StructuredFuzzer: Fuzzing Structured Text-Based Control Logic Applications
Abstract
1. Introduction
- A fuzzing framework for PLC control logic applications written in ST specified by the IEC 61131-3 [16] standard. It is worth noting that the IEC 61131-3 standard is widely recognized in the industry and defines the syntax and semantics for textual and graphical programming languages for PLCs such as ST and LL or Ladder Diagram (LD). This standardization ensures that the programs are portable across different PLC vendors. Our work, therefore, extends fuzzing to a broad range of real-world PLC applications. The novelty lies in the framework’s ability to guide the fuzzing process to fuzz internal logical flaws, thus potentially augmenting the robustness of ICS devices against external threats. This has been found crucial since ST is a widely utilized language in PLC programming, yet effective fuzzing tools specifically designed and optimized for such languages have been lacking. This framework can be a valuable tool for detecting bugs and verifying the correctness of ST programs based on a specification.
- A custom PLC runtime is integrated into the fuzzing process. This is unique, as it provides contextual execution information for ST applications, permitting a more targeted and efficient fuzzing process. This substantially improves upon conventional techniques in which the runtime and fuzzing components frequently operate in isolation.
- A custom fuzzer for effective input generation is explicitly designed to generate inputs for fuzzing ST-based control logic applications. This fuzzer’s utility stems from its competence in generating diverse inputs, considering the program’s context, thereby enhancing the chance of uncovering vulnerabilities that might otherwise be overlooked by a generic fuzzer.
- An evaluation of the efficacy of our framework is performed using a collection of carefully crafted ST programs. This rigorous evaluation reinforces confidence in our proposed framework’s utility and presents a benchmark for future research in this area.
2. Background
2.1. Programmable Logic Controllers
- Structured Text (ST): A high-level, block-structured language resembling Pascal or C, used for complex tasks that may be cumbersome to implement with graphical languages.
- Ladder logic (LL): A graphical language representing control logic in a form that emulates electrical relay logic, making it intuitive for electricians and technicians.
- Sequential Function Chart (SFC): This graphical programming language is used for designing sequential control systems and complex program structures with multiple distinct states and transitions.
- Function Block Diagram (FBD): Another graphical language that represents functions between input and output variables using blocks connected by lines, similar to electronic circuit diagrams.
2.2. Fuzzing
2.3. Motivating Examples
| Listing 1. Example of a logical bug in a control logic application for an automated temperature control system. |
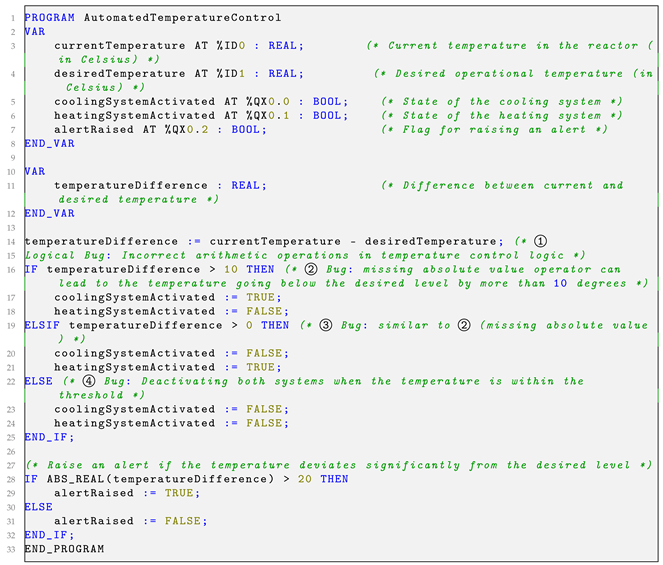 |
| Listing 2. Example of a logical bug in a control logic application for an automated reactor control system. |
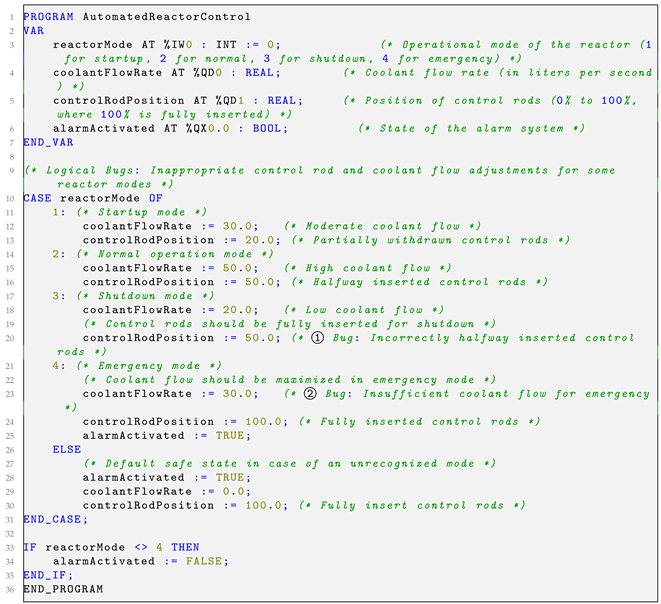 |
3. Proposed Fuzzing Framework
3.1. Challenges in Fuzzing PLCs Control Applications
- PLC Programming Languages and Runtime: Despite its potential, fuzzing has been underutilized in the ICS domain, mainly due to the unique challenges posed by the specialized nature of ICS programming languages and the real-time constraints under which these systems operate. PLC control binaries are compiled into specific formats for each vendor, which makes it tedious to apply a general analysis technique to secure them. The lack of standardization of the PLC runtime environments greatly exacerbates this issue. Specifically, the runtime is the software environment, running as a process of the PLC operating system (OS) in which the control logic is executed. It is responsible not only for executing the applications but also for interfacing with the physical I/O modules. Therefore, the lack of standardization of the runtime environments makes it challenging to develop a general-purpose fuzzer for control logic applications. Additionally, the runtime is itself often proprietary and closed-source, rendering the development of a fuzzer that can work across different PLC vendors even more difficult. Since the PLC runtime is often tightly integrated with the I/O modules, dissociating and fuzzing each one independently is quite cumbersome. Finally, the runtime is often optimized for real-time performance, which makes it nearly impossible to fuzz the control logic without a degradation in the performance of the PLC [3].
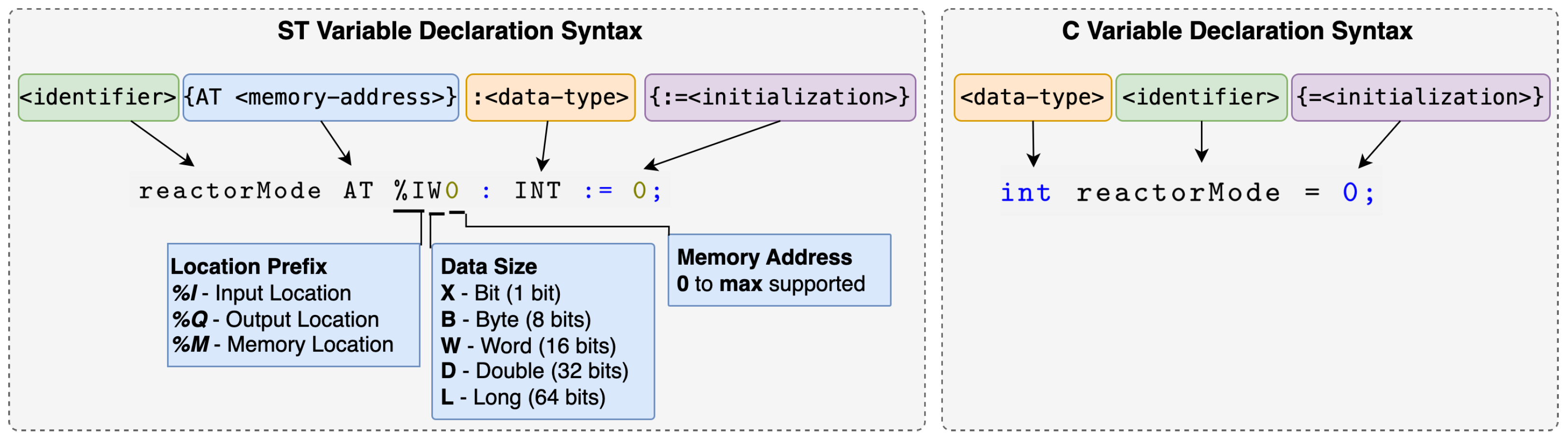
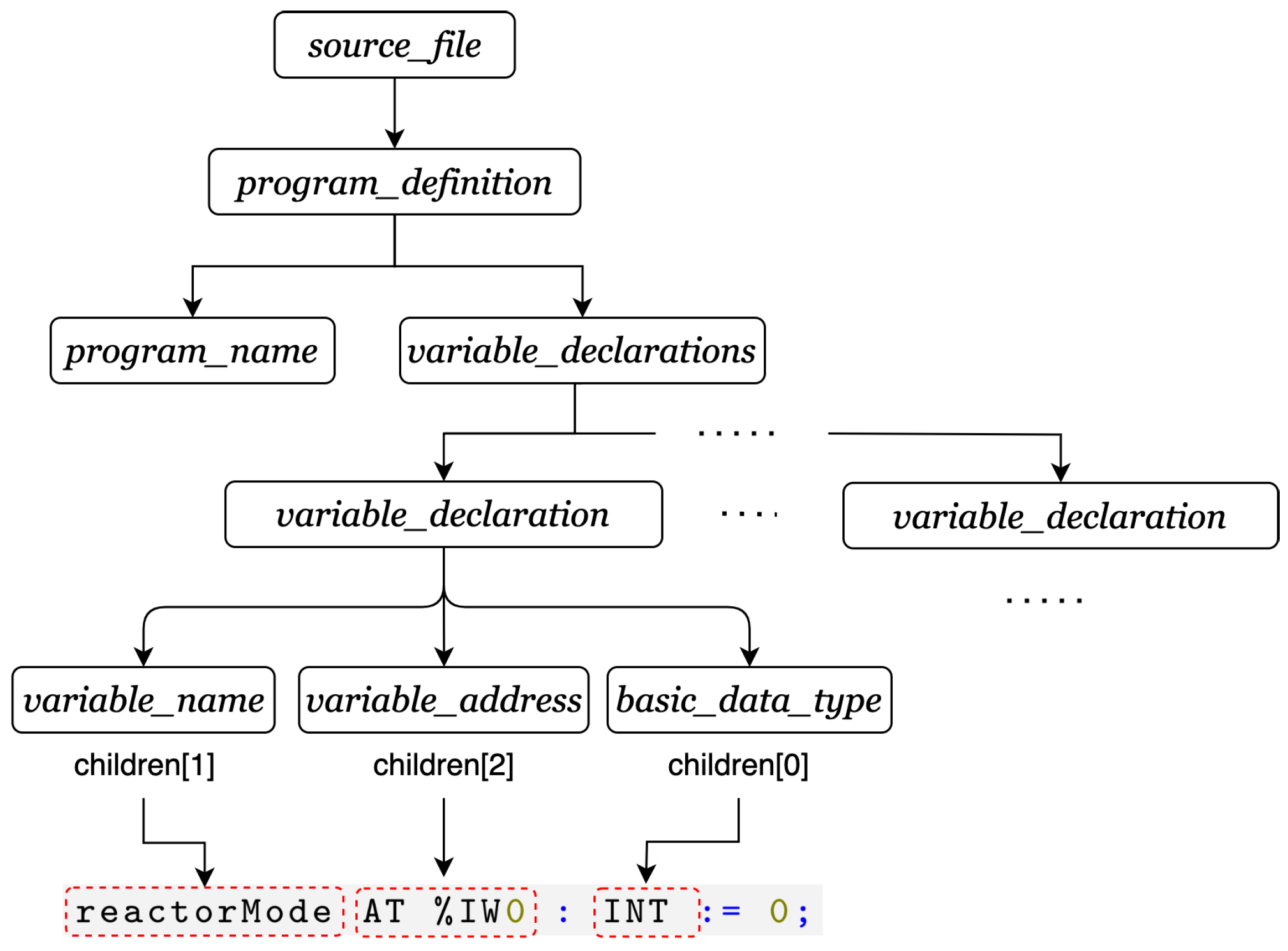
- Complex Input Structures: Unlike traditional programming languages like C, ST requires explicit memory and I/O addressing during variable declaration as shown in Figure 2. Nevertheless, memory addressing is specific to the hardware of the target device in ST, in contrast to C, which is generally portable.
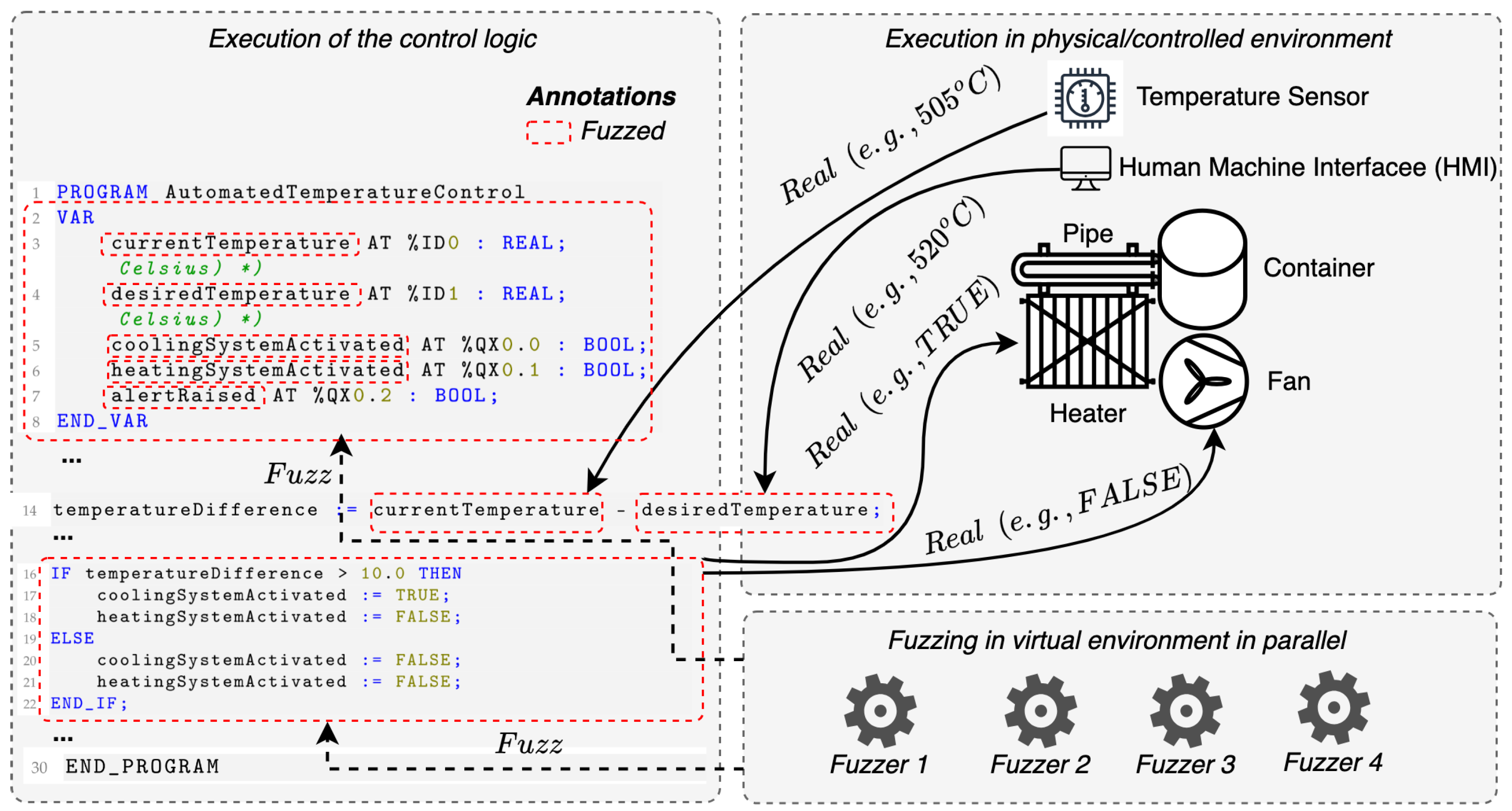
- Physical Process Interactions and Safety Concerns: PLC roles typically involve perceiving changes in the physical environment and controlling or influencing them. This means that ST applications frequently interact with physical processes, which directly affects the status of machinery. Generally, during the fuzzing process, valid inputs are extensively altered, potentially leading to software crashes of the test target. However, in cases where the target interacts with a physical process, such inputs may have calamitous consequences. Therefore, to maintain the system’s safety and reliability, it is critical to identify these issues in advance, possibly even offline, without interacting with the environment.
3.2. Proposed Framework Overview
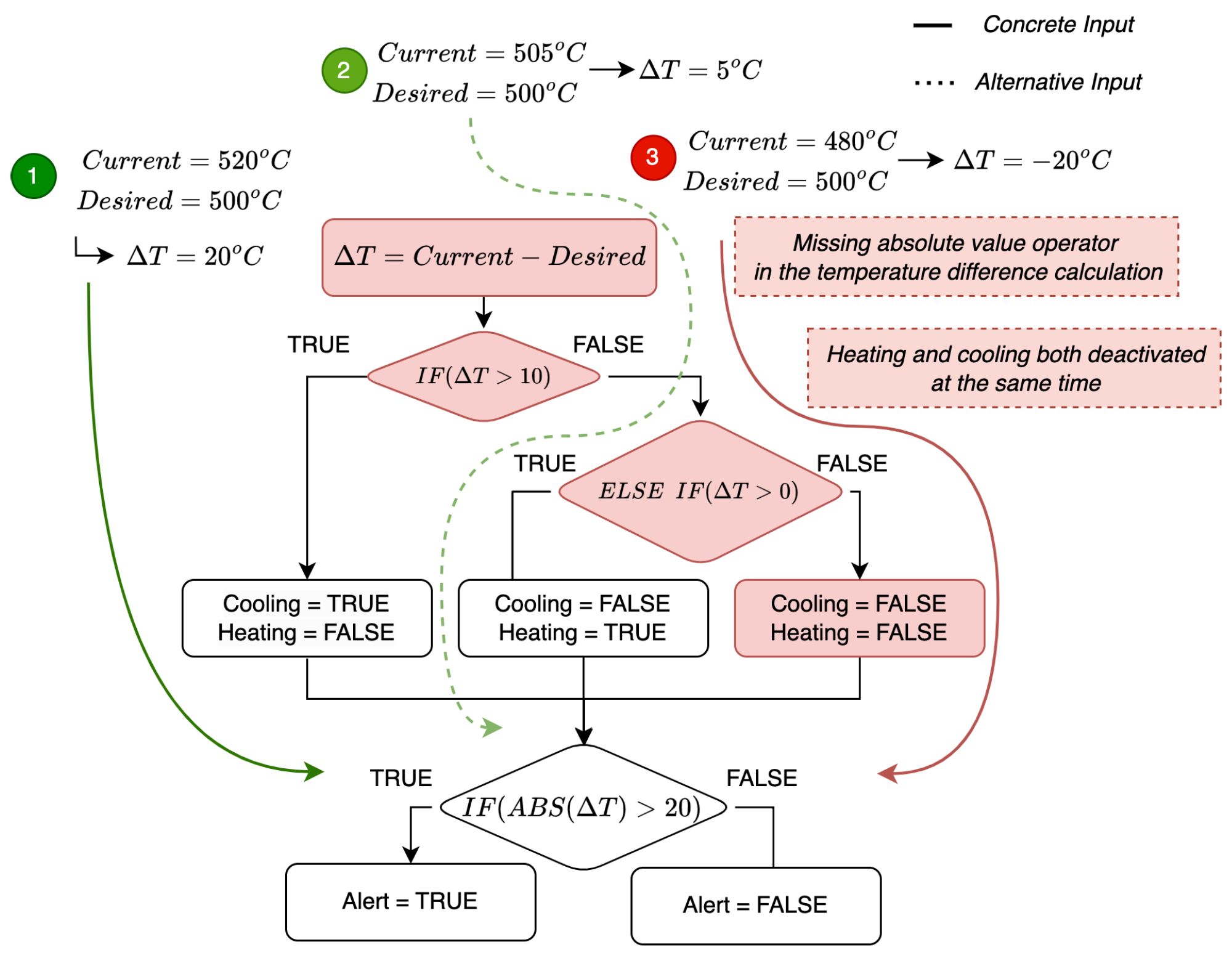
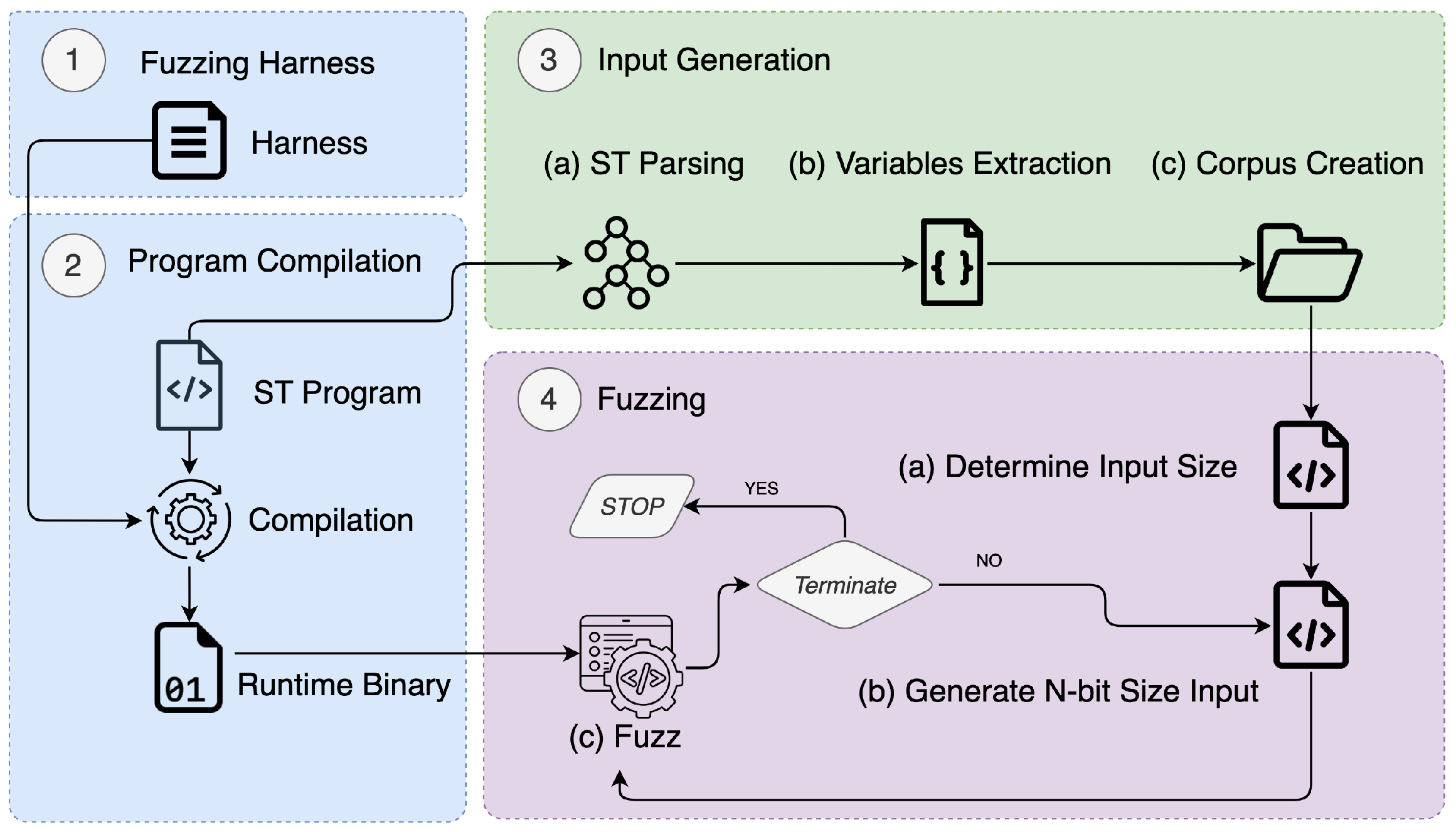
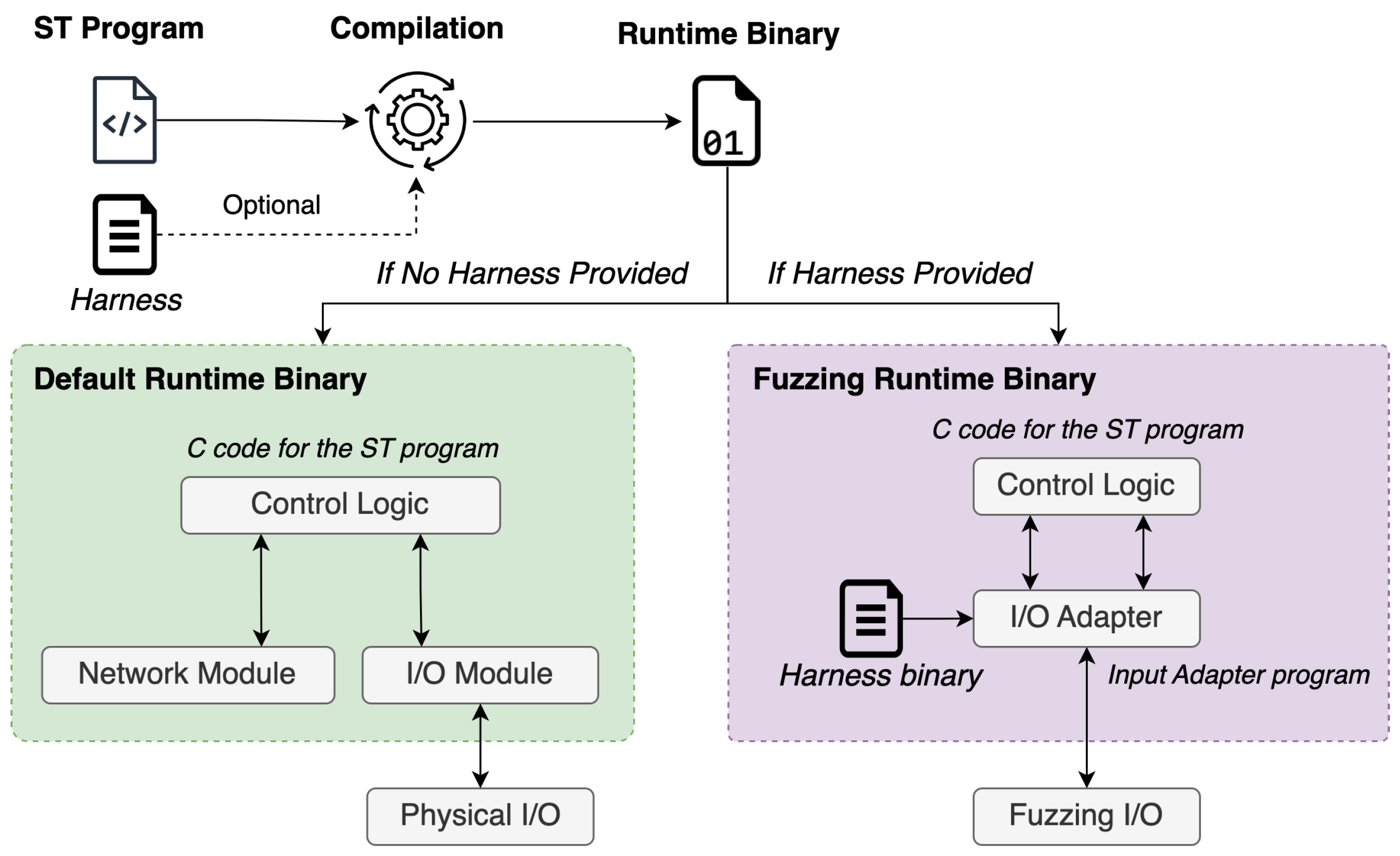
- Step 1: Specifying a Fuzzing Harness (Optional): The first step involves creating a harness, i.e., a user-defined set of specifications regarding the correctness of the target ST programs. In particular, the harness should provide input restrictions that are considered valid when certain outputs are observed, or the system is in certain states. If these are violated, then it is assumed that it is due to a bug. Therefore, a code for signaling a fuzzer about this should exist. The latter can be achieved through code that aborts the execution of the program or emulates a crash. Thus, the harness can be implemented in C to express some violations of the desired program’s behavior (specifications) as assertion failures. Listing 3 provides an example of a harness for the automated temperature control system application. Precisely, it specifies invalid states or conditions (violations) as crashes that the fuzzer can detect, i.e., those that deviate from the specifications ➀ to ➃. The above-described step is optional, and it typically occurs when the fuzzing process is meant to be conducted offline and in the absence of a controlled environment.
| Listing 3. Example of a harness for the automated temperature control system application for a desired temperature of 500 °C |
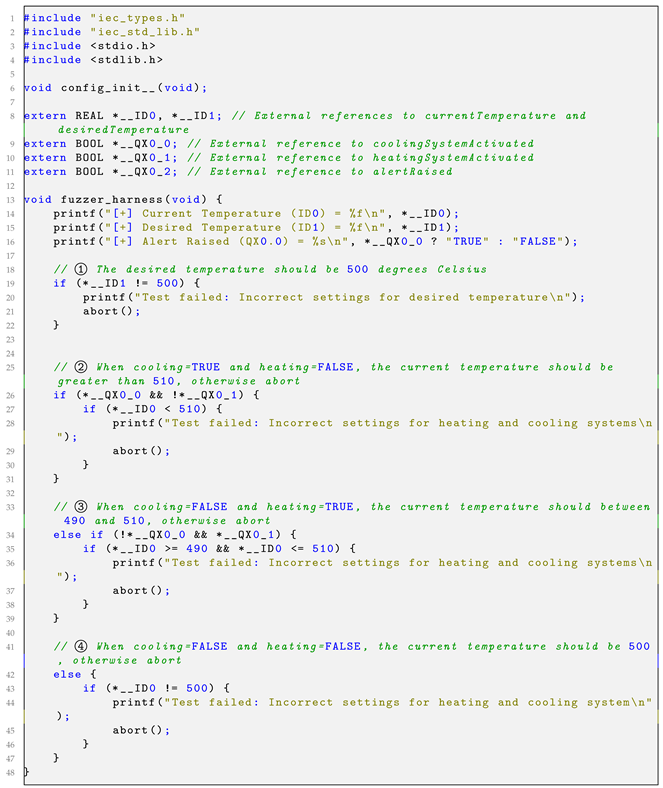 |
- Step 2: ST Program Compilation: The second step of the framework depicted in Figure 5 is to transcode the ST programs to the corresponding PLC runtime. In our implementation, the compilation process is performed with the aid of Matiec iec2c compiler [36]. It is a source-to-source compiler that compiles ST programs to C. This compiler is used by many open-source projects such as OpenPLC [37].
- Step 3: Input Generation: The third step involves generating the initial fuzzing inputs (seeds). This step is critical since using seeds from a previous fuzzing (i.e., one that was not provided with initial seeds) of the same program can be ineffective. The importance of good initial seeds for fuzzing has been demonstrated by prior studies [38,39]. For this reason, we developed a static code analysis (SCA) tool for generating good initial seeds. It utilizes the Tree-Sitter library to parse the ST program. Parsing the ST provides a more reliable way to perform various program analyses, unlike regular expressions, which are generally error-prone. Tree-Sitter [40] is a parser generator tool as well as an incremental parsing library previously used for similar purposes [41]. To parse the programs with Tree-Sitter, a grammar for the target language is required. However, there is a lack of extensive research on grammar specifically tailored for ST programming. To address this shortcoming, we construct a Tree-Sitter grammar for ST that enables us to build an abstract syntax tree (AST) from an ST source file. We utilize the AST in our analysis to extract the types and addresses of the variables used in the programs as shown in Algorithm 1. Importantly, this step is required to ensure the fuzzer generates inputs compatible with the types and addresses used within the ST program.
Algorithm 1 Algorithm for automatic fuzzing harness generation. - Require: ▹ ST program source file
- Ensure: ▹ Source file for the input adapter program
- 1:
- 2: ▹ Initialize the list of variables in the ST program
- 3: for do
- 4: if then
- 5:
- 6:
- 7:
- 8:
- 9: end if
- 10: end for
- 11:
- 12: return
| Algorithm 2 Function (Generate PLC Input Adapter Function). |
|
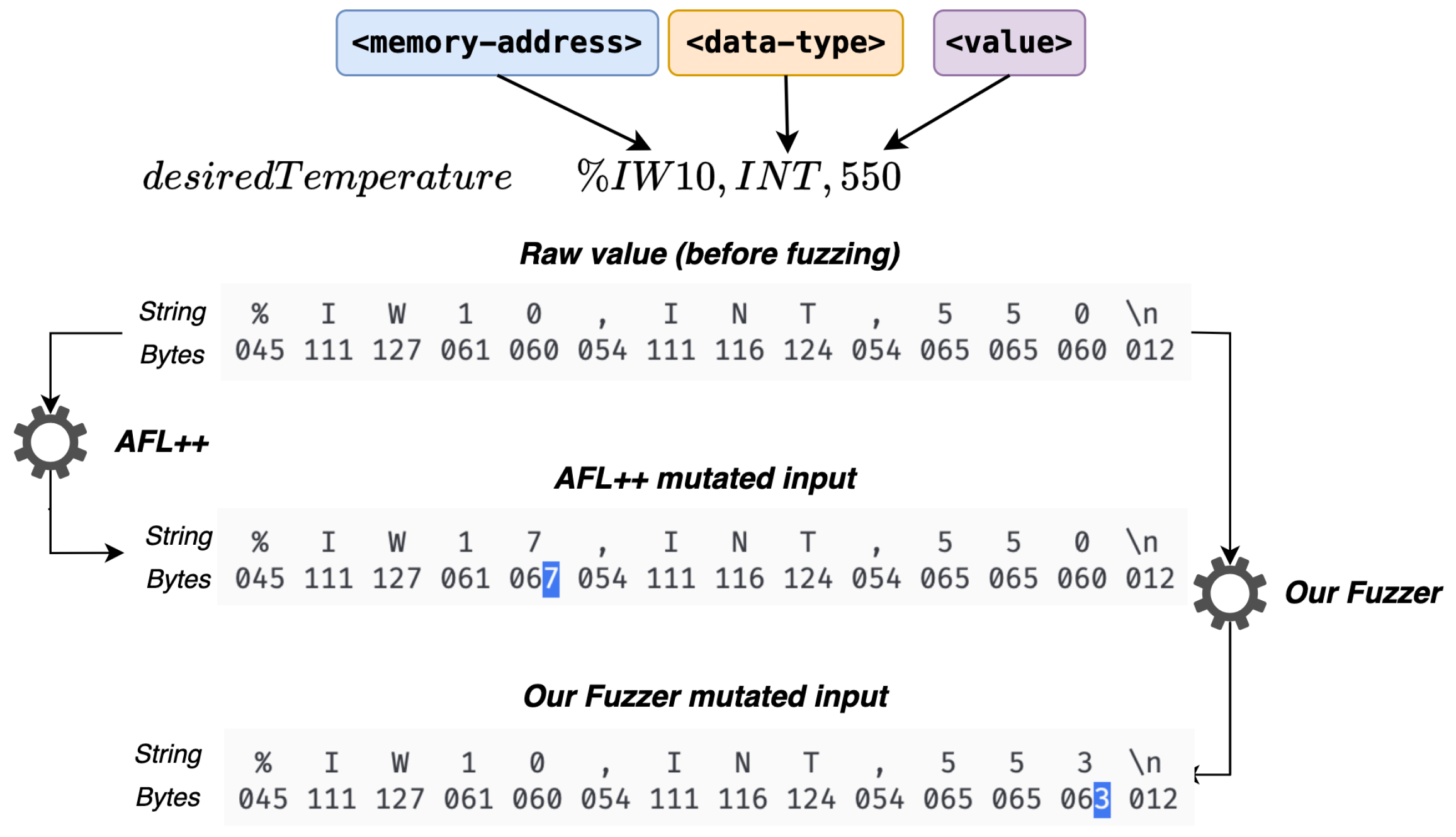
- Step 4: Fuzzing: The final step is fuzzing the control logic using the proposed PLC runtime along with a fuzzer. To do that, we implemented a custom fuzzer in Rust based on the LibAFL [42] fuzzing library. In further detail, LibAFL is a popular library that provides a set of utilities for building custom fuzzers. It separates fuzzers into several modules, each providing core functionalities such as mutators, generators, feedbacks, observers, monitors, and executors. The LibAFL plugin-like system enables adding new components or reusing existing modules to construct fuzzers. To this extent, the proposed fuzzer reuses some core functionalities present in AFL++ but with a new custom mutator, namely, PLCRandomInputMutator, designed specifically for fuzzing control applications. As depicted in Algorithm 3, the mutator is fed with inputs derived from the provided corpus, the current state of the fuzzer, and the index of the current fuzzing stage. At the end of the procedure, the mutated inputs and a new state of the fuzzer are expected to be output. In detail, first, a random number generator based on the state of the fuzzer is initialized. Next, the current inputs are parsed into a set of ST variable structures. If the parsing fails, i.e., the list of variables is empty, the fuzzer state is set to Skipped, indicating a failed mutation; otherwise, it is set to Mutated to indicate a successful mutation. Note that for each variable in the set of PLC variables, the mutation procedure determines its size (in bits) for generating alternative inputs, using the random number generator from the fuzzer’s state to generate random values for the control logic inputs. Following, the fuzzer utilizes the mutation procedure (mutate) and the PLC runtime to fuzz the native control logic code. The execution of the program is monitored during fuzzing of the control logic until a STOP (e.g., SIGTERM or SIGKILL signals in Linux) signal is received. If the harness is provided during the compilation of the binary, the fuzzer would detect the crashes (e.g., signaled via an abort() statement). In the same vein, during fuzzing, the runtime binary would execute the code of the harness on each execution with the mutated inputs. Alternatively, a fuzzer such as AFL++ can be coupled with the proposed runtime to fuzz the control application.
Algorithm 3 (Random Input Generation for Fuzzing). - Require: ▹ Fuzzer’s state
- Require: ▹ Current input to fuzz
- Require: ▹ Current fuzzing stage index
- Ensure: ▹ Mutated PLC inputs
- Ensure: ▹ New fuzzing state to indicate whether the mutation was applied
- 1: procedure Mutate()
- 2: ▹ Initialize the mutated inputs
- 3: ▹ Initialize the random number generator from state
- 4: ▹ Get the C variables from ST
- 5: if then
- 6:
- 7: end if
- 8: for do
- 9: if then ▹ Variable size is 1 bit
- 10: ▹ Flip boolean value
- 11: else if then ▹ Variable size is 8-bit (byte)
- 12: ▹ Generate random 8-bit
- 13: else if then ▹ Variable size is 16-bit (word)
- 14: ▹ Generate random 16-bit
- 15: else if then ▹ Variable size is 32-bit (double)
- 16: ▹ Generate random 32-bit
- 17: else if then ▹ Variable size is 64-bit (long)
- 18: ▹ Generate random 64-bit
- 19: end if
- 20:
- 21:
- 22: end for
- 23: return
- 24: end procedure
4. Experimental Evaluation
4.1. Experimental Setup
4.2. Results and Discussion
5. Related Work
- Network protocol fuzzing: Fuzzing often involves the security testing of communication protocols [10,11,12]. For instance, in PropFuzz [13], the authors present a protocol fuzzer designed for proprietary ICS protocols. The tool fuzzes network protocols by analyzing the communication between a device, say, a PLC, and an integrated development environment (IDE) to extract and mutate the relevant network fields. Then, it sends the sniffed (mutated) packets to the device. In addition, the fuzzer receives execution feedback by monitoring an output channel of the PLC. Similarly, Luo et al. present Polar [14], a protocol fuzzer that extracts semantic information from ICS protocol packets to identify vulnerable protocol function fields. The tool uses static analysis and dynamic taint analysis to identify the fields that are most likely to contain vulnerable operations and to fuzz them. The authors in CGFuzzer [15] propose a deep learning-based approach for fuzzing IIoT protocols, focusing on the DNP3 protocol. Their tool uses a coverage-guided generative adversarial network model (GAN), namely, CovGAN, to learn the specifications of the underlying network protocol and generate fuzz test cases. The authors demonstrate the effectiveness of CGFuzzer in identifying vulnerabilities in the DNP3 protocol by evaluating the fuzzer on a public dataset and an in-house capture dataset. Overall, the discussed studies underscore the significance of protocol fuzzing in improving the security of ICS devices, emphasizing the need for tools and methodologies to address the unique challenges of ICS security testing.
- Device Fuzzing: Fuzzing has also been applied to test the security of ICS devices like PLCs. The most common approaches include emulation-based, harness-based, and on-device fuzzing [44]. Emulation-based fuzzing involves testing the firmware of the device through an emulator, i.e., a technique also known as re-hosting. For instance, developed by Scharnowski et al., Fuzzware [45] is a fuzzing tool that uses memory-mapped I/O (MMIO) to model the peripherals of devices to fuzz their firmware. It is designed to identify vulnerabilities in the firmware of embedded devices via concolic execution-based fuzzing. Similarly, Tychalas et al. present IFFSET [46], a fuzzing tool that uses Quick-Emulation (QEMU) to emulate the Linux-based ICS firmware of Codesys PLCs. The approach relies on reverse engineering the firmware to extract the linked shared objects of I/Os and network-related code that are called from a harness during fuzzing. The authors of IM [47] propose a hardware-independent firmware fuzzing via peripherals modeling. Their tool instantiates a device model from an abstract model for the ARM Cortex-M architecture. During fuzzing, their tool can discriminate between benign and crashing inputs through the proposed model. In Sizzler [48], the authors present a tool for fuzzing QEMU-based emulated PLC firmware. It utilizes a sequential generative adversarial network (SeqGAN) to generate test cases for mutation-based fuzzing. Unlike emulation-based fuzzing, harness-based fuzzing involves using a harness to connect the fuzzer and the device. For example, SP-Fuzz [49] is a tool that generates a harness in a semi-automated fashion using context information from the execution of the PLC runtime. In contrast, on-device fuzzing involves executing the fuzzer directly on the device, e.g., ICSFuzz [3].
6. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| IG | Input Generation |
| AFL | American Fuzzy Lop |
| AFL++ | American Fuzzy Lop Plus Plus |
| ST | Structured Text |
| SCA | Static Code Analysis |
| IEC | International Electrotechnical Commission |
| PLC | Programmable Logic Controller |
| LL | Ladder Logic |
| LD | Ladder Diagram |
| FBD | Function Block Diagram |
| SFC | Sequential Function Chart |
| ICS | Industrial Control Systems |
| HMI | Human–Machine Interface |
References
- Stouffer, K.; Pease, M.; Tang, C.; Zimmerman, T.; Pillitteri, V.; Lightman, S.; Hahn, A.; Saravia, S.; Sherule, A.; Thompson, M. Guide to Operational Technology (OT) Security; Technical Report NIST Special Publication (SP) 800-82 Rev. 3; NIST: Gaithersburg, MD, USA, 2023. [Google Scholar] [CrossRef]
- Bhamare, D.; Zolanvari, M.; Erbad, A.; Jain, R.; Khan, K.; Meskin, N. Cybersecurity for industrial control systems: A survey. Comput. Secur. 2020, 89, 101677. [Google Scholar] [CrossRef]
- Tychalas, D.; Benkraouda, H.; Maniatakos, M. {ICSFuzz}: Manipulating {I/Os} and Repurposing Binary Code to Enable Instrumented Fuzzing in {ICS} Control Applications. In Proceedings of the 30th USENIX Security Symposium (USENIX Security 21), Vancouver, BC, Canada, 11–13 August 2021; pp. 2847–2862. [Google Scholar]
- Shehod, A. Ukraine power grid cyberattack and US susceptibility: Cybersecurity implications of smart grid advancements in the US. Cybersecur. Interdiscip. Syst. Lab. MIT 2016, 22, 2016-22. [Google Scholar]
- Myung, J.w.; Hong, S. ICS malware Triton attack and countermeasures. Int. J. Emerg. Multidiscip. Res. 2019, 3, 13–17. [Google Scholar] [CrossRef]
- Robles, F.; Perlroth, N. Dangerous Stuff’: Hackers Tried to Poison Water Supply of Florida Town. The New York Times, 2021. [Google Scholar]
- Hajda, J.; Jakuszewski, R.; Ogonowski, S. Security challenges in industry 4.0 PLC Systems. Appl. Sci. 2021, 11, 9785. [Google Scholar] [CrossRef]
- NIST Glossary: Fuzz Testing. Available online: https://csrc.nist.gov/glossary/term/fuzz_testing (accessed on 20 April 2024).
- Li, J.; Zhao, B.; Zhang, C. Fuzzing: A survey. Cybersecurity 2018, 1, 1–13. [Google Scholar] [CrossRef]
- Chen, Y.; Poskitt, C.M.; Sun, J.; Adepu, S.; Zhang, F. Learning-Guided Network Fuzzing for Testing Cyber-Physical System Defences. In Proceedings of the 2019 34th IEEE/ACM International Conference on Automated Software Engineering (ASE), San Diego, CA, USA, 11–15 November 2019; pp. 962–973. [Google Scholar] [CrossRef]
- Wijaya, H.; Aniche, M.; Mathur, A. Domain-Based Fuzzing for Supervised Learning of Anomaly Detection in Cyber-Physical Systems. In Proceedings of the IEEE/ACM 42nd International Conference on Software Engineering Workshops, ICSEW’20, Seoul, Republic of Korea, 27 June–19 July 2020; pp. 237–244. [Google Scholar] [CrossRef]
- Kampourakis, V.; Chatzoglou, E.; Kambourakis, G.; Dolmes, A.; Zaroliagis, C. Wpaxfuzz: Sniffing out vulnerabilities in wi-fi implementations. Cryptography 2022, 6, 53. [Google Scholar] [CrossRef]
- Niedermaier, M.; Fischer, F.; von Bodisco, A. PropFuzz—An IT-security fuzzing framework for proprietary ICS protocols. In Proceedings of the 2017 International Conference on Applied Electronics (AE), Pilsen, Czech Republic, 5–6 September 2017; pp. 1–4. [Google Scholar] [CrossRef]
- Luo, Z.; Zuo, F.; Jiang, Y.; Gao, J.; Jiao, X.; Sun, J. Polar: Function Code Aware Fuzz Testing of ICS Protocol. ACM Trans. Embed. Comput. Syst. 2019, 18, 93:1–93:22. [Google Scholar] [CrossRef]
- Yu, Z.; Wang, H.; Wang, D.; Li, Z.; Song, H. CGFuzzer: A Fuzzing Approach Based on Coverage-Guided Generative Adversarial Networks for Industrial IoT Protocols. IEEE Internet Things J. 2022, 9, 21607–21619. [Google Scholar] [CrossRef]
- Tiegelkamp, M.; John, K.H. IEC 61131-3: Programming Industrial Automation Systems; Springer: Berlin/Heidelberg, Germany, 2010; Volume 166. [Google Scholar]
- Editor, C.C. Programmable Logic Controller—Glossary|CSRC. Available online: https://csrc.nist.gov/glossary/term/programmable_logic_controller (accessed on 22 April 2024).
- Di Pinto, A.; Dragoni, Y.; Carcano, A. TRITON: The first ICS cyber attack on safety instrument systems. Proc. Black Hat USA 2018, 2018, 1–26. [Google Scholar]
- Kampourakis, V.; Gkioulos, V.; Katsikas, S. A systematic literature review on wireless security testbeds in the cyber-physical realm. Comput. Secur. 2023, 133, 103383. [Google Scholar] [CrossRef]
- Kushner, D. The real story of stuxnet. IEEE Spectr. 2013, 50, 48–53. [Google Scholar] [CrossRef]
- Eisele, M.; Maugeri, M.; Shriwas, R.; Huth, C.; Bella, G. Embedded fuzzing: A review of challenges, tools, and solutions. Cybersecurity 2022, 5, 18. [Google Scholar] [CrossRef]
- Miller, B.P.; Fredriksen, L.; So, B. An empirical study of the reliability of UNIX utilities. Commun. ACM 1990, 33, 32–44. [Google Scholar] [CrossRef]
- Gascon, H.; Wressnegger, C.; Yamaguchi, F.; Arp, D.; Rieck, K. Pulsar: Stateful black-box fuzzing of proprietary network protocols. In Proceedings of the Security and Privacy in Communication Networks: 11th EAI International Conference, SecureComm 2015, Dallas, TX, USA, 26–29 October 2015; Springer: Berlin/Heidelberg, Germany, 2015; pp. 330–347. [Google Scholar]
- Böhme, M.; Pham, V.T.; Nguyen, M.D.; Roychoudhury, A. Directed greybox fuzzing. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017; pp. 2329–2344. [Google Scholar]
- Zhang, M.; Arcuri, A.; Li, Y.; Liu, Y.; Xue, K. White-box fuzzing RPC-based APIs with EvoMaster: An industrial case study. ACM Trans. Softw. Eng. Methodol. 2023, 32, 1–38. [Google Scholar] [CrossRef]
- Lyu, C.; Ji, S.; Zhang, C.; Li, Y.; Lee, W.H.; Song, Y.; Beyah, R. {MOPT}: Optimized mutation scheduling for fuzzers. In Proceedings of the 28th USENIX Security Symposium (USENIX Security 19), Santa Clara, CA, USA, 14–16 August 2019; pp. 1949–1966. [Google Scholar]
- Wang, J.; Chen, B.; Wei, L.; Liu, Y. Skyfire: Data-driven seed generation for fuzzing. In Proceedings of the 2017 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 25 May 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 579–594. [Google Scholar] [CrossRef]
- Chen, Y.; Li, P.; Xu, J.; Guo, S.; Zhou, R.; Zhang, Y.; Wei, T.; Lu, L. SAVIOR: Towards Bug-Driven Hybrid Testing. In Proceedings of the 2020 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 21 May 2020; pp. 1580–1596, ISSN 2375-1207. [Google Scholar] [CrossRef]
- Hsu, C.C.; Wu, C.Y.; Hsiao, H.C.; Huang, S.K. Instrim: Lightweight instrumentation for coverage-guided fuzzing. In Proceedings of the Symposium on Network and Distributed System Security (NDSS), Workshop on Binary Analysis Research, San Diego, CA, USA, 18–21 February 2018; Volume 40. [Google Scholar]
- Li, W.; Shi, J.; Li, F.; Lin, J.; Wang, W.; Guan, L. µAFL: Non-intrusive feedback-driven fuzzing for microcontroller firmware. In Proceedings of the 44th International Conference on Software Engineering, Pittsburgh Pennsylvania, San Diego, CA, USA, 8–27 May 2022; pp. 1–12. [Google Scholar] [CrossRef]
- Rawat, S.; Jain, V.; Kumar, A.; Cojocar, L.; Giuffrida, C.; Bos, H. VUzzer: Application-aware Evolutionary Fuzzing. In Proceedings of the NDSS, San Diego, CA, USA, 26 February–1 March 2017; Volume 17, pp. 1–14. [Google Scholar]
- FuzzBench: Oss-Fuzz-Benchmarks Report (Running). Available online: https://commondatastorage.googleapis.com/fuzzbench-reports/oss-fuzz-benchmarks/index.html (accessed on 22 April 2024).
- American Fuzzy Lop. Available online: https://lcamtuf.coredump.cx/afl/ (accessed on 12 April 2024).
- Fioraldi, A.; Maier, D.; Eißfeldt, H.; Heuse, M. {AFL++}: Combining incremental steps of fuzzing research. In Proceedings of the 14th USENIX Workshop on Offensive Technologies (WOOT 20), Boston, MA, USA, 10–11 August 2020. [Google Scholar]
- Serhane, A.; Raad, M.; Raad, R.; Susilo, W. Programmable logic controllers based systems (PLC-BS): Vulnerabilities and threats. SN Appl. Sci. 2019, 1, 924. [Google Scholar] [CrossRef]
- Catalão, T.H.A.A. An LLVM Based Compiler for the IEC 61131-3. Master’s Thesis, University of Porto, Porto, Portugal, 2020. [Google Scholar]
- Alves, T.R.; Buratto, M.; De Souza, F.M.; Rodrigues, T.V. OpenPLC: An open source alternative to automation. In Proceedings of the IEEE Global Humanitarian Technology Conference (GHTC 2014), San Jose, CA, USA, 10–13 October 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 585–589. [Google Scholar] [CrossRef]
- Wang, M.; Liang, J.; Chen, Y.; Jiang, Y.; Jiao, X.; Liu, H.; Bin Zhao, X.; Sun, J. SAFL: Increasing and accelerating testing coverage with symbolic execution and guided fuzzing. In Proceedings of the 2018 IEEE/ACM 40th International Conference on Software Engineering: Companion (ICSE-Companion), Gothenburg, Sweden, 27 May–3 June 2018; pp. 61–64. [Google Scholar] [CrossRef]
- Cheng, L.; Zhang, Y.; Zhang, Y.; Wu, C.; Li, Z.; Fu, Y.; Li, H. Optimizing seed inputs in fuzzing with machine learning. In Proceedings of the 2019 IEEE/ACM 41st International Conference on Software Engineering: Companion Proceedings (ICSE-Companion), Montreal, QC, Canada, 25–31 May 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 244–245. [Google Scholar]
- Latif, A.; Azam, F.; Anwar, M.; Zafar, A. Comparison of Leading Language Parsers—ANTLR, JavaCC, SableCC, Tree-sitter, Yacc, Bison. In Proceedings of the 2023 13th International Conference on Software Technology and Engineering (ICSTE), Osaka, Japan, 27–29 October 2023; pp. 7–13. [Google Scholar] [CrossRef]
- Guo, S.; Wu, M.; Wang, C. Symbolic execution of programmable logic controller code. In Proceedings of the 2017 11th Joint Meeting on Foundations of Software Engineering, ESEC/FSE 2017, Paderborn, Germany, 4–8 September 2017; pp. 326–336. [Google Scholar] [CrossRef]
- Fioraldi, A.; Maier, D.C.; Zhang, D.; Balzarotti, D. Libafl: A framework to build modular and reusable fuzzers. In Proceedings of the 2022 ACM SIGSAC Conference on Computer and Communications Security, Los Angeles, CA, USA, 11 November 2022; pp. 1051–1065. [Google Scholar]
- Falcon. 2023. Available online: https://www.c3plus3.org/falcon/ (accessed on 17 January 2024).
- Yun, J.; Rustamov, F.; Kim, J.; Shin, Y. Fuzzing of Embedded Systems: A Survey. ACM Comput. Surv. 2023, 55, 1–33. [Google Scholar] [CrossRef]
- Scharnowski, T.; Bars, N.; Schloegel, M.; Gustafson, E.; Muench, M.; Vigna, G.; Kruegel, C.; Holz, T.; Abbasi, A. Fuzzware: Using Precise {MMIO} Modeling for Effective Firmware Fuzzing. In Proceedings of the 31st USENIX Security Symposium (USENIX Security 22), Boston, MA, USA, 10–12 August 2022; pp. 1239–1256. [Google Scholar]
- Tychalas, D.; Maniatakos, M. IFFSET: In-Field Fuzzing of Industrial Control Systems using System Emulation. In Proceedings of the 2020 Design, Automation & Test in Europe Conference & Exhibition (DATE), Grenoble, France, 9–13 March 2020; pp. 662–665, ISSN 1558-1101. [Google Scholar] [CrossRef]
- Feng, B.; Mera, A.; Lu, L. {P2IM}: Scalable and Hardware-independent Firmware Testing via Automatic Peripheral Interface Modeling. In Proceedings of the 29th USENIX Security Symposium (USENIX Security 20), Boston, MA, USA, 12–14 August 2020; pp. 1237–1254. [Google Scholar]
- Feng, K.; Cook, M.M.; Marnerides, A.K. Sizzler: Sequential Fuzzing in Ladder Diagrams for Vulnerability Detection and Discovery in Programmable Logic Controllers. IEEE Trans. Inf. Forensics Secur. 2024, 19, 1660–1671. [Google Scholar] [CrossRef]
- Jeon, S.; Seo, J.T. SP-Fuzz: Fuzzing Soft PLC with Semi-automated Harness Synthesis. In Proceedings of the Information Security Applications (WISA 2023), Jeju Island, Republic of Korea, 23–25 August 2023; Kim, H., Youn, J., Eds.; 2023; pp. 282–293. [Google Scholar] [CrossRef]
- Wang, F.; Shoshitaishvili, Y. Angr-The Next Generation of Binary Analysis. In Proceedings of the 2017 IEEE Cybersecurity Development (SecDev), Cambridge, MA, USA, 24–26 September 2017; pp. 8–9. [Google Scholar] [CrossRef]

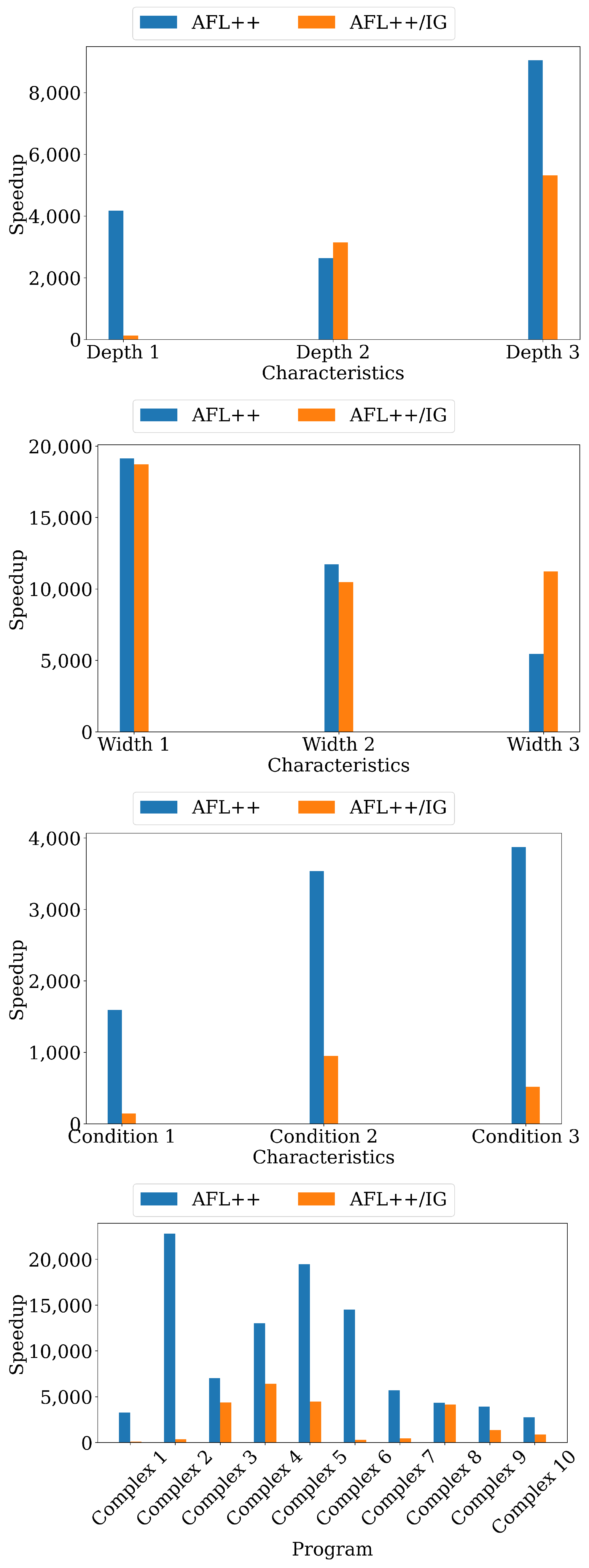

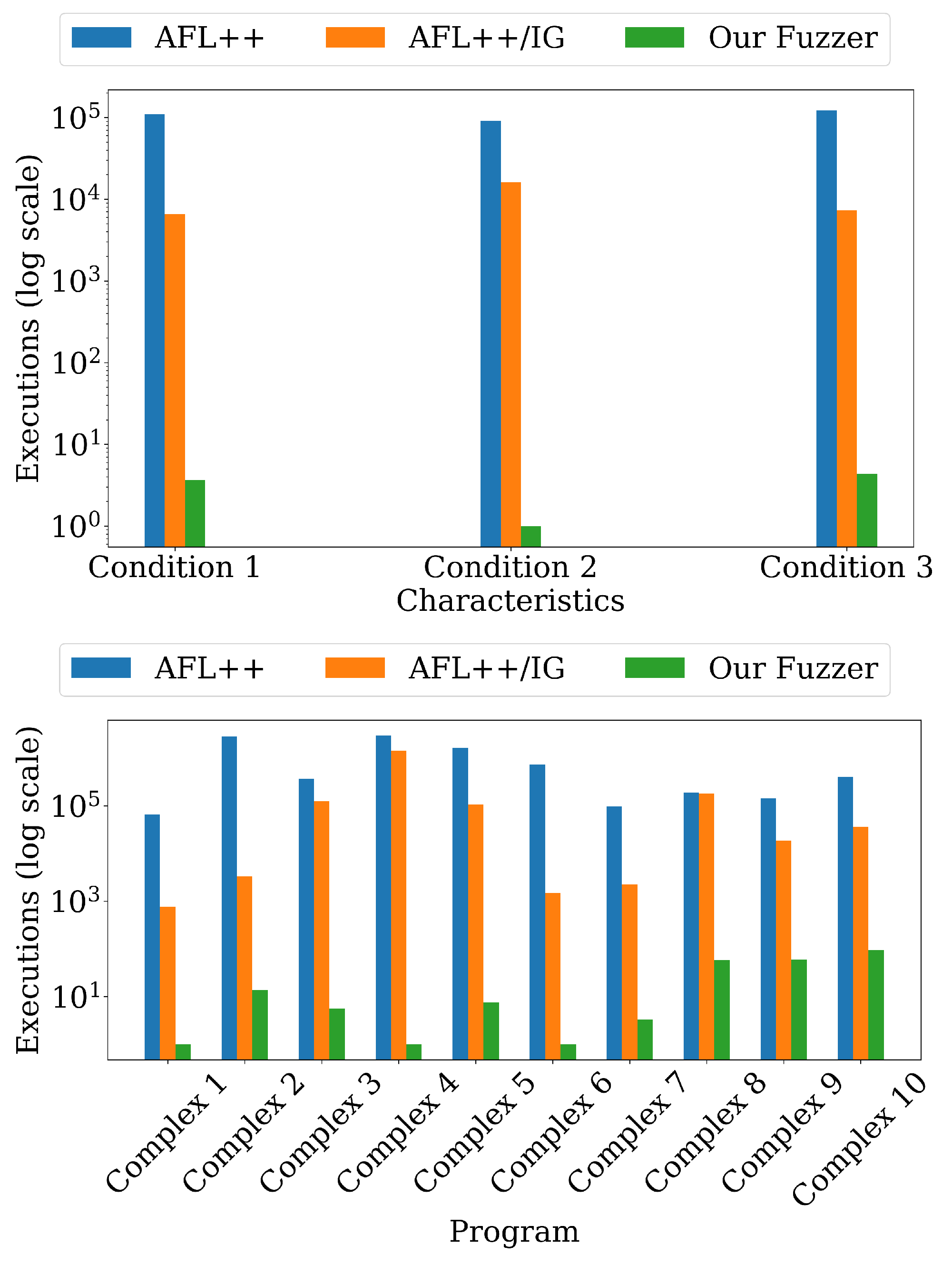
| Programs | Characteristics | Description |
|---|---|---|
| Depth 1 to 3 | Branch Depth | Programs with increasing branch depths |
| Width 1 to 3 | Branch Width | Programs with increasing branch widths |
| Condition 1 to 3 | Branch Condition | Programs with various branch conditions complexities |
| Complex 1 to 10 | Real-world Program | Programs resembling real-world PLC programs |
| Characteristics | AFL++ | AFL++/IG | Our Fuzzer | Speedup | Speedup |
|---|---|---|---|---|---|
| Branch Depth | |||||
| Depth 1 | 559.29 | 16.86 | 0.13 | 4302.23 | 129.69 |
| Depth 2 | 358.00 | 427.00 | 0.14 | 2557.14 | 3050.00 |
| Depth 3 | 1509.67 | 887.17 | 0.17 | 8880.41 | 5218.65 |
| Branch Width | |||||
| Width 1 | 3954.17 | 3870.00 | 0.21 | 18,829.38 | 18,428.57 |
| Width 2 | 2174.33 | 1943.50 | 0.19 | 11,443.84 | 10,228.95 |
| Width 3 | 1114.47 | 2298.20 | 0.20 | 5572.35 | 11,491.00 |
| Branch Condition | |||||
| Condition 1 | 220.47 | 19.88 | 0.14 | 1574.79 | 142.00 |
| Condition 2 | 522.14 | 140.00 | 0.15 | 3480.93 | 933.33 |
| Condition 3 | 561.50 | 75.25 | 0.14 | 4010.71 | 537.50 |
| Real-world Program | |||||
| Complex 1 | 780.67 | 20.08 | 0.24 | 3252.79 | 83.67 |
| Complex 2 | 6002.92 | 95.08 | 0.26 | 23,088.15 | 365.69 |
| Complex 3 | 1361.44 | 844.22 | 0.19 | 7165.47 | 4443.26 |
| Complex 4 | 5378.27 | 2655.82 | 0.41 | 13,117.73 | 6477.61 |
| Complex 5 | 3975.45 | 909.00 | 0.20 | 19,877.25 | 4545.00 |
| Complex 6 | 2379.80 | 44.40 | 0.16 | 14,873.75 | 277.50 |
| Complex 7 | 993.38 | 77.62 | 0.17 | 5843.41 | 456.59 |
| Complex 8 | 1223.70 | 1167.00 | 0.28 | 4370.36 | 4167.86 |
| Complex 9 | 1082.22 | 380.56 | 0.28 | 3865.07 | 1359.14 |
| Complex 10 | 1496.67 | 473.11 | 0.55 | 2721.22 | 860.20 |
| Characteristics | AFL++ | AFL++/IG | Our Fuzzer |
|---|---|---|---|
| Branch Depth | |||
| Depth 1 | 273,970.00 | 5591.57 | 7.43 |
| Depth 2 | 179,891.75 | 334,971.25 | 9.88 |
| Depth 3 | 942,404.50 | 441,799.67 | 13.50 |
| Branch Width | |||
| Width 1 | 1,882,189.50 | 1,459,524.83 | 1.0 |
| Width 2 | 710,572.67 | 577,395.33 | 1.0 |
| Width 3 | 765,733.93 | 1,677,735.47 | 1.0 |
| Branch Condition | |||
| Condition 1 | 110,527.24 | 6581.53 | 3.65 |
| Condition 2 | 91,400.43 | 16,189.00 | 1.00 |
| Condition 3 | 122,671.00 | 7353.38 | 4.38 |
| Real-world Program | |||
| Complex 1 | 64,996.17 | 772.92 | 1.00 |
| Complex 2 | 2,841,554.00 | 3275.00 | 13.62 |
| Complex 3 | 367,426.44 | 124,724.56 | 5.56 |
| Complex 4 | 2,967,611.73 | 1,427,264.82 | 1.00 |
| Complex 5 | 1,615,857.82 | 106,716.45 | 7.64 |
| Complex 6 | 734,122.60 | 1464.20 | 1.00 |
| Complex 7 | 96,081.50 | 2249.12 | 3.25 |
| Complex 8 | 189,611.80 | 181,804.10 | 58.70 |
| Complex 9 | 141,941.11 | 18,508.11 | 60.11 |
| Complex 10 | 402,542.33 | 36,779.22 | 95.11 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Koffi, K.A.; Kampourakis, V.; Song, J.; Kolias, C.; Ivans, R.C. StructuredFuzzer: Fuzzing Structured Text-Based Control Logic Applications. Electronics 2024, 13, 2475. https://doi.org/10.3390/electronics13132475
Koffi KA, Kampourakis V, Song J, Kolias C, Ivans RC. StructuredFuzzer: Fuzzing Structured Text-Based Control Logic Applications. Electronics. 2024; 13(13):2475. https://doi.org/10.3390/electronics13132475
Chicago/Turabian StyleKoffi, Koffi Anderson, Vyron Kampourakis, Jia Song, Constantinos Kolias, and Robert C. Ivans. 2024. "StructuredFuzzer: Fuzzing Structured Text-Based Control Logic Applications" Electronics 13, no. 13: 2475. https://doi.org/10.3390/electronics13132475
APA StyleKoffi, K. A., Kampourakis, V., Song, J., Kolias, C., & Ivans, R. C. (2024). StructuredFuzzer: Fuzzing Structured Text-Based Control Logic Applications. Electronics, 13(13), 2475. https://doi.org/10.3390/electronics13132475








