An Optimized, Dynamic, and Efficient Load-Balancing Framework for Resource Management in the Internet of Things (IoT) Environment
Abstract
1. Introduction
- Segmenting fog processes
- Identifying nodes with extra storage space
- Dynamically allocating resources to various parts of the fog web
- Balancing workloads with global resource allocation
- This paper discusses three massive problems: load balancing, energy use, and computing cost.
- Present a particular technique in this work called dynamic energy-efficient load balancing (DEELB) to handle these IoT resource allocation issues.
Background
- A mapping is created at the virtual machine level between applications loaded in the cloud on the virtual machine. The load balancer assigns the required virtual machine to actual machines to balance the load on various PC programs [25].
- A virtual machine-to-host resource mapping that enables the host to handle numerous incoming application requests.
2. Related Literature
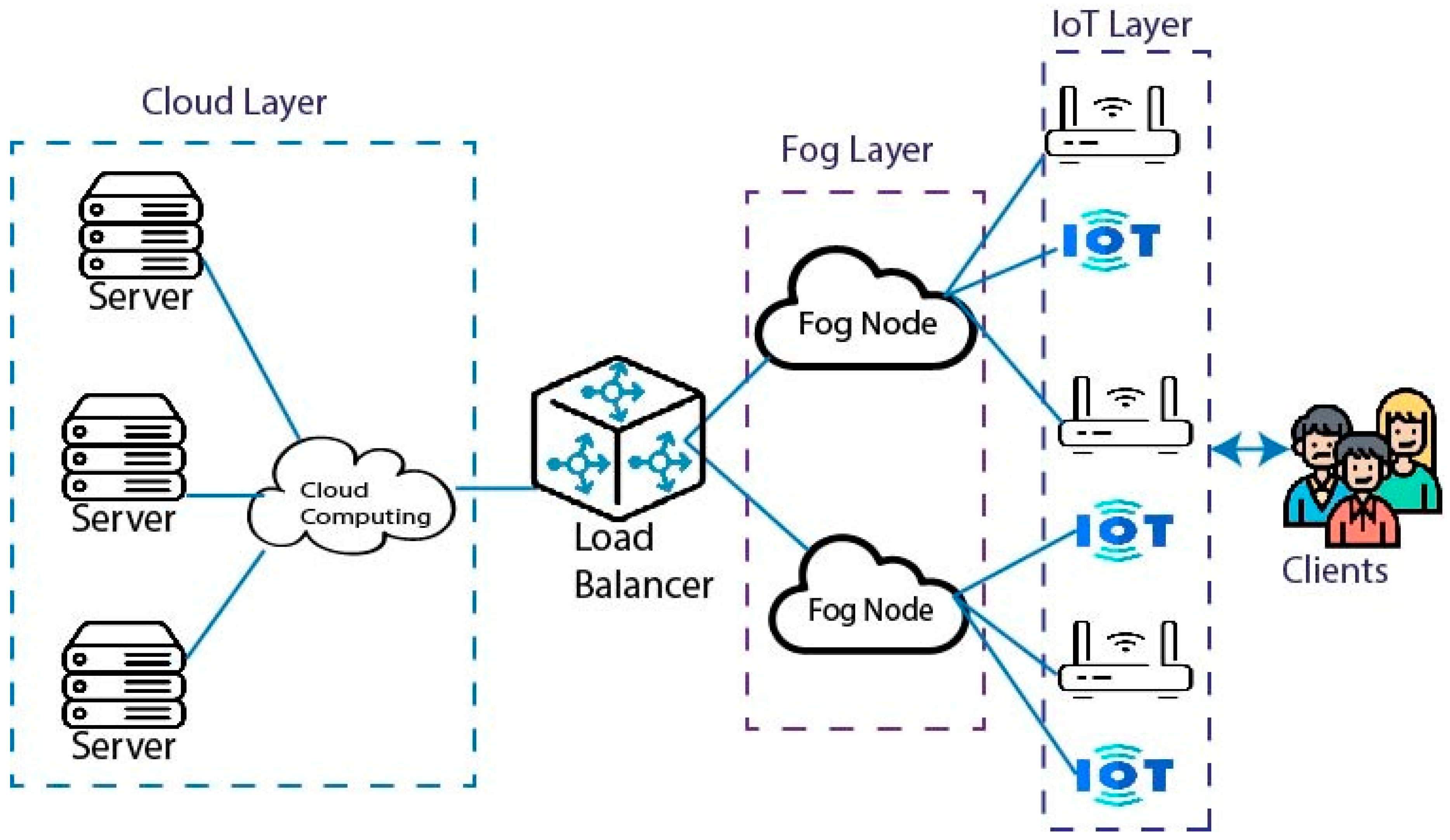
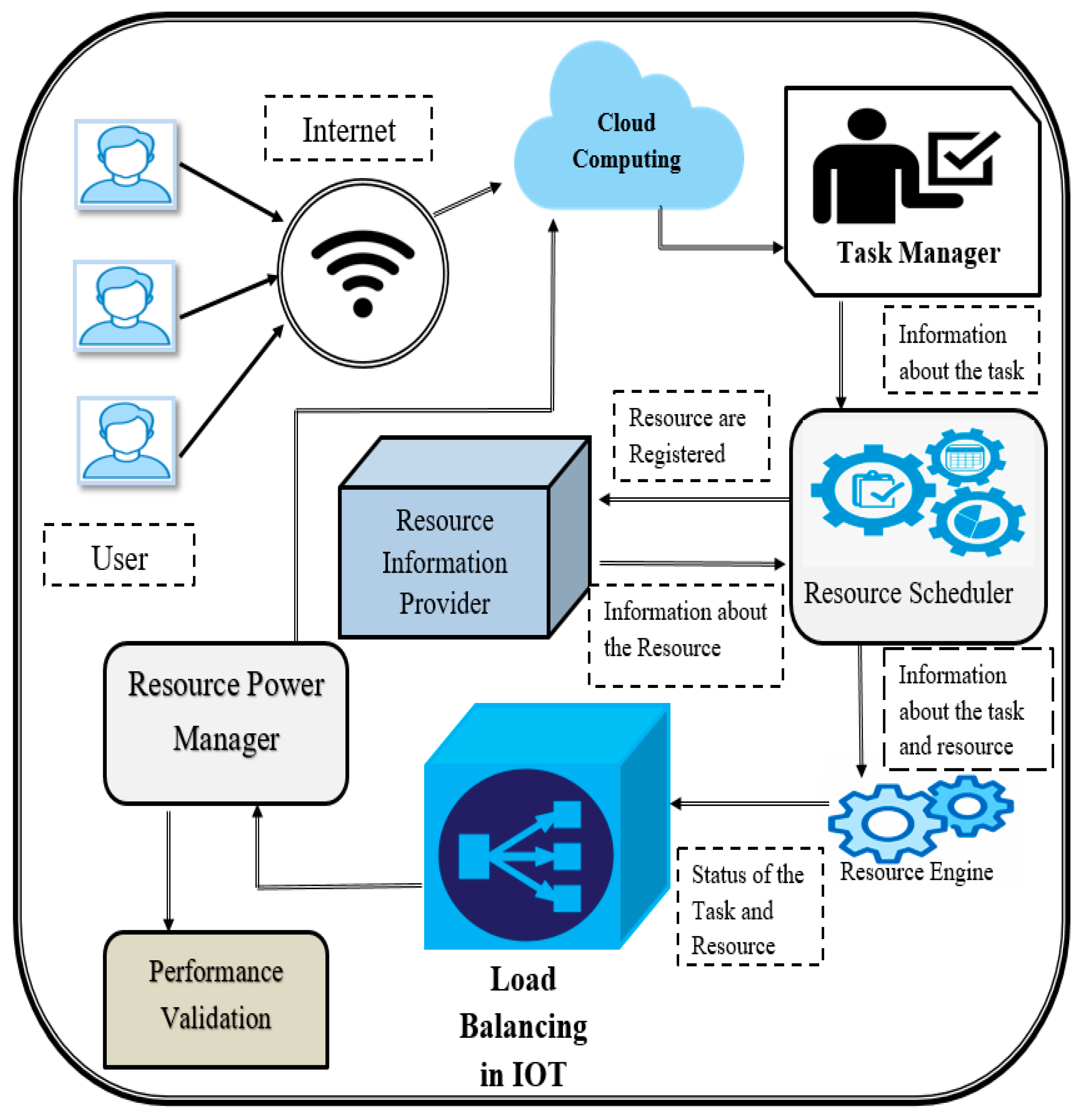
3. Proposed System
- The user will send the Task Manager “n” tasks. Based on the instructions it provides, each activity’s computing cost and energy consumption are seen as being preset.
- In this scenario, the information provider will register n resources via the Resource Registration and Inventory Protocol. Each task must also have specified computational expenses and energy requirements for each resource based on the work instructions.
- The Tasks Manager sends task information to the Resource Scheduler. Jobs are arranged in descending order based on cost and energy calculations: S1S2R2 > R3…Rn.
- RIP provides information about resources that are readily available to the Resource Scheduler. The available resources are arranged according to computational cost and energy consumption: R1 > R2 > R3…Rn.
- The Resource Engine needs data from the Resource Scheduler regarding jobs and available resources to carry out its task.
- When tasks are assigned to available resources, the Resource Engine starts the execution process and updates the Resource Load Manager on its status.
- After a process, the Resource Load Manager will inform the Resource Power Manager of the current resource load.
- The Resource Power Manager decides whether or not the resource is powered on based on the resource’s usage.
- If everything goes as planned, the Resource Engine will collect and provide the data to the user.
3.1. Energy Efficiency Problem Formulation
3.2. DEELB Strategy Components
- (1)
- User: A User is a person or thing that makes requests for things to be done. A task may be submitted simultaneously by one or more people.
- (2)
- Task Manager: User tasks are collected by the Task Manager and sent to the Resource Scheduler for scheduling. The Task Manager is in charge of making sure that the tasks submitted are legitimate. The Task Manager also keeps track of how much energy and money each task uses in the calculation.
- (3)
- Resource Information Provider: In addition to registration, the Resource Information Provider (RIP) also disseminates knowledge about the resources that are accessible. Additionally, the data includes the resources’ computed costs and energy usage.
- (4)
- Resource Scheduler: The Resource Scheduler gathers resource information from the Resource Information Provider and task information from the Task Manager. The Resource Scheduler subsequently sorts the submitted jobs.
3.3. Load-Balancing Model in the IoT Environment
4. Result and Discussion
4.1. Experiment Setup
4.2. Evaluation Parameters
- (a)
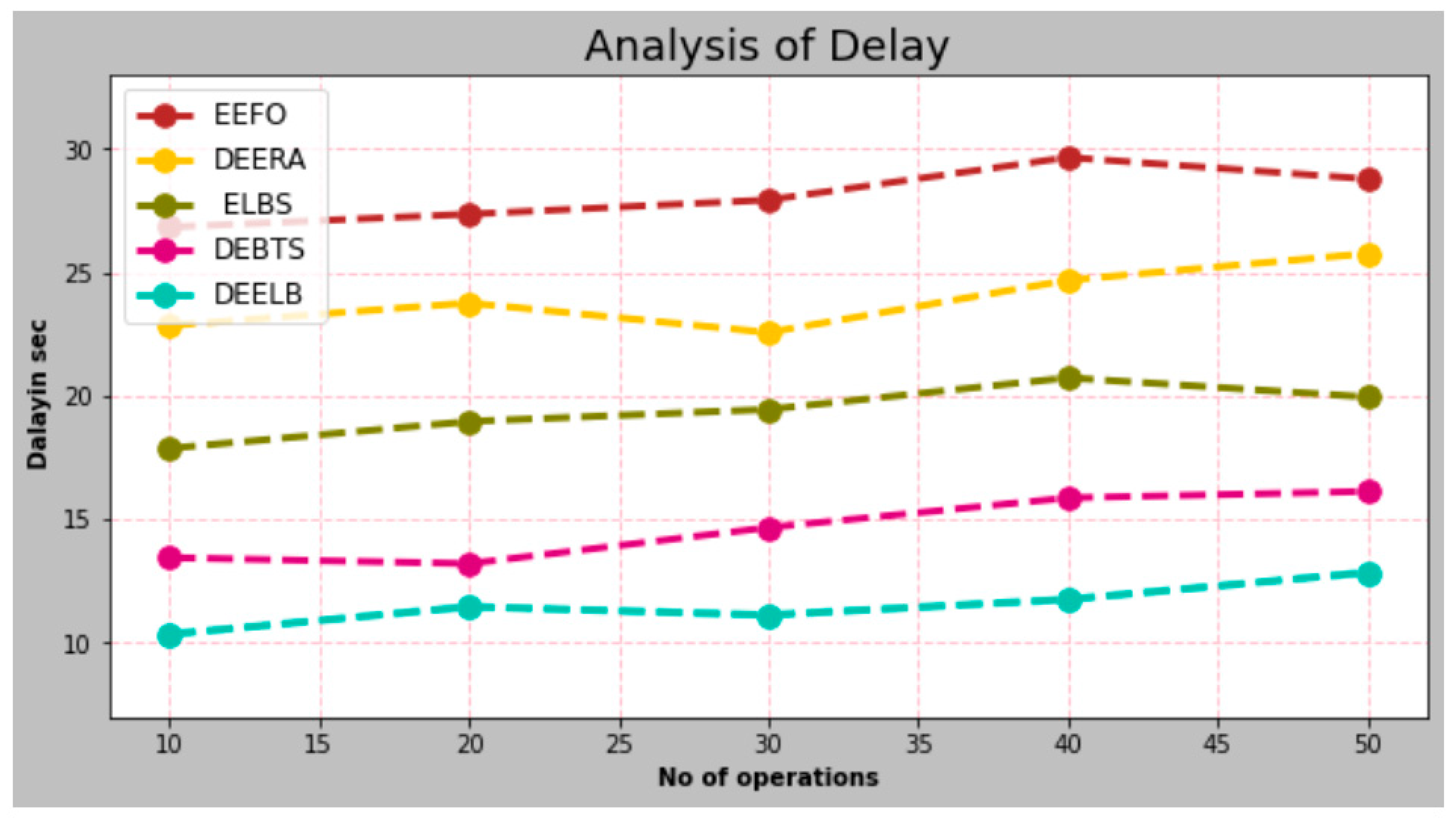
- Delay
- (b)
- Response Time
- (c)
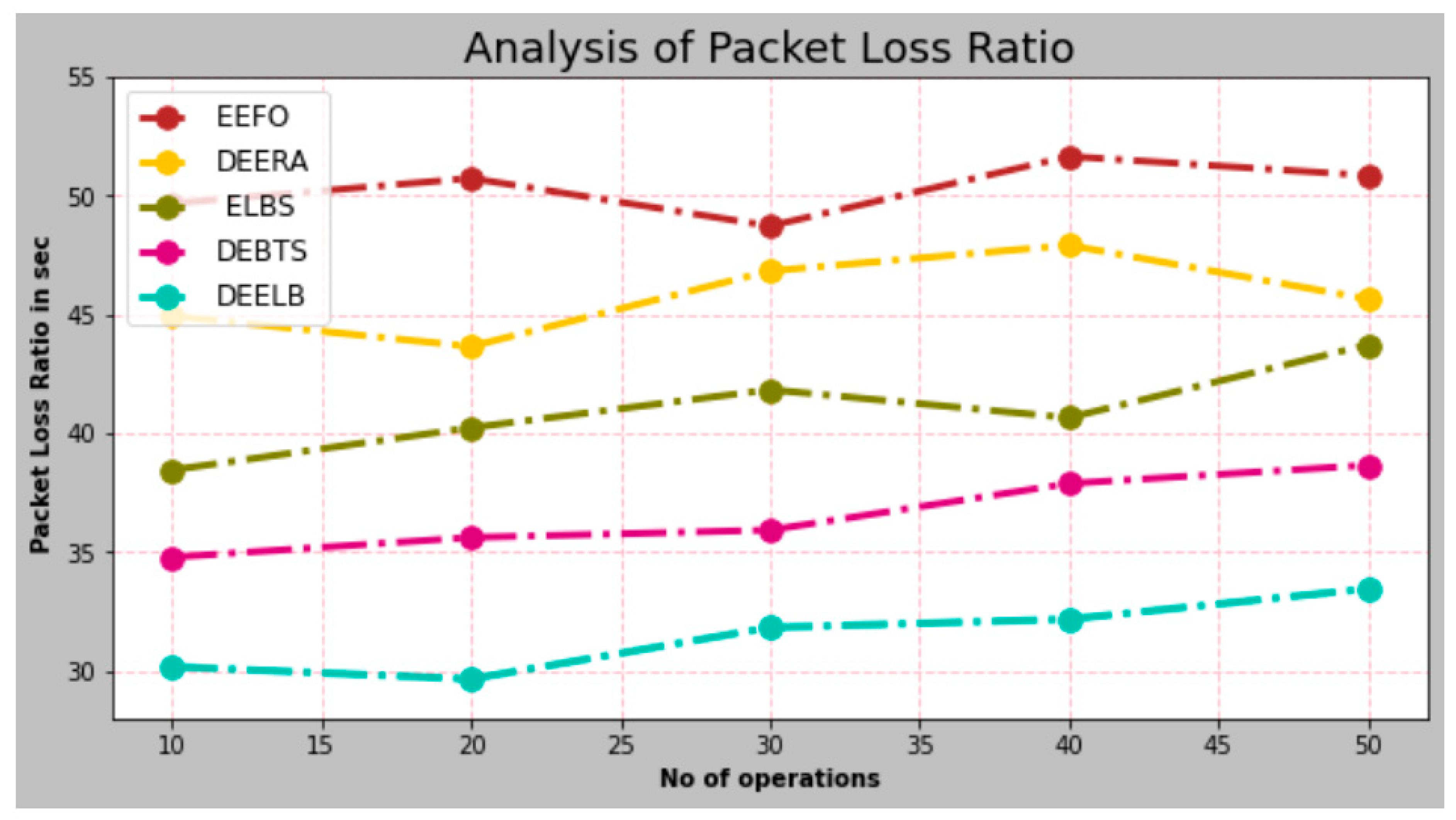
- Packet Loss Ratio
- (d)
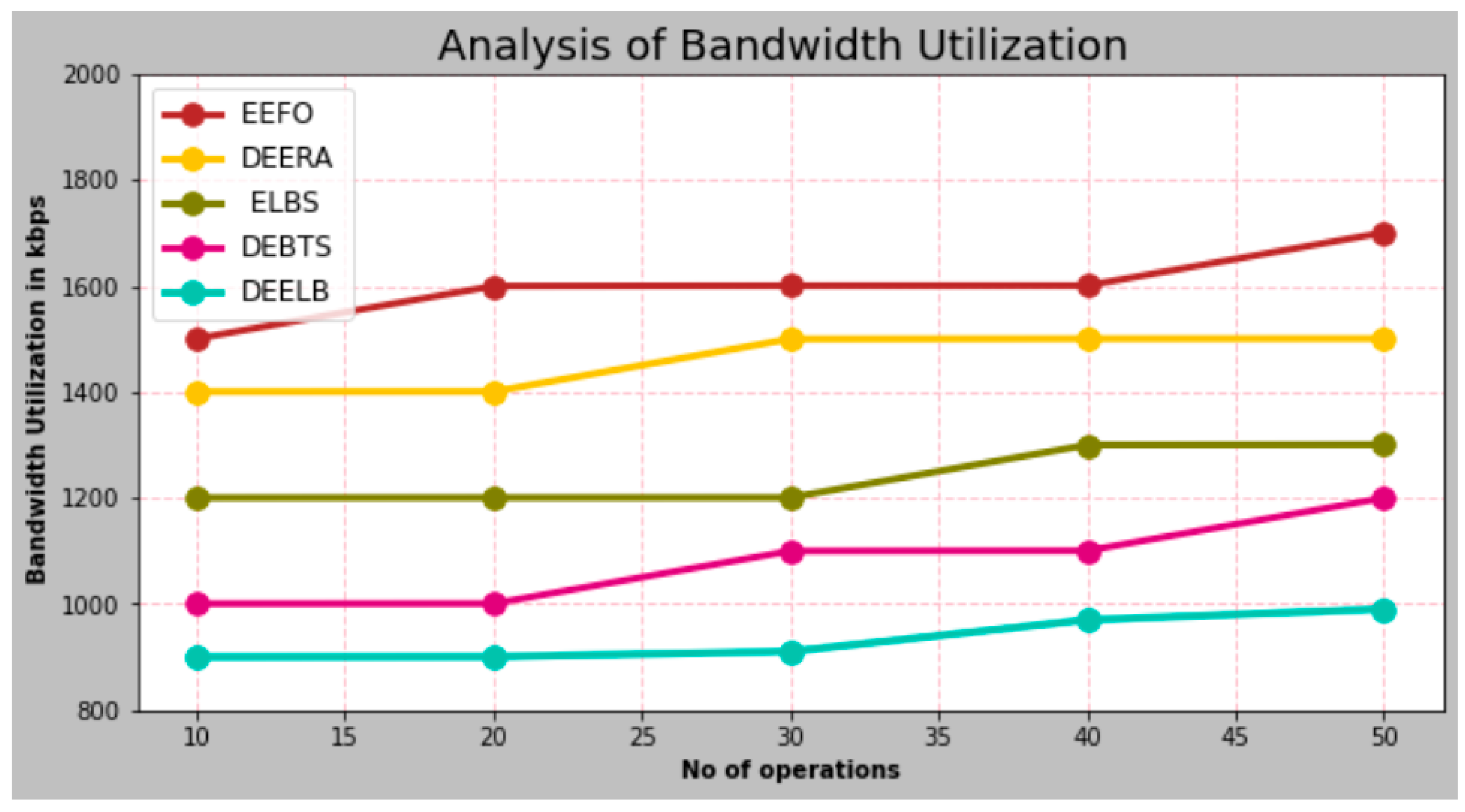
- Bandwidth Utilization
- (e)
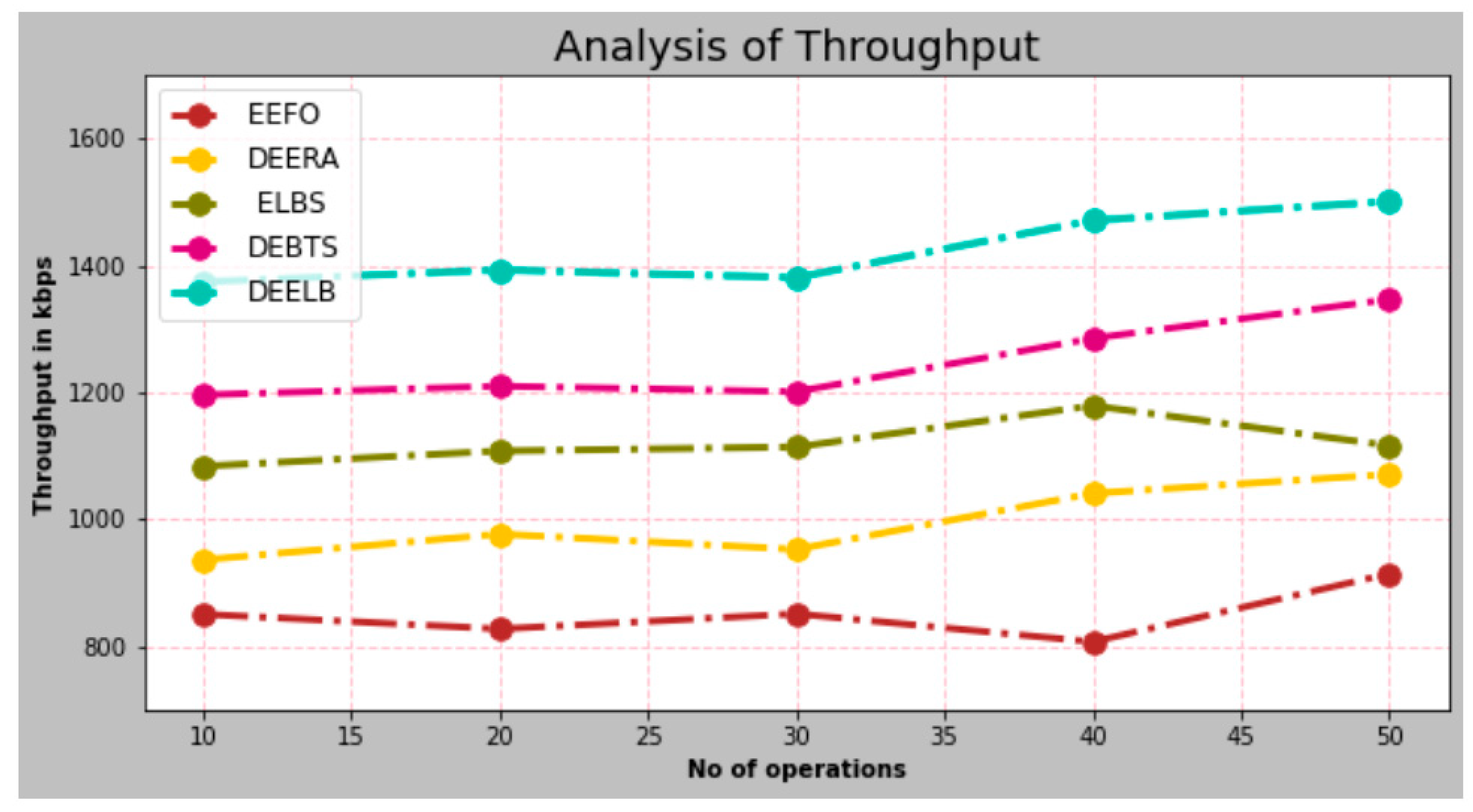
- Throughput
- (f)
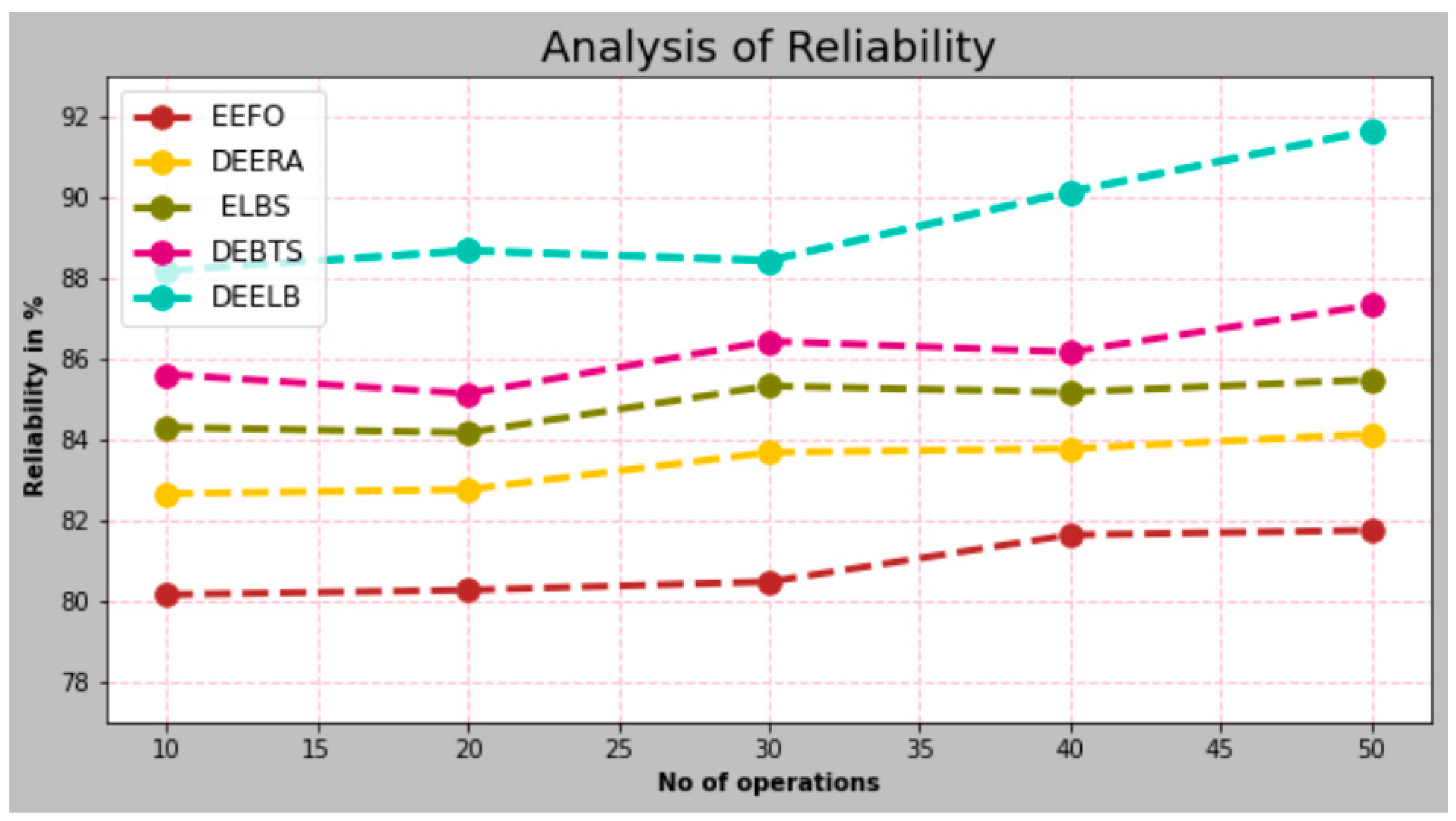
- Reliability
- (g)
- Packet Delivery Ratio
5. Future Research Work
- Service Migration: In the future, we will try to analyze the detrimental effects of service migration on various factors, such as traffic for different computer node types, service migration cost, service migration performance deterioration, and data transmission. We will also devise a plan to balance service migration’s advantages and disadvantages.
- Security Concern: Security concerns and standardization are significant challenges to dynamic load balancing and orchestration. While orchestration provides dynamic allocation and mobility for IoT nodes, it will require further hopping of data that may cause security breaches that have not been thoroughly examined yet. There are also many heterogeneous devices in a fog environment, so it is not easy to provide a standard procedure, and less effort has been expended towards such standardization. These aspects can also be considered for future research. Besides these future plans, blockchain integration in fog computing and its effect on load-balancing mechanisms can also be studied in detail [38].
- Machine Learning Application: Traditional load-balancing approaches are generally not very efficient for dynamic conditions. Machine learning (ML) can be suitable for implementing dynamic load balancing when conditions change swiftly. Some research has been done in this domain, but further research is needed, especially in heterogeneous environments. A detailed study to find the best-suited ML approach in such conditions is needed as well [40].
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Lin, Z.; Lin, M.; De Cola, T.; Wang, J.-B.; Zhu, W.-P.; Cheng, J. Supporting IoT with Rate-Splitting Multiple Access in Satellite and Aerial-Integrated Networks. IEEE Internet Things J. 2021, 8, 11123–11134. [Google Scholar] [CrossRef]
- Niu, H.; Lin, Z.; Chu, Z.; Zhu, Z.; Xiao, P.; Nguyen, H.X.; Lee, I.; Al-Dhahir, N. Joint Beamforming Design for Secure RIS-Assisted IoT Networks. IEEE Internet Things J. 2022, 10, 1628–1641. [Google Scholar] [CrossRef]
- Qi, L.; Lin, W.; Zhang, X.; Dou, W.; Xu, X.; Chen, J. A Correlation Graph Based Approach for Personalized and Compatible Web APIs Recommendation in Mobile APP Development. IEEE Trans. Knowl. Data Eng. 2022. Early Access. [Google Scholar] [CrossRef]
- Li, J.; Peng, H.; Cao, Y.; Dou, Y.; Zhang, H.; Philip, S.Y.; He, L. Higher-Order Attribute-Enhancing Heterogeneous Graph Neural Networks. IEEE Trans. Knowl. Data Eng. 2021, 35, 560–574. [Google Scholar] [CrossRef]
- Huang, J.; Tong, Z.; Feng, Z. Geographical POI Recommendation for Internet of Things: A Federated Learning Approach Using Matrix Factorization. Int. J. Commun. Syst. 2022, e5161. [Google Scholar] [CrossRef]
- Huang, J.; Wang, M.; Wu, Y.; Chen, Y.; Shen, X. Distributed Offloading in Overlapping Areas of Mobile-Edge Computing for Internet of Things. IEEE Internet Things J. 2022, 9, 13837–13847. [Google Scholar] [CrossRef]
- Fu, S.; Gao, J.; Zhao, L. Collaborative Multi-Resource Allocation in Terrestrial-Satellite Network towards 6G. IEEE Trans. Wirel. Commun. 2021, 20, 7057–7071. [Google Scholar] [CrossRef]
- Qu, G.; Wu, H.; Li, R.; Jiao, P. DMRO: A Deep Meta Reinforcement Learning-Based Task Offloading Framework for Edge-Cloud Computing. IEEE Trans. Netw. Serv. Manag. 2021, 18, 3448–3459. [Google Scholar] [CrossRef]
- Wu, H.; Zhang, Z.; Guan, C.; Wolter, K.; Xu, M. Collaborate Edge and Cloud Computing with Distributed Deep Learning for Smart City Internet of Things. IEEE Internet Things J. 2020, 7, 8099–8110. [Google Scholar] [CrossRef]
- Xu, X.; Zhang, X.; Khan, M.; Dou, W.; Xue, S.; Yu, S. A Balanced Virtual Machine Scheduling Method for Energy-Performance Trade-Offs in Cyber-Physical Cloud Systems. Futur. Gener. Comput. Syst. 2020, 105, 789–799. [Google Scholar] [CrossRef]
- Luo, E.; Bhuiyan, M.Z.A.; Wang, G.; Rahman, M.A.; Wu, J.; Atiquzzaman, M. Privacyprotector: Privacy-Protected Patient Data Collection in IoT-Based Healthcare Systems. IEEE Commun. Mag. 2018, 56, 163–168. [Google Scholar] [CrossRef]
- Singh, J.K.; Goel, A.K. Data Security Through Fog Computing Paradigm Using IoT. In Proceedings of the Academia-Industry Consortium for Data Science: AICDS 2020, Wenzhou, China, 19–20 December 2020; Springer: Singapore, 2022; pp. 95–103. [Google Scholar]
- Sabireen, H.; Neelanarayanan, V. A Review on Fog Computing: Architecture, Fog with IoT, Algorithms and Research Challenges. Ict Express 2021, 7, 162–176. [Google Scholar]
- Alam, S.; Siddiqui, S.T.; Ahmad, A.; Ahmad, R.; Shuaib, M. Internet of Things (IoT) Enabling Technologies, Requirements, and Security Challenges. In Lecture Notes in Networks and Systems; Springer: Singapore, 2020; Volume 94, pp. 119–126. [Google Scholar]
- Xu, X.; Dou, W.; Zhang, X.; Chen, J. EnReal: An Energy-Aware Resource Allocation Method for Scientific Workflow Executions in Cloud Environment. IEEE Trans. Cloud Comput. 2015, 4, 166–179. [Google Scholar] [CrossRef]
- Alam, S.; Shuaib, M.; Ahmad, S.; Jayakody, D.N.K.; Muthanna, A.; Bharany, S.; Elgendy, I.A. Blockchain-Based Solutions Supporting Reliable Healthcare for Fog Computing and Internet of Medical Things (IoMT) Integration. Sustainability 2022, 14, 15312. [Google Scholar] [CrossRef]
- Rahmani, M.K.I.; Shuaib, M.; Alam, S.; Siddiqui, S.T.; Ahmad, S.; Bhatia, S.; Mashat, A. Blockchain-Based Trust Management Framework for Cloud Computing-Based Internet of Medical Things (IoMT): A Systematic Review. Comput. Intell. Neurosci. 2022, 2022, 9766844. [Google Scholar] [CrossRef]
- Xie, Y.; Gui, F.-X.; Wang, W.-J.; Chien, C.-F. A Two-Stage Multi-Population Genetic Algorithm with Heuristics for Workflow Scheduling in Heterogeneous Distributed Computing Environments. IEEE Trans. Cloud Comput. 2021. Early Access. [Google Scholar] [CrossRef]
- Shuaib, M.; Samad, A.; Alam, S.; Siddiqui, S.T. Why Adopting Cloud Is Still a Challenge?—A Review on Issues and Challenges for Cloud Migration in Organizations. In Advances in Intelligent Systems and Computing; Springer: Singapore, 2019; Volume 904, pp. 387–399. [Google Scholar]
- Hosseinian-Far, A.; Ramachandran, M.; Slack, C.L. Emerging Trends in Cloud Computing, Big Data, Fog Computing, IoT and Smart Living. In Technology for Smart Futures; Springer: Berlin/Heidelberg, Germany, 2018; pp. 29–40. [Google Scholar]
- Li, C.; Xue, Y.; Wang, J.; Zhang, W.; Li, T. Edge-Oriented Computing Paradigms: A Survey on Architecture Design and System Management. ACM Comput. Surv. 2018, 51, 1–34. [Google Scholar] [CrossRef]
- De Donno, M.; Tange, K.; Dragoni, N. Foundations and Evolution of Modern Computing Paradigms: Cloud, Iot, Edge, and Fog. IEEE Access 2019, 7, 150936–150948. [Google Scholar] [CrossRef]
- Asghar, A.; Abbas, A.; Khattak, H.A.; Khan, S.U. Fog Based Architecture and Load Balancing Methodology for Health Monitoring Systems. IEEE Access 2021, 9, 96189–96200. [Google Scholar] [CrossRef]
- Gupta, H.; Vahid Dastjerdi, A.; Ghosh, S.K.; Buyya, R. IFogSim: A Toolkit for Modeling and Simulation of Resource Management Techniques in the Internet of Things, Edge and Fog Computing Environments. Softw. Pract. Exp. 2017, 47, 1275–1296. [Google Scholar] [CrossRef]
- Iwendi, C.; Khan, S.; Anajemba, J.H.; Bashir, A.K.; Noor, F. Realizing an Efficient IoMT-Assisted Patient Diet Recommendation System through Machine Learning Model. IEEE Access 2020, 8, 28462–28474. [Google Scholar] [CrossRef]
- Liaqat, M.; Naveed, A.; Ali, R.L.; Shuja, J.; Ko, K.-M. Characterizing Dynamic Load Balancing in Cloud Environments Using Virtual Machine Deployment Models. IEEE Access 2019, 7, 145767–145776. [Google Scholar] [CrossRef]
- Lan, X.; Zhang, Y.; Chen, Q.; Cai, L. Energy Efficient Buffer-Aided Transmission Scheme in Wireless Powered Cooperative NOMA Relay Network. IEEE Trans. Commun. 2019, 68, 1432–1447. [Google Scholar] [CrossRef]
- Yuan, H.; Bi, J.; Zhou, M. Geography-Aware Task Scheduling for Profit Maximization in Distributed Green Data Centers. IEEE Trans. Cloud Comput. 2020, 10, 1864–1874. [Google Scholar] [CrossRef]
- Mishra, S.K.; Sahoo, B.; Parida, P.P. Load Balancing in Cloud Computing: A Big Picture. J. King Saud Univ. Inf. Sci. 2020, 32, 149–158. [Google Scholar] [CrossRef]
- Kaur, R.; Verma, S.; Jhanjhi, N.Z.; Talib, M.N. A Comprehensive Survey on Load and Resources Management Techniques in the Homogeneous and Heterogeneous Cloud Environment. Proc. J. Phys. Conf. Ser. 2021, 1979, 12036. [Google Scholar] [CrossRef]
- Rui, X.; Wu, J.; Zhao, J.; Khamesinia, M.S. Load balancing in the internet of things using fuzzy logic and shark smell optimization algorithm. Circ. World 2020, 47, 335–344. [Google Scholar] [CrossRef]
- Wang, W.; Xu, H.; Alazab, M.; Gadekallu, T.R.; Han, Z.; Su, C. Blockchain-Based Reliable and Efficient Certificateless Signature for IIoT Devices. IEEE Trans. Ind. Inform. 2021, 18, 7059–7067. [Google Scholar] [CrossRef]
- Iwendi, C.; Maddikunta, P.K.R.; Gadekallu, T.R.; Lakshmanna, K.; Bashir, A.K.; Piran, M.J. A Metaheuristic Optimization Approach for Energy Efficiency in the IoT Networks. Softw. Pract. Exp. 2021, 51, 2558–2571. [Google Scholar] [CrossRef]
- Lin, Z.; An, K.; Niu, H.; Hu, Y.; Chatzinotas, S.; Zheng, G.; Wang, J. SLNR-Based Secure Energy Efficient Beamforming in Multibeam Satellite Systems. IEEE Trans. Aerosp. Electron. Syst. 2022. Early Access. [Google Scholar] [CrossRef]
- Lin, Z.; Niu, H.; An, K.; Wang, Y.; Zheng, G.; Chatzinotas, S.; Hu, Y. Refracting RIS-Aided Hybrid Satellite-Terrestrial Relay Networks: Joint Beamforming Design and Optimization. IEEE Trans. Aerosp. Electron. Syst. 2022, 58, 3717–3724. [Google Scholar] [CrossRef]
- Xiang, Z.; Zheng, Y.; He, M.; Shi, L.; Wang, D.; Deng, S.; Zheng, Z. Energy-Effective Artificial Internet-of-Things Application Deployment in Edge-Cloud Systems. Peer-Peer Netw. Appl. 2022, 15, 1029–1044. [Google Scholar] [CrossRef]
- Lim, J. Scalable Fog Computing Orchestration for Reliable Cloud Task Scheduling. Appl. Sci. 2021, 11, 10996. [Google Scholar] [CrossRef]
- Costa, B.; Bachiega, J., Jr.; de Carvalho, L.R.; Araujo, A.P.F. Orchestration in Fog Computing: A Comprehensive Survey. ACM Comput. Surv. 2022, 55, 1–34. [Google Scholar] [CrossRef]
- Mittal, M.; Iwendi, C.; Khan, S.; Rehman Javed, A. Analysis of Security and Energy Efficiency for Shortest Route Discovery in Low-energy Adaptive Clustering Hierarchy Protocol Using Levenberg-Marquardt Neural Network and Gated Recurrent Unit for Intrusion Detection System. Trans. Emerg. Telecommun. Technol. 2021, 32, e3997. [Google Scholar] [CrossRef]
- Seyfollahi, A.; Taami, T.; Ghaffari, A. Towards Developing a Machine Learning-Metaheuristic-Enhanced Energy-Sensitive Routing Framework for the Internet of Things. Microprocess. Microsyst. 2023, 96, 104747. [Google Scholar] [CrossRef]


| Author | Techniques/Methodology | Year |
|---|---|---|
| Liaqat et al. [26] | Dynamic load balancing using VM for Cloud | 2019 |
| Lan et al. [27] | The buffer-aided transmission system uses power-splitting relaying which consumes less energy | 2019 |
| Yuan et al. [28] | Geography-Aware Task Scheduling | 2020 |
| Mishra et al. [29] | Review of load balancing approached in cloud computing | 2020 |
| Rui et al. [31] | Shark Smell Optimization algorithm (SSO) | 2020 |
| Wang et al. [32] | Lightweight Certificateless Signature (CLS) protocol | 2021 |
| Kaur et al. [30] | Techniques for managing loads and resources in a diverse and homogenous cloud environment | 2021 |
| Iwendi et al. [33] | Whale Optimization Algorithm (WOA) | 2021 |
| Lim [37] | Fog computing orchestration | 2021 |
| Lin et al. [34] | Reconfigurable Intelligent Surface (RIS) | 2022 |
| Xiang et al. [36] | Directed Acyclic Graphs (DAGs) | 2022 |
| Costa et al. [38] | Systematic literature review of fog orchestration | 2022 |
| No. of Operations | EEFO | DEERA | ELBS | DEBTS | DEELB |
|---|---|---|---|---|---|
| 10 | 26.832 | 22.851 | 17.877 | 13.453 | 10.352 |
| 20 | 27.356 | 23.762 | 18.965 | 13.211 | 11.467 |
| 30 | 27.931 | 22.565 | 19.453 | 14.671 | 11.132 |
| 40 | 29.652 | 24.683 | 20.732 | 15.872 | 11.763 |
| 50 | 28.781 | 25.762 | 19.954 | 16.132 | 12.852 |
| No. of Operations | EEFO | DEERA | ELBS | DEBTS | DEELB |
|---|---|---|---|---|---|
| 10 | 8.872 | 8.165 | 6.256 | 5.111 | 3.675 |
| 20 | 9.165 | 8.675 | 6.326 | 5.675 | 3.436 |
| 30 | 9.321 | 8.132 | 6.123 | 5.732 | 4.723 |
| 40 | 9.956 | 8.756 | 7.145 | 5.832 | 4.263 |
| 50 | 9.652 | 8.653 | 7.656 | 6.132 | 4.732 |
| No. of Operations | EEFO | DEERA | ELBS | DEBTS | DEELB |
|---|---|---|---|---|---|
| 10 | 49.67 | 44.93 | 38.45 | 34.78 | 30.17 |
| 20 | 50.73 | 43.65 | 40.23 | 35.61 | 29.65 |
| 30 | 48.72 | 46.83 | 41.83 | 35.92 | 31.82 |
| 40 | 51.65 | 47.91 | 40.65 | 37.88 | 32.17 |
| 50 | 50.85 | 45.65 | 43.72 | 38.65 | 33.45 |
| No. of Operations | EEFO | DEERA | ELBS | DEBTS | DEELB |
|---|---|---|---|---|---|
| 10 | 1500.97 | 1400.65 | 1200.65 | 1000.82 | 900.32 |
| 20 | 1600.12 | 1400.91 | 1200.83 | 1000.96 | 900.75 |
| 30 | 1600.72 | 1500.15 | 1200.96 | 1100.12 | 910.65 |
| 40 | 1600.85 | 1500.65 | 1300.13 | 1100.65 | 970.12 |
| 50 | 1700.91 | 1500.82 | 1300.65 | 1200.15 | 990.65 |
| No. of Operations | EEFO | DEERA | ELBS | DEBTS | DEELB |
|---|---|---|---|---|---|
| 10 | 850.18 | 935.86 | 1083.36 | 1195.75 | 1373.98 |
| 20 | 826.95 | 976.48 | 1107.48 | 1209.56 | 1392.74 |
| 30 | 850.84 | 952.32 | 1113.65 | 1200.85 | 1380.67 |
| 40 | 806.72 | 1040.57 | 1178.74 | 1284.86 | 1470.73 |
| 50 | 913.87 | 1070.65 | 1152.85 | 1346.29 | 1500.65 |
| No. of Operations | EEFO | DEERA | ELBS | DEBTS | DEELB |
|---|---|---|---|---|---|
| 10 | 80.153 | 82.657 | 84.297 | 85.612 | 88.178 |
| 20 | 80.267 | 82.757 | 84.165 | 85.132 | 88.675 |
| 30 | 80.472 | 83.678 | 85.322 | 86.432 | 88.432 |
| 40 | 81.632 | 83.769 | 85.168 | 86.167 | 90.132 |
| 50 | 81.749 | 84.132 | 85.477 | 87.322 | 91.652 |
| No. of Operations | EEFO | DEERA | ELBS | DEBTS | DEELB |
|---|---|---|---|---|---|
| 10 | 78.34 | 88.32 | 72.32 | 82.76 | 89.97 |
| 20 | 79.02 | 87.74 | 73.24 | 83.18 | 90.32 |
| 30 | 80.34 | 88.53 | 74.65 | 84.37 | 90.75 |
| 40 | 82.76 | 87.32 | 75.64 | 85.29 | 92.76 |
| 50 | 81.27 | 89.29 | 74.21 | 85.31 | 93.65 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shuaib, M.; Bhatia, S.; Alam, S.; Masih, R.K.; Alqahtani, N.; Basheer, S.; Alam, M.S. An Optimized, Dynamic, and Efficient Load-Balancing Framework for Resource Management in the Internet of Things (IoT) Environment. Electronics 2023, 12, 1104. https://doi.org/10.3390/electronics12051104
Shuaib M, Bhatia S, Alam S, Masih RK, Alqahtani N, Basheer S, Alam MS. An Optimized, Dynamic, and Efficient Load-Balancing Framework for Resource Management in the Internet of Things (IoT) Environment. Electronics. 2023; 12(5):1104. https://doi.org/10.3390/electronics12051104
Chicago/Turabian StyleShuaib, Mohammed, Surbhi Bhatia, Shadab Alam, Raj Kumar Masih, Nayef Alqahtani, Shakila Basheer, and Mohammad Shabbir Alam. 2023. "An Optimized, Dynamic, and Efficient Load-Balancing Framework for Resource Management in the Internet of Things (IoT) Environment" Electronics 12, no. 5: 1104. https://doi.org/10.3390/electronics12051104
APA StyleShuaib, M., Bhatia, S., Alam, S., Masih, R. K., Alqahtani, N., Basheer, S., & Alam, M. S. (2023). An Optimized, Dynamic, and Efficient Load-Balancing Framework for Resource Management in the Internet of Things (IoT) Environment. Electronics, 12(5), 1104. https://doi.org/10.3390/electronics12051104








