Attribute-Based Proxy Signature Scheme Supporting Flexible Threshold Predicate for UAV Networks
Abstract
:1. Introduction
1.1. Problem Statement
- Using a proxy signature scheme may help UAVs execute commands promptly in UAV networks.
- Using an ABS scheme, a UAV verifies the signature to confirm that the signer’s attributes meet the requirements. The UAV does not obtain the signer’s identity, which protects the signer’s privacy.
1.2. Our Contributions
1.3. Structure of the Paper
2. Related Work
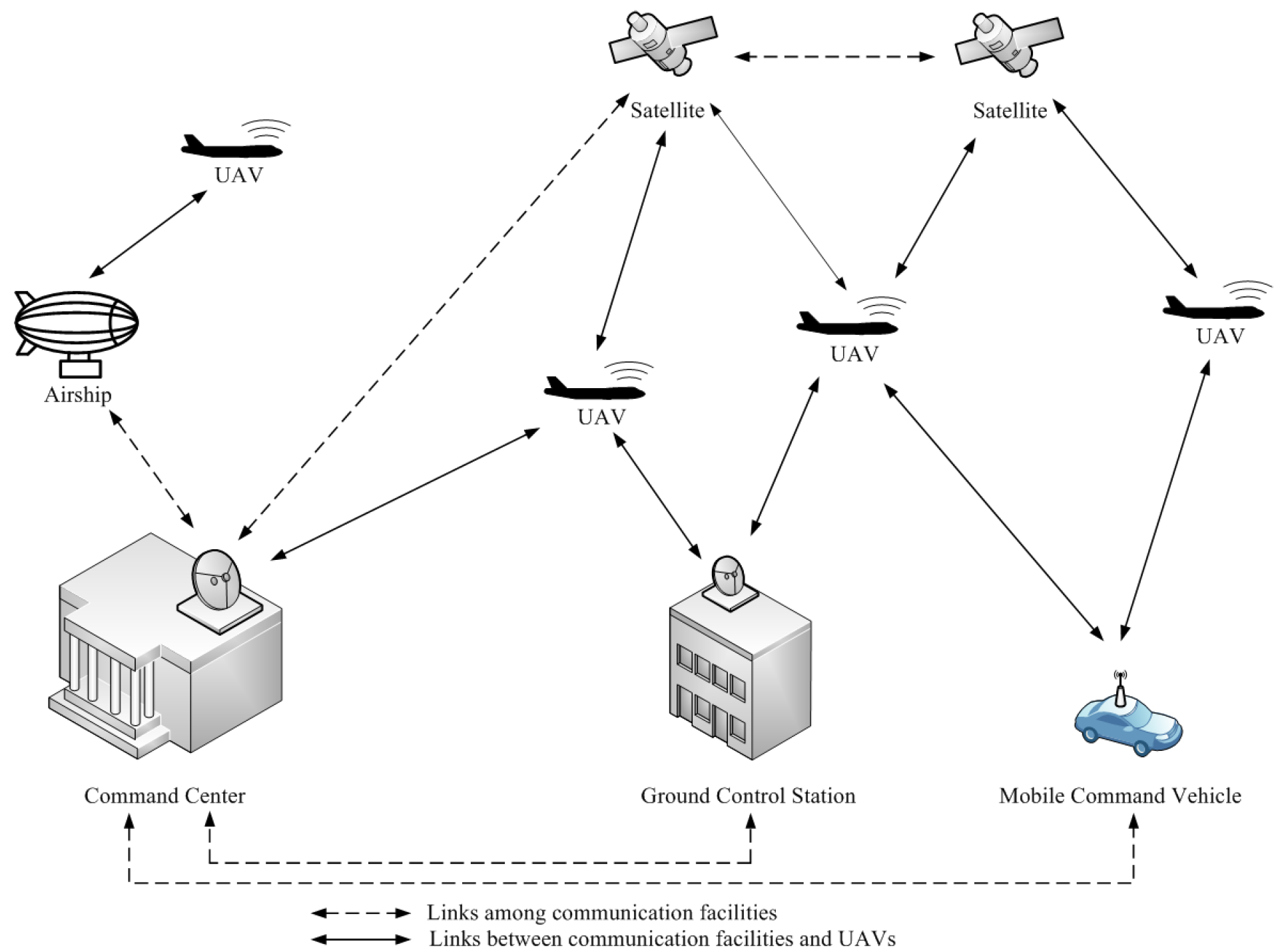
2.1. Security Solutions for UAV Networks
2.2. ABS Schemes
2.3. Proxy Signature Schemes
3. Preliminaries
3.1. Complexity Assumption
3.2. Supported Predicate
3.3. Lagrange Interpolation
4. ABPS Scheme for UAV Networks
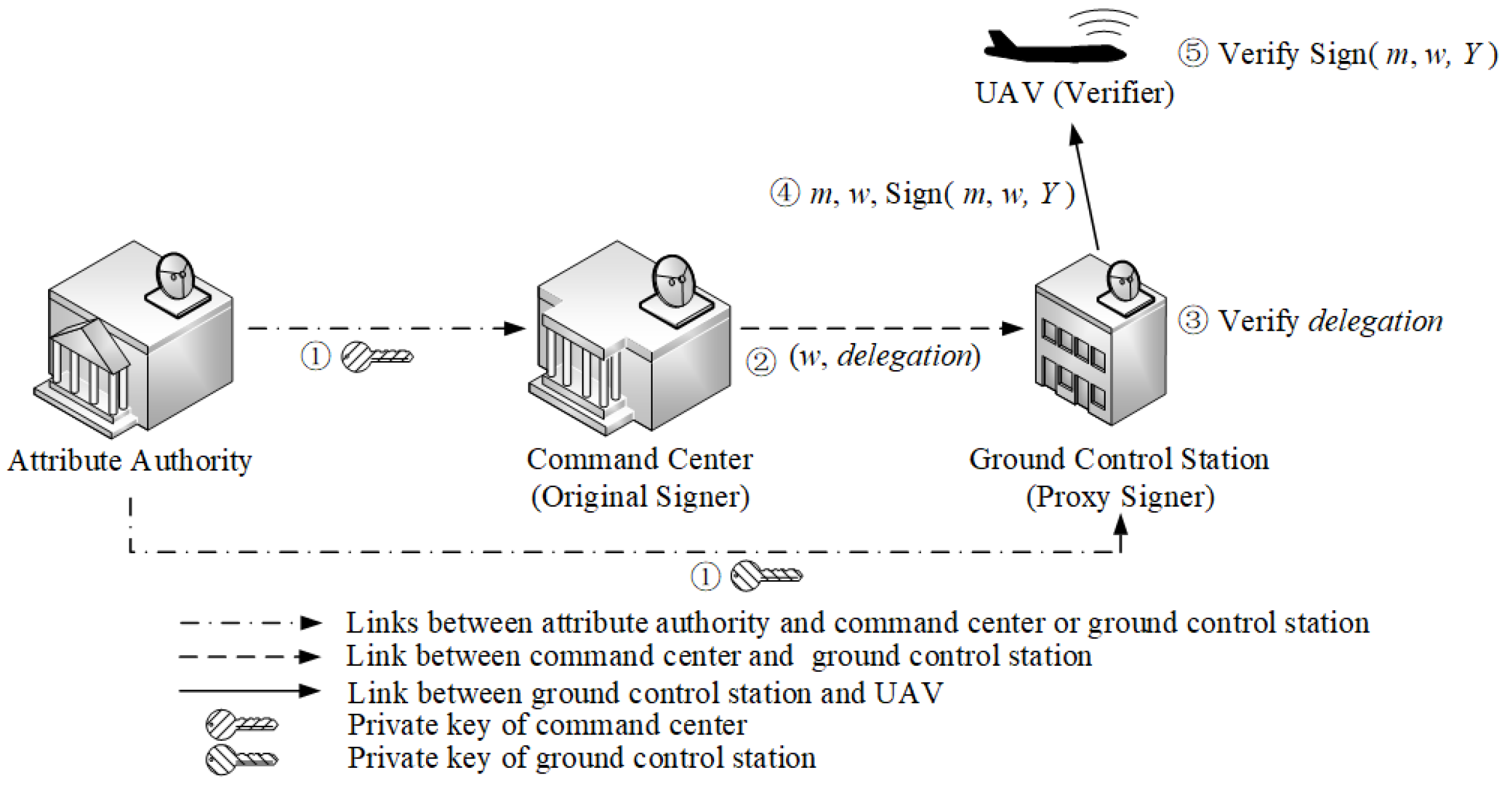
4.1. Overview
- The attribute authority generates system parameters. It generates based on the attribute set . Similarly, it also generates based on the attribute set . The default attribute set is added to achieve a flexible threshold predicate in this system, which allows a user to change threshold value in the predicate without proposing a new signature scheme.
- The command center generates a warrant w and uses its attribute set and private key to compute the delegation on for the GCS.
- The GCS verifies the delegation. If it is valid, the GCS will keep the delegation.
- Based on the delegation, the GCS uses its attribute set and to compute the proxy signature on .
- The UAV verifies the signature and outputs the result.
4.2. Our ABPS Scheme
- (1)
- Setup
- (2)
- Extract
- (3)
- DelGen
- (4)
- DelVer
- (5)
- SignThe proxy signer performs the following steps.
- (i)
- It selects a subset with and a default attribute set with .
- (ii)
- It generates random numbers for and a random number .
- (iii)
- It computes , , , and .
- (iv)
- The proxy signer sends to the verifier.
- (6)
- Verify
5. Formal Model and Security Model
5.1. Formal Model
- (1)
- Setup: It inputs the system security parameter and outputs public parameters and a master secret key .
- (2)
- Extract: The attribute authority computes for the original signer based on attribute set . It also computes for the proxy signer based on attribute set .
- (3)
- DelGen: The inputs of this algorithm include , a warrant w, predicate where , and . This algorithm outputs a delegation .
- (4)
- DelVer: Its inputs include , w, , and . This algorithm determines whether the is valid. If it is valid, the proxy signer will keep the delegation.
- (5)
- Sign: Its inputs include , w, , predicate where , , and message m. It outputs the proxy signature .
- (6)
- Verify: Its inputs include , w, , m, and . This algorithm determines whether the signature is valid. If it is valid, the verifier will output a boolean value . Otherwise, it will output a boolean value .
5.2. Security Model
5.2.1. Unforgeability
- : The adversary only has the public key of the original signer and the public key of the proxy signer .
- : The adversary has , , and .
- : The adversary has , , and .
- (1)
- Initialization: chooses the challenge predicate .
- (2)
- Setup: A challenger selects the security parameter and generates and . It runs algorithm Extract to generate , , , and . keeps and secret and sends and to .
- (3)
- Queries: can query the private key extraction oracle, delegation generation oracle, and signing oracle.
- (4)
- Forgery: outputs the signature .
- has never submitted where there is not a subset satisfying to the private key extraction oracle.
- has never submitted (, ) to the delegation generation oracle.
- has never submitted (, , ) to the signing oracle.
- The is valid.
- (1)
- Initialization: chooses the challenge predicate .
- (2)
- Setup: runs algorithm Extract to generate , , , and . keeps and secret and sends and to .
- (3)
- Queries: can query the private key extraction oracle and signing oracle.
- (4)
- Forgery: outputs the signature .
- has never submitted where there is not a subset satisfying to the private key extraction oracle.
- has never submitted (, , ) to the signing oracle.
- The is valid.
5.2.2. Signer’s Privacy
- (1)
- Setup: chooses security parameter and generates and .
- (2)
- Queries: queries two attribute sets and to obtains private keys and .
- (3)
- Challenge: outputs a message , , , and predicate, which satisfies and . randomly chooses and computes signature on with . It sends to .
- (4)
- Guess: guesses was computed from or and outputs . If guesses that was computed from , it will output . Otherwise, it will output . If , wins this game.
6. ABPS Scheme Analysis
6.1. Correctness
6.2. Security Analysis
6.2.1. Unforgeability
- If , generates the delegation normally by obtaining the simulated private key.
- If and , it is aborted.
- If and , selects a random subset with from . It sets and simulates as , , . Here, is a random number and .
6.2.2. Signer’s Privacy
6.3. Efficiency Analysis
6.3.1. Computation Costs
6.3.2. Communication Costs
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Gupta, L.; Jain, R.; Vaszkun, G. Survey of important issues in UAV communication networks. IEEE Commun. Surv. Tutorials 2016, 18, 1123–1152. [Google Scholar] [CrossRef]
- Guo, J.; Gao, H.; Liu, Z.; Huang, F.; Zhang, J.; Li, X.; Ma, J. ICRA: An intelligent clustering routing approach for UAV ad hoc networks. IEEE Trans. Intell. Transp. Syst. 2023, 24, 2447–2460. [Google Scholar] [CrossRef]
- Samanth, S.; Prema, K.V.; Balachandra, M. Security in Internet of drones: A comprehensive review. Cogent Eng. 2022, 9, 2029080. [Google Scholar] [CrossRef]
- Khan, M.A.; Ullah, I.; Nisar, S.; Noor, F.; Qureshi, I.M.; Khanzada, F.; Khattak, H.; Aziz, M.A. Multiaccess edge computing empowered flying ad hoc networks with secure deployment using identity-based generalized signcryption. Mob. Inf. Syst. 2020, 2020, 8861947. [Google Scholar] [CrossRef]
- Khan, M.A.; Shah, H.; Rehman, S.U.; Kumar, N.; Ghazali, R.; Shehzad, D.; Ullah, I. Securing Internet of drones with identity-based proxy signcryption. IEEE Access 2021, 9, 89133–89142. [Google Scholar] [CrossRef]
- Din, N.; Waheed, A.; Zareei, M.; Alanazi, F. An improved identity-based generalized signcryption scheme for secure multi-access edge computing empowered flying ad hoc networks. IEEE Access 2021, 9, 120704–120714. [Google Scholar] [CrossRef]
- Pan, X.; Jin, Y.; Wang, Z.; Li, F. A pairing-free heterogeneous signcryption scheme for unmanned aerial vehicles. IEEE Internet Things J. 2022, 9, 19426–19437. [Google Scholar] [CrossRef]
- Khan, M.A.; Ullah, I.; Abdullah, A.M.; Mohsan, S.A.H.; Noor, F. An efficient and conditional privacy-preserving heterogeneous signcryption scheme for the Internet of drones. Sensors 2023, 23, 1063. [Google Scholar] [CrossRef] [PubMed]
- Khan, M.A.; Ullah, I.; Nisar, S.; Noor, F.; Qureshi, I.M.; Khanzada, F.U.; Amin, N.U. An efficient and provably secure certificateless key-encapsulated signcryption scheme for flying ad-hoc network. IEEE Access 2020, 8, 36807–36828. [Google Scholar] [CrossRef]
- Khan, M.A.; Qureshi, I.M.; Ullah, I.; Khan, S.; Khanzada, F.; Noor, F. An efficient and provably secure certificateless blind signature scheme for flying ad-hoc network based on multi-access edge computing. Electronics 2020, 9, 30. [Google Scholar] [CrossRef]
- Qu, Y.; Zeng, J. Certificateless proxy signcryption in the standard model for a UAV network. IEEE INternet Things J. 2022, 9, 15116–15127. [Google Scholar] [CrossRef]
- Liu, Z.; Guo, J.; Huang, F.; Cai, D.; Wu, Y.; Chen, X.; Igorevich, K.K. Lightweight trustworthy message exchange in unmanned aerial vehicle networks. IEEE Trans. Intell. Transp. Syst. 2023, 24, 2144–2157. [Google Scholar] [CrossRef]
- Guo, J.; Liu, Z.; Tian, S.; Huang, F.; Li, J.; Li, X.; Igorevich, K.K.; Ma, J. TFL-DT: A trust evaluation scheme for federated learning in digital twin for mobile networks. IEEE J. Sel. Areas Commun. 2023, 41, 3548–3560. [Google Scholar] [CrossRef]
- Maji, H.K.; Prabhakaran, M.; Rosulek, M. Attribute-based signatures. In Proceedings of the Cryptographers’ Track at the RSA Conference 2011, San Francisco, CA, USA, 14–18 February 2011. [Google Scholar]
- Li, J.; Au, M.H.; Susilo, W.; Xie, D.; Ren, K. Attribute-based signature and its applications. In Proceedings of the 5th ACM Symposium on Information, Computer and Communications Security, Beijing, China, 13–16 April 2010. [Google Scholar]
- Su, J.; Cao, D.; Zhao, B.; Wang, X.; You, I. ePASS: An expressive attribute-based signature scheme with privacy and an unforgeability guarantee for the Internet of things. Future Gener. Comput. Syst. 2014, 33, 11–18. [Google Scholar] [CrossRef]
- Okamoto, T.; Takashima, K. Efficient attribute-based signatures for non-monotone predicates in the standard model. IEEE Trans. Cloud Comput. 2014, 2, 409–421. [Google Scholar] [CrossRef]
- Chen, X.; Li, J.; Huang, X.; Li, J.; Xiang, Y.; Wong, D.S. Secure outsourced attribute-based signatures. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 3285–3294. [Google Scholar] [CrossRef]
- Mo, R.; Ma, J.; Liu, X.; Liu, H. EOABS: Expressive outsourced attribute-based signature. Peer Peer Netw. Appl. 2018, 11, 979–988. [Google Scholar] [CrossRef]
- Huang, Z.; Duan, R.; Chen, Q.; Huang, H.; Zhou, Y. Secure outsourced attribute-based signatures with perfect anonymity in the standard model. Secur. Commun. Netw. 2021, 2021, 7884007. [Google Scholar] [CrossRef]
- Huang, Z.; Lin, Z.; Chen, Q.; Zhou, Y.; Huang, H. Outsourced attribute-based signatures with perfect privacy for circuits in cloud computing. Concurrency Comput. Pract. Exp. 2021, 33, e6173. [Google Scholar] [CrossRef]
- Cui, H.; Deng, R.H.; Liu, J.K.; Yi, X.; Li, Y. Server-aided attribute-based signature with revocation for resource-constrained industrial-Internet-of-things devices. IEEE Trans. Ind. Inform. 2018, 14, 3724–3732. [Google Scholar] [CrossRef]
- Xiong, H.; Bao, Y.; Nie, X.; Asoor, Y.I. Server-aided attribute-based signature supporting expressive access structures for industrial Internet of things. IEEE Trans. Ind. Inform. 2020, 16, 1013–1023. [Google Scholar] [CrossRef]
- Huang, Z.; Lin, Z. Secure server-aided attribute-based signature with perfect anonymity for cloud-assisted systems. J. Inf. Secur. Appl. 2022, 65, 103066. [Google Scholar] [CrossRef]
- Bao, Y.; Qiu, W.; Cheng, X. Efficient and fine-grained signature for IIoT with resistance to key exposure. IEEE Internet Things J. 2021, 8, 9189–9205. [Google Scholar] [CrossRef]
- Mambo, M.; Usuda, K.; Okamoto, E. Proxy signatures for delegating signing operation. In Proceedings of the 3rd ACM Conference on Computer and Communications Security, New Delhi, India, 14–15 March 1996. [Google Scholar]
- Huang, X.; Susilo, W.; Mu, Y.; Wu, W. Proxy signature without random oracles. In Proceedings of the Second International Conference on Mobile Ad-hoc and Sensor Networks, Hong Kong, China, 13–15 December 2006. [Google Scholar]
- Wu, W.; Mu, Y.; Susilo, W.; Seberry, J.; Huang, X. Identity-based proxy signature from pairings. In Proceedings of the 4th International Conference on Autonomic and Trusted Computing, Hong Kong, China, 11–13 July 2007. [Google Scholar]
- Verma, G.K.; Singh, B.B.; Kumar, N.; Obaidat, M.S.; He, D.; Singh, H. An efficient and provable certificate-based proxy signature scheme for IIoT environment. Inf. Sci. 2020, 518, 142–156. [Google Scholar] [CrossRef]
- Qiao, Z.; Zhou, Y.; Yang, B.; Zhang, M.; Wang, T.; Xia, Z. Secure and efficient certificate-based proxy signature schemes for industrial Internet of things. IEEE Syst. J. 2022, 16, 4719–4730. [Google Scholar] [CrossRef]
- Liu, X.; Ma, J.; Xiong, J.; Zhang, T.; Li, Q. Personal health records integrity verification using attribute based proxy signature in cloud computing. In Proceedings of the 6th International Conference on Internet and Distributed Computing Systems, Hangzhou, China, 28–30 October 2013. [Google Scholar]
- Sun, C.; Guo, Y.; Li, Y. One secure attribute-based proxy signature. Wirel. Pers. Commun. 2018, 103, 1273–1283. [Google Scholar] [CrossRef]
- He, L.; Ma, J.; Wei, D. Attribute-based proxy signature scheme for unmanned aerial vehicle networks. J. Commun. 2021, 42, 87–96. [Google Scholar]
- Caro, A.D.; Iovino, V. jPBC: Java pairing based cryptography. In Proceedings of the 2011 IEEE Symposium on Computers and Communications, Kerkyra, Greece, 28 June–1 July 2011. [Google Scholar]



| Acronym | Meaning |
|---|---|
| ABS | Attribute-based signature |
| FANET | Flying ad hoc network |
| IoD | Internet of drones |
| HSC | Heterogeneous signcryption |
| CL-KESC | Certificateless key-encapsulated signcryption |
| CL-BS | Certificateless blind signature |
| CL-PSC | Certificateless proxy signcryption |
| OABS | Outsourced attribute-based signature |
| S-CSP | Signing-cloud service provider |
| LSSS | Linear secret-sharing scheme |
| SA-ABS | Server-aided attribute-based signature |
| CBPS | Certificate-based proxy signature |
| ABPS | Attribute-based proxy signature |
| Security Solutions | Confidentiality | Integrity | Authentication |
|---|---|---|---|
| Din et al. [6] | √ | √ | √ |
| Pan et al. [7] | √ | √ | √ |
| Khan et al. [9] | √ | √ | √ |
| Signature Schemes | Authentication | Signer’s Privacy | Flexible Threshold Predicate |
|---|---|---|---|
| Our ABPS | √ | √ | √ |
| ABPS-LXM | √ | √ | √ |
| ABPS-SCX | √ | √ | × |
| ABPS-HL | √ | √ | × |
| Signature Schemes | Exponential Operation | Hash Operation | Pairing Operation |
|---|---|---|---|
| Our ABPS | 2n + 4d − 2k + 2 | n + d − k + 1 | 0 |
| ABPS-LXM | (n + d − k)(n + 4) + 2d + 4 | 0 | 0 |
| ABPS-SCX | 2 | 1 | 0 |
| ABPS-HL | 6d | d + 1 | 0 |
| Signature Schemes | Exponential Operation | Hash Operation | Pairing Operation |
|---|---|---|---|
| Our ABPS | 0 | 2(n + d − k + 1) | 2(n + d − k) + 3 |
| ABPS-LXM | 2(n + d − k)(n + 2) | 0 | 2(n + d − k) + 3 |
| ABPS-SCX | (n + 3)d | 2 | 3d + 2 |
| ABPS-HL | 2d | 2d + 2 | 4d + 1 |
| Basic Operation | Computation Time (ms) |
|---|---|
| Exponential operation | 8.96 |
| Hash operation | 19.84 |
| Pairing operation | 9.61 |
| Signature Schemes | Signature Length |
|---|---|
| Our ABPS | |
| ABPS-LXM | |
| ABPS-SCX | |
| ABPS-HL |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
He, L.; Gan, Y.; Zhang, Y. Attribute-Based Proxy Signature Scheme Supporting Flexible Threshold Predicate for UAV Networks. Electronics 2023, 12, 4854. https://doi.org/10.3390/electronics12234854
He L, Gan Y, Zhang Y. Attribute-Based Proxy Signature Scheme Supporting Flexible Threshold Predicate for UAV Networks. Electronics. 2023; 12(23):4854. https://doi.org/10.3390/electronics12234854
Chicago/Turabian StyleHe, Lei, Yong Gan, and Yanhua Zhang. 2023. "Attribute-Based Proxy Signature Scheme Supporting Flexible Threshold Predicate for UAV Networks" Electronics 12, no. 23: 4854. https://doi.org/10.3390/electronics12234854
APA StyleHe, L., Gan, Y., & Zhang, Y. (2023). Attribute-Based Proxy Signature Scheme Supporting Flexible Threshold Predicate for UAV Networks. Electronics, 12(23), 4854. https://doi.org/10.3390/electronics12234854





