An Efficient and Secure Blockchain Consensus Protocol for Internet of Vehicles
Abstract
:1. Introduction
1.1. Research Backgrounds
1.2. Related Work
1.3. Research Contributions
- (1)
- We propose a blockchain consensus model suitable for the IoV environment, employing a permissioned chain mechanism involving entities such as Onboard Units (OBUs) and Roadside Units (RSUs). The consensus process is divided into the Pre-prepare, Prepare1, Prepare2, Commit1, and Commit2 phases.
- (2)
- Based on the above consensus model, we introduce the ESBCP consensus protocol tailored for the IoV environment. This protocol integrates various strategies including trust assessment mechanisms, node partition, Dynamic Unique Node List (DUNL), and improved consensus algorithms. It addresses the high latency and difficult adaptability issues present in the classical PBFT algorithm.
- (3)
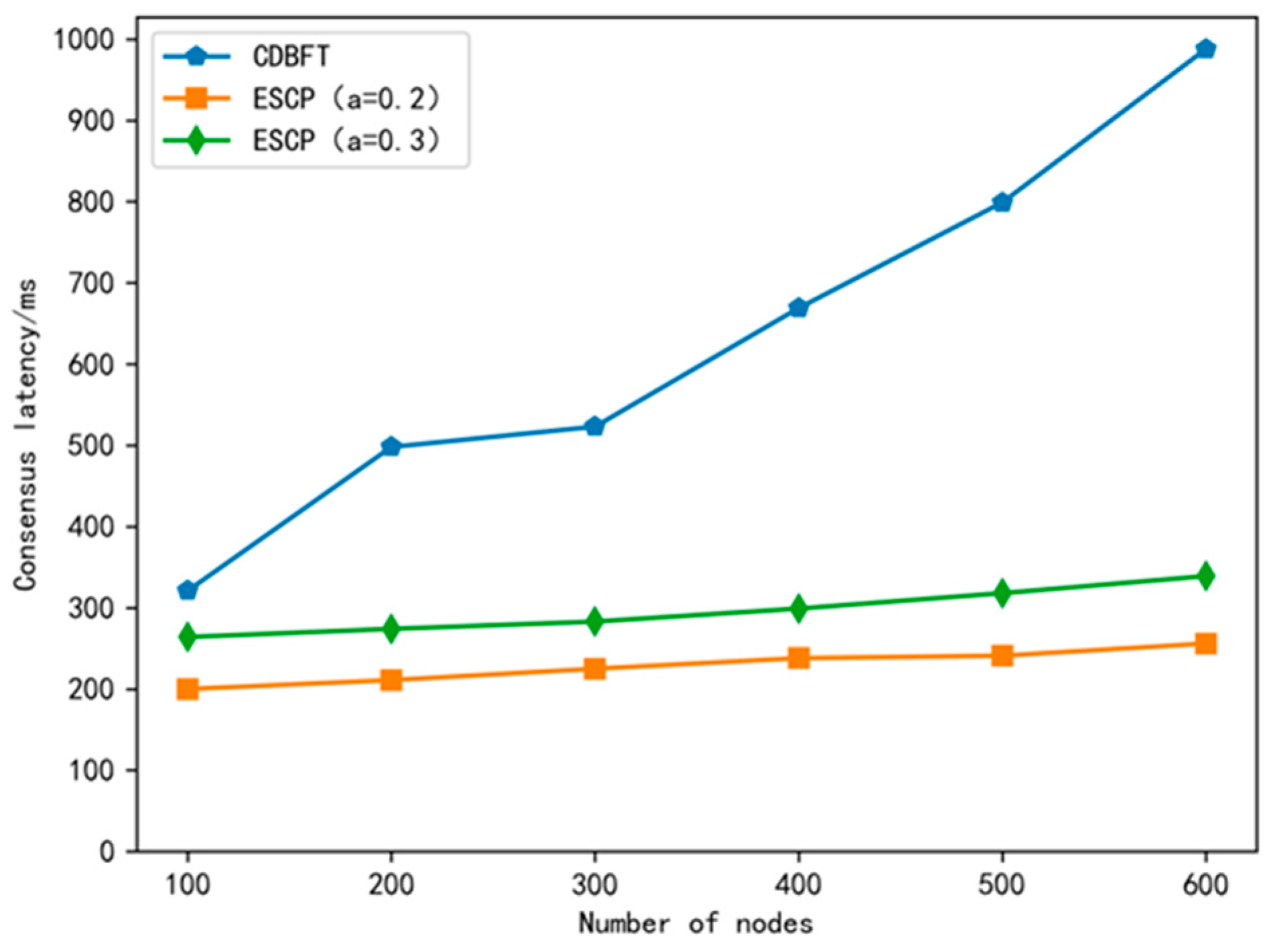
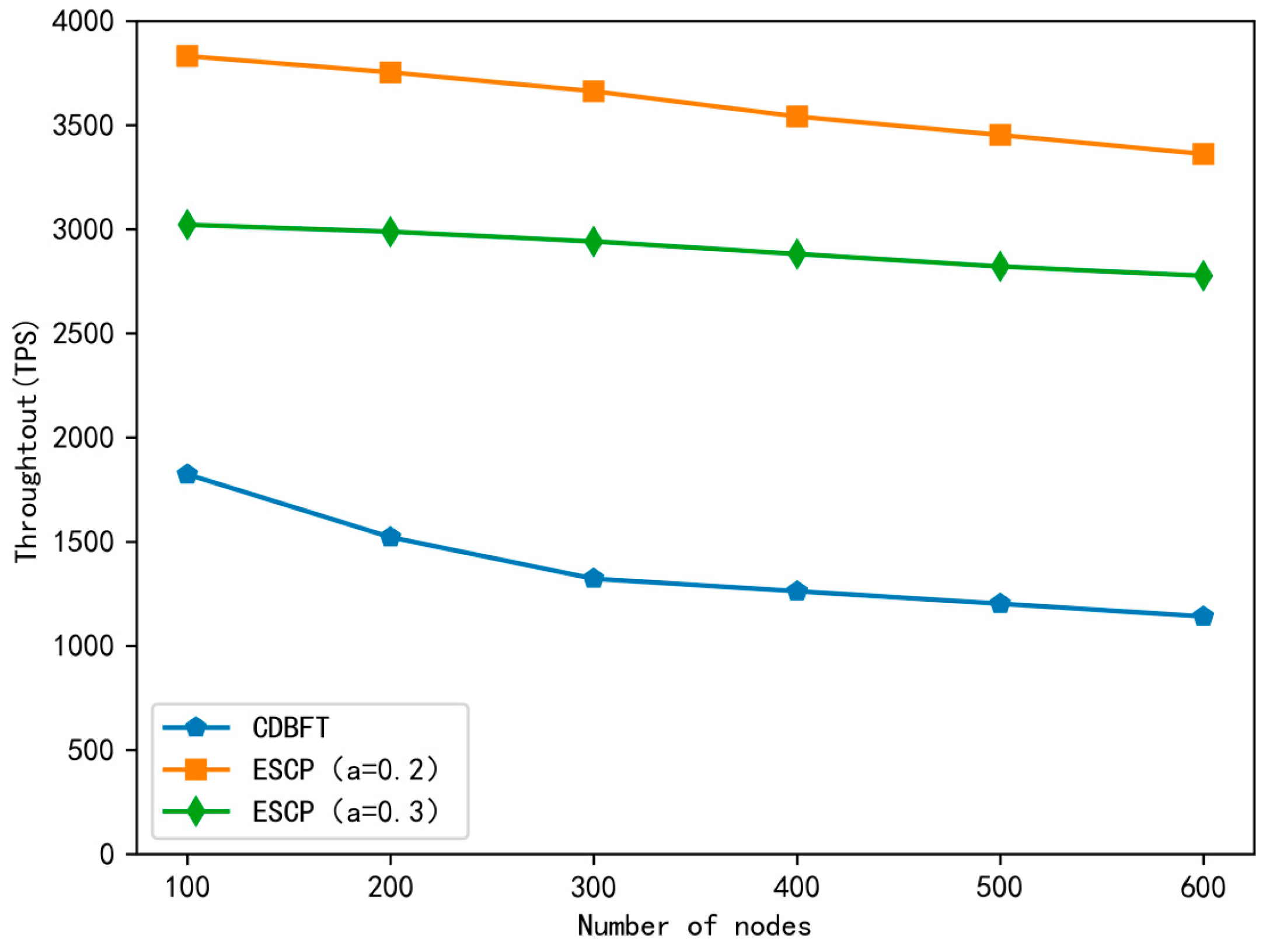
- We conduct detailed theoretical analysis and comparative experimental validation of the ESBCP consensus protocol. The theoretical analysis demonstrates the effectiveness of ESBCP in preventing external and internal security risks. The communication complexity of ESBCP is O(n). The protocol exhibits excellent scalability. Comparative experiments indicate that, in contrast to the CDBFT and SG-PBFT algorithms, ESBCP achieves lower latency, higher throughput, and is more suitable for large-scale IoV environments.
2. Preliminary Knowledge
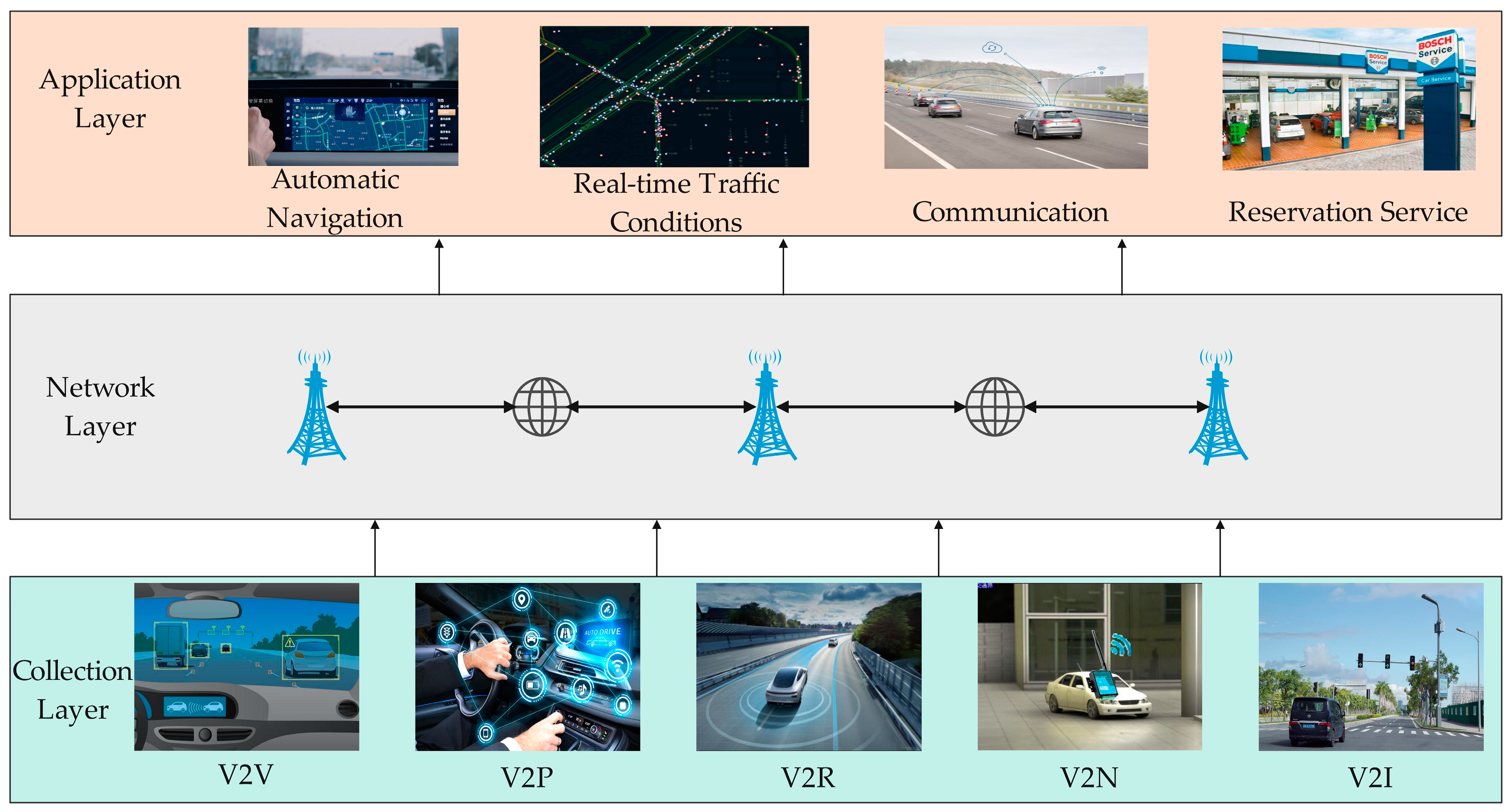
2.1. Internet of Vehicles (IoV)
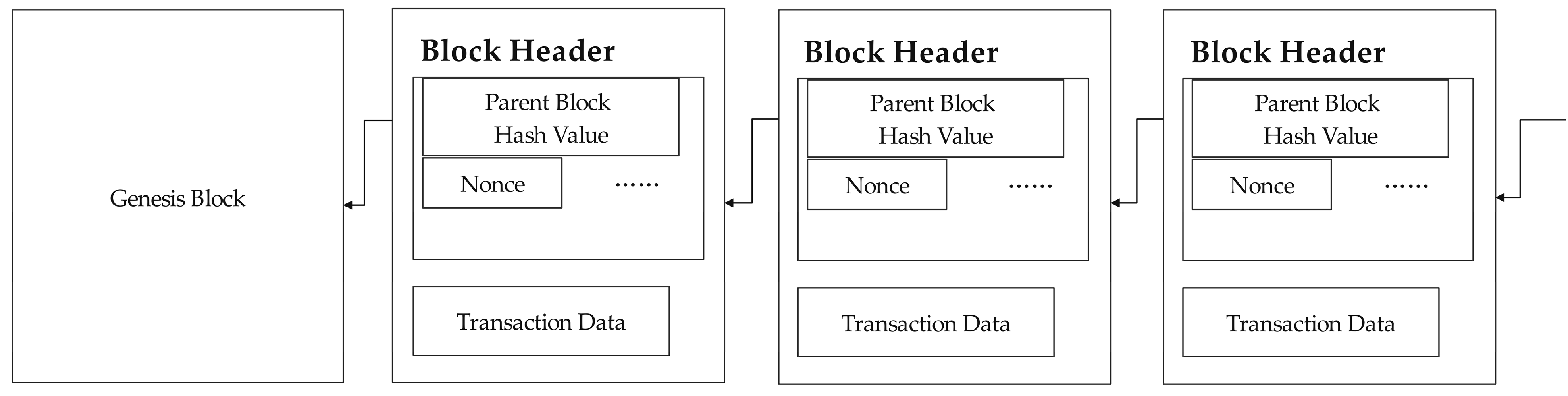
2.2. Blockchain
2.3. PBFT Consensus Algorithm
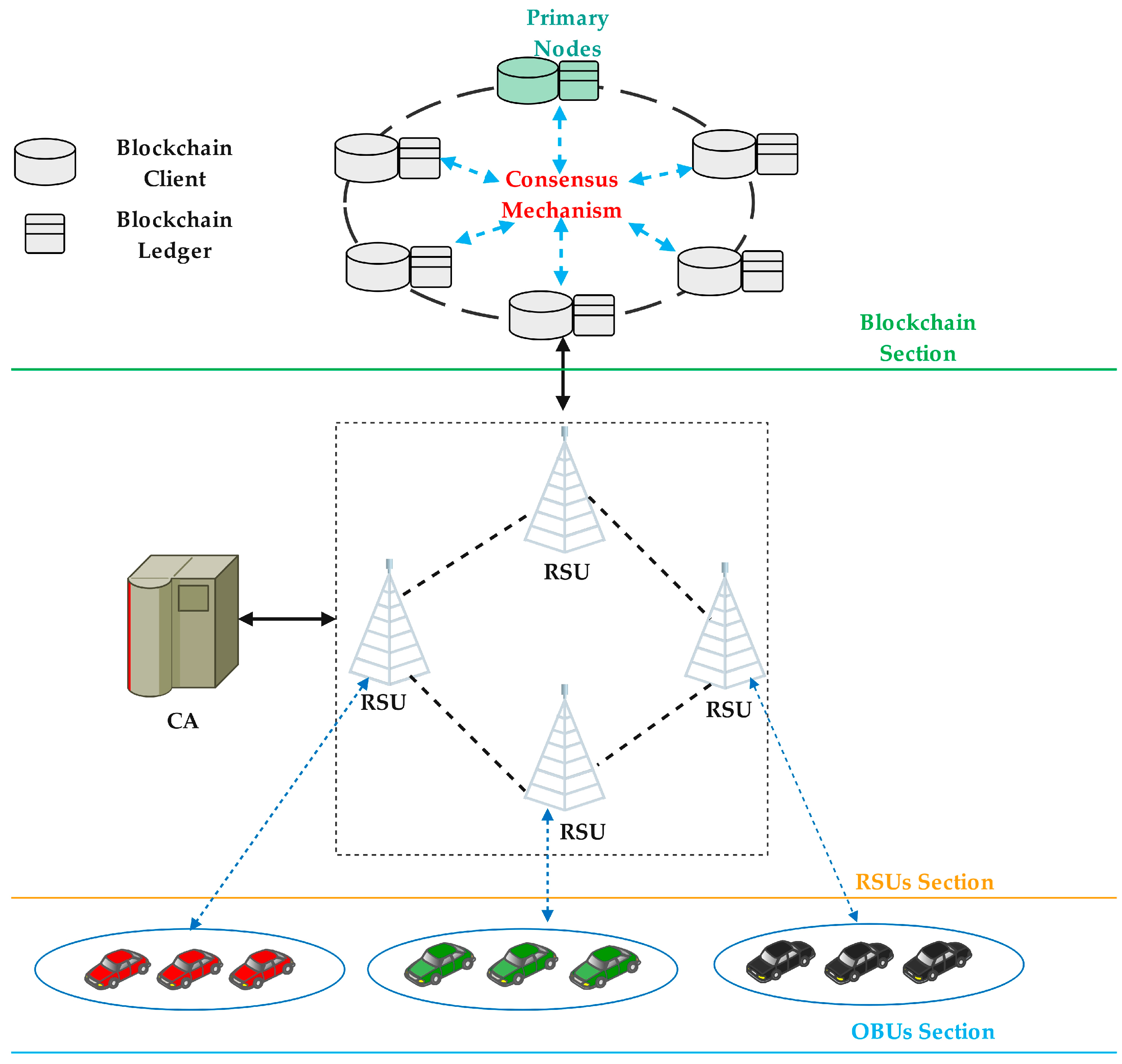
3. Blockchain Consensus Model for Vehicular Networks
- (1)
- RSUs select high-quality vehicle nodes from the OBU section to participate in consensus based on trust assessment algorithms and an improved algorithm using a unique node list.
- (2)
- Node partition algorithm design is carried out by calculating the similarity between nodes based on communication delay, route hops, and distance.
- (3)
- Consensus nodes in the blockchain section proceed with the corresponding partition’s DK-PBFT (Dynamic K-medoids Practical Byzantine Fault Tolerance) consensus process. DK-PBFT includes the Pre-prepare, Prepare1, Prepare2, Commit1, and Commit2 phases.
4. ESBCP Consensus Protocol Design and Implementation
4.1. Trust Assessment Algorithm
| Algorithm 1: Trust Value Calculation |
| Input: (), , , |
| Output: |
| 1: set 0; ; ; |
| 2: for ; ; do |
| 3: for |
| 4: ; |
| 5: if then |
| 6: ; |
| 7: else |
| 8: ; |
| 9: end if |
| 10: end for |
| 11: ; |
| 12: ; |
| 13: ; |
| 14: end for |
4.2. Node Partition Algorithm
4.3. Improved UNL Algorithm
4.4. DK-PBFT Consensus Algorithm
- (1)
- Pre-prepare Phase: After verifying the signature of the received request information , each primary node broadcasts a pre-prepare message to other primary nodes. In this message, identifies the pre-prepare message for consensus, represents the signature of the primary node on pre-prepare message , is the sequence number assigned by the primary nodes to message , and message comprises the original transaction request set with the signature of the client. Primary nodes also broadcast pre-prepare messages to the participating consensus nodes in their respective vicinity.
- (2)
- Prepare1 Phase: Upon receiving the Pre-prepare message from the primary nodes, the consensus nodes first verify the signature and sequence number of the message. After successful verification, it takes the union of transactions from different primary nodes and sorts them based on timestamps. The resulting transaction set is denoted as . The consensus node then sends a message to the primary nodes, where is the hash value of transaction set .
- (3)
- Prepare2 Phase: When the primary nodes receive the Prepare1 message from more than nodes, it compares the hash values from each message. If the hash values from more than nodes are the same, the primary nodes broadcast a message to all nodes, where represents the collection of messages received by the primary nodes.
- (4)
- Commit1 Phase: After receiving the Prepare2 message, normal nodes vote on the message and then send the voting information back to the primary nodes.
- (5)
- Commit2 Phase: When the master node receives the Commit1 message from over nodes, it performs a weighted calculation to decide whether to add the information shared by these vehicle nodes to the blockchain. After successful verification, the primary nodes package these transactions into a block. The primary nodes broadcast this block to all RSU nodes. When the block is validated by all consensus nodes, it signifies the completion of consensus and successful blockchain integration.
| Algorithm 2: DK-PBFT |
| Input: |
| Output: |
| 1: ; |
| 2: while do |
| 3: broadcast ; |
| 4: if |
| 5: ; |
| 6: ; |
| 7: ; |
| 8: end if |
| 9: if |
| 10: if |
| 11: ; |
| 12: end if |
| 13: end if |
| 14: if |
| 15: ; |
| 16: end if |
| 17: if |
| 18: ; |
| 19: end if |
| 20: if then |
| 21: do ; |
| 22: reply to the client; |
| 23: end if |
| 24: ; |
| 25: ; |
| 26: ; |
| 27: ; |
| 28: return ; |
| 29: end while |
5. Theoretical Analysis
5.1. Security Analysis
5.2. Communication Overhead Analysis
6. Experimental Analysis
6.1. Consensus Latency
6.2. Throughput
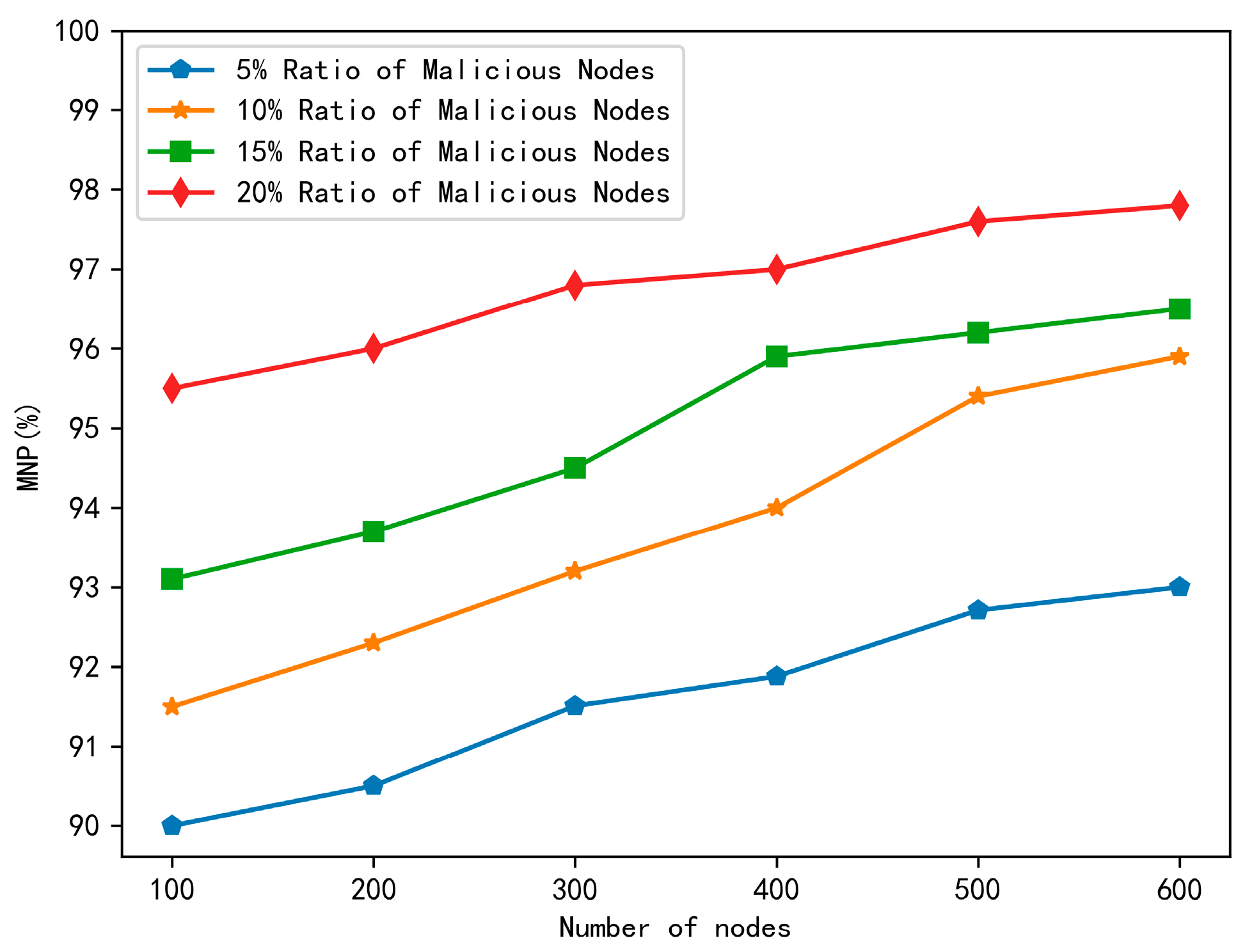
6.3. Malicious Node Precision
6.4. Malicious Node Recall
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Ren, Y.; Zhu, F.; Wang, J.; Sharma, P.K.; Ghosh, U. Novel vote scheme for decision-making feedback based on blockchain in internet of vehicles. IEEE Trans. Intell. Transp. Syst. 2021, 23, 1639–1648. [Google Scholar] [CrossRef]
- Wang, H.Y.; Guo, K.X.; Pan, Q.Q. Byzantine fault tolerance consensus algorithm based on voting mechanism. J. Comput. Appl. 2019, 39, 1766–1771. [Google Scholar]
- Li, Y.; Wang, Z.; Fan, J.; Zheng, Y.; Luo, Y.; Deng, C.; Ding, J. An extensible consensus algorithm based on PBFT. In Proceedings of the 2019 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery (CyberC), Guilin, China, 17–19 October 2019; pp. 17–23. [Google Scholar]
- Lao, L.; Dai, X.; Xiao, B.; Guo, S. G-pbft: A location-based and scalable consensus protocol for iot-blockchain applications. In Proceedings of the 2020 IEEE International Parallel and Distributed Processing Symposium (IPDPS), New Orleans, LA, USA, 18–22 May 2020; pp. 664–673. [Google Scholar]
- Wang, R.H.; Zhang, L.F.; Xu, Q.Q.; Zhou, H. Byzantine fault tolerance algorithm for consortium blockchain. Appl. Res. Comput. 2020, 37, 3382–3386. [Google Scholar]
- Du, N.; Liang, Z.; Huang, Y.; Guo, Z.; Yang, H.; Wang, S. Performance optimisation Method of PBFT Consensus for Supply Chain Integration SVM. In Proceedings of the 2020 7th International Conference on Dependable Systems and Their Applications (DSA), Xi’an, China, 28–29 November 2020; pp. 371–377. [Google Scholar]
- Seo, J.; Ko, D.; Kim, S.; Park, S. A Coordination Technique for Improving Scalability of Byzantine Fault-Tolerant Consensus. Appl. Sci. 2020, 10, 7609. [Google Scholar] [CrossRef]
- Ren, X.L.; Zhang, L. Improved multi-primary-node consensus mechanism based on practical Byzantine fault tolerance. J. Comput. Appl. 2022, 42, 1500–1507. [Google Scholar]
- Kumar, A.; Vishwakarma, L.; Das, D. R-PBFT: A secure and intelligent consensus algorithm for Internet of vehicles. Veh. Commun. 2023, 41, 100609. [Google Scholar] [CrossRef]
- Chen, Z.H.; Li, Q. Improved PBFT Consensus Mechanism Based on K-medoids. Comput. Sci. 2019, 46, 101–107. [Google Scholar]
- Liu, W.; Ruan, M.J.; She, W.; Zhang, Z.H.; Tian, Z. PBFT Optimized Consensus Algorithm for Internet of Things. Comput. Sci. 2021, 48, 151–158. [Google Scholar]
- Zhang, X.; Li, R.; Zhao, H. A Parallel Consensus Mechanism Using PBFT Based on DAG-Lattice Structure in the Internet of Vehicles. IEEE Internet Things J. 2022, 10, 5418–5433. [Google Scholar] [CrossRef]
- Yu, G.; Wu, B.; Niu, X. Improved blockchain consensus mechanism based on PBFT algorithm. In Proceedings of the 2020 2nd International Conference on Advances in Computer Technology, Information Science and Communications (CTISC), Suzhou, China, 20–22 March 2020; pp. 14–21. [Google Scholar]
- Xu, G.Q.; Bai, H.P.; Xing, J.; Luo, T.; Xiong, N.N.; Cheng, X.C.; Liu, S.Y.; Zheng, X. SG-PBFT: A secure and highly efficient distributed blockchain PBFT consensus algorithm for intelligent Internet of vehicles. J. Parallel Distrib. Comput. 2022, 164, 1–11. [Google Scholar] [CrossRef]
- Duan, J.; Lü, X.; Liu, F. Hierarchical Consensus Optimization of Blockchain Based on Trust Delegation. Comput. Eng. 2020, 46, 120–130+136. [Google Scholar]
- Wang, Y.; Cai, S.; Lin, C.; Chen, Z.; Wang, T.; Gao, Z.; Zhou, C. Study of blockchains’s consensus mechanism based on credit. IEEE Access 2019, 7, 10224–10231. [Google Scholar] [CrossRef]
- Xu, X.L.; Zhu, D.W.; Yang, X.X.; Wang, S.; Qi, L.Y.; Dou, W.C. Concurrent practical byzantine fault tolerance for integration of blockchain and supply chain. ACM Trans. Internet Technol. (TOIT) 2021, 21, 1–17. [Google Scholar] [CrossRef]
- Tan, X.D.; Cheng, W.; Huang, H.P.; Jing, T.Y.; Wang, H.Y. Edge-aided searchable data sharing scheme for IoV in the 5G environment. J. Syst. Archit. 2023, 136, 102834. [Google Scholar] [CrossRef]
- Lu, Y.L.; Huang, X.H.; Zhang, K.; Maharjan, S.; Zhang, Y. Blockchain empowered asynchronous federated learning for secure data sharing in internet of vehicles. IEEE Trans. Veh. Technol. 2020, 69, 4298–4311. [Google Scholar] [CrossRef]
- Limbasiya, T.; Das, D. IoVCom: Reliable Comprehensive Communication System for Internet of Vehicles. IEEE Trans. Dependable Secur. Comput. 2019, 18, 2752–2766. [Google Scholar] [CrossRef]
- Su, Z.; Wang, Y.T.; Xu, Q.C.; Zhang, N. LVBS: Lightweight vehicular blockchain for secure data sharing in disaster rescue. IEEE Trans. Dependable Secur. Comput. 2020, 19, 19–32. [Google Scholar] [CrossRef]
- Kamal, M.; Srivastava, G.; Tariq, M. Blockchain-based lightweight and secured v2v communication in the internet of vehicles. IEEE Trans. Intell. Transp. Syst. 2020, 22, 3997–4004. [Google Scholar] [CrossRef]
- Dai, H.N.; Zheng, Z.B.; Zhang, Y. Blockchain for Internet of Things: A survey. IEEE Internet Things J. 2019, 6, 8076–8094. [Google Scholar] [CrossRef]
- Feng, Q.; He, D.B.; Zeadally, S.; Khan, M.K. A survey on privacy protection in blockchain system. J. Netw. Comput. Appl. 2019, 126, 45–58. [Google Scholar] [CrossRef]
- Li, W.Y.; Feng, C.L.; Zhang, L.; Xu, H.; Cao, B.; Imran, M.A. A scalable multi-layer PBFT consensus for blockchain. IEEE Trans. Parallel Distrib. Syst. 2020, 32, 1146–1160. [Google Scholar] [CrossRef]
- Mišić, J.; Mišić, V.B.; Chang, X.L.; Qushtom, H. Adapting PBFT for use with blockchain-enabled IoT systems. IEEE Trans. Veh. Technol. 2020, 70, 33–48. [Google Scholar] [CrossRef]
- Kim, Y.; Park, J. Hybrid decentralized PBFT Blockchain Framework for OpenStack message queue. Hum. Centric Comput. Inf. Sci. 2020, 10, 31. [Google Scholar] [CrossRef]
- Zhang, H.B.; Cao, Y.K.; Liu, K.J.; Wang, R.Y. Distributed trust management scheme based on blockchain in Internet of vehicles. J. Commun. 2023, 44, 148–157. [Google Scholar]
- Wang, D.; Jin, C.J.; Xiao, B.B.; Li, Z.; He, X. Proof-of-activity consensus algorithm based on K-medoids clustering. Big Data Res. 2021, 26, 100266. [Google Scholar] [CrossRef]
- Li, F.; Wang, C. Develop a multi-linear-trend fuzzy information granule based short-term time series forecasting model with k-medoids clustering. Inf. Sci. 2023, 629, 358–375. [Google Scholar] [CrossRef]
- Jia, B.; Zhang, X.S.; Liu, J.W.; Zhang, Y.; Huang, K.; Liang, Y.Q. Blockchain-enabled federated learning data protection aggregation scheme with differential privacy and homomorphic encryption in IIoT. IEEE Trans. Ind. Inform. 2021, 18, 4049–4058. [Google Scholar] [CrossRef]
- Han, R.C.; Shapiro, G.; Gramoli, V.; Xu, X.W. On the performance of distributed ledgers for internet of things. Internet Things 2020, 10, 100087. [Google Scholar] [CrossRef]
- Zheng, Z.B.; Xie, S.A.; Dai, H.N.; Chen, X.P.; Wang, H.M. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Zhang, C.; Zhao, M.; Zhu, L.; Zhang, W.; Wu, T.; Ni, J. FRUIT: A Blockchain-Based Efficient and Privacy-Preserving Quality-Aware Incentive Scheme. IEEE J. Sel. Areas Commun. 2022, 40, 3343–3357. [Google Scholar] [CrossRef]
- Zhang, C.; Hu, C.; Wu, T.; Zhu, L.; Liu, X. Achieving Efficient and Privacy-Preserving Neural Network Training and Prediction in Cloud Environments. IEEE Trans. Dependable Secur. Comput. 2023, 20, 4245–4257. [Google Scholar] [CrossRef]
- Hu, C.F.; Zhang, C.; Lei, D.; Wu, T.; Liu, X.M.; Zhu, L.H. Achieving Privacy-Preserving and Verifiable Support Vector Machine Training in the Cloud. IEEE Trans. Inf. Forensics Secur. 2022, 40, 3343–3357. [Google Scholar] [CrossRef]



| Node Type | Node Description | Node Rights |
|---|---|---|
| Primary Node | Trusted, selected from RSUs | Voting Rights, Block Generation Rights, Block Verification Rights |
| General RSU Node | Trusted | Voting Rights, Block Verification Rights |
| Normal Node | Vehicle nodes ensuring correct and timely message communication | Voting Rights |
| Abnormal Node | Experiencing malfunction or engaged in malicious behavior | No rights granted |
| Consensus Phase | PBFT | CDBFT | SG-PBFT | ESBCP |
|---|---|---|---|---|
| Request | 1 | 1 | 1 | |
| Pre-prepare | N − 1 | N − 1 | N/2 − 1 | (N − 1) |
| Prepare | (N − 1)2 | (N − 1)2 | (N/2 − 1)(N/2 − 1) | (N − 1) |
| Commit | N(N − 1) | N(N − 1) | N/2 − 1 | (N − 1) + (N − 1) |
| Reply | N | N | N | |
| Total | 2N2 − N + 1 | 2N2 − N + 1 | N2/4 + N | N |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Si, X.; Li, M.; Yao, Z.; Zhu, W.; Liu, J.; Zhang, Q. An Efficient and Secure Blockchain Consensus Protocol for Internet of Vehicles. Electronics 2023, 12, 4285. https://doi.org/10.3390/electronics12204285
Si X, Li M, Yao Z, Zhu W, Liu J, Zhang Q. An Efficient and Secure Blockchain Consensus Protocol for Internet of Vehicles. Electronics. 2023; 12(20):4285. https://doi.org/10.3390/electronics12204285
Chicago/Turabian StyleSi, Xueming, Min Li, Zhongyuan Yao, Weihua Zhu, Jianmei Liu, and Qian Zhang. 2023. "An Efficient and Secure Blockchain Consensus Protocol for Internet of Vehicles" Electronics 12, no. 20: 4285. https://doi.org/10.3390/electronics12204285
APA StyleSi, X., Li, M., Yao, Z., Zhu, W., Liu, J., & Zhang, Q. (2023). An Efficient and Secure Blockchain Consensus Protocol for Internet of Vehicles. Electronics, 12(20), 4285. https://doi.org/10.3390/electronics12204285







