A Hardware Trojan Detection and Diagnosis Method for Gate-Level Netlists Based on Machine Learning and Graph Theory
Abstract
:1. Introduction
- (1)
- An HT detection and diagnosis method for GLN based on ML and GT is proposed.
- (2)
- This paper, for the first time, proposes the concept and partition algorithm of MSOS to address the issue of nonunique submodule partition.
- (3)
- A total of 24 HT-related features are selected and extracted, including circuit diagram structure and static circuit attribute features.
- (4)
- We present a GT-based GLHT diagnosis method, which takes into account the comprehensiveness of HTs to fine-grain discover their locations.
- (5)
- In the implanted node search experiment, we propose the breadth-first comparison (BFC) algorithm, thereby increasing the diagnosis success rate.
2. Related Work
3. HT Detection Method for GLN Based on ML
- (1)
- MSOS partition: We partitioned the circuit diagram of the gate-level netlist into several MSOSs.
- (2)
- Feature extraction of MSOSs: We calculated and collected node information, and we then extracted HT-related features from the MSOSs.
- (3)
- Feature filter: We used chi-square tests and variance filtering methods to filter features of the MSOSs.
- (4)
- Model training: We trained a specific supervised learning model with optimized hyperparameters.
- (5)
- MSOS label prediction: We input the filtered features extracted from the MSOS into a specific supervised learning model for prediction.
- (6)
- Detection report: We reported whether the gate-level netlist contains an HT based on the labels.
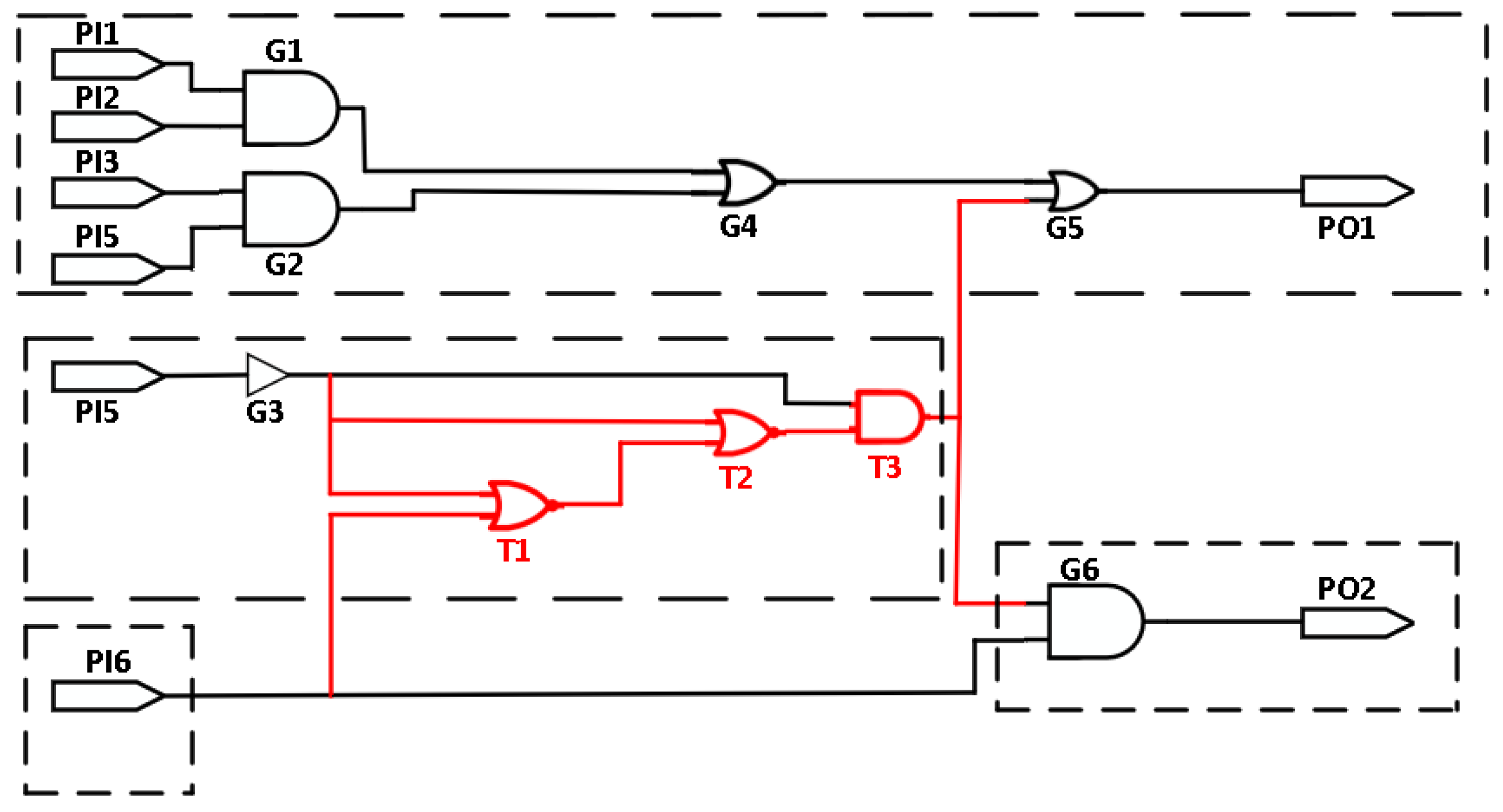
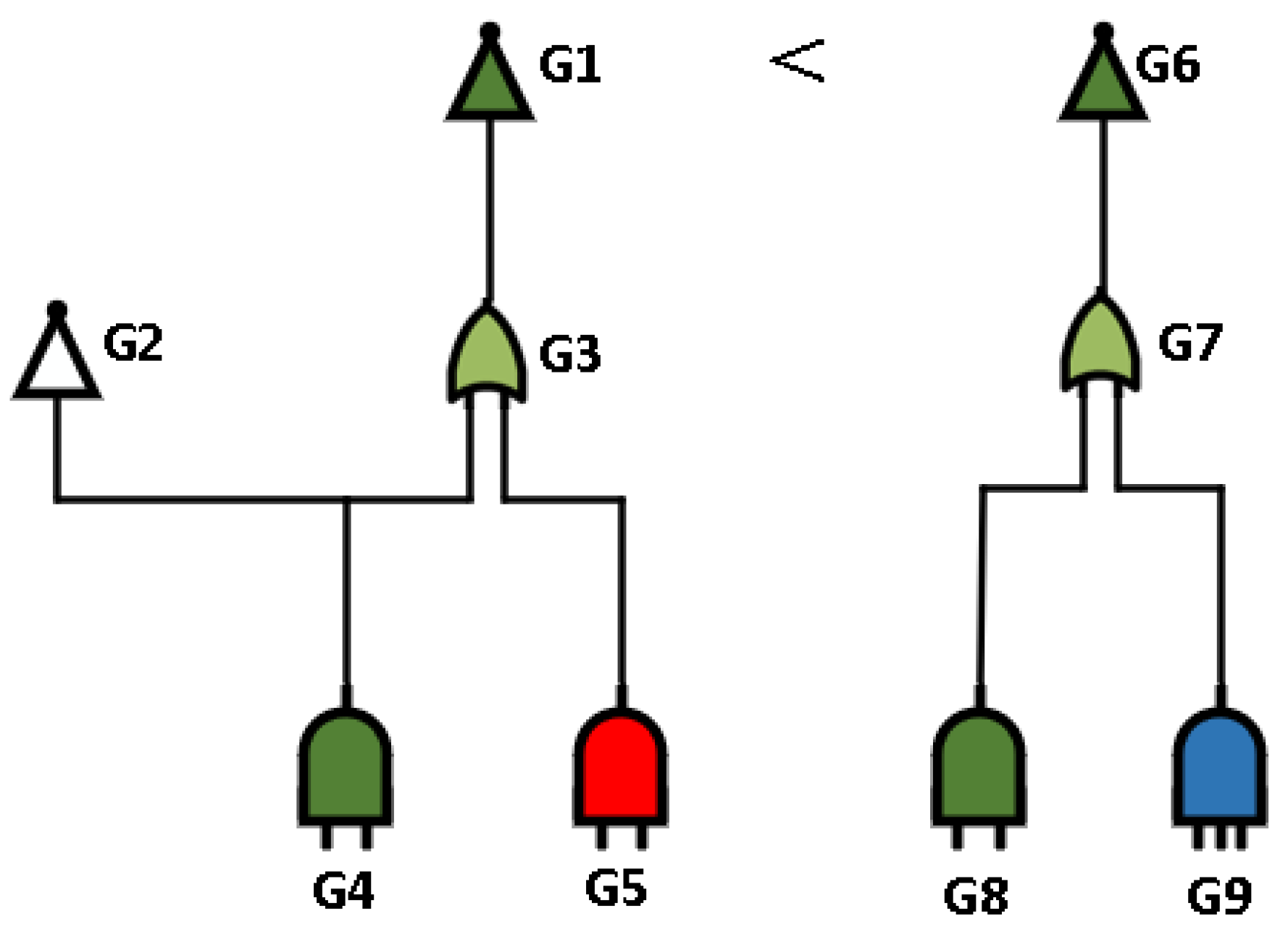
3.1. MSOS Partition
| Algorithm 1: MSOS partition. |
 |
3.2. Feature Extraction of MSOS
3.2.1. Structure Class Features of Circuit Diagram
- Node fan-in indicator: the maximum, minimum, and average value of the number of nodes entered by a node.
- Node fan-out indicator: the maximum, minimum, and average value of the number of nodes output by a node.
- SCC size indicator: the maximum, minimum, and average value of the number of nodes contained in the SCC to which the node belongs.
- Module fan-in: the number of input nodes when the entire MSOS is regarded as a single node.
- Module fan-out: the number of output nodes when the entire MSOS is regarded as a single node.
- Total number of nodes: the number of nodes contained in the MSOS.
3.2.2. Attribute Class Features of Static Circuit
- Combinational 0-controllability (CC0) index: the maximum, minimum, and average value of node CC0.
- Combinational 1-controllability (CC1) index of node combination 1: the maximum value, minimum value, and average value of node CC1.
- Combinational controllability (CC) index: the maximum, minimum, and average value of node CC.
- Combinational observability (CO) index of the nodes: the maximum, minimum, and average of node CO.
3.3. Model Training and Label Prediction
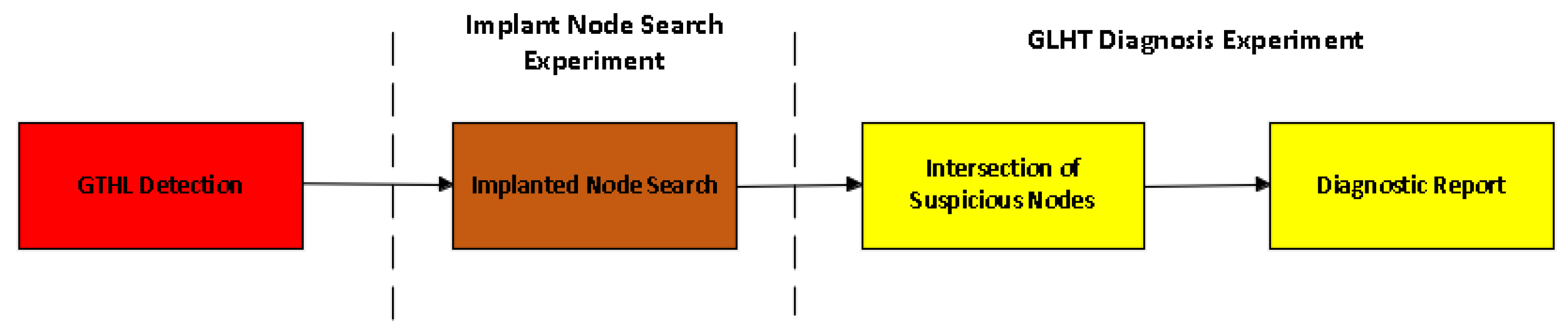
4. HT Diagnosis Method for GLN Based on GT
- (1)
- GLHT detection: We used the GLHT detection method based on the ML models studied in this article.
- (2)
- Implanted node search: By comparing the circuit diagram structure of the target netlist and the GLN, we identified additional implanted nodes in the target netlist relative to the GLN.
- (3)
- Intersection of suspicious nodes (i.e., HT node localization): We intersected the nodes contained in the MSOS of the “HT” detected in step (1) and the nodes obtained from the implanted node search.
- (4)
- Diagnosis report: We reported the obtained node intersection as an HT node set.
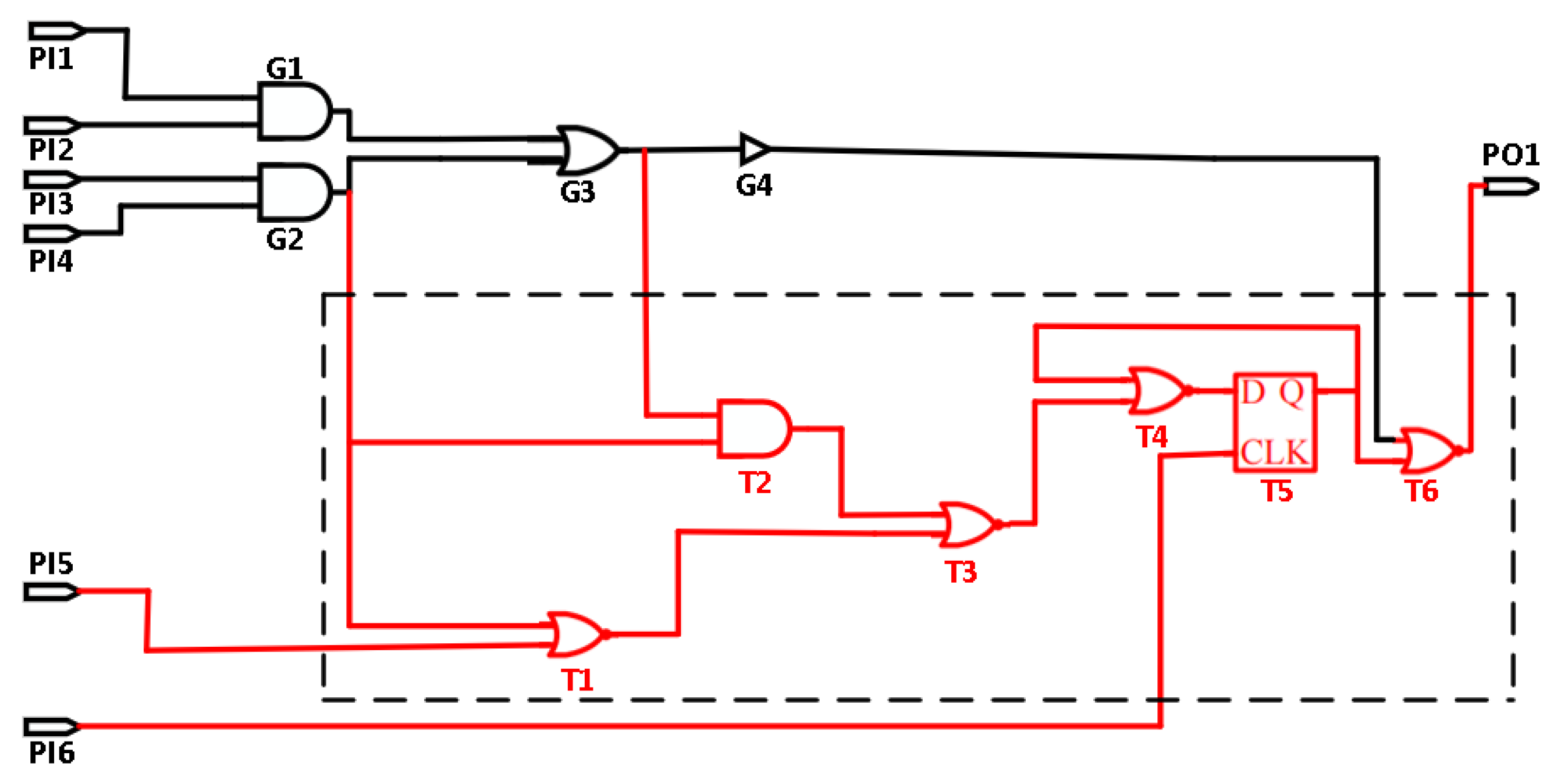
4.1. Implanted Node Search Based on BFC
- (1)
- Input nodes reordering: We determined the size relationships between nodes using an input-side BFC algorithm, and we then sorted the input nodes of all the nodes in the target netlist and GLN.
- (2)
- Internal netlist nodes sorting: We sorted the nodes of the target netlist and GLN.
- (3)
- Subtracting nodes between netlists: Sequentially, we compared the nodes in the target netlist and GLN to identify all the differing nodes, which were considered as candidate implanted points.
- (4)
- Nonimplanted nodes filtering: We filtered the nonimplanted nodes among the candidate implanted nodes based on the structure features and implantation ways of the GLHTs.
4.1.1. Input-Side BFC Algorithm
4.1.2. Nonimplanted Node Filtering Algorithm
4.1.3. Input Node Reordering Algorithm
| Algorithm 2: Input-side BFC algorithm. |
 |
4.2. Intersection of Suspicious Nodes
| Algorithm 3: Filtering of nonimplant nodes. |
 |
| Algorithm 4: Filtering of nonimplant nodes. |
 |
| Algorithm 5: Filtering of nonimplant nodes. |
 |
5. Experiments and Results
5.1. Evaluation Measures
5.2. HT in GLN Detection Experiment
5.3. HT in GLN Diagnosis Experiment
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Huang, Z.; Wang, Q.; Chen, Y.; Jiang, X. A survey on machine learning against hardware Trojan attacks: Recent advances and challenges. IEEE Access 2020, 8, 10796–10826. [Google Scholar] [CrossRef]
- Salmani, H.; Tehranipoor, M. Digital Circuit Vulnerabilities to Hardware Trojans. In Hardware IP Security and Trust; Mishra, P., Bhunia, S., Tehranipoor, M., Eds.; Springer: Cham, Sitzerland, 2017. [Google Scholar]
- Agrawal, D.; Baktir, S.; Karakoyunlu, D.; Rohatgi, P. Trojan detection using IC fingerprinting. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP ’07), Berkeley, CA, USA, 20–23 May 2007; pp. 296–310. [Google Scholar]
- Jin, Y.; Kupp, N.; Makris, Y. Experiences in hardware trojan design and implementation. In Proceedings of the 2009 IEEE International Workshop on Hardware-Oriented Security and Trust, San Francisco, CA, USA, 27–27 July 2009; pp. 50–57. [Google Scholar]
- Salmani, H.; Tehranipoor, M.; Plusquellic, J. A novel technique for improving hardware trojan detection and reducing trojan activation time. IEEE Trans. Very Large Scale Integr. (Vlsi) Syst. 2012, 20, 112–125. [Google Scholar] [CrossRef]
- He, J.; Zhao, Y.; Guo, X.; Jin, Y. Hardware trojan detection through chip-free electromagnetic side-channel statistical analysis. IEEE Trans. Very Large Scale Integr. (Vlsi) Syst. 2017, 25, 2939–2948. [Google Scholar] [CrossRef]
- Faezi, S.; Yasaei, R.; Barua, A.; Al Faruque, M.A. Brain-inspired golden chip free hardware trojan detection. IEEE Trans. Inf. Forensics Secur. 2017, 16, 2697–2708. [Google Scholar] [CrossRef]
- Dupuis, S.; Flottes, M.-L.; Di Natale, G.; Rouzeyre, B. Protection against hardware trojans with logic testing: Proposed solutions and challenges ahead. IEEE Des. Test 2018, 35, 73–90. [Google Scholar] [CrossRef]
- Wolff, F.; Papachristou, C.; Bhunia, S.; Chakraborty, R.S. Towards trojan-free trusted ICs: Problem analysis and detection scheme. In Proceedings of the 2008 Design, Automation and Test in Europe, Munich, Germany, 10–14 March 2008; pp. 1362–1365. [Google Scholar]
- Saha, S.; Chakraborty, R.S.; Nuthakki, S.S.; Anshul; Mukhopadhyay, D. Improved test pattern generation for hardware trojan detection using genetic algorithm and boolean satisfiability. In Proceedings of the Cryptographic Hardware and Embedded Systems–CHES 2015, Saint-Malo, France, 13–16 September 2015; Springer: Berlin/Heidelberg, Germany, 2015; pp. 577–596. [Google Scholar]
- Kampel, L.; Kitsos, P.; Simos, D.E. Locating hardware trojans using combinatorial testing for cryptographic circuits. IEEE Access 2022, 10, 18787–18806. [Google Scholar] [CrossRef]
- Zhang, X.; Tehranipoor, M. Case study: Detecting hardware trojans in third-party digital IP cores. In Proceedings of the 2011 IEEE International Symposium on Hardware-Oriented Security and Trust, San Diego, CA, USA, 5–6 June 2011; pp. 67–70. [Google Scholar]
- He, J.; Guo, X.; Meade, T.; Dutta, R.G.; Zhao, Y.; Jin, Y. SoC interconnection protection through formal verification. Integration 2019, 64, 143–151. [Google Scholar] [CrossRef]
- Qin, M.; Hu, W.; Wang, X.; Mu, D.; Mao, B. Theorem proof based gate-level information flow tracking for hardware security verification. Comput. Secur. 2019, 85, 225–239. [Google Scholar] [CrossRef]
- Waksman, A.; Suozzo, M.; Sethumadhavan, S. FANCI: Identification of stealthy malicious logic using boolean functional analysis. In Proceedings of the ACM SIGSAC Conference on Computer & Communications Security, Berlin, Germany, 4–8 November 2013. [Google Scholar]
- Fyrbiak, M.; Wallat, S.; Swierczynski, P.; Hoffmann, M.; Hoppach, S.; Wilhelm, M.; Weidlich, T.; Tessier, R.; Paar, C. HAL–The missing piece of the puzzle for hardware reverse engineering, trojan detection and insertion. IEEE Trans. Dependable Secur. Comput. 2019, 16, 498–510. [Google Scholar] [CrossRef]
- Oya, M.; Shi, Y.; Yanagisawa, M.; Togawa, N. A score-based classification method for identifying hardware trojans at gate-level netlists. In Proceedings of the Design, Automation & Test in Europe Conference & Exhibition (DATE), Grenoble, France, 9–13 March 2015; pp. 465–470. [Google Scholar]
- Hasegawa, K.; Oya, M.; Yanagisawa, M.; Togawa, N. Hardware trojans classification for gate-level netlists based on machine learning. In In Proceedings of the IEEE 22nd International Symposium on On-Line Testing and Robust System Design (IOLTS), Sant Feliu de Guixols, Spain, 4–6 July 2016; pp. 203–206. [Google Scholar]
- Hasegawa, K.; Yanagisawa, M.; Togawa, N. Hardware trojans classification for gate-level netlists using multi-layer neural networks. In Proceedings of the IEEE 23rd International Symposium on On-Line Testing and Robust System Design (IOLTS), Thessaloniki, Greece, 3–5 July 2017; pp. 227–232. [Google Scholar]
- Hasegawa, K.; Yanagisawa, M.; Togawa, N. Trojan-feature extraction at gate-level netlists and its application to hardware-trojan detection using random forest classifier. In Proceedings of the IEEE International Symposium on Circuits and Systems (ISCAS), Baltimore, MD, USA, 28–31 May 2017; pp. 1–4. [Google Scholar]
- Salmani, H. Cotd: Reference-free hardware trojan detection and recovery based on controllability and observability in gate-level netlist. IEEE Trans. Inf. Forensics Secur. 2017, 12, 338–350. [Google Scholar] [CrossRef]
- Zhao, J.; Shi, G. Survey on the research progress of hardware trojans. J. Inf. Secur. 2017, 2, 17. [Google Scholar]
- Du, M. A HT Detection and Diagnosis Method for Gate-level Netlists based on Machine Learning. Ph.D. Dissertation, Xi’an University of Electronic Science and Technology, Xi’an, China, 2021. [Google Scholar]
- Yanjian, Y.; Conghui, Z.; Yanjiang, L. Hardware Trojan Detection Technology Based on Multidimensional Structural Features. J. Electron. Inf. Technol. 2021, 43, 2128. [Google Scholar]
- Ma, S.; Liu, Y.; Wu, Y.; Zhang, S.; Zhang, Y.; Wang, D. Hybrid Mode Gate-Level Hardware Trojan Detection Method Based on XGBoost. J. Electron. Inf. Technol. 2021, 43, 3050. [Google Scholar]
- Xin, L.; Haiming, L.; Jian, M. Hardware Trojan Detection Based on Circuit Structure Analysis Using Integrated Model. Microelectron. Comput. 2021, 38, 80–86. [Google Scholar]
- Shi, J.; Wen, C.; Liu, H.; Wang, Z.; Zhang, S.; Ma, P.; Li, K. Hardware Trojan Detection for Gate-level Netlists Based on Graph Neural Network. J. Electron. Inf. Technol. 2023, 45, 3253–3262. [Google Scholar]
- Huang, Z.; Xie, C.J.; Li, Z.Y.; Du, M.F.; Wang, Q. A hardware trojan detection and diagnosis method for gate-level netlists based on different machine learning algorithms. J. Circuits Syst. Comput. 2022, 31, 2250135:1–2250135:25. [Google Scholar] [CrossRef]
- Cruz, J.; Huang, Y.; Mishra, P.; Bhunia, S. An automated configurable trojan insertion framework for dynamic trust benchmarks. In Proceedings of the Design, Automation & Test in Europe Conference & Exhibition (DATE), Dresden, Germany, 19–23 March 2018; pp. 1598–1603. [Google Scholar]
- Hasegawa, K.; Hidano, S.; Nozawa, K.; Kiyomoto, S.; Togawa, N. R-htdetector: Robust hardware-trojan detection based on adversarial training. IEEE Trans. Comput. 2023, 72, 333–345. [Google Scholar] [CrossRef]





| Features | |||
|---|---|---|---|
| Circuit structure features | Maximum node fan-in | Minimum node fan-in | Average node fan-in |
| Maximum node fan-out | Minimum node fan-out | Average node fan-out | |
| Largest SCC size | Smallest SCC size | Average SCC size | |
| Module fan-in | Module fan-out | Total number of nodes | |
| Static circuit attribute features | Maximum CC0 | Minimum CC0 | Average CC0 |
| Maximum CC1 | Minimum CC1 | Average CC1 | |
| Maximum CC | Minimum CC | Average CC | |
| Maximum CO | Minimum CO | Average CO | |
| Weighting Strategy | K-Value | Minkowski Distance Exponent | |
|---|---|---|---|
| Optional values | Uniform weighting/distance weighting | 1/2/3/4/5 | 1/2/3 |
| Selected values | Uniform weighting | 1 | 2 |
| Optimal balanced accuracy | 81.2% | ||
| Number of Decision Trees | Maximum Depth of Decision Trees | |
|---|---|---|
| Optional values | 10/20/30 | 1 to 10 |
| Selected values | 20 | 7 |
| Optimal balanced accuracy | 95.5% | |
| C | Gamma | |
|---|---|---|
| Optional values | 1/10/100 | 0.01/0.1/1 |
| Selected values | 100 | 1 |
| Optimal balanced accuracy | 84.2% | |
| Predicted Positive Result | Predicted Negative Result | |
|---|---|---|
| Positive Result | True Positive (TP) | False Negative (FN) |
| Negative Result | False Positive (FP) | True Negative (TN) |
| Metric | Calculation Formula |
|---|---|
| Accurracy | |
| Precision | |
| Recall (TPR) | |
| TNR | |
| F1 Score | |
| Balanced Accuracy |
| Label | Number | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 |
|---|---|---|---|---|---|---|---|---|---|---|
| Netlist | ||||||||||
| s1423 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| s1423_T002 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | |
| Feature | Value | Number | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 |
|---|---|---|---|---|---|---|---|---|---|---|---|
| Netlist | |||||||||||
| Maximum node fan-in | s1423 | 0 | 1 | 0 | 0 | 5 | 5 | 4 | 2 | 0 | |
| s1423_T002 | 0 | 1 | 0 | 0 | 5 | 5 | 4 | 2 | 0 | ||
| Minimum node fan-in | s1423 | 0 | 1 | 0 | 0 | 0 | 1 | 2 | 2 | 0 | |
| s1423_T002 | 0 | 1 | 0 | 0 | 0 | 1 | 2 | 2 | 0 | ||
| Average node fan-in | s1423 | 0 | 1 | 0 | 0 | 2.4 | 2.7 | 2.7 | 2 | 0 | |
| s1423_T002 | 0 | 1 | 0 | 0 | 2.4 | 2.7 | 2.7 | 2 | 0 | ||
| Maximum node fan-out | s1423 | 20 | 18 | 138 | 138 | 17 | 1 | 1 | 0 | 0 | |
| s1423_T002 | 20 | 18 | 138 | 138 | 17 | 1 | 1 | 0 | 0 | ||
| Minimum node fan-out | s1423 | 20 | 18 | 138 | 138 | 1 | 0 | 0 | 0 | 0 | |
| s1423_T002 | 20 | 18 | 138 | 138 | 1 | 0 | 0 | 0 | 0 | ||
| Average node fan-out | s1423 | 20 | 18 | 138 | 138 | 1.9 | 0.8 | 0.8 | 0 | 0 | |
| s1423_T002 | 20 | 18 | 138 | 138 | 1.9 | 0.8 | 0.8 | 0 | 0 | ||
| Largest SCC size | s1423 | 1 | 1 | 1 | 1 | 523 | 1 | 1 | 1 | 1 | |
| s1423_T002 | 1 | 1 | 1 | 1 | 532 | 1 | 1 | 1 | 1 | ||
| Smallest SCC size | s1423 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | |
| s1423_T002 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | ||
| Average SCC size | s1423 | 1 | 1 | 1 | 1 | 500.1 | 1 | 1 | 1 | 1 | |
| s1423_T002 | 1 | 1 | 1 | 1 | 509.1 | 1 | 1 | 1 | 1 | ||
| Module fan-in | s1423 | 0 | 1 | 0 | 0 | 308 | 11 | 11 | 2 | 0 | |
| s1423_T002 | 0 | 1 | 0 | 0 | 308 | 11 | 11 | 2 | 0 | ||
| Module fan-out | s1423 | 20 | 18 | 138 | 138 | 19 | 0 | 0 | 0 | 0 | |
| s1423_T002 | 20 | 18 | 138 | 138 | 19 | 0 | 0 | 0 | 0 | ||
| Total number of nodes | s1423 | 1 | 1 | 1 | 1 | 547 | 6 | 6 | 1 | 1 | |
| s1423_T002 | 1 | 1 | 1 | 1 | 556 | 6 | 6 | 1 | 1 | ||
| Feature | Number\Value\Netlist | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 |
|---|---|---|---|---|---|---|---|---|---|---|
| Maximum CC0 | s1423 | 1 | 2 | 1 | 1 | 372 | 14 | 237 | 12 | 1 |
| s1423_T002 | 1 | 2 | 1 | l | 372 | 14 | 237 | 12 | l | |
| Minimum CCO | s1423 | 1 | 2 | 1 | 1 | 1 | 3 | 10 | 12 | 1 |
| s1423_T002 | 1 | 2 | 1 | 1 | 1 | 3 | 10 | 12 | 1 | |
| Average CC0 | s1423 | 1 | 2 | 1 | 1 | 32.2 | 9.7 | 88 | 12 | 1 |
| s1423_T002 | 1 | 2 | 1 | 1 | 31.8 | 9.7 | 88 | 12 | 1 | |
| Maximum CC1 | s1423 | 1 | 2 | 1 | 1 | 219 | 77 | 258 | 14 | 1 |
| s1423_T002 | 1 | 2 | 1 | l | 237 | 77 | 258 | 14 | l | |
| Minimum CC1 | s1423 | 1 | 2 | 1 | 1 | 1 | 21 | 11 | 14 | 1 |
| s1423_T002 | 1 | 2 | 1 | 1 | 1 | 21 | 11 | 14 | 1 | |
| Average CC1 | s1423 | 1 | 2 | 1 | 1 | 26.9 | 33.5 | 61.2 | 14 | 1 |
| s1423_T002 | 1 | 2 | 1 | 1 | 27.7 | 33.5 | 612 | 14 | 1 | |
| Maximum CC | s1423 | 1.4 | 2.8 | 1.4 | 1.4 | 372.1 | 77.1 | 258.2 | 18.4 | 1.4 |
| s1423_T002 | 1.4 | 2.8 | 1.4 | 1.4 | 372.1 | 77.1 | 258.2 | 18.4 | 1.4 | |
| Minimum CC | s1423 | 1.4 | 2.8 | 1.4 | 1.4 | 1.4 | 22.9 | 24.2 | 18.4 | 1.4 |
| s1423_T002 | 1.4 | 2.8 | 1.4 | 1.4 | 1.4 | 22.9 | 24.2 | 18.4 | 1.4 | |
| Average CC | s1423 | 1.4 | 2.8 | 1.4 | 1.4 | 50.9 | 35.5 | 138.9 | 18.4 | 1.4 |
| s1423_T002 | 1.4 | 2.8 | 1.4 | 1.4 | 51.2 | 35.5 | 138.9 | 18.4 | 1.4 | |
| Maximum CO | s1423 | 28 | 47 | 23 | 16 | 321 | 73 | 45 | 0 | >1000 |
| s1423_T002 | 28 | 47 | 23 | 16 | 353 | 73 | 45 | 0 | >1000 | |
| Minimum CO | s1423 | 28 | 47 | 23 | 16 | 0 | 0 | 0 | 0 | >1000 |
| s1423_T002 | 28 | 47 | 23 | 16 | 0 | 0 | 0 | 0 | >1000 | |
| Average CO | s1423 | 28 | 47 | 23 | 16 | 120.2 | 27.2 | 35.2 | 0 | >1000 |
| s1423_T002 | 28 | 47 | 23 | 16 | 122.8 | 27.2 | 35.2 | 0 | >1000 |
| Value | Evaluation Metrics | TP | FP | TN | FN | TPR | TNR | F1 |
|---|---|---|---|---|---|---|---|---|
| ML Mode | ||||||||
| KNN | 287 | 5 | 3411 | 16 | 94.7% | 99.9% | 96.5% | |
| RF | 296 | 2 | 3414 | 7 | 97.7% | 99.9% | 98.5% | |
| SVM | 285 | 20 | 3396 | 18 | 94.1% | 99.4% | 93.7% | |
| ML Mode | TP | FP | TN | FN | TPR | TNR | F1 | Time Consumption (ms) | |
|---|---|---|---|---|---|---|---|---|---|
| Our method | KNN | 281 | 4 | 4 | 11 | 96.2% | 50.0% | 97.4% | 21,648 |
| RF | 287 | 4 | 4 | 5 | 98.3% | 50.0% | 98.4% | 21,765 | |
| SVM | 280 | 5 | 3 | 12 | 95.9% | 37.5% | 97.0% | 21,832 | |
| [23] | KNN | 283 | 6 | 2 | 9 | 96.9% | 25.0% | 97.4% | 3258 |
| RF | 286 | 8 | 0 | 6 | 97.9% | 0 | 97.6% | 3034 | |
| SVM | 275 | 8 | 0 | 17 | 94.2% | 0 | 95.7% | 3197 |
| Value | Evaluation Metrics | TPR | TNR | F1 |
|---|---|---|---|---|
| Method | ||||
| Our RF-based method | 98.3% | 50.0% | 98.4% | |
| Our KNN-based method | 96.2% | 50.0% | 97.4% | |
| Our SVM-based method | 95.9% | 37.5% | 97% | |
| KNN-based method [29] | 90.9% | 93.1% | 79.7% | |
| DT-based method [29] | 86.4% | 98.6% | 83.6% | |
| NB-based method [29] | 100% | 65.2% | 34.7% | |
| TPR, TNR | ML Mode | KNN | RF | SVM |
|---|---|---|---|---|
| Search Method | ||||
| BFC | 97.3%, 100% | 97.7%, 100% | 93.4%, 100% | |
| Value | Evaluation Metrics | TPR | TNR | ||
|---|---|---|---|---|---|
| Netlist | |||||
| R-HTDetector | Our Method | R-HTDetector | Our Method | ||
| c2670_T000 | 100% | 100% | 85.9% | 100% | |
| c2670_T001 | 100% | 100% | 84.0% | 100% | |
| c2670_T002 | 75.0% | 80.0% | 90.9% | 99.9% | |
| c3540_T000 | 100% | 100% | 93.5% | 100% | |
| c3540_T001 | 100% | 100% | 64.6% | 100% | |
| c3540_T002 | 100% | 100% | 68.0% | 100% | |
| c5315_T000 | 87.5% | 100% | 78.4% | 100% | |
| c5315_T001 | 77.8% | 100% | 86.3% | 100% | |
| c5315_T002 | 100% | 100% | 71.0% | 100% | |
| s1423_T000 | 100% | 100% | 90.8% | 100% | |
| s1423_T001 | 83.3% | 100% | 91.9% | 100% | |
| s1423_T002 | 100% | 100% | 86.9% | 100% | |
| s13207_T000 | 100% | 100% | 96.2% | 100% | |
| s13207_T001 | 100% | 100% | 96.1% | 100% | |
| s13207_T002 | 100% | 100% | 95.5% | 100% | |
| Average | 94.9% | 98.7% | 85.3% | 100% | |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, J.; Zhai, G.; Gao, H.; Xu, L.; Li, X.; Li, Z.; Huang, Z.; Xie, C. A Hardware Trojan Detection and Diagnosis Method for Gate-Level Netlists Based on Machine Learning and Graph Theory. Electronics 2024, 13, 59. https://doi.org/10.3390/electronics13010059
Wang J, Zhai G, Gao H, Xu L, Li X, Li Z, Huang Z, Xie C. A Hardware Trojan Detection and Diagnosis Method for Gate-Level Netlists Based on Machine Learning and Graph Theory. Electronics. 2024; 13(1):59. https://doi.org/10.3390/electronics13010059
Chicago/Turabian StyleWang, Junjie, Guangxi Zhai, Hongxu Gao, Lihui Xu, Xiang Li, Zeyu Li, Zhao Huang, and Changjian Xie. 2024. "A Hardware Trojan Detection and Diagnosis Method for Gate-Level Netlists Based on Machine Learning and Graph Theory" Electronics 13, no. 1: 59. https://doi.org/10.3390/electronics13010059
APA StyleWang, J., Zhai, G., Gao, H., Xu, L., Li, X., Li, Z., Huang, Z., & Xie, C. (2024). A Hardware Trojan Detection and Diagnosis Method for Gate-Level Netlists Based on Machine Learning and Graph Theory. Electronics, 13(1), 59. https://doi.org/10.3390/electronics13010059






