Reliably Controlling Massive Traffic between a Sensor Network End Internet of Things Device Environment and a Hub Using Transmission Control Protocol Mechanisms
Abstract
:1. Introduction and State-of-the-Art
1.1. Relevance of the Research
1.2. State-of-the-Art
1.3. Main Attributes of this Research
- -
- to formalize the parametric space for an adequate representation of the research object;
- -
- to formalize the concepts that characterize the features of the interaction of the main mechanisms of the TCP (Slow Start, Additive-Increase/Multiplicative-Decrease) when controlling massive data transfer from the SNEIoTD environment to a hub discretely and continuously;
- -
- to formalize the information technology for calculating the TCP Window Size of both mentioned mechanisms and the <ssthresh> parameter;
- -
- to implement a numerical experiment, the results of which will justify the effectiveness of the created mathematical apparatus.
2. Materials and Methods
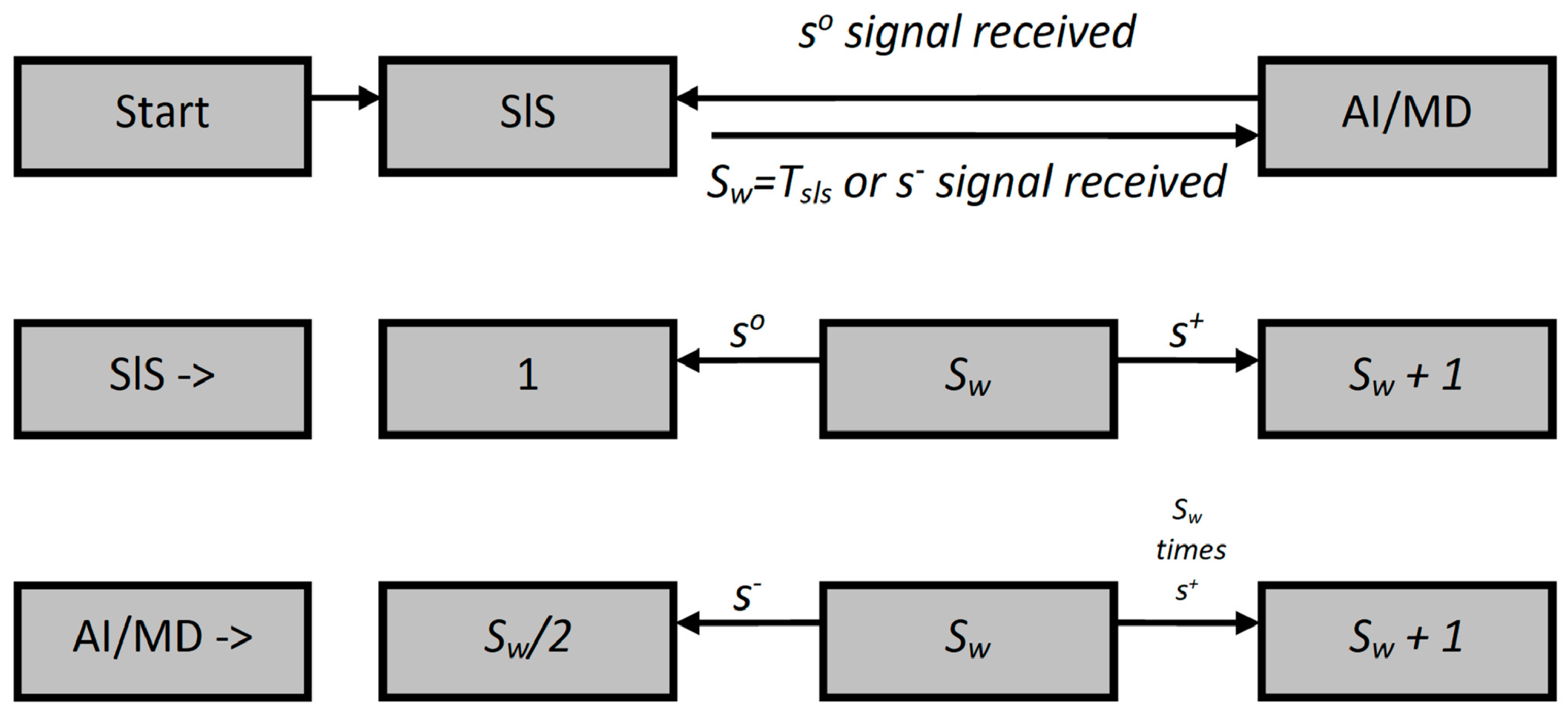
2.1. Statement of the Research
- -
- data block received in full: ,
- -
- data block received with skips: ,
- -
- reverse signal not received (communication channel overload): .
- -
- the probabilities are determined exclusively by an existing value of the parameter and do not depend on the previous values of the parameters , ;
- -
- for the probabilities , the equality is fulfilled. At the same time, when , the values of probabilities represent the functioning of the SlS mechanism, and when the values of probabilities represent the functioning of the AI/MD mechanism;
- -
- SNEIoTD always has relevant data for sending to a hub;
- -
- the initiating value is at the same time a deterministic upper limit of the value of the parameter for any moment of implementation of the studied process;
- -
- parameter is a stochastic value with distribution function .
2.2. Research of the Distribution Function of the Stochastic Parameter TCP Window Size for the Studied Process
2.3. Elements of the Research of a TCP Window Size Dynamic Properties in Continuous Time
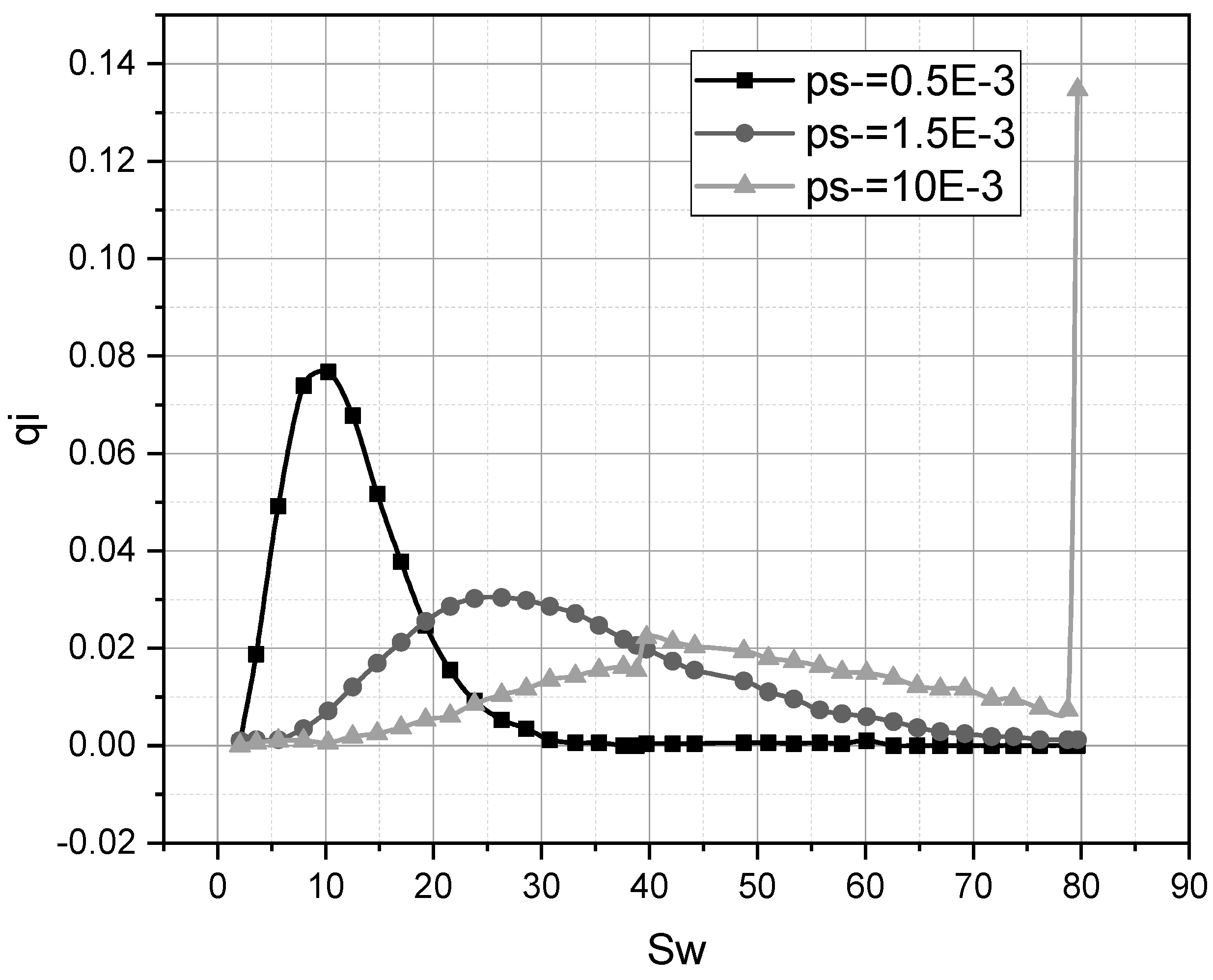
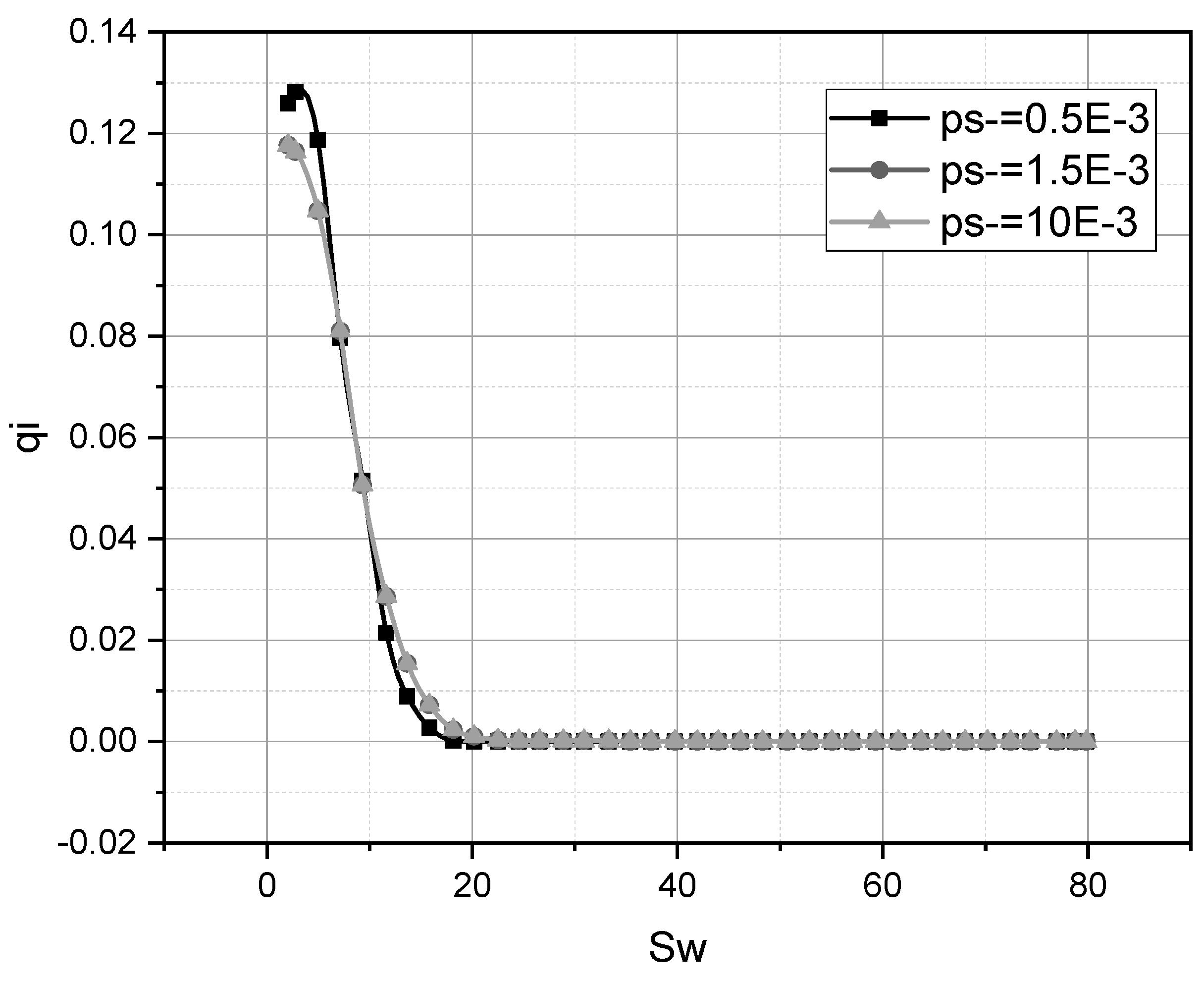
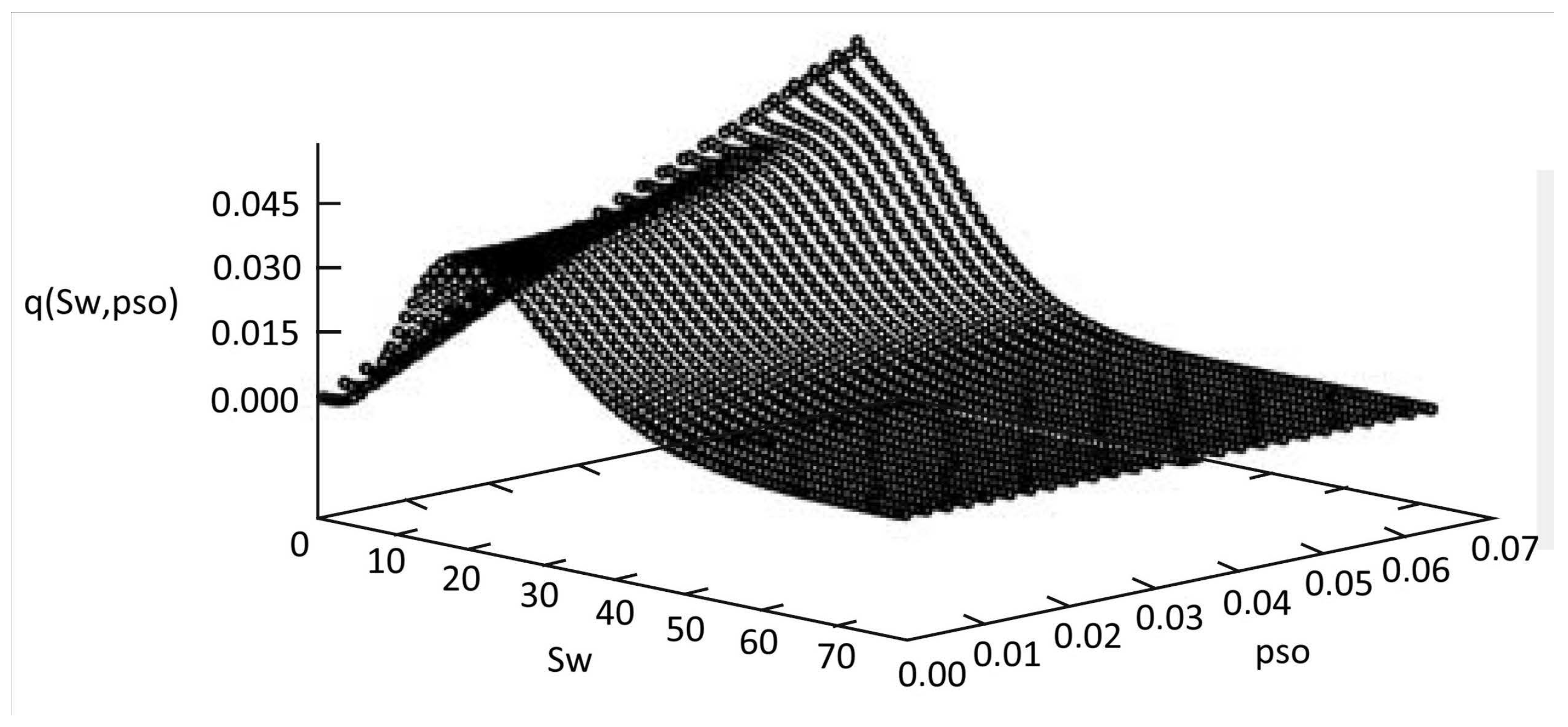
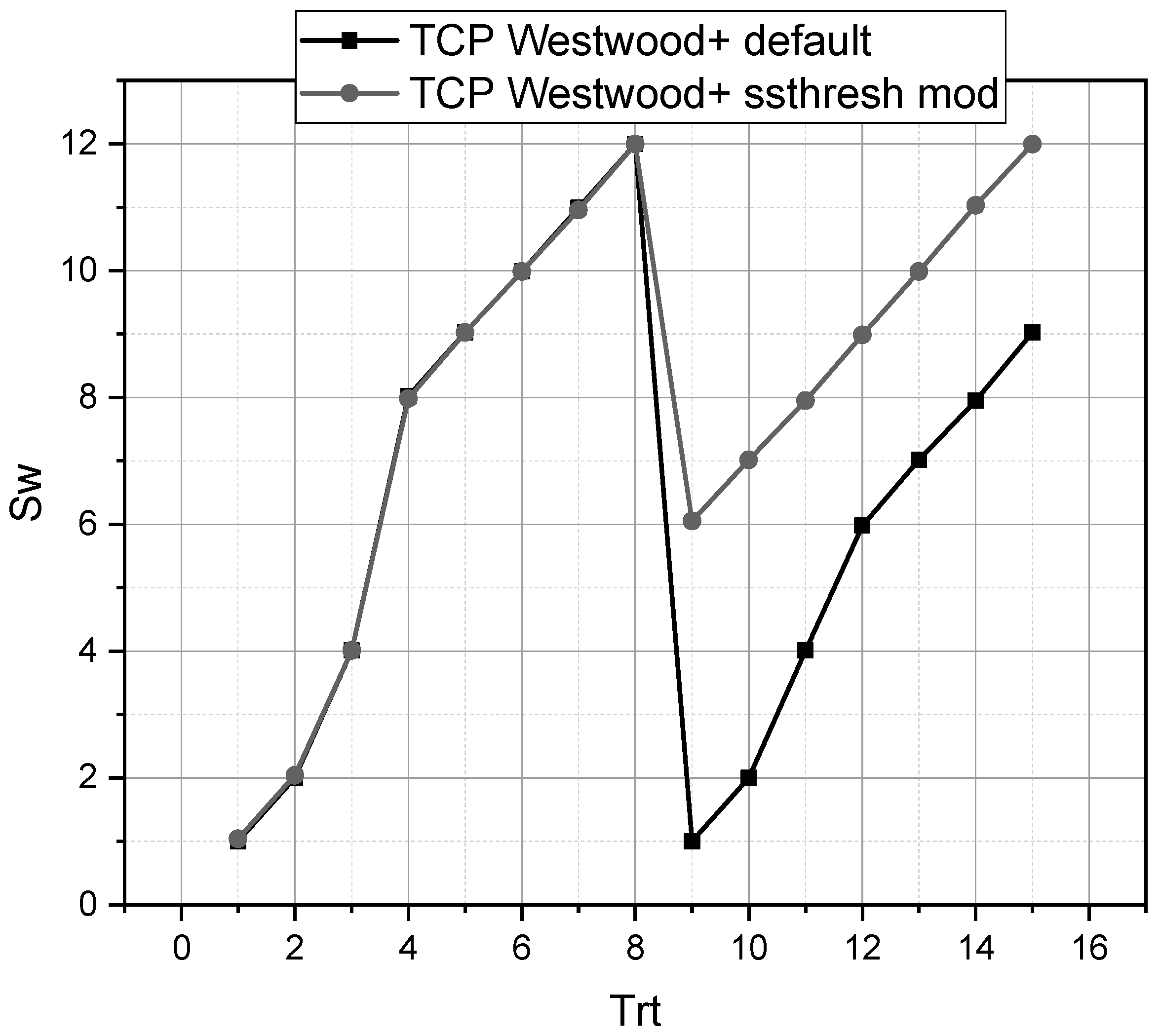
3. Results and Discussion
4. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Nomenclature
| is TCP Window Size; |
| is a Slow Start Threshold; |
| is a set of feedback signals; |
| is Round-Trip Time; |
| is a “data block received” feedback signal; |
| is a “data block received with skips” feedback signal; |
| is a “reverse signal not received” feedback signal; |
| is the actual capacity of the route between the SNEIoTD and a hub; |
| is the probability of obtaining a series of signals of length ; |
| is the probability of obtaining an arbitrary series of signals of length ; |
| is the probability of obtaining a signal for a series of data blocks of length sent to a hub at ; |
| is a distribution function of a stochastic parameter ; |
| is the deterministic upper limit of the value of the parameter for any moment of implementation of the studied process; |
| is a basic representation of the investigated process; |
| is a binary parameter, where corresponds to the SlS mechanism, and corresponds to the AI/MD mechanism; |
| is the stationary distribution of a vector ; |
| is a parameter derived from ; |
| , are iterators. |
References
- Rezaee, N.; Zanjirchi, S.M.; Jalilian, N.; Bamakan, S.M.H. Internet of Things Empowering Operations Management; A Systematic Review Based on Bibliometric and Content Analysis. Telemat. Inform. Rep. 2023, 11, 100096. [Google Scholar] [CrossRef]
- Verma, H.; Chauhan, N.; Awasthi, L.K. A Comprehensive Review of ‘Internet of Healthcare Things’: Networking Aspects, Technologies, Services, Applications, Challenges, and Security Concerns. Comput. Sci. Rev. 2023, 50, 100591. [Google Scholar] [CrossRef]
- Moges, T.H.; Lakew, D.S.; Nguyen, N.P.; Dao, N.-N.; Cho, S. Cellular Internet of Things: Use Cases, Technologies, and Future Work. Internet Things 2023, 24, 100910. [Google Scholar] [CrossRef]
- Izonin, I.; Tkachenko, R.; Duriagina, Z.; Shakhovska, N.; Kovtun, V.; Lotoshynska, N. Smart Web Service of Ti-Based Alloy’s Quality Evaluation for Medical Implants Manufacturing. Appl. Sci. 2022, 12, 5238. [Google Scholar] [CrossRef]
- Sulieman, N.A.; Celsi, L.R.; Li, W.; Zomaya, A.; Villari, M. Edge-Oriented Computing: A Survey on Research and Use Cases. Energies 2022, 15, 452. [Google Scholar] [CrossRef]
- Capra, M.; Peloso, R.; Masera, G.; Roch, M.R.; Martina, M. Edge Computing: A Survey On the Hardware Requirements in the Internet of Things World. Futur. Internet 2019, 11, 100. [Google Scholar] [CrossRef]
- Kovtun, V.; Grochla, K.; Połys, K. Investigation of the Information Interaction of a sensor network end IoT Device and a hub at the Transport Protocol Level. Electronics 2023, 12, 4662. [Google Scholar] [CrossRef]
- Kovtun, V.; Altameem, T.; Al-Maitah, M.; Kempa, W. The Markov Concept of the Energy Efficiency Assessment of the Edge Computing Infrastructure Peripheral Server Functioning over Time. Electronics 2023, 12, 4320. [Google Scholar] [CrossRef]
- Alavikia, Z.; Shabro, M. A Comprehensive Layered Approach for Implementing Internet of Things-Enabled Smart Grid: A Survey. Digit. Commun. Netw. 2022, 8, 388–410. [Google Scholar] [CrossRef]
- Lombardi, M.; Pascale, F.; Santaniello, D. Internet of Things: A General Overview between Architectures, Protocols and Applications. Information 2021, 12, 87. [Google Scholar] [CrossRef]
- Amin, M.S.; Rahman, S. An Introduction of Open System Interconnection (OSI) Model and Its Architecture. Preprints 2023. [Google Scholar] [CrossRef]
- Kovtun, V.; Izonin, I.; Gregus, M. Mathematical Models of the Information Interaction Process in 5G-IoT Ecosystem: Different Functional Scenarios. ICT Express 2023, 9, 264–269. [Google Scholar] [CrossRef]
- Gerodimos, A.; Maglaras, L.; Ferrag, M.A.; Ayres, N.; Kantzavelou, I. IoT: Communication Protocols and Security Threats. Internet Things Cyber-Phys. Syst. 2023, 3, 1–13. [Google Scholar] [CrossRef]
- Habib, S.; Qadir, J.; Ali, A.; Habib, D.; Li, M.; Sathiaseelan, A. The Past, Present, and Future of Transport-Layer Multipath. J. Netw. Comput. Appl. 2016, 75, 236–258. [Google Scholar] [CrossRef]
- Herrero, R. Analysis of the Constrained Application Protocol over Quick UDP Internet Connection Transport. Internet Things 2020, 12, 100328. [Google Scholar] [CrossRef]
- Nor, S.A.; Alubady, R.; Kamil, W.A. Simulated Performance of TCP, SCTP, DCCP and UDP Protocols over 4G Network. Procedia Comput. Sci. 2017, 111, 2–7. [Google Scholar] [CrossRef]
- Kovtun, V.; Izonin, I.; Gregus, M. Formalization of the Metric of Parameters for Quality Evaluation of the Subject-System Interaction Session in the 5G-IoT Ecosystem. Alex. Eng. J. 2022, 61, 7941–7952. [Google Scholar] [CrossRef]
- Ren, Y.; Yang, W.; Zhou, X.; Chen, H.; Liu, B. A Survey on TCP over mmWave. Comput. Commun. 2021, 171, 80–88. [Google Scholar] [CrossRef]
- Garcia-Macias, J.A. Transport in the IP-Based Internet of Things: Status Report. Procedia Comput. Sci. 2023, 224, 18–25. [Google Scholar] [CrossRef]
- Wytrębowicz, J.; Cabaj, K.; Krawiec, J. Messaging Protocols for IoT Systems—A Pragmatic Comparison. Sensors 2021, 21, 6904. [Google Scholar] [CrossRef] [PubMed]
- Anelli, P.; Diana, R.; Lochin, E. FavorQueue: A Parameterless Active Queue Management to Improve TCP Traffic Performance. Comput. Netw. 2014, 60, 171–186. [Google Scholar] [CrossRef]
- Tran, V.-H.; De Coninck, Q.; Hesmans, B.; Sadre, R.; Bonaventure, O. Observing Real Multipath TCP Traffic. Comput. Commun. 2016, 94, 114–122. [Google Scholar] [CrossRef]
- Lee, I.W.; Fapojuwo, A.O. Analysis and modeling of a campus wireless network TCP/IP traffic. Comput. Netw. 2009, 53, 2674–2687. [Google Scholar] [CrossRef]
- Christin, N.; Liebeherr, J. Marking Algorithms for Service Differentiation of TCP Traffic. Comput. Commun. 2005, 28, 2058–2069. [Google Scholar] [CrossRef]
- Hussain, S.Z.; Parween, S. Comparative Study of TCP Congestion Control Algorithm in IoT. In Proceedings of the 2021 3rd International Conference on Advances in Computing, Communication Control and Networking (ICAC3N), Greater Noida, India, 17–18 December 2021. [Google Scholar] [CrossRef]
- Pandya, P. Transmission Control Protocol/Internet Protocol Packet Analysis. In Computer and Information Security Handbook; Morgan Kaufmann: Burlington, MA, USA, 2013; pp. e205–e218. [Google Scholar] [CrossRef]
- Loshin, P. Transmission Control Protocol. TCP/IP Clear. Explain. 2003, 351–382. [Google Scholar] [CrossRef]
- Verma, L.P.; Kumar, M. An IoT Based Congestion Control Algorithm. Internet Things 2019, 9, 100157. [Google Scholar] [CrossRef]
- Briones, A.; Mallorquí, A.; Zaballos, A.; de Pozuelo, R.M. Wireless Loss Detection over Fairly Shared Heterogeneous Long Fat Networks. Electronics 2021, 10, 987. [Google Scholar] [CrossRef]
- Ju, B.-G.; Kim, M.; Kim, S.; Moreno-Ternero, J.D. Fair International Protocols for the Abatement of GHG Emissions. Energy Econ. 2021, 94, 105091. [Google Scholar] [CrossRef]
- Ragnoli, M.; Stornelli, V.; Del Tosto, D.; Barile, G.; Leoni, A.; Ferri, G. Flood Monitoring: A LoRa Based Case-Study in the City of L’Aquila. In Proceedings of the 2022 17th Conference on Ph.D Research in Microelectronics and Electronics (PRIME), Villasimius, Italy, 12–15 June 2022. [Google Scholar] [CrossRef]
- Perković, T.; Rodić, L.D.; Šabić, J.; Šolić, P. Machine Learning Approach towards LoRaWAN Indoor Localization. Electronics 2023, 12, 457. [Google Scholar] [CrossRef]
- Zhdanok, A. Invariant Finitely Additive Measures for General Markov Chains and the Doeblin Condition. Mathematics 2023, 11, 3388. [Google Scholar] [CrossRef]
- Sarkar, N.I.; Ammann, R.; Zabir, S.M.S. Analyzing TCP Performance in High Bit Error Rate Using Simulation and Modeling. Electronics 2022, 11, 2254. [Google Scholar] [CrossRef]
- Olmedo, G.; Lara-Cueva, R.; Martínez, D.; de Almeida, C. Performance Analysis of a Novel TCP Protocol Algorithm Adapted to Wireless Networks. Futur. Internet 2020, 12, 101. [Google Scholar] [CrossRef]






Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kovtun, V.; Grochla, K.; Kempa, W.; Połys, K. Reliably Controlling Massive Traffic between a Sensor Network End Internet of Things Device Environment and a Hub Using Transmission Control Protocol Mechanisms. Electronics 2023, 12, 4920. https://doi.org/10.3390/electronics12244920
Kovtun V, Grochla K, Kempa W, Połys K. Reliably Controlling Massive Traffic between a Sensor Network End Internet of Things Device Environment and a Hub Using Transmission Control Protocol Mechanisms. Electronics. 2023; 12(24):4920. https://doi.org/10.3390/electronics12244920
Chicago/Turabian StyleKovtun, Viacheslav, Krzysztof Grochla, Wojciech Kempa, and Konrad Połys. 2023. "Reliably Controlling Massive Traffic between a Sensor Network End Internet of Things Device Environment and a Hub Using Transmission Control Protocol Mechanisms" Electronics 12, no. 24: 4920. https://doi.org/10.3390/electronics12244920
APA StyleKovtun, V., Grochla, K., Kempa, W., & Połys, K. (2023). Reliably Controlling Massive Traffic between a Sensor Network End Internet of Things Device Environment and a Hub Using Transmission Control Protocol Mechanisms. Electronics, 12(24), 4920. https://doi.org/10.3390/electronics12244920








