MVPN: A Defense Architecture against VPN Traffic Hijacking Based on MTD
Abstract
1. Introduction
2. Related Work
3. Materials and Methods
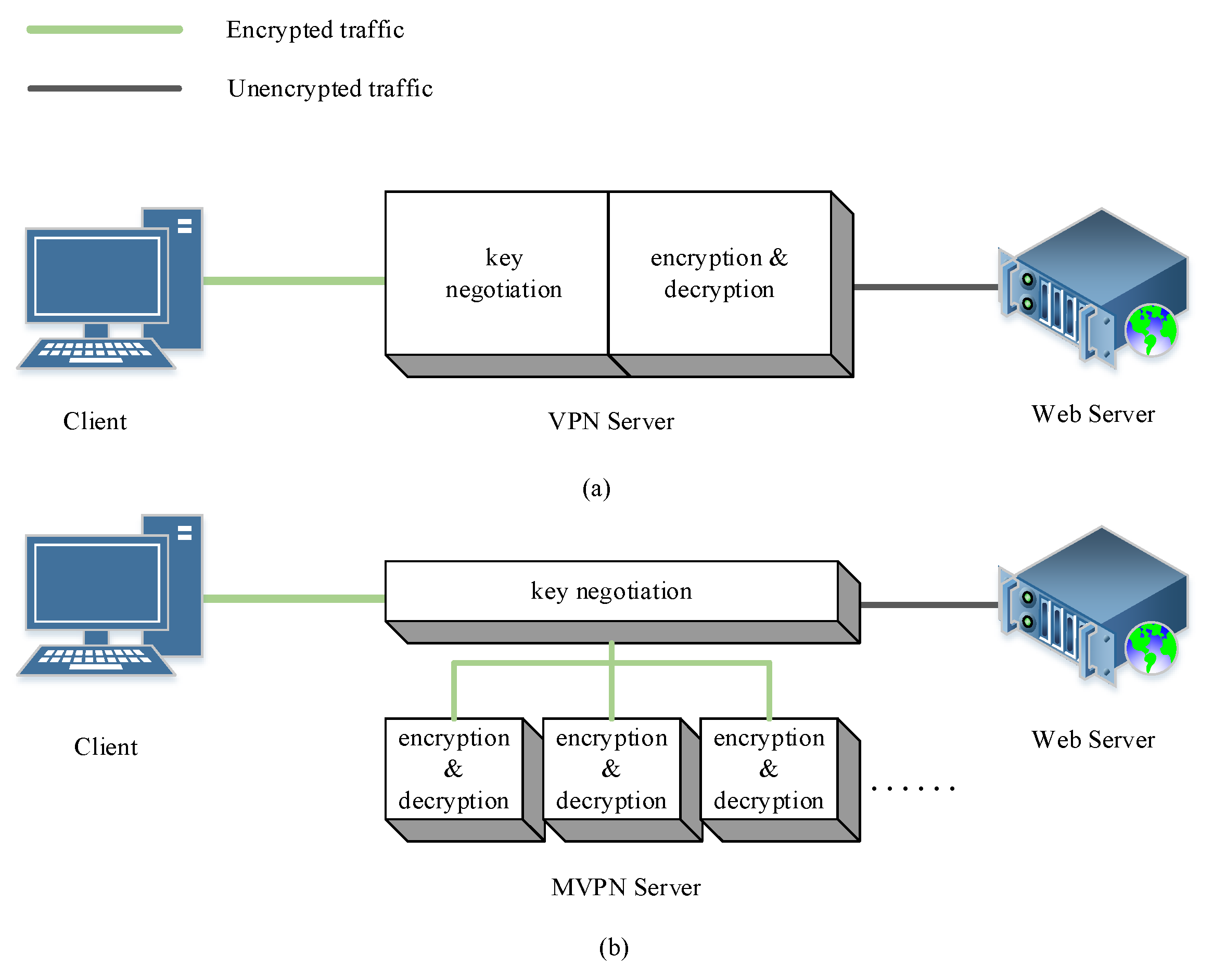
3.1. MVPN Architecture
- (1)
- The architecture can defend against blind in/on-path attacks effectively and, depending on the attacker’s action, dynamically changes the state over time, thereby increasing the attacker’s attack difficulty.
- (2)
- The existing VPN protocol should not be changed. MVPN can offer the same service as traditional VPNs, and it is easy to deploy.
- (3)
- Transparent to clients. MVPN’s dynamic architecture is transparent to VPN clients, and clients do not need to install redundant plugins or change communication protocols.
- (4)
- Minimizing the network delay. Due to its dynamic and redundant properties, the MVPN architecture will inevitably cause disruption in the transmission of the network and affect the transmission speed of the network.
- (5)
- Keep the stability of network transmission. When the state changes dynamically, normal network communication cannot be affected.
- (1)
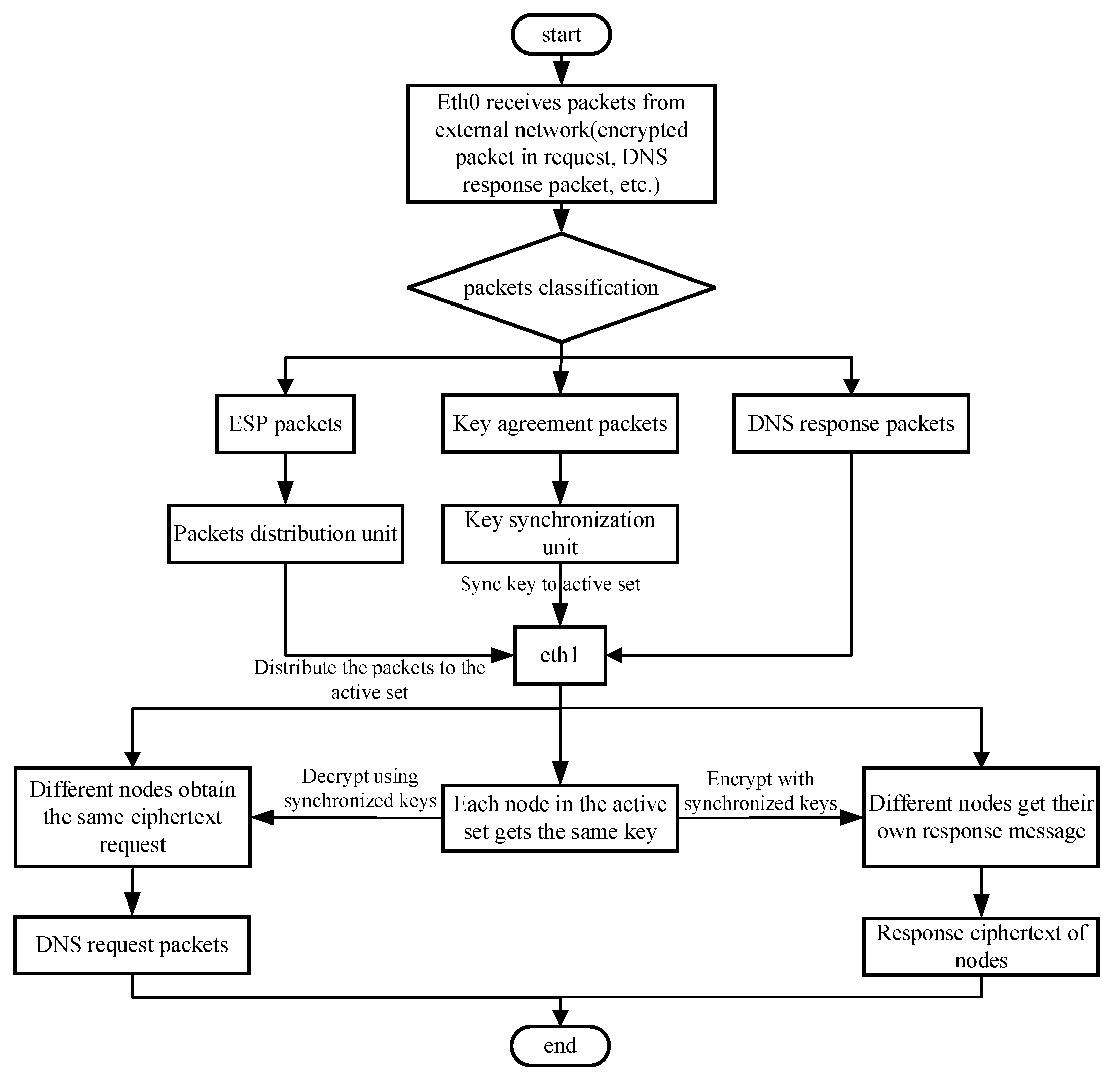
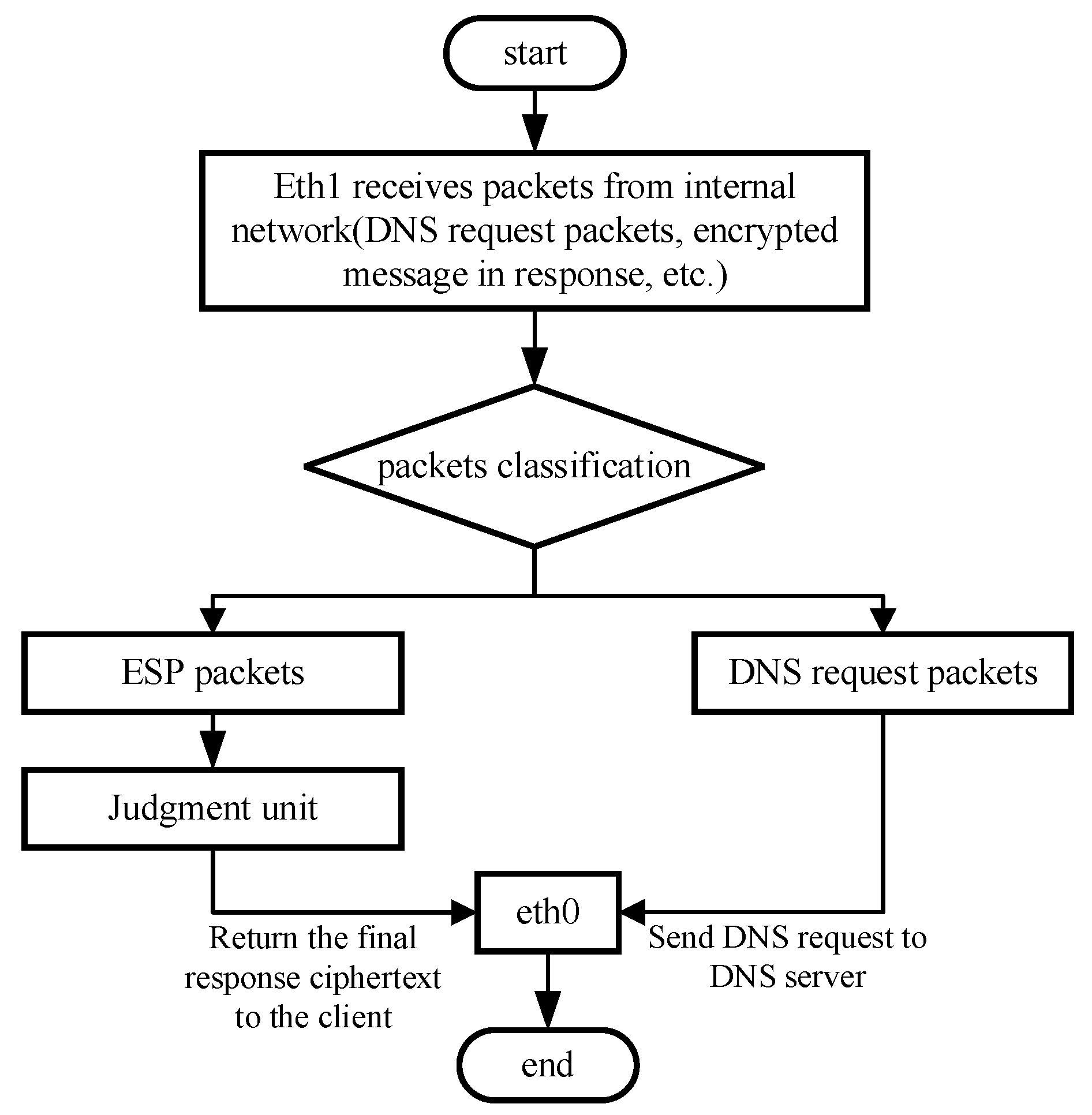
- Packet receiving and sending unit. This unit is responsible for receiving and sending packets from the internal and external networks.
- (2)
- Packets classification unit. This unit is responsible for classifying and forwarding all traffic received by the interfaces bound to the DPDK. According to the transmission direction (inbound or outbound) and the protocol type of the packets, the packet is sent to the matching functional unit.
- (3)
- Key agreement unit. This unit is responsible for key agreements with VPN clients and transferring the negotiated key to the key synchronization unit without changing the original VPN negotiation protocol and process.
- (4)
- Key synchronization unit. This unit is responsible for transferring the current key to the encryption-decryption node in the active set. The key can be transmitted based on TLS, SSL, or other encryption protocols to avoid key disclosure.
- (5)
- Packets distribution unit. This unit is responsible for copying and forwarding encrypted data packets and TCP packets. Taking IPsec protocol as an example, ESP is a major protocol in IPsec, which provides confidentiality and integrity through encryption and verification. The unit distributes the ESP packets to the encryption-decryption nodes in the active for synchronization. Since TCP needs to maintain the connection state, it also needs to distribute it to the nodes for synchronization.
- (6)
- Packet forwarding unit. This unit is responsible for forwarding UDP packets directly to the encryption-decryption node or the public network according to the transmission direction of the packets.
- (7)
- Judgment unit. This unit is responsible for judging whether the MVPN system is suffering from blind in/on-path attacks by comparing the encrypted packets sent to the client from the active set. The decision is based on the following assumption: it is difficult for attackers to guess the temporary ports used by different nodes at the same time. Therefore, the same reply from nodes can be considered the correct and safe reply. If an inconsistent reply is found, the judgment unit will send the inconsistent packet information (source IP, source port, etc.) to the NAT status update unit.
- (8)
- NAT status update unit. This unit judges which encryption-decryption node is being attacked according to the inconsistent information determined by the judgment unit and sends the command to update the NAT status to the suspicious node.
- (9)
- Encryption-decryption node pool. This unit consists of multiple encryption-decryption nodes. Each node maintains the same VPN protocol. This unit is mainly responsible for decrypting the packets forwarded by the VPN proxy and returning the encrypted packets to the VPN proxy.
- (10)
- Management layer. The system administrator can change the configuration file of the MVPN to register new VPN users, change the number of DPDK binding cores and the database access password, or perform other management operations.
3.2. Workflow
4. MVPN Key Technology Design
4.1. Multichannel Packet Classification Mechanism
4.2. Consistency Judgment Algorithm
| Algorithm 1: Consistency judgment algorithm. |
| Input: encryption packets from different encryption-decryption nodes. Output: consistently encrypt packets or adjudicate inconsistent messages.
|
4.3. NAT Status Update Strategy
- (1)
- Temporal triggering. Under the no abnormal judgment condition, the NAT state is changed regularly to increase the dynamics of the MVPN system. For example, the MVPN can periodically modify the target DNS server through DNAT to confuse attackers.
- (2)
- Event triggering. In the event of an anomalous judgment, the NAT state update unit confirms the anomalous node according to the anomalous information. Meanwhile, this unit sends the command to the node to update the NAT state. Depending on the command, the node removes the conntrack entries that may be exploited by attackers and set a new DNS request address by default.
4.4. Availability Assurance Strategy
- (1)
- Only when the encryption-decryption functions are normal can the node return the encrypted packets to the judgment unit. Therefore, the judgment unit maintains the status information of the nodes by counting the encrypted packets sent by the node. When the cumulative encrypted packet responses returned by a node exceed the threshold value, the node is considered normal.
- (2)
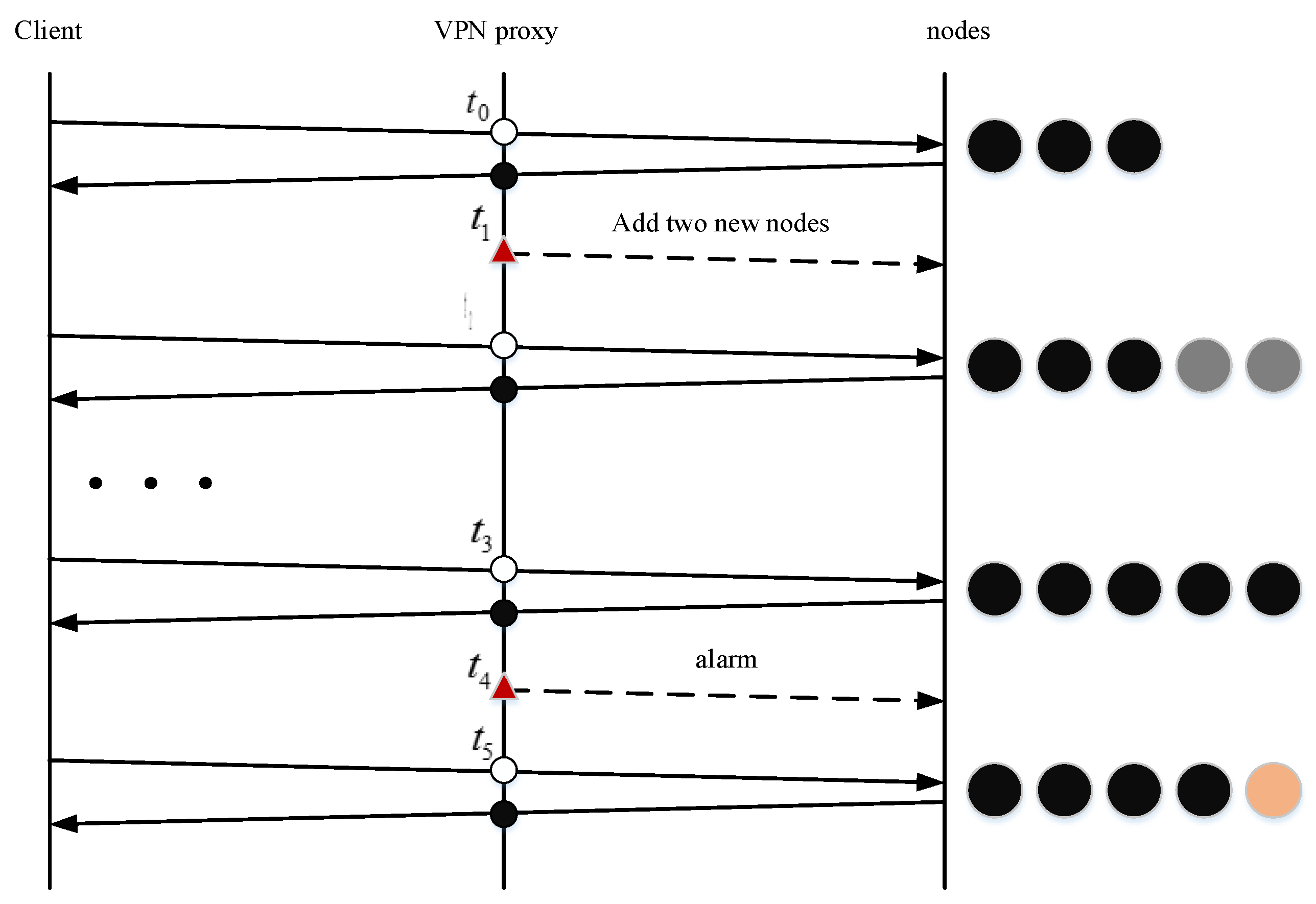
- The node in a normal state participates in the judgment. The nodes identified as normal by the judgment unit participate in the decision, while the nodes identified as abnormal do not participate in the decision, but they are still counted. For example, for the two new nodes added at the time, since the accumulated encrypted messages of the two new nodes have not exceeded the threshold, the status is not normal, and the returned responses do not participate in the judgment. That is, the judgment unit still uses the responses returned by the three nodes in normal status to determine the request in time. When the encrypted packet count of the newly added node exceeds the threshold value, it is set as the normal state at the time, and then all five normal nodes participate in the judgment, as shown in Figure 6.
- (3)
- Nodes judged as abnormal are removed from the active set. At the time, the judgment unit determines the abnormal node, sets the node status information as abnormal, and resets the counter. At the same time, the response returned by this node will not participate in the next decision until the node count reaches the threshold again.
5. Theoretical Analysis and Simulation
5.1. Theoretical Analysis
5.2. Simulation
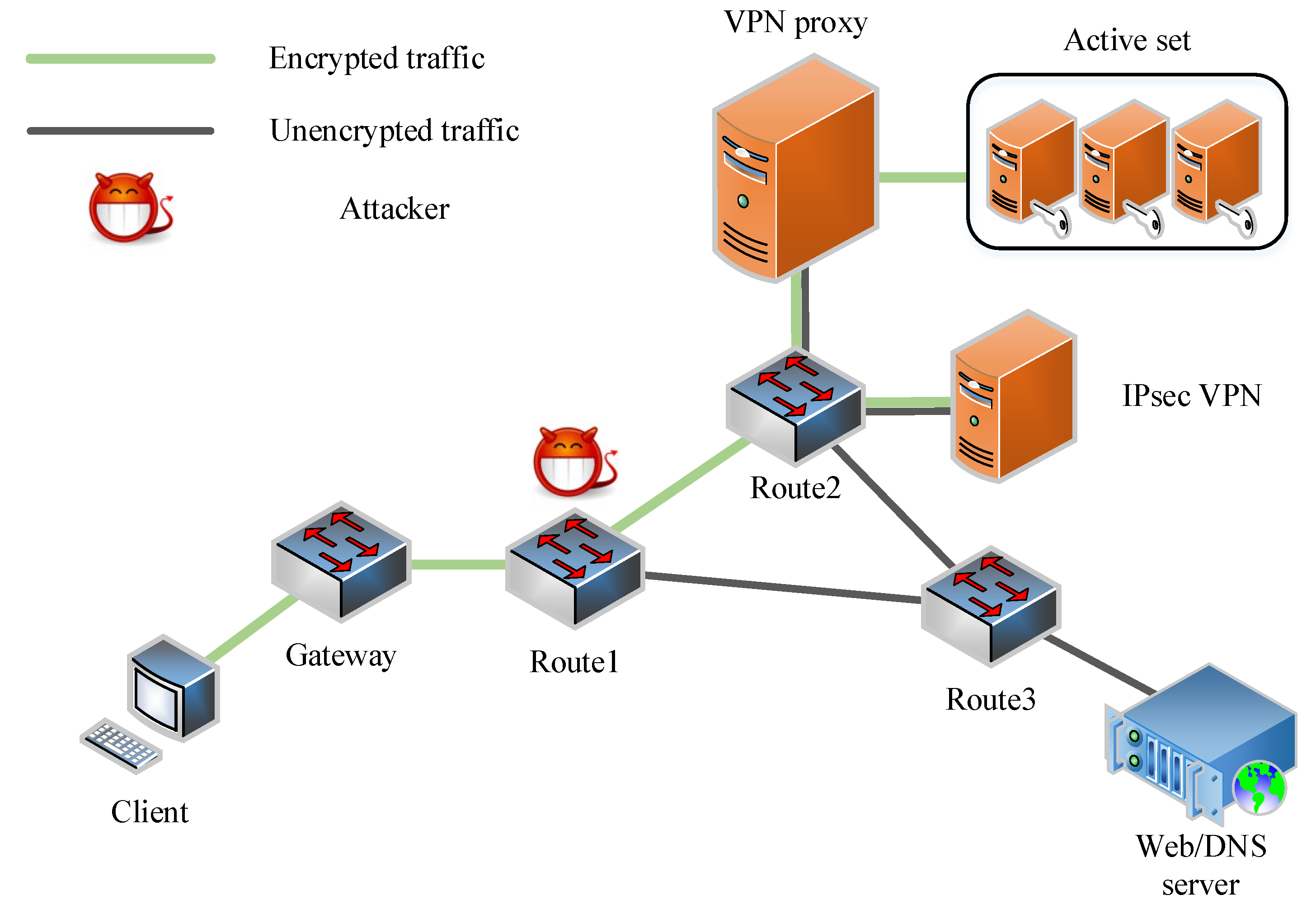
5.2.1. Verification of Model Authenticity
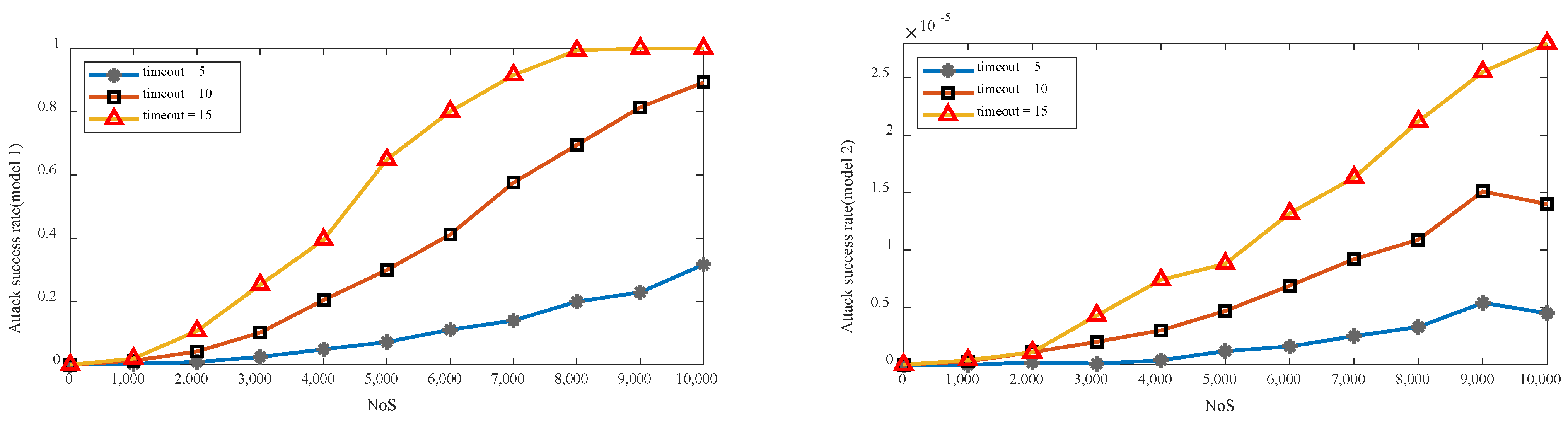
5.2.2. Attack Success Rate under MVPN Model
5.2.3. Attack Success Rate under White Box Condition
- (1)
- The attacker knows which nodes selected by the VPN proxy are active sets and hijacks the nodes in the active set.
- (2)
- When the attack on a node succeeds, the attacker can instantly perceive and immediately turn to the next node.
6. Experiments and Evaluation in the Real Environment
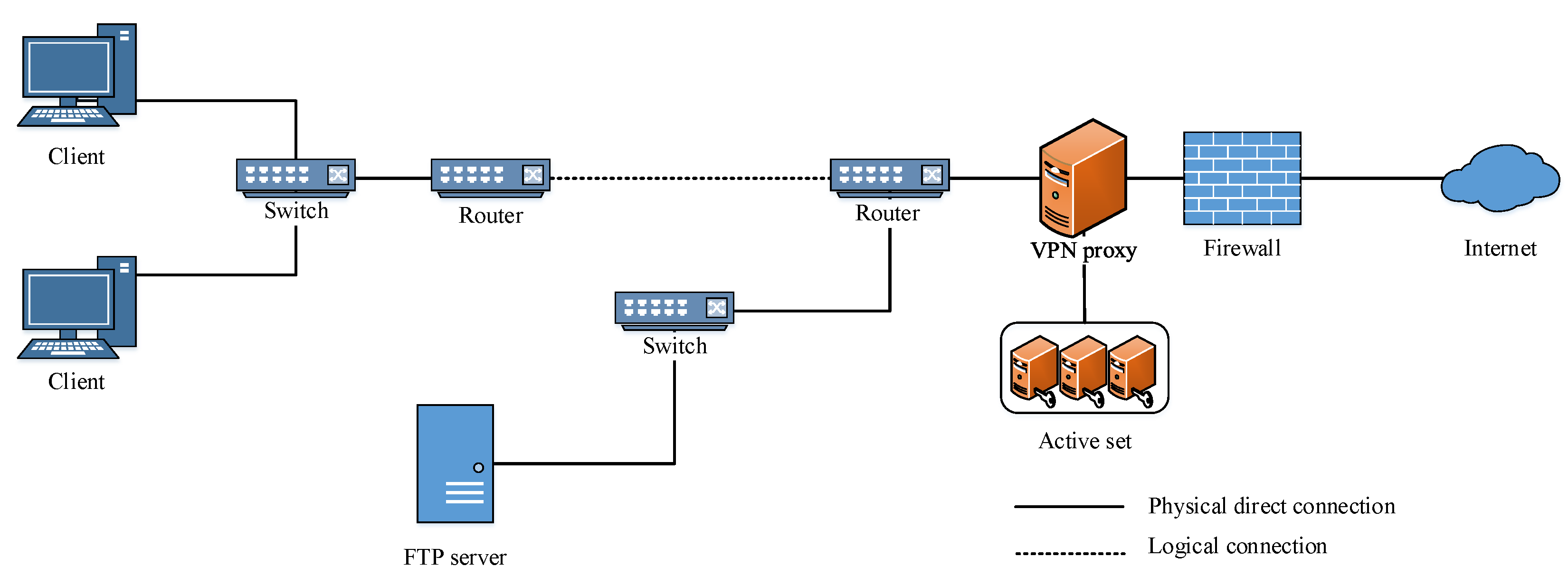
6.1. Experimental Environment Settings
- Whether the MVPN defense against the blind in/on-path attacks is effective;
- Whether the MVPN system can reduce the success rate of blind in/on-path DNS hijacking attacks to a certain extent in the real environment;
- Evaluate the active defense capability of the MVPN system;
- Test delay and performance of the MVPN system.
6.2. Attack and Defense Test (Experiment II)
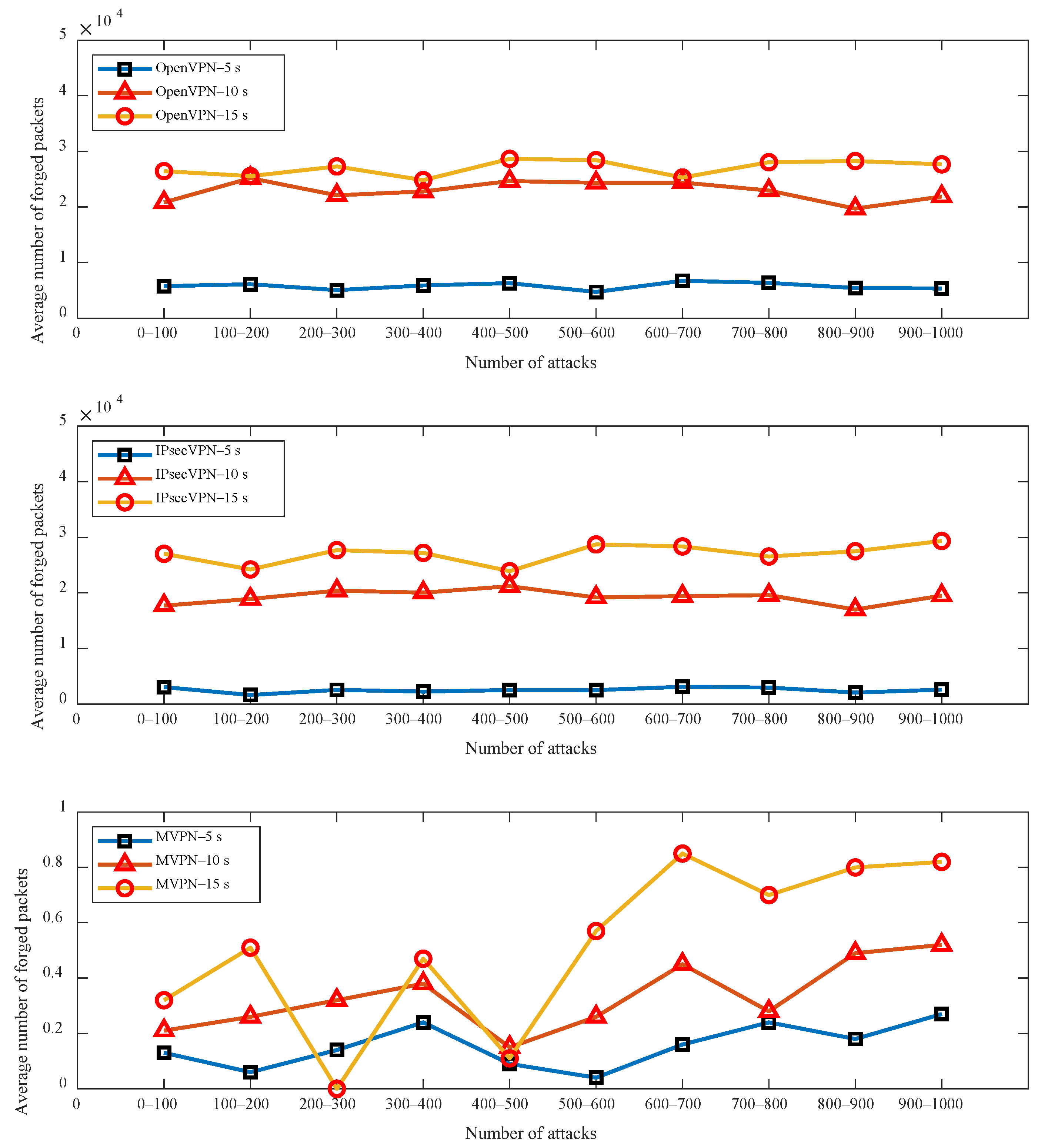
6.3. Active Defense Capability Assessment (Experiment III)
6.4. Performance Testing (Experiment IV)
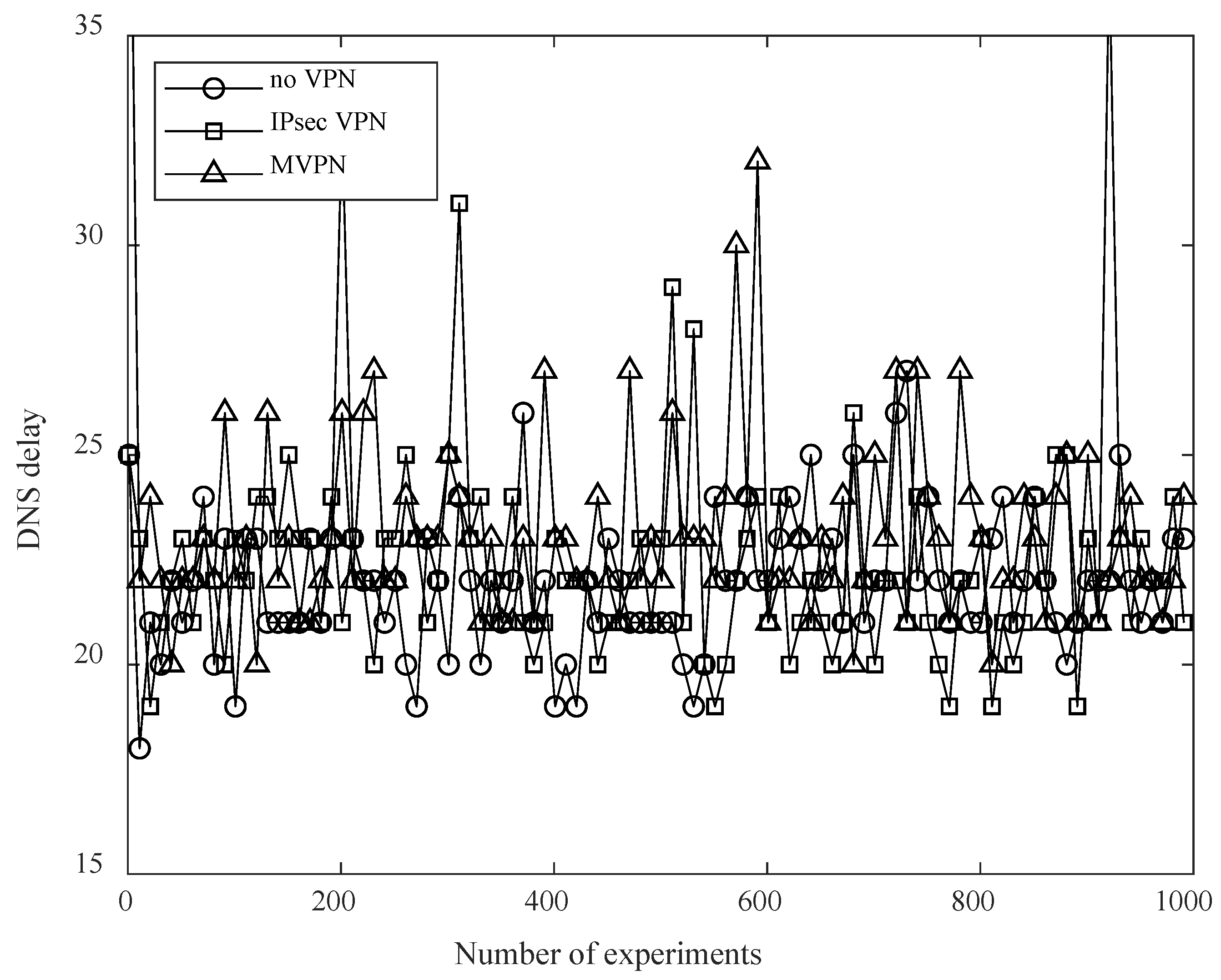
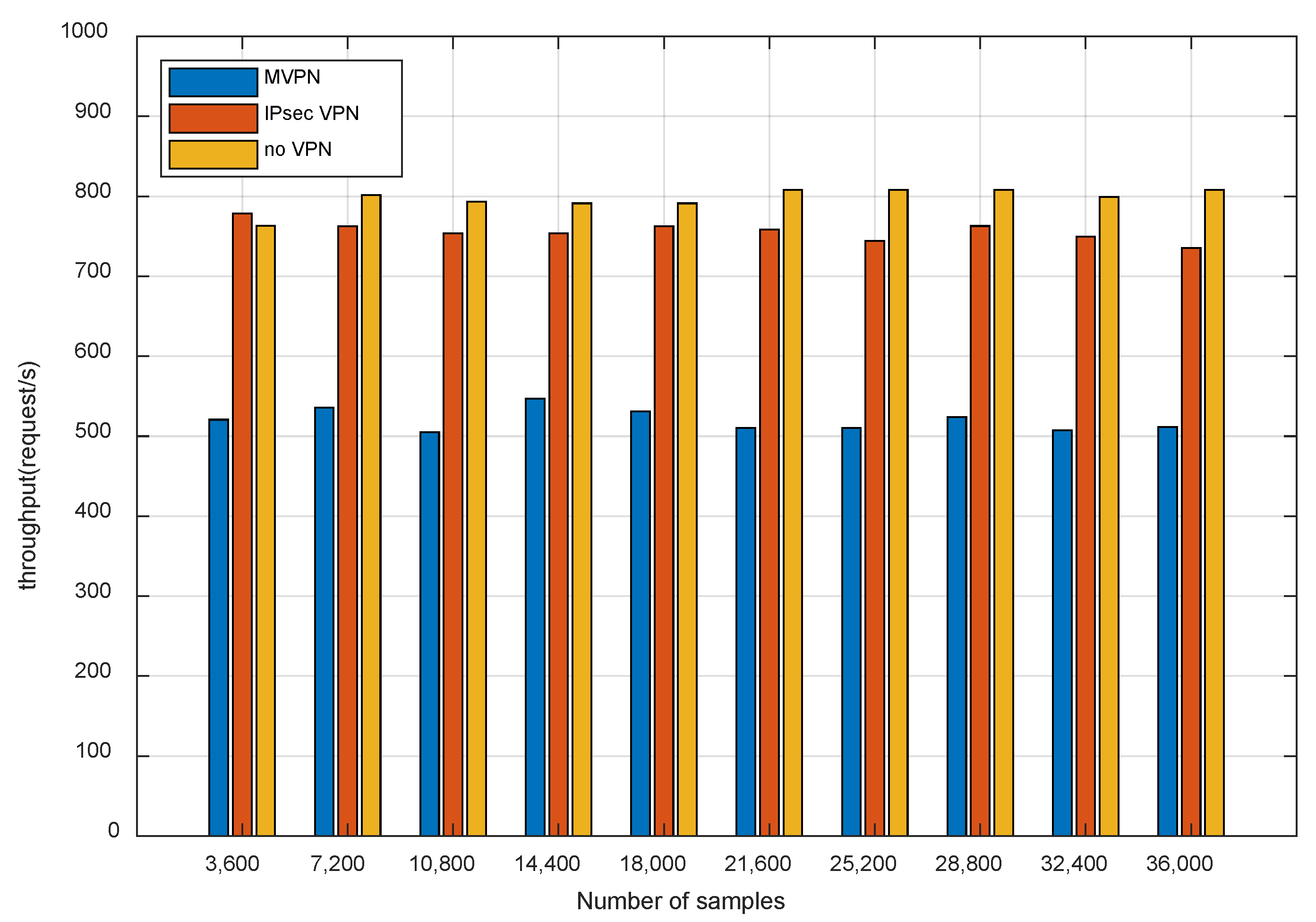
6.4.1. Delay and Throughput
6.4.2. System Stability Assessment
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Khan, M.T.; Deblasio, J.; Voelker, G.M.; Snoeren, A.C.; Vallina-Rodriguez, N. An empirical analysis of the commercial VPN ecosystem. In Proceedings of the Internet Measurement Conference 2018, Boston, MA, USA, 31 October–2 November 2018; pp. 443–456. [Google Scholar]
- Tolley, W.J.; Kujath, B.; Khan, M.T.; Vallina-Rodriguez, N.; Crandall, J.R. Blind In/On-Path Attacks and Applications to VPNs. In Proceedings of the 30th USENIX Security Symposium (USENIX Security 21), Online, 11–13 August 2021; pp. 3129–3146. [Google Scholar]
- Wang, Y.; Chen, Q.; Yi, J.; Guo, J. U-tri: Unlinkability through random identifier for sdn network. In Proceedings of the 2017 Workshop on Moving Target Defense, Dallas, TX, USA, 30 October 2017; pp. 3–15. [Google Scholar]
- Sharma, D.P.; Kim, D.S.; Yoon, S.; Lim, H.; Cho, J.-H.; Moore, T.J. FRVM: Flexible random virtual IP multiplexing in software-defined networks. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; pp. 579–587. [Google Scholar]
- Woo, S.; Moon, D.; Youn, T.Y.; Lee, Y.; Kim, Y. Can id shuffling technique (cist): Moving target defense strategy for protecting in-vehicle can. IEEE Access 2019, 7, 15521–15536. [Google Scholar] [CrossRef]
- Yuan, E.; Malek, S.; Schmerl, B.; Garlan, D.; Gennari, J. Architecture-based self-protecting software systems. In Proceedings of the 9th International ACM Sigsoft conference on Quality of software architectures, Vancouver, BC, Canada, 17–21 June 2013; pp. 33–42. [Google Scholar]
- Li, Y.; Dai, R.; Zhang, J. Morphing communications of cyber-physical systems towards moving-target defense. In Proceedings of the 2014 IEEE International Conference on Communications (ICC), Sydney, Australia, 10–14 June 2014; pp. 592–598. [Google Scholar]
- Cho, J.-H.; Sharma, D.P.; Alavizadeh, H.; Yoon, S.; Ben-Asher, N.; Moore, T.J.; Kim, D.S.; Lim, H.; Nelson, F.F. Toward proactive, adaptive defense: A survey on moving target defense. IEEE Commun. Surv. Tutor. 2020, 22, 709–745. [Google Scholar] [CrossRef]
- Marwa, A.; Malika, B.; Nacira, G. Contribution to enhance IPSec security by a safe and efficient internet key exchange proto-col. In Proceedings of the 2013 world congress on computer and information technology (WCCIT), Sousse, Tunisia, 22–24 June 2013; pp. 1–5. [Google Scholar]
- Nagalakshmi, V.; Babu, I.R.; Avadhani, P.S. Modified Protocols for Internet Key Exchange (IKE) Using Public Encryption and Signature Keys. In Proceedings of the 2011 Eighth International Conference on Information Technology: New Generations, Las Vegas, NV, USA, 11–13 April 2011; pp. 376–381. [Google Scholar]
- Fu, Z.; Wu, S.F.; Huang, H.; Loh, K.; Gong, F.; Baldine, I.; Xu, C. IPSec/VPN security policy: Cor-rectness, conflict detection, and resolution. In Proceedings of the International Workshop on Policies for Distributed Systems and Networks, Bristol, UK, 29–31 January 2001; Springer: Berlin/Heidelberg, Germany, 2001; pp. 39–56. [Google Scholar]
- Singh, A.K.; Samaddar, S.G.; Misra, A.K. Enhancing VPN security through security policy management. In Proceedings of the 2012 1st Interna-Tional Conference on Recent Advances in Information Tech-nology (RAIT), Dhanbad, India, 15–17 March 2012; pp. 137–142. [Google Scholar]
- Xue, D.; Ramesh, R.; Jain, A.; Kallitsis, M.; Halderman, J.A.; Crandall, J.R.; Ensafi, R. OpenVPN is Open to VPN Fingerprinting. In Proceedings of the 31st USENIX Security Symposium (USE-NIX Security 22), Boston, MA, USA, 10–12 August 2022; pp. 483–500. [Google Scholar]
- Perta, V.C.; Barbera, M.; Tyson, G.; Haddadi, H.; Mei, A. A glance through the VPN looking glass: IPv6 leakage and DNS hijacking in commercial VPN clients. Proc. Priv. Enh. Technol. 2015, 2015, 77–91. [Google Scholar] [CrossRef]
- Ikram, M.; Vallina-Rodriguez, N.; Seneviratne, S.; Ali, K.M.; Vern, P. An analysis of the privacy and security risks of android vpn permission-enabled apps. In Proceedings of the 2016 Internet Measurement Conference, Santa Monica, CA, USA, 14–16 November 2016; pp. 349–364. [Google Scholar]
- RFC 883; Domain Names—Implementation and Specification. IETF: Fremont, CA, USA, November 1983.
- RFC 793; Transmission Control Protocol. IETF: Fremont, CA, USA, September 1981.
- RFC 5246; The Transport Layer Security (TLS) Protocol. IETF: Fremont, CA, USA, August 2008.
- RFC 7626; DNS privacy considerations. IETF: Fremont, CA, USA, August 2015.
- Bushart, J.; Rossow, C. Padding ain’t enough: Assessing the privacy guarantees of encrypted DNS. In Proceedings of the 10th USENIX Workshop on Free and Open Communications on the Internet (FOCI 20), Online, 11 August 2020. [Google Scholar]
- Siby, S.; Juarez, M.; Diaz, C.; Vallina-Rodriguez, N.; Troncoso, C. Encrypted DNS--> Privacy? A traffic analysis perspective. arXiv 2019, arXiv:1906.09682. [Google Scholar]
- Wang, X.; Chen, S.; Jajodia, S. Network flow watermarking attack on low-latency anonymous communication systems. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP’07), Berkeley, CA, USA, 20–23 May 2007; pp. 116–130. [Google Scholar]
- Miller, B.; Huang, L.; Joseph, A.D.; Tygar, J.D. I know why you went to the clinic: Risks and realization of https traffic analysis. In Proceedings of the International Symposium on Privacy Enhancing Technologies Symposium, Amsterdam, The Netherlands, 16–18 July 2014; Springer: Cham, Switzerland, 2014; pp. 143–163. [Google Scholar]
- MacFarland, D.C.; Shue, C.A. The SDN shuffle: Creating a moving-target defense using host-based software-defined networking. In Proceedings of the Second ACM Workshop on Moving Target Defense, Denver, CO, USA, 12 October 2015; pp. 37–41. [Google Scholar]
- Antonatos, S.; Akritidis, P.; Markatos, E.P.; Anagnostakis, K.G. Defending against hitlist worms using network address space randomization. In Proceedings of the 2005 ACM Workshop on Rapid Malcode, Fairfax, VA, USA, 11 November 2005; pp. 30–40. [Google Scholar]
- Luo, Y.B.; Wang, B.S.; Cai, G.L. Effectiveness of port hopping as a moving target defense. In Proceedings of the 2014 7th International Conference on Security Technology, Hainan, China, 20–23 December 2014; pp. 7–10. [Google Scholar]
- Lei, C.; Zhang, H.Q.; Tan, J.L.; Zhang, Y.-C.; Liu, X.-H. Moving target defense techniques: A survey. Secur. Commun. Netw. 2018, 2018, 3759626. [Google Scholar] [CrossRef]
- Duan, Q.; Al-Shaer, E.; Jafarian, H. Efficient random route mutation considering flow and network constraints. In Proceedings of the 2013 IEEE Conference on Communications and Network Security (CNS), National Harbor, MD, USA, 14–16 October 2013; pp. 260–268. [Google Scholar]
- Carlson, J. Redis in Action; Simon and Schuster: New York, NY, USA, 2013. [Google Scholar]
- Chen, F.C.; He, W.Z.; Cheng, G.Z.; Huo, S.; Zhou, D. Design of key technologies for intranet dynamic gateway based on DPDK. J. Commun. 2020, 41, 139–151. [Google Scholar]
- Wang, Z.-P.; Hu, H.-C.; Cheng, G.-Z. A DNS Architecture Based on Mimic Security Defense. Acta Electron. Sin. 2017, 45, 2705–2714. [Google Scholar]
- De la Cadena, W.; Mitseva, A.; Hiller, J.; Pennekamp, J.; Reuter, S.; Filter, J.; Engel, T.; Wehrle, K.; Panchenko, A. Trafficsliver: Fighting website fingerprinting attacks with traffic splitting. In Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security, Online, 9–13 November 2020; pp. 1971–1985. [Google Scholar]




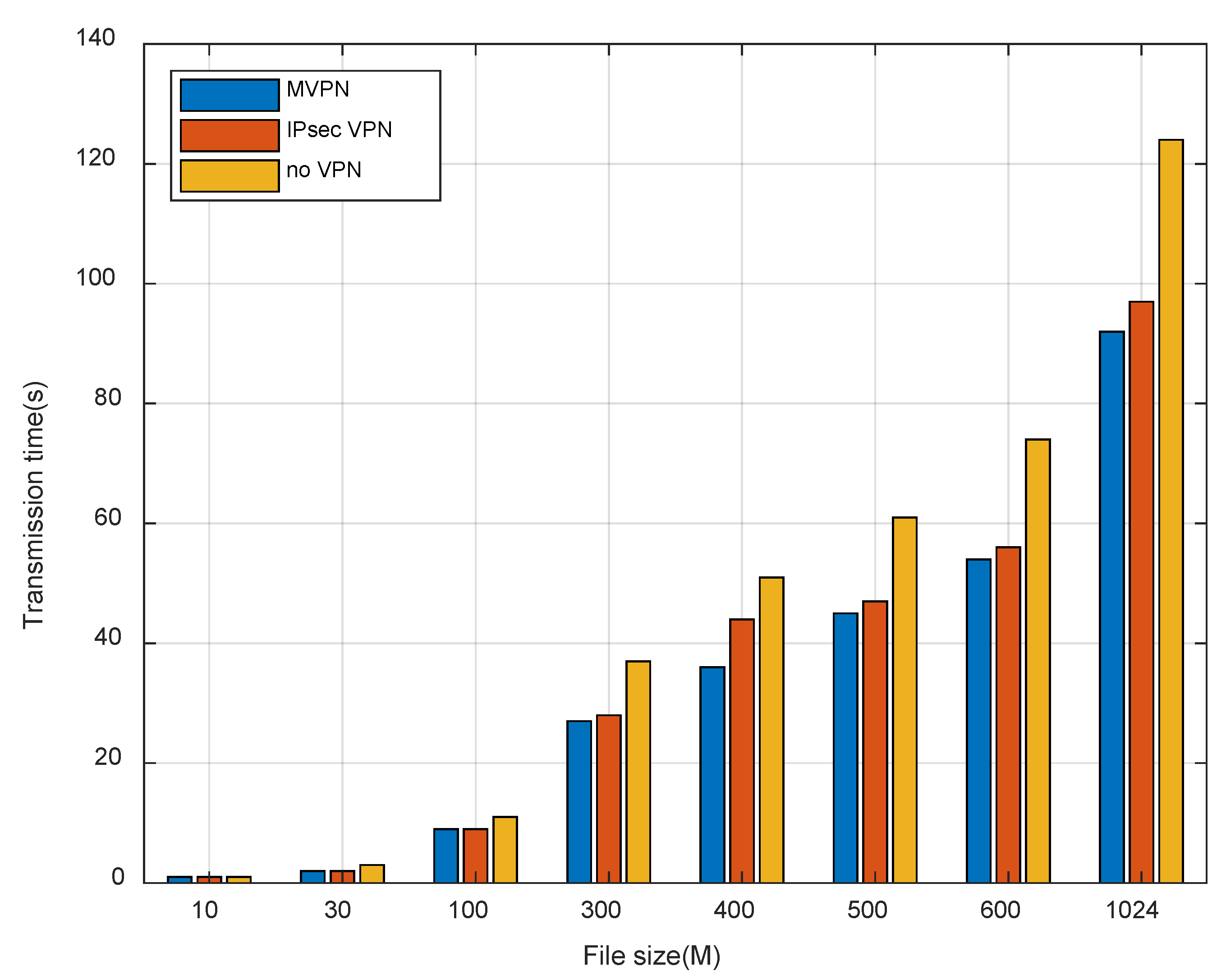
| Variable Name | Variable Meaning |
|---|---|
| The probability that an attacker can “guess” a single forged message | |
| DNS timeout | |
| The number of forged packets sent by attackers within the timeout period | |
| Number of forged packets sent by attackers per second | |
| Value range of TXID | |
| Value range of port | |
| Number of nodes in the active set |
| Variable Name | Variable Value |
|---|---|
| 64,000 | |
| 65,535 | |
| 3 | |
| 5 | |
| 10 | |
| 15 |
| Timeout | Experimental Result [2] | Simulation Result |
|---|---|---|
| 5 | 75.3% | 79.6% |
| 10 | 48.1% | 43.7% |
| 15 | 11.6% | 10.8% |
| Timeout | IPsec VPN | MVPN |
|---|---|---|
| 5 | 77.6% | 0 |
| 10 | 50.2% | 0 |
| 15 | 9.5% | 0 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gao, Z.; Chen, F.; Wang, Y.; He, W.; Shi, X.; Xie, G. MVPN: A Defense Architecture against VPN Traffic Hijacking Based on MTD. Electronics 2023, 12, 711. https://doi.org/10.3390/electronics12030711
Gao Z, Chen F, Wang Y, He W, Shi X, Xie G. MVPN: A Defense Architecture against VPN Traffic Hijacking Based on MTD. Electronics. 2023; 12(3):711. https://doi.org/10.3390/electronics12030711
Chicago/Turabian StyleGao, Zhen, Fucai Chen, Yawen Wang, Weizhen He, Xin Shi, and Genlin Xie. 2023. "MVPN: A Defense Architecture against VPN Traffic Hijacking Based on MTD" Electronics 12, no. 3: 711. https://doi.org/10.3390/electronics12030711
APA StyleGao, Z., Chen, F., Wang, Y., He, W., Shi, X., & Xie, G. (2023). MVPN: A Defense Architecture against VPN Traffic Hijacking Based on MTD. Electronics, 12(3), 711. https://doi.org/10.3390/electronics12030711






