Cybersecurity in Autonomous Vehicles—Are We Ready for the Challenge?
Abstract
1. Introduction
2. The Methodology of the Literature Search
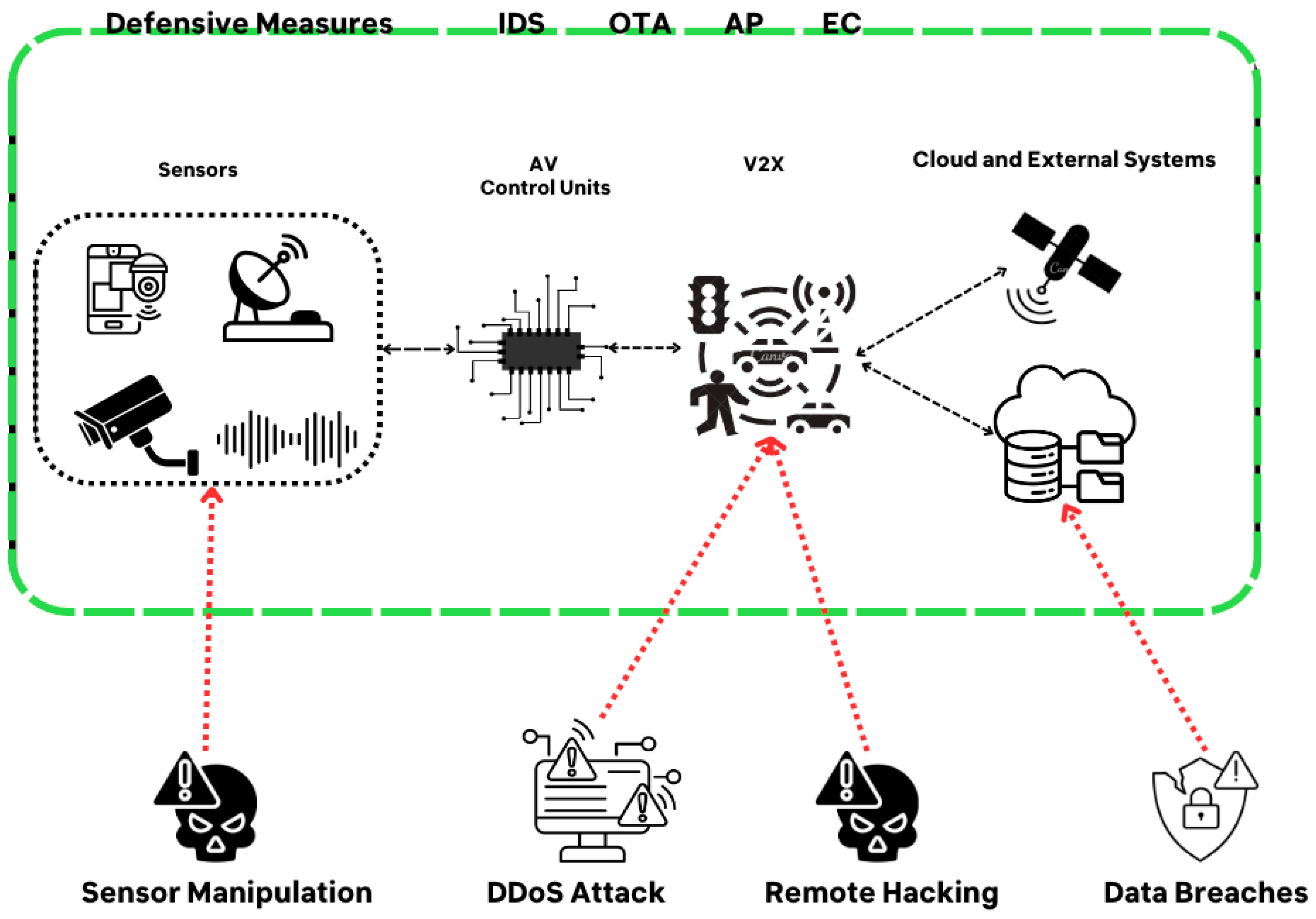
3. Threat Landscape
3.1. Remote Hacking
3.2. Sensor Manipulation
3.3. Data Breaches
- Encryption—Employing strong encryption protocols for data both at rest and in transit to prevent unauthorized access [45].
- Authentication and Access Control—Implementing stringent authentication mechanisms and access control policies to ensure that only authorized personnel and systems can access sensitive data [46].
- Intrusion Detection Systems (IDSs)—Deploying advanced IDSs to monitor network traffic and detect suspicious activities that may indicate a breach attempt [47].
- Regular Security Audits—Conducting regular security audits and penetration testing to identify and address potential vulnerabilities in the AV systems [48].
- Data Anonymization—Anonymizing personal data where possible to minimize the impact of any potential data breach on individual privacy [49].
3.4. Denial of Service (DoS) Attacks
- Redundancy and Failover Mechanisms—Implementing redundant communication channels and computational resources can help ensure that the vehicle remains operational even if one pathway is compromised. Failover mechanisms can automatically switch to backup systems in the event of an attack [57].
- Traffic Filtering and Rate Limiting—Utilizing advanced traffic filtering techniques and rate limiting can help prevent network saturation by identifying and blocking malicious traffic patterns [58].
- Anomaly Detection System—Deploying anomaly detection systems that monitor network traffic and system behavior in real time can help identify and mitigate DoS attacks before they cause significant disruption. These systems can use machine learning algorithms to recognize unusual patterns indicative of an attack [59].
- Resource Management—Implementing efficient resource management protocols can ensure that critical systems have the necessary computational power and bandwidth to function correctly, even under attack conditions [60].
- Regular Security Updates—Ensuring that all software components are regularly updated and patched to fix known vulnerabilities can reduce the risk of exploitation by DoS attacks [61].
- In 2015, researchers Charlie Miller and Chris Valasek demonstrated a remote hack of a Jeep Cherokee, where they gained control over the vehicle’s critical functions such as braking and acceleration through its infotainment system.
- In 2016, researchers at the University of South Carolina successfully deceived a Tesla Model S’s autopilot system by projecting images that mimicked lane markings, causing the vehicle to veer off its path.
- In 2020, a cybersecurity firm revealed that hackers could exploit vulnerabilities in the backend servers of several electric vehicle manufacturers, potentially gaining access to user data and vehicle control systems.
4. Existing Countermeasures
4.1. Intrusion Detection Systems (IDSs)
- Network-based IDSs (NIDSs)—These systems monitor traffic between devices within the vehicle’s network and between the vehicle and external networks. By analyzing network packets in real time, NIDSs can detect intrusions that attempt to exploit vulnerabilities in communication protocols or launch denial of service attacks. They can also monitor data exchanges between the vehicle and cloud services, ensuring the integrity and security of transmitted data [70,73].
- Host-based IDSs (HIDSs)—These systems focus on monitoring activities on individual devices or endpoints within the vehicle, such as control units, sensors, and onboard computers. HIDSs can detect suspicious activities at the device level, such as unauthorized changes to system files, unusual process behavior, and attempts to execute malicious code. By providing detailed visibility into the internal operations of each device, HIDSs complement the broader network monitoring capabilities of NIDSs [74].
4.2. Encryption
- Preventing Eavesdropping—Encryption ensures that data transmitted between the AV and external systems (such as traffic management servers, other vehicles, and cloud services) are unintelligible to unauthorized entities. This prevents eavesdroppers from intercepting and understanding sensitive information, such as the vehicle’s location or destination [64,86,87].
- Preventing Data Breaches—In the event of unauthorized access to the vehicle’s data storage systems, encryption ensures that the compromised data remain unusable without the decryption keys. This protects sensitive information, including passenger details and driving patterns, from being exposed and misused [88,89].
- Maintaining Data Integrity—Encryption helps prevent tampering with the data by ensuring that any unauthorized modifications can be detected. For instance, if an attacker attempts to alter navigation instructions or sensor data, the encryption process will detect these changes, alerting the system to the potential breach [33,42].
- Key Management—Securely managing encryption keys is critical to maintaining the effectiveness of encryption. This involves generating strong keys, securely storing them, and regularly updating them to prevent unauthorized access [90].
- End-to-End Encryption—Employing end-to-end encryption ensures that data remain encrypted throughout their entire journey, from the point of origin to the final destination. This approach minimizes the risk of data exposure at intermediate points [91].
- Regular Audits—Conducting regular security audits and assessments helps identify potential weaknesses in the encryption implementation and ensures compliance with the latest security standards [45].
- Layered Security—Encryption should be part of a multi-layered security approach, complemented by other measures such as authentication, intrusion detection systems, and access control to provide comprehensive protection [25].
4.3. Regular Updates
- Addressing Vulnerabilities: As cybersecurity researchers and malicious actors continuously discover new vulnerabilities, it is imperative to patch these weaknesses as quickly as possible. OTA updates allow for the rapid deployment of fixes, reducing the window of opportunity for attackers to exploit these vulnerabilities [23].
- Enhancing Security Features: Regular updates can introduce new security features and improvements, thereby enhancing the overall security posture of the AV. These updates might include advanced encryption methods, improved intrusion detection algorithms, and more robust authentication protocols [72].
- Bug Fixes: Beyond security vulnerabilities, regular updates address software bugs that could potentially be exploited by attackers or cause system malfunctions. By fixing these bugs, manufacturers ensure the smooth and secure operation of the vehicle’s systems [94].
- Adapting to Emerging Threats: The cybersecurity landscape is continually evolving, with new threats emerging regularly. OTA updates enable AV manufacturers to adapt to these changes by integrating the latest threat intelligence and defense mechanisms into the vehicle’s software, thereby staying ahead of potential attacks [95].
- Minimizing Downtime: OTA updates can be scheduled and executed with minimal disruption to the vehicle’s operation, ensuring that the vehicle remains operational while receiving necessary security updates. This minimizes downtime and inconvenience for users [96].
- Maintaining Compliance: Regulatory bodies may mandate certain security standards and updates for AVs. Regular updates ensure that the vehicles remain compliant with these regulations, avoiding potential legal and financial repercussions [97].
- Secure Update Mechanism: The OTA update process itself must be secure to prevent unauthorized modifications. This includes using strong authentication methods and encryption to protect the integrity and confidentiality of the update files [98].
- Testing and Validation: Updates should undergo rigorous testing and validation to ensure they do not introduce new vulnerabilities or disrupt existing functionalities. This involves thorough quality assurance processes and possibly phased rollouts [99].
- User Notification and Consent: Users should be informed about the updates being installed on their vehicles and, where appropriate, provide consent. This transparency helps build trust and ensures that users are aware of the changes being made [100].
- Regular Update Schedule: Establishing a regular schedule for updates can help ensure that vehicles receive timely security patches and enhancements. While emergency updates should be deployed as needed, a consistent update schedule helps manage the overall maintenance of the vehicle’s software [97].
4.4. Authentication Protocols
- Something You Know: a password or PIN.
- Something You Have: a smart card, token, or mobile device.
- Something You Are: biometric verification, such as fingerprints or facial recognition.
- Multi-Factor Authentication (MFA): Combines multiple forms of verification, such as passwords, smart cards, and biometric verification, to significantly reduce the risk of unauthorized access.
- Digital Certificates: Utilize public key infrastructure (PKI) to verify the identities of devices and users, ensuring that communications within the AV ecosystem are secure.
- Authentication Protocols in Practice:
- Vehicle-to-Everything (V2X) Communication: Autonomous vehicles rely on V2X communication to interact with other vehicles, infrastructure, and cloud services. Authentication protocols ensure that all entities involved in V2X communication are legitimate and authorized. For example, vehicles can use digital certificates to authenticate each other and exchange information securely, preventing malicious actors from injecting false data into the network [107,108].
- Access Control for Onboard Systems: Authentication protocols control access to the vehicle’s onboard systems, such as the infotainment system, navigation, and critical control units. By implementing MFA and digital certificates, only authorized users and devices can interact with these systems, reducing the risk of unauthorized modifications or control [84,109].
- Software and Firmware Updates: Secure authentication protocols verify the source and integrity of software and firmware updates before they are installed on the vehicle. This prevents malicious updates that could compromise the vehicle’s security. Digital signatures and certificates can be used to authenticate update packages, ensuring that they come from a trusted source [66,110].
- Remote Access: Autonomous vehicles often support remote access for diagnostics, maintenance, and fleet management. Authentication protocols ensure that only authorized personnel can access the vehicle remotely. MFA and secure key management practices are particularly important in these scenarios to prevent unauthorized remote access [111,112].
- Preventing Cyber Threats
- Remote Hacking: authentication protocols ensure that only authorized entities can access the vehicle’s network, preventing hackers from gaining control remotely [24].
- Data Breaches: by verifying the identity of devices and users, authentication protocols protect sensitive data from unauthorized access and theft [7].
- Spoofing Attacks: digital certificates and secure key management prevent attackers from impersonating legitimate devices or users, ensuring the integrity of communications [39].
5. Challenges in Cybersecurity for Autonomous Vehicles
5.1. Complexity of AV Systems
5.2. Lack of Standardization
5.3. Resource Constraints
6. Future Directions
6.1. AI and Machine Learning Applications
- Threat Detection and Response: AI-driven systems can analyze vast amounts of data from various sensors and network traffic to identify anomalies indicative of cyber threats. Machine learning algorithms can be trained to recognize patterns associated with known attacks and predict potential future threats, enabling proactive defense mechanisms [130].
- Adaptive Security Systems: Machine learning models can continuously learn from new data, allowing AV security systems to adapt and improve over time. This continuous learning process helps in refining the detection capabilities and reducing false positives, ensuring more accurate and timely responses to genuine threats [131].
- Automated Mitigation: AI can facilitate automated responses to cyber threats, minimizing human intervention and reducing response times. Automated systems can isolate compromised components, re-route communication, and apply security patches without delay, thereby mitigating the impact of attacks swiftly [132].
- Anomaly Detection: Machine learning algorithms can analyze vast amounts of data from AV sensors and communication networks to identify deviations from normal behavior, indicating potential cyber threats.
- Automated Mitigation: AI can facilitate automated responses to detected threats, such as isolating compromised components or re-routing communication paths.
6.2. Blockchain Technology
- Secure Communication: Blockchain can be used to secure vehicle-to-everything (V2X) communication, ensuring that data exchanged between AVs, infrastructure, and other entities are tamper-proof and authenticated. This can prevent unauthorized access and data manipulation [134].
- Data Integrity: Blockchain’s immutable ledger ensures that all recorded data are verifiable and cannot be altered retroactively. This is particularly useful for maintaining the integrity of sensor data, driving logs, and software updates, thereby enhancing trust in the system [135].
- Identity Management: Blockchain can provide a decentralized framework for identity management, ensuring that only authenticated and authorized entities can access AV systems. This reduces the risk of identity spoofing and unauthorized access [136].
6.3. Industry Collaboration and Standardization
- Consistent Security Standards: Developing and adopting industry-wide cybersecurity standards can ensure that all AV manufacturers adhere to a baseline level of security, reducing vulnerabilities and inconsistencies across different models and brands [139].
- Joint Research Initiatives: Collaborative research initiatives can drive innovation in AV cybersecurity. By pooling resources and expertise, industry stakeholders can explore new technologies and strategies to enhance the security of AV systems [141].
6.4. Legislative and Policy Developments
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Parekh, D.; Poddar, N.; Rajpurkar, A.; Chahal, M.; Kumar, N.; Joshi, G.P.; Cho, W. A Review on Autonomous Vehicles: Progress, Methods and Challenges. Electronics 2022, 11, 2162. [Google Scholar] [CrossRef]
- Wang, J.; Zhang, L.; Huang, Y.; Zhao, J.; Bella, F. Safety of Autonomous Vehicles. J. Adv. Transp. 2020, 2020, 8867757. [Google Scholar] [CrossRef]
- Ahangar, M.N.; Ahmed, Q.Z.; Khan, F.A.; Hafeez, M. A Survey of Autonomous Vehicles: Enabling Communication Technologies and Challenges. Sensors 2021, 21, 706. [Google Scholar] [CrossRef] [PubMed]
- Shetty, A.; Yu, M.; Kurzhanskiy, A.; Grembek, O.; Tavafoghi, H.; Varaiya, P. Safety Challenges for Autonomous Vehicles in the Absence of Connectivity. Transp. Res. Part. C Emerg. Technol. 2021, 128, 103133. [Google Scholar] [CrossRef]
- Xu, W. From Automation to Autonomy and Autonomous Vehicles. Interactions 2021, 28, 48–53. [Google Scholar] [CrossRef]
- Bathla, G.; Bhadane, K.; Singh, R.K.; Kumar, R.; Aluvalu, R.; Krishnamurthi, R.; Kumar, A.; Thakur, R.N.; Basheer, S. Autonomous Vehicles and Intelligent Automation: Applications, Challenges, and Opportunities. Mob. Inf. Syst. 2022, 2022, 7632892. [Google Scholar] [CrossRef]
- Kim, K.; Kim, J.S.; Jeong, S.; Park, J.-H.; Kim, H.K. Cybersecurity for Autonomous Vehicles: Review of Attacks and Defense. Comput. Secur. 2021, 103, 102150. [Google Scholar] [CrossRef]
- Sharma, P.; Gillanders, J. Cybersecurity and Forensics in Connected Autonomous Vehicles: A Review of the State-of-the-Art. IEEE Access 2022, 10, 108979–108996. [Google Scholar] [CrossRef]
- Girdhar, M.; Hong, J.; Moore, J. Cybersecurity of Autonomous Vehicles: A Systematic Literature Review of Adversarial Attacks and Defense Models. IEEE Open J. Veh. Technol. 2023, 4, 417–437. [Google Scholar] [CrossRef]
- Algarni, A.; Thayananthan, V. Autonomous Vehicles: The Cybersecurity Vulnerabilities and Countermeasures for Big Data Communication. Symmetry 2022, 14, 2494. [Google Scholar] [CrossRef]
- Khalid Khan, S.; Shiwakoti, N.; Stasinopoulos, P.; Warren, M. Modelling Cybersecurity Regulations for Automated Vehicles. Accid. Anal. Prev. 2023, 186, 107054. [Google Scholar] [CrossRef] [PubMed]
- Malik, S.; Sun, W. Analysis and Simulation of Cyber Attacks Against Connected and Autonomous Vehicles. In Proceedings of the 2020 International Conference on Connected and Autonomous Driving (MetroCAD), Detroit, MI, USA, 27–28 February 2020; pp. 62–70. [Google Scholar]
- Al-Sabaawi, A.; Al-Dulaimi, K.; Foo, E.; Alazab, M. Addressing Malware Attacks on Connected and Autonomous Vehicles: Recent Techniques and Challenges. In Malware Analysis Using Artificial Intelligence and Deep Learning; Springer International Publishing: Cham, Switzerland, 2021; pp. 97–119. [Google Scholar]
- Meyer, S.F.; Elvik, R.; Johnsson, E. Risk Analysis for Forecasting Cyberattacks against Connected and Autonomous Vehicles. J. Transp. Secur. 2021, 14, 227–247. [Google Scholar] [CrossRef]
- Sharma, O.; Sahoo, N.C.; Puhan, N.B. Recent Advances in Motion and Behavior Planning Techniques for Software Architecture of Autonomous Vehicles: A State-of-the-Art Survey. Eng. Appl. Artif. Intell. 2021, 101, 104211. [Google Scholar] [CrossRef]
- Bezai, N.E.; Medjdoub, B.; Al-Habaibeh, A.; Chalal, M.L.; Fadli, F. Future Cities and Autonomous Vehicles: Analysis of the Barriers to Full Adoption. Energy Built Environ. 2021, 2, 65–81. [Google Scholar] [CrossRef]
- Khayyam, H.; Javadi, B.; Jalili, M.; Jazar, R.N. Artificial Intelligence and Internet of Things for Autonomous Vehicles. In Nonlinear Approaches in Engineering Applications; Springer International Publishing: Cham, Switzerland, 2020; pp. 39–68. [Google Scholar]
- Dash, S.; Azad, C. Cyber Security and Threat Analysis in Autonomous Vehicles. In Autonomous Vehicles Volume 1; Wiley: Hoboken, NJ, USA, 2022; pp. 161–180. [Google Scholar]
- Azam, S.; Munir, F.; Sheri, A.M.; Kim, J.; Jeon, M. System, Design and Experimental Validation of Autonomous Vehicle in an Unconstrained Environment. Sensors 2020, 20, 5999. [Google Scholar] [CrossRef] [PubMed]
- Frigerio, A.; Vermeulen, B.; Goossens, K.G.W. Automotive Architecture Topologies: Analysis for Safety-Critical Autonomous Vehicle Applications. IEEE Access 2021, 9, 62837–62846. [Google Scholar] [CrossRef]
- Sontakke, P.V.; Chopade, N.B. Impact and Analysis of Denial-of-Service Attack on an Autonomous Vehicle Test Bed Setup. In Proceedings of Third International Conference on Intelligent Computing, Information and Control Systems; Springer: Singapore, 2022; pp. 221–236. [Google Scholar]
- Rajabli, N.; Flammini, F.; Nardone, R.; Vittorini, V. Software Verification and Validation of Safe Autonomous Cars: A Systematic Literature Review. IEEE Access 2021, 9, 4797–4819. [Google Scholar] [CrossRef]
- Vargas, J.; Alsweiss, S.; Toker, O.; Razdan, R.; Santos, J. An Overview of Autonomous Vehicles Sensors and Their Vulnerability to Weather Conditions. Sensors 2021, 21, 5397. [Google Scholar] [CrossRef] [PubMed]
- Khan, S.K.; Shiwakoti, N.; Stasinopoulos, P.; Chen, Y. Cyber-Attacks in the next-Generation Cars, Mitigation Techniques, Anticipated Readiness and Future Directions. Accid. Anal. Prev. 2020, 148, 105837. [Google Scholar] [CrossRef]
- Pham, M.; Xiong, K. A Survey on Security Attacks and Defense Techniques for Connected and Autonomous Vehicles. Comput. Secur. 2021, 109, 102269. [Google Scholar] [CrossRef]
- Pascale, F.; Adinolfi, E.A.; Coppola, S.; Santonicola, E. Cybersecurity in Automotive: An Intrusion Detection System in Connected Vehicles. Electronics 2021, 10, 1765. [Google Scholar] [CrossRef]
- Bangui, H.; Buhnova, B. Recent Advances in Machine-Learning Driven Intrusion Detection in Transportation: Survey. Procedia Comput. Sci. 2021, 184, 877–886. [Google Scholar] [CrossRef]
- Wang, Y.; Bian, N.; Zhang, L.; Huang, Y.; Chen, H. Resilient Path-following Control of Autonomous Vehicles Subject to Intermittent Denial-of-service Attacks. IET Intell. Transp. Syst. 2021, 15, 1508–1521. [Google Scholar] [CrossRef]
- Dasgupta, S.; Rahman, M.; Islam, M.; Chowdhury, M. A Sensor Fusion-Based GNSS Spoofing Attack Detection Framework for Autonomous Vehicles. IEEE Trans. Intell. Transp. Syst. 2022, 23, 23559–23572. [Google Scholar] [CrossRef]
- Chen, L.; He, Y.; Wang, Q.; Pan, W.; Ming, Z. Joint Optimization of Sensing, Decision-Making and Motion-Controlling for Autonomous Vehicles: A Deep Reinforcement Learning Approach. IEEE Trans. Veh. Technol. 2022, 71, 4642–4654. [Google Scholar] [CrossRef]
- El-Rewini, Z.; Sadatsharan, K.; Sugunaraj, N.; Selvaraj, D.F.; Plathottam, S.J.; Ranganathan, P. Cybersecurity Attacks in Vehicular Sensors. IEEE Sens. J. 2020, 20, 13752–13767. [Google Scholar] [CrossRef]
- Malik, S.; Bandi, P.; Sun, W. An Experimental Study of Denial of Service Attack Against Platoon of Smart Vehicles. In Proceedings of the 2021 Fourth International Conference on Connected and Autonomous Driving (MetroCAD), Detroit, MI, USA, 8–29 April 2021; pp. 23–30. [Google Scholar]
- Sun, H.; Peng, C.; Ding, F. Self-discipline Predictive Control of Autonomous Vehicles against Denial of Service Attacks. Asian J. Control 2022, 24, 3538–3551. [Google Scholar] [CrossRef]
- Khalid Khan, S.; Shiwakoti, N.; Stasinopoulos, P. A Conceptual System Dynamics Model for Cybersecurity Assessment of Connected and Autonomous Vehicles. Accid. Anal. Prev. 2022, 165, 106515. [Google Scholar] [CrossRef]
- Sun, X.; Yu, F.R.; Zhang, P. A Survey on Cyber-Security of Connected and Autonomous Vehicles (CAVs). IEEE Trans. Intell. Transp. Syst. 2022, 23, 6240–6259. [Google Scholar] [CrossRef]
- Yang, T.; Lv, C. A Secure Sensor Fusion Framework for Connected and Automated Vehicles Under Sensor Attacks. IEEE Internet Things J. 2022, 9, 22357–22365. [Google Scholar] [CrossRef]
- Zhao, X.; Fang, Y.; Min, H.; Wu, X.; Wang, W.; Teixeira, R. Potential Sources of Sensor Data Anomalies for Autonomous Vehicles: An Overview from Road Vehicle Safety Perspective. Expert. Syst. Appl. 2024, 236, 121358. [Google Scholar] [CrossRef]
- Channon, M.; Marson, J. THE Liability for Cybersecurity Breaches of Connected and Autonomous Vehicles. Comput. Law. Secur. Rev. 2021, 43, 105628. [Google Scholar] [CrossRef]
- Liu, N.; Nikitas, A.; Parkinson, S. Exploring Expert Perceptions about the Cyber Security and Privacy of Connected and Autonomous Vehicles: A Thematic Analysis Approach. Transp. Res. Part. F Traffic Psychol. Behav. 2020, 75, 66–86. [Google Scholar] [CrossRef]
- Seetharaman, A.; Patwa, N.; Jadhav, V.; Saravanan, A.S.; Sangeeth, D. Impact of Factors Influencing Cyber Threats on Autonomous Vehicles. Appl. Artif. Intell. 2021, 35, 105–132. [Google Scholar] [CrossRef]
- Katrakazas, C.; Theofilatos, A.; Papastefanatos, G.; Härri, J.; Antoniou, C. Cyber Security and Its Impact on CAV Safety: Overview, Policy Needs and Challenges. Adv. Transp. Policy Plan. 2020, 5, 73–94. [Google Scholar]
- Kim, S.; Shrestha, R. Automotive Cyber Security; Springer: Singapore, 2020; ISBN 978-981-15-8052-9. [Google Scholar]
- Sun, H.-T.; Peng, C.; Ge, X.; Chen, Z. Secure Event-Triggered Sliding Control for Path Following of Autonomous Vehicles Under Sensor and Actuator Attacks. IEEE Trans. Intell. Veh. 2024, 9, 981–992. [Google Scholar] [CrossRef]
- Chattopadhyay, A.; Lam, K.-Y.; Tavva, Y. Autonomous Vehicle: Security by Design. IEEE Trans. Intell. Transp. Syst. 2021, 22, 7015–7029. [Google Scholar] [CrossRef]
- Benyahya, M.; Collen, A.; Nijdam, N.A. Analyses on Standards and Regulations for Connected and Automated Vehicles: Identifying the Certifications Roadmap. Transp. Eng. 2023, 14, 100205. [Google Scholar] [CrossRef]
- Maeng, K.; Kim, W.; Cho, Y. Consumers’ Attitudes toward Information Security Threats against Connected and Autonomous Vehicles. Telemat. Inform. 2021, 63, 101646. [Google Scholar] [CrossRef]
- Karopoulos, G.; Kambourakis, G.; Chatzoglou, E.; Hernández-Ramos, J.L.; Kouliaridis, V. Demystifying In-Vehicle Intrusion Detection Systems: A Survey of Surveys and a Meta-Taxonomy. Electronics 2022, 11, 1072. [Google Scholar] [CrossRef]
- Mateo Sanguino, T.d.J.; Lozano Domínguez, J.M.; de Carvalho Baptista, P. Cybersecurity Certification and Auditing of Automotive Industry. Adv. Transp. Policy Plan. 2020, 5, 95–124. [Google Scholar]
- Panda, S.; Panaousis, E.; Loukas, G.; Kentrotis, K. Privacy Impact Assessment of Cyber Attacks on Connected and Autonomous Vehicles. In Proceedings of the 18th International Conference on Availability, Reliability and Security, Benevento, Italy, 29 August–1 September 2023; ACM: New York, NY, USA, 2023; pp. 1–9. [Google Scholar]
- Xiao, S.; Ge, X.; Han, Q.-L.; Zhang, Y. Secure Distributed Adaptive Platooning Control of Automated Vehicles Over Vehicular Ad-Hoc Networks Under Denial-of-Service Attacks. IEEE Trans. Cybern. 2022, 52, 12003–12015. [Google Scholar] [CrossRef] [PubMed]
- Alsaade, F.W.; Al-Adhaileh, M.H. Cyber Attack Detection for Self-Driving Vehicle Networks Using Deep Autoencoder Algorithms. Sensors 2023, 23, 4086. [Google Scholar] [CrossRef]
- Giannaros, A.; Karras, A.; Theodorakopoulos, L.; Karras, C.; Kranias, P.; Schizas, N.; Kalogeratos, G.; Tsolis, D. Autonomous Vehicles: Sophisticated Attacks, Safety Issues, Challenges, Open Topics, Blockchain, and Future Directions. J. Cybersecur. Priv. 2023, 3, 493–543. [Google Scholar] [CrossRef]
- Sun, J.; Xu, G.; Zhang, T.; Cheng, X.; Han, X.; Tang, M. Secure Data Sharing With Flexible Cross-Domain Authorization in Autonomous Vehicle Systems. IEEE Trans. Intell. Transp. Syst. 2023, 24, 7527–7540. [Google Scholar] [CrossRef]
- Hu, S.; Yu, W.; Yang, J.; Chen, X.; Xie, X.; Ma, Y. Attack Parameter Dependent Resilient H∞ Path-Following Control Design for Autonomous Vehicles under Cyber Attacks. Control Eng. Pract. 2023, 135, 105488. [Google Scholar] [CrossRef]
- Wang, S.; Li, C.; Ng, D.W.K.; Eldar, Y.C.; Poor, H.V.; Hao, Q.; Xu, C. Federated Deep Learning Meets Autonomous Vehicle Perception: Design and Verification. IEEE Netw. 2023, 37, 16–25. [Google Scholar] [CrossRef]
- Cai, X.; Shi, K.; Sun, Y.; Cao, J.; Wen, S.; Qiao, C.; Tian, Z. Stability Analysis of Networked Control Systems Under DoS Attacks and Security Controller Design With Mini-Batch Machine Learning Supervision. IEEE Trans. Inf. Forensics Secur. 2024, 19, 3857–3865. [Google Scholar] [CrossRef]
- Verma, P.; Bharot, N.; Breslin, J.G.; Sharma, M.; Chaurasia, N.; Vidyarthi, A. Uncovering Collateral Damages and Advanced Defense Strategies in Cloud Environments against DDoS Attacks: A Comprehensive Review. Trans. Emerg. Telecommun. Technol. 2024, 35, e4934. [Google Scholar] [CrossRef]
- Basiri, M.H.; Azad, N.L.; Fischmeister, S. Secure Dynamic Nonlinear Heterogeneous Vehicle Platooning: Denial-of-Service Cyber-Attack Case. In Security in Cyber-Physical Systems; Springer: Cham, Switzerland, 2021; pp. 287–315. [Google Scholar]
- Khadka, A.; Karypidis, P.; Lytos, A.; Efstathopoulos, G. A Benchmarking Framework for Cyber-Attacks on Autonomous Vehicles. Transp. Res. Procedia 2021, 52, 323–330. [Google Scholar] [CrossRef]
- Nayak, B.P.; Hota, L.; Kumar, A.; Turuk, A.K.; Chong, P.H.J. Autonomous Vehicles: Resource Allocation, Security, and Data Privacy. IEEE Trans. Green Commun. Netw. 2022, 6, 117–131. [Google Scholar] [CrossRef]
- Limbasiya, T.; Teng, K.Z.; Chattopadhyay, S.; Zhou, J. A Systematic Survey of Attack Detection and Prevention in Connected and Autonomous Vehicles. Veh. Commun. 2022, 37, 100515. [Google Scholar] [CrossRef]
- Chow, M.C.; Ma, M.; Pan, Z. Attack Models and Countermeasures for Autonomous Vehicles. In Intelligent Technologies for Internet of Vehicles; Springe: Cham, Switzerland, 2021; pp. 375–401. [Google Scholar]
- Niroumand, F.J.; Ansari Bonab, P.; Sargolzaei, A. Security of Connected and Autonomous Vehicles: A Review of Attacks and Mitigation Strategies. In Proceedings of the SoutheastCon 2024, Atlanta, GA USA, 15 March 2024; pp. 1197–1204. [Google Scholar]
- Kim, S.; Shrestha, R. Security and Privacy in Intelligent Autonomous Vehicles. In Automotive Cyber Security; Springer: Singapore, 2020; pp. 35–66. [Google Scholar]
- Karim, H.; Rawat, D.B. TollsOnly Please—Homomorphic Encryption for Toll Transponder Privacy in Internet of Vehicles. IEEE Internet Things J. 2022, 9, 2627–2636. [Google Scholar] [CrossRef]
- Qureshi, A.; Marvi, M.; Shamsi, J.A.; Aijaz, A. EUF: A Framework for Detecting over-the-Air Malicious Updates in Autonomous Vehicles. J. King Saud. Univ.-Comput. Inf. Sci. 2022, 34, 5456–5467. [Google Scholar] [CrossRef]
- Jiang, Q.; Zhang, N.; Ni, J.; Ma, J.; Ma, X.; Choo, K.-K.R. Unified Biometric Privacy Preserving Three-Factor Authentication and Key Agreement for Cloud-Assisted Autonomous Vehicles. IEEE Trans. Veh. Technol. 2020, 69, 9390–9401. [Google Scholar] [CrossRef]
- Anthony, C.; Elgenaidi, W.; Rao, M. Intrusion Detection System for Autonomous Vehicles Using Non-Tree Based Machine Learning Algorithms. Electronics 2024, 13, 809. [Google Scholar] [CrossRef]
- Abdallah, E.E.; Aloqaily, A.; Fayez, H. Identifying Intrusion Attempts on Connected and Autonomous Vehicles: A Survey. Procedia Comput. Sci. 2023, 220, 307–314. [Google Scholar] [CrossRef]
- Aldhyani, T.H.H.; Alkahtani, H. Attacks to Automatous Vehicles: A Deep Learning Algorithm for Cybersecurity. Sensors 2022, 22, 360. [Google Scholar] [CrossRef]
- He, Q.; Meng, X.; Qu, R.; Xi, R. Machine Learning-Based Detection for Cyber Security Attacks on Connected and Autonomous Vehicles. Mathematics 2020, 8, 1311. [Google Scholar] [CrossRef]
- Jiang, J.; Wang, C.; Chattopadhyay, S.; Zhang, W. Road Context-Aware Intrusion Detection System for Autonomous Cars. In Proceedings of the Information and Communications Security: 21st International Conference, ICICS 2019, Beijing, China, 15–17 December 2019; pp. 124–142. [Google Scholar]
- Onur, F.; Gönen, S.; Barışkan, M.A.; Kubat, C.; Tunay, M.; Yılmaz, E.N. Machine Learning-Based Identification of Cybersecurity Threats Affecting Autonomous Vehicle Systems. Comput. Ind. Eng. 2024, 190, 110088. [Google Scholar] [CrossRef]
- Baz, M. SEHIDS: Self Evolving Host-Based Intrusion Detection System for IoT Networks. Sensors 2022, 22, 6505. [Google Scholar] [CrossRef]
- Yang, L.; Moubayed, A.; Shami, A. MTH-IDS: A Multitiered Hybrid Intrusion Detection System for Internet of Vehicles. IEEE Internet Things J. 2022, 9, 616–632. [Google Scholar] [CrossRef]
- Xie, Y.; Zhou, Y.; Xu, J.; Zhou, J.; Chen, X.; Xiao, F. Cybersecurity Protection on In-vehicle Networks for Distributed Automotive Cyber-physical Systems: State-of-the-art and Future Challenges. Softw. Pract. Exp. 2021, 51, 2108–2127. [Google Scholar] [CrossRef]
- Aloqaily, M.; Kanhere, S.; Bellavista, P.; Nogueira, M. Special Issue on Cybersecurity Management in the Era of AI. J. Netw. Syst. Manag. 2022, 30, 39. [Google Scholar] [CrossRef]
- Markevych, M.; Dawson, M. A Review of Enhancing Intrusion Detection Systems for Cybersecurity Using Artificial Intelligence (AI). Int. Conf. Knowl.-Based Organ. 2023, 29, 30–37. [Google Scholar] [CrossRef]
- Kukkala, V.K.; Thiruloga, S.V.; Pasricha, S. Roadmap for Cybersecurity in Autonomous Vehicles. IEEE Consum. Electron. Mag. 2022, 11, 13–23. [Google Scholar] [CrossRef]
- Guan, T.; Han, Y.; Kang, N.; Tang, N.; Chen, X.; Wang, S. An Overview of Vehicular Cybersecurity for Intelligent Connected Vehicles. Sustainability 2022, 14, 5211. [Google Scholar] [CrossRef]
- Rathore, M.S.; Poongodi, M.; Saurabh, P.; Lilhore, U.K.; Bourouis, S.; Alhakami, W.; Osamor, J.; Hamdi, M. A Novel Trust-Based Security and Privacy Model for Internet of Vehicles Using Encryption and Steganography. Comput. Electr. Eng. 2022, 102, 108205. [Google Scholar] [CrossRef]
- Parekh, R.; Patel, N.; Gupta, R.; Jadav, N.K.; Tanwar, S.; Alharbi, A.; Tolba, A.; Neagu, B.-C.; Raboaca, M.S. GeFL: Gradient Encryption-Aided Privacy Preserved Federated Learning for Autonomous Vehicles. IEEE Access 2023, 11, 1825–1839. [Google Scholar] [CrossRef]
- Cui, J.; Yu, J.; Zhong, H.; Wei, L.; Liu, L. Chaotic Map-Based Authentication Scheme Using Physical Unclonable Function for Internet of Autonomous Vehicle. IEEE Trans. Intell. Transp. Syst. 2023, 24, 3167–3181. [Google Scholar] [CrossRef]
- Cui, J.; Chen, X.; Zhang, J.; Zhang, Q.; Zhong, H. Toward Achieving Fine-Grained Access Control of Data in Connected and Autonomous Vehicles. IEEE Internet Things J. 2021, 8, 7925–7937. [Google Scholar] [CrossRef]
- Murad, S.; Khan, A.; Shiaeles, S.; Masala, G. Data Encryption and Fragmentation in Autonomous Vehicles Using Raspberry Pi 3. In Proceedings of the 2019 IEEE World Congress on Services (SERVICES), Milan, Italy, 8–13 July 2019; pp. 212–216. [Google Scholar]
- Ansari, S.; Ahmad, J.; Aziz Shah, S.; Kashif Bashir, A.; Boutaleb, T.; Sinanovic, S. Chaos-based Privacy Preserving Vehicle Safety Protocol for 5G Connected Autonomous Vehicle Networks. Trans. Emerg. Telecommun. Technol. 2020, 31, e3966. [Google Scholar] [CrossRef]
- Thing, V.L.L.; Wu, J. Autonomous Vehicle Security: A Taxonomy of Attacks and Defences. In Proceedings of the 2016 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Chengdu, China, 15–18 December 2016; pp. 164–170. [Google Scholar]
- Gao, C.; Wang, G.; Shi, W.; Wang, Z.; Chen, Y. Autonomous Driving Security: State of the Art and Challenges. IEEE Internet Things J. 2022, 9, 7572–7595. [Google Scholar] [CrossRef]
- Azam, N.; Michala, L.; Ansari, S.; Truong, N.B. Data Privacy Threat Modelling for Autonomous Systems: A Survey From the GDPR’s Perspective. IEEE Trans. Big Data 2023, 9, 388–414. [Google Scholar] [CrossRef]
- Jha, S.; Jha, N.; Prashar, D.; Ahmad, S.; Alouffi, B.; Alharbi, A. Integrated IoT-Based Secure and Efficient Key Management Framework Using Hashgraphs for Autonomous Vehicles to Ensure Road Safety. Sensors 2022, 22, 2529. [Google Scholar] [CrossRef]
- Hussain, M.; Hong, J.-E. Enforcing Safety in Cooperative Perception of Autonomous Driving Systems through Logistic Chaos Map-Based End-to-End Encryption. In Proceedings of the 2022 16th International Conference on Open Source Systems and Technologies (ICOSST), Lahore, Pakistan, 14 December 2022; pp. 1–6. [Google Scholar]
- Ghosal, A.; Halder, S.; Conti, M. STRIDE: Scalable and Secure Over-The-Air Software Update Scheme for Autonomous Vehicles. In Proceedings of the ICC 2020—2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar]
- Feroz, B.; Mehmood, A.; Maryam, H.; Zeadally, S.; Maple, C.; Shah, M.A. Vehicle-Life Interaction in Fog-Enabled Smart Connected and Autonomous Vehicles. IEEE Access 2021, 9, 7402–7420. [Google Scholar] [CrossRef]
- Min, H.; Fang, Y.; Wu, X.; Lei, X.; Chen, S.; Teixeira, R.; Zhu, B.; Zhao, X.; Xu, Z. A Fault Diagnosis Framework for Autonomous Vehicles with Sensor Self-Diagnosis. Expert. Syst. Appl. 2023, 224, 120002. [Google Scholar] [CrossRef]
- Tan, S.Y.; Taeihagh, A. Adaptive Governance of Autonomous Vehicles: Accelerating the Adoption of Disruptive Technologies in Singapore. Gov. Inf. Q. 2021, 38, 101546. [Google Scholar] [CrossRef]
- Ahmed, H.U.; Huang, Y.; Lu, P.; Bridgelall, R. Technology Developments and Impacts of Connected and Autonomous Vehicles: An Overview. Smart Cities 2022, 5, 382–404. [Google Scholar] [CrossRef]
- Pek, C.; Manzinger, S.; Koschi, M.; Althoff, M. Using Online Verification to Prevent Autonomous Vehicles from Causing Accidents. Nat. Mach. Intell. 2020, 2, 518–528. [Google Scholar] [CrossRef]
- Bouchelaghem, S.; Bouabdallah, A.; Omar, M. Autonomous Vehicle Security: Literature Review of Real Attack Experiments. In Proceedings of the Risks and Security of Internet and Systems: 15th International Conference, CRiSIS 2020, Paris, France, 4–6 November 2020; pp. 255–272. [Google Scholar]
- Hu, S.; Zhang, Q.; Weimerskirch, A.; Mao, Z.M. Gatekeeper. In Proceedings of the 2022 ACM on Asia Conference on Computer and Communications Security, Nagasaki, Japan, 30 May–3 June 2022; ACM: New York, NY, USA, 2022; pp. 494–507. [Google Scholar]
- Martínez-Cruz, A.; Ramírez-Gutiérrez, K.A.; Feregrino-Uribe, C.; Morales-Reyes, A. Security on In-Vehicle Communication Protocols: Issues, Challenges, and Future Research Directions. Comput. Commun. 2021, 180, 1–20. [Google Scholar] [CrossRef]
- Miao, J.; Wang, Z.; Ning, X.; Xiao, N.; Cai, W.; Liu, R. Practical and Secure Multifactor Authentication Protocol for Autonomous Vehicles in 5G. Softw. Pract. Exp. 2022, 1–18. [Google Scholar] [CrossRef]
- Bagga, P.; Das, A.K.; Wazid, M.; Rodrigues, J.J.P.C.; Park, Y. Authentication Protocols in Internet of Vehicles: Taxonomy, Analysis, and Challenges. IEEE Access 2020, 8, 54314–54344. [Google Scholar] [CrossRef]
- Aman, M.N.; Javaid, U.; Sikdar, B. A Privacy-Preserving and Scalable Authentication Protocol for the Internet of Vehicles. IEEE Internet Things J. 2021, 8, 1123–1139. [Google Scholar] [CrossRef]
- Vasudev, H.; Deshpande, V.; Das, D.; Das, S.K. A Lightweight Mutual Authentication Protocol for V2V Communication in Internet of Vehicles. IEEE Trans. Veh. Technol. 2020, 69, 6709–6717. [Google Scholar] [CrossRef]
- Cui, J.; Chen, Y.; Zhong, H.; He, D.; Wei, L.; Bolodurina, I.; Liu, L. Lightweight Encryption and Authentication for Controller Area Network of Autonomous Vehicles. IEEE Trans. Veh. Technol. 2023, 72, 14756–14770. [Google Scholar] [CrossRef]
- Nyangaresi, V.O.; Rodrigues, A.J.; Abeka, S.O. Efficient Group Authentication Protocol for Secure 5G Enabled Vehicular Communications. In Proceedings of the 2020 16th International Computer Engineering Conference (ICENCO), Cairo, Egypt, 29 December 2020; pp. 25–30. [Google Scholar]
- Hasan, M.; Mohan, S.; Shimizu, T.; Lu, H. Securing Vehicle-to-Everything (V2X) Communication Platforms. IEEE Trans. Intell. Veh. 2020, 5, 693–713. [Google Scholar] [CrossRef]
- Noor-A-Rahim, M.; Liu, Z.; Lee, H.; Khyam, M.O.; He, J.; Pesch, D.; Moessner, K.; Saad, W.; Poor, H.V. 6G for Vehicle-to-Everything (V2X) Communications: Enabling Technologies, Challenges, and Opportunities. Proc. IEEE 2022, 110, 712–734. [Google Scholar] [CrossRef]
- Zhang, Q.; Zhong, H.; Cui, J.; Ren, L.; Shi, W. AC4AV: A Flexible and Dynamic Access Control Framework for Connected and Autonomous Vehicles. IEEE Internet Things J. 2021, 8, 1946–1958. [Google Scholar] [CrossRef]
- Dafoe, J.; Singh, H.; Chen, N.; Chen, B. Enabling Real-Time Restoration of Compromised ECU Firmware in Connected and Autonomous Vehicles. LNICST 2024, 552, 15–33. [Google Scholar]
- Martinho, A.; Herber, N.; Kroesen, M.; Chorus, C. Ethical Issues in Focus by the Autonomous Vehicles Industry. Transp. Rev. 2021, 41, 556–577. [Google Scholar] [CrossRef]
- Paddeu, D.; Shergold, I.; Parkhurst, G. The Social Perspective on Policy towards Local Shared Autonomous Vehicle Services (LSAVS). Transp. Policy 2020, 98, 116–126. [Google Scholar] [CrossRef]
- Dobryakova, L.; Lemieszewski, L.; Ochin, E. The Vulnerability of Unmanned Vehicles to Terrorist Attacks Such as Global Navigation Satellite System Spoofing. Sci. J. Marit. Univ. Szczec. 2016, 46, 118. [Google Scholar]
- Hussain, N.; Rani, P.; Chouhan, H.; Gaur, U.S. Cyber Security and Privacy of Connected and Automated Vehicles (CAVs)-Based Federated Learning: Challenges, Opportunities, and Open Issues. In Federated Learning for IoT Applications; Springer: Cham, Switzerland, 2022; pp. 169–183. [Google Scholar]
- Krause, T.; Ernst, R.; Klaer, B.; Hacker, I.; Henze, M. Cybersecurity in Power Grids: Challenges and Opportunities. Sensors 2021, 21, 6225. [Google Scholar] [CrossRef] [PubMed]
- Lemieszewski, Ł.; Radomska-Zalas, A.; Perec, A.; Dobryakova, L.; Ochin, E. Gnss and Lnss Positioning of Unmanned Transport Systems: The Brief Classification of Terrorist Attacks on Usvs and Uuvs. Electronics 2021, 10, 401. [Google Scholar] [CrossRef]
- Chen, B.; Sun, D.; Zhou, J.; Wong, W.; Ding, Z. A Future Intelligent Traffic System with Mixed Autonomous Vehicles and Human-Driven Vehicles. Inf. Sci. 2020, 529, 59–72. [Google Scholar] [CrossRef]
- Grigorescu, S.; Trasnea, B.; Cocias, T.; Macesanu, G. A Survey of Deep Learning Techniques for Autonomous Driving. J. Field Robot. 2020, 37, 362–386. [Google Scholar] [CrossRef]
- Das, H.S.; Rahman, M.M.; Li, S.; Tan, C.W. Electric Vehicles Standards, Charging Infrastructure, and Impact on Grid Integration: A Technological Review. Renew. Sustain. Energy Rev. 2020, 120, 109618. [Google Scholar] [CrossRef]
- Joubert, N.; Reid, T.G.R.; Noble, F. Developments in Modern GNSS and Its Impact on Autonomous Vehicle Architectures. In Proceedings of the 2020 IEEE Intelligent Vehicles Symposium (IV), Las Vegas, NV, USA, 19 October 2020; pp. 2029–2036. [Google Scholar]
- Storck, C.R.; Duarte-Figueiredo, F. A Survey of 5G Technology Evolution, Standards, and Infrastructure Associated With Vehicle-to-Everything Communications by Internet of Vehicles. IEEE Access 2020, 8, 117593–117614. [Google Scholar] [CrossRef]
- Deveci, M.; Pamucar, D.; Gokasar, I. Fuzzy Power Heronian Function Based CoCoSo Method for the Advantage Prioritization of Autonomous Vehicles in Real-Time Traffic Management. Sustain. Cities Soc. 2021, 69, 102846. [Google Scholar] [CrossRef]
- Mehra, A.; Mandal, M.; Narang, P.; Chamola, V. ReViewNet: A Fast and Resource Optimized Network for Enabling Safe Autonomous Driving in Hazy Weather Conditions. IEEE Trans. Intell. Transp. Syst. 2021, 22, 4256–4266. [Google Scholar] [CrossRef]
- Wang, Y.; Liu, Q.; Mihankhah, E.; Lv, C.; Wang, D. Detection and Isolation of Sensor Attacks for Autonomous Vehicles: Framework, Algorithms, and Validation. IEEE Trans. Intell. Transp. Syst. 2022, 23, 8247–8259. [Google Scholar] [CrossRef]
- Hakak, S.; Gadekallu, T.R.; Maddikunta, P.K.R.; Ramu, S.P.; M, P.; De Alwis, C.; Liyanage, M. Autonomous Vehicles in 5G and beyond: A Survey. Veh. Commun. 2023, 39, 100551. [Google Scholar] [CrossRef]
- Hataba, M.; Sherif, A.; Mahmoud, M.; Abdallah, M.; Alasmary, W. Security and Privacy Issues in Autonomous Vehicles: A Layer-Based Survey. IEEE Open J. Commun. Soc. 2022, 3, 811–829. [Google Scholar] [CrossRef]
- Cao, D.; Wang, X.; Li, L.; Lv, C.; Na, X.; Xing, Y.; Li, X.; Li, Y.; Chen, Y.; Wang, F.-Y. Future Directions of Intelligent Vehicles: Potentials, Possibilities, and Perspectives. IEEE Trans. Intell. Veh. 2022, 7, 7–10. [Google Scholar] [CrossRef]
- Gul, F.; Mir, I.; Abualigah, L.; Sumari, P.; Forestiero, A. A Consolidated Review of Path Planning and Optimization Techniques: Technical Perspectives and Future Directions. Electronics 2021, 10, 2250. [Google Scholar] [CrossRef]
- Soori, M.; Arezoo, B.; Dastres, R. Artificial Intelligence, Machine Learning and Deep Learning in Advanced Robotics, a Review. Cogn. Robot. 2023, 3, 54–70. [Google Scholar] [CrossRef]
- Bachute, M.R.; Subhedar, J.M. Autonomous Driving Architectures: Insights of Machine Learning and Deep Learning Algorithms. Mach. Learn. Appl. 2021, 6, 100164. [Google Scholar] [CrossRef]
- Ullah, Z.; Al-Turjman, F.; Mostarda, L.; Gagliardi, R. Applications of Artificial Intelligence and Machine Learning in Smart Cities. Comput. Commun. 2020, 154, 313–323. [Google Scholar] [CrossRef]
- Jing, P.; Hu, H.; Zhan, F.; Chen, Y.; Shi, Y. Agent-Based Simulation of Autonomous Vehicles: A Systematic Literature Review. IEEE Access 2020, 8, 79089–79103. [Google Scholar] [CrossRef]
- Narbayeva, S.; Bakibayev, T.; Abeshev, K.; Makarova, I.; Shubenkova, K.; Pashkevich, A. Blockchain Technology on the Way of Autonomous Vehicles Development. Transp. Res. Procedia 2020, 44, 168–175. [Google Scholar] [CrossRef]
- Nair, M.M.; Tyagi, A.K. Preserving Privacy Using Blockchain Technology in Autonomous Vehicles. In Proceedings of International Conference on Network Security and Blockchain Technology; Springer: Singapore, 2022; pp. 237–248. [Google Scholar]
- Kamble, N.; Gala, R.; Vijayaraghavan, R.; Shukla, E.; Patel, D. Using Blockchain in Autonomous Vehicles. In Artificial Intelligence and Blockchain for Future Cybersecurity Applications; Springer: Cham, Switzerland, 2021; pp. 285–305. [Google Scholar]
- Gupta, R.; Tanwar, S.; Kumar, N.; Tyagi, S. Blockchain-Based Security Attack Resilience Schemes for Autonomous Vehicles in Industry 4.0: A Systematic Review. Comput. Electr. Eng. 2020, 86, 106717. [Google Scholar] [CrossRef]
- Almeaibed, S.; Al-Rubaye, S.; Tsourdos, A.; Avdelidis, N.P. Digital Twin Analysis to Promote Safety and Security in Autonomous Vehicles. IEEE Commun. Stand. Mag. 2021, 5, 40–46. [Google Scholar] [CrossRef]
- Lee, D.; Hess, D.J. Regulations for On-Road Testing of Connected and Automated Vehicles: Assessing the Potential for Global Safety Harmonization. Transp. Res. Part. A Policy Pract. 2020, 136, 85–98. [Google Scholar] [CrossRef]
- Omeiza, D.; Webb, H.; Jirotka, M.; Kunze, L. Explanations in Autonomous Driving: A Survey. IEEE Trans. Intell. Transp. Syst. 2022, 23, 10142–10162. [Google Scholar] [CrossRef]
- Alawadhi, M.; Almazrouie, J.; Kamil, M.; Khalil, K.A. Review and Analysis of the Importance of Autonomous Vehicles Liability: A Systematic Literature Review. Int. J. Syst. Assur. Eng. Manag. 2020, 11, 1227–1249. [Google Scholar] [CrossRef]
- Vermesan, O.; John, R.; Pype, P.; Daalderop, G.; Kriegel, K.; Mitic, G.; Lorentz, V.; Bahr, R.; Sand, H.E.; Bockrath, S.; et al. Automotive Intelligence Embedded in Electric Connected Autonomous and Shared Vehicles Technology for Sustainable Green Mobility. Front. Future Transp. 2021, 2, 688482. [Google Scholar] [CrossRef]
- Lu, Y.; Ma, H.; Smart, E.; Yu, H. Real-Time Performance-Focused Localization Techniques for Autonomous Vehicle: A Review. IEEE Trans. Intell. Transp. Syst. 2022, 23, 6082–6100. [Google Scholar] [CrossRef]
- Sohrabi, S.; Khreis, H.; Lord, D. Impacts of Autonomous Vehicles on Public Health: A Conceptual Model and Policy Recommendations. Sustain. Cities Soc. 2020, 63, 102457. [Google Scholar] [CrossRef]
- Wang, H.; Khajepour, A.; Cao, D.; Liu, T. Ethical Decision Making in Autonomous Vehicles: Challenges and Research Progress. IEEE Intell. Transp. Syst. Mag. 2022, 14, 6–17. [Google Scholar] [CrossRef]
- Othman, K. Exploring the Implications of Autonomous Vehicles: A Comprehensive Review. Innov. Infrastruct. Solut. 2022, 7, 165. [Google Scholar] [CrossRef]
- Xing, Y.; Lv, C.; Cao, D.; Hang, P. Toward Human-Vehicle Collaboration: Review and Perspectives on Human-Centered Collaborative Automated Driving. Transp. Res. Part. C Emerg. Technol. 2021, 128, 103199. [Google Scholar] [CrossRef]
- Benyahya, M.; Collen, A.; Kechagia, S.; Nijdam, N.A. Automated City Shuttles: Mapping the Key Challenges in Cybersecurity, Privacy and Standards to Future Developments. Comput. Secur. 2022, 122, 102904. [Google Scholar] [CrossRef]
| Threat Type | Description | Real-World Examples | Potential Impacts |
|---|---|---|---|
| Remote Hacking | Unauthorized access to vehicle systems via wireless communication | Jeep Cherokee hack (2015) | Vehicle control takeover, disabling functions, safety risks [18] |
| Sensor Manipulation | Interference with sensors like LiDAR, radar, cameras | Tesla autopilot deception (2016) | False obstacle detection, erratic behavior, collisions [19] |
| Data Breaches | Unauthorized access to sensitive data stored or transmitted by the vehicle | Electric vehicle manufacturer server hack (2020) | Privacy violations, identity theft, compromised decision-making [20] |
| DoS Attacks | Overloading vehicle’s systems to disrupt normal operations | DDoS attacks on vehicle-to-infrastructure networks | Performance degradation, connectivity loss, vehicle immobilization [21] |
| Countermeasure | Description | Benefits |
|---|---|---|
| Intrusion Detection Systems | Monitoring network traffic for malicious activity | Real-time threat detection, anomaly identification [64] |
| Encryption | Securing data in transit and at rest | Protects data integrity and confidentiality [65] |
| Regular Updates | OTA updates for software and firmware | Addresses vulnerabilities, enhances functionality [66] |
| Authentication Protocols | Ensuring only authorized access to vehicle systems | Prevents unauthorized access, secures communication [12] |
| Challenge | Description | Examples |
|---|---|---|
| Complexity of AV Systems | Numerous interconnected subsystems and technologies | LiDAR radar, GPS, machine learning [52] |
| Lack of Standardization | No universally accepted cybersecurity standards | Varied security practices, regulatory gaps [114] |
| Latency Issues | Real-time data processing and communication requirements | Encryption delays, threat detection latency [20] |
| Resource Constraints | Limited computational and energy resources | Processing power, energy consumption, cost constraints [115] |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Durlik, I.; Miller, T.; Kostecka, E.; Zwierzewicz, Z.; Łobodzińska, A. Cybersecurity in Autonomous Vehicles—Are We Ready for the Challenge? Electronics 2024, 13, 2654. https://doi.org/10.3390/electronics13132654
Durlik I, Miller T, Kostecka E, Zwierzewicz Z, Łobodzińska A. Cybersecurity in Autonomous Vehicles—Are We Ready for the Challenge? Electronics. 2024; 13(13):2654. https://doi.org/10.3390/electronics13132654
Chicago/Turabian StyleDurlik, Irmina, Tymoteusz Miller, Ewelina Kostecka, Zenon Zwierzewicz, and Adrianna Łobodzińska. 2024. "Cybersecurity in Autonomous Vehicles—Are We Ready for the Challenge?" Electronics 13, no. 13: 2654. https://doi.org/10.3390/electronics13132654
APA StyleDurlik, I., Miller, T., Kostecka, E., Zwierzewicz, Z., & Łobodzińska, A. (2024). Cybersecurity in Autonomous Vehicles—Are We Ready for the Challenge? Electronics, 13(13), 2654. https://doi.org/10.3390/electronics13132654







