Abstract
Augmented reality (AR) is a virtual technology that integrates virtual information and objects into real environments, offering unprecedented possibilities in such fields such as architecture, education, and healthcare. Real-time communication and security protocols are critical to the successful deployment of AR applications to ensure user immersion, prevent motion sickness, and address security problems. This paper proposes a secure user-to-user (U2U) and user-to-infrastructure (U2I) authentication protocol suitable for edge computing-based AR environments. We also employ extended Chebyshev chaotic maps and physical unclonable functions to ensure security and efficiency during the authentication process. The proposed protocol initiates session keys after U2I authentication when an AR user enters the edge node area, facilitating secure U2U authentication for sharing data with nearby users. We conduct comprehensive studies of the security robustness of the proposed protocol using formal and informal analyses, including “Burrows–Abadi–Needham logic”, “Real-Or-Random model”, the “Scyther tool” and informal security analyses. Furthermore, we measure the performance of cryptographic primitives using the “Multiprecision Integer and Rational Arithmetic Cryptographic Library” Cryptographic SDK. We perform a comparative analysis of security features and functionality, and we conduct a computational and communication cost analysis. The results reveal that the proposed protocol can provide security and efficiency for edge computing-based AR environments, presenting the methods for seamless and secure real-time AR data exchanges for U2I and U2U communications.
1. Introduction
Augmented Reality (AR) is a computer graphics technology that overlays virtual information and objects in real environments. In contrast to traditional computer graphics, AR uses real-time data on the actual surrounding environments, including length, depth, texture, and distance. Furthermore, AR devices are equipped with high-pixel displays, eye and object-tracking systems, and sensitive cameras and sensors to process real-time information [1]. Figure 1 illustrates the simplification of AR data processing. Recently, various network environments have attempted to use AR technology with the development of mobile chipset and wireless communication technologies. For instance, Microsoft launched the HoloLens series, which can perform AR tasks, including architectural design, education, and healthcare [2]. HoloLens increases work efficiency by querying necessary data from industrial sites and using them as visual material.
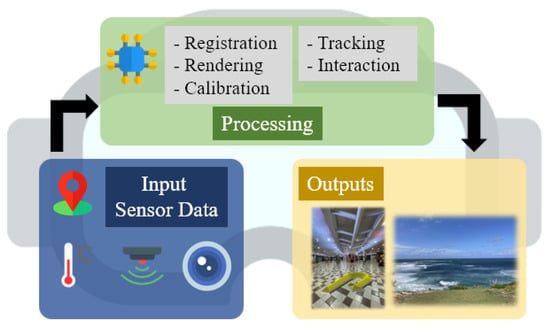
Figure 1.
Simplification of general AR data processing.
The implementation of real-time big data processing is necessary to ensure user immersion and prevent motion sickness in AR technology. Furthermore, the output of information with a higher pixel density (bit rate) than typical photographs and videos is essential. However, traditional cloud computing technology is burdened by high latency, and stand-alone technology demands high performance from end devices. Edge computing technology addresses this challenge by installing edge nodes at the network’s bottom, enabling efficient communication and performance in AR environments [3,4].
In edge computing-based AR environments, edge nodes provide similar visual information-based AR services to users within the area because of their locality. Furthermore, AR environments necessitate the real-time processing of substantial data compared to existing mobile computing environments [5]. Thus, edge computing-based AR environments still have a problem, potentially leading to frequent overloading on edge nodes, which is similar to traditional cloud-based mobile computing environments. The method of sharing AR content between users involves each user downloading necessary data from nearby users, bypassing the need for AR services from the edge node [6,7]. Through this approach, AR users can receive real-time data directly from nearby users, enabling the establishment of an efficient ad hoc network. Consequently, the overall operational efficiency can be enhanced because edge nodes do not need to carry the workload for all AR users employing user-to-user (U2U) communications.
The edge-computing-based AR content-sharing scheme can be subject to security problems because the communication channels of U2U and user-to-infrastructure (U2I) communications are public and wireless environments. If messages are hijacked, deleted, or captured by attackers, infringement of the user information can occur. Moreover, stolen or lost AR devices can threaten user privacy because they store sensitive information. If user information stored in an edge node is leaked, adversaries can use it to attempt a spoofing attack. In edge computing AR environments, edge nodes can be targeted to paralysis because they are regarded as local servers. Since user data in the AR environment are completely personalized data, untraceability and anonymity must be guaranteed. Nevertheless, the user’s identity must be verified in U2U and U2I communication while ensuring anonymity, and this process must be seamless and lightweight. Therefore, a secure authentication protocol is necessary for U2U and U2I communications. The security requirements and challenges for edge computing-based AR environments are as follows.
- Authentication: Mutual authentication is necessary to identify edge computing nodes and AR content users.
- Privacy preserving: Because the data that users use for AR services are based on personal information, resistance to privacy leaks is necessary.
- Anonymity and untraceability: Because the user’s AR device utilizes sensitive data and has mobility, it must provide anonymity and untraceability in U2U and U2I communications.
- Data access: Sophisticated data access is required because data are generated based on the user’s visual and auditory information in an edge computing-based AR environments.
- Latency: Since real-time communication is more important in the AR environment than in traditional environments, it must provide high performance while maintaining security.
In this paper, we propose a secure U2U and U2I authentication protocol for edge computing-based AR environments. The proposed protocol utilizes extended Chebyshev chaotic maps to ensure security and efficiency during the authentication process. After the user enters the edge node area through U2I authentication, a session key is created, and data are shared through U2U authentication with users who have adjacent AR content. Moreover, we use physical unclonable functions (PUFs) to guarantee the privacy of edge nodes. Therefore, AR users can receive seamless and secure real-time AR data from edge nodes and surrounding users.
1.1. Motivation
The edge computing-based AR environment has the characteristic of exchanging a huge amount of data compared to the traditional mobile networks. Since the exchanged data contain sensitive information of users, it can cause serious problem when these data are encrypted in low-level security. If a lot of computational resources are consumed for data masking, delays can occur due to low data response rates, which deteriorate service quality such as motion sickness. Based on the above motivations, we designed an authentication protocol to provide seamless U2I and U2U communications considering various security threats and efficiency for edge computing-based AR environments.
1.2. Contribution
The main contributions are as follows:
- We propose a secure and efficient authentication protocol for edge computing-based AR environments. The proposed protocol considers secure U2U and U2I communications for secure edge computing. Moreover, the proposed protocol can provide an efficient communication process using extended Chebyshev chaotic maps and PUFs.
- We analyze the security robustness of the proposed protocol using formal and informal analyses, such as “Burrows–Abadi–Needham (BAN) logic [8]”, “Real-Or-Random (ROR) model [9]” the “Scyther tool [10,11]”, and “informal security analysis”.
- We measure the performance of various cryptographic primitives using the “Multiprecision Integer and Rational Arithmetic Cryptographic Library (MIRACL) [12]” Cryptographic SDK. From that, we compare the security features and functionalities, and we conduct a computation and communication costs analysis of the proposed protocol and other related schemes.
2. Related Works
Edge computing-based AR environments have been being researched for a few years. In 2019, Ren et al. [13] introduced an architecture for AR environments based on edge computing technology. In Ren et al.’s AR architecture, cloud, edge, and user layers are constructed forming a hierarchy. Moreover, they present an operation mechanism to implement the edge computing-based AR technology. In 2021, Siriwardhana et al. [14] discussed AR technology that combines fifth-generation (5G) and edge computing. One of the main contributions in their paper is a division and analysis of AR environments, such as cloud, edge, localized, and hybrid-based architectures. They also discussed the requirements of security threats and solutions for AR environments. In the same year, Chen et al. [3] proposed an offloading scheme for AR edge computing environments. They considered a deep reinforcement learning model to obtain an optimized resource allocation. They demonstrated that their scheme could decrease the computation complexity and achieve a real-time offloading because this model does not consider combinatorial optimization. In 2022, Morín et al. [15] introduced a simplified AR offloading architecture using edge computing technology. Depending on the size and resource status of AR data, three AR offloading scenarios were introduced in their architecture: full, object detection and segmentation, and occlusion handling.
Recently, various service caching mechanisms have been proposed to address heavy computing tasks in AR environments. Dang et al. [16] proposed an on-device computational caching scheme for AR environments. In Dang et al.’s scheme, they presented a system model that can provide various AR services through computing caching-based device to device (D2D) communications. In their system model, D2D communication is activated when a user device cannot access an edge server due to overloading problems. In 2023, Park et al. [17] presented an object modeling system using collaborative communication for AR streaming services. In Park et al.’s modeling system, an AR user requests a part of segments from the edge computing node (ECN) and other nearby AR users to construct a complete three-dimensional (3D) virtual object. From that, the AR user can receive a decreased end-to-end delay and check the quality of the part-segments directly.
To provide secure communications between devices, D2D authentication schemes are introduced considering various network environments. In 2019, Chen et al. [18] proposed an authentication protocol for smart grid environments. Chen et al. considered communication channels between energy-trading consumers and constructed an U2U authentication protocol using bilinear pairings. Alzahrani et al. [19] introduced a two-party authentication scheme for the Internet of Vehicles. In their system model, various autonomous devices, including sensors, cameras, and smart vehicles, are registered to certificate authority. Then, the autonomous devices exchanges the authentication messages directly using the public key infrastructure. In 2021, Pham and Dang [20] proposed a lightweight D2D authentication protocol for the Internet of Things (IoT) environment using elliptic curve cryptography (ECC). In Phan and Dang’s protocol, a gateway participates in the authentication process to burden the computational overhead of ECC. In 2022, Hajian et al. [21] proposed a mutual authentication and key agreement protocol for D2D IoT deployments. In Hajian et al.’s protocol, IoT devices authenticate with each other using a direct communication link. Moreover, Hajian et al. used ECC to ensure a higher security than symmetric key-based cryptosystems. However, the above schemes [18,19,20,21] used ECC and bilinear pairings, which are unsuitable for U2U and U2I communications in edge computing-based AR environments. Moreover, several schemes used the main server as a certificate authority to complete D2D authentications, which can increase communication overhead. Because large volumes of data interact in real time in AR environments, designing computationally-efficient authentication protocols is essential. Thus, we propose a mutual authentication protocol using extended Chebyshev chaotic maps and PUFs to ensure a lightweight and secure scheme. Table 1 shows the summarized literature review of the related schemes and the proposed protocol.

Table 1.
Summary of the related schemes for D2D and U2U authentications.
3. Preliminaries
In this section, we introduce the backgrounds of the proposed protocol, such as the system model, adversary model, security model, extended Chebyshev chaotic maps, and PUFs.
3.1. System Model
The proposed system model consists of the AR cloud, edge computing nodes (ECNs), and AR users. Figure 2 presents the proposed system model and details as follows:
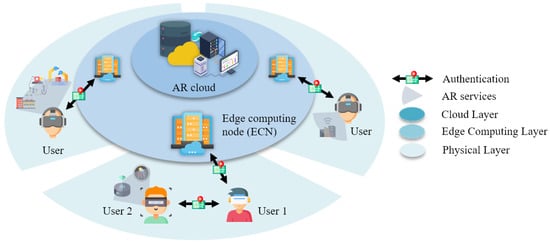
Figure 2.
Proposed edge computing-based AR environments.
- AR cloud:
- The AR cloud manages the proposed network system. Thus, the AR cloud registers ECN and AR users, and it stores their data in a secure database. The AR cloud has substantial data and computational resources.
- ECN:
- The ECN is a infrastructure that performs the tasks of the AR cloud. Thus, ECNs are deployed in specific areas to provide useful AR services to service users. The ECNs communicate with the AR cloud to receive and store AR user data in the edge cache [13]. The data can be distributed to the corresponding AR users to enable real-time services. In the proposed system model, ECNs have sufficient computation and storage resources.
- AR user:
- These users are end nodes that receive AR services using smart devices, including head-mounted display (HMD) devices. They interact with the corresponding infrastructure and users using wireless communication links. With the downloaded data, smart devices display the rendered information, and AR users can receive AR services. Thus, AR users register to the AR cloud and receive AR information from ECNs. Moreover, AR users can share their AR service data with other users (AR service user) when the ECN suffers from overloading problems.
3.2. Adversary Model
We adopt the well-known adversary model, “Dolev–Yao (DY)” [22] and “Canetti–Krawczyk (CK)” [23] network model. In the DY network model, network participants communicate with each other through public channels. Thus, adversaries can be concerned with the messages because adversaries have authority over public networks. The adversary can handle (e.g., eavesdrop, delete, insert, capture) messages transmitted via open channels. In the CK network model, the adversary can obtain short-term (e.g., ephemeral secret parameters) or long-term (e.g., master key) parameters. Thus, the adversary can try to calculate network participants’ sensitive information using ephemeral secret parameters or the master key of an AR cloud. The adversary also can obtain the legitimate AR user’s secret value using power analysis attacks [24]. Therefore, the adversary can conduct various security attacks as follows:
- The adversary can try to impersonate a legitimate user [25].
- The adversary can attempt to compute the session key using secret parameters [26].
- The adversary can try to reveal the real identity or the location information of the AR user [27].
- The adversary can conduct various security threats, including insider, replay, verification table leakage, and man-in-the-middle attacks [28].
3.3. Extended Chebyshev Chaotic Maps
The extended Chebyshev chaotic maps are a cryptosystem based on the Chebyshev polynomials [29]: . Note that , , , , and . Moreover, the extended Chebyshev chaotic maps can be described as the following equation: . Therefore, the extended Chebyshev chaotic maps have the property of being a semi-group.
The extended Chebyshev chaotic maps can be utilized as a cryptosystem using the following mathematical problems:
- Extended chaotic map-based discrete logarithm problem (ECMDLP): A problem to find an integer a when x and y are given (Equation: ).
- Extended chaotic map-based computational Diffie–Hellman (ECMCDH): A problem to calculate when and are given.
- Extended chaotic map-based decisional Diffie–Hellman (ECMDDH): A problem to decide when , , and are given.
3.4. Physical Unclonable Functions
PUFs are the technology that makes physical replication impossible. PUFs utilize differences in the microstructure of semiconductors produced in the same manufacturing process. Thus, the same PUF-based devices output different results when the same values are input. PUFs can be utilized as a fingerprint for various devices by creating a unique security key that cannot be physically copied. In this paper, we define an equation where R, , and C indicate response, PUF function, and challenge, respectively. We utilize PUF technology to preserve the security of the private key for ECNs.
3.5. Security Model
We introduce the security model of the proposed protocol for the ROR model [9]. The ROR model is a formal analysis to verify a secure session key agreement of the security protocol. We define the primitives which are used in the ROR model.
3.5.1. Participants
Participants are the network entities in the proposed protocol. Thus, we define , , and as AR user, ECN, and AR cloud, respectively. Note that () is the instance of the participants.
3.5.2. Partnering
If two instances have session identity and the values are the same, they become partners. In the proposed protocol, it can be considered as a partnering when and share unique values, such as .
3.5.3. Freshness
If the adversary is unable to reveal the session key and thus cannot distinguish between and random nonce, we consider instance to be fresh.
3.5.4. Adversary
In the ROR model, the adversary can capture, delete, hijack, and insert messages over the public channel. The adversary conducts the following queries with the above abilites.
- : The adversary can obtain the content of messages over the public channel.
- : The adversary actively transmits messages to a participant and receives the return message. This query can be considered as active attack.
- : The adversary reveals the secret values from the smart device of an AR user. This query can be considered as active attack.
- : When the adversary conducts this query, the adversary obtains a flipped unbiased coin f. If the flipped coin shows 1 (), it means that the adversary cannot distinguish the session key and random number. Thus, can be considered as fresh and secure. When the flipped coin shows 0 (), is not fresh. Otherwise, the result outputs value (⊥).
4. Proposed Protocol
We introduce the proposed protocol which is designed for edge computing-based AR environments. The proposed protocol consists of six phases: Initialization, ECN registration, AR user registration, U2I authentication, AR service user search, and U2U authentication phases. Table 2 presents the explanation for each notation.

Table 2.
Notations and descriptions.
4.1. Initialization Phase
The AR cloud selects its master key and a large prime number q. Then, the AR cloud selects for q. From that, the AR cloud computes its public key and picks a hash function . Finally, the AR cloud publishes to the network.
4.2. ECN Registration Phase
- MNR1:
- An ECN selects its identity and generates a random number . Then, the ECN computes and sends to the AR cloud via a secure channel.
- MNR2:
- The AR cloud checks the validity of and generates and . After that, the AR cloud computes and sends to the ECN through a secure channel.
- MNR3:
- The ECN computes , fuzzy extractor [30] , , and . Moreover, the ECN stores in its secure database and sends to the AR cloud.
- MNR4:
- The AR cloud computes and , and it stores in its secure database.
4.3. AR User Registration Phase
- AUR1:
- An AR user selects an identity and password . Then, the AR user generates and computes , , , and . The AR user sends to the AR cloud via a secure channel.
- AUR2:
- The AR cloud checks the identity of AR user and generates , . The AR cloud retrieves and from and , respectively. Then, the AR cloud computes , , , , , and . After that, the AR cloud stores , in its database and returns to the AR user through a secure channel.
- AUR3:
- The AR user computes , , , , and mod . Then, the AR user stores , in the memory.
4.4. U2I Authentication Phase
After the registration phase, the AR user enters the management region of ECN and sends an initial authentication request message to ECN. Then, the ECN and AR user perform a U2I authentication process. Figure 3 shows the U2I authentication phase, and the details are as follows.

Figure 3.
U2I authentication phase of the proposed scheme.
- U2I1:
- The AR user inputs and , and computes , , , , , , and mod . After checking , the AR user generates a random nonce and timestamp , and they compute , , , , and . The AR user generates an authentication request message and sends it to the ECN via an open channel.
- U2I2:
- The ECN first checks and computes , , , , , , , and . When the result of is correct, the ECN generates and and computes , , a session key , and . Then, the ECN sends to the AR user through an open channel.
- U2I3:
- The AR user checks and computes , , and . If , the session key is completely agreed.
4.5. AR Service User Search Phase
After the U2I authentication phase, the AR user requests AR data from the ECN. If the ECN has a lot of work or is overloaded, it transmits search results about nearby users who own AR service data. Details are as follows.
- AUS1:
- The AR user generates an AR request message and timestamp , and they compute , . Then, the AR user sends to the ECN.
- AUS2:
- After checking , the ECN decrypts and computes . If , the ECN searches a service user . Then, the ECN generates and computes , , and . Note that , , are the session key, pseudo-identity, and verification parameter for . Finally, the ECN sends to the AR user via an open channel.
- AUS3:
- The AR user checks and decrypts to obtain . The AR user computes and checks .
4.6. U2U Authentication Phase
The AR user broadcasts an authentication request message. The AR service user who owns AR data inspects this message and conducts the U2U authentication process. Figure 4 indicates the U2U authentication phase, and the details are as follows.
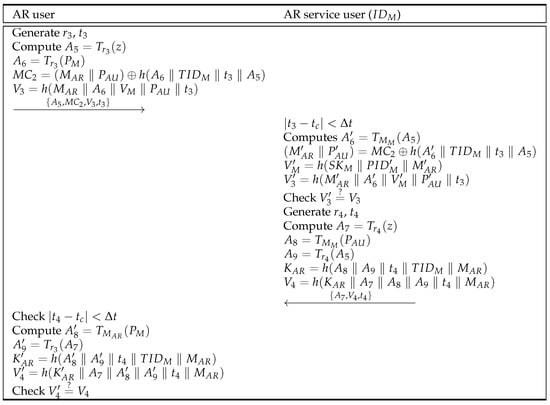
Figure 4.
U2U authentication phase of the proposed scheme.
- U2U1:
- The AR user generates , and computes , , , and . Then, the AR user sends to the AR service user .
- U2U2:
- The AR service user first checks and computes , , , and . If , the AR service user generates , and computes , , , , and . Then, the AR service user sends to the AR user via an open channel.
- U2U3:
- The AR user checks and computes , , , and . If , the U2U authentication phase is successful and the AR user receives the AR contents using the session key .
5. Security Analysis
To prove the security robustness of the proposed protocol, we conduct informal security analysis, using the Scyther tool, BAN logic, and the ROR model.
5.1. Informal Security Analysis
5.1.1. Replay and Man-in-the-Middle Attack
In our protocol, the network participants send messages with random numbers , , , and , and timestamps , , , and . Thus, network participants can check the freshness of messages. Although an adversary captures and sends a message from a previous session, the network participants can filter it using the timestamp and random nonce. Therefore, the proposed protocol can prevent replay and man-in-the-middle attacks.
5.1.2. AR User Impersonation Attack
Suppose that an adversary captures messages of a legitimate user and tries to impersonate the user. However, the messages transmitted through open channels are masked in the public key of AR user , so the adversary must obtain the private key . Moreover, the adversary cannot impersonate as the AR user without knowing the pseudo-identity . These parameters are encrypted in the AR user’s device with the identity and password. Thus, the proposed protocol is secure against impersonation attacks.
5.1.3. Privileged Insider Attack
If an adversary is a privileged insider in our proposed network system, the adversary can reveal and captures all of registration messages, including . Moreover, suppose that the adversary obtains secret parameters of the AR user . To calculate and decrypt these parameters, the adversary must guess the password of the AR user. However, our protocol utilizes fuzzy verifier , so the probability of guessing correct is . Therefore, the proposed protocol can prevent privileged insider attacks.
5.1.4. Verification Table Leakage Attack
Suppose that the adversary obtains the leaked-verification table and . From that, the adversary tries to reveal and attack the proposed network. However, the adversary cannot reveal any secret parameters without knowing the master key of AR cloud . Therefore, the proposed protocol can prevent verification table leakage attacks.
5.1.5. Ephemeral Secret Leakage Attack
If an adversary obtains the ephemeral secret parameters , , , and , the adversary tries to compute the session key and . To calculate the session key, the adversary must obtain , , , and . However, this task is infeasible according to the ECMCDH problem. Thus, the proposed protocol is secure against ESL attacks.
5.1.6. Anonymity
If AR users send their real identity , it can cause various security and privacy problems, including traceability. In our protocol, AR users use the temporary identities , which are used in a specific session. Thus, the adversary cannot distinguish and trace the AR user. Thus, the proposed protocol can ensure AR user anonymity.
5.1.7. Perfect Forward Secrecy
Suppose that an adversary obtains the master key and the public messages , , , , , and . However, the adversary cannot calculate the session key and because these parameters are composed of the secret parameters of AR users and ECNs, extended chaotic maps, and ephemeral secret parameters. Thus, the proposed protocol can guarantee perfect forward secrecy.
5.1.8. Mutual Authentication
In our protocol, all messages include timestamps , , , and , and network participants check the validity of them. If these processes are successful, the network participants decrypt messages and check the integrity using , , , and . When the integrity correctness process is complete, the mutual authentication is successful. Thus, the proposed protocol can ensure mutual authentication.
5.2. Scyther Tool
In this section, we simulate the security robustness of the proposed protocol using the Scyther tool. To simulate the proposed protocol, we first convert it into “Security Protocol Description Language (SPDL)”, which is the specific language for the Scyther tool. After that, the Scyther command-line tool verifies the security of the proposed protocol using various claim events. When the simulation is complete, we can obtain the result window which indicates the security robustness of the proposed protocol. If the result window shows “OK” in the “Status” tab and “No attacks” in the “Comment” tab, we can ensure that the proposed protocol has a secure authentication process. Table 3 shows the claim events and Figure 5 indicates the result window of the proposed protocol.

Table 3.
Scyther tool claim events.
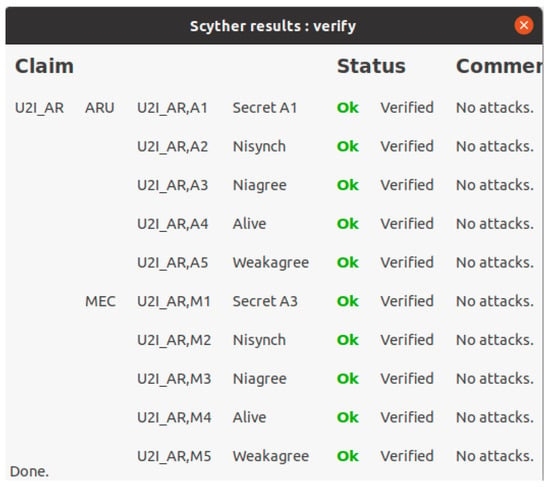
Figure 5.
Scyther result window of the proposed protocol.
5.3. BAN Logic
BAN logic [8] is a formal analysis method to prove the mutual authentication of the protocol. Thus, various security protocols analyzed the property of mutual authentication using BAN logic [31,32,33]. To analyze the proposed protocol using BAN logic, we define basic notations and descriptions in Table 4.

Table 4.
Basic notations and description.
5.3.1. Rules
In BAN logic, there are five rules. The details are outlined below.
- 1.
- Message meaning rule (MMR):
- 2.
- Nonce verification rule (NVR):
- 3.
- Jurisdiction rule (JR):
- 4.
- Belief rule (BR):
- 5.
- Freshness rule (FR):
5.3.2. Goals
In our protocol, a session key is established between the network participants during the authentication phase. Therefore, the goals in our protocol are as follows.
- Goal 1:
- Goal 2:
- Goal 3:
- Goal 4:
5.3.3. Idealized Forms
In our protocol, an AR user and ECN exchange and through open channels. Thus, we convert these messages into idealized forms.
- IF 1:
- IF 2:
5.3.4. Assumptions
In our protocol, assumptions are as follows.
Assumption A1.
.
Assumption A2.
.
Assumption A3.
.
Assumption A4.
.
5.3.5. BAN Logic Analysis
- Step 1:
- From , we can obtain .
- Step 2:
- We can obtain utilizing the message meaning rule and Assumption 3.
- Step 3:
- We can obtain utilizing the freshness rule and Assumption 1.
- Step 4:
- We can obtain utilizing the nonce verification rule, , and .
- Step 5:
- From , we can obtain .
- Step 6:
- We can obtain utilizing the message meaning rule and Assumption 4.
- Step 7:
- We can obtain utilizing the freshness rule and Assumption 2.
- Step 8:
- We can obtain utilizing the nonce verification rule, , and .
- Step 9:
- In our protocol, and establish the session key . Thus, we use and to obtain and .
- Step 10:
- We can obtain and using , , and the jurisdiction rule.
5.4. ROR Model
In this section, we analyze the session key security of the proposed protocol using the ROR model [9]. We utlize the security model in Section 3.5 and follow the security proof of [34,35,36] which proved the session key security using the ROR model.
Theorem 1.
In the ROR model, the adversary tries to reveal the session key in polynomial time. Thus, let be the probability that the session key security is broken in polynomial time. We also define , , , and as hash function ’s range space, the number of hash queries, the function ’s range space, the number of PUF queries, and probability to break the ECMDDH problem. and are the Zipf’s parameters [37].
We perform six games () to prove the security of the session key in our proposed protocol. In each game , the winning probability of the adversary and the advantage is and , respectively.
- : It is a stating game where the adversary has no information about the session key. Thus, the adversary selects a random bit. Thus, the relationship between and can be expressed as follows.
- : In this game, the adversary collects messages transmitted over public channels using the query. Thus, the adversary obtains , , , and . With this information, the adversary tries to reveal the session key and . After that, the adversary conducts a query to distinguish the session key and random number. However, the adversary cannot guess a successful session key because each parameter in the message is masked in various security parameters, including , , and . Thus, we obtain the following equation.
- : The adversary performs and hash queries. However, the adversary cannot have an advantage in this game because all of security parameters are masked in cryptographic one-way hash functions, which has resistance against hash collision problems. Using birthday paradox [38], we can obtain the following inequation.
- : In this game, the adversary performs and PUF queries. As we mentioned in Section 3.4, the adversary cannot have an advantage because PUF is an anti-duplicated microstructure. Thus, we can obtain the inequation similar to (4).
- : The adversary tries to reveal the session key calculating , , , and . However, the adversary must solve the ECMDDH problem to find random numbers , , , and . However, this process is not possible in polynomial time. Thus, we obtain the following inequation.
- : This is the final game that the adversary conducts, using the query. With the revealed parameters from the AR user’s smart device, the adversary tries to guess the session key. However, the adversary cannot reveal the real identity and password of the AR user because the verification parameter is processed under fuzzy verifier . Thus, the adversary cannot guess and simultaneously. As a result, we obtain the following inequation using Zipf’s law [37].
When all the games are finished, the adversary guesses a random bit.
Using the triangular inequality, we obtain the following:
At last, we obtain the following inequation multiplying (11) by 2. Thus, we can prove Theorem 1.
6. Performance Analysis
In this section, we conduct comparative studies about computational, communicational, and security features. To estimate the performance of the proposed protocol, we utilize the MIRACL testbed. We compare the performance result of the proposed protocol and the other related schemes [18,19,20,21] which are proposed for U2U and U2I authentication schemes.
6.1. Execution Time of Cryptographic Primitives Using MIRACL
The MIRACL is a C/C++ language-based cryptographic SDK that facilitates the development of cryptographic schemes. There are built-in libraries for various cryptographic primitives, including ECC, bilinear pairings, hash functions, and symmetric encryptions. Thus, we measure the execution time of each primitive using MIRACL in the desktop (11th Generation Intel(R) Core(TM) i5-11400 @ 2.60 GHz with 24.0 GB RAM) and Raspberry-PI 4 (Broadcom BCM2711, Quad core Cortex-A72 (ARM v8) 64-bit System on Chip @ 1.8 GHz, with 8 GB RAM) testbed environments. We measured the execution time for each cryptographic primitive 100 times. We defined the ECC multiplication, ECC addition, hash function, AES encryption, AES decryption, modular exponentiation, and bilinear pairing as , , , , , , and , respectively. Table 5 and Table 6 show the performance results for the max, min, and the average time for each primitive using MIRACL. The testbed results show that the desktop platform has much better performance compared to Raspberry-PI 4. Thus, we apply the desktop and Raspberry-PI 4 platform to infrastructure and user devices, respectively.

Table 5.
Performance results on the desktop platform using MIRACL.

Table 6.
Performance results in Raspberry-PI 4 platform using MIRACL.
6.2. Comparison of Computational Cost
We compare the computational cost of the proposed protocol and the related schemes [18,19,20,21]. The computational cost of , , , , , , and can be denoted as ms, ms, ms, ms, ms, ms, and ms according to Table 5, and ms, ms, ms, ms, ms, ms, and ms according to Table 6. Note that the computational cost of extended Chebyshev chaotic maps is one-third of [39] ( ms in a desktop and ms in the Raspberry-PI platform). In addition, the computational cost of fuzzy extractor is similar to . The results of computational cost analysis are shown in Table 7. Thus, the proposed protocol can provide a more lightweight authentication process than the related schemes [18,19,20,21].

Table 7.
Comparison of computational cost.
6.3. Comparison of Communcational Cost
We conduct a comparatvie study of computational cost among the proposed protocol and the related schemes [18,19,20,21]. According to [40], we define that the real identity, hash function, timestamp, ECC operation, Chebyshev polynomial, and elements in group and are 64 bits, 160 bits, 32 bits, 320 bits, 256 bits, 1024 bits, and 1024 bits, respectively. The result of communicational cost comparison is shown in Table 8. The result shows that the proposed protocol has a lower communicational overhead than the related schemes [18,19,20,21].

Table 8.
Comparison of communcational cost.
6.4. Security Features
Table 9 presents the security and functionality features of the proposed protocol and the related schemes [18,19,20,21]. We define (SEC1: Replay attacks), (SEC2: Man-in-the-middle attacks), (SEC3: Impersonation attacks), (SEC4: Privileged insider attacks), (SEC5: ESL attacks), (SEC6: Verification table leakage attacks), (SEC7: Anonymity), (SEC8: Perfect forward secrecy), and (SEC9: Mutual authentication), respectively. Therefore, the proposed protocol can provide a robust secure and lightweight communication for edge computing-based AR environments.

Table 9.
Security and functionality features comparison.
7. Conclusions
In this paper, we proposed an authentication protocol for edge computing-based AR environments. The proposed protocol consists of U2I and U2U authentication processes considering the workload of edge nodes. Moreover, the proposed protocol can provide secure and lightweight authentication services using Chebyshev chaotic maps and PUFs. We performed various security analyses, such as the Scyther tool, BAN logic, and informal security analysis. Moreover, we conducted comparative performance analysis using MIRACL, proving the computational and communicational lightweightness against the related schemes. Thus, the proposed protocol is suitable for edge computing AR environments, and users can share AR data using a robust secure communication channel. In future work, we will implement a practical AR environment and design an improved scheme to make secure and seamless AR services.
Author Contributions
Conceptualization, D.K.; methodology, D.K.; software, D.K.; validation, D.K. and Y.P.; formal analysis, D.K.; writing—original draft preparation, D.K.; writing—review and editing, Y.P.; supervision, Y.P.; project administration, Y.P. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by the National Research Foundation of Korea (NRF) funded by the Ministry of Education under grant 2020R1I1A3058605.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Ren, P.; Qiao, X.; Huang, Y.; Liu, L.; Dustdar, S.; Chen, J. Edge-assisted distributed DNN collaborative computing approach for mobile web augmented reality in 5G networks. IEEE Netw. 2020, 34, 254–261. [Google Scholar] [CrossRef]
- Gsaxner, C.; Li, J.; Pepe, A.; Jin, Y.; Kleesiek, J.; Schmalstieg, D.; Egger, J. The HoloLens in medicine: A systematic review and taxonomy. Med. Image Anal. 2023, 85, 102757–102785. [Google Scholar] [CrossRef] [PubMed]
- Chen, M.; Liu, W.; Wang, T.; Liu, A.; Zeng, Z. Edge intelligence computing for mobile augmented reality with deep reinforcement learning approach. Comput. Netw. 2021, 195, 108186. [Google Scholar] [CrossRef]
- Salman, S.M.; Sitompul, T.A.; Papadopoulos, A.V.; Nolte, T. Fog computing for augmented reality: Trends, challenges and opportunities. In Proceedings of the 2020 IEEE International Conference on Fog Computing (ICFC), Sydney, NSW, Australia, 21–24 April 2020; pp. 56–63. [Google Scholar]
- Hossain, M.D.; Huynh, L.N.; Sultana, T.; Nguyen, T.D.; Park, J.H.; Hong, C.S.; Huh, E.N. Collaborative task offloading for overloaded mobile edge computing in small-cell networks. In Proceedings of the 2020 International Conference on Information Networking (ICOIN), Barcelona, Spain, 7–10 January 2020; pp. 717–722. [Google Scholar]
- Apicharttrisorn, K.; Chen, J.; Sekar, V.; Rowe, A.; Krishnamurthy, S.V. Breaking edge shackles: Infrastructure-free collaborative mobile augmented reality. In Proceedings of the 20th ACM Conference on Embedded Networked Sensor Systems, Boston, MA, USA, 6–9 November 2022; pp. 1–15. [Google Scholar]
- Ren, P.; Qiao, X.; Huang, Y.; Liu, L.; Pu, C.; Dustdar, S.; Chen, J. Edge ar x5: An edge-assisted multi-user collaborative framework for mobile web augmented reality in 5g and beyond. IEEE Trans. Cloud Comput. 2020, 10, 2521–2537. [Google Scholar] [CrossRef]
- Burrows, M.; Abadi, M.; Needham, R. A logic of authentication. ACM Trans. Comput. Syst. (TOCS) 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Abdalla, M.; Fouque, P.; Pointcheval, D. Password-based authenticated key exchange in the three-party setting. In Public Key Cryptography—PKC 2005, Proceedings of the 8th International Workshop on Theory and Practice in Public Key Cryptography, Les Diablerets, Switzerland, 23–26 January 2005; Lecture Notes in Computer Science (LNCS); Springer: Berlin/Heidelberg, Germany, 2005; pp. 65–84. [Google Scholar]
- Cremers, C.J. The Scyther Tool: Verification, Falsification, and Analysis of Security Protocols: Tool Paper. In Proceedings of the International Conference on Computer Aided Verification, Princeton, NJ, USA, 7–14 July 2008; pp. 414–418. [Google Scholar]
- Scyther Tool. Available online: https://people.cispa.io/cas.cremers/scyther/ (accessed on 27 December 2023).
- MIRACL Cryptographic SDK. Available online: https://github.com/miracl/MIRACL (accessed on 27 December 2023).
- Ren, J.; He, Y.; Huang, G.; Yu, G.; Cai, Y.; Zhang, Z. An edge-computing based architecture for mobile augmented reality. IEEE Netw. 2019, 33, 162–169. [Google Scholar] [CrossRef]
- Siriwardhana, Y.; Porambage, P.; Liyanage, M.; Ylianttila, M. A survey on mobile augmented reality with 5G mobile edge computing: Architectures, applications, and technical aspects. IEEE Commun. Surv. Tutor. 2021, 23, 1160–1192. [Google Scholar] [CrossRef]
- Morín, D.G.; Pérez, P.; Armada, A.G. Toward the distributed implementation of immersive augmented reality architectures on 5G networks. IEEE Commun. Mag. 2022, 60, 46–52. [Google Scholar] [CrossRef]
- Dang, T.N.; Kim, K.; Khan, L.U.; Kazmi, S.A.; Han, Z.; Hong, C.S. On-device computational caching-enabled augmented reality for 5G and beyond: A contract-theory-based incentive mechanism. IEEE Internet Things J. 2021, 8, 17382–17394. [Google Scholar] [CrossRef]
- Park, G.S.; Kim, R.; Song, H. Collaborative virtual 3D object modeling for mobile augmented reality streaming services over 5G networks. IEEE Trans. Mob. Comput. 2022, 22, 3855–3869. [Google Scholar] [CrossRef]
- Chen, Y.; Martínez, J.F.; Castillejo, P.; López, L. A bilinear map pairing based authentication scheme for smart grid communications: Pauth. IEEE Access 2019, 7, 22633–22643. [Google Scholar] [CrossRef]
- Alzahrani, B.A.; Chaudhry, S.A.; Barnawi, A.; Al-Barakati, A.; Shon, T. An anonymous device to device authentication protocol using ECC and self certified public keys usable in Internet of Things based autonomous devices. Electronics 2020, 9, 520. [Google Scholar] [CrossRef]
- Pham, C.D.; Dang, T.K. A lightweight authentication protocol for D2D-enabled IoT systems with privacy. Pervasive Mob. Comput. 2021, 74, 101399. [Google Scholar] [CrossRef]
- Hajian, R.; Haghighat, A.; Erfani, S.H. A secure anonymous D2D mutual authentication and key agreement protocol for IoT. Internet Things 2022, 18, 100493. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Universally composable notions of key exchange and secure channels. In Advances in Cryptology—EUROCRYPT 2002, Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Amsterdam, The Netherlands, 28 April–2 May 2002; Springer: Berlin/Heidelberg, Germany, 2002; pp. 337–351. [Google Scholar]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Advances in Cryptology—CRYPTO’99, Proceedings of the 19th Annual International Cryptology Conference, Santa Barbara, CA, USA, 15–19 August 1999; Springer: Berlin/Heidelberg, Germany, 1999; pp. 388–397. [Google Scholar]
- Son, S.; Lee, J.; Park, Y.; Park, Y.; Das, A.K. Design of blockchain-based lightweight V2I handover authentication protocol for VANET. IEEE Trans. Netw. Sci. Eng. 2022, 9, 1346–1358. [Google Scholar] [CrossRef]
- Oh, J.; Kim, M.; Park, Y.; Park, Y. A Secure Content Trading for Cross-Platform in the Metaverse with Blockchain and Searchable Encryption. IEEE Access 2023, 11, 120680–120693. [Google Scholar] [CrossRef]
- Park, Y.; Ryu, D.; Kwon, D.; Park, Y. Provably secure mutual authentication and key agreement scheme using PUF in internet of drones deployments. Sensors 2023, 23, 2034. [Google Scholar] [CrossRef]
- Kwon, D.; Son, S.; Park, Y.; Kim, H.; Park, Y.; Lee, S.; Jeon, Y. Design of secure handover authentication scheme for urban air mobility environments. IEEE Access 2022, 10, 42529–42541. [Google Scholar] [CrossRef]
- Hsieh, Y.P.; Lee, K.C.; Lee, T.F.; Su, G.J. Extended chaotic-map-based user authentication and key agreement for HIPAA privacy/security regulations. Appl. Sci. 2022, 12, 5701. [Google Scholar] [CrossRef]
- Dodis, Y.; Reyzin, L.; Smith, A. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. In Advances in Cryptology-EUROCRYPT 2004, Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 2–6 May 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 523–540. [Google Scholar]
- Son, S.; Kwon, D.; Lee, S.; Jeon, Y.; Das, A.K.; Park, Y. Design of Secure and Lightweight Authentication Scheme for UAV-Enabled Intelligent Transportation Systems using Blockchain and PUF. IEEE Access 2023, 11, 60240–60253. [Google Scholar] [CrossRef]
- Cho, Y.; Oh, J.; Kwon, D.; Son, S.; Lee, J.; Park, Y. A secure and anonymous user authentication scheme for IoT-enabled smart home environments using PUF. IEEE Access 2022, 10, 101330–101346. [Google Scholar] [CrossRef]
- Kwon, D.K.; Yu, S.J.; Lee, J.Y.; Son, S.H.; Park, Y.H. WSN-SLAP: Secure and lightweight mutual authentication protocol for wireless sensor networks. Sensors 2021, 21, 936. [Google Scholar] [CrossRef] [PubMed]
- Majumder, S.; Ray, S.; Sadhukhan, D.; Dasgupta, M.; Das, A.K.; Park, Y. ECC-EXONUM-eVOTING: A Novel Signature-Based e-Voting Scheme Using Blockchain and Zero Knowledge Property. IEEE Open J. Commun. Soc. 2023, 5, 583–598. [Google Scholar] [CrossRef]
- Son, S.; Oh, J.; Kwon, D.; Kim, M.; Park, K.; Park, Y. A Privacy-Preserving Authentication Scheme for a Blockchain-Based Energy Trading System. Mathematics 2023, 11, 4653. [Google Scholar] [CrossRef]
- Park, K.; Lee, J.; Das, A.K.; Park, Y. BPPS: Blockchain-enabled privacy-preserving scheme for demand-response management in smart grid environments. IEEE Trans. Dependable Secur. Comput. 2022, 20, 1719–1729. [Google Scholar] [CrossRef]
- Wang, D.; Cheng, H.; Wang, P.; Huang, X.; Jian, G. Zipf’s law in passwords. IEEE Trans. Inf. Forensics Secur. 2017, 12, 2776–2791. [Google Scholar] [CrossRef]
- Boyko, V.; MacKenzie, P.; Patel, S. Provably secure password-authenticated key exchange using Diffie-Hellman. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Bruges, Belgium, 14–18 May 2000; pp. 156–171. [Google Scholar]
- Abbasinezhad-Mood, D.; Ostad-Sharif, A.; Mazinani, S.M.; Nikooghadam, M. Provably secure escrow-less Chebyshev chaotic map-based key agreement protocol for vehicle to grid connections with privacy protection. IEEE Trans. Ind. Inform. 2020, 16, 7287–7294. [Google Scholar] [CrossRef]
- Zhang, L.; Zhu, Y.; Ren, W.; Wang, Y.; Choo, K.K.R.; Xiong, N.N. An energy-efficient authentication scheme based on Chebyshev chaotic map for smart grid environments. IEEE Internet Things J. 2021, 8, 17120–17130. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).