Secure Multi-Level Privacy-Protection Scheme for Securing Private Data over 5G-Enabled Hybrid Cloud IoT Networks
Abstract
1. Introduction
2. Related Work
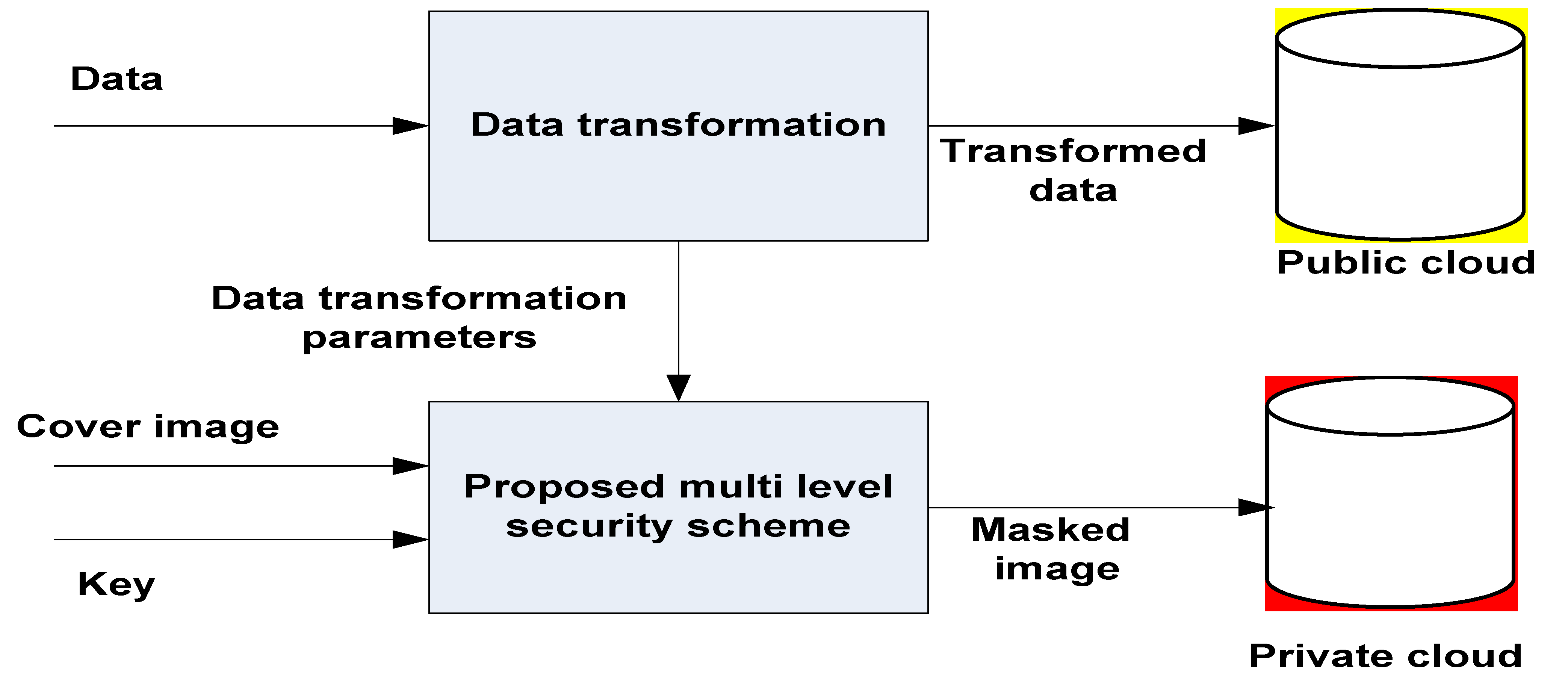
3. Multilevel Privacy-Protection Scheme
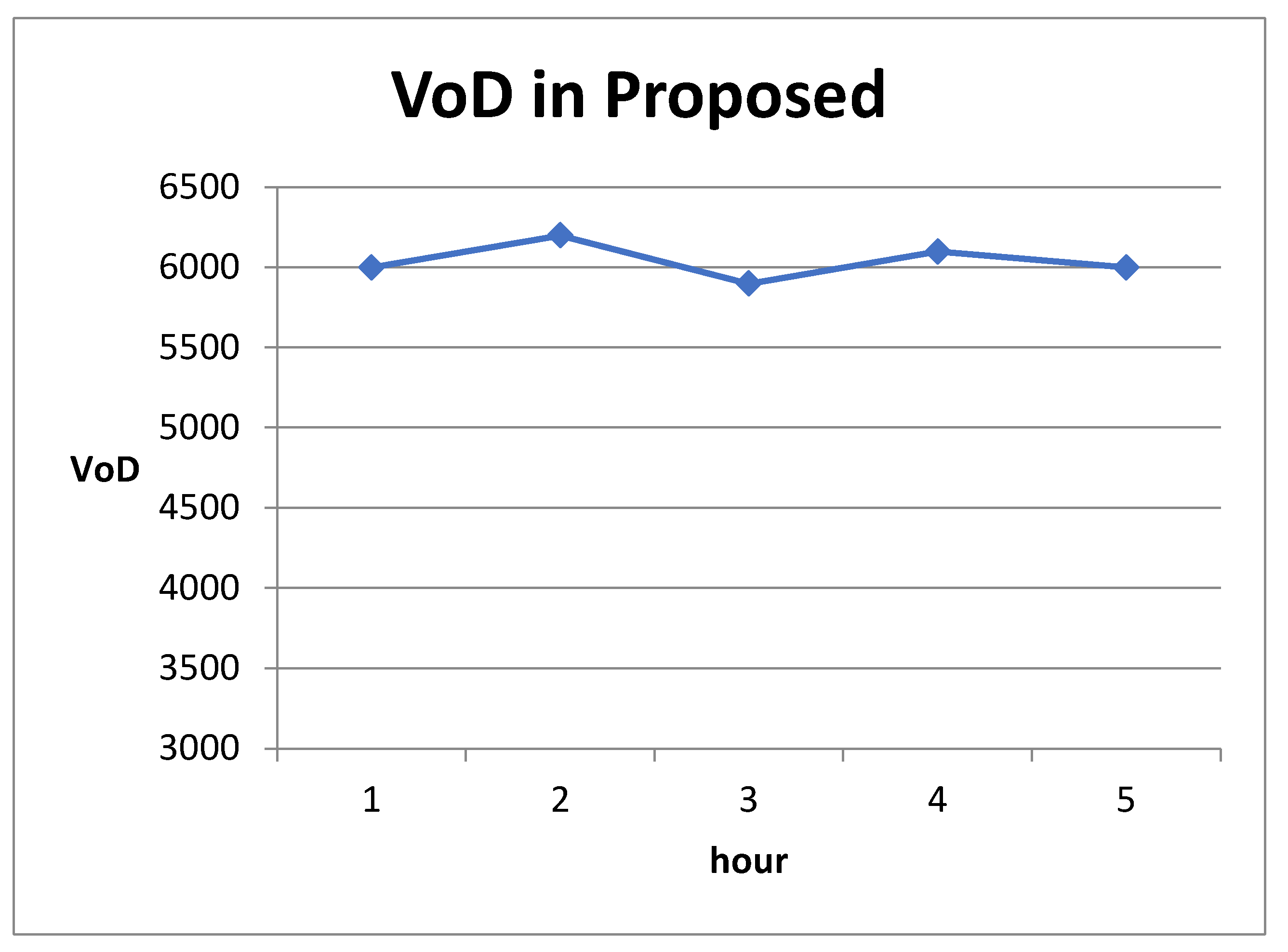
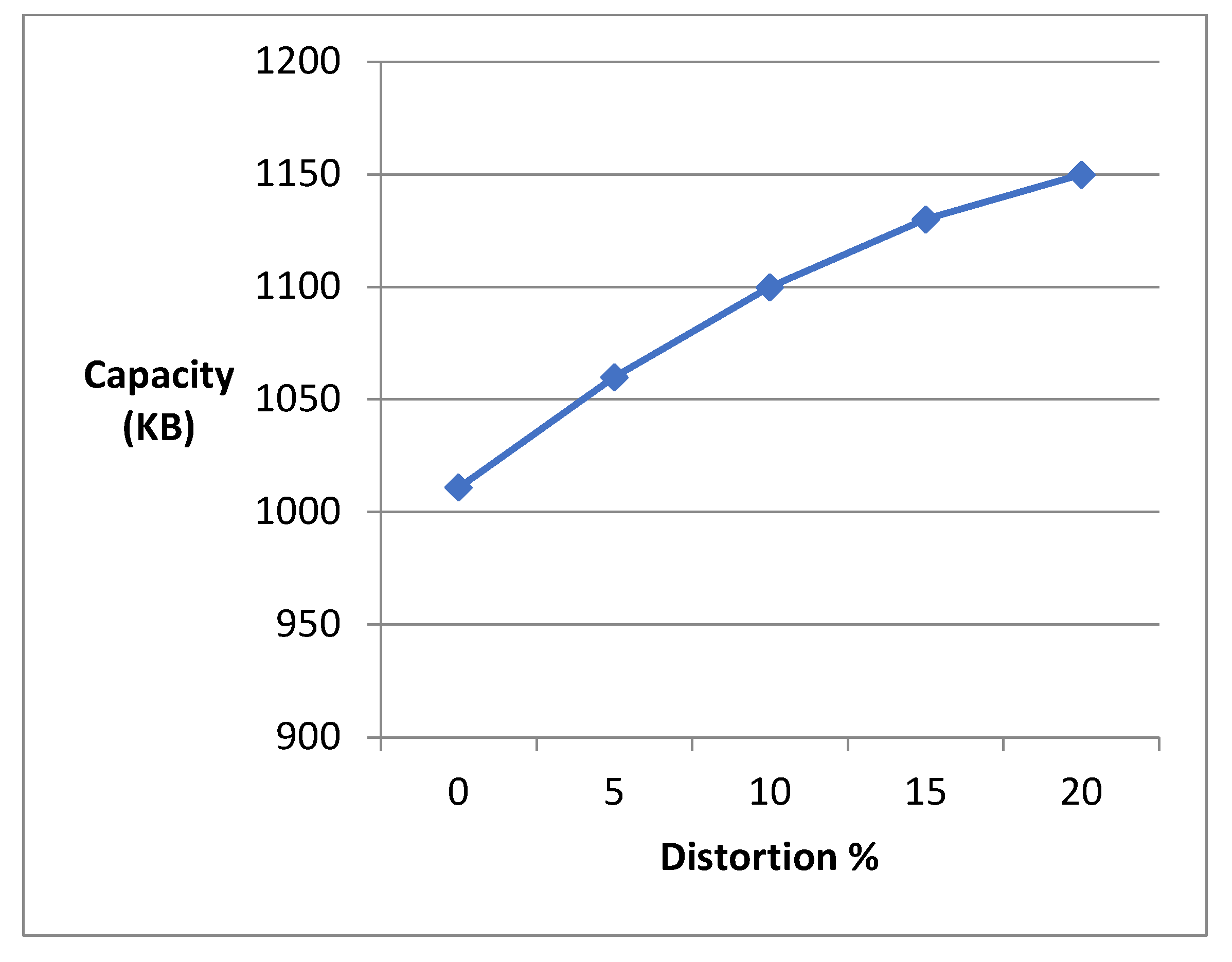
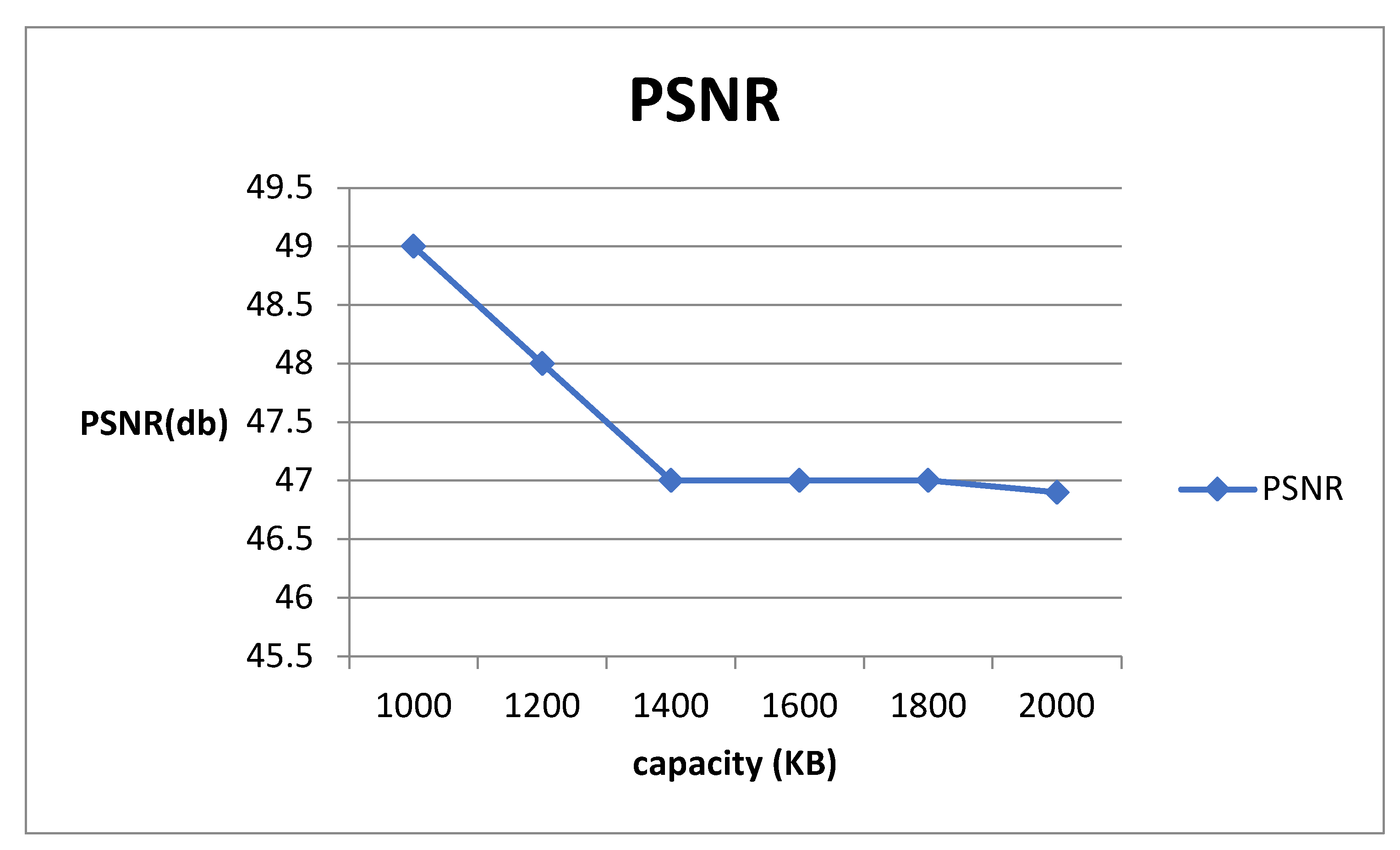
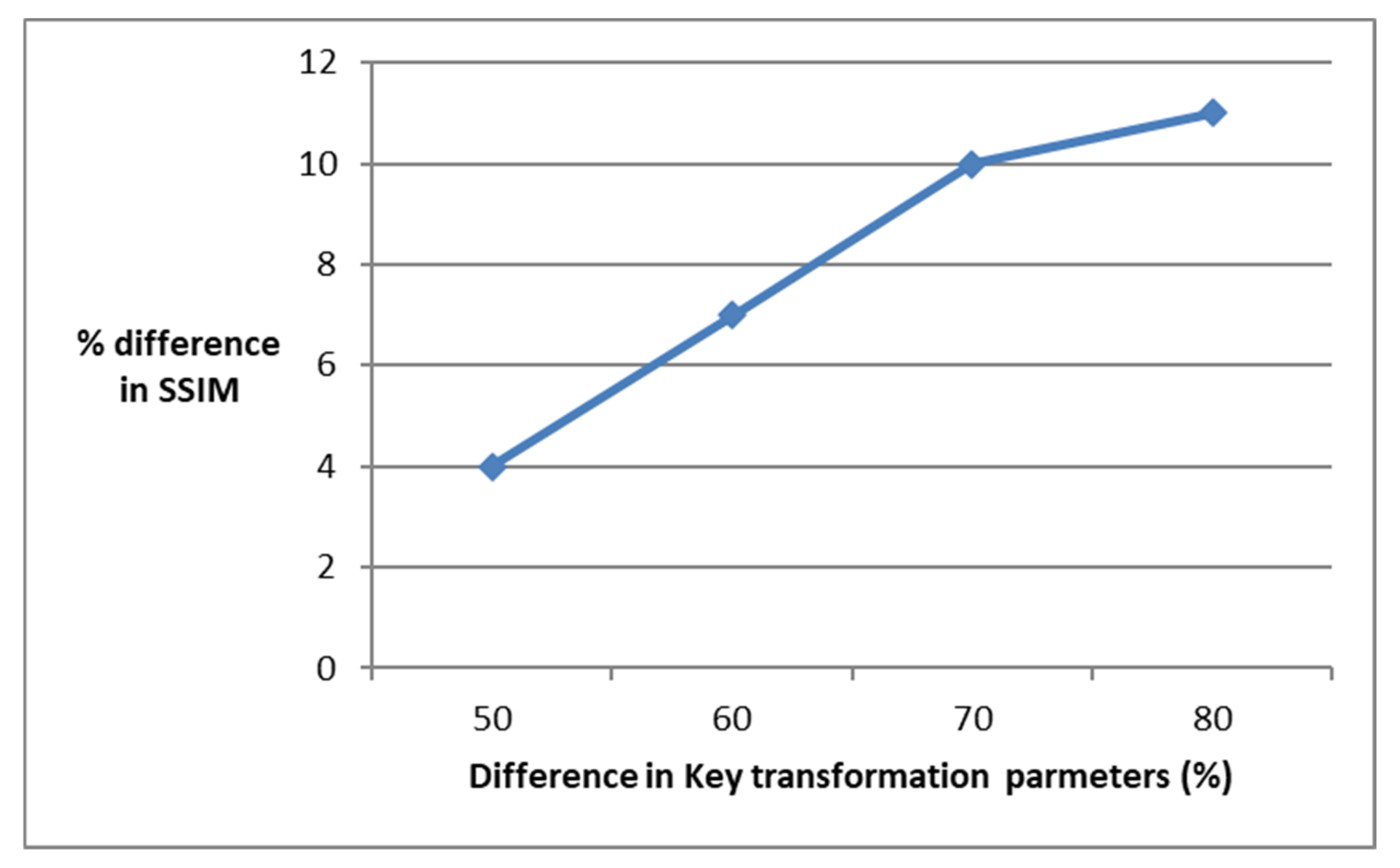
4. Results
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Fabian, B.; Ermakova, T.; Junghanns, P. Collaborative and secure sharing of healthcare data in multi-clouds. Inf. Syst. 2015, 48, 132–150. [Google Scholar] [CrossRef]
- Yang, J.; Li, J.; Niu, Y. A hybrid solution for privacy preserving medical data sharing in the cloud environment. Future Gener. Comput. Syst. 2015, 43–44, 7486. [Google Scholar] [CrossRef]
- Zhang, H.; Zhou, Z.; Ye, L.; Du, X. Towards Privacy Preserving Publishing of Set-Valued Data on Hybrid Cloud. IEEE Trans. Cloud Comput. 2018, 6, 316–329. [Google Scholar] [CrossRef]
- Zhou, Z.; Zhang, H.; Du, X.; Li, P.; Yu, X. Prometheus: Privacy-Aware Data Retrieval on Hybrid Clouds. In Proceedings IEEE INFOCOM; IEEE: Piscataway, NJ, USA, 2013. [Google Scholar]
- Lyu, L.; Bezdek, J.C.; Law, Y.W.; He, X.; Palaniswami, M. Privacy-preserving collaborative fuzzy clustering. Data Knowl. Eng. 2018, 116, 21–41. [Google Scholar] [CrossRef]
- Chen, K.; Sun, G.; Liu, L. Towards Attack-Resilient Geometric Data Perturbation; Wright State University: Dayton, OH, USA, 2007. [Google Scholar] [CrossRef]
- Chen, K.; Liu, L. Geometric data perturbation for privacy preserving outsourced data mining. Knowl. Inf. Syst. 2011, 29, 657–695. [Google Scholar] [CrossRef]
- Yuan, X.; Wang, X.; Wang, C.; Weng, J.; Ren, K. Enabling Secure and Fast Indexing for Privacy-Assured Healthcare Monitoring via Compressive Sensing. IEEE Trans. Multimed. 2016, 18, 2002–2014. [Google Scholar] [CrossRef]
- Huang, X.; Du, X. Efficiently secure data privacy on hybrid cloud. In Proceedings of the 2013 IEEE International Conference on Communications (ICC), Budapest, Hungary, 9–13 June 2013; pp. 1936–1940. [Google Scholar]
- Abbas, M.S.; Mahdi, S.S.; Hussien, S.A. Security Improvement of Cloud Data Using Hybrid Cryptography and Steganography. In Proceedings of the 2020 International Conference on Computer Science and Software Engineering (CSASE), Duhok, Iraq, 16–18 April 2020; pp. 123–127. [Google Scholar]
- Huang, X.; Du, X. Achieving big data privacy via hybrid cloud. In Proceedings of the 2014 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, ON, Canada, 27 April–2 May 2014; pp. 512–517. [Google Scholar]
- Abrishami, H.; Rezaeian, A.; Naghibzadeh, M. A novel deadline-constrained scheduling to preserve data privacy in hybrid Cloud. In Proceedings of the 2015 5th International Conference on Computer and Knowledge Engineering (ICCKE), Mashhad, Iran, 29 October 2015; pp. 234–239. [Google Scholar]
- Xu, X.; Zhao, X. A Framework for Privacy-Aware Computing on Hybrid Clouds with Mixed-Sensitivity Data. In Proceedings of the 2015 IEEE 17th International Conference on High Performance Computing and Communications, 2015 IEEE 7th International Symposium on Cyberspace Safety and Security, and 2015 IEEE 12th International Conference on Embedded Software and Systems, Washington, DC, USA, 24–26 August 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 1344–1349. [Google Scholar]
- Li, J.; Li, Y.K.; Chen, X.; Lee, P.P.C.; Lou, W. A Hybrid Cloud Approach for Secure Authorized Deduplication. IEEE Trans. Parallel Distrib. Syst. 2015, 26, 1206–1216. [Google Scholar] [CrossRef]
- Saritha, K.; Subasree, S. Analysis of hybrid cloud approach for private cloud in the de-duplication mechanism. In Proceedings of the 2015 IEEE International Conference on Engineering and Technology (ICETECH), Coimbatore, India, 20 March 2015; pp. 1–3. [Google Scholar]
- Sridhar, S.; Smys, S. A hybrid multilevel authentication scheme for private cloud environment. In Proceedings of the 2016 10th International Conference on Intelligent Systems and Control (ISCO), Coimbatore, India, 7–8 January 2016; pp. 1–5. [Google Scholar]
- Udendhran, R. A hybrid approach to enhance data security in cloud storage. In Proceedings of the Second International Conference on Internet of things, Data and Cloud Computing (ICC ‘17). Association for Computing Machinery, New York, NY, USA, 22–23 March 2017; Article 90. pp. 1–6. [Google Scholar]
- Nagaty, K.A. A Secured Hybrid Cloud Architecture for mHealth Care. In Mobile Health. Springer Series in Bio-/Neuroinformatics; Adibi, S., Ed.; Springer: Cham, Switzerland, 2015; Volume 5. [Google Scholar]
- Qureshi, B.; Koubaa, A.; Al Mhaini, M. A Lightweight and Secure Framework for Hybrid Cloud Based EHR Systems. In Proceedings of the First International Conference, SCITA 2017, Jeddah, Saudi Arabia, 27–29 November 2017; Springer International Publishing: Berlin/Heidelberg, Germany, 2018. [Google Scholar] [CrossRef]
- Arrhythmia Data Set. Available online: https://archive.ics.uci.edu/ml/datasets/Arrhythmia (accessed on 12 October 2022).
- Reddy, V.S.; Rao, B.T. A Combined Clustering and Geometric Data Perturbation Approach for Enriching Privacy Preservation of Healthcare Data in Hybrid Clouds. Int. J. Intell. Eng. Systems 2018, 11, 201–210. [Google Scholar] [CrossRef]
- Ma, X.; Yang, W.; Zhu, Y.; Bai, Z. A Secure and Efficient Data Deduplication Scheme with Dynamic Ownership Management in Cloud Computing. In Proceedings of the 2022 IEEE International Performance, Computing, and Communications Conference (IPCCC), Austin, TX, USA, 11–13 November 2022; pp. 194–201. [Google Scholar]
- Hybrid Cloud Networks. Available online: https://www.dropbox.com/ (accessed on 20 October 2022).
- Hughes, B.; Bothe, S.; Farooq, H.; Imran, A. Generative adversarial learning for machine learning empowered self organizing 5G networks. In Proceedings of the 2019 international conference on computing, networking and communications (ICNC), Honolulu, HI, USA, 18–21 February 2019; pp. 282–286. [Google Scholar]

| Solution | Summary | Gap |
|---|---|---|
| Fabian et al. [1] | Cryptographic secret sharing along with attribute-based encryption | Sharing location and the access control parameters are kept in the cloud, and this can be compromised |
| Yang et al. [2] | Data are split vertically and encrypted before being published to the cloud | Method has a higher security risk of compromise of partition information and encryption keys |
| Zhang et al. [3] | Data are partitioned using a quasi-identifier partitioning technique | Approach is completely insecure against leakage of partition information stored in the cloud |
| Zhou et al. [4] | Data-partition strategy | Security of keys and partition information is not considered in this work |
| Lyu et al. [5] | Two-stage data perturbation to secure data in the hybrid cloud | Scheme is insecure against data-compromise attacks |
| Chen et al. [6] | Geometric data-perturbation scheme for securing data | Perturbation sequence stored in the private cloud is insecure against data-compromise attacks |
| Chen et al. [7] | Random projection-based data perturbation to secure data in the cloud | Approach did not consider data compromise in the cloud |
| Yuan et al. [8] | Compressed sensing for data perturbation before storing in the cloud | Reconstruction matrix is kept in the private cloud, and it is insecure against data-compromise attacks on it |
| Huang et al. [9] | Securing images on the hybrid cloud by splitting into blocks and shuffling | Even if partial information on shuffling order is leaked, the entire image can be reconstructed by the attacker |
| Abbas et al. [10] | Combined cryptography, steganography, and hashing to ensure data privacy in the hybrid cloud | Mechanism is not scalable, and storing the keys in the private cloud with ciphering makes it insecure |
| Huang et al. [11] | Pixel values are modified using a random one-to-one function | Shuffling order and pixel-mapping functions are kept in the cloud, posing a data-leakage issue |
| Xu et al. [13] | Sensitive data aggregation scheme | Aggregation rules are stored in the private cloud and upon leakage of it, the privacy of data in the public cloud is at risk |
| Li et al. [14] | Convergent encryption scheme for the hybrid cloud | Security of encryption keys during the compromise of private cloud data is not considered |
| Saritha et al. [15] | Multilevel authentication | Scheme is not secure against internal attacks on data |
| Sridhar et al. [16] | Hybrid multilevel authentication | Scheme is not able to secure data from insider attacks and virtualization attacks |
| Nagaty et al. [18] | Integrated cryptography and access control to secure data in the hybrid cloud | Access control information along with cryptography keys are stored in the private cloud without any security |
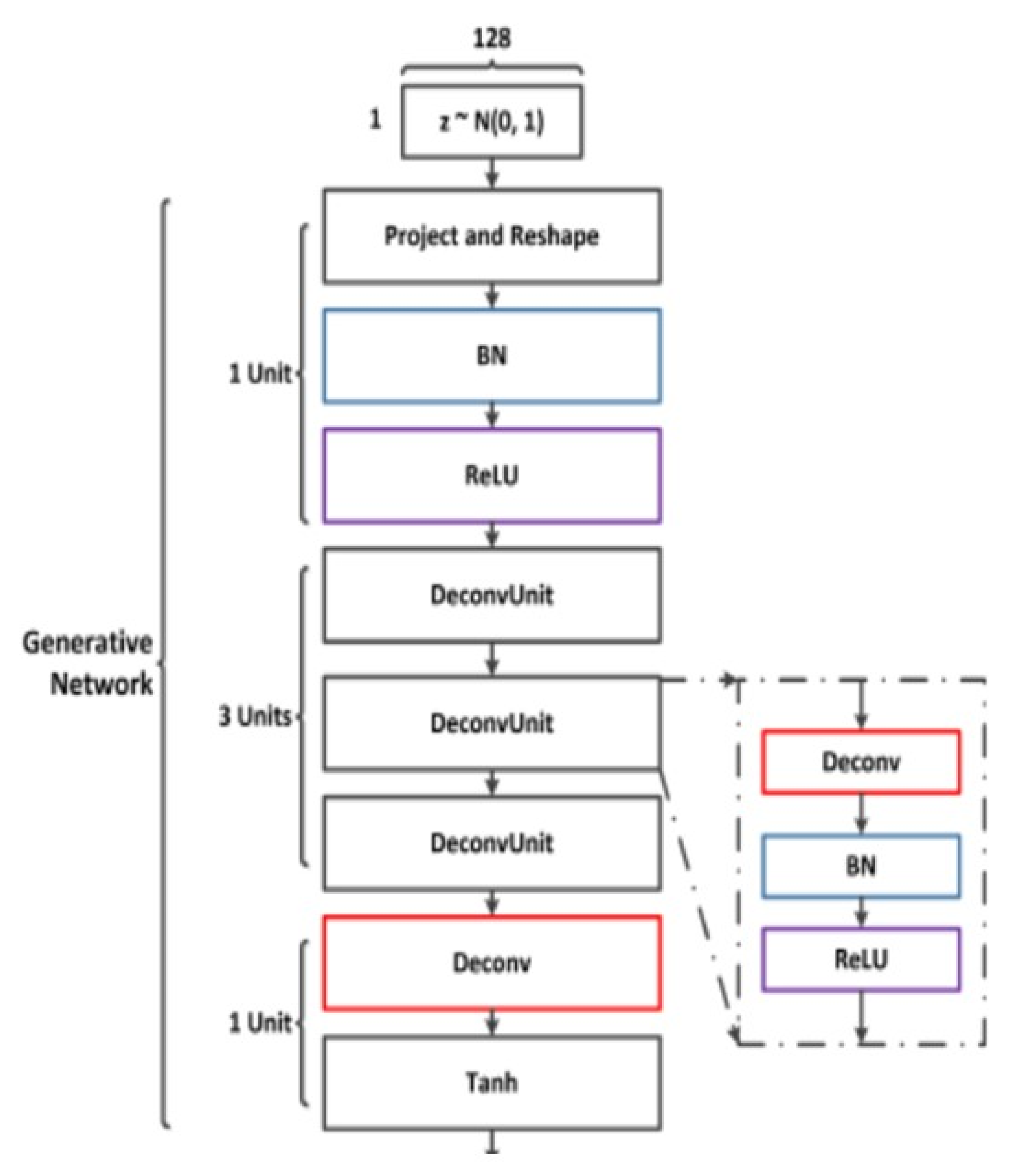
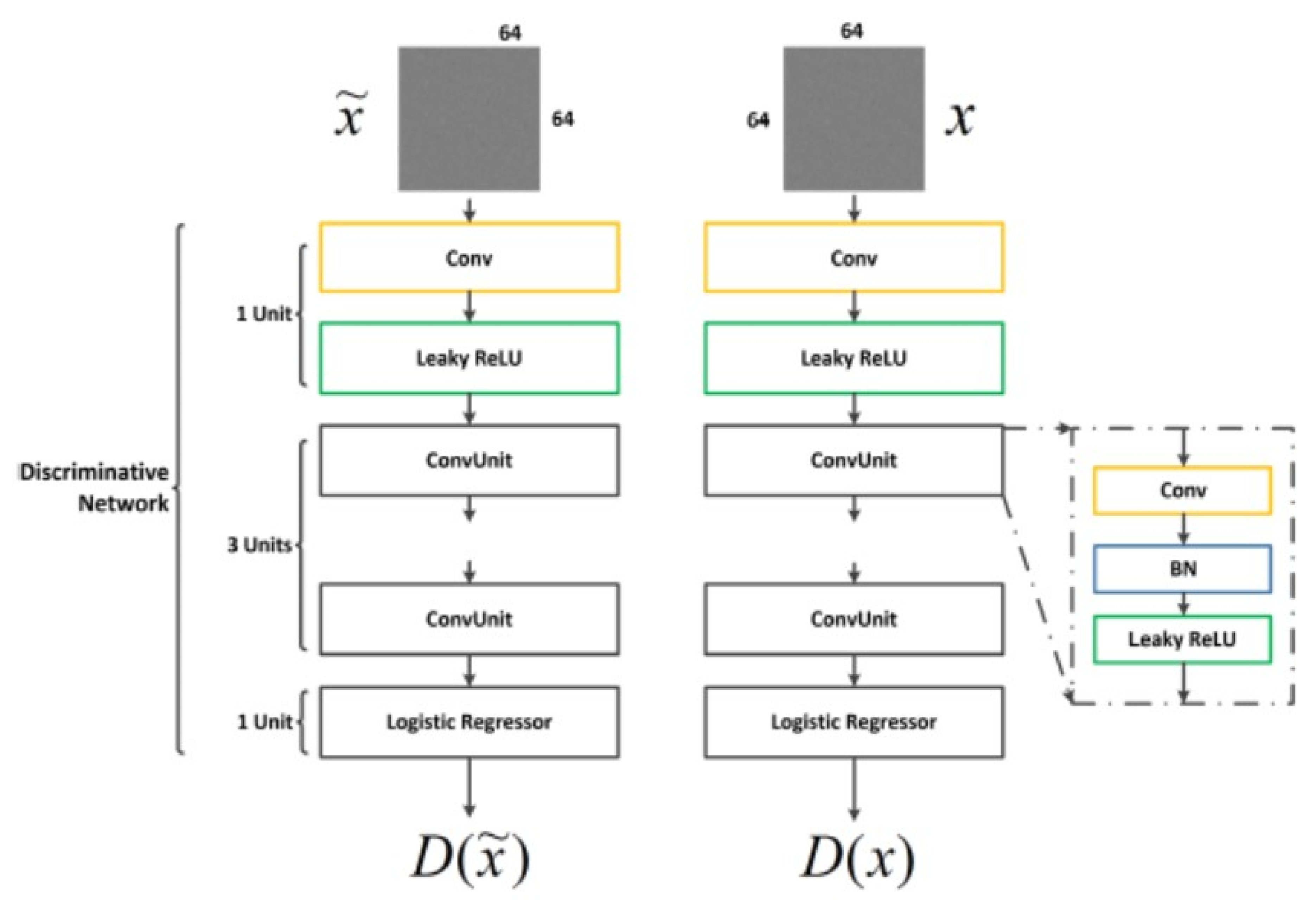
| Conv | Convolution with Kernel Size 5 × 5 |
|---|---|
| Deconv | De-convolution |
| BN | Batch normalization |
| ReLU | Rectified Linear Unit |
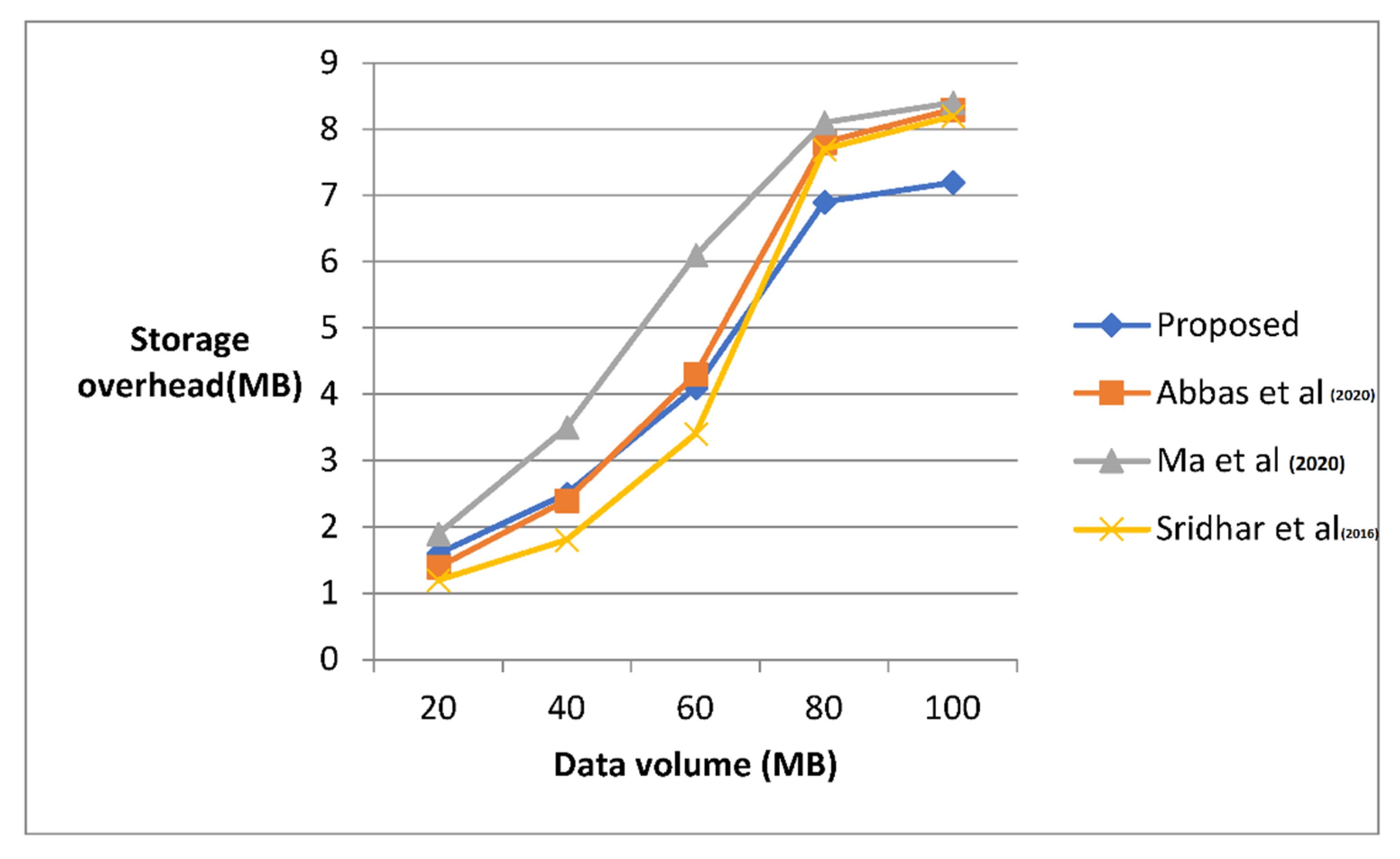
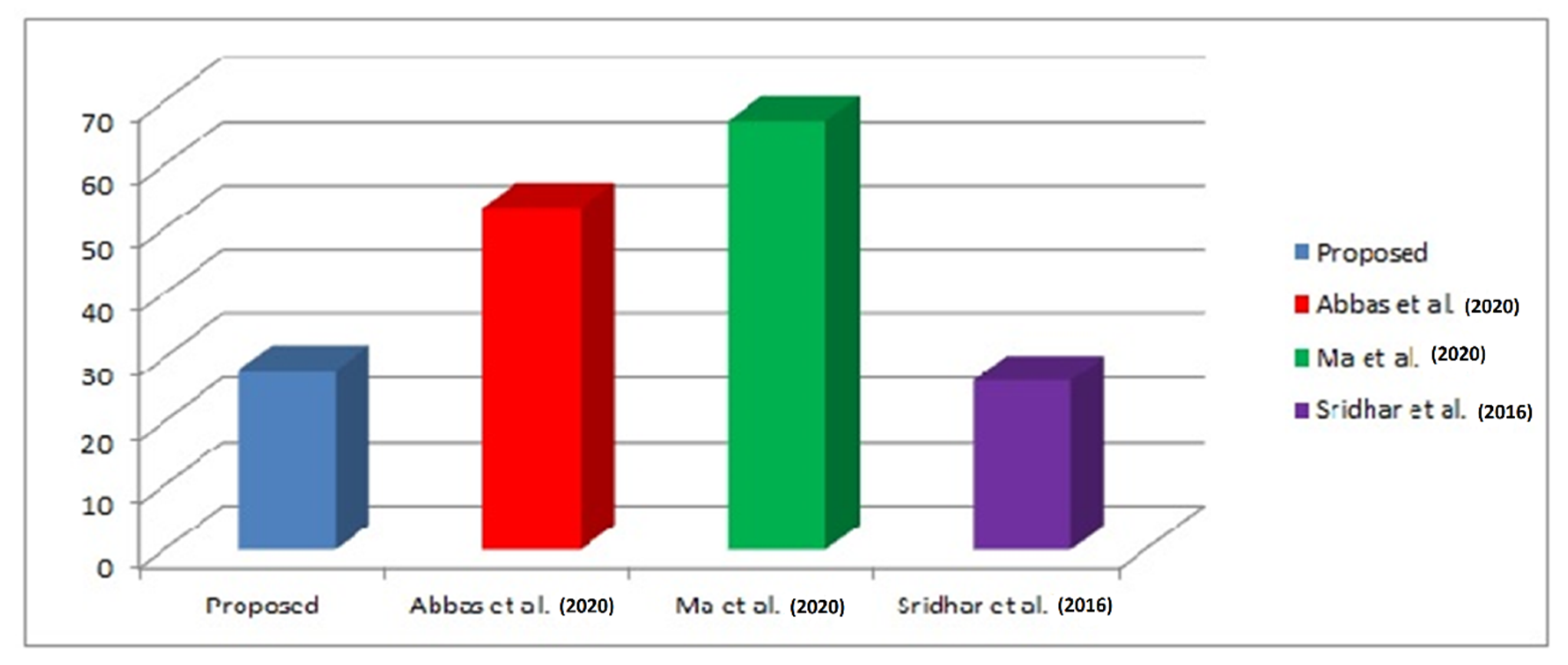
| Size (MB) | Storage Overhead (MB) | |||
|---|---|---|---|---|
| Proposed | Abbas et al. [10] | Ma et al. [22] | Sridhar et al. [16] | |
| 20 | 1.6 | 1.4 | 1.9 | 1.2 |
| 40 | 2.5 | 2.4 | 3.5 | 1.8 |
| 60 | 4.1 | 4.3 | 6.1 | 3.4 |
| 80 | 6.9 | 7.8 | 8.1 | 7.7 |
| 100 | 7.2 | 8.3 | 8.4 | 8.2 |
| Average | 4.46 | 4.84 | 5.6 | 4.46 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Budati, A.K.; Vulapula, S.R.; Shah, S.B.H.; Al-Tirawi, A.; Carie, A. Secure Multi-Level Privacy-Protection Scheme for Securing Private Data over 5G-Enabled Hybrid Cloud IoT Networks. Electronics 2023, 12, 1638. https://doi.org/10.3390/electronics12071638
Budati AK, Vulapula SR, Shah SBH, Al-Tirawi A, Carie A. Secure Multi-Level Privacy-Protection Scheme for Securing Private Data over 5G-Enabled Hybrid Cloud IoT Networks. Electronics. 2023; 12(7):1638. https://doi.org/10.3390/electronics12071638
Chicago/Turabian StyleBudati, Anil Kumar, Sridhar Reddy Vulapula, Syed Bilal Hussian Shah, Anas Al-Tirawi, and Anil Carie. 2023. "Secure Multi-Level Privacy-Protection Scheme for Securing Private Data over 5G-Enabled Hybrid Cloud IoT Networks" Electronics 12, no. 7: 1638. https://doi.org/10.3390/electronics12071638
APA StyleBudati, A. K., Vulapula, S. R., Shah, S. B. H., Al-Tirawi, A., & Carie, A. (2023). Secure Multi-Level Privacy-Protection Scheme for Securing Private Data over 5G-Enabled Hybrid Cloud IoT Networks. Electronics, 12(7), 1638. https://doi.org/10.3390/electronics12071638