1. Introduction
All over the world, the internet is moving rapidly towards Internet Protocol version 6 (IPv6) address architectures, with the support of virtualization architectures such as Software-Defined Networks (SDNs) and Network Function Virtualization (NFV) [
1]. The IPv6 address architecture provides a large IP address range, efficient segment routing, built-in security, and mobility features [
2]. The industrial revolution and technological enhancement in mobile communication have changed the traditional way of networking and have introduced the term “Industrial Internet of Everything (IIoE)”. The Internet of Everything (IoE) is a network connection of people, processes, data, and things [
3,
4]. Smart homes, smart cities, smart industry, and smart education are some projects of the IoE [
5,
6]. In the IoE, billions of smart devices and people are connected and exchange data with the help of several applications. Due to the increase in applications on different IoE-based smart networks, security threats have also increased [
7]. The communication links between people or from one machine to another machine are insecure, so authentication and confidentiality are significant concerns [
8].
A Next-Generation Network (NGN) transports information and services at a very high speed through software-based devices instead of dedicated physical devices [
9]. Data communication services are provided through NFV and SDNs in the NGN. NFV is a new concept and an emerging technology that was introduced in 2012 [
10]. The main objectives of NFV are to eliminate hardware equipment and to deliver networking services like routing, security, storage, etc., through software-based virtual machines (VMs). NFV gives many advantages, such as decreasing equipment expenses, the platform’s openness, improved overall performance, efficient operations, scalability, flexibility, and short production cycles [
11].
The IPv6 address architecture provides security services, including extension headers [
12]. But some attacks, such as man-in-the-middle (MITM) attacks, impersonation attacks, and replay attacks affect the IPv6 architecture [
13]. In an MITM attack, an intruder is secretly involved between two communicating parties [
14]. The sender or receiver does not verify the legitimacy of the source and replies to the attacker. Authentication and data confidentiality are compromised due to the MITM attack [
15,
16]. Authentication is a technique for the legitimate identification of someone or a device [
17]. Confidentiality means that the personal data that might be dispatched with the aid of the sender is not made available or disclosed to unauthorized persons during conversations [
18].
1.1. Motivation and Contribution
Although many asymmetric key-based or symmetric key-based secure systems are available to provide security services, the available secure systems follow computationally complex procedures. Therefore, computation and communication overheads are increased. The objective of this research is to propose a lightweight and certificateless client–server secure communication system that provides authentication, data confidentiality, and data integrity services with low/reduced computation and communication overheads.
The major contributions of the paper are described as follows:
We introduce a lightweight symmetric-session-key exchange algorithm for the client–server network model.
We propose an authentication scheme by using the Hash-based Message Authentication Code (HMAC) algorithm with a symmetric session key to identify the receiver and the sender.
We use an Advanced Encryption Standard (AES) algorithm with an initially symmetric session key of 128 bits in length to provide data confidentiality and the Secure Hash Algorithm 2 (SHA-2) with a 256-bit digest (SHA-2-256) for data integrity.
We exhibit the security analysis of our proposed client–server secure communication scheme.
We use Graphical Network Simulator-3 (GNS3) and Oracle VirtualBox manager 6.1 to design NFV-based IPv4-IPv6 virtual networks and implement our proposed security scheme on Linux-based Lubuntu 20.04 Long-Term Support (LTS) virtual machines through Java programming.
We compare our proposed security scheme with other security schemes with regard to computation and communication costs.
Finally, we measure and analyze the performance of our proposed security scheme over the NFV-based IPv4 and IPv6 virtual networks based on several parameters, such as throughput, delays, and packet loss.
1.2. Organization of the Paper
The remaining portion of the paper is structured as follows:
Section 2 presents related works and highlights the weaknesses of existing studies.
Section 3 describes our proposed end-to-end secure communication scheme.
Section 4 presents formal and informal security analysis.
Section 5 shows the implementation, comparisons of the results, and performance evaluation. Eventually,
Section 6 concludes the paper.
2. Related Work
Authentication and data confidentiality services with asymmetric keys are vulnerable in the single form [
19]. Asymmetric key-based security systems provide data confidentiality and authentication services together. So they increase the computation cost and communication time. Therefore, they are considered too heavyweight for smart devices. Rivest–Shamir–Adleman (RSA) and Elliptic Curve Cryptography (ECC) are the two most famous asymmetric key generation algorithms. Researchers proposed mutual authentication schemes using the RSA algorithm in [
20,
21,
22,
23]. The RSA algorithm generates key pairs slowly as compared to ECC [
24]. So RSA-based security systems are not suitable for lightweight devices.
In [
25,
26], the researchers introduced mutual authentication schemes using ECC. The schemes adopted complex procedures for authentication. So this also increases computation and communication costs. ECC is threatened by numerous attacks, including twist-security attacks, easy-timing attacks, and facet-channel attacks [
27]. The major drawback of ECC is that it is not easily implemented. So these security models are not feasible for smart devices.
In [
28], the researchers proposed an end-to-end secure communication framework for smart devices. The proposed framework provides authentication and encryption services by using a pre-shared key. This framework is not suitable for smart devices because the framework adopted computationally complex procedures for authentication. The proposed framework did not exhibit formal or informal proof against known attacks such as MITM attacks, impersonation attacks, or replay attacks.
In [
29], the researchers added a comfortable remote consumer authentication scheme for the smart home environment. The stated authentication scheme uses multiple hashing and XOR functions during the whole process. The said scheme provides security against replay attacks, eavesdropping attacks, smartphone device loss attacks, impersonation attacks, session key guessing attacks, and MITM attacks. The authors proved the security of the proposed scheme through Burrows–Abadi–Needham (BAN) logic and the Automated Validation of Internet Security Protocols and Applications (AVISPA) tool. The said authentication scheme increases computation and communication overhead for smart devices. Therefore, the said authentication scheme is not recommended for smart home environments.
In [
30], the researchers proposed a hash-based authentication and key exchange protocol for the Industrial Internet of Things (IIoT). The proposed scheme achieves mutual authentication and key establishment whilst ensuring the anonymity of identities. The said scheme is stated as lightweight and effective due to limited computational overhead and resistance against many significant attacks. Although the scheme is declared robust through the AVISPA tool, the said scheme does not ensure privacy. However, the stated scheme does not employ any ciphering version. The said scheme adopted a very complicated key agreement and mutual authentication method that increased the computation time as well as the communication time. In this scheme, the large size of messages exchanged during conversations overburdens the overall scheme. Thus, the stated scheme is not considered to be lightweight.
In [
31], the researchers introduced a lightweight key exchange and physically secure mutual authentication protocol for Industrial Wireless Sensor Networks (IWSNs). The proposed protocol uses multiple iterations of one-way hash functions, physically unclonable functions (PUFs), and bitwise exclusive operations during the key exchange and authentication process. The researchers evaluated their proposed security protocol on the real-or-random (ROR) model. The proposed security model provides security services against several known attacks, but the security model adopted a complicated procedure for authentication. It consumed a large amount of time. So it is not recommended for wireless devices.
In [
32], the researchers proposed a symmetric key agreement protocol and lightweight XOR-based authentication scheme named A2P for vehicle-to-smart-grid networks. The proposed scheme reduced the load on the grid. The proposed scheme provides security services against DoS attacks, replay attacks, and MITM attacks. The researchers proved their proposed authentication scheme through informal and formal security analyses through the AVISPA tool. This scheme also adopted complex mathematical techniques during the key agreement and pseudonym update phase. Therefore, this scheme increased the computational time of the key agreement phase.
Most of the existing security systems consist of computationally complex algorithms, and they require extra time to process, while some systems do not offer the claimed robust protection against safety assaults. A comparative analysis based on computation and communication costs between existing security models is shown in
Table 1. After assessing the existing research, we recommend and enforce a strong, lightweight (in terms of computation and conversation costs), and end-to-end secure communication model. Our proposed secure communication scheme provides mutual authentication and data confidentiality services by using a pre-shared key. IPsec also provides these security services [
33] on the network layer, with high costs in terms of computation and communication.
3. Proposed Secure Communication Model
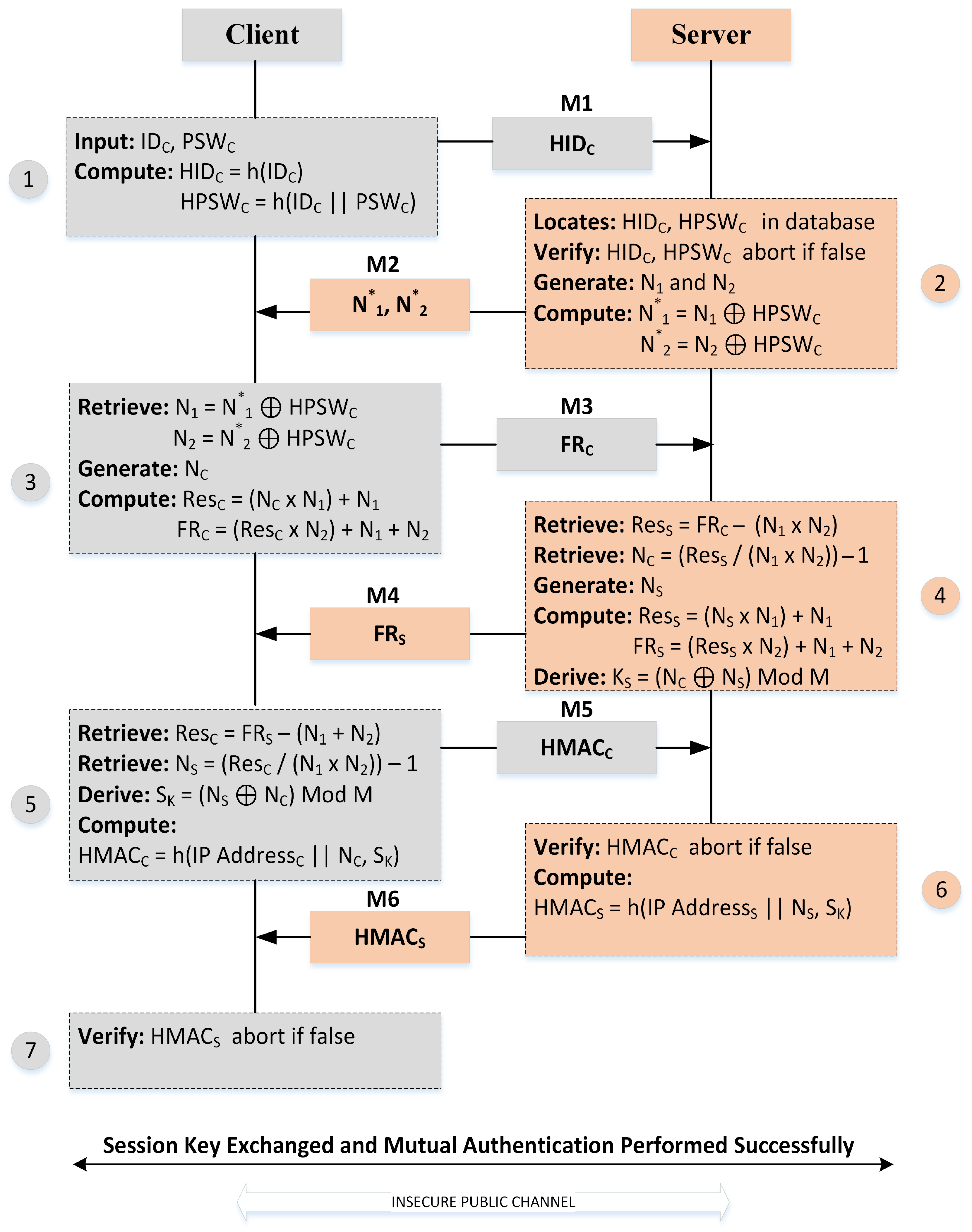
The primary goal of our proposed secure communication scheme is to provide authentication and data confidentiality services in the client–server network model so that the MITM’s interception will fail. After the client–server connection is established, our proposed security scheme performs. The process state diagram of our proposed client–server security model is shown in
Figure 1. Our proposed security scheme consists of several phases. All of the phases are discussed in detail in [
34].
Table 2 describes the notations and their descriptions.
3.1. User Registration Phase
During the user registration phase, the user’s credentials, such as hash-based identity, hash-based password, name, address, phone number, and email address, are saved on the server’s database. The user as a client picks an identity as
and a password as
. The client calculates the hash-based identity
and hash-based password
as described in Equation (
1) and Equation (
2), respectively.
3.2. Login Phase
The user as a client C sends his hash-based identity to the server S for verification. The server locates the hash-based password from the database against a given identity. If the given identity is not located, then the server terminates the connection. If the server locates the hash-based password against the given identity, then the server generates two large random numbers and . The server calculates = (⊕), = (⊕) and sends , to the user.
3.3. Session Key Exchange Phase
The next step is to exchange the secret key between the server and the client. A bigger key length reduces the threat of brute-force attacks [
35]. We proposed a robust and lightweight symmetric key exchange algorithm [
36]. Initially, the key size is 128 bits. However, the proposed key exchange algorithm supports larger key sizes such as 1024 bits or more without modification. A bigger key size also reduces post-quantum resistance [
37].
3.4. Authentication Phase
The next step is to authenticate the sender and the receiver. We use the HMAC algorithm, which uses a hashing function along with a symmetric session key
that is exchanged between the sender and receiver for authentication [
38]. The HMAC size depends on the hashing algorithm [
39]. We use the (SHA-2-256) algorithm with a symmetric session key, concatenation with a random number generated by the device, and the IP address of the device for mutual authentication as described in Equation (
3) and Equation (
4), respectively.
Figure 2 shows the key exchange and authentication processes.
3.5. Secret Data Transmission
After the mutual authentication process has been done, the next process is to send or receive data secretly. For encryption and decryption, we use the AES algorithm with the symmetric session key as described in Equation (
5) and Equation (
6), respectively.
The working of AES is fast [
40]. AES provides services in different block cipher modes (at least 10) of operation [
41]. The comparative results between the five different modes indicate that the electronic code block (ECB) consumes less execution time in encryption and decryption processes based on the software and hardware specifications that were used during experiments [
42].
3.6. Data Integrity
To ensure data integrity, remote users and the server send or receive hash values along with the data. The hash value is calculated by using any hashing algorithm, such as (SHA-2-256), along with the key, as shown in Equation (
7). Hashing is a one-way process [
43]. On the receiving end, the receiver calculates the hash value and compares it to what was received. If both hash values are the same, it means the data were not altered. If both hash values are not the same, then it means that the data were altered.
4. Security Analysis
We show the robustness of our proposed end-to-end secure client–server communication scheme against MITM attacks and impersonation attacks through informal and formal security analyses.
4.1. Security against Impersonation Attacks
In our proposed system, the client sends a hash-based identity as instead of the identity in clear text. On the server side, the server locates in the database. If the given identity is incorrect, then the server terminates the connection immediately. Multiple wrong attempts block the identity temporarily. The size of the hash-based identity is large. So brute-force and spoofing attacks fail.
4.2. Security against Replay Attacks
Using the random nonce concept, our proposed security scheme provides safety against replay attacks. The random nonce will be changed on every newly established connection between the client and the server.
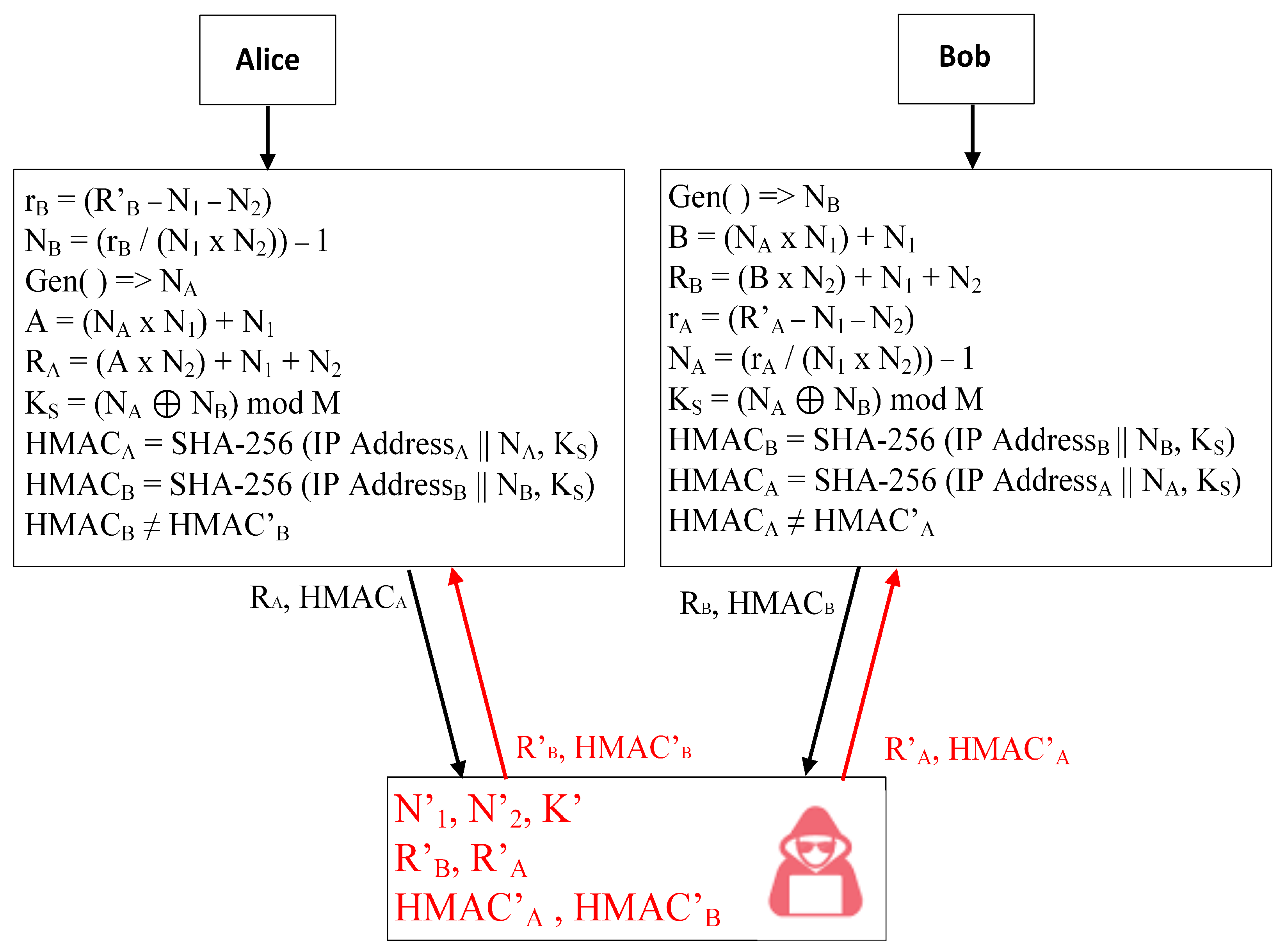
4.3. Safety against MITM Attacks
The client and the server authenticated each other using the combination of a pre-shared key, the IP address of the party, and a random number generated by the party. The values of
,
,
, and
are hidden to adversaries. Similarly, the pre-shared symmetric key is also hidden from adversaries. The pre-shared key’s value changes every time. The client and the server send only
and
to each other. The attacker only knows
,
,
,
,
, and
, as shown in
Table 3. If the adversary sends a fake hash value, it is detected easily during the authentication process, as shown in
Figure 3.
4.4. Safety against Side-Channel Attacks
Side-channel attacks (SCAs) are timing attacks. In SCAs, the attacker gains information from the physical implementation of a computer system rather than exploiting software vulnerabilities [
44]. The clock randomization technique is an old method of countermeasure against side-channel attacks [
45]. Our proposed security scheme is safe against SCAs because our key exchange algorithm shows constant time behavior [
36]. In addition, the SHA module is also safe against SCAs because we use SHA in HMAC along with a large symmetric session key.
4.5. Safety against Quantum Computers
Post-quantum cryptography (PQC) is another fundamental security aspect of current scientific phenomena [
46]. Authentication, hashing, and cryptography algorithms provide security against post-quantum resistance by having large keys [
34]. Our proposed security scheme is safe against post-quantum resistance because our key exchange algorithm can exchange a large key size such as 1024 bits or more without modification.
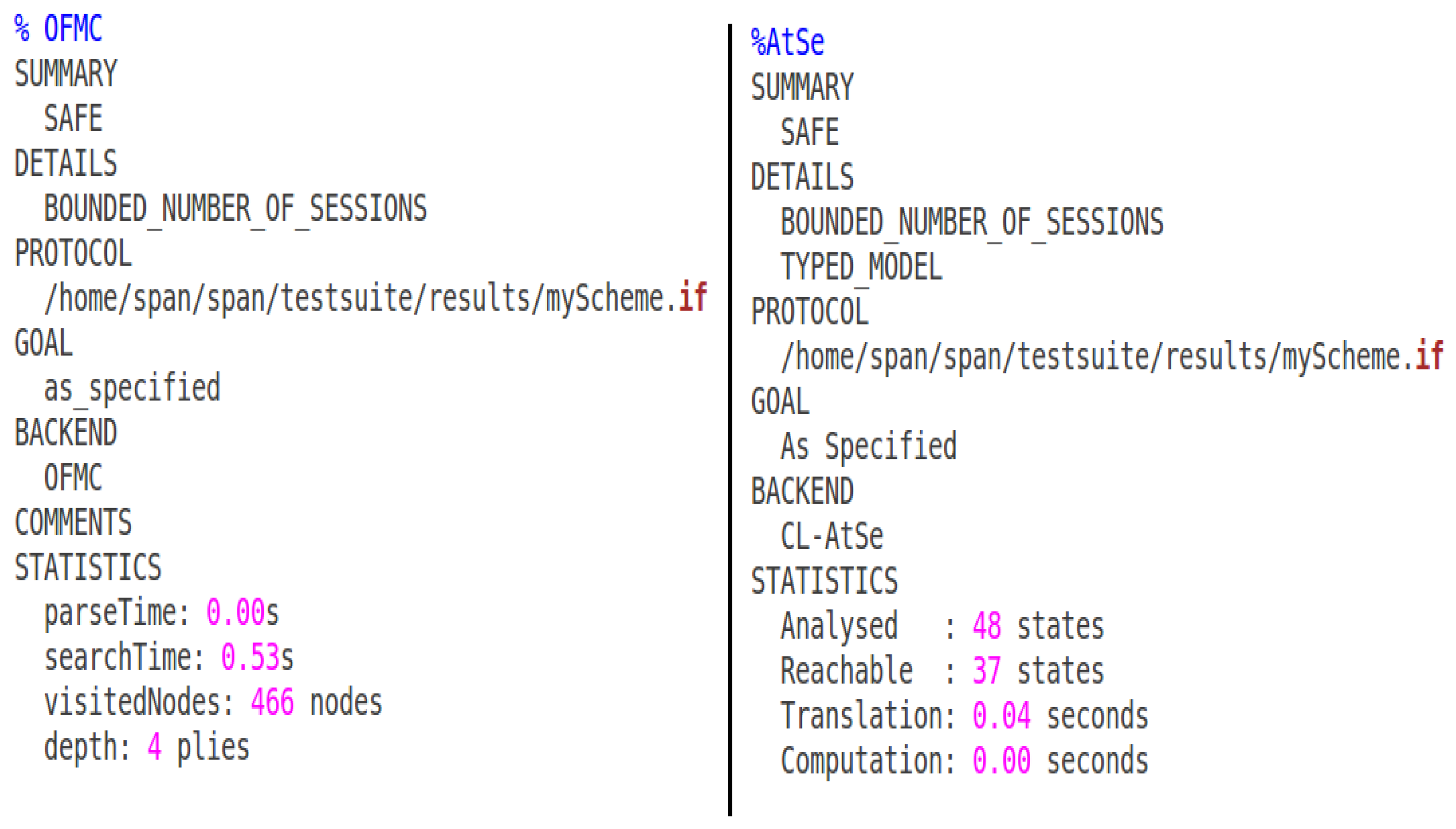
4.6. Formal Security Analysis through AVISPA
We used the AVISPA tool to examine the robustness of our proposed security scheme against MITM attacks and impersonation attacks. AVISPA is a dependable and open-source tool. It is used to check the safety of several types of security protocols and schemes that contain messages exchanged between two or more nodes [
47]. AVISPA adopts the Doley–Yao (DY) adversary model in which the communication channels that are used between nodes are compromised and liable to all forms of attacks [
48].
4.6.1. Server Role
The server issues the IDs and password and sends two randomly generated large numbers
and
. Symmetric key exchange and authentication processes are also performed by the server. The AVISPA code and other relevant configuration files are available on GitHub [
49].
4.6.2. Client Role
The client sends a request to the server for login, key exchange, and mutual authentication.
4.6.3. Results through AVISPA
The robustness of our designed cozy communication version in opposition to a couple of intense assaults has been validated using the OFMC and CL-AtSe on the backend and became safe, as shown in
Figure 4.
5. Implementation over NFV-Based Virtual Networks and Performance Analysis
We implement our proposed secure end-to-end communication scheme on Linux-based Lubuntu virtual machines by using socket programming in Java with built-in Java packages such as java.io.* and java.net.* integrated on the GNS3 simulator. The system specifications are: HP EliteBook 840 G3 series, Intel(R) Core i5-6300U 2.4 GHz processor, 16 GB DDR4 RAM, 3 MB cache memory, and 64-bit Windows 10 Professional operating system.
5.1. NFV
NFV is a rising technology that was introduced recently and is quickly becoming a part of the Internet due to its many benefits. NFV is changing the shape of networks. NFV is used to convert networking functions from committed hardware appliances to primarily software-based packages [
50]. NFV provides network functionality and services through one or more VMs that may run on different high-volume servers and software. For example, a virtual firewall could be deployed on a high-volume server to protect the network without installing and mounting a physically dedicated security device. Similarly, many other examples of NFV include virtualized routers, intrusion detection/prevention devices, load balancers, WAN accelerators, and session border controllers [
51]. It is used to design, deploy, and manage network services with lower cost and energy consumption by decoupling proprietary physical network equipment [
10].
5.2. Experimental Setup
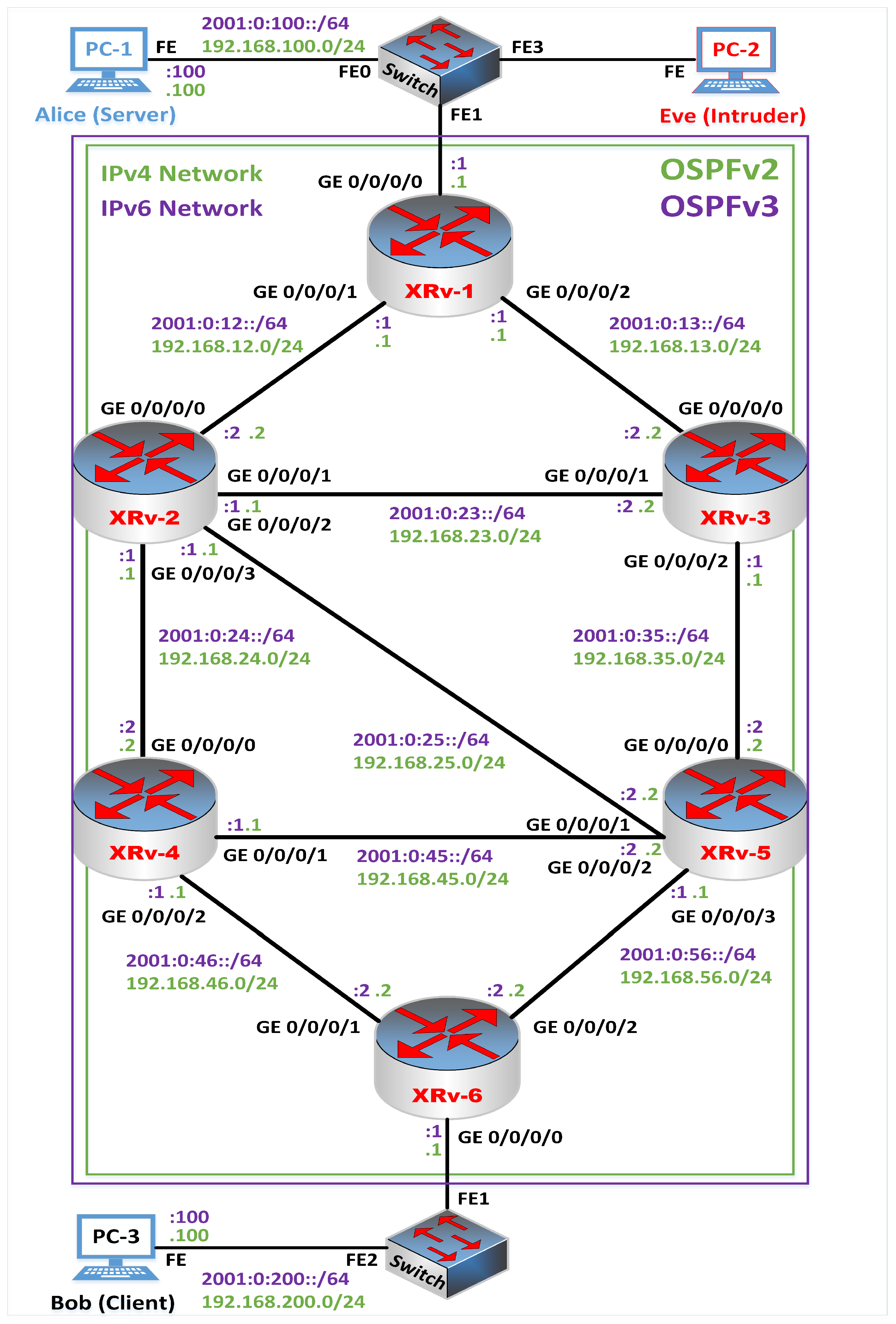
The experimental design is shown in
Figure 5. Our virtual network consists of 6 virtual routers, 2 virtual layer-2 switches, and 3 virtual hosts. The virtual routers are supported by IPv4 and IPv6 and are connected with Gigabit Ethernet as a mesh topology. The outline of the devices that were used in the experiments is shown in
Table 4. A Cisco IOS XRv router is installed on a virtual machine through VirtualBox and is integrated with the GNS3 simulator. The virtual machine consists of 4 GB RAM and 2 processors. It reduces the equipment cost. PC-1 acts as a server, and PC-3 acts as a client, while PC-2 acts as an intruder. The intruder controls the communication network fully. Both virtual machines run a Linux-based Lubuntu 20.04 LTS operating system installed as a VM through Oracle VM VirtualBox manager and integrated with the GNS3 simulator. Lubuntu is a lightweight operating system [
52]. The Open Shortest Path First (OSPF) routing protocol is configured for both the IPv4 and IPv6 networks for dynamic routing.
Socket programming is a technique for connecting two or more nodes on a network to communicate with each other [
53]. The virtual machine PC-1 runs the server.java program, while PC-3 runs the client.java program for client–server communication. Suppose the server sent
= 79 and
= 95 to the client. The client picked
= 60, and the server picked
= 35. M = 128. The pre-shared session key
= 31. The binary value of the pre-shared key is “11111”. An identical system is carried out for bigger symmetric keys. The key exchange, mutual authentication processes, and encryption or decryption between the client and the server on the IPv6 network are shown in
Figure 6 and
Figure 7, respectively.
5.3. Computation Cost Comparisons
We compare our designed secure communication scheme with existing schemes based on predicted computation cost. The computation results come after performing multiple mathematical or computing operations that are finished at some point in the key exchange and authentication process.
Table 5 shows the unit times for numerous operations that were performed throughout the execution. We suppose ECC with a 32-byte key length and SHA-256 as a hash function. The predicted calculated computation value of our proposed scheme is 4
+ 6
+ 3
+ 22
on both sides.
Table 6 shows the comparison results for the computational costs for our designed scheme and most related schemes. The table shows that our designed secure scheme decreased the computation cost by up to 38.87% compared to the method in [
29].
5.4. Communication Cost Comparisons
We compared our designed secure communication scheme with existing schemes based on transmitted messages on both sides. To make a reasonable comparison, we defined the lengths of different messages’ variable timestamps, random numbers, IDs, hash values, EC points, and encryption/decryption as 32 bits, 128 bits, 128 bits, 256 bits, 320 bits, and 512 bits, respectively. The anticipated overall calculated conversation value of our designed scheme is 1280 bits (160 bytes) for six messages that cross both facets.
Table 7 displays the comparative results for our proposed safety scheme and other current models. The table shows that our designed secure system decreased communication cost by up to 26.08% compared to the method in [
29].
5.5. Comparison with IPsec
IPsec is a protocol suite that provides security services such as key exchange, authentication, data confidentiality, and data integrity on the network layer of the OSI model using a combination of different protocols. IPsec works in two modes. One is called “transport mode”, while the second is called “tunnel mode”. IPsec encapsulates the data with additional headers such as Encapsulating Security Payload (ESP), Authentication Header (AH), and Internet Key Exchange (IKE) [
54]. It increases overhead for resource-constrained IoT-enabled smart devices. IPsec provides authentication with digital certificates by using the asymmetric key. This method consumes extra time and is not suitable for resource-constrained devices.
In IPsec, the DH key exchange algorithm is used for symmetric key exchange as a common practice. The DH key exchange algorithm is not self-authenticated and is vulnerable to MITM attacks [
36]. The enhanced version of DH increases the key exchange time because the complexity behavior of the DH is polynomial. Our proposed secure system is most applicable in smart homes and smart healthcare systems where small IoT-enabled devices and sensors are used.
5.6. Experimental Results over IPv4-IPv6
Data were captured through the network commands during experiments. All experiments were done several times (5–7) at alternative times, then we picked the mean of the results.
5.6.1. Connectivity and Traffic Path
The “ping” command is used to check the connectivity of the devices on the network. The ping command sends an Internet Control Message Protocol (ICMP) echo request to the receiver, and the receiver sends the echo reply to the sender over the network [
55]. If the sender receives a response from the receiver, then this ensures that connection has been established. We tested connectivity from PC-1 to PC-3 over the NFV-based IPv4-IPv6 networks by using the ping command. Similarly, the “trace” command is used to check the traffic path between the sender and the receiver over the network. The path shows the total number of hops from the source to the destination with the time in milliseconds for each node. Most of the time, multiple paths exist between the sender and receiver. The routing protocol selects the best path if various paths exist. In our experimental setup, multiple paths are available from PC-1 to PC-3. Using the trace command, we discovered the path from PC-1 to PC-3 over the NFV-based IPv4-IPv6 networks. The route XRv-1 → XRv-3 → XRv-5 → XRv-6 was followed.
Figure 8 shows the connectivity and traffic path from PC-1 to PC-3.
5.6.2. Round Trip Time
We measured the average round trip times (RTTs) of different sizes of messages that passed over the hybrid IPv4-IPv6 NFV-based virtual networks during communication by using the simple ping command. The RTT is the full time it takes for a packet to be dispatched plus the amount of time it takes for an acknowledgment that the packet was received [
56]. It is based on queuing delays in routers and processing at the end system. More put-off and heavy congestion will cause the packet to drop [
57].
Table 8 shows the total time, minimum, maximum, average, standard deviation (SD), and coefficient of variation (CV) of the RTT from PC-1 to PC-3 with different sizes of packets passed over NFV-based IPv4 and IPv6 virtual networks. The experimental results show that the performance of IPv6 is better than the performance of IPv4 based on the CV.
5.6.3. Packet Loss
Packet loss is when any packet does not reach its destination for any reason. Packet loss takes place due to errors in transmission statistics, buffer overflow, or congestion [
58]. Various sizes of the 100 packets of ICMP were sent to calculate the packet loss ratio.
Table 9 shows the packet loss ratios for different sizes of packets from PC-1 to PC-3 passed over both IPv4 and IPv6 NFV-based virtual networks. The results show that packet loss for smaller packets is zero, while for 64 KByte packets, the packet loss ratio in IPv6 is comparatively high as compared to IPv4. For fixed window sizes, when multiple heavy sizes of packets arrive, then due to queuing delays, processing delays, and propagation delays, packets are lost.
The successful execution, robustness verification, and comparative analyses proved the supremacy of the proposed secure communication scheme in contrast to the traditional approaches over large-scale NFV-based hybrid IPv4-IPv6 virtual networks.