1. Introduction
Encryption and watermarking are two essential techniques for copyright protection. Copy control, broadcasting, authentication and fingerprinting are some other applications of watermarking. Encryption is a very strong methodology for all kinds of multimedia elements, especially for images and videos. However, encryption provides security during data transfer, but, after decryption, it does not provide any protection. The watermarking method is applied to images or videos to prove ownership. Watermarking is a method to hide secret data from multimedia elements. Secret data might be another image, stamp, logo, or text. The data-hiding scheme is called embedding, while finding out whatthe embedded message is is called extraction. There are two types of watermarks, which are pseudo random number (PRN) and visible logos. The PRN-based watermarking process only detects whether there is a watermark. Watermarking extraction is based on three methods, including non-blind, semi-blind, and blind watermarking. The non-blind watermarking process uses both the cover image and the watermarked image to extract the embedded message. Semi-blind watermarking uses a watermark logo and watermarked image, while blind watermarking uses a secret key only to find the embedded watermark.
Image watermarking is mainly used to prove that an image belongs to someone; that the image in question relates to the sender who sent it. There are also other uses of watermarking, such as advertisement tracking, transaction tracking, and metadata storage [
1]. Image watermarking involves embedding data into an image in a way that it will not be possible to see or remove the watermark from the image without destroying the overall appearance of the image. Although, generally, it is apparent that the image contains a watermark, it must not be seen or extracted without the key and the relevant method. Watermarking methods aim to prove ownership. The embedded watermark must survive common image operations, such as Lossy compression, format change, filtering, cropping, rotation, or resizing. This property is known as the robustness of the method. The algorithm must also be robust against damaging operations, such as rotation, cropping and re-watermarking [
1,
2,
3]. It is also desired for the watermarked image to resemble the original image as much as possible. This property is called the fidelity of the method. Fidelity is measured as the peak signal-to-noise ratio (PSNR) value as given in Equation [
1]. The rounded mean square error (RMSE) is measured between two images as in Equation [
2] where I is the original image and I* is the watermarked image, and i, j are the pixel coordinates. There is always a trade-off between robustness and fidelity. When robustness increases, fidelity decreases.
Another type of watermarking is authentication purpose watermarking. In this type, the aim is to detect changes made to an image and to decide whether the image is the same as the original. Although our work involves proving the watermarking ownership type, it mainly deals with the authentication type of watermarking.
When devising a blind image authentication algorithm it must take into account that the center of the image contains more important data than the edges. Watermark embedding may affect important parts of an image in a negative way. The present study seeks to reduce the effect of watermark embedding on important parts of the image, while making sure that the image does not undergo a malicious change. It is better to determine the genuineness of an image without having to obtain an original copy from a trusted party. In this sense, blind image authentication is a more desirable watermarking method than a non-blind method. A blind authentication and proof of ownership image watermarking algorithm that may resist certain innocent image operations, while detecting malicious alterations to an image, is proposed. The proposed method will make it possible to determine which parts of a received image have been maliciously altered by an attacker.
2. Related Work
Singh et al. [
4] proposed an Arnold-transform-based watermarking method for images. Both the cover image and thewatermark are shuffled using an Arnold cat map, then a second-level decomposition of DWT and SVD are applied to embed the watermark. The experimental results were compared with the five most frequently used watermarking algorithms. The results showed that the proposed algorithm was very strong against filtering, noise and geometric attacks. Cheng et al. [
5] proposed a watermarking method for privacy leakage and response latency in outsourced multimedia elements. In this work, encryption and discrete wavelet transforms were used for information security. Several attacks and methodologies able to find out an embedded watermark, erase or change it were identified. Qi et al. [
6] proposed a generic reversible visible watermarking method using graph Fourier transform, which was visible and could resist several attacks. However, the proposed method is a blind watermarking approach, which is more difficult to apply than other methods, such as non-blind and semi-blind. Singh et al. [
6] proposed a hybrid watermarking algorithm for healthcare. Currently, several types of patient data are used in healthcare, with most being images and videos. When using images, it is important to select the region of interest to embed the watermark so as not to distort patient information. In this work, DWT and SVD transformations were used to embed patient information as a watermark. The approach was tested with several geometric and image-processing attacks, and the results obtained were very strong. Application of the measurement metrics PSNR and SSIM indicated that the proposed algorithm was very promising.
DCT is another frequency domain watermarking type; it is a robust and secure method. In the literature, several studies are reported which use PRN embedding using the mid-coefficient of the DCT. Rupa et al. [
7] proposed a DCT algorithm to embed a logo image into a cover image. DCT is very successful for image decoding, watermarking and image processing. It is a very fast and secure algorithm for information hiding. Elbasi [
8] proposed a third-level decomposition-based wavelet embedding algorithm. The DWT has four bands—the LL band is for low frequencies and other bands are for high frequencies. Embedding a binary watermark in a third-level decomposition of the DWT gives very high PSNR values after geometric and statistical attacks. In addition, the similarity ratio (SR) values are very high after extraction of the watermarks.
Patient data protection is very important for medical imaging, such as ultrasound and magnetic resonance. Hadjer et al. [
9] proposed a dual-image watermarking scheme to embed watermarks and electronic patient records (EPRs) into medical images. The watermark image is encrypted using chaotic logistic map methods to increase robustness and security. PSNR, normalized correlation (NC) and bit error-rate measurement metrics were evaluated for the proposed algorithm; the results showed that dual-image watermarking produces higher robustness and imperceptibility values [
9]. Zhou et al. [
10] proposed a reversible watermarking scheme to protect medical data in colour images. Most of the work in the literature is based on gray-level images which have some limitations in terms of robustness, imperceptibility, and embedded capacity for colour images. In this work, DWT was applied to several medical images, the proposed methodology was found to be more robust and secure than other algorithms described in the literature. Modification of the coefficients in the wavelet was more suitable for information hiding than modification in the spatial domain. Theproposed approach was robust against common and geometric attacks, such as rotation and resizing, and demonstrated high data capacity without any distortion black after attacks.
Kushlev et al. [
11] worked on medical image watermarking. Medical images might include patient, disease, doctor or hospital information which is private information. In this work, wavelet and DCT frequency-based algorithms were used to hide this information in the region of interest to provide robust and secure hiding. The proposed watermarking algorithm was tested against Gaussian noise, salt and pepper noise, and median filter. The PSNR, mean secure error (MSE) and NC evaluation results were very promising. The medical data watermarking method enables the secure collection, storage and sharing of patient data. Wu et al. [
12] proposed a quantum D4 wavelet transform algorithm for images. Combining quantum wavelet transform and a controlled rotating gate produced promising results, especially for attacks. Lena, baboon, boat, man and sailboat images were tested with the proposed algorithm. The PSNR values were higher than 50 dB in all images, indicating greater efficiency than for other frequency and spatial domain algorithms. Simulation results showed that the proposed algorithm was feasible, effective and robust. Mohammmed et al. [
13] worked on Canny-edge-detection-based watermarking, the edges being very critical pixels for hiding information. It is very difficult to identify, change and see the watermark, which is hidden in the edge of the image. The embedding process does not distort the image [
14,
15]. DCT and SVD algorithms were used together in this work. The PSNR values were between 51 dB and 55 dB, which is very strong when compared with embedding with DCT or SVD. The binary image was embedded into the Lena, baboon, airplane, splash and girl images using the proposed algorithm. The proposed work was resistant against histogram equalization and JPEG compression attacks [
16,
17,
18,
19].
There are also variations in authentication types of watermarking. Some fields, such as medicine or military, might require exact authentication. In exact authentication, even a bit change in the watermarked image causes the authentication to fail. Usually an image signature or a hash of the image is computed from some part of the image and stored in another part of the image. As is known, even a bit value change in the image will yield a completely different hash value to the embedded hash value. Exact authentication is also known as fragile authentication—there are many studies concerning fragile types of watermarking in the literature. One of the first studies of authentication-type image watermarking was carried out by Yeung et al. [
20]. In this study, gray-level values [0…255] were mapped to binary values 0, 1 and this mapping was the key for watermark extraction. The binary watermark was inserted into the host image where the gray-level value was changed with the nearest value having the same mapping to the desired watermark bit value (0 or 1), or remained the same if the current gray-level value mapped to the desired watermark bit. Min et al.’s work [
21] used a similar approach in which they mapped DCT domain values to binary values 0,1 instead of to pixel gray-level values. Subsequent to Yeung and Mintzer’s work, several articles were published which showed that mapping of gray-level values can be attacked easily [
22,
23]. Wu and Liu’s work [
21] also has the same kind of weakness. Rao and Kumari in [
24] studied the uses of watermarking in authenticating medical images and ensuring their security.
Generally, the least significant bits are used for authentication-type watermarking. Lin et al. in [
25] divided the image into non-overlapping 4 × 4 blocks and further divided each 4 × 4 block into 2 × 2 sub-blocks, firstly setting the least significant two bits of pixels of the block to zero, calculating the parity and authentication bits using the difference between the mean intensity levels of the sub-blocks. Using a mapping algorithm, the authors made pairs of 4 × 4 blocks, and a 6-bit length mean intensity value of one block was inserted into the least significant bits (LSBs) of the corresponding block. Although their study succeeded in detecting and localizing changes and image restoration to some extent, the method constitutes exact authentication and is sensitive to innocent changes, such as Lossy compression. Chamlawi et al. in [
25] proposed a semi-fragile watermarking method in which two watermarks were embedded in a host image, one binary image watermark being embedded in the LL3 band of the third level DWT of the host image, the other watermark calculated as an image digest by taking the DCT of the DWT LL1 band and embedding the image digest into the LH2 and HL2 DWT bands. The first watermark was used for authentication and the second image digest watermark was used for image restoration and tamper localization. The authors claimed that their method ensured authentication, recovery of the image and localization of tampered areas.
Liu et al. in [
26] took a colour image into YCbCr colour space, then the DWT LL1 of the Y channel was divided into 8 × 8 blocks; each block was quantized by a luminance quantization table and the quantized LL1 values replaced the HH1 band of the Y channel. After taking inverse DWT, a robust watermarked image was obtained, which was then taken to the RGB colour space. After that, the red, green and blue channels were watermarked by a fragile watermark. The fragile watermark was inserted into the pixel domain. A sequence of ones and zeros represented the watermark, which was converted to base 10 digits by a 3n-base formula containing a parameter
n. Each obtained digit was watermarked as a bit sequence to the LSBs of n pixel values of the corresponding colour channel. In their paper, Pillai and Theagarajan claim to have devised a method that embeds two watermarks into the host image, one for authentication, the other for restoration [
27]. The authentication watermark was calculated from the DWT LL1 band of the host image. The LL1 band was divided into blocks, the blocks being grouped into two groups, namely A and B. The blocks were paired as one block from group A, and one block from group B. For each pair of blocks, the DCT of the blocks was taken and compared with the corresponding DCT value of the paired block; a value of 1 or 0 was calculated according to a ‘<’ comparison. The majority bits of the comparison bit sequences were combined to form the authentication watermark. The authentication watermark was embedded into the HL2 and LH2 bands of the host image’s DWT HL1 band. The HL2 and LH2 values were divided by or multiplied by α, depending on the bit value to be embedded. A recovery watermark was obtained by quantizing the LL3 values of the host image, which were then watermarked to the HL1 band’s five LSBs. Although a recovery watermark was embedded, the recovery process was not reported in the experiments.
It is easy to insert a similar watermarked block or block pairs from a known authenticated image into another image for forgery purposes [
22]. Therefore, in any authentication type of watermarking, if the inserted watermark does not depend on the host image itself, then it is vulnerable to counterfeiting attacks. If the method is block-wise, the watermark must be calculated from one of the block pair and inserted into the other one in the pair. Block-pairing must depend on a key so that it cannot be predicted. Boujerfaoui et al. [
28] proposed a convolutional-neural-network-based watermarking algorithm resistant against print-cam attacks, which are very strong attacks and introduce several distortions during picture capture. The proposed approach was compared with Fourier-transformation-based watermarking. The results obtained were robust, secure and of high quality. Cai et al. [
29] proposed a Chinese cryptographic algorithm for copyright protection. Nowadays, it is very easy to collect, share, distort, and change images and videos using information technology. It is a concern for everyone because of the security and copyright implications. The Chinese cryptographic algorithm uses SM2 and SM3, which are hash functions for random password operation and generation. Copyright information is embedded into the image using this encryption method. It is low cost and low risk compared with other frequency-based algorithms. Campos et al. [
30] proposed a block-based algorithm for tamper detection. Lifting wavelet transformation and check sum hashing algorithms are used together. The embedded pixels are selected from the least significant bits in the cover image. Several evaluation methods were used in experiments undertaken, such as the false positive, false negative and tamper-detection rates. The proposed algorithm was found to be very strong against copy paste, copy move, averaging, adding noise and image manipulations.
The health sector uses electronic data frequently. Patient data can be collected, stored and shared with others using information technology. There are several medical-imaging technologies available in all hospitals. Patient data can be kept secret using watermarking and encryption algorithms for privacy purposes. Singh et al. [
31] discussed several spatial domain, frequency domain and cryptographic algorithms to compare their performance in both embedding and extraction. There are some limitations to using watermarking for medical images. For example, if the embedding process is applied to some of the critical parts of the image content, it might affect the doctor’s decision. Discrete cosine transformation is one of the frequency-based embedding methods in image watermarking. Especially if the watermark is a pseudo-random number, the scaling factor is an important coefficient to provide balance between invisibility and robustness. Ernawan et al. [
32] proposed a flexible scaling-factor-based DCT watermarking algorithm in blocks. In this work, selected coefficients were compared against the average coefficients using flexible scaling. The PSNR and SSIM values were very high compared to the DCT algorithm. The watermarked image was resistant against several filtering, adding noise and compression attacks.
Sahu et al. [
33] proposed a reversible fragile watermarking methodology for tamper detection. In this method, two secrets are embedded into the cover image for a dual watermarking scheme. Experiments showed that the proposed method was more robust and had high capacity and transparency. The proposed methodology finds tampered regions and relocates efficiently. Zhang et al. [
34] proposed an M-sequence and sliding window-based watermarking method for audio. This method was found to be robust and secure against large-scale cropping attacks. In this methodology, audio is converted into DWT, DCT, graph-based transform (GBT), and SVD. The secret data is applied to cover audio.
3. Proposed Method
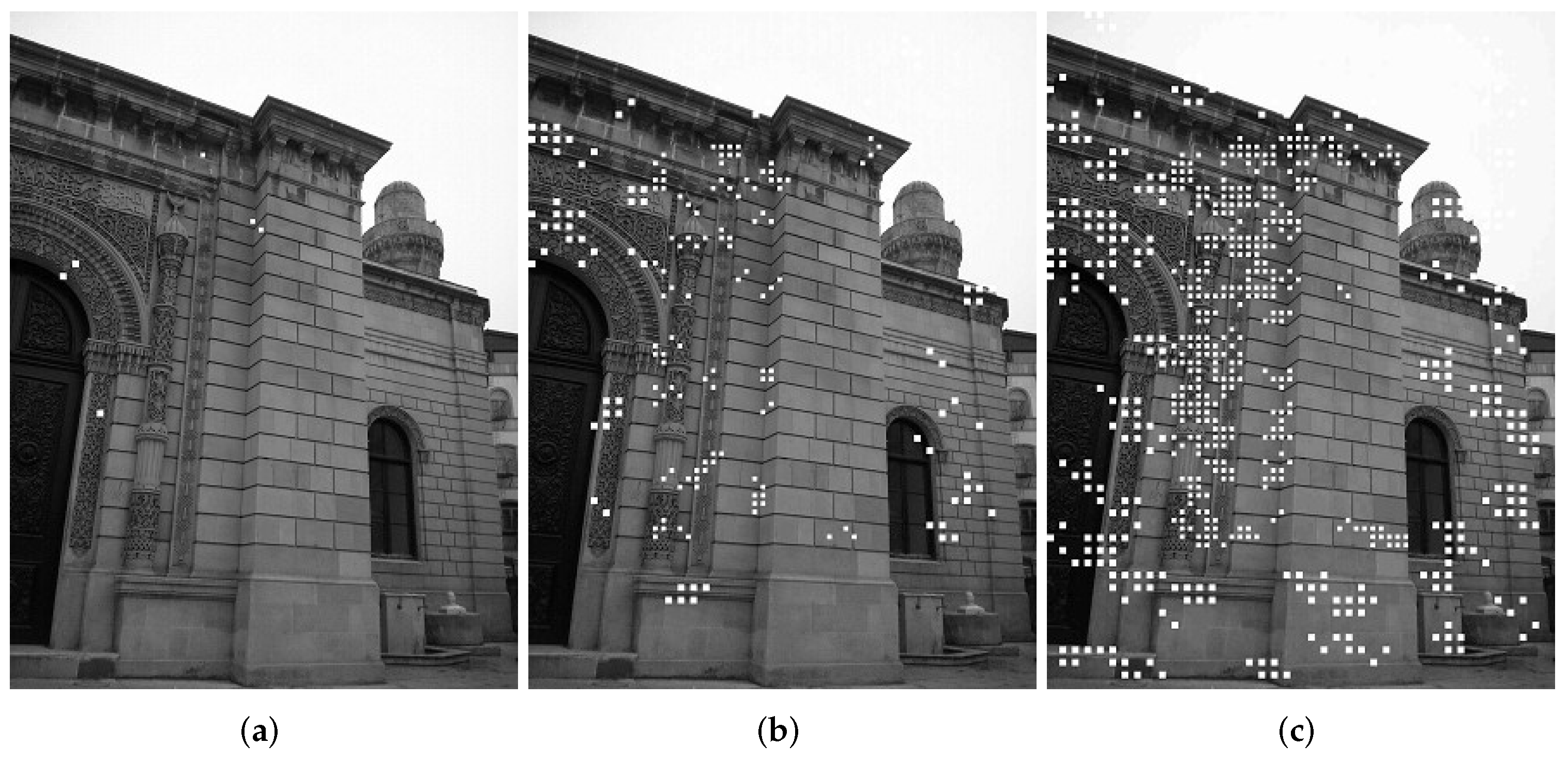
In the proposed method, the image is considered as two parts: the center and probably more important part, and the image’s exterior part, as seen in
Figure 1. In photographs, the important thing, person or the main object is usually centered or around the center. The main idea in this study is to watermark the center of the image with a robust watermark to prove ownership, with a watermark strength that does not degrade the fidelity of the image to a marked extent. After that, the center part and outer part are divided into blocks and the center blocks are paired with the outer blocks of the image, watermarking the image digest of the inner block to the outer block for authentication purpose.
The center part is watermarked with a robust watermark to prevent someone who knows the algorithm from cropping only the center part and using it without permission. The center part is watermarked in the DWT domain with the method proposed in [
20]. The DWT of the center part and watermarking are shown in Equations (
3) and (
4). The watermark is embedded into the low frequencies, which are located in the LL1 band. This watermark does not degrade fidelity very much. The watermarked images after the center part watermarking have a PSNR value of 57, which is a very high fidelity value. In this study, the main concern is the authentication part. Because of this, no experimental results for the robust watermark are provided. For those interested in the method and success of robust ownership watermarking that is used for the inner parts, please see [
20].
As a next step, the bands of the inner blocks are represented in binary form by making the values 1 that are greater than the threshold value and assigning a value 0 in other cases. The threshold value is decided so as to make the number of ones and zeros almost equal to each other in the whole inner part. This is done to embed the watermark in a more balanced way to decrease the negative effect on fidelity.
In
Figure 1, the center part is contoured with thick black lines. The center part is divided into blocks that are of reduced area compared to the outer block sizes. The algorithm depends on a prime number
. The prime number
will be given to the authenticator program that is used on the other side. After making pairs of blocks, one from the inner part and one from the outer part, a binary image is calculated from the inner block and that binary image block is embedded in the corresponding outer block. The outer blocks are greater in size compared to the inner blocks. This offers greater precision on the inner part to decide which block(s) are changed. This is reasonable because, in most of the images, the important person or thing is generally placed in the center part of the image. Moreover, the watermark storing capacity of the outer block increases as the block size increases. In
Figure 2, the difference in block size is shown more clearly.
3.1. The Embedding Algorithm
The pseudocode for the embedding algorithm is as follows:
In step 1.a.iii, since the number of blocks in the inner part and the outer part may differ, it is considered sufficient to pair at least 90% of the inner blocks with the outer blocks. Since pairing is performed using a secret key, the risk is not high for not pairing at most 10% of the inner blocks. Since the inner blocks are previously watermarked with a robust watermark, this presents no problem for the inner blocks. There might be a risk that, if someone knows the algorithm, they may try to find outer blocks that are not paired with an inner block and try to change the block contents. Firstly, since the pairing depends on a secret key, it is not possible to determine non-paired blocks without the key. Secondly, the non-paired outer blocks are not contiguously located—they are scattered along the exterior part of the image. Changing a 24 × 24 block may not yield a desired malicious change in the image.
In step 4,
takes into consideration the block size
of the outer blocks.
is the total number of pixel values of an outer block. In 6.b, while converting the LL1 value to a binary value, a threshold value is calculated to make the number of bits value 1 equal to the number of 0’s in the whole of the inner blocks. As shown in step 6.c, the DCT of the outer block is obtained. After that, a zigzag scan of the DCT values is obtained.
is the number of values that are not used from the beginning and from the end of the zigzag values. By doing this, we are not changing the DC component and the most precious low-frequency values as well as the high-frequency values. We try to preserve fidelity by not using high-rank, low-frequency components. By doing this, we try to make our watermarking method robust to Lossy compression, which destroys high-frequency components the most. In
Figure 3, it is seen how an image is considered as the inner and outer parts and how the inner and outer parts are divided into different block sizes.
3.2. The Authentication Algorithm
The pseudocode for the authentication algorithm is as follows:
- 1.
The image is divided into parts: inner part, outer part with the same principles as in embedding
- 2.
Make pairs , from inner part, from outer part using the given key
- 3.
Load the given
- 4.
- 5.
For each block from inner part
- (a)
Find out DWT
- (b)
Obtain binary image from band of DWT
- (c)
, where is corresponding block from outer part
- (d)
- (e)
, excluding first and last values
- (f)
- (g)
While
- i.
take values of length from
- ii.
- iii.
- iv.
if
else
- v.
Put the bit value in proper place in the order it is embedded
- vi.
- (h)
- (i)
*
- (j)
If
Mark the inner and outer block as changed
- 6.
Embed robust watermark into center blocks for the purpose of proving ownership as in [
20]
Both the embedding and extraction algorithms should be robust and secure in the watermarking process. The authentication process is important to find out embedded secret information in the cover images for copyright protection. In the proposed methodology, the cover image is divided into inner and outer blocks. Each block is transformed into the discrete wavelet transformation (DWT). The DWT gives low frequencies (LL band) and high frequencies (HL, LH, and HH bands). The LL bands were transformed into the DCT using zigzag order. If the correlation of the inner block is greater than the correlation of the outer block, then the pixel value is assigned to 1; otherwise 0. In the extraction process, the similarity ratio (SR) is used for quality measurement. For binary watermarking, an SR value of 1 demonstrates the best quality of the extracted watermark.
3.3. The Scrambling Algorithm
In many of the authentication-type watermarking methods, the image is divided into blocks and the blocks are paired as (B1, B2). An image digest, a binary image or image features are calculated from the B1 block and embedded in the B2 block. It is important to make the secret pairing of blocks because, if someone knows or predicts the block sizes and pairs, they could easily replace the block pair with a pair from an already authenticated image. In [
25], it is mentioned that torus automorphisms can be used for that purpose. A torus automorphism is a dynamic stately system that has a beginning state and change state at t intervals.
A two-dimensional torus automorphism can be defined by
,
,
The system is chaotic and repeats itself at every time step
R, that is
. Voyatzis and Pitas [
35] proposed a special type of matrix A for Equation (
6), where A can be formed from one value
k.
In our study, the one-dimensional mapping method mentioned in [
25] and given in Equation [
8] is used.
where
are the block numbers at t and t+1, k is a prime number and the secret key, N is the number of blocks. The set of inner blocks is S1 and the number of elements in S1 is N1, whereas the set of outer blocks is S2 and the number of elements is N2. The scrambling algorithm maps the blocks in S1 to blocks in S2 and it is a one-to-one mapping.
Although mapping between inner and outer blocks uses a scrambling algorithm and a secret key, it is not the only security prevention. The block sizes of the inner blocks and the outer blocks are also determined on the run which makes the attacks more difficult. The attacker will not know the blocking structure in the image. The number of excluded values in the DCT transform is also not known by the attacker. A little weakness in the pairing scrambling algorithm may be easily compensated for by the mentioned unknown parts of the algorithm.
4. Experiments and Results
The original image is as shown in
Figure 4a. The binary logo watermark image watermarked into the inner part is shown in
Figure 4b. In
Figure 4c, a watermarked image with a proving ownership and authentication watermark is shown. The PSNR of the image is 40.577. Although the PSNR value may be seen as a lower fidelity value, the sacrifice is with semi-fragility and it pays off. The success of the algorithm for different types of attacks is given in
Table 1. The algorithm authenticates an image that is Lossy-JPEG-compressed with a quality factor of 75%; the authenticated image is seen in
Figure 5a. It shows only six blocks as changed which are not contiguous and can be considered an innocent type of operation. The algorithm does not authenticate 50% quality and 25% quality JPEG compressed images, as seen in
Figure 5b,c. The algorithm also authenticates images with intensity adjustment and histogram equalization, as seen in
Figure 6b,c. The most common objective evaluation tool, the mean square error (MSE), is very unreliable, resulting in poor correlation with the human visual system (HVS). The peak signal-to-noise ratio (PSNR) is one of the image-quality measurement metrics. It represents a ratio between the highest value of a signal and the power of distorted noise.
In
Figure 7a, the watermarked image has been tampered with as a non-existent ornament is placed on the mosque on the figure. In
Figure 7b, it can be seen that the changed blocks are successfully signed as “changed” by the algorithm without any false negatives. The authenticator program needs the PSNR and the scrambling key for authentication. In
Figure 7c, the watermarked image with no attack is attempted to be authenticated with the wrong key and almost all the blocks are signed as tampered with by the algorithm. If the wrong key is given to the authenticator, or the key is not known, the image cannot be authenticated.
The algorithm does not authenticate watermarked images with scale attacks, which can be seen as an innocent type of operation. Moreover, the number of blocks marked as tampered with is largely as predicted for a watermarked image filtered by a 3 × 3 averaging filter, as seen in
Figure 8a. The Gaussian filtered image is marked tampered with for a very few blocks, as seen in
Figure 8b.
Figure 6 demonstrates watermarked images after re-scale authentication, intensity adjustment and histogram equalization attacks.
There are several measurement metrics in the watermarking process. In semi-fragile watermarking, we use the similarity ratio, which measures the quality of the extracted secret information.
Table 2 shows the SR values for the watermarked image and the extracted watermark.
Table 3 shows acomparison with four of the previous approaches that resemble our study. When previous works are examined, some of the methods divide the host image into blocks and authenticate the blocks rather than the whole image. Most of the block-wise methods use a secret key to pair the blocks and calculate some value from one block and embed it into the corresponding pair. When compared with semi-fragile works [
36], a watermarked image compressed with 70% quality is authenticated JPEG, and does not mention another type of image operation that the authentication watermark survives. Our method authenticates an image that is subjected to 75% JPEG compression, histogram equalization and gamma correction. Pillai and Theagarajan’s [
27] authentication algorithm can resist 90% JPEG compression at most. In these respects, our algorithm performs better. The algorithm may detect some changes in some block pairs in innocent operations of a 3 × 3 average filter, scale-rescale operation, JPEG 50% compressions, and JPEG 25% compressions. Thus, selective fragility is not successful for this kind of innocent operation.
With respect to tamper localization, our method can localize tamper detection in 4 × 4 block precision, which can be considered as very sensitive. The fidelity metric PSNR is around 40 for watermarked images with our method, which is an acceptable fidelity value and only worse than one of the previous methods. Our method only needs the scrambling key, which is a prime number, and the PSNR, which is not a long sequence. For the security of the watermarking method, these numbers must be passed to the authenticator. When one looks at the previous methods, all the previous methods must pass some secret value to the authenticator.
The proposed algorithm and Chamlavi [
36] are semi-fragile embedding methodologies. Both algorithms need a watermark and secret key for the extraction process. The proposed algorithm resists JPEG 75 compression, while the Chamlavi algorithm resists JPEG 70 compression. The proposed algorithm has a better PSNR value than the other algorithms, which shows the high quality of the watermarked image.
5. Conclusions and Future Work
In this study, we devised a new method for authentication-type watermarking that also includes copyright protection. The images are considered as two main parts: an inner part and an outer part. The inner part is first watermarked with a robust watermark for copyright protection. After that, the inner part is divided into blocks, DWT is applied for each block separately and binary image digests of the LL1 bands are formed for embedding into the outer blocks. The outer parts are also divided into larger blocks, and each inner block is paired with one outer block using a scrambling algorithm based on a key value. DCT is applied to the outer blocks and binary image digests of the inner blocks are embedded into the DCT values of the corresponding outer blocks. During this embedding, low-frequency and high-frequency DCT values of the outer blocks, including the DC component, are not changed to preserve the fidelity and to authenticate low-pass image operations. This process authenticates images with JPEG compression of up to a 75% quality level, subjected to histogram equalization, intensity adjustment and gamma correction, which can be considered as innocent types of image operations.
The study makes a contribution to the literature on image watermarking by considering the image as inner and outer parts and dividing the inner part into smaller blocks than the outer parts. By doing so, the watermark-holding capacity of the outer blocks is enlarged, the fidelity of the inner parts is improved, and the authentication watermark’s robustness to JPEG compression, intensity adjustment, histogram equalization and gamma correction operations is increased. Tamper localization is also improved for the inner parts by using smaller block sizes. Since the method embeds a watermark obtained from the image itself, and block pairing is performed with a secret key, the method is secure against collage attacks. The proposed algorithm is blind, robust, and secure and has high data capacity, being stronger than other algorithms described in the literature. In the future, we plan to further enhance the algorithms to obtain a more robust, secure, and resistant embedding process for both images and videos. In video watermarking, several additional issues need to be resolved, such as temporal attacks, including image dropping, swapping, and averaging. In addition, the embedding processes should be resistant to any type of video compression.