An Efficient Reduction of Timer Interrupts for Model Checking of Embedded Assembly Programs
Abstract
1. Introduction
2. Related Works
3. IHER
- Detect dependencies between IHs.Step 1 is performed when two or more IHs exist. IH depend on each other if any of the following conditions are true (access here means both writing and reading):
- One IH enables or disables the other IH;
- One IH writes to a memory location accessed by the other IH;
- One IH writes to the memory location used in an atomic proposition (AP).
Examples of APs include a variable being equal to a certain value. An IH that manipulates the memory location of an AP manipulates the core of the program. It is therefore necessarily associated with all IHs. In other words, only one IH is mentioned, and if one IH writes the memory location used by the AP, then all IHs are dependent on each other. - Detect dependencies between program locations and IHs.Step 2 shows the conditions under which two labels, the label and the label, are attached to locations to detect dependencies between the program and the IH. An label allows the execution of an IH after the execution of the program instruction. On the other hand, the label denotes that there exists a dependency between that program location and an IH, and therefore this IH needs to be executed before the instruction at that location is executed. In determining the label, we assume that program location k is a direct predecessor of program location l. Let program location k be a direct predecessor of program location l. Formally, for each , l is labeled with if one of the following conditions is satisfied:
- k enables or disables i;
- k writes a memory location that i accessed;
- k writes a memory location that is used in an AP.
Also, for each IH, a program location l is labeled with if one of the following conditions is satisfied.- i writes a memory location that l accesses;
- l enables or disables i;
- l writes a memory location that i accesses;
- l writes a memory location that is used in an AP.
- Refine results.Step 3 performs refinement on the label. Each label is moved until one of the following conditions is satisfied.
- A program location labeled with is reached;
- A loop entry is found;
- A loop exit is found.
- Label blocking locations.In the last step, all program node positions are labeled IH. At this point, IH, and we assign a label to any location without an label.
4. Formal Model of an Assembly Program
- -
- L is a set of program locations;
- -
- L, and is the initial location of the program;
- -
- O is a finite set of instructions in the main program (non-interrupt);
- -
- I is a finite set of executions of interrupt handlers;
- -
- T indicates execution times such as the OT and IT of each instruction in O and I at each program location;
- -
- →⊆ is the set of transition relations.
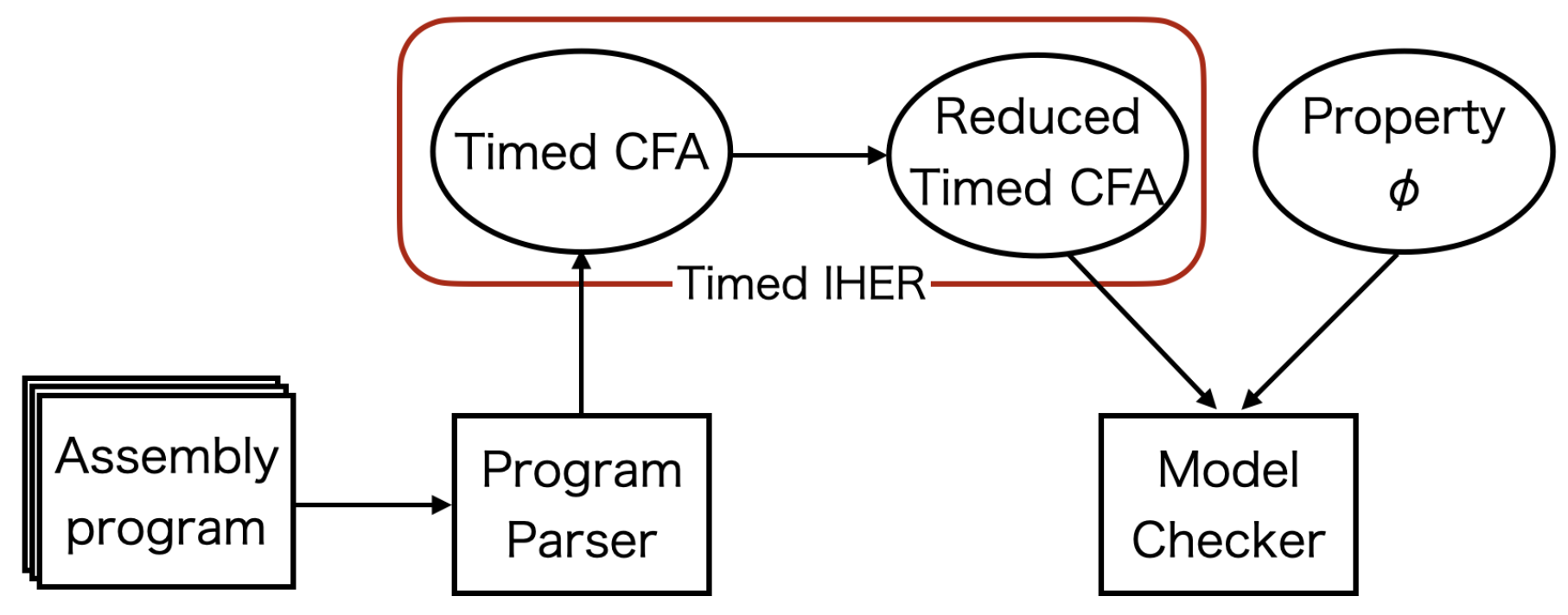
5. Proposed Method of Timed IHER
5.1. Verification System
5.2. Algorithm
| Algorithm 1 Timed IHER |
| Require: Timed CFA |
| Ensure: Reduced Timed CFA |
|
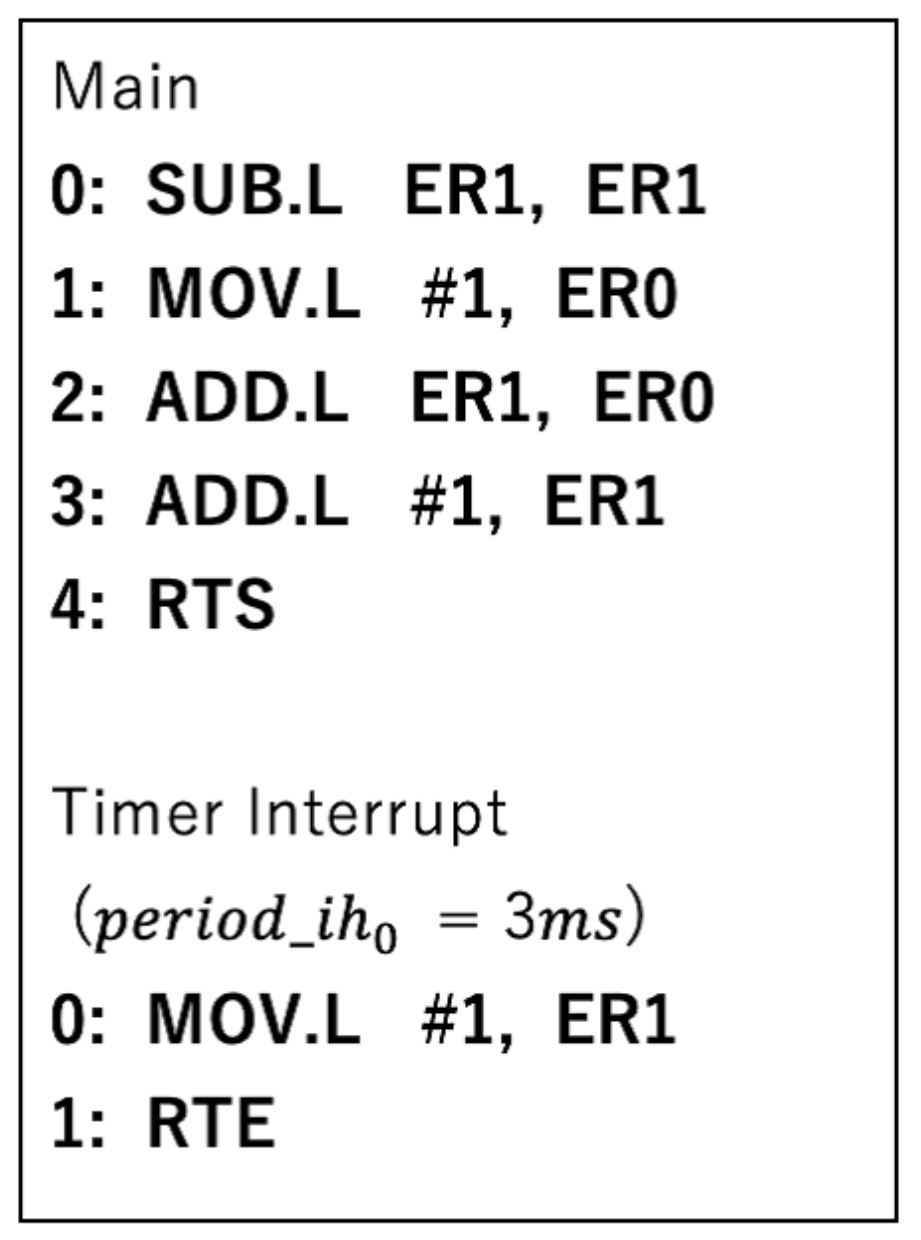
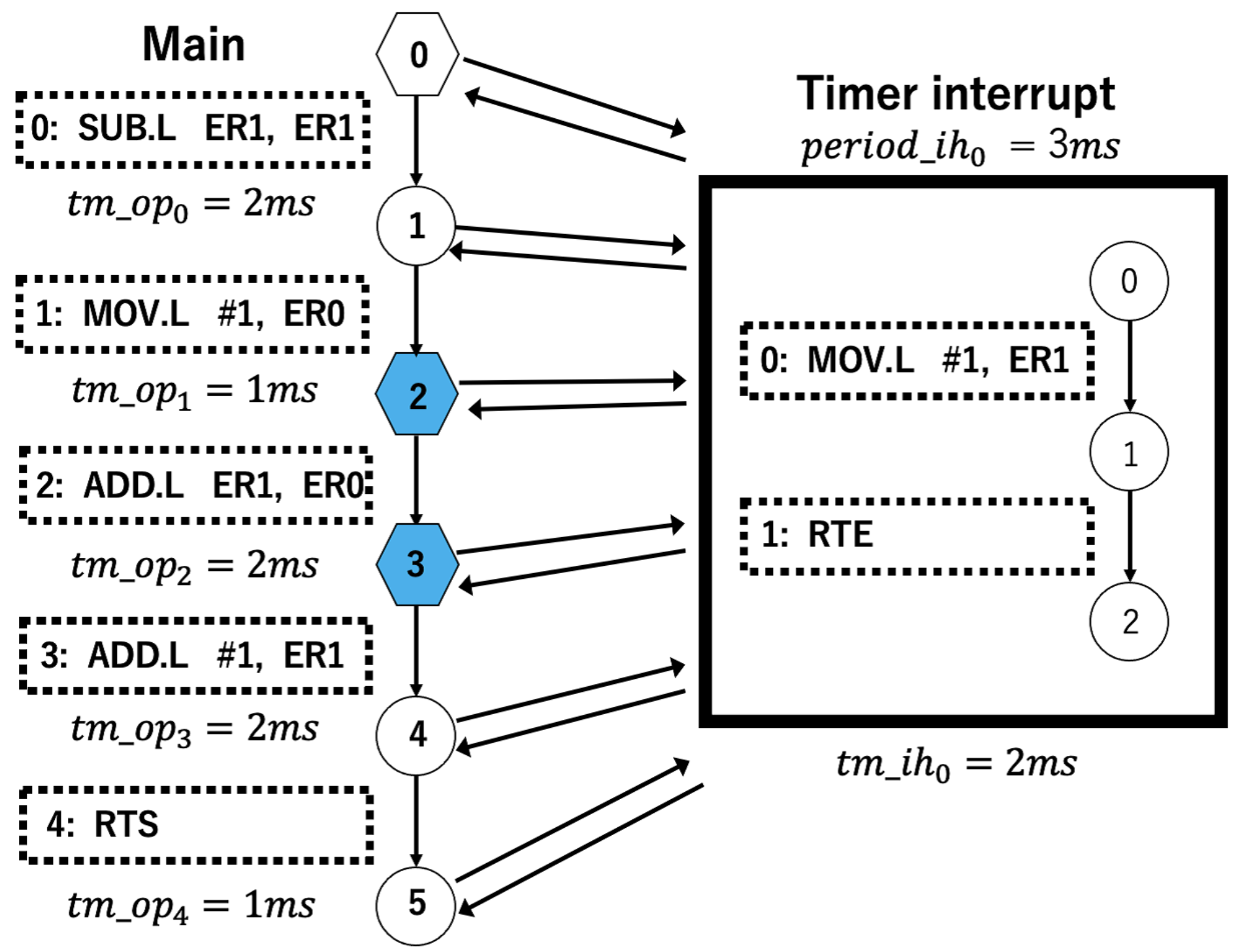
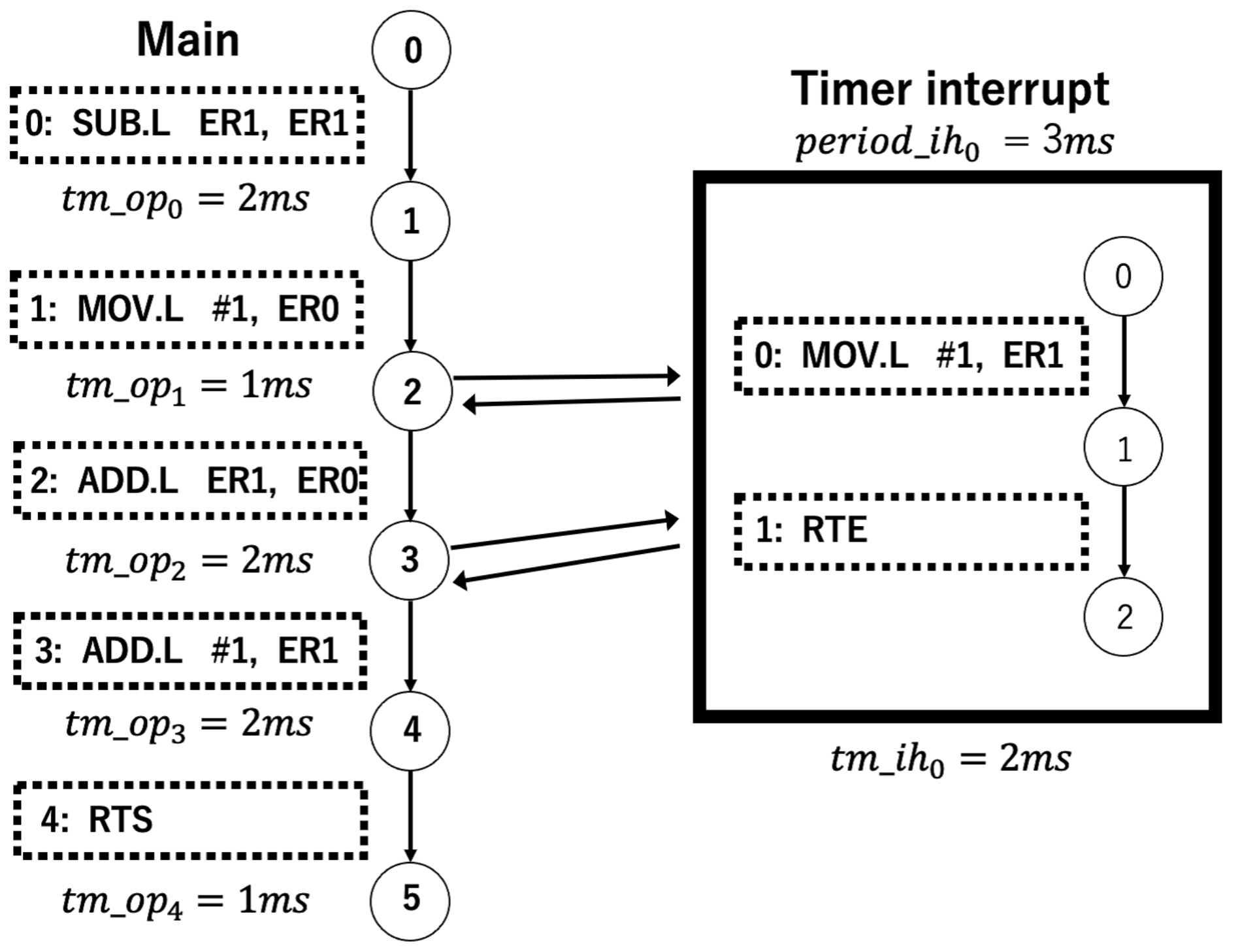
5.3. Example
5.4. Computational Analysis and Partial Correctness of Algorithm 1
5.4.1. Computational Analysis of Algorithm 1
- Step 1.Let be the number of locations in the interrupt handler . The time complexity is .
- Step 2:j is the number of nodes, and is the number of instructions in . Also, is the number of interrupts. The time complexity is .
- Step 3:The time complexity is .
- Step 4:The time complexity is .
5.4.2. Partial Correctness of Algorithm 1
- The correctness of the theory of timed IHER.We establish the correctness of our timed IHER by showing that the original timed CFA G and the reduced timed CFA are equivalent. According to the reference [3], we can show the correctness of the time interrupt reduction by defining the semantics of a timed CFA using a labeled transition system. Only a summary of the correctness is given below. We define the labeled transition system of a timed CFA G and the labeled transition system of a reduced timed CFA by timed IHER. We can establish the correctness of our timed IHER by showing that the original timed CFA G and the reduced timed CFA are equivalent. More concretely, we can show that the original timed CFA G and the reduced timed CFA are related by divergence-sensitive stutter bisimulation [15,25].
- The correctness of the algorithm of timed IHER.We show that the reduced timed CFA resulting from timed IHER is correctly constructed by our algorithm. The fundamental idea of Schlich’s IHER is to reduce the number of normal IH executions by blocking normal HIs at program locations where there is no dependency between certain normal HIs and the program [3]. Also, the fundamental idea of our proposed timed IHER is to reduce the number of timer IH executions by blocking timer HIs at program locations where there is no dependency between certain timer HIs and the program. In order to realize timed IHER, we deal with the execution time of the program. For reasons of space limitation, this section will focus on the key points such as step 2 and step 3 of the algorithm:
- a
- Step 2.The execution time is calculated and the label is determined. First, in order to calculate the execution time, the outermost loop denoted by “FOR of ” adds up the execution times of the instructions. Next, the inner loop denoted by “FOR interrupts” depends on whether timer interrupts or normal interrupts are used as follows:
- a-1
- Timer interrupts.If the same conditions as for the label are satisfied, the label is applied to the node, the execution time of the interrupt process is added to all , and is assigned through division by . If does not exceed , the current timer time is stored in for use in step 3, is assigned by subtracting , and the label is applied. Also, if the same conditions for the label are satisfied, then the node should be labeled .
- a-2
- Normal interrupts. We label locations with and according to [3].
- b
- Step 3.The outermost loop denoted by “FOR of ” refines the and labels. The label is moved until reaching the label, i.e., the entrance or exit of the loop. The label is moved until reaching the label, i.e., the entrance or exit of the loop.
- c
- Step 4.As locations without or labels do not affect the execution and can be reduced, the label is applied to block interrupts at these locations.
6. Experiment
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Clarke, E.M.; Grumberg, O.; Peled, D. Model Checking; The MIT Press: Cambridge, MA, USA, 1999. [Google Scholar]
- Schlich, B.; Kowalewski, S. Model checking C source code for embedded systems. Int. J. Softw. Tools Technol. Transf. 2009, 11, 187–202. [Google Scholar] [CrossRef]
- Schlich, B.; Thomas, N.; Brauer, J.; Brutschy, L. Reduction of interrupt handler executions for model checking embedded software. In Proceedings of the Haifa Verification Conference, Haifa, Israel, 19–22 October 2009; Springer: Berlin/Heidelberg, Germany, 2009; pp. 5–20. [Google Scholar]
- Schlich, B. Model Checking of Software for Microcontrollers. ACM Trans. Embed. Comput. Syst. 2010, 9, 1–27. [Google Scholar] [CrossRef]
- Yamane, S.; Konoshita, R.; Kato, T. Model checking of embedded assembly program based on simulation. IEICE Trans. Inf. Syst. 2017, 100, 1819–1826. [Google Scholar] [CrossRef]
- Schlich, B.; Brauer, J.; Kowalewski, S. Application of static analyses for state-space reduction to the microcontroller binary code. Sci. Comput. Program 2011, 76, 100–118. [Google Scholar] [CrossRef][Green Version]
- Armando, A.; Mantovani, J.; Platania, L. Bounded model checking of software using SMT solvers instead of SAT solvers. Int. J. Softw. Tools Technol. Transf. 2009, 11, 69–83. [Google Scholar] [CrossRef]
- Yamane, S.; Kobashi, J.; Uemura, K. Verification Method of Safety Properties of Embedded Assembly Program by Combining SMT-Based Bounded Model Checking and Reduction of Interrupt Handler Executions. Electronics 2020, 9, 1060. [Google Scholar] [CrossRef]
- Kuo, M.; Sinha, M.; Roop, P. Efficient WCRT analysis of synchronous programs using reachability. In Proceedings of the 48th Design Automation Conference (DAC ’11), San Diego, CA, USA, 5–10 June 2011; Association for Computing Machinery: New York, NY, USA, 2011; pp. 480–485. [Google Scholar]
- Wu, Y.; Yamane, S. Model Checking of Real-Time Properties for Embedded Assembly Program Using Real-Time Temporal Logic RTCTL and Its Application to Real Microcontroller Software. IEICE Trans. Inf. Syst. 2020, 103, 800–812. [Google Scholar] [CrossRef]
- Alur, R.; Dill, D. The theory of timed automata. In Proceedings of the Real-Time: Theory in Practice: REX Workshop Mook, 1991 Proceedings, Mook, The Netherlands, 3–7 June 1991; Springer: Berlin/Heidelberg, Germany, 1992. [Google Scholar]
- Kiriyama, T.; Wu, Y.; Yamane, S. Reduction of Timer Interrupts for Embedded Assembly Programs Based on Reduction of Interrupt Handler Executions. In Proceedings of the 2021 IEEE 10th Global Conference on Consumer Electronics (GCCE), Kyoto, Japan, 12–15 October 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 464–466. [Google Scholar]
- Liang, L.; Melham, T.; Kroening, D.; Schrammel, P. Tautschnig, M. Effective Verification for Low-Level Software with Competing Interrupts. ACM Trans. Embed. Comput. Syst. 2018, 17, 36:1–36:26. [Google Scholar] [CrossRef]
- Peled, D. Ten years of partial order reduction. In Proceedings of the CAV 1998, LNCS, Vancouver, BC, Canada, 28 June–2 July 1998; Hu, A.J., Vardi, M.Y., Eds.; Springer: Berlin/Heidelberg, Germany, 1998; Volume 1427, pp. 17–28. [Google Scholar]
- Browne, M.C.; Clarke, E.M.; Grumberg, O. Characterizing Finite Kripke Structures in Propositional Temporal Logic. Theor. Comput. Sci. 1988, 59, 115–131. [Google Scholar] [CrossRef]
- Beyer, D.; Henzinger, T.A.; Jhala, R.; Majumdar, R. The software model checker blast. Int. J. Softw. Tools Technol. Transf. 2007, 9, 505–525. [Google Scholar] [CrossRef]
- Muchnick, S. Advanced Compiler Design and Implementation; Morgan Kaufmann Publishers Inc.: Burlington, MA, USA, 1997. [Google Scholar]
- Aho, A.V.; Sethi, R.; Ullman, J.D. Compilers: Principles, Techniques and Tools, 2nd ed.; Pearson: London, UK, 2006. [Google Scholar]
- Toth, T.; Majzik, I. Formal Modeling of Real-Time Systems with Data Processing. In Proceedings of the 23rd PhD Mini-Symposium; Pataki, B., Ed.; Budapest University of Technology and Economics: Budapest, Hungary, 2016; pp. 46–49. [Google Scholar]
- Ermedahl, A.; Engblom, J. Execution Time Analysis for Embedded Real-Time Systems. In Handbook of Real-Time and Embedded Systems; CRC Press: Boca Raton, FL, USA, 2007. [Google Scholar]
- Hou, G.; Kong, W.; Zhou, K.; Wang, J.; Cao, X.; Fukuda, A. Analysis of Interrupt Behavior Based on Probabilistic Model Checking. In Proceedings of the 2018 7th International Congress on Advanced Applied Informatics (IIAI-AAI), Yonago, Japan, 8–13 July 2018; pp. 86–91. [Google Scholar]
- Corporation, R.E. Renesas Electronics, Renesas Electronics Corporation (Online). Available online: http://japan.renesas.com/ (accessed on 12 October 2019).
- JFlex—The Fast Scanner Generator for Java. 2015. Available online: http://jflex.de/ (accessed on 11 March 2023).
- BYACC/J Java Extension. 2013. Available online: http://byaccj.sourceforge.net/ (accessed on 3 September 2022).
- van Glabbeek, R.; Weijland, W. Branching time and abstraction in bisimulation semantics. J. ACM 1996, 43, 555–600. [Google Scholar] [CrossRef]
- ZMP Inc. Nuvo R WHEEL. 2010. Available online: https://robot.watch.impress.co.jp/cda/news/2006/07/12/81.html (accessed on 3 September 2022).


| OS | macOS Monterey 12.4 |
| CPU | Intel(R) Core(TM) i5-8257U CPU @ 1.40 GHz |
| Memory | 8 GB |
| Java | 11.0.4 |
| Program | 12,000 lines |
| Case | TI | SI | Without | Without | Reduction | ||
|---|---|---|---|---|---|---|---|
| Timed | Timed | Timed | Timed | ||||
| IHER | IHER | IHER | IHER | ||||
| (Required | (Execution | (Required | (Execution | ||||
| Memory (kb)) | Time (s)) | Memory (kb)) | Time (s)) | ||||
| 1 | 2 | 0 | 117,448 | 1889.6 | 7134 | 997.2 | 94% |
| 2 | 1 | 158,747 | 2125.8 | 8049 | 1075.2 | 95% | |
| 2 | 1 | 1 | 20,260 | 304.3 | 8624 | 280.4 | 57% |
| 2 | 0 | 26,324 | 253.8 | 10,520 | 131 | 60% | |
| 3 | 2 | 0 | 2,160,677 | 45,032.7 | 204,433 | 25,032.7 | 91% |
| 2 | 1 | 2,528,550 | 52,042 | 573,202 | 32,051.3 | 77% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yamane, S.; Kriyama, T.; Wu, Y. An Efficient Reduction of Timer Interrupts for Model Checking of Embedded Assembly Programs. Electronics 2024, 13, 463. https://doi.org/10.3390/electronics13020463
Yamane S, Kriyama T, Wu Y. An Efficient Reduction of Timer Interrupts for Model Checking of Embedded Assembly Programs. Electronics. 2024; 13(2):463. https://doi.org/10.3390/electronics13020463
Chicago/Turabian StyleYamane, Satoshi, Taro Kriyama, and Yajun Wu. 2024. "An Efficient Reduction of Timer Interrupts for Model Checking of Embedded Assembly Programs" Electronics 13, no. 2: 463. https://doi.org/10.3390/electronics13020463
APA StyleYamane, S., Kriyama, T., & Wu, Y. (2024). An Efficient Reduction of Timer Interrupts for Model Checking of Embedded Assembly Programs. Electronics, 13(2), 463. https://doi.org/10.3390/electronics13020463






