1. Introduction
In the past, the communication of urban traffic control (UTC) systems used dedicated networks, which resulted in rare occurrences of attacks on traffic signal networks. As a result, research on the security protection of traffic signal networks has not received widespread attention. Li et al. discovered and proved that the currently deployed connected traffic signal systems in the United States have many security vulnerabilities due to system failures. They proposed a game theory framework that promotes network security and efficient traffic management [
1,
2]. Haddad et al. proposed an elastic boundary control scheme based on the macroscopic fundamental diagram (MFD) to mitigate the impact of network attacks on traffic signal systems. The developed algorithm can adaptively compensate for the effects of attacks without the need for online fault detection. The stability of closed-loop systems regarding tracking and parameter errors is also demonstrated [
3]. Khattak et al. analyzed the security vulnerabilities of active traffic management (ATM) in Virginia, providing a method to determine whether the monitoring system is under attack in real time [
4]. Other security researchers have also identified various vulnerabilities in traffic signal systems [
5].
Research on UTC system security is relatively scarce. Industrial control systems and UTC systems are both cyber-physical systems that share many similarities. Therefore, research on industrial control system security can provide valuable insights. Nateghi et al. studied the problem of online security state estimation and attack reconstruction to design a resilient controller for systems. The effectiveness of this technique was validated through attack simulations on a real power system [
6]. Wang et al. introduced a Bayesian honeypot game model as a bait system for detecting and collecting attack information in advanced metering infrastructure (AMI) in industrial power control systems. This model overcomes the weakness of traditional honeypot technology in detecting dynamic attacks [
7]. However, the construction of precise system mechanism models and attack models is complex and challenging, limiting their practical application. Xu et al. proposed a resilient, memory event-triggered scheme (RMETS) for systems. This scheme effectively balances the security performance required by the system with limited network resources in the event of an attack [
8].
Research on the information security issues of UTC systems is valuable and necessary. In the process of information attack and defense in UTC systems, attackers and defenders engage in a clear game relationship, making game theory an appropriate method for modeling and analyzing these issues. There have been numerous studies on information security using game theory. Lye et al. applied stochastic game theory to establish a two-player game model for attackers and defenders, obtaining the optimal strategies for both parties by calculating the Nash equilibrium solutions of the model [
9]. Zhu et al. employed multi-player non-zero-sum and stochastic game methods to analyze the adversarial behavior between intrusion detection systems and malicious intruders, optimizing the configuration and cooperation of defense systems [
10]. Hewett et al. used a complete and perfect information dynamic game approach to analyze the information security of a power grid SCADA system [
11]. Game theory has also been applied to defend against distributed denial of service (DDoS) attacks [
12,
13,
14]. Information security often involves incomplete information games. Shaolin Tan et al. developed an absolute distance-based consensus protocol for multi-agent systems to help agents reach a consensus point without knowing the relative positions of other agents [
15]. Singh et al. designed the learning algorithm for the incomplete information game (LAIIG), which effectively updates participants’ information machines [
16]. Varga B et al. designed near-potential differential games (NPDG) and applied them to large-scale vehicle control systems, verifying the effectiveness of the algorithm [
17].
Ahmad F et al. categorized the research on game theory related to traffic into four groups: traffic management, behavioral interactions, routing operation, and transport safety. They found that classical game theory has various limitations, while evolutionary game theory (EGT) is more suitable for simulating real-world scenarios. They mention that Nash equilibrium (NE) does not necessarily guarantee optimal returns for each participant. In some games, there may be multiple NE states, and evolutionary game theory focuses on the decision-making process, which can effectively solve the problem of multiple equilibria. Some scholars have already applied EGT to information security research [
18]. Shi L et al. constructed a three-party evolutionary game model of array honeypots composed of defenders, attackers, and legitimate users. By analyzing the strategies and benefits of participants in the game and establishing a three-party game payoff matrix, they obtained evolutionarily stable strategies by analyzing the replicator dynamic equations of each party [
19]. Yang Y et al. proposed a multistage asymmetric information attack and defense model (MAIAD) for Internet of Things (IoT) systems. Under the premise of information asymmetry, MAIAD can determine the optimal defense strategy for IoT systems [
20]. Their research only focuses on the information level or IoT as the object, without considering the actual situation in the traffic control environment.
In UTC systems, there are often two control entities, upper computers (UC) and traffic signal machines (TSM), which can respond to the impacts of attackers through coordinated control or individual defense. We use EGT analysis tools to explore the stable strategies and system equilibrium points in this three-party attack–defense game. Evolutionary game theory assumes that players are rational given their preferences, but these preferences may evolve over time. In this study, EGT can be represented as follows: attackers in the traffic environment make attack decisions based on individual profit maximization (i.e., they respond rationally to the current state of the system), while the system state evolves over time, causing changes in the payoffs for attacking and not attacking, leading UC and TSM to replicate and dynamically adjust their defense strategies. Compared to traditional information security research that only focuses on the game between attackers and defenders, the three-party game introduces more uncertainty factors, making cooperation and coordination between UC and TSM more challenging, especially in situations where false negatives and false positives may occur.
This paper answers the following key questions:
(1) In order to counter attacks, what defense strategies should Upper Computers (UC) and Traffic Signal Machines (TSM) adopt?
(2) What defense strategies should Upper Computers (UC) and Traffic Signal Machines (TSM) adopt to counter attacks? How do detection rates and defense costs affect the decision making of the participants?
(3) Is it possible for both UC and TSM to abandon defense in the end? This would be highly undesirable. What conditions might lead to this, and how can we prevent it from occurring?
The remainder of the paper is organised as follows:
Section 2 describes the problem and its corresponding assumptions, and establishes the framework of the basic model.
Section 3 analyzes the strategy stability of each participant.
Section 4 employs the first Lyapunov method to analyze the stability of pure-strategy equilibria of the replicator dynamic system, obtaining evolutionarily stable strategy combinations under different conditions.
Section 5 and
Section 6 conduct numerical simulations and discuss the impact of parameters.
Section 7 concludes the research and provides insights.
2. Evolutionary Game Model
To investigate the security issues of a traffic signal network, it is necessary to first understand the network structure of the UTC system, as shown in
Figure 1. Typically, the TSM is located near a corresponding intersection, and is responsible for receiving data information from the UC and various traffic detection devices, as well as controlling the traffic signal lights. The UC is housed in the local public transportation management department and is primarily responsible for the coordination, management, and control of the TSMs at each intersection.
In the UTC system, there are numerous attackers who use various attack methods to disrupt or even paralyze the traffic signal system in order to achieve their own objectives. In response to the malicious behavior of attackers, security personnel in different locations employ various defensive strategies. At the beginning, there is limited knowledge about each other’s situation, and through continuous experimentation, they learn about each other and improve their strategies. Eventually, they find the choices that are most favorable to themselves, leading to a stable state. Therefore, studying these stable states and the conditions for their occurrence is meaningful for ensuring the secure operation of the UTC system. Sometimes, the defense cost may be too high, such as protecting one road smoothly at the expense of causing congestion on others, which is clearly not wise. Finding the conditions under which UC and TSM abandon defense can help security personnel avoid such situations. Similarly, identifying the conditions under which attackers abandon their attacks can effectively reduce security incidents in the UTC system. Therefore, the use of EGT to analyze and study the security game process in the UTC system will be beneficial.
Hypothesis 1. Let
represent the UC, and its defensive strategy includes selecting defense
with probability
and not defending
with probability
,
. Let
represent the TSM, and its defensive strategy includes selecting defense
with probability
and not defending
with probability
,
. Let
represent the attacker, and its strategy includes selecting attack
with probability
and not attacking
with probability
,
. Let
represent the detection rate of the attack detection system (true positive rate, TPR),
. represents the false alarm rate (false positive rate, FPR),
. represents the security value of the traffic network.
represents the attack cost,
. represents the individual defense cost of the UC, and
represents the UC’s defense cost when coordinating with the TSM,
. Let
represent the individual defense cost of the TSM, and
represent the TSM’s defense cost when coordinating with the UC,
.
Hypothesis 2. If both parties in the game are purely rational, the security value of the traffic network S should be greater than any cost. Otherwise, there is no reason for the parties to adopt strategies for the sake of security value [21]. Next, we discuss the payoffs under various strategies for the attacker when the attacker targets the UC position. When the strategy is , the attacker’s payoff is ; the payoffs for the two defenders are . When the strategy is the UC and TSM engage in coordinated defense; the UC’s expected payoff is , and the same applies to the TSM. The attacker’s payoff is the loss of the defenders’ payoff minus the attack cost: . When the strategy is , the UC’s payoff for individual defense is , the TSM’s payoff is , and the attacker’s payoff is . When there are no detection errors by the attack detection system, the defenders incur cost: .
By analyzing the payoffs under various strategies for the participants, we can obtain the evolutionary game payoff matrix of the three-party game, as shown in
Table 1. This table reflects the payoff situation of the three parties under various strategy combinations when the attacker chooses a certain attack behavior at a particular moment. If the attacker switches to another attack method, the defensive strategies of the UC and TSM will change accordingly, and the values of the corresponding strategy costs and detection rates will also change.
3. Strategic Stability Analysis
The expected payoff and average expected payoff for the UC when adopting the strategy are
The replicator dynamic equation for the UC, based on the Malthusian equation and combined Equations (1)–(3), is as follows [
22,
23]:
The expected payoff and average expected payoff for the TSM when adopting the strategy are
The replicator dynamic equation for the TSM is
The expected payoff and average expected payoff for the attacker when adopting the strategy are
The replicator dynamic equation for the attacker is
Based on the above, the replicator dynamic equation system for the three-party evolutionary game is as follows:
According to the principle of evolutionary stability, the probability of strategy choices by participants must satisfy the following conditions to reach evolutionary stability:
First, analyzing the UC by combining Equations (13) and (14):
When , , the UC’s strategy choice remains stable and does not vary over time. When , and . According to Equation (14), we find that is a stable point, representing the UC’s strategy () as an evolutionarily stable strategy (ESS). When , and . According to Equation (14), we find that is an ESS, representing the UC’s strategy choice of not defending.
Analyzing the TSM by combining Equations (13) and (14):
When , , the TSM’s strategy choice remains stable and does not vary over time. When , and . According to Equation (14), we find that is an ESS, representing the TSM’s strategy choice of defending. When , and . According to Equation (14), we find that is an ESS, representing the TSM’s strategy choice of not defending.
Lastly, analyzing the attacker by combining Equations (13) and (14):
When , , the attacker’s strategy choice remains stable and does not vary over time. When , and . According to Equation (14), we find that is an ESS, representing the attacker’s strategy choice of not attacking. When , and . According to Equation (14), we find that is an ESS, representing the attacker’s strategy choice of attacking.
4. Equilibrium Point Stability Analysis
By solving
, we obtain 8 pure-strategy equilibrium points, as shown in
Table 2. In this paper, the stability of the evolutionary game system is determined using the Liapunov method. Based on the replicator dynamic equation system (13), the Jacobian matrix is as follows:
Using the Liapunov first method [
24], if all eigenvalues of the Jacobian matrix have negative real parts, the equilibrium points are asymptotically stable. If at least one eigenvalue of the Jacobian matrix has a positive real part, the equilibrium points are unstable. If the Jacobian matrix has eigenvalues with real parts equal to zero, while the remaining eigenvalues have negative real parts, the equilibrium points are in a critical state and their stability cannot be determined solely by the sign of the eigenvalues. The stability of each equilibrium point is analyzed as follows:
For the equilibrium point , when or , the equilibrium point is in a critical state and its stability cannot be determined by the sign of the eigenvalues. When and , the equilibrium point is asymptotically stable. This indicates that when the detection rate is too low or the defense cost is close to the security value, both the UC and TSM evolve to a stable state of not defending due to their own interests. As a result, the system is vulnerable to attacks, and poses a serious threat to the safety of urban public transportation. To avoid the situation where the game stabilizes at the strategy combination , traffic signal system security workers should strive to increase the detection rate and reduce the defense cost.
For the equilibrium point , by the same analysis, when or , the equilibrium point is in a critical state and its stability cannot be determined by the sign of the eigenvalues. When and , the equilibrium point is asymptotically stable. This indicates that when the detection rate is high or the defense cost of the UC is low, for their own interests, the evolutionary stable strategy combination for the three parties will stabilize at the strategy combination , indicating that the UC will actively defend against the attacker’s attacks.
For the equilibrium point , by the same analysis, when or , the equilibrium point is in a critical state and its stability cannot be determined by the sign of the eigenvalues. When and , the equilibrium point is asymptotically stable. This indicates that when the detection rate is high or the defense cost of the TSM is low, for their own interests, the evolutionary stable strategy combination for the three parties will stabilize at the strategy combination , indicating that the TSM will actively defend against the attacker’s attacks.
5. Simulation
To verify the effectiveness of the stability analysis, numerical values are assigned to the model and numerical simulations are conducted using MATLAB. The parameters used are as follows:
These parameters satisfy the conditions for the equilibrium points
and
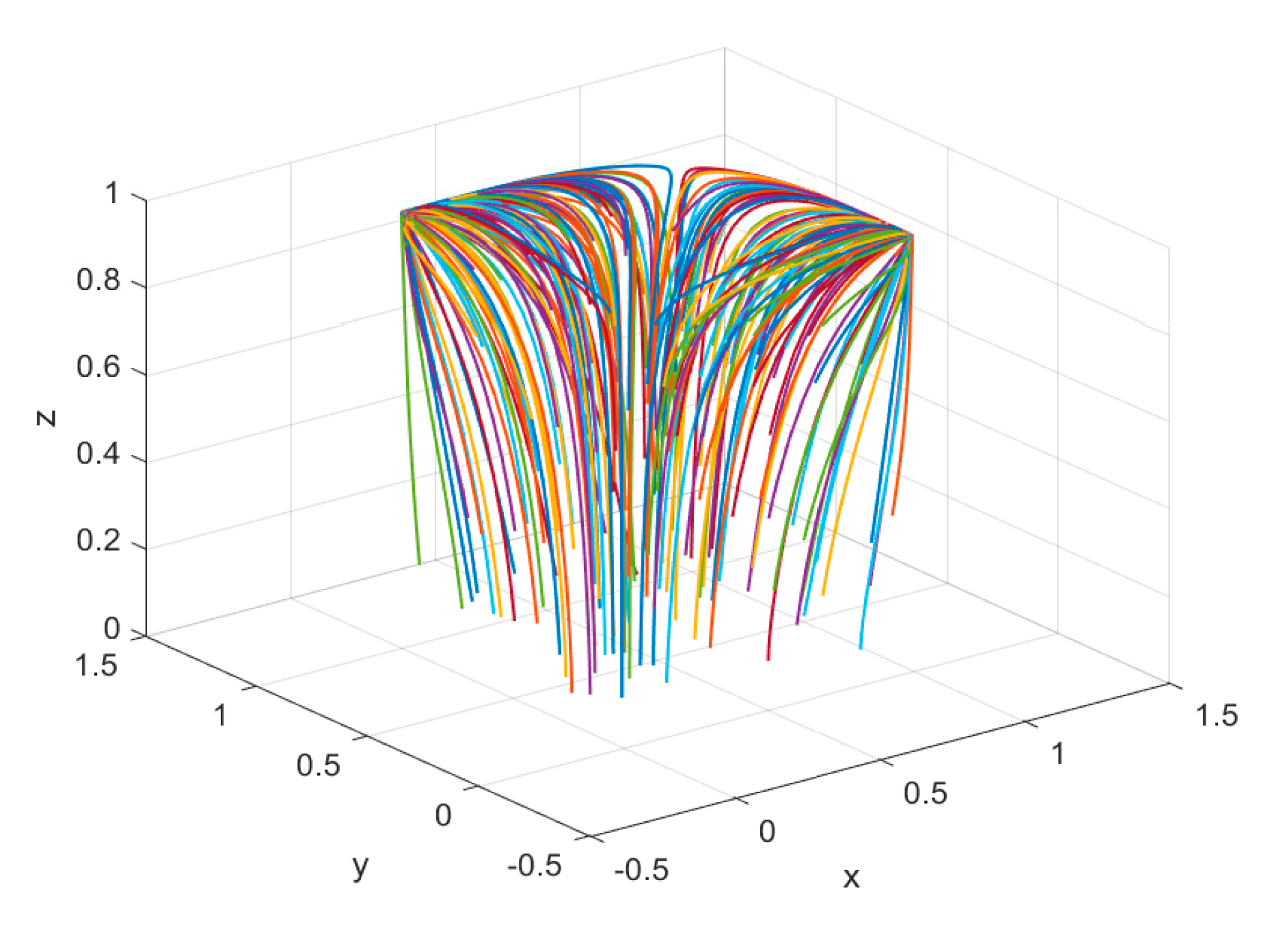
to be asymptotically stable. To analyze the impact of different initial strategy probabilities for each participant on the overall evolutionary path, initial strategy probability combinations
are randomly selected within
. The evolutionary results are shown in
Figure 2. Although different initial strategy probabilities lead to different evolutionary rates, they all converge to
and
, confirming the correctness of the theoretical derivation.
Next, we conducted a simulation of the attack−defense evolution process of the UTC system based on the data from Case Study I [
21]. The system security value (S) was set to 200, and the security requirements were represented by
. The TPR and FPR were set to
α = 91.78%,
β = 0.25%, respectively. The initial state of the game was set to
. After 50 iterations, we obtained the replicating dynamics of the evolving game, as shown in
Figure 3. The trajectory exhibits a spiral convergence, indicating a mixed−strategy equilibrium. At this point
, the attacker tends to abandon the attack, while both UC and TSM adopt active defense.
To compare the security systems of the UC and TSM, we set
, while keeping the other parameters unchanged. After 50 iterations, we obtained the replicating dynamics of the evolving game, as shown in
Figure 4. The trajectory forms a closed loop around the central point, and there is no asymptotic ESS of the three-party game. In this scenario, TSM abandons defense due to its high cost, and the ratio between the attacker and UC remains in constant flux.
In order to analyze the influence of each parameter on the three-party strategy selection, we set the parameters to satisfy the condition of a pure strategy equilibrium point , with α = 40% and keeping the other parameters unchanged. Then, we varied one of the parameters and observed the changes in the trajectory.
First, we analyze the impact of the detection rate on the evolutionary process and results. Setting the detection rate
, the results after 50 iterations are shown in
Figure 5. Decreasing the detection rate accelerates the evolutionary rate of the attacker’s strategy choice of attack. With an increased detection rate, the UC’s probability of adopting the defense strategy increases, while the attacker’s probability of choosing the attack strategy decreases. Therefore, information security personnel should strengthen the research and development of corresponding attack detection technologies to increase the detection rate and reduce the probability of system attacks.
Next, we analyze the impact of defense cost on the evolutionary process and results. Setting the defense cost
, the results after 50 iterations are shown in
Figure 6. The results show that during the evolutionary process, as the defense cost increases, the UC’s probability of adopting the defense strategy decreases, while the attacker’s probability of choosing the attack strategy increases. Therefore, reducing the cost of defense strategies is an effective means of ensuring the safe and stable operation of the traffic system.
Lastly, we analyze the impact of the attack cost. Setting the attack cost
, the results after 50 iterations are shown in
Figure 7. It can be observed that as the attack cost increases, the UC’s probability of adopting the defense strategy increases, while the attacker’s probability of choosing the attack strategy decreases. From a system design perspective, designers should focus on designing more secure systems, increasing the cost of attacks, and reducing the probability of being attacked.
6. Discussion
The simulated results above reveal the impact of the main parameters on the three-party behavioral strategy evolution and provide different final states of the three-party game evolution under various conditions, which can increase the probability of attackers abandoning their attacks. We found that higher detection rates and comparable attack and defense costs can effectively encourage attackers to abandon their attacks. Lower TPR and higher defense costs can significantly increase the probability of the UTC system being attacked, leading to a tendency for defenders to abandon defense, which is highly dangerous.
The factors influencing the evolutionary dynamics of the UTC system information security can be divided into three priority levels based on their impact. The first priority is TPR, the second priority is defense cost, and the third priority is attack cost. Based on the simulation results, we combined the probabilities of attack and defense to determine the degree of influence of these factors. As shown in
Figure 5,
Figure 6 and
Figure 7, among all the influencing factors, TPR has the most significant impact, followed by defense cost, while the impact of attack cost is the smallest.
In comparison with the Bayesian game method in [
21], the evolutionary game approach allows for a more intuitive understanding of the degree of influence of each parameter on the three-party strategy selection. It helps identify various final evolutionary game states and their corresponding conditions, as well as the evolutionary process from the initial state to the final state. The accuracy of the analysis results of the Bayesian game method is highly dependent on the selection of prior probabilities. Therefore, our approach is more advantageous in assisting researchers in analyzing information security issues in UTC systems.
7. Conclusions
The issue of information security in UTC systems has received relatively little attention. However, as they become increasingly integrated with various information networks, information security concerns are becoming more prominent. In this paper, a three-party evolutionary game model was constructed to analyze the network structure of UTC systems and the interactions between attackers, the UC, and the TSM. The stability of strategy choices for each party, the stability of equilibrium strategy combinations in the game system, and the relationships between various factors were analyzed. The validity of the conclusions was verified through simulation analysis. The main conclusions and insights are as follows.
In situations where the attack detection rate is high and the attack defense costs are unequal, there is no asymptotic ESS, and the behavior of the participants exhibits periodic characteristics. However, in situations where the attack detection rate is high and the attack defense costs are equal, the system trajectory converges in a spiral and then stabilizes. This finding suggests that UTC systems’ security personnel can gradually reduce the probability of system attacks by controlling the TPR and costs.
The attack detection rate and defense cost are negatively correlated with the probability of system attacks and positively correlated with the defense rate. These parameters can be further optimized and prioritized based on their impact on the evolutionary dynamics of the system’s attack and defense. Therefore, security personnel should focus their efforts on developing strategies that address specific priorities.
Finally, as the attack detection rate decreases and defense costs increase to a certain extent, the system will tend to abandon defense and the probability of being attacked will significantly increase. Therefore, UTC systems’ security personnel should continuously monitor new attack methods in the field of information security, and regularly update the system’s detection and defense methods.