprising two pcap files (a file format for storing raw data packets transmitted across a network) for training and testing. Additionally, the dataset includes two csv files (a file format for storing tabular data in plain text form) assigning labels to each packet in the pcaps. Six labels denote various packet types: ‘normal’ (unattached), ‘P_I’ (PTP synchronization attack), ‘M_F’ (switch MAC flooding attack), ‘F_I’ (frame injection attack), ‘C_D’ (CAN DoS attack), and ‘C_R’ (CAN replay attack). We utilized the Wireshark parser pyshark and the packet grabber tshark, both packets encapsulated in Python, to grab and parse pacp files.
Table 1 outlines the packet distribution for each label in both datasets, with the training set containing 1,196,737 packets and the test set containing 791,611 packets.
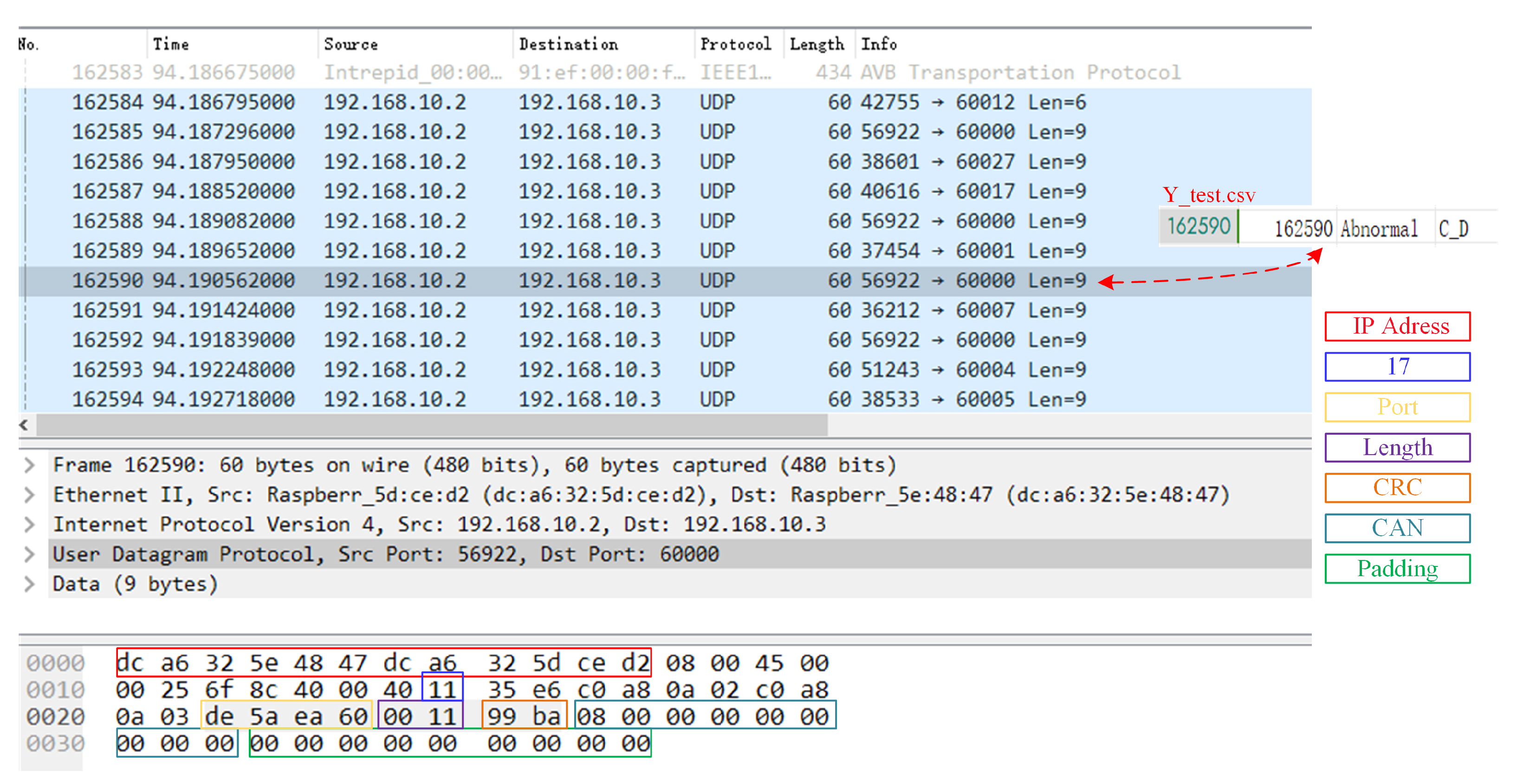
The content contained in the packet flow file is illustrated in
Figure 9. The CAN message numbered 162,590, highlighted in grey within the figure, was already represented in UDP format within the pcap file. This message is utilized as an illustrative example. The C_D attack message (annotated by the csv file) incorporates all the UDP content depicted in
Figure 8, alongside timestamp and additional information.
3.2. Data Pre-Processing
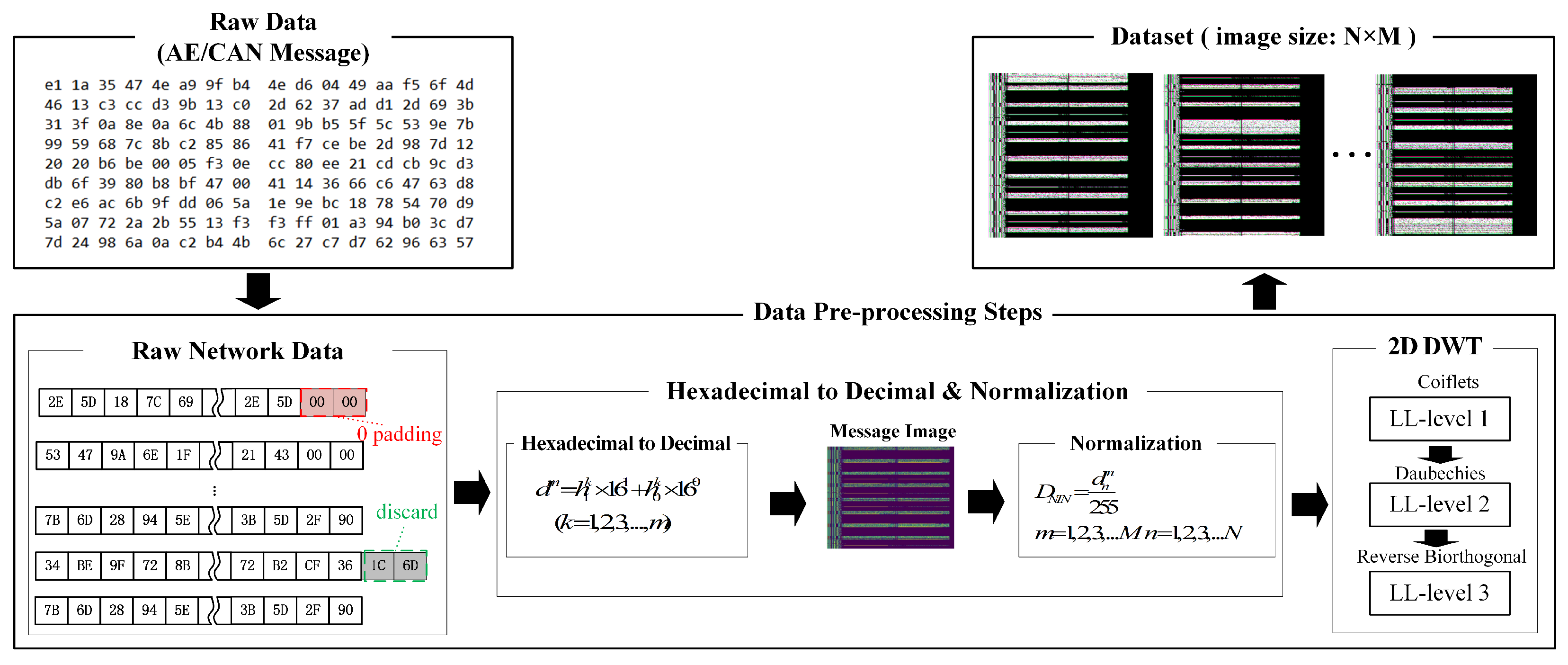
Each AE protocol carries data of varying lengths, such as AVTP with 434 bytes, gPTP with 60–90 bytes, and CAN-to-UDP packets with 60 bytes. To prepare the dataset for training the Swin Transformer model for intrusion detection, multiple images of size
N × M are generated from the network packets (raw data), where
N is the number of packets and
M is the packet length. If
M is smaller than the selected image width, padding with zeros is applied. Conversely, if
M exceeds the image width, excess bytes are discarded to match the image width. Subsequently, each byte in the packet is converted from hexadecimal to decimal notation to facilitate data processing and analysis using Equation (
1). After this step, the range of data values become 0–255, and then the
N decimal-number messages of length
M are formed into
N×M ×3 images, allowing the extraction of the original image data.
Since the value of each byte in the network packet ranges from 0 to 255, this continuous and wide-ranging data disparity may result in gradient explosion and vanishing problems during model training. Therefore, to enhance the data processing efficiency and alleviate this issue, the data converted to decimal values are normalized through linear transformation to constrain the data between 0 and 1. Equation (
2) illustrates the normalization process.
Finally, considering the real-time demands and computational constraints in automotive intrusion detection, we address the challenge posed by the large algorithm parameters and model sizes resulting from extensive input data. To manage this, we employ 2D DWT for image compression (as illustrated in [
16,
25,
26], the 2D DWT preserves the core information of the image more effectively than the 1D DWT and is more computationally resource-efficient than the continuous wavelet transform). This method effectively compresses data while preserving essential image information by decomposing the input image into four sub-bands: low–low (LL), low–high (LH), high–low (HL), and high–high (HH). LL approximates the input image at approximately 1/4 of its original size, while LH, HL, and HH capture horizontal, vertical, and diagonal features, respectively. To optimize computational resources, we utilize three different wavelet filters (level 1 decomposition: Coiflet 1, level 2 decomposition: Daubechies 3, level 3 decomposition: and Reverse biorthogonal 1.3). The LL sub-bands generated by these filters are combined to produce RGB images corresponding to the network packets, as illustrated in
Figure 10. These images serve as inputs to the Swin Transformer model during the training, validation, and testing phases of intrusion detection.
This preprocessing approach enhances the computational efficiency, while ensuring a robust representation of the input data, enabling the IDS to respond promptly and accurately to complex network traffic.
3.3. Model Architecture
In this study, we employ the Swin Transformer [
17] as the principal model for intrusion detection using image datasets derived from AE message traffic. Given the real-time demands and computational limitations inherent in the in-vehicle network environment, the structural attributes of the Swin Transformer are notably well-suited. The model refines the conventional Transformer by integrating a self-attention mechanism based on moving windows, which adeptly addresses global features in large-scale images, while also mitigating computational complexity.
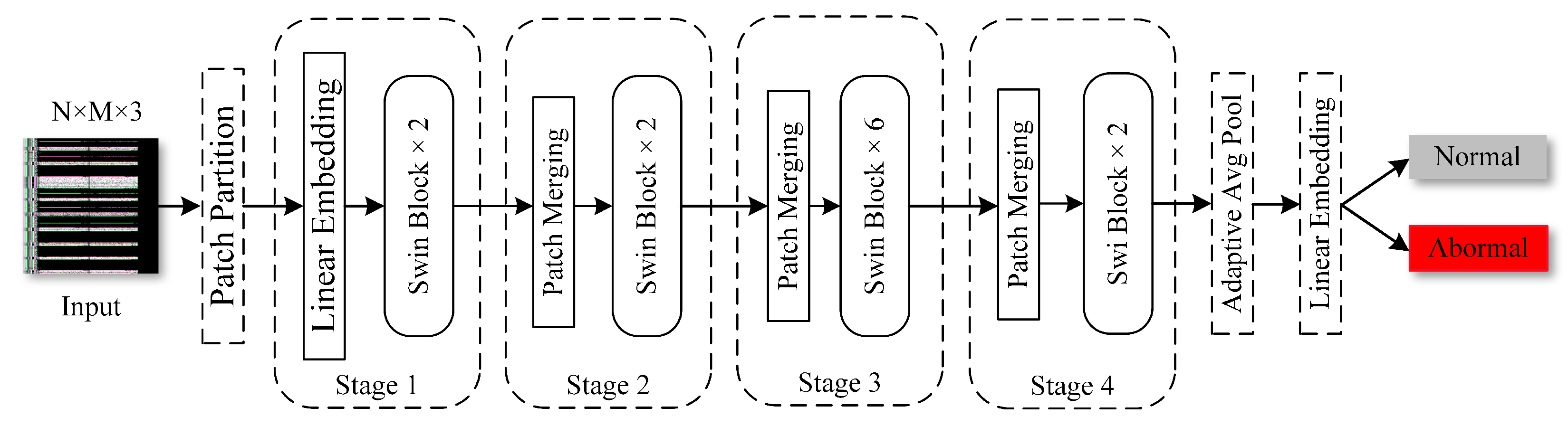
The Swin Transformer, illustrated in
Figure 11, showcases a sophisticated architecture, starting with a convolutional layer for the initial feature extraction. This is followed by a linear embedding layer, or fully connected layer, which prepares the data for the model’s core: multiple Swin Transformer blocks (Swin Blocks, in
Figure 12). Each Swin Block is engineered with four essential modules: layer normalization (LN) for input standardization; windowed multi-head self-attention (W-MSA) and its variant, shifted window multi-head self-attention (SW-MSA), for focused and comprehensive context gathering; and a multi-layer perceptron (MLP) for complex feature extraction. Patch merging further enhances the architecture, consolidating data and creating a global adaptive pooling layer that adapts to different input sizes.
In this study, we converted AE traffic messages into RGB images, serving as inputs to the Swin Transformer. This transformation encodes complex traffic data into a visual format, highlighting essential traffic features and potential anomaly patterns. The hierarchical structure of the Swin Transformer is particularly well suited to this data type because it filters out redundant features, while retaining critical information.
The model processing begins with the patch partition stage, where the input RGB image is divided into non-overlapping 16×16 blocks and flattened (patch_size is 16 in the program). The image proceeds through a linear embedding layer to stage 1, comprising two Swin Blocks for feature extraction and processing. The Swin Transformer iteratively enhances its understanding of the image across multiple stages, including patch merging and Swin Blocks. Each patch merging operation reduces spatial dimensions, while increasing the depth and refining and enriching the feature map.
In the final classification stage, the feature maps processed by Swin Transformer are classified through the full connectivity layer to determine whether the traffic is abnormal or not. This entire process not only improves the efficiency of the model in handling complex network traffic but also ensures that key features are effectively captured, thus enabling the IDS to respond quickly and accurately in the face of complex hybrid automotive in-vehicle network environments.
5. Conclusions
With the development of the concept of SDVs, the future design of an IDS with high accuracy, real-time performance, and reliability for hybrid vehicle in-vehicle networks is an ongoing research problem. In order to have a high level of reliability and safety in today’s automobiles, it is imperative to address the security threats to hybrid automotive in-vehicle networks consisting of AE and CANs. Currently, security research related to hybrid vehicle in-vehicle networks is in the preliminary stage. Most of the existing IDSs focus on detecting attack types of one protocol. In this study, we proposed a novel IDS to solve the problem of a high FPR, low real-time response, or low accuracy.The proposed method was based on the Swin Transformer, which focuses on three protocols: AVTP, gPTP, and UDP (CAN). In Step 1, N messages of length M in the packet are converted into an image, preserving its spatial features. In Step 2, to save time for model training and detection, the original image data are compressed using 2D DWT, which reduces the parameters and preserves the core information. Finally, the processed image is input into Swin Transformer for training and detection. To prove the advantages of this model in various aspects, we selected the classical network models ResNet18, VGG16, and Inception in image recognition and classification for comparison experiments. Our method demonstrated a high detection accuracy of 99.82% and a 0 false positive rate, F1 score, and recall rate of more than 99%. In addition, using 2D DWT compression resulted in significant time cost savings, reducing the response time for detecting 512 messages from 100.925 ms to 19.163 ms—a fivefold reduction. Notably, the experimental results of this study may have been limited by the characteristics of the used datasets and model parameters. Therefore, to better adapt to real-world application scenarios, future research needs to validate a wider range of datasets and further explore the optimization and light weight of model parameters. In addition, considering the continuous evolution of the network environment of autonomous vehicles, continuous research and updating of intrusion detection systems to adapt to new security threats and technological changes will also be an important direction for future work.